Sniffing RDP Auth with Cain and Able.
You can download Cain & Able from http://www.oxid.it/cain.html
This was tested in my lab with 2 xp machines. 1 of which has the latest version of RDP installed, both directions the traffic is readable once decrypted.
You will need a minimum of 3 machines to test this. 1 Windows Host with RDP enabled, 1 Windows host for Cain and Able (You cant spoof yourself!), and an additional machine linux or windows box with RDP client.
For more info on ARP attack see
http://en.wikipedia.org/wiki/ARP_poisoning
Install the app.
Once the app is installed, open up Cain and click the sniffer Button (Network interface icon torwards the top of window)
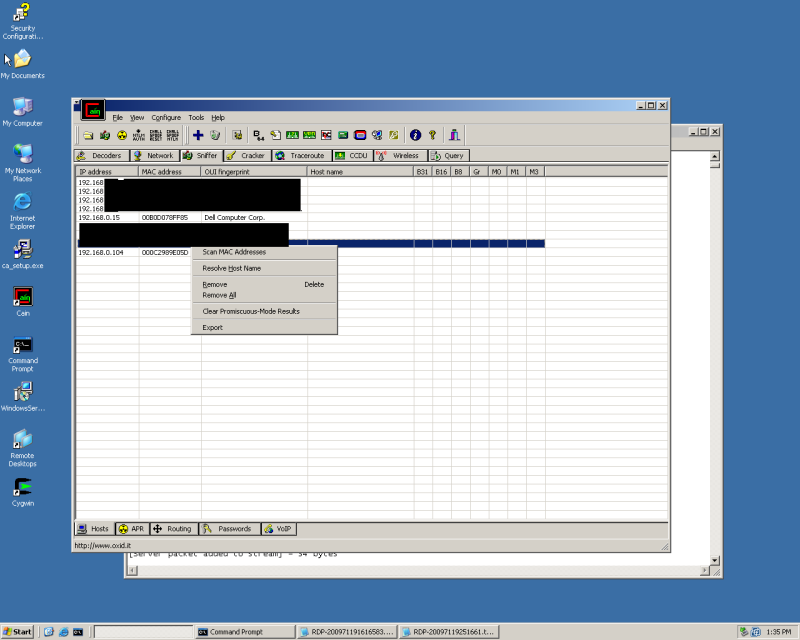
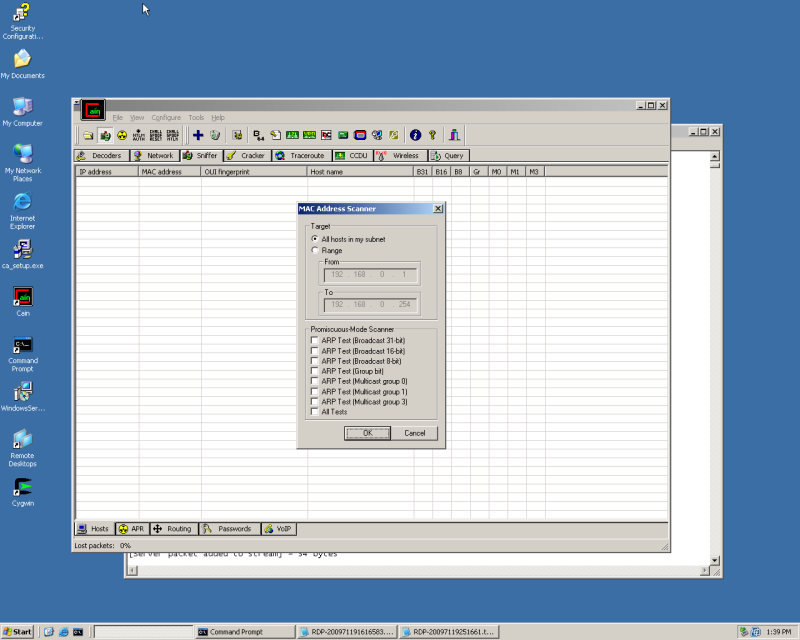
Right Click inside the blank area, select Scan Mac's, you'll be prompted for scanning a range or subnet, select what you need.
Once the scan completes you should see a list of hosts
Select the APR Tab (Radioactive symbol) at the bottom of the window,
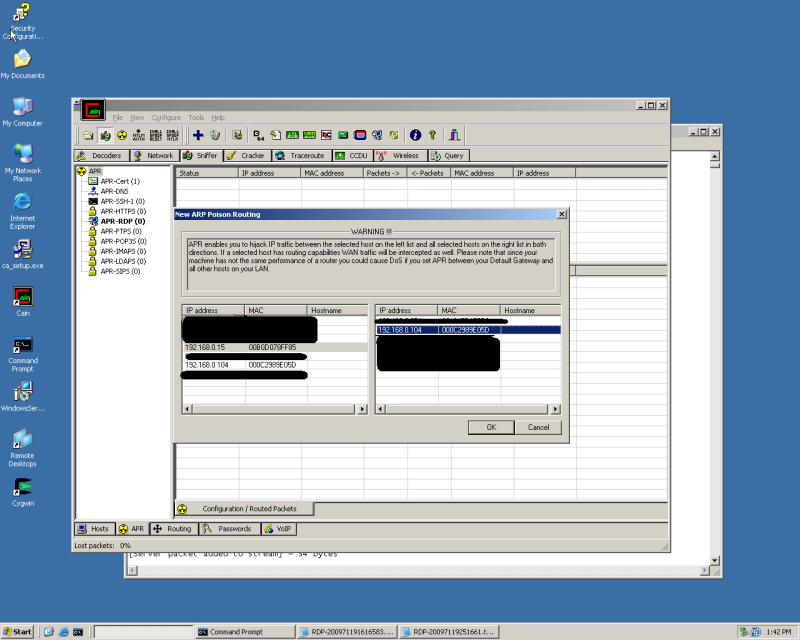
Next select the Blue + and select the 2 machines you would like to ARP Poison (The order you select them in makes no difference)
***Note: Be very careful on what devices you are spoofing in relation to the hardware you are using, you can lock up a network in no time.
At this point you will show a status of idle. Enable Arp Spoofing by clicking the Radioactive Icon at the TOP of the window (right next to the sniffer button) You should see the status change to Poisoning.
Now Generate your RDP traffic.
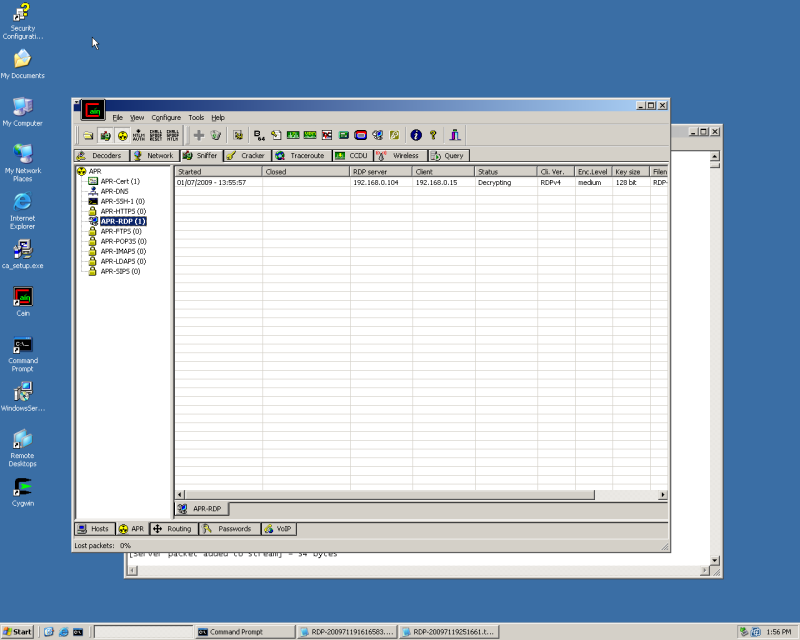
You should the the APR-RDP value populate. Disconnect your RDP session.
You should see the status change from Decrypting to "Closed" You're now ready to dig through the file
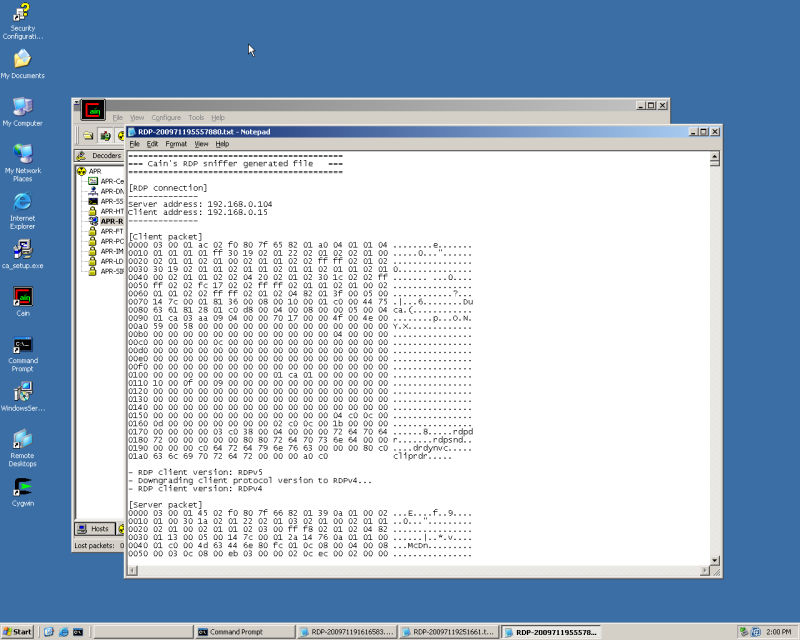
Right Click and view the file. You should see a file similar to my example.
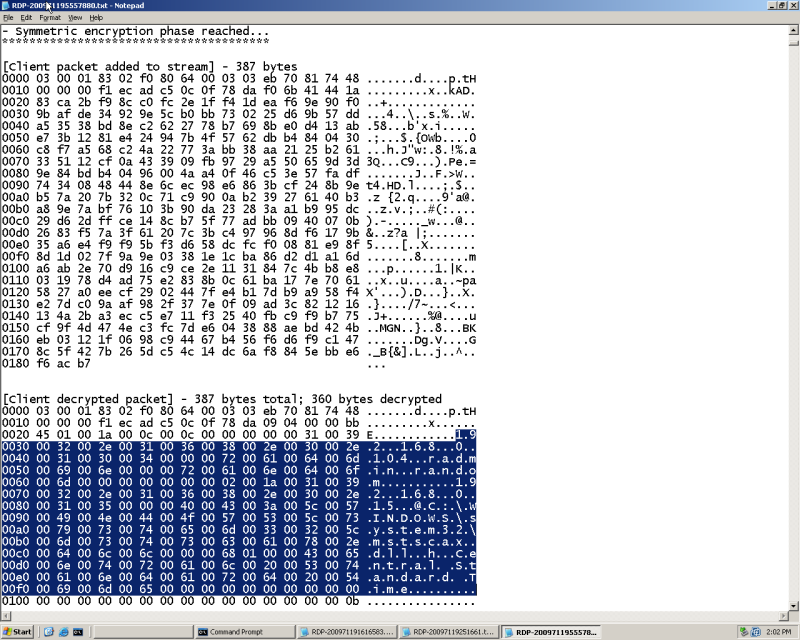
Ctrl F for "- Symmetric encryption phase reached..." Look at the second column down from there.
I've Highlighted the Information in question, You can see the IP address you are accessing followed by username and password. In my case, radmin is the username and random is the password.
EvX
google.com and some free time!