Network Defense
OpenVPN
31 March, 2010 - 01:46 — kidA web-scale networking platform enabling the next wave of VPN services
? Supports scalable and secure VPN services across Internet
? Works with existing enterprise applications
? Enables real-time interactive collaboration applications
? Remote and secure access to your network and application resources
? Secure and scalable Site-to-Site VPN
? Wireless security
Scanrand
31 March, 2010 - 01:40 — kidAn unusually fast stateless network service and topology discovery system
Scanrand is a stateless host-discovery and port-scanner similar in design to Unicornscan. It trades off reliability for amazingly fast speeds and uses cryptographic techniques to prevent attackers from manipulating scan results. This utility is a part of a software package called Paketto Keiretsu, which was written by Dan Kaminsky. Scanrand and Paketto are no longer actively maintained, but the latest released version can still be found at DoxPara.Com.
Snort
18 March, 2010 - 11:24 — greySnort is a free, open source network intrusion detection and prevention system capable of performing real-time traffic analysis and packet logging on IP networks.

Snort can perform protocol analysis and content searching/matching. It can be used to detect a variety of attacks and probes, such as buffer overflows, stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts, and much more. It uses a flexible rules language to describe traffic that it should collect or pass, as well as a detection engine that utilizes a modular plug-in architecture. Snort has a real-time alerting capability as well, incorporating alerting mechanisms for syslog, a user specified file, a UNIX socket, or WinPopup messages to Windows clients. Snort has three primary uses: a straight packet sniffer like tcpdump, a packet logger (useful for network traffic debugging, etc), or a full-blown network intrusion prevention system.
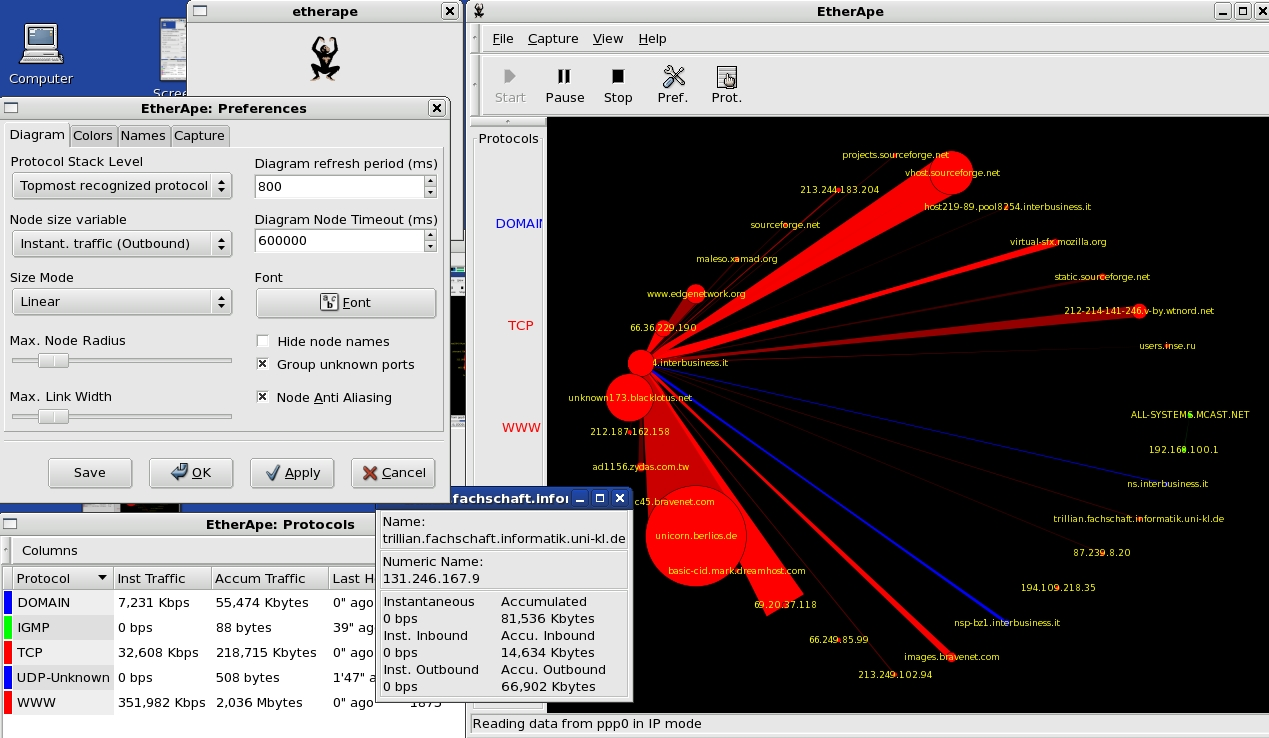
EtherApe
18 March, 2010 - 11:14 — greyEtherApe is a graphical network monitor for Unix modeled after etherman. Featuring link layer, ip and TCP modes, it displays network activity graphically. Hosts and links change in size with traffic. Color coded protocols display.
It supports Ethernet, FDDI, Token Ring, ISDN, PPP and SLIP devices. It can filter traffic to be shown, and can read traffic from a file as well as live from the network.
AATools
18 March, 2010 - 01:40 — greyAATools is a multithreaded network diagnostic tool. Its purpose is to accumulate data pertaining to network status and availability, using all of the latest development tools in network research.
It is a 12-in-1 utility, including Port Scanner, Proxy Analyzer, TraceRoute, Email Verifier, Links Analyzer, Network Status, Process Info, Whois, System Info, Resource Viewer and Registry Cleaner.
- Port Scanner - analyses hosts and different services started on them. Its comprehensive scanning engine gathers all the information about the services, threads etc. Port Scanner accurately determines the mapping of the active services on the appropriate host using TCP/IP port interrogation. This information is rather critical for developing and/or verifying of the security policies;
- Proxy Analyzer - a special instrument, designed to manage a database of proxy ervers located all over the world. This program is essential for those who are concerned with their privacy and who want to surf the web anonymously;
- RBL (RealTime Black List) Locator is a special tool, designed to quickly search for an IP address in DNS-Based (RBL*) spam databases. RBL Locator checks a given IP address against the most known blacklists.
- TraceRoute - shows you the path a packet sent from your machine to some other machine on the network takes as it hops from router to router. It will show you the IP address (and the actual name, usually) of each router, line-by-line.
- Email Verifier - the unique solution for the "message delivery error". You don't need to disturb your clients and friends anymore to check if their
e-mail addresses are still valid. E-mail Verifier connects directly to their SMTP server and checks it for you. Nothing is sent to the recipient;
Port Reporter
18 March, 2010 - 00:35 — greyThe Port Reporter tool runs as a service on computers that are running Windows Server 2003, Windows XP, and Windows 2000. The tool logs TCP and UDP port activity.
Tcptraceroute
17 March, 2010 - 15:15 — kidtcptraceroute is a traceroute implementation using TCP packets.
The more traditional traceroute( sends out either UDP or ICMP ECHO packets with a TTL of one, and increments the TTL until the destination has been reached. By printing the gateways that generate ICMP time exceeded messages along the way, it is able to determine the path packets are taking to reach the destination.
sends out either UDP or ICMP ECHO packets with a TTL of one, and increments the TTL until the destination has been reached. By printing the gateways that generate ICMP time exceeded messages along the way, it is able to determine the path packets are taking to reach the destination.
The problem is that with the widespread use of firewalls on the modern Internet, many of the packets that traceroute( sends out end up being filtered, making it impossible to completely trace the path to the destination. However, in many cases, these firewalls will permit inbound TCP packets to specific ports that hosts sitting behind the firewall are listening for connections on. By sending out TCP SYN packets instead of UDP or ICMP ECHO packets, tcptraceroute is able to bypass the most common firewall filters.
sends out end up being filtered, making it impossible to completely trace the path to the destination. However, in many cases, these firewalls will permit inbound TCP packets to specific ports that hosts sitting behind the firewall are listening for connections on. By sending out TCP SYN packets instead of UDP or ICMP ECHO packets, tcptraceroute is able to bypass the most common firewall filters.
IP Filter
17 March, 2010 - 15:12 — kidIPFilter is a software package that can be used to provide network address translation (NAT) or firewall services. To use, it can either be used as a loadable kernel module or incorporated into your UNIX kernel; use as a loadable kernel module where possible is highly recommended. Scripts are provided to install and patch system files, as required.
Sguil
17 March, 2010 - 15:07 — kidSguil (pronounced sgweel) is built by network security analysts for network security analysts. Sguil's main component is an intuitive GUI that provides access to realtime events, session data, and raw packet captures. Sguil facilitates the practice of Network Security Monitoring and event driven analysis. The Sguil client is written in tcl/tk and can be run on any operating system that supports tcl/tk (including Linux, *BSD, Solaris, MacOS, and Win32).
CallerIP
16 March, 2010 - 22:56 — greySimilar to Caller ID for your telephone, CallerIP shows you who is connecting to your system at any time.
# Plot all connections
This feature enables you to have CallerIP plot all the connections on the world map. This in turn allows for easy and quick analysis of where connections made to/from your machine reside.
# New look table
The new look table includes gradient fills. This means the color of the row in the table depends on the threat of the connection. If the connection being made to your machine is harmless then the gradient will be green. Another quick an easy way to identify the threat of a connection.
# Condensed CallerIP
CallerIP now allows you to minimize it to a very small and detailed dialog box. The small window gives you everything you need to know but stays in the background.
# Realtime monitoring instantly identifies suspect activity and spyware
CallerIP monitors all connections to and from your system and actively scans ports for possible back doors that allow unauthorized access.
# Identifies the country of origin for all connections
A connection to/from a high-risk country is a key indicator of suspect activity and could likely be someone looking to steal your confidential information or compromise your system. CallerIP shows you the country location of connections so you can identify suspect activity and protect your information.
# Network Provider reporting with abuse reporting information
See the contact and abuse reporting information for the company providing internet access for an IP address or website, so you can easily report hackers or Internet abuse.
# Worldwide Whois reports
CallerIP Pro queries worldwide databases to report the up-to-date registration information for the 'owner' of an IP address or domain. Information includes name, address, phone and email contact information.
# Detailed log of connection history with search options