Remote Administration Tool
skl0g
23 April, 2010 - 16:46 — kidThis is a keylogger which can log all keystrokes, is case-sensitive and supports all standard keys. It has been written in vb, uses the GetAsyncKeyState API call and doesn't need any other dll or ocx file(only the standard vb6 dlls). It restarts when you start windows (modifies the registry) and can be started/stopped anytime by using key combinations.
OpenVPN
31 March, 2010 - 01:46 — kidA web-scale networking platform enabling the next wave of VPN services
? Supports scalable and secure VPN services across Internet
? Works with existing enterprise applications
? Enables real-time interactive collaboration applications
? Remote and secure access to your network and application resources
? Secure and scalable Site-to-Site VPN
? Wireless security
BootRoot
18 March, 2010 - 00:31 — greyeEye BootRoot is a project presented at Black Hat USA 2005 by researchers Derek Soeder and Ryan Permeh, as an exploration of technology that custom boot sector code can use to subvert the Windows kernel as it loads. The eEye BootRootKit is a boot sector-based NDIS backdoor that demonstrates the implementation of this technology.
Additional Information
Because BootRoot is detected and auto-quarantined by most anti-virus installations, the .zip is password protected with 'eeye' as the password.
Big Brother
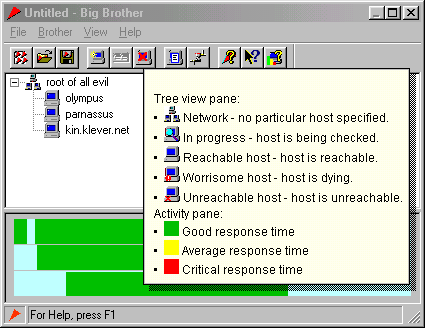
16 March, 2010 - 22:46 — greyBig Brother is the simplest tool for monitoring your IP-network for troubles. It gives you a comprehensive picture of what happened to any point on the Net that you put in. Just add the host of interest by specifying its IP address or hostname and optional short description for your information.
PuTTY
16 February, 2010 - 23:28 — kidA secure way to access remote computers
SSH (Secure Shell) is the now ubiquitous program for logging into or executing commands on a remote machine. It provides secure encrypted communications between two untrusted hosts over an insecure network, replacing the hideously insecure telnet/rlogin/rsh alternatives.
Returnil Virtual System 2010
26 January, 2010 - 01:07 — greyReturnil Virtual System 2010 is similar to Faronics-Deepfreeze, with a few differences. it can be turned on and off like you would turn a light on and off, a simple press of a button. It is your standard Virtualization software coupled with an antivirus that helps protect your computer from permanent damage. It, like Deepfreeze has the capability of mounting a virtual disk for static data storage. And all the settings can be password protected so that you can edit them without having to be signed in to any special account.
Driftnet
4 August, 2009 - 23:56 — EverestXDriftnet: One of the funnest ways to watch your userland web traffic with no text!
Excerpt from the page:
"Inspired by EtherPEG [...], Driftnet is a program which listens to network traffic and picks out images from TCP streams it observes. Fun to run on a host which sees lots of web traffic.
In an experimental enhancement, driftnet now picks out MPEG audio streams from network traffic and tries to play them. You can also now use driftnet with Jamie Zawinski's webcollage, so that it can run as a screen saver."
Faronics-Deep Freeze
20 November, 2008 - 15:08 — watchmakerAdded by recommendation from K80
Faronics Deep Freeze helps eliminate workstation damage and downtime by making computer configurations indestructible. Once Deep Freeze is installed on a workstation, any changes made to the computer—regardless of whether they are accidental or malicious—are never permanent. Deep Freeze provides immediate immunity from many of the problems that plague computers today—inevitable configuration drift, accidental system misconfiguration, malicious software activity, and incidental system degradation.
Deep Freeze ensures computers are absolutely bulletproof, even when users have full access to system software and settings. Users get to enjoy a pristine and unrestricted computing experience, while IT personnel are freed from tedious helpdesk requests, constant system maintenance, and continuous configuration drift.
Netcat
6 April, 2008 - 16:59 — OriginNetcat is a computer networking service for reading from and writing network connections using TCP or UDP. Netcat is designed to be a dependable “back-end” device that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and investigation tool, since it can produce almost any kind of correlation you would need and has a number of built-in capabilities.
In 2000, according to www.insecure.org, Netcat was voted the second most functional network security tool. Also, in 2003 and 2006 it gained fourth place in the same category. Netcat is often referred to as a "Swiss-army knife for TCP/IP." Its list of features includes port scanning, transferring files, and port listening, and it can be used as a backdoor.
Some of netcat's major features are:
* Outbound or inbound connections, TCP or UDP, to or from any ports
* Full DNS forward/reverse checking, with appropriate warnings
* Ability to use any local source port
* Ability to use any locally-configured network source address
* Built-in port-scanning capabilities, with randomization
* Built-in loose source-routing capability
* Can read command line arguments from standard input
* Slow-send mode, one line every N seconds
* Hex dump of transmitted and received data
* Optional ability to let another program service established connections
* Optional telnet-options responder
* Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel.
Examples
Opening a raw connection to port 25 (like telnet)
nc mail.server.net 25
Setting up a one-shot webserver on port 8080 to present a file
{ echo -ne "HTTP/1.0 200 OK\r\n\r\n"; cat some.file; } | nc -l 8080
