Extending your MSF Exploit list with Packetstorms Exploit releases sloppy style.
What you'll need:
-----------------
1 Linux box, for this example I am using BT4 Pre
2 A tgz with rb.txt files. I've supplied 2 links above.
A working install of Metasploit.
A wall of text and disclaimer:
====================
If you aren't aware Packetstormsecurity.org releases a monthly tgz of all the exploits for the month, and they also release annual packages.
For example you can find the month of December 2009's here (599 exploits)
http://packetstormsecurity.org/0912-exploits/0912-exploits.tgz
And the year 2009 package here (4,006 exploits).
http://packetstormsecurity.org/0912-exploits/2009-exploits.tgz
These packages regularly come with .rb files for framework, however many of these releases are never included in the official download of framework for whatever various reason.
I'm going to show you an *extremely sloppy* method to extract the .rb.txt files and place them in your framework install. Essentially, all it is extract, rename extensions, cp to the framework directory, start framework. If you understand that, then you really wont need to read a whole lot of this.
While most Linux regulars will take this as casual tasks, many users simply dont. To explain why I say this is a sloppy method, not all of the .rb files are always going to be working right off the bat, or may require plugins, etc, and will not run, this is just a simple method to increase the amount of available exploits for you to use in framework rather quickly. I highly recommend that you take a look over your .rb files before running them, and researching the various exploits you are interested in how they work and so forth.
It's also worth nothing, that in general most of the exploits are not usable in MSF in the file, but as you will see in a minute, there are quite a few none the less. To clarify, you will not gain 4,006 usable exploits for framework with the '09 package not even close. For this example I'll be demonstrating this process with the 2009 complete package.
If you aren't familiar with these releases, they have a great HTML setup with details regarding the things. In several cases I have seen some of the files be released for framework but not have a .rb extension in which case the renamer will miss it, so once again this proves how this is an overall sloppy method.
Also with this method about 10 of the files will toss up errors on launch of msf, research the .rb file, the author will let you know of any requirements or directory structure.
I'll also mention that some of the months dont have any .rb.txt files at all. There are 2 in 0906, amd 1 in 0909 the rest are in 0910 and up.
Brass Tack's:
=========
First Step:
-----------
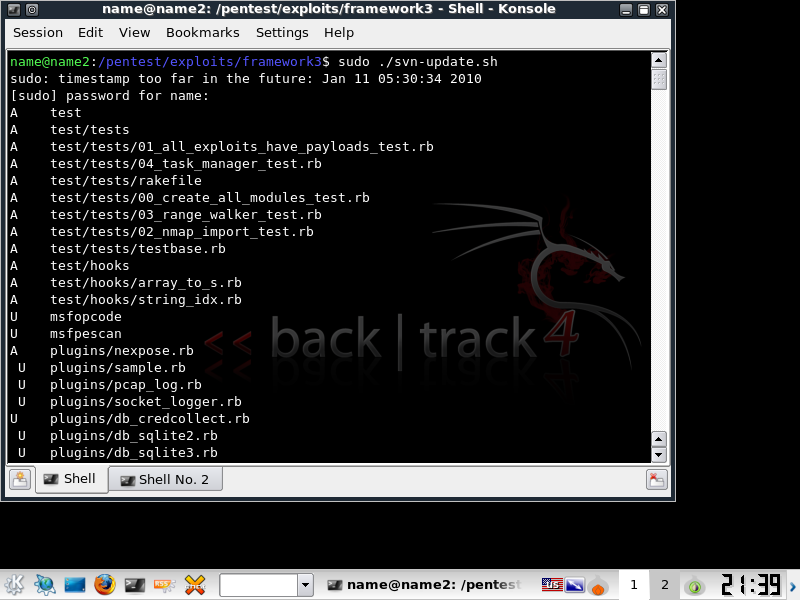
First update your msf. If you are on a base install of Framework in BT4 Pre, this will take a while.
sudo msfupdate or svn-update.sh in /pentest/exploits/framework3/
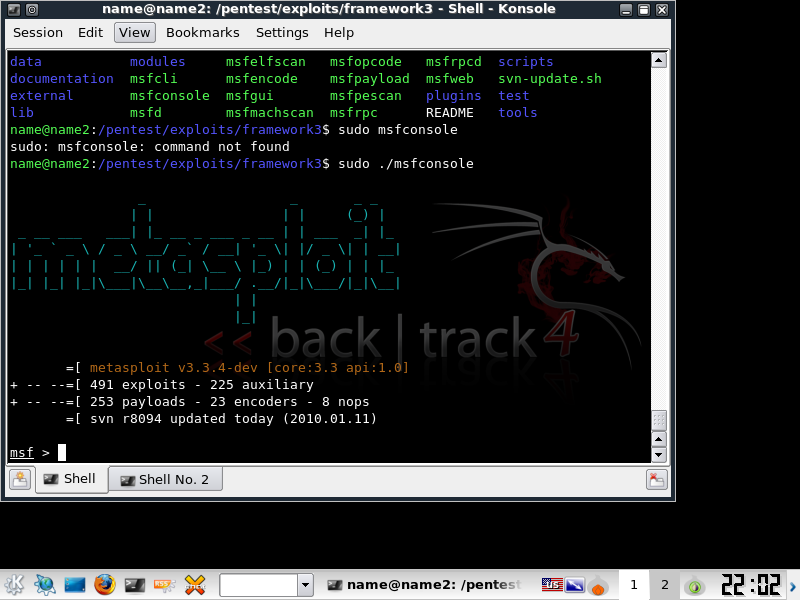
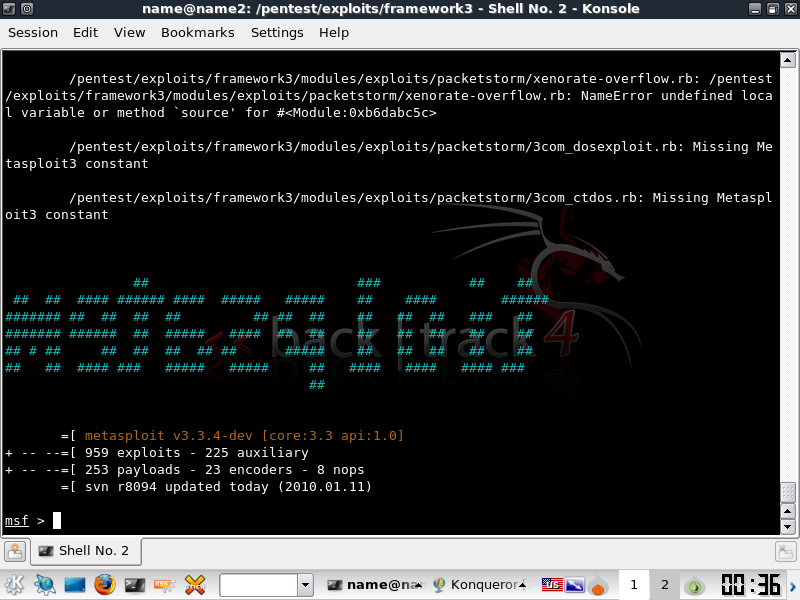
Here's a screen shot of the latest version of Framework (as of this date revision 8094). Notice that there are currently 491 exploits.
Download the Annual exploit package.
-------------------------------------------------
This file is 30mb and may take some time to download.
wget -d http://packetstormsecurity.org/0912-exploits/2009-exploits.tgz
Extract the File
tar -xzvf 2009-exploits.tgz
Creating the file renamer script.
----------------------------------------
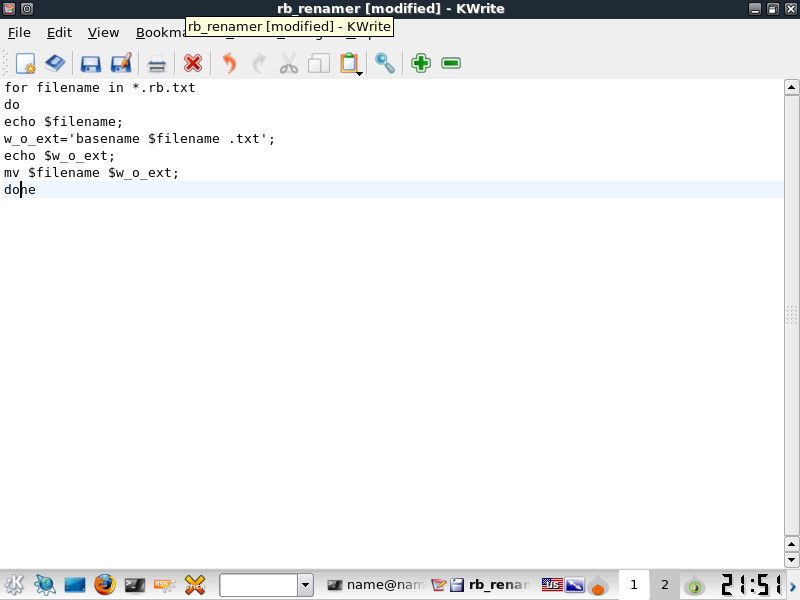
Here's a 7 line script I tossed together based on examples on the net. Create a file called rb_renamer and paste this into the contents. Honestly, I'd like to modify the script to automatically move the .rb files out to the right path but currently its just a simple renamer. You'll be moving them out of the directorys manually. In the example I used kwrite to create and enter the contents. You should use vim.
=============SCRIPT===============
for filename in *.rb.txt
do
echo $filename;
w_o_ext=`basename $filename .txt`;
echo $w_o_ext;
mv $filename $w_o_ext;
done
=============SCRIPT===============
Now Chmod your file to execute.
chmod 777 rb_renamer
Using the renamer
-----------------
Now you should have the renamer created as well as the tar extracted, since the script must be run from the path of the files, you will need to move it to the various months files with cp.
cp rb_renamer 0906-exploits
./rb_renamer
The files are renamed from rb.txt to .rb if everything went well. Now cp them to /pentest/exploits/framework3/modules/exploits/[some dir]/
cp *.rb /pentest/exploits/framework3/modules/exploits/[some dir/
REPEAT THIS STEP FOR THE REST OF THE MONTHS LISTED AT THE TOP OF THE PAGE containing .rb files
At this point, you've copied the files fire up MSF and see what you got out of this whole ordeal. 949 total listed exploits, that's well over 300 additional working exploits with minimal effort. Granted not all of them will work with this method, some are in the wrong directory, or not exploits at all. If you would read through the HTML info, it would reduce a lof of the confusion. Doing your research really helps fix these issues.
That's it.
For those of you worried about the updates and package download showing up over the wire you can use proxychains with wget, apt-get, and Framework. Please note you will likely leak dns traffic. See my guide on TORK in BT4 under tutorials for more information.
EvX